
In an era where cyber threats loom larger than ever, the healthcare sector stands at a critical juncture, facing an urgent need for robust cybersecurity measures. Fully managed cybersecurity services provide a lifeline, offering organizations comprehensive protection that enables them to focus on their core missions without the constant worry of security breaches. However, as the landscape of cyber threats evolves, how can executives ensure that their cybersecurity strategies are not only effective but also adaptable to future challenges?
The implications for healthcare organizations are profound. With the increasing frequency and sophistication of cyberattacks, CFOs must navigate a complex environment where the stakes are high. The potential for data breaches not only jeopardizes patient safety but also threatens the financial stability of healthcare institutions. This is where Cyber Solutions come into play, addressing these challenges head-on. By implementing tailored cybersecurity strategies, organizations can safeguard sensitive information and maintain trust with their patients.
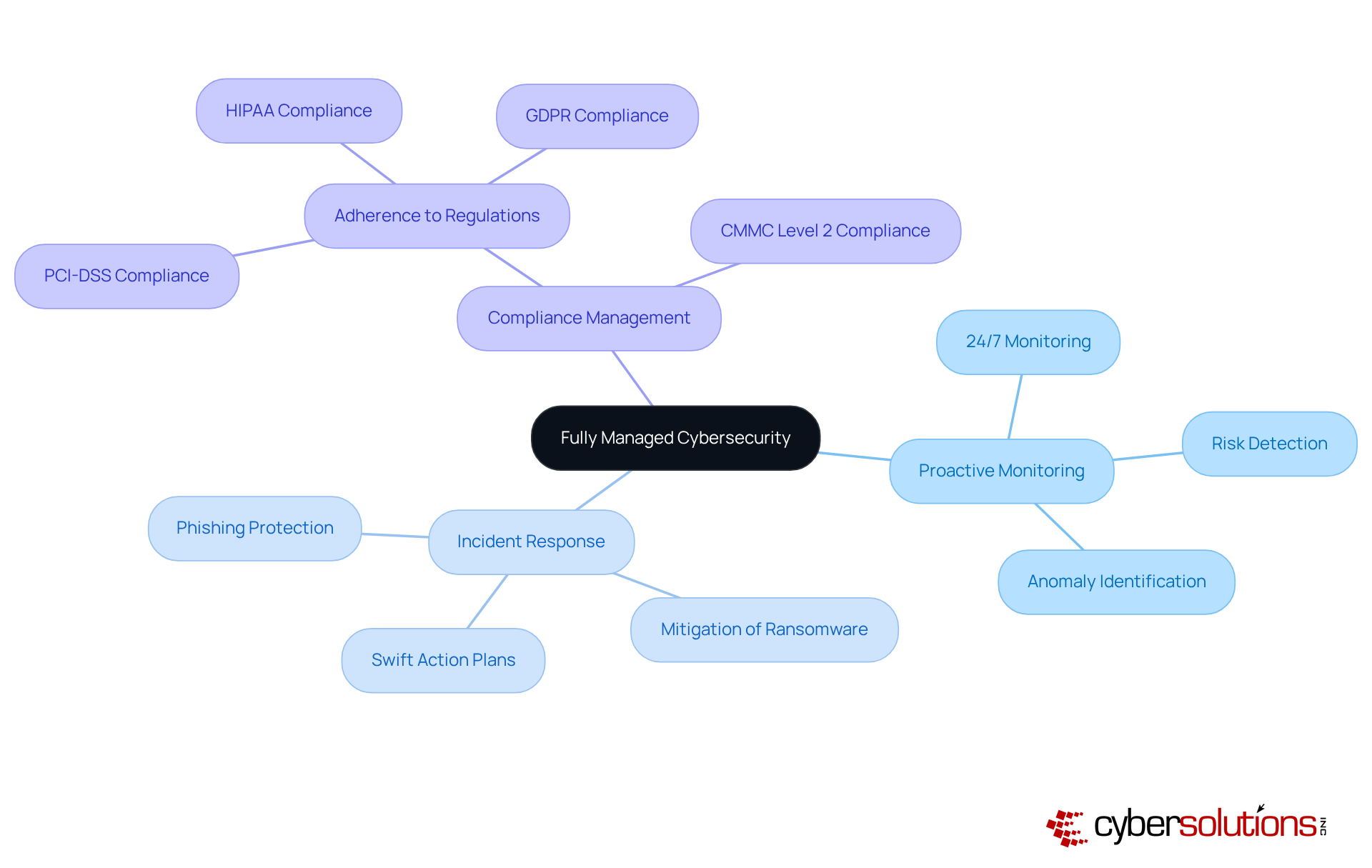
In today's digital landscape, the importance of robust cybersecurity in healthcare cannot be overstated. With the rise of sophisticated cyber threats, healthcare organizations face unique challenges that demand immediate attention. Outsourcing an organization's cybersecurity needs to specialized providers like Cyber Solutions offers a comprehensive solution through fully managed cybersecurity. This service encompasses continuous monitoring, risk detection, incident response, and compliance management, ensuring that healthcare entities can focus on their core operations without compromising security.
Proactive Monitoring: Cyber Solutions delivers 24/7 monitoring of your network, identifying anomalies and potential vulnerabilities. This continuous surveillance allows for the swift detection of suspicious activities, enabling timely interventions that prevent downtime or breaches.
Incident Response: In the event of a breach, swift action plans are crucial. Cyber Solutions establishes these plans to mitigate harm, protecting your business from ransomware, phishing, and other malware attacks.
Compliance Management: Adhering to industry regulations such as HIPAA, PCI-DSS, and GDPR is essential. Cyber Solutions assists in maintaining compliance standards, safeguarding federal data, and ensuring eligibility for government contracts, including CMMC Level 2 compliance for Controlled Unclassified Information (CUI).
The importance of fully managed cybersecurity is highlighted by its capability to offer peace of mind for organizations. By allowing specialists to handle safety requirements, businesses can concentrate on essential operations. This approach not only enhances security posture but also optimizes operational efficiency and minimizes potential financial losses from cyber incidents.
Are you ready to elevate your cybersecurity strategy? With Cyber Solutions, you can navigate the complexities of digital protection confidently.
In today's rapidly evolving digital landscape, the importance of fully managed cybersecurity in healthcare is paramount. With increasing threats targeting sensitive patient data, healthcare organizations face unique challenges that demand immediate attention and action through fully managed cybersecurity.
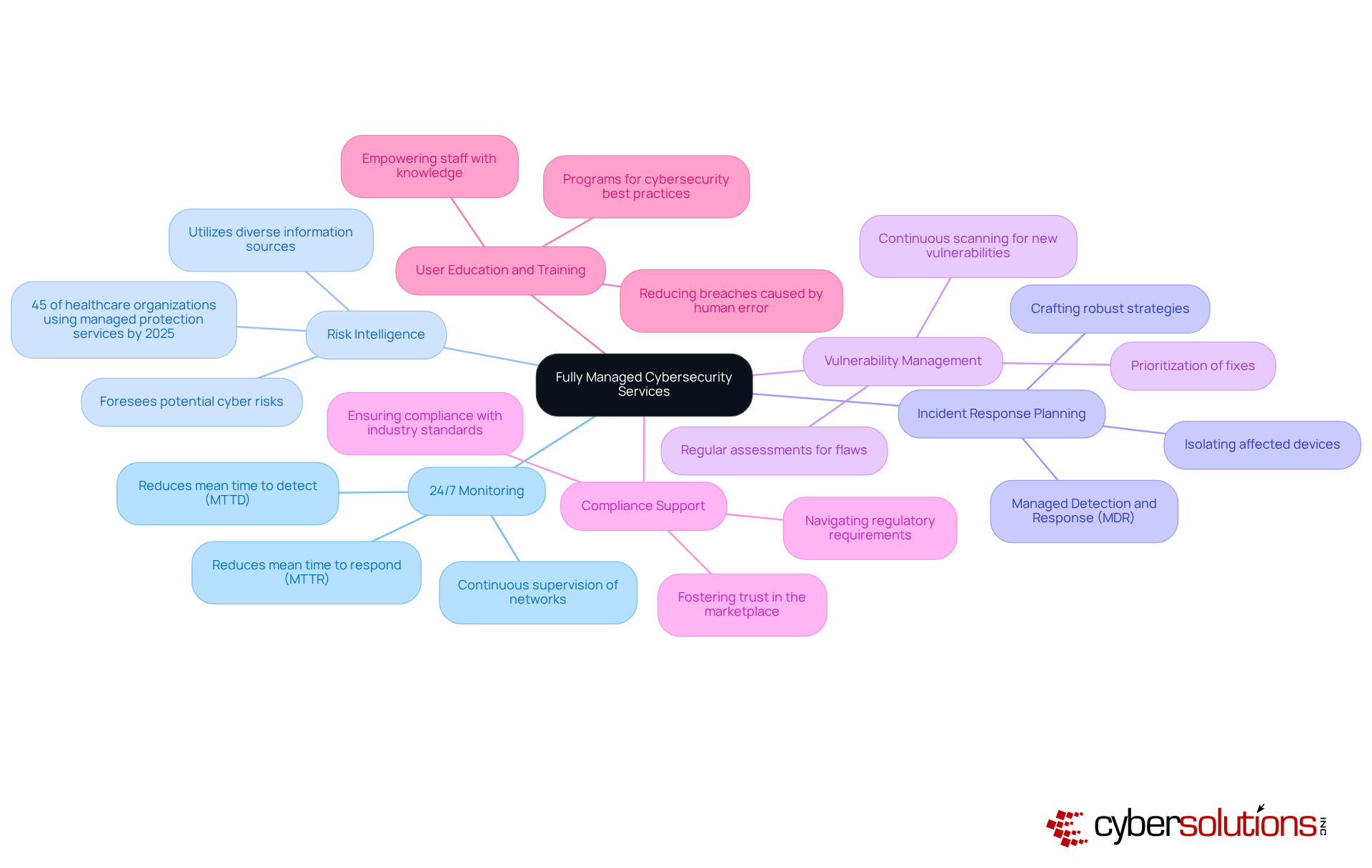
Key Components of Fully Managed Cybersecurity Services
24/7 Monitoring: Continuous supervision of networks and systems is essential for identifying anomalies and risks in real-time. This proactive approach significantly reduces the mean time to detect (MTTD) and respond (MTTR) to incidents, ensuring rapid containment and minimal downtime.
Risk Intelligence: By leveraging information from diverse sources, organizations can effectively foresee and mitigate potential cyber risks. As of 2025, approximately 45% of healthcare organizations are employing managed protection services, underscoring the growing reliance on threat intelligence to enhance defense strategies.
Incident Response Planning: Crafting and executing robust strategies for incident response is crucial. Fully managed cybersecurity services, including Managed Detection and Response (MDR), are pivotal in isolating affected devices and restoring systems, providing structured responses that not only mitigate damage but also inform future prevention strategies.
Vulnerability Management: Regular assessments are conducted to identify and rectify flaws within systems. This proactive stance is vital, as new security vulnerabilities emerge weekly, necessitating continuous scanning and prioritization of fixes to minimize exploitation risks.
Compliance Support: Navigating regulatory requirements is critical, especially in sectors like healthcare and finance. Fully managed cybersecurity services help organizations navigate complex compliance landscapes, ensuring they not only meet but often exceed regulatory benchmarks, thereby fostering trust in the marketplace.
User Education and Training: Programs aimed at educating employees about cybersecurity best practices and risk awareness are fundamental. By empowering staff with knowledge, organizations can significantly reduce the risk of breaches caused by human error, a prevalent vulnerability in today's digital environment.
These elements work in unison to create a comprehensive security strategy that not only protects sensitive information but also ensures compliance with industry regulations. Ultimately, this approach enhances organizational resilience against the ever-evolving landscape of cyber risks.
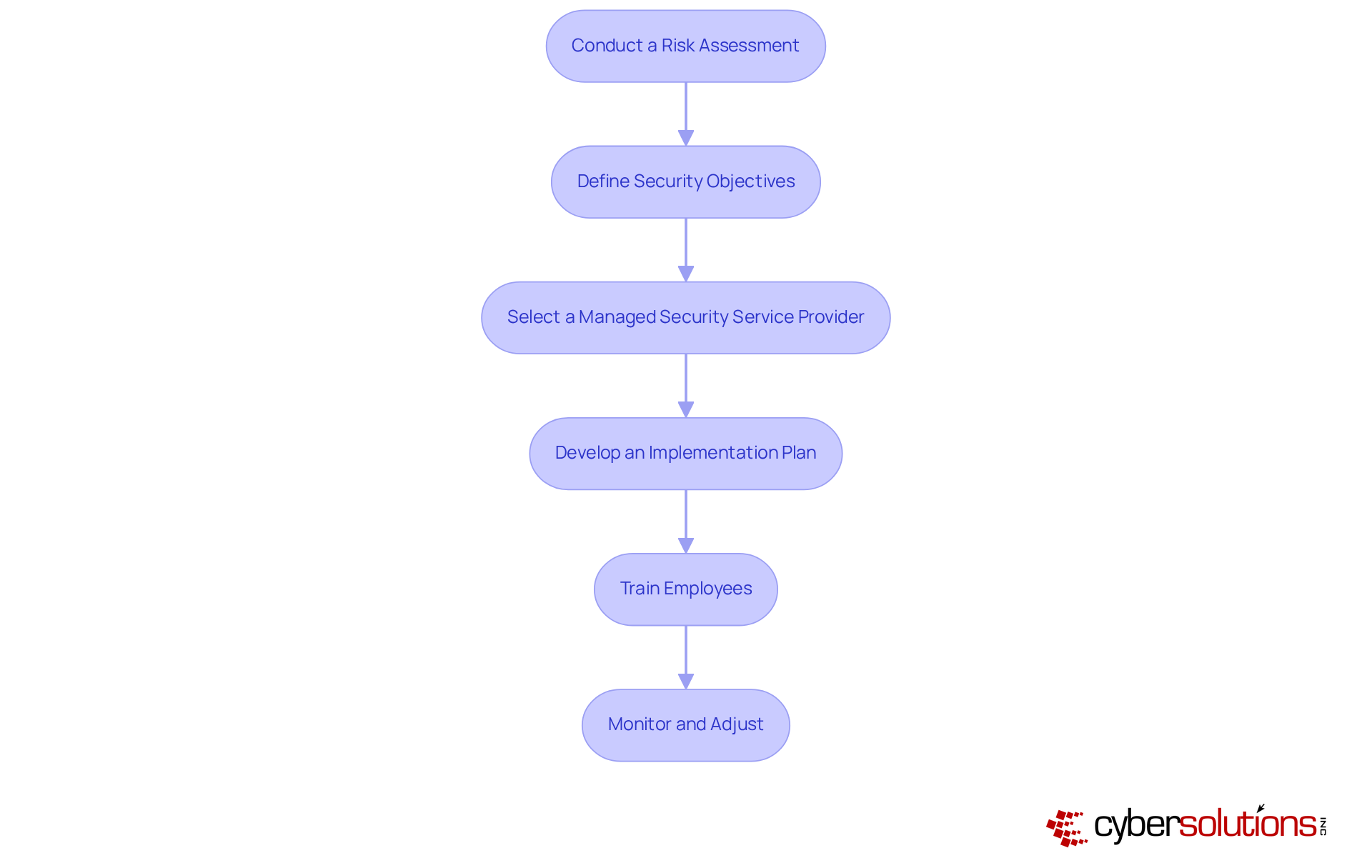
To effectively implement fully managed cybersecurity, executives must follow these essential steps:
Conduct a Risk Assessment: Identify potential vulnerabilities and threats specific to your organization. This involves assessing current protective measures and understanding the unique risks associated with your industry.
Define Security Objectives: Establish clear goals for what your cybersecurity strategy should achieve. Align these objectives with business priorities, ensuring they address compliance requirements and operational continuity.
Select a Managed Security Service Provider (MSSP): Choose a provider that meets your organization's needs and compliance requirements. Look for an MSSP that offers a comprehensive suite of services, including 24/7 monitoring, incident response, and vulnerability management, tailored to your specific context.
Develop an Implementation Plan: Create a roadmap outlining the integration process, including timelines and responsibilities. This plan should detail how the MSSP's services will be integrated with existing systems and processes.
Train Employees: Ensure that all staff are educated on new protocols and the importance of online security. Regular training sessions can help foster a culture of awareness and adherence within the organization.
Monitor and Adjust: Continuously assess the effectiveness of your security measures and make necessary modifications based on evolving threats. This includes reviewing incident response outcomes and adapting strategies to mitigate new risks.
By following these steps, organizations can seamlessly integrate fully managed cybersecurity into their operations, significantly enhancing their overall defense posture.
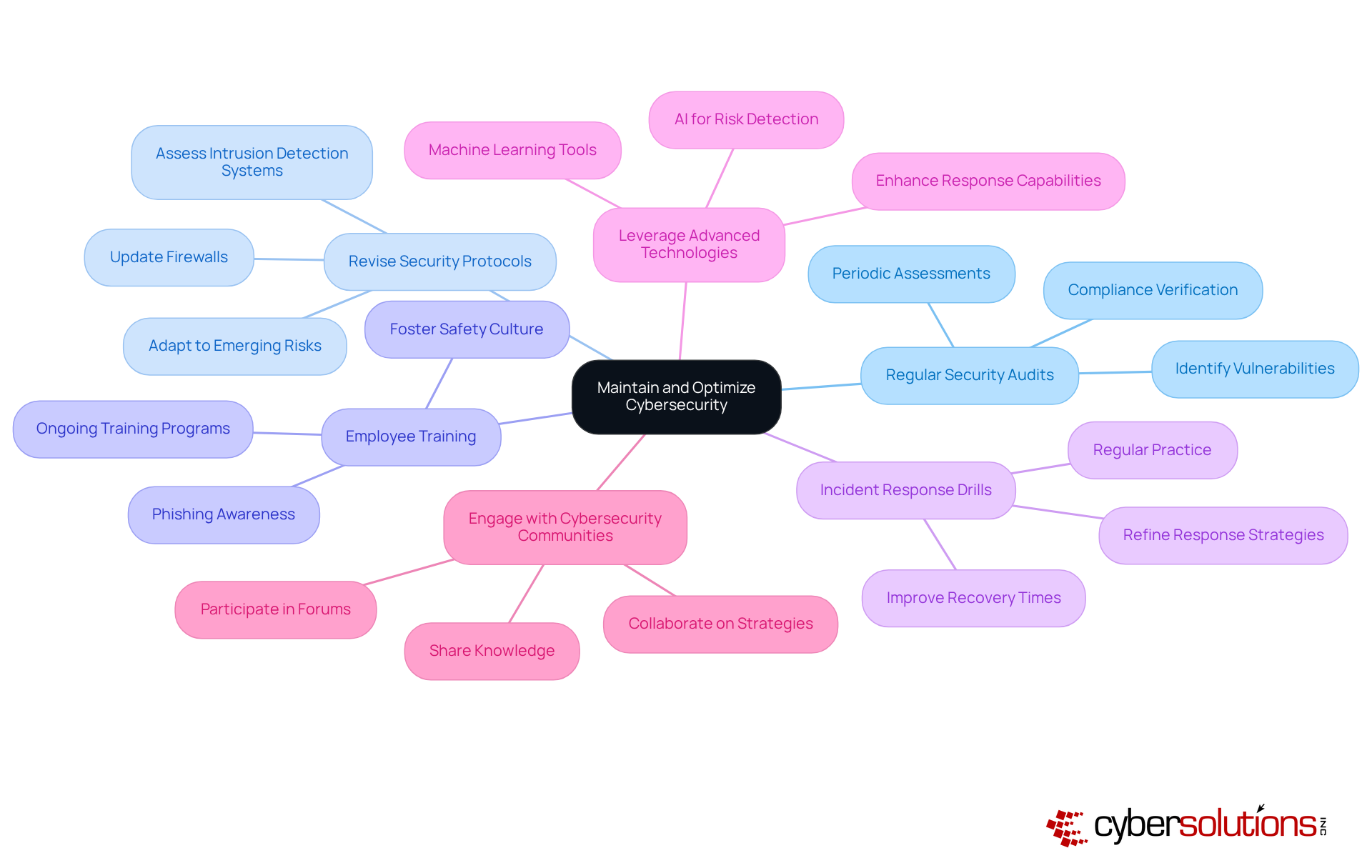
In today's digital landscape, maintaining robust fully managed cybersecurity is not just an option; it's a necessity for organizations. With cyber threats evolving at an alarming rate, the stakes have never been higher. Organizations must adopt comprehensive strategies that include fully managed cybersecurity to safeguard their assets and data against potential breaches.
Regular Security Audits: Conducting periodic assessments is essential to evaluate the effectiveness of current security measures and identify areas for improvement. Regular audits reveal vulnerabilities before they can be exploited. Studies show that entities investing in routine audits can significantly lower the risk of cyberattacks and data breaches.
Revise Security Protocols: Staying informed about the latest cybersecurity trends is crucial. Organizations must modify their protocols to tackle emerging risks effectively. As cyber threats develop, protective measures like firewalls and intrusion detection systems should be routinely assessed and updated to mitigate risks.
Employee Training: Implementing ongoing training programs keeps staff informed about the latest phishing tactics and best practices for protection. Continuous education fosters a culture of safety awareness, which is vital since human errors remain a primary cause of breaches.
Incident Response Drills: Regularly practicing incident response plans ensures readiness in the event of a security breach. These drills refine response strategies and improve recovery times, ultimately enhancing overall resilience.
Leverage Advanced Technologies: Utilizing AI and machine learning tools can significantly enhance risk detection and response capabilities. As cybercriminals adopt increasingly complex methods, incorporating advanced technologies provides a considerable edge in detecting and mitigating threats.
Engage with Cybersecurity Communities: Participating in industry forums and discussions allows organizations to share knowledge and stay informed about emerging risks and solutions. Collaboration within the security community leads to valuable insights and strategies that strengthen defenses against evolving threats.
By implementing these strategies, organizations can maintain their cybersecurity defenses through fully managed cybersecurity and continuously improve their resilience against cyber threats. Are you ready to take action and fortify your cybersecurity measures?
In today's healthcare landscape, the importance of fully managed cybersecurity cannot be overstated. As cyber threats escalate, healthcare organizations face unique challenges that demand immediate attention. By outsourcing cybersecurity needs to specialized providers, organizations can not only enhance their security posture but also focus on their core functions, ensuring robust protection against evolving threats.
Essential components of fully managed cybersecurity services include:
Each of these elements is crucial in crafting a comprehensive security strategy that mitigates risks and ensures adherence to industry regulations. For executives, understanding these components is vital; they serve as a roadmap for integrating these services effectively into their organizations.
As cyber threats continue to evolve, proactive measures are imperative. Engaging in continuous improvement and fostering a culture of cybersecurity awareness are essential strategies for executives. By prioritizing these approaches, leaders can protect their organizations and contribute to a safer digital environment for all. Are you ready to take the necessary steps to safeguard your organization against cyber threats?
What is fully managed cybersecurity?
Fully managed cybersecurity refers to outsourcing an organization's cybersecurity needs to specialized providers, such as Cyber Solutions, which offers comprehensive services including continuous monitoring, risk detection, incident response, and compliance management.
Why is cybersecurity particularly important in healthcare?
Cybersecurity is crucial in healthcare due to the rise of sophisticated cyber threats and the unique challenges faced by healthcare organizations, which require immediate attention to protect sensitive data and maintain operational integrity.
What services are included in fully managed cybersecurity by Cyber Solutions?
The services include proactive monitoring of networks, incident response planning, and compliance management to ensure adherence to industry regulations.
How does proactive monitoring work?
Proactive monitoring involves 24/7 surveillance of the network to identify anomalies and potential vulnerabilities, allowing for the swift detection of suspicious activities and timely interventions to prevent breaches or downtime.
What is the role of incident response in managed cybersecurity?
Incident response involves establishing swift action plans to mitigate harm in the event of a breach, protecting the organization from threats such as ransomware, phishing, and other malware attacks.
How does Cyber Solutions assist with compliance management?
Cyber Solutions helps organizations maintain compliance with industry regulations like HIPAA, PCI-DSS, and GDPR, safeguarding federal data and ensuring eligibility for government contracts, including CMMC Level 2 compliance for Controlled Unclassified Information (CUI).
What are the benefits of fully managed cybersecurity for organizations?
The benefits include enhanced security posture, optimized operational efficiency, minimized potential financial losses from cyber incidents, and allowing organizations to focus on their core operations without compromising security.