
In a time when cyber threats are more prevalent than ever, the stakes for C-suite leaders have reached unprecedented heights. Defensive artificial intelligence stands out as a powerful ally, providing a range of benefits that not only bolster cybersecurity but also streamline operations and enhance compliance. As organizations face increasingly sophisticated attacks, one pressing question arises: how can executives fully leverage defensive AI to safeguard their assets while simultaneously driving business growth?
This article explores ten compelling advantages of integrating defensive AI into strategic decision-making, illustrating how it can reshape the landscape of organizational resilience. By understanding these benefits, leaders can take decisive action to protect their organizations and foster a culture of innovation and security.
In today's digital landscape, the importance of cybersecurity cannot be overstated. Defensive artificial intelligence utilizes advanced machine learning algorithms to analyze vast datasets in real-time, adeptly identifying patterns and anomalies that signal potential cyber risks. For organizations, adopting AI-driven threat detection systems significantly enhances their ability to uncover sophisticated attacks, thereby reducing the risk of data breaches and operational disruptions.
This proactive approach not only safeguards sensitive information but also aligns with financial objectives by minimizing potential losses linked to cyber incidents. Consider this: companies leveraging security AI have reported average savings of $1.9 million compared to those that do not. This statistic underscores the financial advantages of integrating such technologies into their operations.
As cybersecurity expert Jenny Stromer-Galley points out, defensive artificial intelligence has transitioned from a supplementary tool to a fundamental element of protection strategies, highlighting its essential role in modern cybersecurity frameworks. Moreover, cultivating a 'risk-aware culture' is crucial for organizations implementing AI technologies, ensuring they effectively navigate the complexities and risks that accompany these advancements.
The integration of machine learning into threat detection processes streamlines operations and strengthens defenses against increasingly complex cyber threats. With Cyber Solutions' 24/7 monitoring and alert services, including comprehensive firewall and network protection options, businesses can swiftly identify anomalies and potential vulnerabilities in real-time. This vigilance is vital for safeguarding against ransomware, phishing, and other malware attacks.
Ultimately, this comprehensive approach guarantees that only authorized users gain access, adapting to new challenges as operations expand. By prioritizing cybersecurity, organizations not only protect their assets but also enhance their overall resilience in an ever-evolving threat landscape.
In today's digital landscape, the importance of cybersecurity cannot be overstated. Defensive artificial intelligence is essential for automating routine protective operations, such as monitoring and incident response, thereby significantly reducing the risk of human error. By adopting AI-driven procedures, organizations can standardize their responses to incidents, ensuring both consistency and precision. This automation not only enhances safety but also allows human resources to focus on strategic initiatives, ultimately driving operational efficiency and cost savings.
Consider this: organizations employing AI have reported a staggering 70% decrease in false positives. This reduction alleviates analyst fatigue and minimizes the risk of overlooking critical threats. Furthermore, AI's ability to learn continuously from past events strengthens detection models, making operations more resilient against evolving cyber threats. With Cyber Solutions' 24/7 network monitoring and alert services, businesses can identify anomalies and potential vulnerabilities in real-time, effectively safeguarding against ransomware, phishing, and other malware attacks.
C-suite executives must view investing in defensive artificial intelligence as a strategic decision that aligns with both security and business objectives. This investment becomes even more impactful when integrated with proactive network hardening tactics and comprehensive employee training on cybersecurity practices. To fully leverage these advantages, companies are encouraged to regularly assess and update their protection protocols while committing to ongoing employee training.
In today's digital landscape, the importance of cybersecurity cannot be overstated. Real-time monitoring powered by defensive artificial intelligence allows organizations to continuously assess their security posture and swiftly identify anomalies. This proactive approach is crucial, especially as cyber threats become increasingly sophisticated. By utilizing predictive analytics, which examines historical data to reveal trends and potential vulnerabilities, companies can effectively combat cyber risks before they escalate.
Organizations that embrace AI-driven predictive security measures have reported significant improvements in their detection capabilities. Systems are now able to identify deviations from typical behavior patterns, such as unusual login attempts or access to sensitive files outside regular hours. This capability not only mitigates the risk of costly breaches but also ensures compliance with regulatory standards. As Renz Soliman emphasizes, "AI enhances cybersecurity by leveraging machine learning models and behavioral analytics to detect threats faster and more accurately than traditional methods."
The implications for healthcare organizations are profound. By adopting these advanced security measures, businesses not only protect sensitive data but also foster greater customer trust. In an increasingly regulated digital environment, this trust is essential for growth and sustainability. As organizations navigate these challenges, the integration of AI in cybersecurity strategies will be a game changer, enabling them to thrive amidst evolving threats.
Defensive artificial intelligence is transforming compliance monitoring and reporting, simplifying the process for businesses to adhere to complex regulatory frameworks like HIPAA, PCI-DSS, and GDPR. In today’s landscape, where compliance is paramount, automating the tracking of compliance metrics and generating detailed reports can significantly reduce the administrative burdens that often accompany compliance management. This automation not only guarantees adherence to regulations but also enhances an organization’s reputation and trustworthiness in the marketplace.
Consider this: organizations that have implemented AI-driven compliance systems have experienced an impressive 79% reduction in audit cycle times, dropping from 42 days to just 9 days. Moreover, AI's capability to filter out up to 95% of irrelevant alerts empowers compliance teams to concentrate on critical issues, thereby boosting overall efficiency. As compliance officers increasingly acknowledge the role of defensive artificial intelligence in streamlining processes, 65% affirm its significance in their compliance programs, with many anticipating a transformative impact in the near future.
By embracing AI alongside robust cybersecurity solutions, such as endpoint protection and application allowlisting from Cyber Solutions, organizations can shift compliance from a reactive obligation to a proactive strategic asset. This shift not only fosters greater trust and transparency with stakeholders but also positions the organization for success in an ever-evolving regulatory environment. To fully leverage these advantages, integrating Cyber Solutions' services into your compliance strategy is essential.
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. Defensive artificial intelligence significantly enhances incident response capabilities by automating both detection and response processes. Upon recognizing a danger, AI systems can swiftly initiate predefined response protocols, drastically reducing the time required to mitigate potential risks.
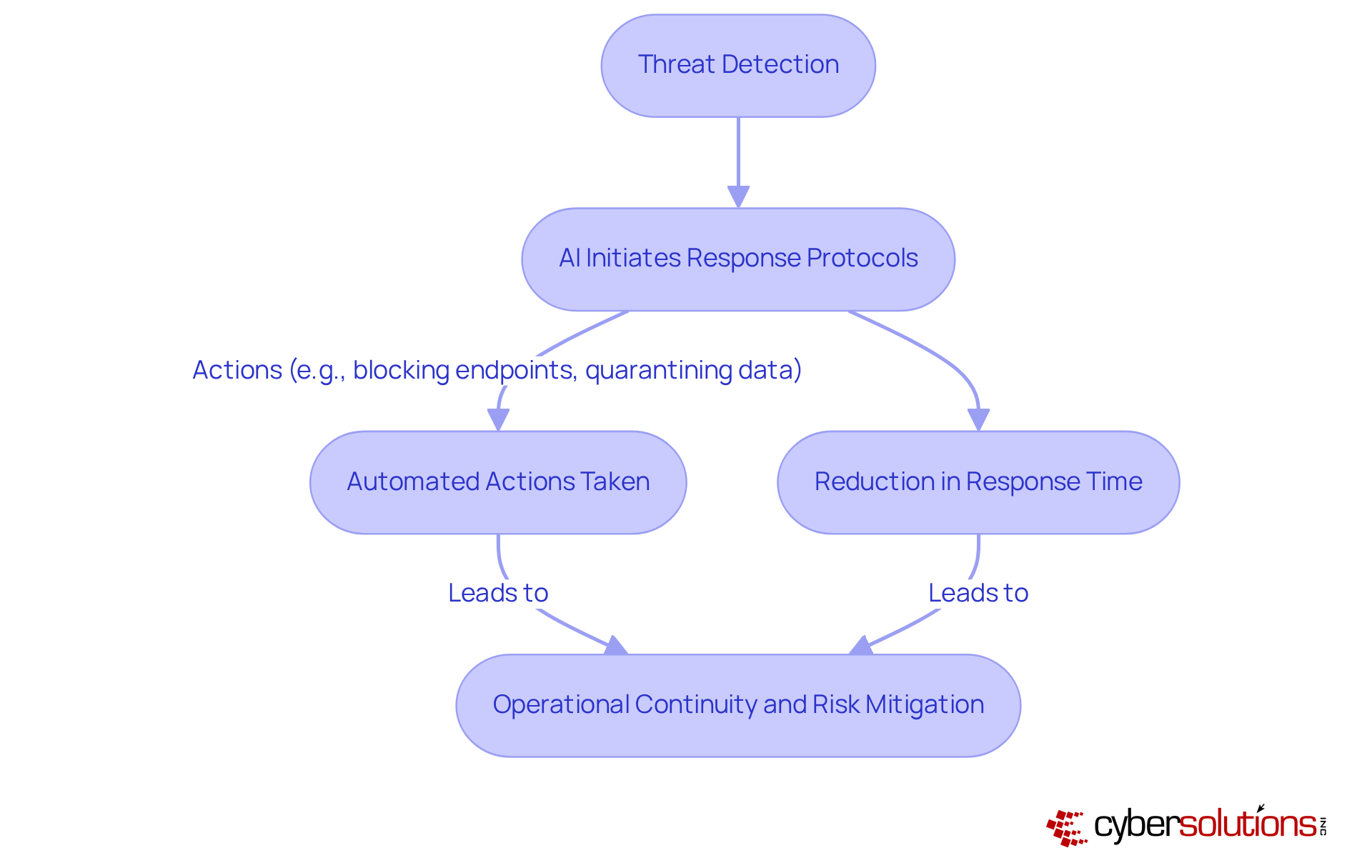
For instance, a European bank that implemented AI copilots in its monitoring services reported a remarkable 40% reduction in downtime within six months, showcasing the effectiveness of automated responses. Similarly, during a ransomware attack, a Singaporean healthcare professional noted that SOC copilots achieved a 70% reduction in response times by automatically blocking suspect endpoints and quarantining data.
This swift reaction not only reduces potential harm but also guarantees operational continuity, protecting the entity's bottom line. Cybersecurity experts stress that the capability to react swiftly to risks is crucial; 97% of UK cybersecurity specialists now consider automation, increasingly driven by AI, as vital for business functions. As organizations encounter complex cyber challenges, the incorporation of defensive artificial intelligence into incident response plans is becoming a strategic necessity, enabling businesses to maintain resilience and efficiency in a constantly changing digital environment.
C-Suite leaders should consider starting with regular audits of AI models to address potential biases and ensure compliance, thereby enhancing the effectiveness of their incident response strategies. Cyber Solutions offers round-the-clock oversight of your network to identify irregularities and possible weaknesses, guaranteeing that questionable actions are recognized and halted before they develop into dangers. This includes advanced alert systems and customized access controls to safeguard against particular risks such as ransomware and phishing.
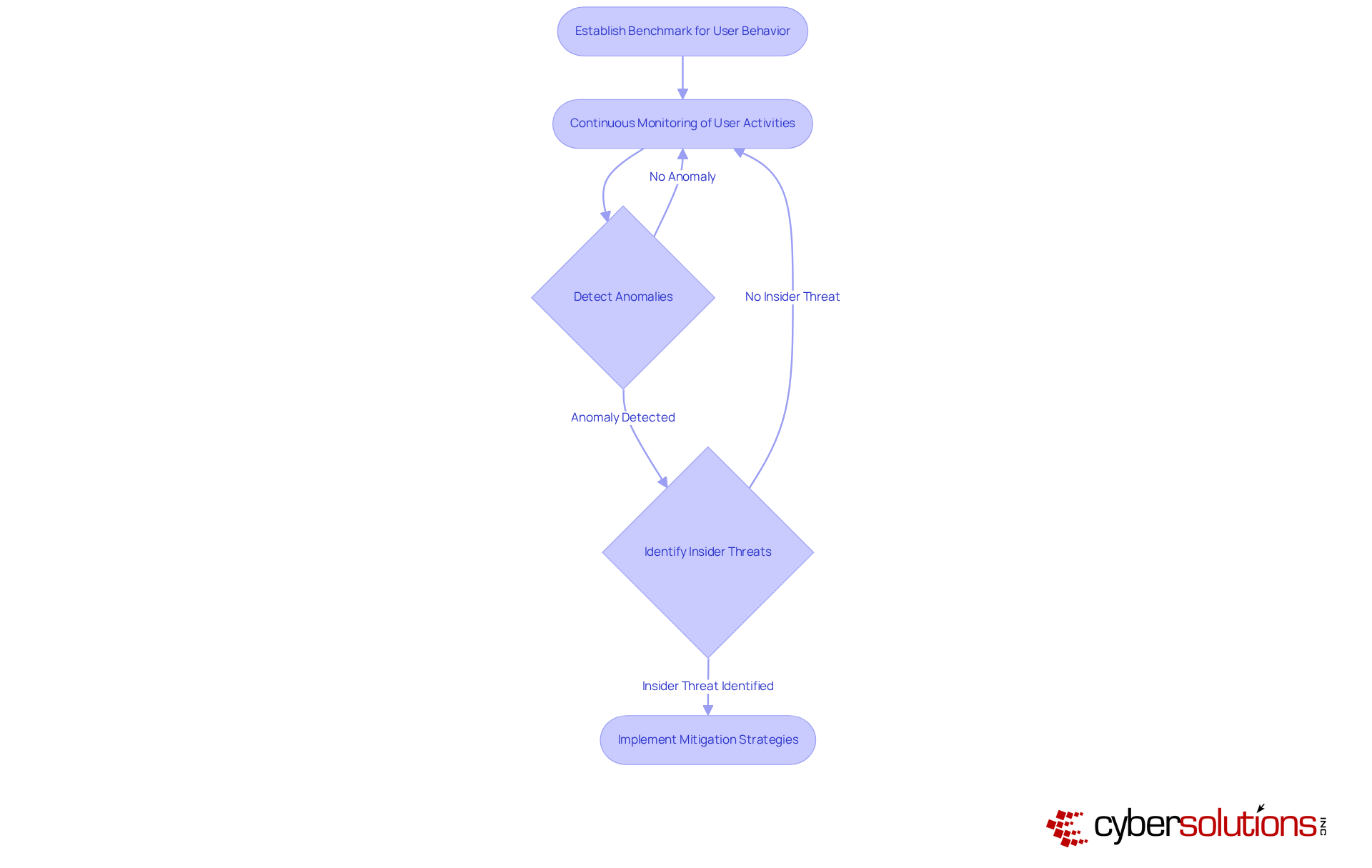
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in healthcare. Defensive artificial intelligence utilizes behavioral analytics to establish a benchmark for typical user behavior, enabling organizations to pinpoint deviations that may indicate potential risks. By continuously monitoring user activities, businesses can swiftly detect insider threats or compromised accounts, which is vital for protecting sensitive data from unauthorized access.
This proactive approach not only enhances security but also employs defensive artificial intelligence to mitigate the risk of significant financial and reputational damage associated with cybersecurity breaches. Organizations that implement behavioral analytics have reported substantial improvements in their anomaly detection capabilities. Advanced systems can identify patterns that traditional security measures often miss. Notably, 18% of breaches involve internal participants, underscoring the necessity of monitoring user behavior to effectively address insider risks.
Cyber Solutions stands ready to assist with comprehensive, round-the-clock network surveillance and alert services, ensuring that suspicious activities are identified and neutralized before they escalate into serious threats. Furthermore, training employees to recognize suspicious behavior significantly boosts the effectiveness of behavioral analytics. By establishing a robust monitoring framework and adopting proactive network hardening strategies, companies can create a secure operational environment, ultimately fostering resilience against evolving cyber threats.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations handling sensitive data. Defensive artificial intelligence significantly enhances data protection by utilizing sophisticated encryption and access control mechanisms. By continuously analyzing data access and usage patterns, organizations can swiftly identify unauthorized attempts to access sensitive information. This proactive strategy not only strengthens data protection but also ensures compliance with data safeguarding regulations, thereby maintaining the organization's reputation.
As industry specialists note, the incorporation of AI in protective protocols enables the identification of threats up to 60% quicker, improving overall responsiveness to potential breaches. Moreover, adopting strong encryption protocols is essential for safeguarding confidential information from unauthorized access. AI-driven solutions enhance these processes, establishing a more resilient stance through defensive artificial intelligence.
Consider this: in a landscape where 83% of global IT leaders have adopted some form of AI, the transformative potential of these technologies in protecting sensitive information is clear. Organizations must act decisively to integrate these advanced solutions into their cybersecurity strategies, ensuring they remain ahead of evolving threats.
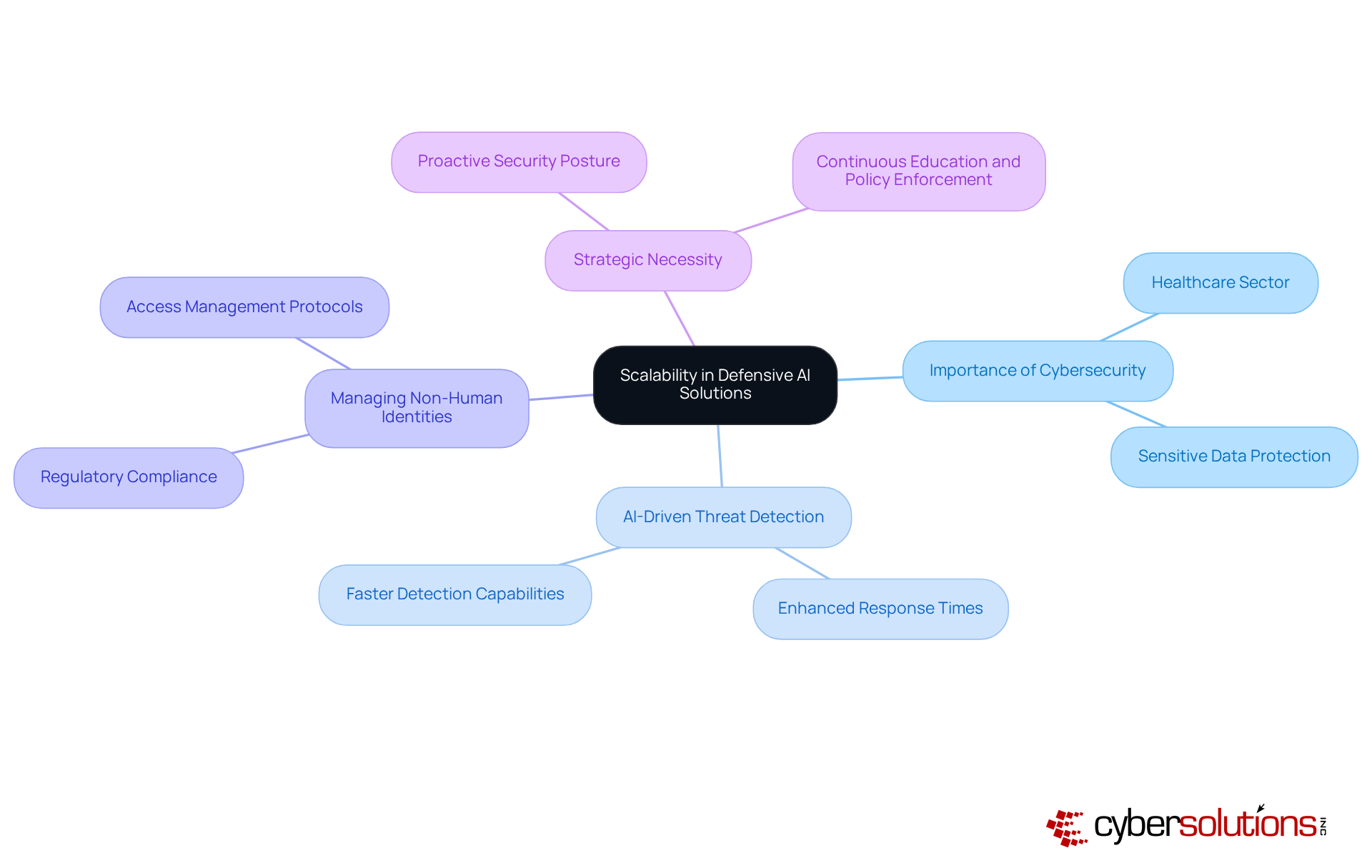
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially in sectors like healthcare where sensitive data is at stake. Defensive artificial intelligence solutions are specifically designed to scale alongside organizational growth, allowing businesses to adapt their cybersecurity measures as they expand. This intrinsic scalability is crucial; it ensures that protective frameworks remain strong and efficient in the face of new challenges and evolving organizational needs. Organizations that have successfully implemented AI-driven protective measures report enhanced threat detection capabilities and faster response times - both essential as their operations grow.
As organizations expand, their digital protection requirements become increasingly complex, necessitating a proactive approach to safeguarding assets. Industry leaders emphasize that investing in scalable AI solutions not only secures digital safety strategies but also fortifies defenses against ever-more sophisticated threats. Angela Shreiber, a recognized authority in cybersecurity, underscores the importance of aligning protective measures with organizational growth, stating, "Creating a culture aware of risks necessitates a continuous dedication to education, policy enforcement, and proactive collaboration across teams."
Moreover, organizations that effectively manage Non-Human Identities (NHIs) and secrets can significantly reduce risks while enhancing compliance. This is particularly critical in industries like finance and healthcare, where adherence to regulations is paramount. By implementing stringent access and secrets management protocols, businesses can bolster customer trust and ensure their protective frameworks evolve alongside their growth trajectories.
In summary, integrating defensive artificial intelligence solutions is not merely a reactive measure; it is a strategic necessity that empowers organizations to navigate the complexities of modern cybersecurity while maintaining operational efficiency and resilience.
Integrating defensive artificial intelligence with existing IT systems is not just beneficial; it’s essential for enhancing overall protection in today’s digital landscape. This integration establishes a unified defense strategy that significantly improves data sharing and communication across systems, providing a comprehensive view of an organization’s protective stance. By ensuring that defensive artificial intelligence solutions align seamlessly with current infrastructure, organizations can bolster their security measures while minimizing operational disruptions.
Ongoing observation plays a crucial role in this process. It guarantees that dubious actions are identified and halted before they escalate into serious threats. Cyber Solutions’ proactive digital security measures, including advanced risk intelligence and real-time monitoring, effectively safeguard businesses from ransomware, phishing, and other malware attacks. IT experts emphasize that a unified strategy not only simplifies risk identification but also enhances incident response capabilities, ultimately leading to a more robust cybersecurity framework.
Organizations that have adopted defensive artificial intelligence for security tools report quicker threat detection and reduced alert fatigue. This allows human analysts to focus on strategic defenses rather than being overwhelmed by alerts. Furthermore, it is vital for entities to regularly audit AI models for bias and fairness, ensuring compliance and upholding ethical standards.
The impact of unified defense strategies is evident in improved cybersecurity effectiveness. Organizations can proactively address emerging threats and adapt to the ever-evolving landscape of cyber risks. As industry experts note, a unified defense strategy not only enhances operational efficiency but also builds trust in AI systems, ensuring that sensitive personal information is handled responsibly.
Cybersecurity is no longer just an option; it’s a necessity for organizations aiming to thrive in today’s digital landscape. Defensive artificial intelligence significantly enhances protection while boosting operational efficiency by automating routine tasks and streamlining processes. This technology not only reduces the time and resources spent on manual security operations but also allows companies to focus on strategic initiatives that drive business growth.
A recent survey revealed that 77% of organizations expect their security budgets to increase, highlighting a growing recognition of the need for advanced solutions to tackle emerging risks. C-suite leaders are increasingly vocal about the role of AI in optimizing business performance. As Marc Benioff aptly noted, "The past eight months have been the most exciting of my career as AI improved efficiency and freed resources for sales efforts."
Moreover, Cyber Solutions offers a flat-rate pricing model that simplifies budgeting by covering all essential services, from email licenses to advanced cybersecurity measures. This predictable monthly cost structure eliminates unexpected IT expenses, providing peace of mind for executives. With 24/7 threat monitoring, Cyber Solutions ensures that suspicious activities are detected and mitigated before they escalate into serious threats, effectively safeguarding businesses from ransomware, phishing, and other malware attacks.
This dual advantage of enhanced security and improved efficiency positions defensive artificial intelligence as a critical investment for executives aiming to optimize their operations and drive sustainable growth. To capitalize on these benefits, leaders must assess their current cybersecurity strategies and identify areas where AI can be integrated. Are you ready to take the next step in securing your organization?
Defensive artificial intelligence stands as a crucial asset for C-suite leaders grappling with the intricate challenges of modern cybersecurity. In an era where cyber threats are becoming increasingly sophisticated, harnessing AI-driven technologies is not just beneficial; it’s essential. Organizations can significantly enhance their threat detection capabilities, automate security operations, and streamline compliance processes, ultimately fortifying their defenses against a relentless tide of cyber risks.
The advantages of defensive AI are compelling. Improved incident response times, reduced human error, and enhanced data protection are just the beginning. With AI's remarkable ability to analyze patterns and anomalies in real-time, organizations can swiftly identify and mitigate potential risks, ensuring operational continuity and safeguarding sensitive information. Furthermore, the integration of predictive analytics and behavioral insights empowers businesses to proactively address vulnerabilities before they escalate into significant issues.
Given these insights, it is imperative for executives to prioritize the integration of defensive artificial intelligence within their cybersecurity strategies. By doing so, organizations not only bolster their security posture but also drive operational efficiency. This fosters a culture of resilience, preparing them for future challenges. Embracing these advanced solutions is not merely a tactical move; it is a strategic imperative that positions organizations for sustainable growth and success in an ever-evolving digital landscape.
What is defensive artificial intelligence in cybersecurity?
Defensive artificial intelligence (AI) utilizes advanced machine learning algorithms to analyze large datasets in real-time, identifying patterns and anomalies that indicate potential cyber risks.
How does AI enhance threat detection for organizations?
AI-driven threat detection systems significantly improve organizations' ability to uncover sophisticated attacks, reducing the risk of data breaches and operational disruptions.
What financial benefits can organizations expect from integrating AI in cybersecurity?
Companies leveraging security AI have reported average savings of $1.9 million compared to those that do not use such technologies, highlighting the financial advantages of integration.
Why is cultivating a 'risk-aware culture' important for organizations using AI?
A 'risk-aware culture' ensures that organizations can effectively navigate the complexities and risks associated with implementing AI technologies in their cybersecurity strategies.
What role does automated security operations play in minimizing human error?
Automated security operations, powered by defensive AI, help standardize responses to incidents, significantly reducing the risk of human error and enhancing operational efficiency.
How has AI impacted the rate of false positives in cybersecurity?
Organizations employing AI have reported a 70% decrease in false positives, which alleviates analyst fatigue and reduces the risk of overlooking critical threats.
What is the significance of real-time monitoring in cyber defense?
Real-time monitoring allows organizations to continuously assess their security posture and swiftly identify anomalies, which is crucial for combating increasingly sophisticated cyber threats.
How does predictive analysis contribute to proactive cyber defense?
Predictive analysis examines historical data to reveal trends and potential vulnerabilities, enabling organizations to address cyber risks before they escalate.
What are the implications of AI-driven cybersecurity for healthcare organizations?
By adopting advanced security measures, healthcare organizations can protect sensitive data and foster greater customer trust, which is essential for growth and sustainability in a regulated digital environment.
What should organizations do to fully leverage the advantages of defensive AI?
Organizations are encouraged to regularly assess and update their protection protocols while committing to ongoing employee training on cybersecurity practices.