
Understanding the complexities of CMMC 2.0 compliance is crucial for organizations within the Defense Industrial Base. This framework not only protects against cyber threats but also opens doors to lucrative defense contracts. As companies strive to achieve Level 2 compliance, they encounter the significant challenge of aligning their cybersecurity practices with stringent regulatory standards.
How can organizations effectively prepare and position themselves to meet these requirements? More importantly, how can they leverage compliance as a competitive advantage? By addressing these questions, organizations can not only safeguard their operations but also enhance their market position.
CMMC 2.0, or the Cybersecurity Maturity Model Certification, stands as a crucial framework established by the Department of Defense (DoD) to bolster the cybersecurity posture of entities within the Defense Industrial Base (DIB). Why is this important? The CMMC 2.0 Level 2 alignment specifically aims to safeguard Controlled Unclassified Information (CUI) and requires adherence to 110 security practices outlined in NIST SP 800-171. For entities seeking contracts with the DoD, this level of compliance is not just a recommendation; it’s essential. Non-compliance can lead to severe financial penalties and operational disruptions.
Achieving these standards does more than protect sensitive information; it enhances a company's reputation and reliability in the marketplace. A pivotal aspect of this compliance is the implementation of application allowlisting, which actively prevents unauthorized or malicious applications from running on systems. By allowing only authorized applications to function, entities can effectively thwart malware, ransomware, and zero-day threats, ensuring their cybersecurity protocols align with necessary standards.
Entities should proactively conduct thorough self-assessments and collaborate with third-party evaluation firms (C3PAOs) to pinpoint and rectify any gaps in their security measures. This proactive approach is vital, as compliance with version 2.0 will unfold over the next three years, with ongoing responsibilities to renew certification annually. Recent articles underscore the urgency for entities to revise their policies and prepare for forthcoming evaluations related to 2.0, emphasizing its role in shaping the cybersecurity landscape for defense contractors.
Moreover, leveraging Compliance as a Service (CaaS) can offer businesses comprehensive solutions to meet regulatory requirements, including assessments, policy development, monitoring, and audit preparation. This service proves particularly beneficial for organizations in highly regulated sectors, ensuring they remain compliant with standards such as HIPAA and PCI-DSS.
In conclusion, understanding and achieving CMMC 2.0 Level 2 compliance is imperative for defense contractors. It not only ensures the protection of sensitive information but also fosters a culture of safety that can lead to enhanced business opportunities and a stronger market presence.
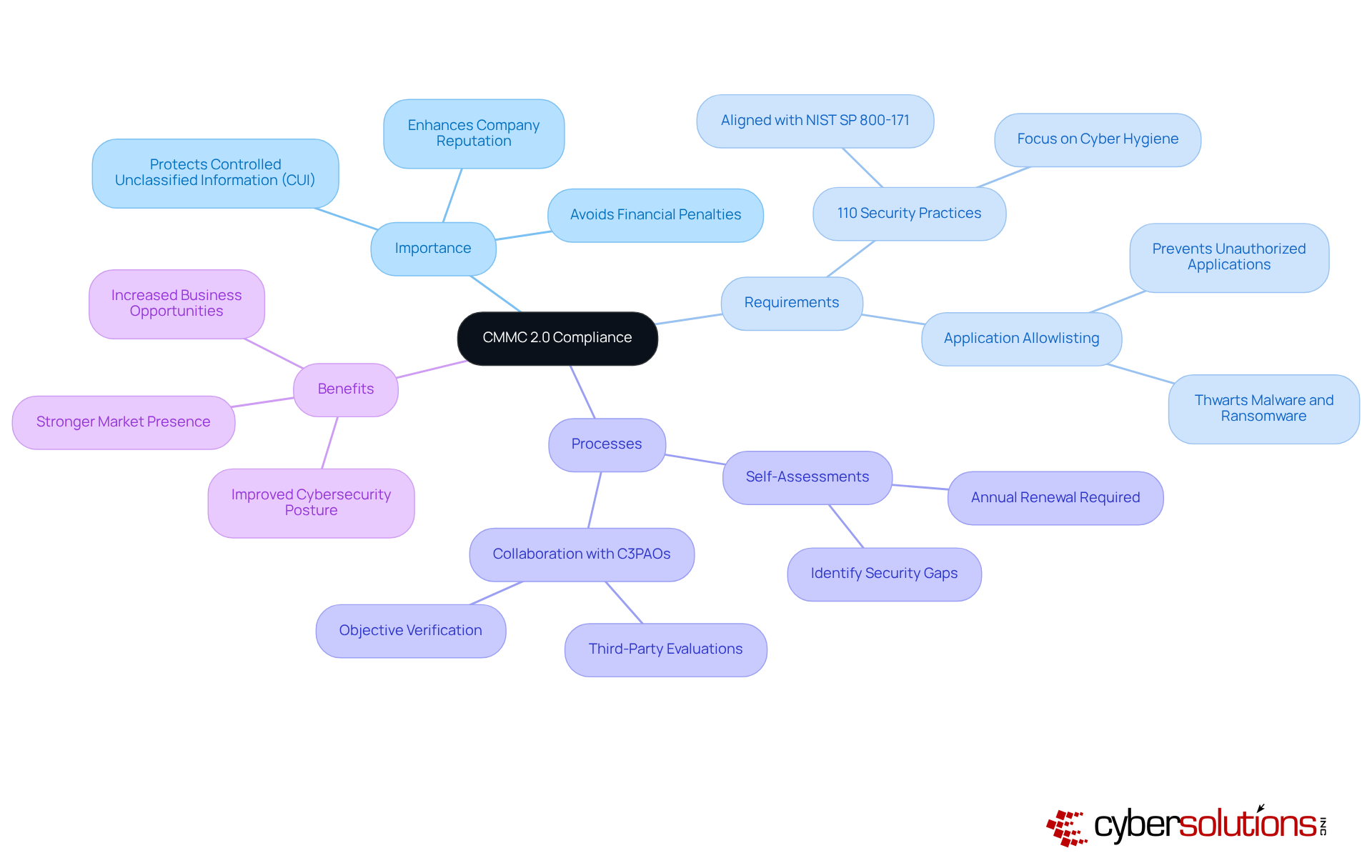
CMMC 2.0 Level 2 requires the implementation of 110 controls across 14 domains, including Access Control, Incident Response, and Risk Management. This is not just a regulatory requirement; it’s a critical step towards safeguarding sensitive information. Here’s what organizations need to know:
Access Control: Establish robust policies that restrict access to Controlled Unclassified Information (CUI) based on user roles. This ensures that only authorized personnel can access sensitive data, which is vital for protecting federal information and maintaining compliance.
Incident Response: Develop and maintain a comprehensive incident response plan. This plan should effectively address potential breaches, minimizing impact and facilitating quick recovery. Aligning this strategy with enhanced security protocols is essential for certification.
Risk Assessment: Regularly conduct risk assessments to pinpoint vulnerabilities within your organization’s systems. Proactively implementing strategies to mitigate these risks is crucial for bolstering your cybersecurity posture and ensuring compliance with CMMC standards.
System Protection Plan (SSP): Create a detailed SSP that outlines the protective measures and practices in place. This document serves as a guide for compliance and management, proving essential during audits.
Continuous Monitoring: Establish processes for ongoing monitoring of security controls. This ensures their effectiveness and allows for adaptation to evolving threats, which is key to safeguarding sensitive federal information.
Organizations should leverage resources like the Assessment Guide to meet all requirements effectively. Additionally, tailored remediation strategies should be developed to address any regulatory gaps identified during evaluations.
Currently, a growing number of organizations are achieving compliance with CMMC 2.0 Level 2, which marks a significant shift towards enhanced cybersecurity practices in the defense sector. This compliance is not merely a regulatory obligation; it’s a strategic advantage that can secure contracts and build trust with procurement officers. Notably, firms that achieve early compliance report smoother renewals and fewer delays in project execution. With enforcement set to begin on November 10, 2025, it’s imperative for companies to act swiftly to meet these requirements.
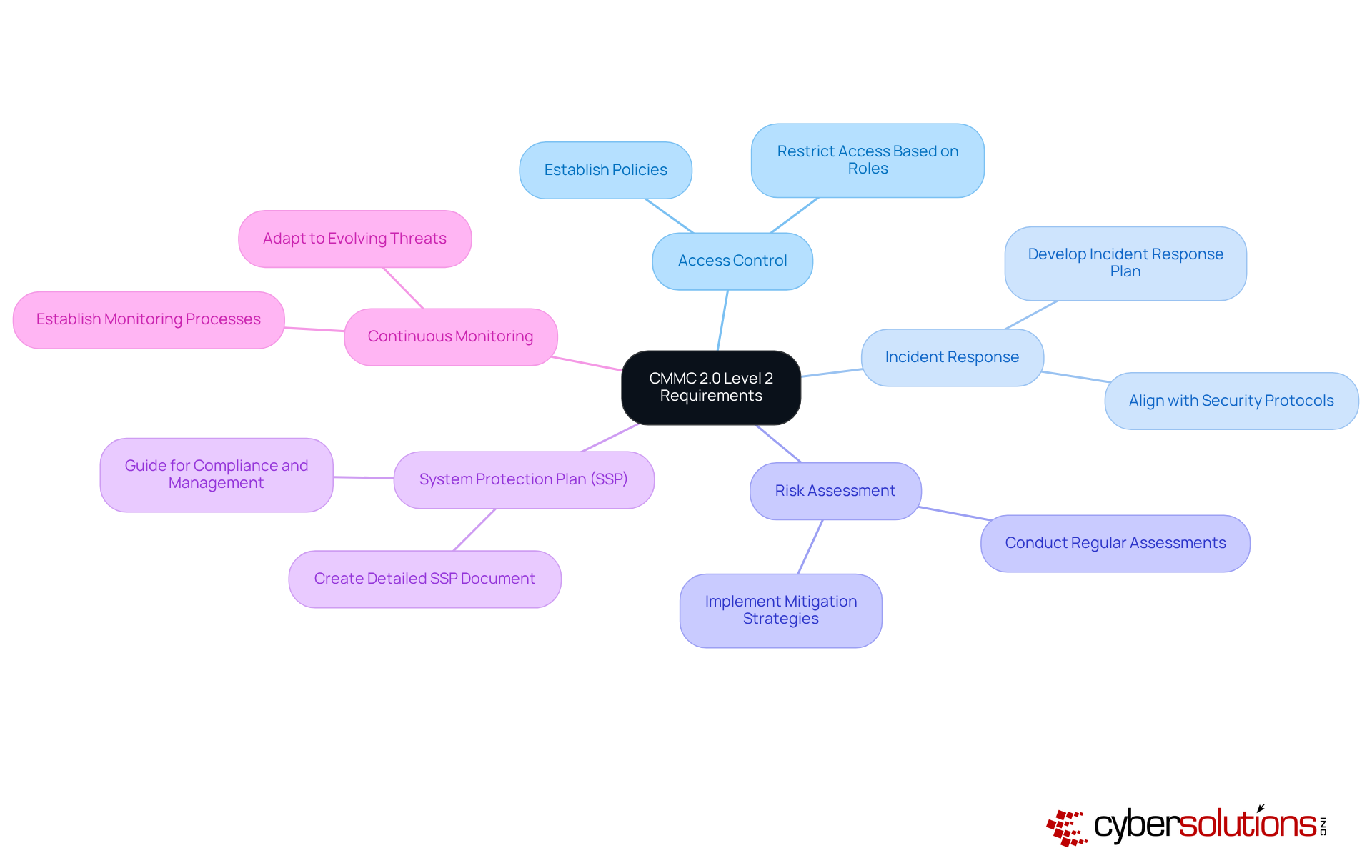
To prepare for CMMC 2.0 Level 2, organizations must take decisive action for compliance. Cybersecurity is not just a regulatory requirement; it’s a critical component of safeguarding sensitive information in today’s digital landscape. Here are essential steps to ensure your organization is ready:
Conduct a Gap Analysis: Evaluate your current cybersecurity practices against the relevant standards to pinpoint areas for improvement. Did you know that almost half of organizations have completed a thorough gap analysis? This emphasizes its essential role in readiness for regulations.
Create a System Security Plan (SSP): Document your current security measures and detail the additional controls needed to meet regulatory standards. Organizations that develop comprehensive SSPs are better equipped to navigate the complexities of CMMC 2.0 Level 2 requirements.
Create a Plan of Action and Milestones (POA&M): Formulate a roadmap for addressing identified gaps, specifying timelines and responsible parties. This structured approach ensures accountability and allows for effective progress tracking.
Engage Stakeholders: Involve key personnel across departments to foster a comprehensive approach to compliance. Collaboration not only enhances the effectiveness of regulatory initiatives but also ensures alignment with organizational objectives.
Allocate Resources: Budget for essential tools, training, and personnel to implement the required security controls effectively. As organizations anticipate rising regulatory expenses, strategic resource allocation becomes crucial for successful implementation.
Utilizing tools like the Compliance Checklist can simplify this preparation process, ensuring that your organization is well-equipped to meet the evolving requirements of cybersecurity standards.
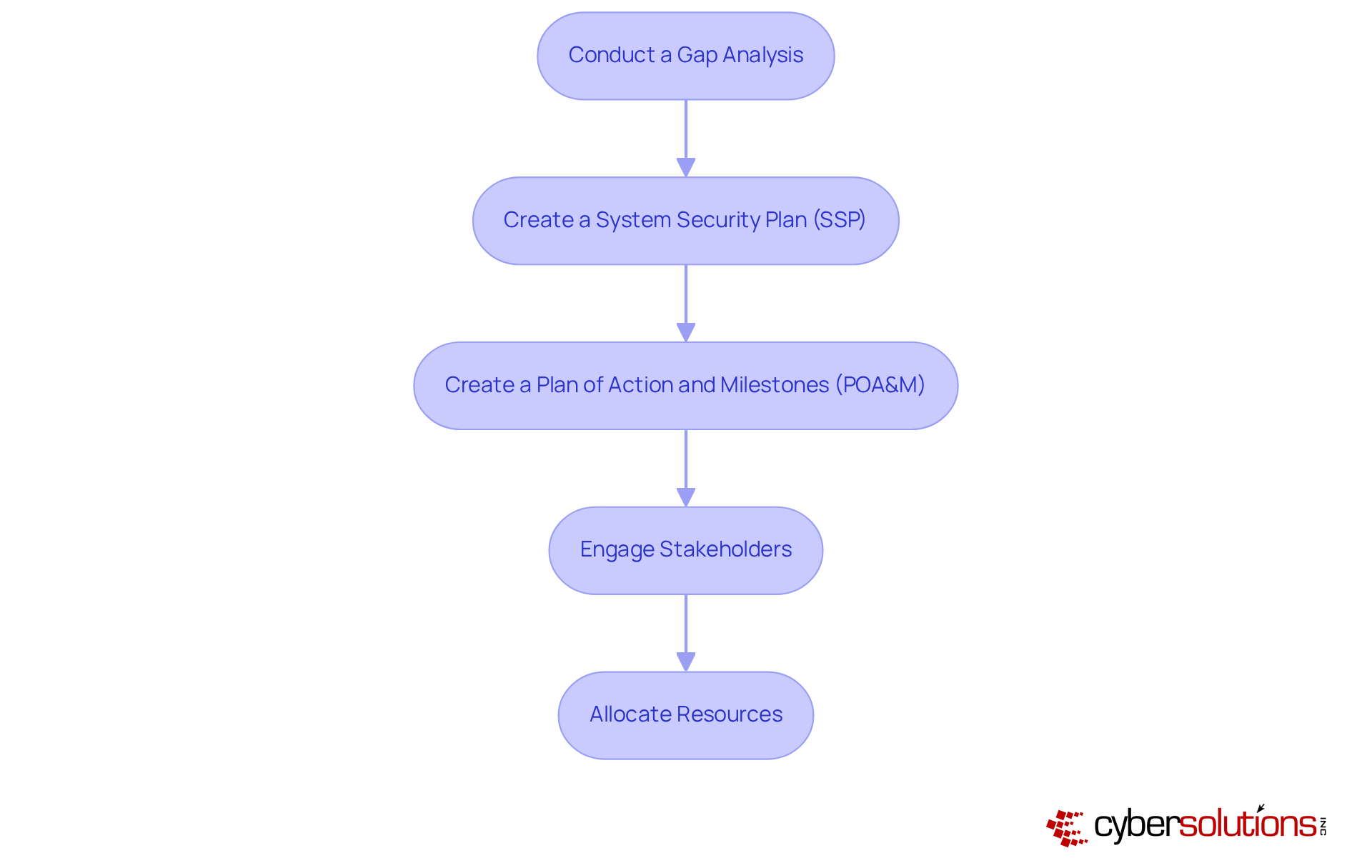
Navigating the CMMC 2.0 assessment process is crucial for your organization's compliance success. By following these essential steps, you can significantly enhance your readiness and ensure a smoother evaluation.
Pre-Assessment: Start with an internal review to confirm that all required controls are effectively implemented and operational. This step is vital for identifying potential gaps before the official assessment.
Select a Certified Third-Party Assessment Organization (C3PAO): Choosing an accredited C3PAO is essential for conducting the official assessment. Look for entities with a proven track record in cybersecurity maturity model standards; their expertise can greatly improve your readiness and increase your chances of success.
Prepare Documentation: Ensure that all necessary documentation, including the System Security Plan (SSP) and Plan of Action and Milestones (POA&M), is complete and readily accessible. Treat your documentation as a living entity, regularly updating it to reflect current practices and controls.
Carry Out the Evaluation: The C3PAO will assess your organization against the CMMC 2.0 Level 2 criteria, focusing on the execution and effectiveness of your security measures. This phase typically lasts 4-6 weeks and includes a thorough review of evidence and interviews with key personnel.
Address Findings: If any gaps are identified during the assessment, promptly develop a remediation plan to tackle these issues. Organizations that actively manage their findings are more likely to achieve compliance and maintain eligibility for future contracts.
By adhering to these steps, organizations can navigate the 2.0 assessment process efficiently, enhancing their chances of compliance and gaining a competitive edge in the defense contracting arena.
In today’s rapidly evolving digital landscape, ensuring compliance with CMMC 2.0 Level 2 is not just a regulatory requirement; it’s a critical component of safeguarding sensitive data. Organizations must adopt the following practices to ensure they meet these standards and protect their information effectively:
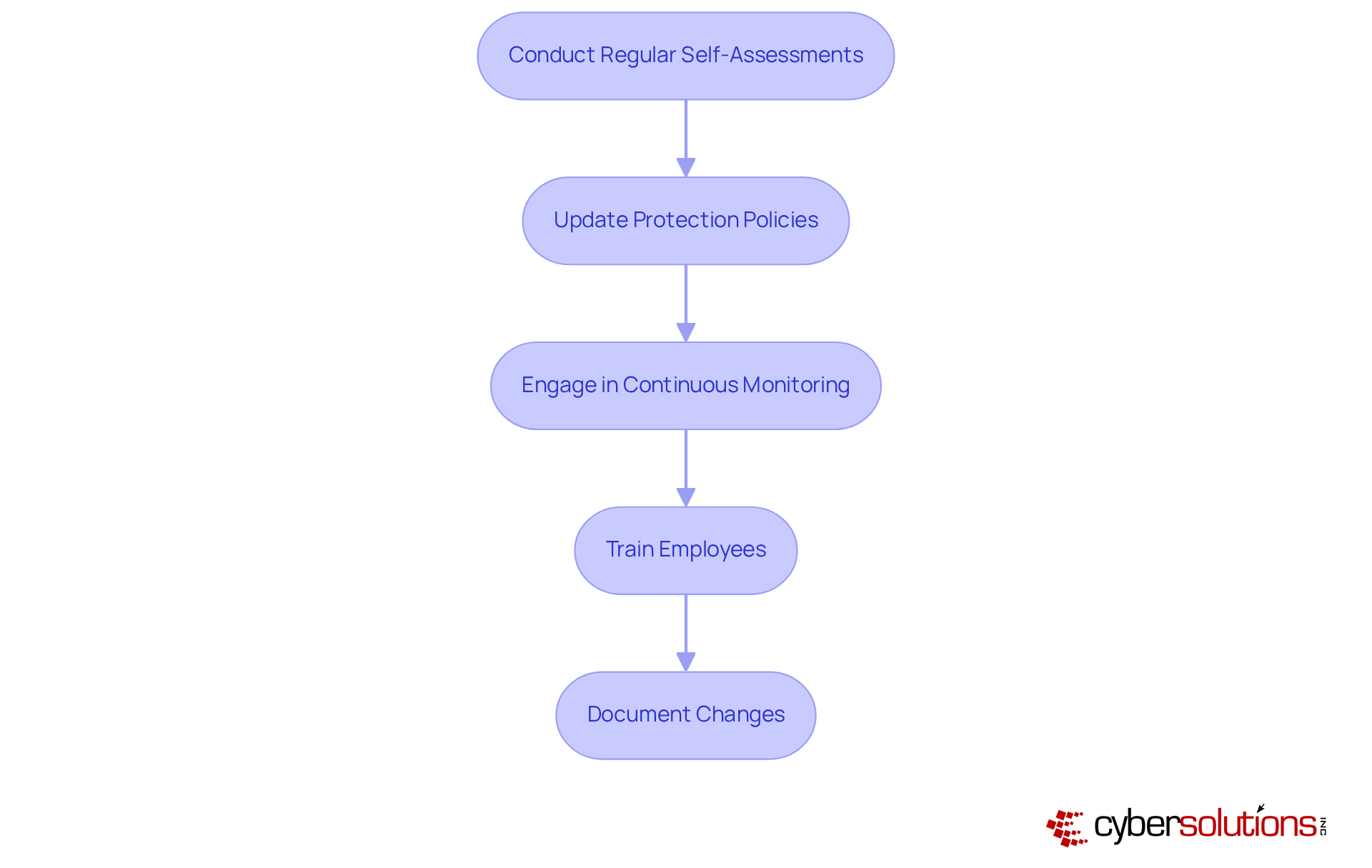
Conduct Regular Self-Assessments: Performing self-assessments at least annually is essential for ongoing adherence to CMMC requirements. This proactive approach not only identifies potential gaps but also reinforces a culture of compliance.
Update Protection Policies: Regularly reviewing and updating protection policies and procedures is vital to reflect changes in the threat landscape and evolving regulatory requirements. This guarantees that protective measures remain effective against emerging threats.
Engage in Continuous Monitoring: Implementing continuous monitoring solutions is crucial for detecting and responding to security incidents in real-time. This capability enhances an organization’s ability to uphold regulations and mitigate risks effectively.
Train Employees: Continuous education for staff is essential to ensure they understand their responsibilities in upholding regulations and safeguarding sensitive information. Empowered employees are key to a robust protective stance.
Document Changes: Keeping detailed records of any changes made to security practices and controls is necessary to demonstrate compliance during future assessments. This documentation serves as proof of a group's commitment to maintaining high standards of cybersecurity.
By following these practices, organizations can ensure compliance with CMMC 2.0 Level 2 and effectively protect their sensitive data. Are you ready to take the necessary steps to enhance your cybersecurity posture?
Achieving CMMC 2.0 Level 2 compliance is not just essential; it’s a strategic imperative for organizations within the Defense Industrial Base. This compliance safeguards sensitive information and positions these organizations favorably in a competitive market. It’s more than a mere checkbox; it’s a commitment to cybersecurity that can significantly influence an organization’s ability to secure contracts with the Department of Defense.
To attain this compliance, organizations must adopt a comprehensive approach. Understanding the requirements is crucial, as is preparing effectively for the assessment process. Key steps include:
These strategies not only facilitate compliance but also enhance an organization’s overall cybersecurity posture.
Given the stringent requirements set forth by CMMC 2.0, proactive measures are essential. The evolving landscape of cybersecurity threats demands a strong commitment to compliance and best practices. By prioritizing these efforts, organizations can safeguard sensitive information and build trust with clients and stakeholders. This commitment ultimately leads to greater business opportunities and success in the defense contracting arena.
What is CMMC 2.0 and why is it important?
CMMC 2.0, or the Cybersecurity Maturity Model Certification, is a framework established by the Department of Defense (DoD) to enhance the cybersecurity posture of entities within the Defense Industrial Base (DIB). It is crucial for safeguarding Controlled Unclassified Information (CUI) and requires compliance with 110 security practices outlined in NIST SP 800-171.
What are the consequences of non-compliance with CMMC 2.0?
Non-compliance with CMMC 2.0 can lead to severe financial penalties and operational disruptions for entities seeking contracts with the DoD.
What is application allowlisting and why is it important?
Application allowlisting is a security practice that prevents unauthorized or malicious applications from running on systems by allowing only authorized applications. This is vital for protecting against malware, ransomware, and zero-day threats.
How should organizations prepare for CMMC 2.0 compliance?
Organizations should conduct thorough self-assessments, collaborate with third-party evaluation firms (C3PAOs), and proactively identify and rectify any gaps in their security measures to prepare for CMMC 2.0 compliance.
What is the timeline for achieving CMMC 2.0 compliance?
Compliance with CMMC 2.0 will unfold over the next three years, with ongoing responsibilities to renew certification annually.
What services can help organizations achieve compliance?
Compliance as a Service (CaaS) can provide comprehensive solutions, including assessments, policy development, monitoring, and audit preparation, particularly beneficial for organizations in highly regulated sectors.
What are the main requirements for CMMC 2.0 Level 2 compliance?
CMMC 2.0 Level 2 requires the implementation of 110 controls across 14 domains, including Access Control, Incident Response, Risk Assessment, System Protection Plan (SSP), and Continuous Monitoring.
What is the significance of the System Protection Plan (SSP)?
The SSP is a detailed document outlining the protective measures and practices in place, serving as a guide for compliance and management, and is essential during audits.
When will enforcement of CMMC 2.0 begin?
Enforcement of CMMC 2.0 is set to begin on November 10, 2025, making it imperative for companies to act swiftly to meet the requirements.
What advantages do organizations gain from achieving early compliance with CMMC 2.0?
Organizations that achieve early compliance with CMMC 2.0 report smoother renewals and fewer delays in project execution, providing a strategic advantage in securing contracts and building trust with procurement officers.