
In today’s digital landscape, where cyber threats are increasingly sophisticated, understanding the nuances of endpoint detection is crucial for businesses looking to safeguard their digital assets. This technology acts as a vital line of defense, continuously monitoring endpoint devices - like laptops and mobile phones - for potential security breaches. With the alarming statistic that the average time to detect a breach exceeds 200 days, organizations must ask themselves: how can they effectively protect against these relentless threats?
Exploring the essential role of endpoint detection not only reveals its significance in modern cybersecurity frameworks but also underscores the proactive measures businesses must adopt to stay ahead of evolving risks. By investing in robust endpoint detection solutions, organizations can enhance their security posture and respond swiftly to potential breaches, ultimately protecting their valuable data and maintaining trust with their stakeholders.
In today's digital landscape, the importance of cybersecurity cannot be overstated. What is endpoint detection, and how does it play a crucial role in safeguarding endpoint devices like laptops, desktops, and mobile devices by continuously monitoring and assessing them for potential security threats? This technology is a cornerstone of modern cybersecurity frameworks, particularly in understanding what is endpoint detection within Endpoint Detection and Response (EDR) systems. EDR solutions not only excel at identifying risks but also offer robust investigation and remediation capabilities, enabling organizations to respond swiftly to incidents.
As we look ahead to 2025, the urgency of addressing cyber risks becomes increasingly apparent. Data reveals that organizations managing a breach within 30 days can save over $1 million. With the average time between a breach and its detection exceeding 200 days, the need for proactive monitoring is critical. How can organizations ensure they are prepared? By leveraging real-time data and advanced analytics, detection capabilities empower organizations to maintain a strong security posture against emerging cyber threats. This proactive approach is essential for effectively mitigating risks associated with ransomware and other malicious attacks.
In conclusion, as cyber threats evolve, so must our strategies for defense. Investing in EDR solutions not only enhances detection capabilities but also fortifies an organization’s overall security framework. The time to act is now-ensure your organization is equipped to face the challenges of tomorrow.
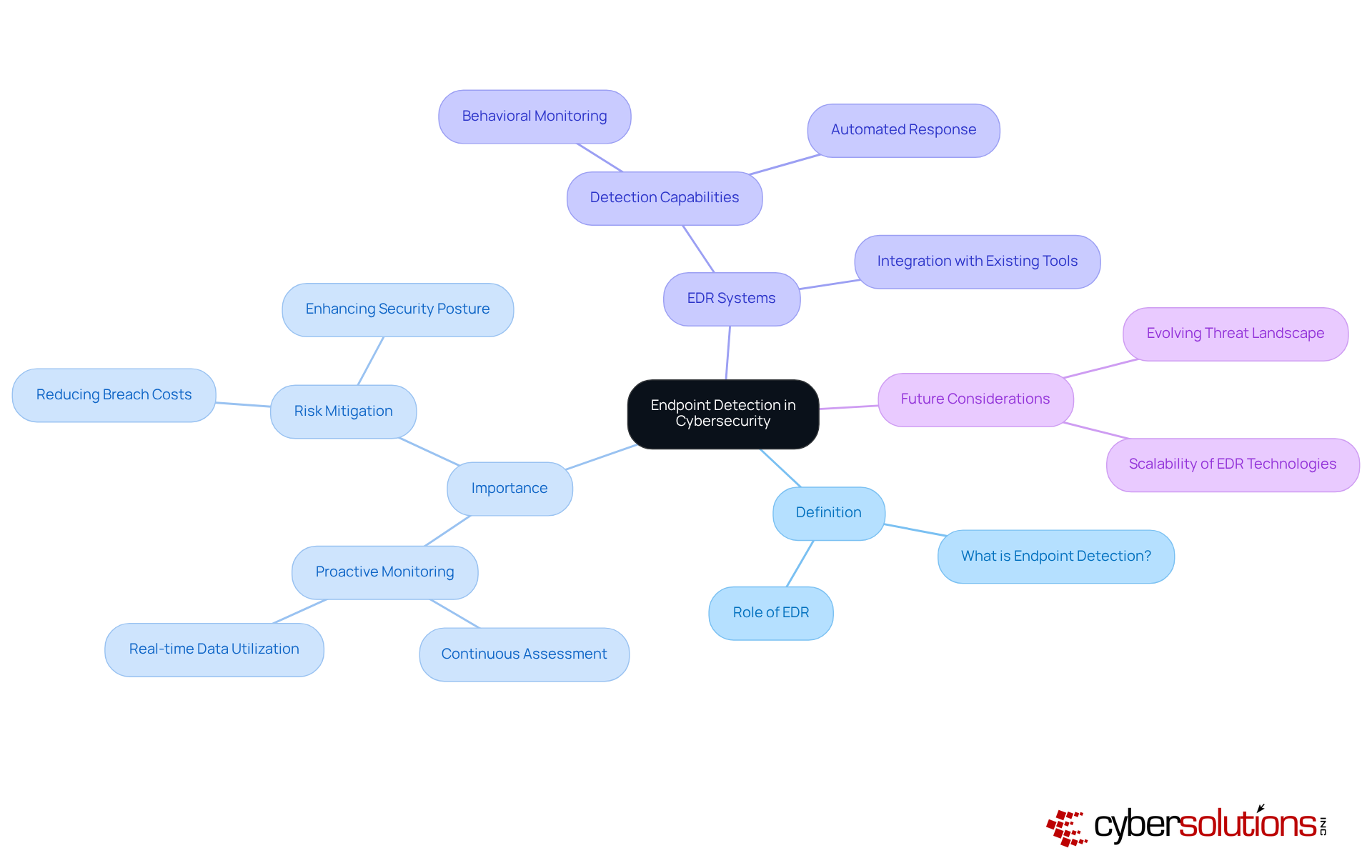
In today's digital landscape, the importance of detection cannot be overstated, especially as cyber threats grow increasingly sophisticated. With the rise of remote work and the multitude of devices connecting to corporate networks, access points have become prime targets for cybercriminals. Effective detection and response (EDR) solutions empower organizations to identify threats early, which relates to what is endpoint detection, significantly reducing the risk of data breaches and operational disruptions.
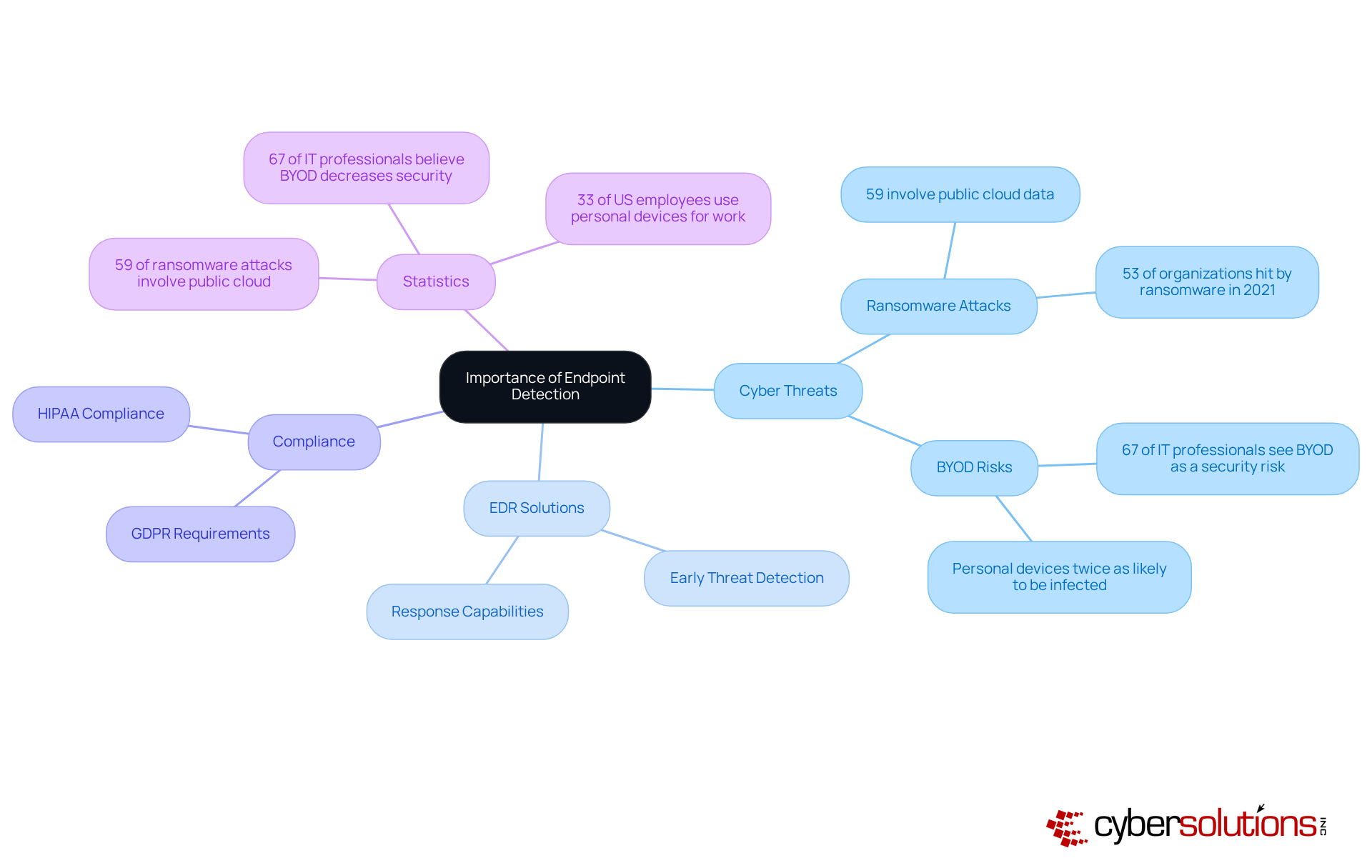
Consider this: a well-implemented EDR system can help answer what is endpoint detection by detecting unusual behaviors that may indicate a ransomware attack, allowing IT teams to intervene before substantial damage occurs. Moreover, compliance with regulations like GDPR and HIPAA necessitates robust measures to safeguard sensitive information, making threat detection a vital component of any comprehensive cybersecurity strategy.
Statistics reveal that:
As organizations navigate the complexities of hybrid work environments, prioritizing device detection is not just a best practice; it is essential for maintaining security and compliance. By investing in effective detection solutions, companies can safeguard their operations and protect sensitive data from evolving cyber threats.
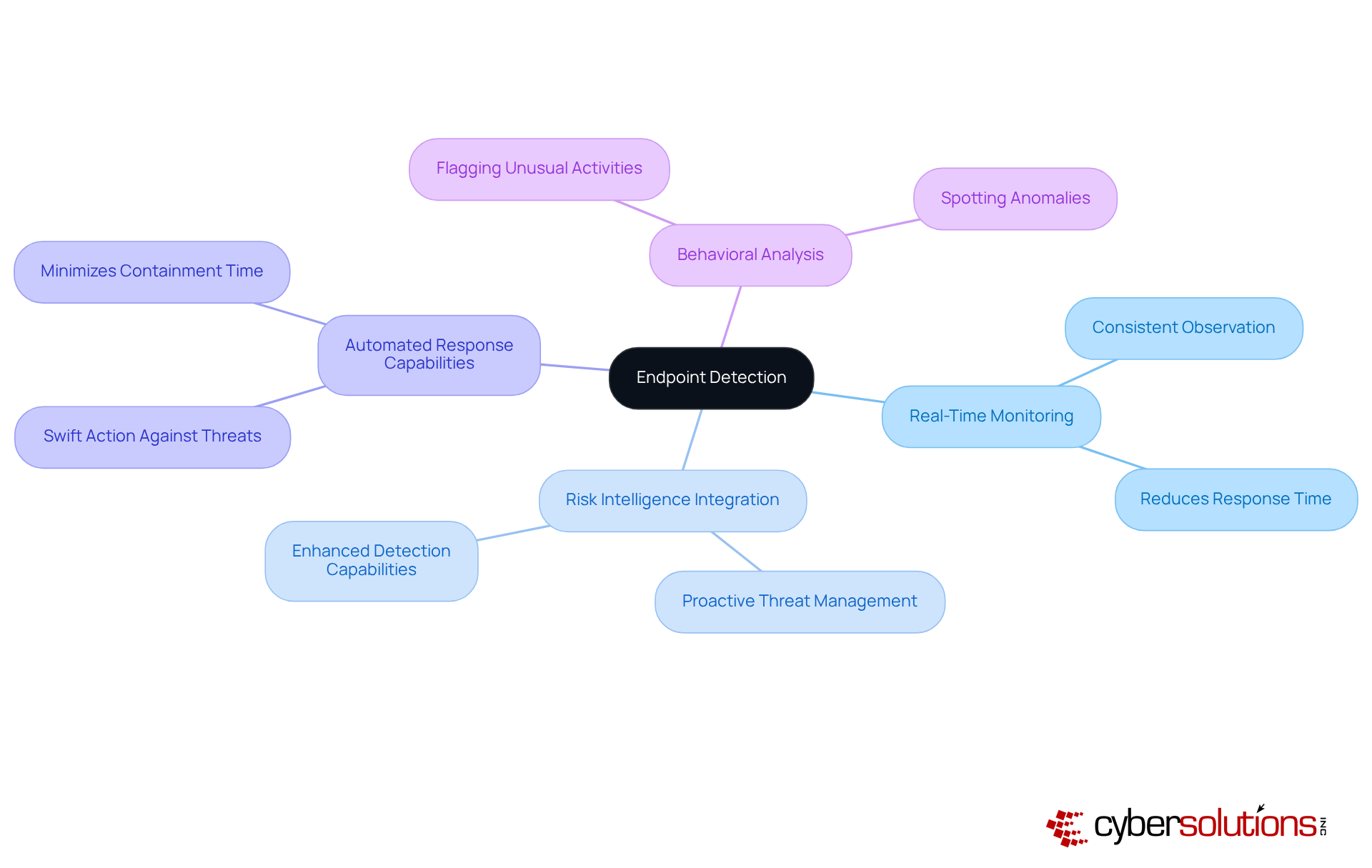
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in healthcare. Key features of device detection - such as real-time monitoring, risk intelligence integration, automated response capabilities, and behavioral analysis - are essential in combating the ever-evolving threats that organizations face.
Real-time monitoring helps teams to consistently observe what is endpoint detection activities. Data indicates that organizations employing these practices can significantly reduce the average time to identify and respond to risks. For instance, automated response capabilities allow for swift action against identified threats, effectively minimizing containment time and bolstering overall defense posture.
Moreover, behavioral analysis is crucial for spotting anomalies in user behavior that may signal a breach. Consider this: if an employee's account accesses sensitive files at unusual hours, the system can flag this activity for further investigation. Together, these features form a robust security framework, enabling organizations to understand what is endpoint detection to proactively safeguard against emerging cyber risks while ensuring compliance with stringent regulations.
In conclusion, as healthcare organizations navigate the complexities of cybersecurity, leveraging these advanced device detection capabilities is not just beneficial - it's imperative for maintaining security and trust.
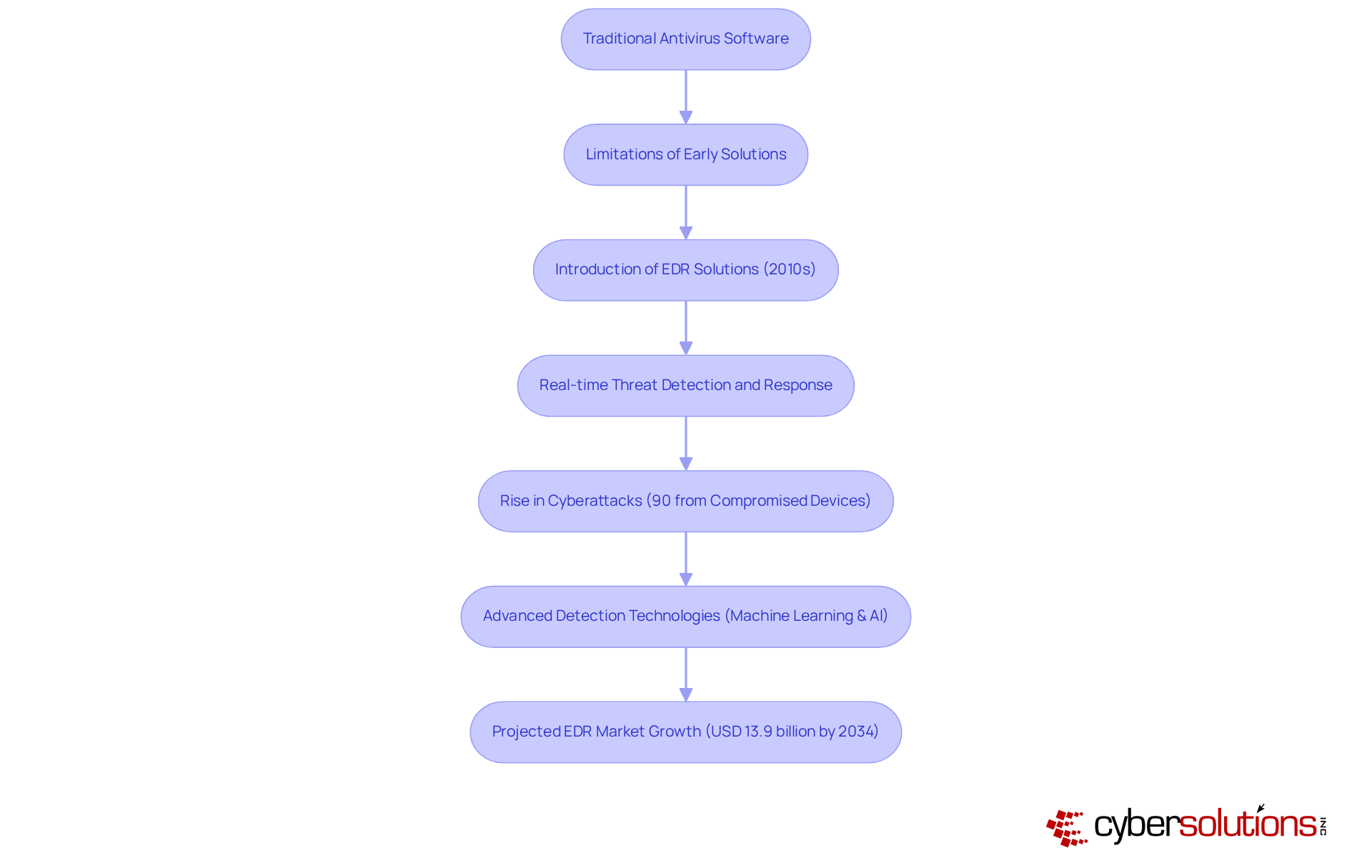
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially in the healthcare sector. As cyber threats evolve, organizations face unique challenges that demand immediate attention. The development of what is endpoint detection technologies began with traditional antivirus software, which primarily focused on identifying known malware threats. However, as cyber risks advanced, the limitations of these early solutions became glaringly apparent.
The introduction of Endpoint Detection and Response (EDR) solutions in the early 2010s highlighted what is endpoint detection as a significant turning point in cybersecurity. These solutions empower organizations not only to detect threats but also to respond to them in real-time. This shift was driven by the alarming rise in cyberattacks, with a staggering 90% of these incidents originating from compromised access devices. Today, detection technologies leverage advanced methods like machine learning and artificial intelligence to analyze vast datasets and identify patterns indicative of malicious activity.
This evolution underscores the necessity for organizations to adopt proactive protective measures that can adapt to an ever-changing threat landscape. The EDR market is projected to experience substantial growth, reaching USD 13.9 billion by 2034, fueled by the increasing demand for sophisticated cybersecurity solutions. As organizations grapple with a surge in ransomware attacks and data breaches, understanding what is endpoint detection and the importance of strong capabilities, including application allowlisting, has never been more critical.
By restricting the applications that can run, organizations can significantly minimize their attack surface and enhance compliance with regulations such as HIPAA, PCI-DSS, and GDPR. This strategic approach not only fortifies their security posture but also fosters trust among stakeholders. In a world where cyber threats are increasingly sophisticated, understanding what is endpoint detection and investing in advanced solutions is not just a choice; it's a necessity for safeguarding sensitive data and ensuring operational integrity.
In the world of cybersecurity, the importance of endpoint detection is paramount. This technology acts as a crucial defense mechanism, constantly monitoring endpoint devices to spot and address potential threats. As cyber threats grow more sophisticated, grasping and implementing endpoint detection strategies becomes essential for businesses that want to safeguard their sensitive data and uphold operational integrity.
Key points throughout this discussion highlight the evolution of endpoint detection technologies, the critical nature of real-time monitoring, and the need for integrating advanced analytics to tackle emerging threats. The transition from traditional antivirus solutions to advanced Endpoint Detection and Response (EDR) systems represents a significant leap in cybersecurity, allowing organizations to react swiftly to incidents and dramatically lower the risk of data breaches. Statistics underscore the urgency of proactive measures, showing that timely intervention can save organizations substantial costs linked to breaches.
The call to action is unmistakable: investing in robust endpoint detection solutions is not just a precaution; it’s a vital strategy for ensuring business security in an increasingly digital landscape. As organizations navigate the complexities of modern cyber threats, prioritizing endpoint detection will not only bolster their security posture but also build trust among stakeholders and clients. Embracing these technologies today will lay the groundwork for a more secure tomorrow.
What is endpoint detection in cybersecurity?
Endpoint detection refers to the continuous monitoring and assessment of endpoint devices, such as laptops, desktops, and mobile devices, for potential security threats.
Why is endpoint detection important?
It plays a crucial role in safeguarding devices by identifying risks and enabling organizations to respond swiftly to incidents, thus enhancing overall cybersecurity.
What are Endpoint Detection and Response (EDR) systems?
EDR systems are cybersecurity solutions that excel at identifying risks and provide robust investigation and remediation capabilities for organizations.
How do EDR solutions help organizations?
EDR solutions help organizations by offering advanced detection capabilities, enabling them to respond quickly to security incidents and maintain a strong security posture.
What is the significance of proactive monitoring in cybersecurity?
Proactive monitoring is critical as it allows organizations to detect breaches early, potentially saving significant costs associated with data breaches.
What does the data reveal about breach management?
Organizations that manage a breach within 30 days can save over $1 million, highlighting the importance of timely detection and response.
What challenges do organizations face in detecting breaches?
The average time between a breach and its detection exceeds 200 days, indicating the need for improved detection capabilities.
How can organizations prepare for emerging cyber threats?
Organizations can prepare by leveraging real-time data and advanced analytics to enhance their detection capabilities against emerging threats.
What should organizations invest in to improve their cybersecurity?
Investing in EDR solutions is recommended as it enhances detection capabilities and fortifies the overall security framework of an organization.