
In today's world, where cyber threats are more prevalent than ever, effective cybersecurity documentation stands as a vital pillar for protecting sensitive information, especially in the healthcare sector. This article explores ten essential practices that not only bolster compliance with industry regulations but also strengthen organizational resilience against potential breaches. With a staggering percentage of cyber incidents arising from human error, one must ask: how can organizations ensure that their documentation transcends mere formality, evolving into a robust framework that actively mitigates risks and cultivates a culture of security?
The healthcare landscape is fraught with unique challenges, making it imperative for CFOs and decision-makers to prioritize cybersecurity. As the stakes rise, so does the need for comprehensive strategies that address these vulnerabilities head-on. By implementing effective documentation practices, organizations can not only comply with regulations but also foster a proactive approach to security that resonates throughout their operations.
In today’s digital landscape, the importance of robust cybersecurity cannot be overstated, especially in the healthcare sector. Cyber Solutions Inc. specializes in creating tailored cybersecurity procedures that address the unique requirements of various industries, ensuring that organizations can navigate the complex web of regulatory requirements with ease. Our Compliance as a Service (CaaS) solutions simplify adherence to standards like HIPAA, PCI-DSS, CMMC, SOX, and GDPR, which are critical for maintaining patient trust and operational integrity.
Healthcare organizations face unique challenges when it comes to cybersecurity. With sensitive patient data at stake, the implications of a breach can be devastating, not just financially but also in terms of reputation. By providing comprehensive risk assessments, policy development, and ongoing compliance monitoring, we ensure that your documentation not only meets compliance requirements but also enhances operational efficiency. This customized strategy assists businesses in reducing risks while upholding a strong protective stance, ultimately enabling them to concentrate on their primary activities without the weight of IT complications.
Moreover, our Incident Response services are designed to minimize the impact of cyberattacks. We rapidly identify, contain, and mitigate threats, restoring systems and ensuring business continuity. In a world where cyber threats are ever-evolving, having a proactive partner like Cyber Solutions can make all the difference. Are you ready to fortify your organization against potential cyber threats? Let us help you navigate the complexities of cybersecurity with confidence.
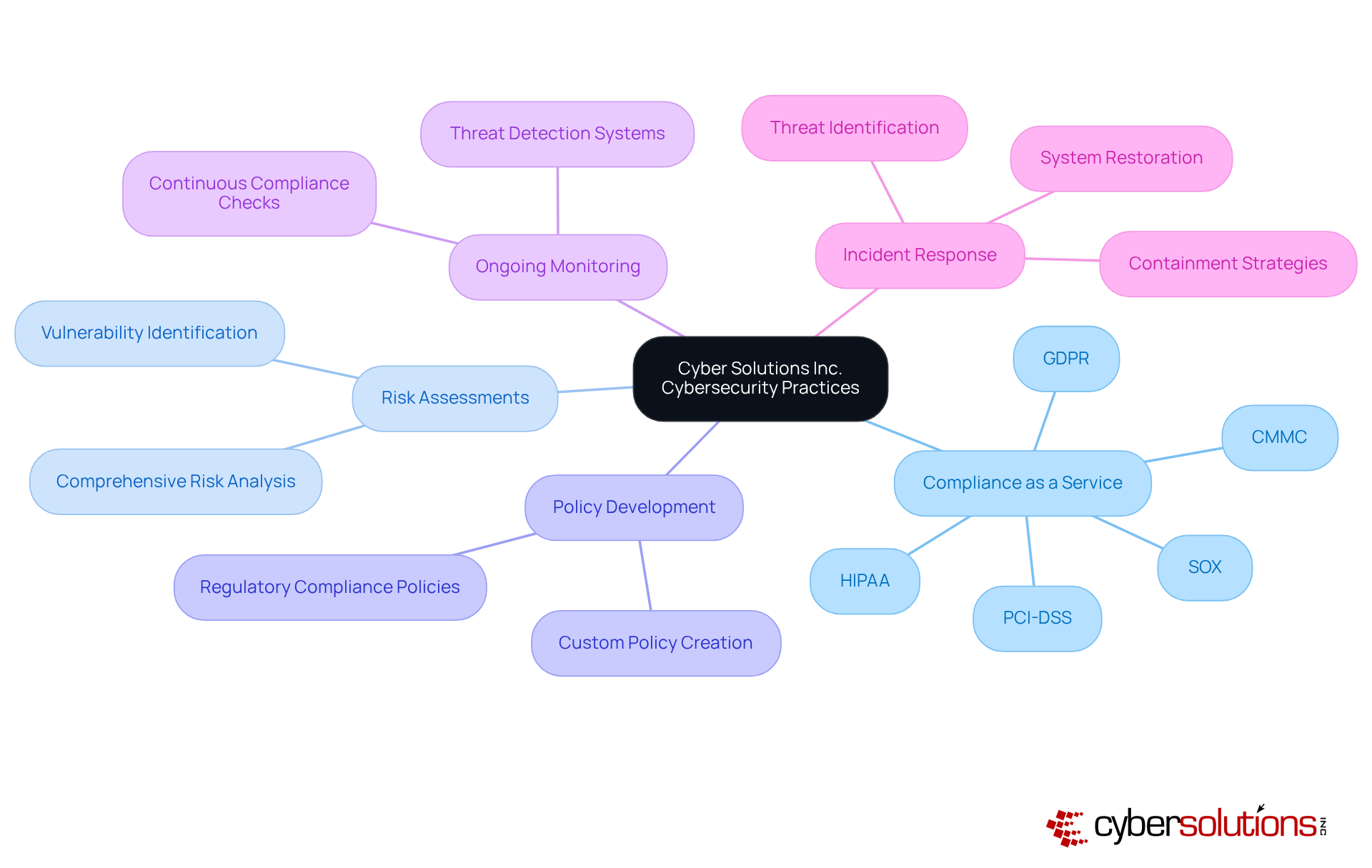
Creating explicit cybersecurity documentation for information protection policies is not just important; it’s essential for outlining a company's safety objectives and expectations, particularly when it comes to safeguarding federal data. In a landscape where 88% of cyber incidents stem from human errors, cybersecurity documentation must thoroughly address:
This ensures adherence to stringent cybersecurity documentation standards that are vital for protecting Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
Organizations that implement robust data protection measures showcase the effectiveness of well-defined policies in maintaining eligibility for lucrative government contracts. By ensuring that all employees comprehend these policies, organizations foster a culture of safety and compliance, which is crucial for adhering to CMMC Level 1 practices. This proactive approach not only reduces the likelihood of breaches but also enhances the overall security posture.
Cybersecurity experts emphasize that effective cybersecurity documentation is foundational. As one expert noted, "Security is a culture, not merely a control," underscoring the necessity for a holistic approach to security. In today’s environment, fostering awareness and adherence to these policies is more critical than ever. Are your policies up to the challenge?
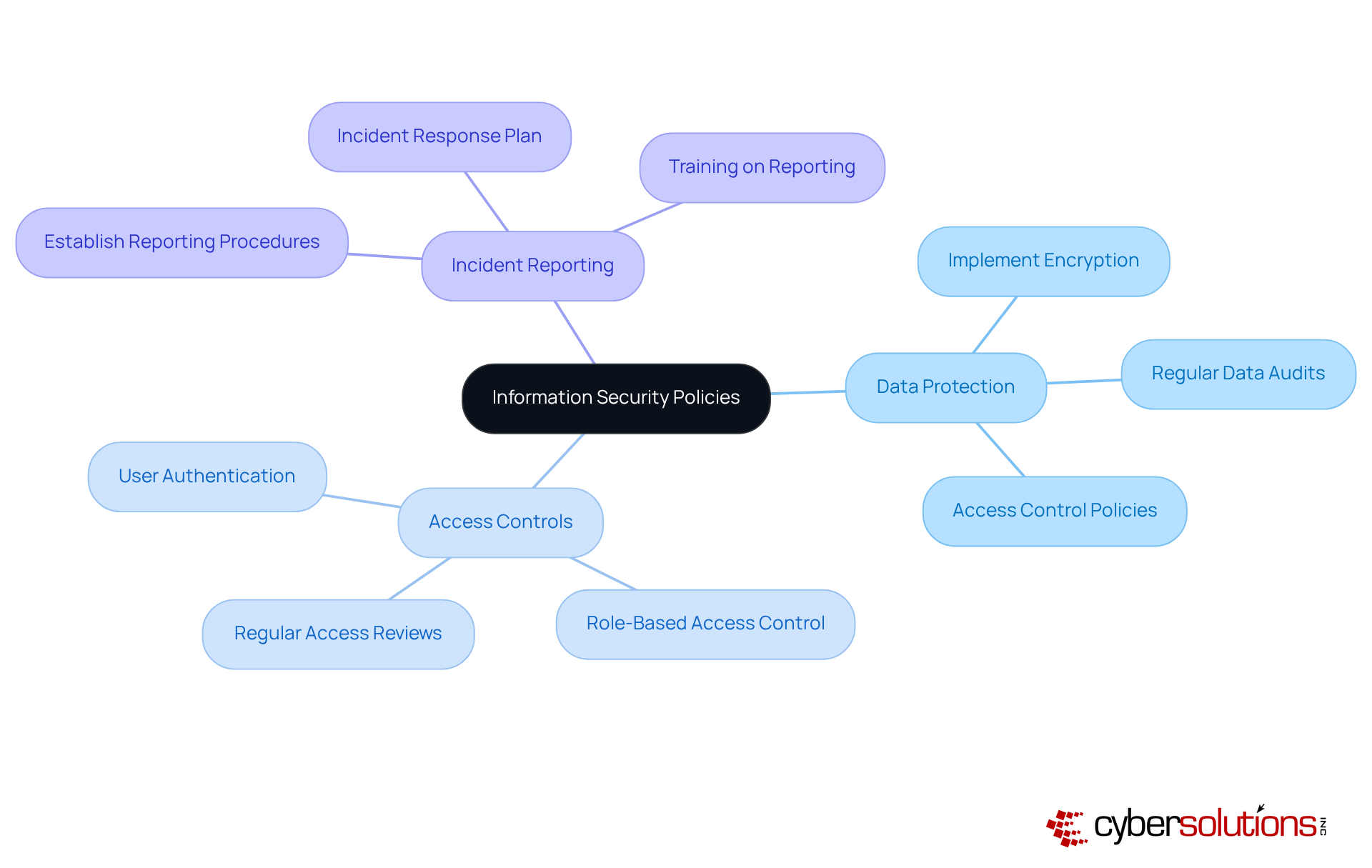
In today’s healthcare landscape, maintaining comprehensive cybersecurity documentation for incident response plans is not just important; it’s essential for organizations to effectively navigate cybersecurity incidents, especially under HIPAA regulations. These plans must clearly define roles, responsibilities, and procedures for detecting, responding to, and recovering from incidents, ensuring that cybersecurity documentation is in strict adherence to HIPAA standards. To keep them effective and relevant in an ever-evolving threat landscape, regular updates and rigorous testing of cybersecurity documentation are crucial.
Organizations that prioritize cybersecurity documentation in their incident response planning can significantly minimize damage and enhance recovery speed following breaches. For instance, Suncor’s robust planning allowed for swift control of their breach, showcasing the effectiveness of proactive strategies in upholding regulations. As Tannu Jiwnani aptly puts it, "Preparation is the foundation," highlighting how proactive planning transforms a reactive mindset into a resilient posture.
Moreover, ongoing training and simulations are vital for maintaining comprehensive cybersecurity documentation. They promote adaptability and ensure that all team members are prepared to react quickly and efficiently when incidents arise, particularly in accordance with HIPAA regulations. Alarmingly, just 30% of organizations evaluate their incident response plans, underscoring the critical need for regular assessments to meet regulatory obligations.
Furthermore, engaging all departments in incident response planning is crucial. A multidisciplinary approach not only improves overall effectiveness but also enhances adherence to HIPAA standards. Neglecting incident response planning can lead to prolonged exposure to threats and increased costs, reinforcing the necessity of a well-structured plan that aligns with HIPAA compliance.
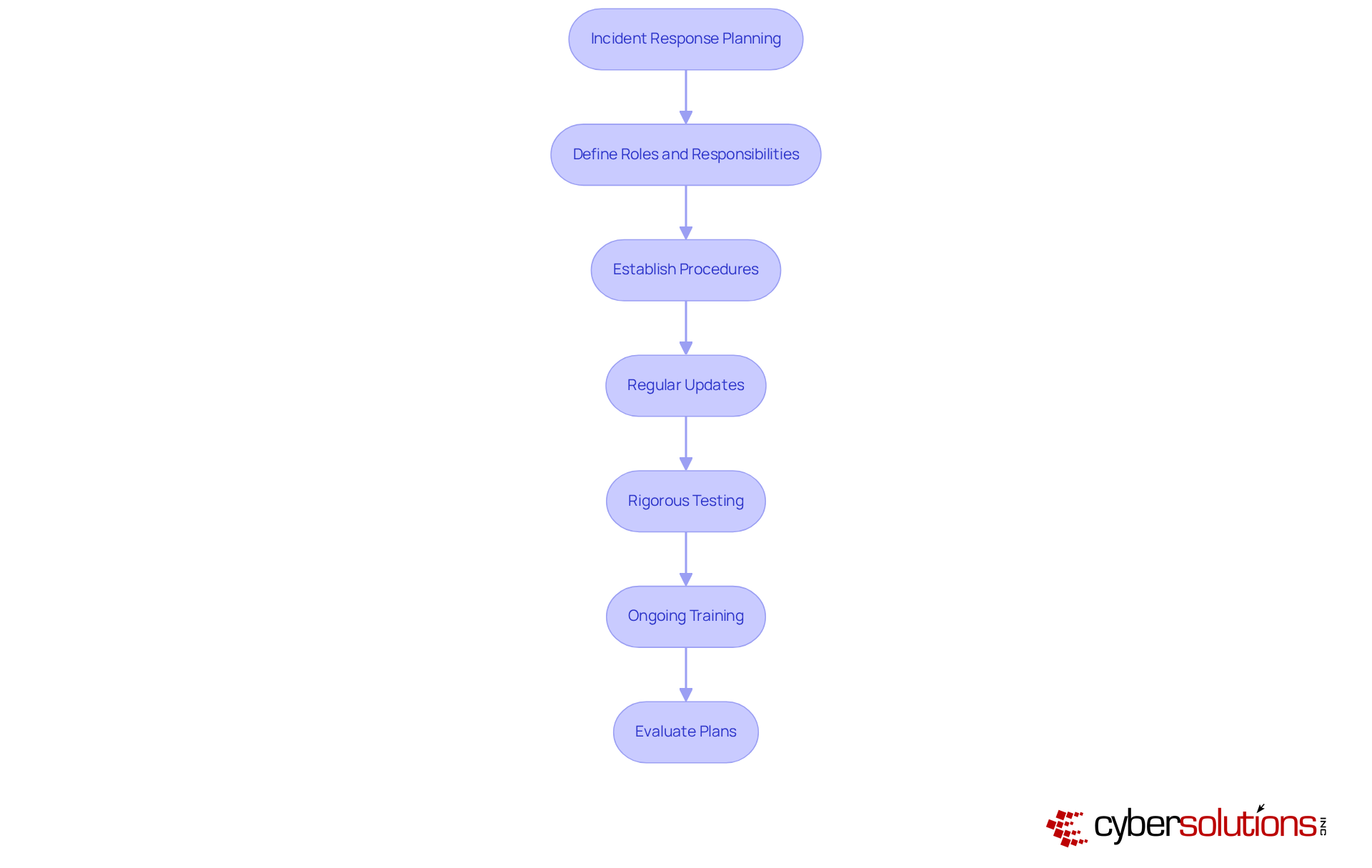
Conducting regular risk evaluations is not just a best practice; it’s essential for identifying potential threats and vulnerabilities within a company. These assessments evaluate the likelihood and impact of various risks, enabling organizations to prioritize their cybersecurity efforts effectively. By integrating risk evaluations into their security strategy, companies can allocate resources more efficiently and enhance their overall security posture.
Current trends indicate that organizations are increasingly recognizing the importance of these assessments. For example, a striking 94% of entities are evaluating Managed Detection and Response (MDR) services, reflecting a significant shift towards proactive threat management. Industry leaders emphasize that without thorough risk evaluations, organizations remain vulnerable to cyberattacks, data breaches, and substantial financial losses. As Mekan Bairyev aptly states, "Without assessing risks, entities remain vulnerable to cyberattacks, data breaches, financial losses, legal consequences, and reputational damage."
To conduct effective risk assessments, organizations should follow a structured approach:
By prioritizing risks according to their significance, organizations can implement targeted strategies to mitigate threats effectively. This proactive stance not only enhances security but also ensures compliance with regulatory frameworks, ultimately safeguarding sensitive data and maintaining operational integrity through comprehensive cybersecurity documentation. Notably, the average cost of a data breach globally is rising to around $4.88 million, underscoring the financial implications of inadequate risk assessments.
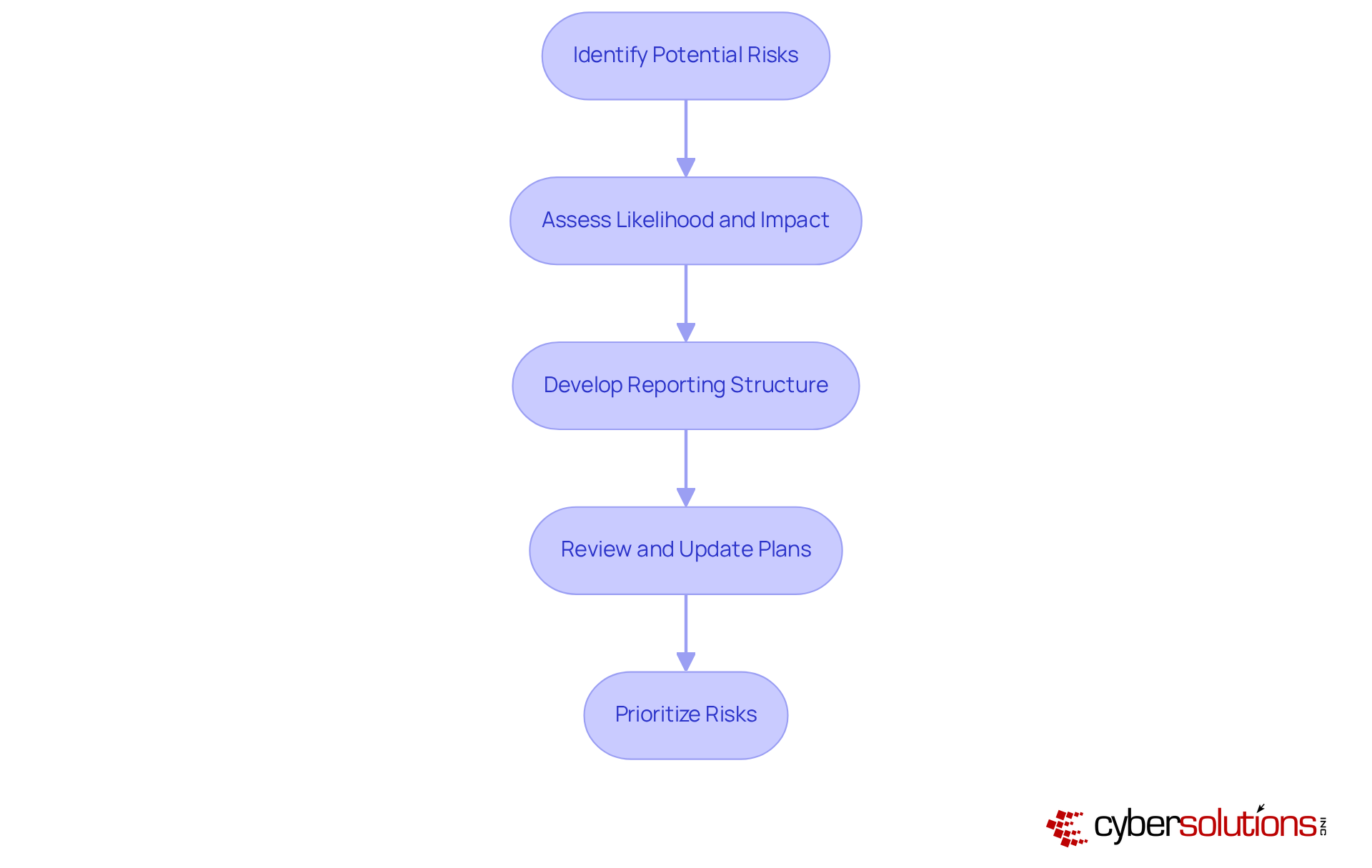
In today's digital landscape, recording adherence to industry regulations is not just important - it's essential for entities operating in regulated environments. This cybersecurity documentation must contain clear evidence of compliance with standards such as HIPAA, PCI-DSS, and GDPR. Effective incident response strategies, as demonstrated in various case studies, show that organizations can significantly enhance their adherence efforts. For instance, the swift deployment of incident response teams not only aids in immediate threat containment but also fortifies adherence by ensuring that protective measures are promptly updated and documented.
Organizations that maintain comprehensive cybersecurity documentation have reported a remarkable reduction in audit preparation time, with some achieving up to a 60% decrease. This efficiency simplifies the audit process and reinforces a company’s commitment to security and compliance, safeguarding its reputation and financial interests. However, current adherence rates reveal a concerning trend: while many entities strive for conformity, gaps remain. For example, only 58% of organizations conduct regular audits to ensure alignment with these critical regulations.
Compliance specialists emphasize that thorough records are not merely a regulatory requirement; they are a strategic asset that enhances operational efficiency and mitigates risks associated with non-compliance. By prioritizing cybersecurity documentation alongside effective incident response, organizations can more adeptly navigate the complexities of regulatory landscapes and strengthen their cybersecurity posture. Are you ready to take the necessary steps to ensure your organization is not just compliant, but also resilient?
In today’s digital landscape, continuous training and awareness programs are essential for equipping employees with the knowledge needed to combat evolving cybersecurity threats. Organizations must tailor these initiatives to their specific needs and ensure they are regularly updated to address new vulnerabilities. A robust protective culture, nurtured through ongoing education, can lead to a significant reduction in human errors - one of the primary contributors to data breaches.
Consider this: entities that implement role-based training have reported up to a 90% improvement in phishing threat detection within just six months. Furthermore, cybersecurity awareness training has been shown to reduce security-related risks by 70%, as highlighted in the case study "Impact of Cybersecurity Awareness Training in 2024." With 95% of data breaches linked to human error, it’s clear that investing in comprehensive training is not just beneficial; it’s essential.
By embedding security awareness into daily workflows, companies empower their employees and create a proactive defense against cyber threats. As Andrew Evers points out, connecting training to real-world scenarios is crucial for enhancing its effectiveness. Employees who are well-informed about potential threats serve as a vital line of defense against cybercrime.
Implementing version control for cybersecurity documentation is not just a best practice; it’s a critical necessity that ensures every modification to cybersecurity documentation policies and procedures is meticulously tracked and managed. This approach safeguards the integrity of documents and allows organizations to revert to previous versions when necessary, significantly reducing the risk of errors. For instance, companies like ABB have successfully adopted version control systems, streamlining their document management processes and enhancing efficiency across various regions. ABB's utilization of ActiveDocs for document automation and template management showcases the tangible benefits of such systems.
Version control plays a pivotal role in fostering collaboration among teams by providing a clear audit trail of changes. In high-stakes environments where accuracy is non-negotiable, this clarity is essential. As highlighted by Docsvault, "This level of control not only prevents errors but also makes collaboration smoother by eliminating uncertainties about who is editing a document and when." Documentation specialists assert that a robust version control system cultivates a culture of accountability and transparency, empowering teams to work cohesively without the fear of overwriting each other's contributions.
To effectively manage changes in records, organizations should establish clear procedures for checking files in and out, ensuring that only the most relevant versions are accessible. Regular reviews of cybersecurity documentation are crucial to ensure alignment with evolving regulatory requirements. Furthermore, it’s vital to prioritize training for personnel on the importance of version control; a well-informed team is better equipped to uphold high standards in record-keeping practices. With 64% of compliance leaders indicating that this is a priority for 2025, implementing these strategies can significantly enhance cybersecurity record-keeping processes, ultimately leading to improved compliance and reduced operational risks.
In today's healthcare landscape, regular audits of cybersecurity documentation are essential, not just important. These audits ensure that policies and procedures remain current and effective in the face of ever-evolving threats. By focusing on the relevance and accuracy of records, organizations can identify gaps and areas that need improvement.
Consider this: entities that conduct structured documentation reviews often uncover shortcomings that, when addressed, significantly enhance their compliance efforts and overall security posture. This proactive approach is crucial, especially when integrating practices like application allowlisting. Such measures can prevent unauthorized software from executing, thereby reducing vulnerabilities and ensuring compliance with critical standards such as HIPAA, PCI-DSS, and GDPR.
Application allowlisting offers features like centralized management and continuous monitoring of application activity, which further strengthens protection by allowing only authorized applications to run. Comprehensive cybersecurity documentation not only helps organizations meet regulatory standards but also acts as a proactive strategy against potential vulnerabilities.
By committing to regular evaluations and implementing robust protective measures like application allowlisting, companies can fortify their cybersecurity frameworks against the ever-changing threat landscape. Are you ready to take action and ensure your organization is protected?
Integrating stakeholder feedback into cybersecurity documentation practices is essential for fostering continuous improvement. By proactively seeking input from staff, management, and external collaborators, organizations can pinpoint opportunities for enhancement and ensure that protective measures effectively address the diverse needs of all stakeholders. This collaborative approach cultivates a culture of safety and accountability, significantly boosting the effectiveness of cybersecurity practices.
Consider this: companies that engage effectively with stakeholders are 30% more likely to succeed with new products. This statistic underscores the tangible benefits of collaboration. Furthermore, a manufacturing firm that implemented a peer-led 'Champions' program, which involved employees in protective processes, saw a remarkable 60% decrease in accidental data leaks within just six months. This clearly illustrates the positive impact of engaging employees in protective initiatives.
Industry leaders consistently emphasize that strong stakeholder management can lead to improved financial outcomes. One expert noted that projects with engaged stakeholders succeed 83% of the time. By incorporating stakeholder input into cybersecurity documentation, companies can enhance their resilience against emerging threats and align their security strategies with broader business objectives.

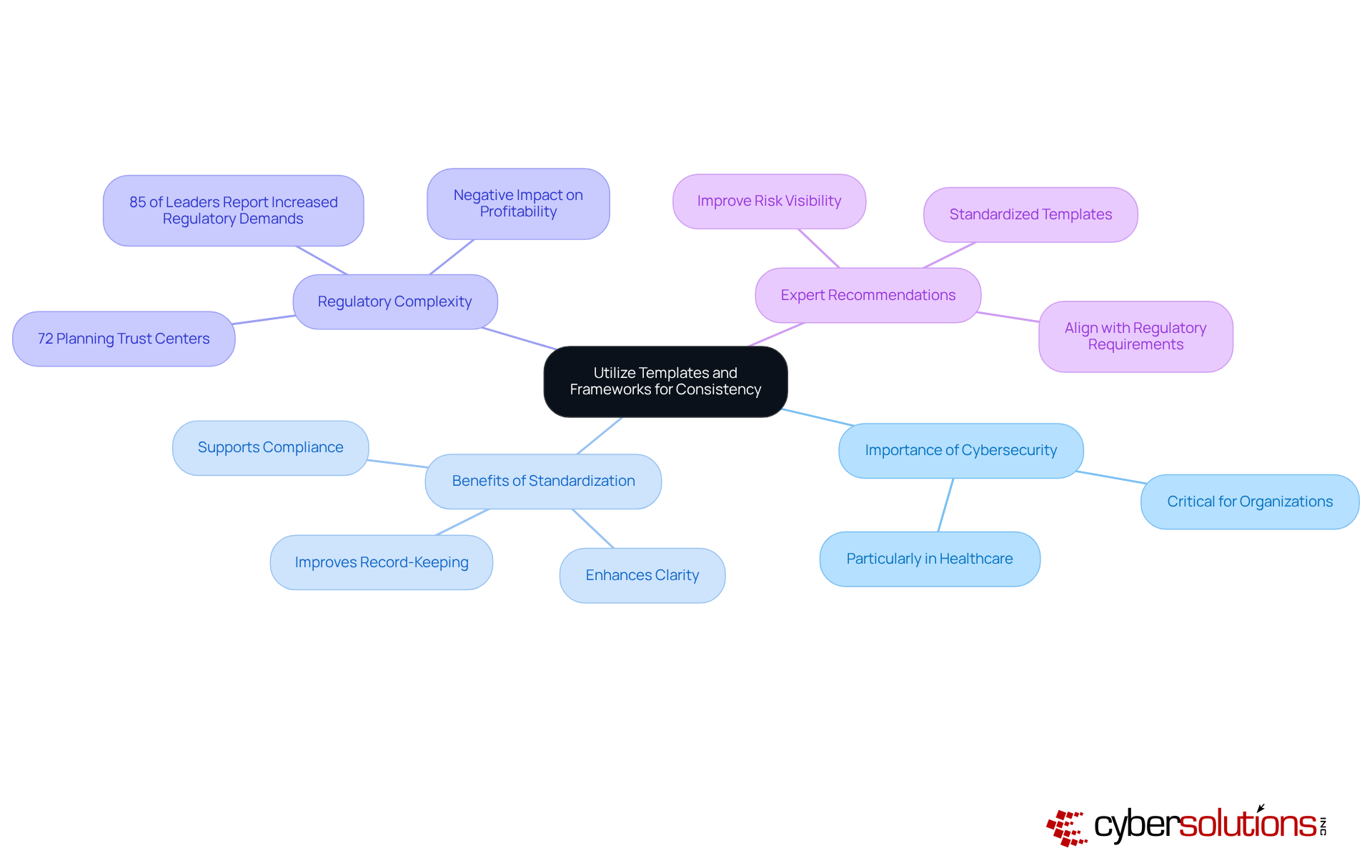
In today’s digital landscape, the importance of cybersecurity cannot be overstated. For organizations, particularly in healthcare, adopting templates and frameworks for cybersecurity documentation is crucial for ensuring consistency and clarity. Standardized formats not only make materials easily understood but also accessible to employees at all levels. This approach simplifies record-keeping and significantly enhances adherence efforts by providing a clear framework for policies and procedures.
Consider this: entities that implement a shared control library can simultaneously prepare for various regulatory frameworks. This capability is increasingly vital, as 85% of leaders report that regulatory demands have become more intricate in recent years. Furthermore, 72% of organizations are either establishing or planning to create Trust Centers for regulatory management, underscoring the growing recognition of the need for standardized record-keeping practices.
Experts advocate for standardized templates, emphasizing their role in improving risk visibility and expediting issue detection - both critical in today’s rapidly evolving cybersecurity landscape. As Anna Fitzgerald points out, the increasing complexity of regulatory demands has negatively impacted profitability for many enterprises. By leveraging established frameworks, organizations can enhance their documentation practices and align their cybersecurity strategies with regulatory requirements. This alignment not only fosters a culture of compliance and security but also positions organizations to navigate the complexities of the regulatory environment effectively.
Effective cybersecurity documentation stands as a cornerstone for organizations, especially in the healthcare sector, where the protection of sensitive data is non-negotiable. In a landscape fraught with complex regulatory demands, tailored practices empower businesses to navigate these challenges while boosting operational efficiency. The strategies outlined here not only ensure compliance with critical standards but also cultivate a culture of security awareness and accountability among employees.
Key practices include:
These are essential for building a robust cybersecurity framework. Furthermore, organizations must prioritize:
Engaging stakeholders and adopting standardized templates significantly enhance the effectiveness of cybersecurity documentation, ensuring it remains relevant and impactful against evolving threats.
In conclusion, organizations must grasp the importance of effective cybersecurity documentation as a proactive defense against potential cyber threats. By committing to these essential practices, businesses can not only safeguard their sensitive information but also establish a resilient cybersecurity posture that aligns with regulatory requirements. Are you ready to enhance your organization's cybersecurity documentation and protect your assets from future vulnerabilities?
What does Cyber Solutions Inc. specialize in?
Cyber Solutions Inc. specializes in creating tailored cybersecurity procedures for various industries, focusing on helping organizations navigate complex regulatory requirements, particularly in the healthcare sector.
How does Cyber Solutions Inc. assist with compliance?
Cyber Solutions Inc. offers Compliance as a Service (CaaS) solutions that simplify adherence to standards such as HIPAA, PCI-DSS, CMMC, SOX, and GDPR, which are crucial for maintaining patient trust and operational integrity.
What unique challenges do healthcare organizations face regarding cybersecurity?
Healthcare organizations face challenges related to the protection of sensitive patient data, where breaches can have devastating financial and reputational implications.
What services does Cyber Solutions Inc. provide to enhance operational efficiency?
Cyber Solutions Inc. provides comprehensive risk assessments, policy development, and ongoing compliance monitoring to ensure documentation meets compliance requirements and enhances operational efficiency.
What is the purpose of Incident Response services offered by Cyber Solutions Inc.?
The Incident Response services are designed to minimize the impact of cyberattacks by rapidly identifying, containing, and mitigating threats, restoring systems, and ensuring business continuity.
Why is clear information security policy documentation essential?
Clear information security policy documentation is essential for outlining a company's safety objectives and expectations, particularly for safeguarding federal data and adhering to cybersecurity standards.
What percentage of cyber incidents result from human errors?
Approximately 88% of cyber incidents stem from human errors.
How can organizations maintain eligibility for government contracts?
Organizations can maintain eligibility for government contracts by implementing robust data protection measures and ensuring all employees understand and comply with cybersecurity policies.
What is the importance of maintaining comprehensive incident response plans?
Comprehensive incident response plans are crucial for effectively navigating cybersecurity incidents, particularly under HIPAA regulations, and must define roles, responsibilities, and procedures for incident management.
What is emphasized by cybersecurity experts regarding documentation?
Cybersecurity experts emphasize that effective cybersecurity documentation is foundational and that security should be viewed as a culture, not merely a control.
How can organizations improve their incident response planning?
Organizations can improve incident response planning by regularly updating and rigorously testing their documentation, engaging all departments, and conducting ongoing training and simulations.
What is a concerning statistic about organizations evaluating their incident response plans?
Alarmingly, only 30% of organizations evaluate their incident response plans, highlighting the critical need for regular assessments to meet regulatory obligations.