
Understanding the Cybersecurity Maturity Model Certification (CMMC) is essential for organizations seeking to secure contracts with the Department of Defense (DoD). This framework establishes rigorous cybersecurity standards that act as a crucial defense against the rising tide of cyber threats. As the compliance deadline looms, the stakes couldn't be higher - failure to comply could result in losing contract eligibility and incurring significant financial penalties.
How can organizations effectively navigate this intricate landscape to ensure compliance while preserving operational integrity? By grasping the nuances of CMMC, organizations can not only safeguard their interests but also enhance their overall cybersecurity posture.
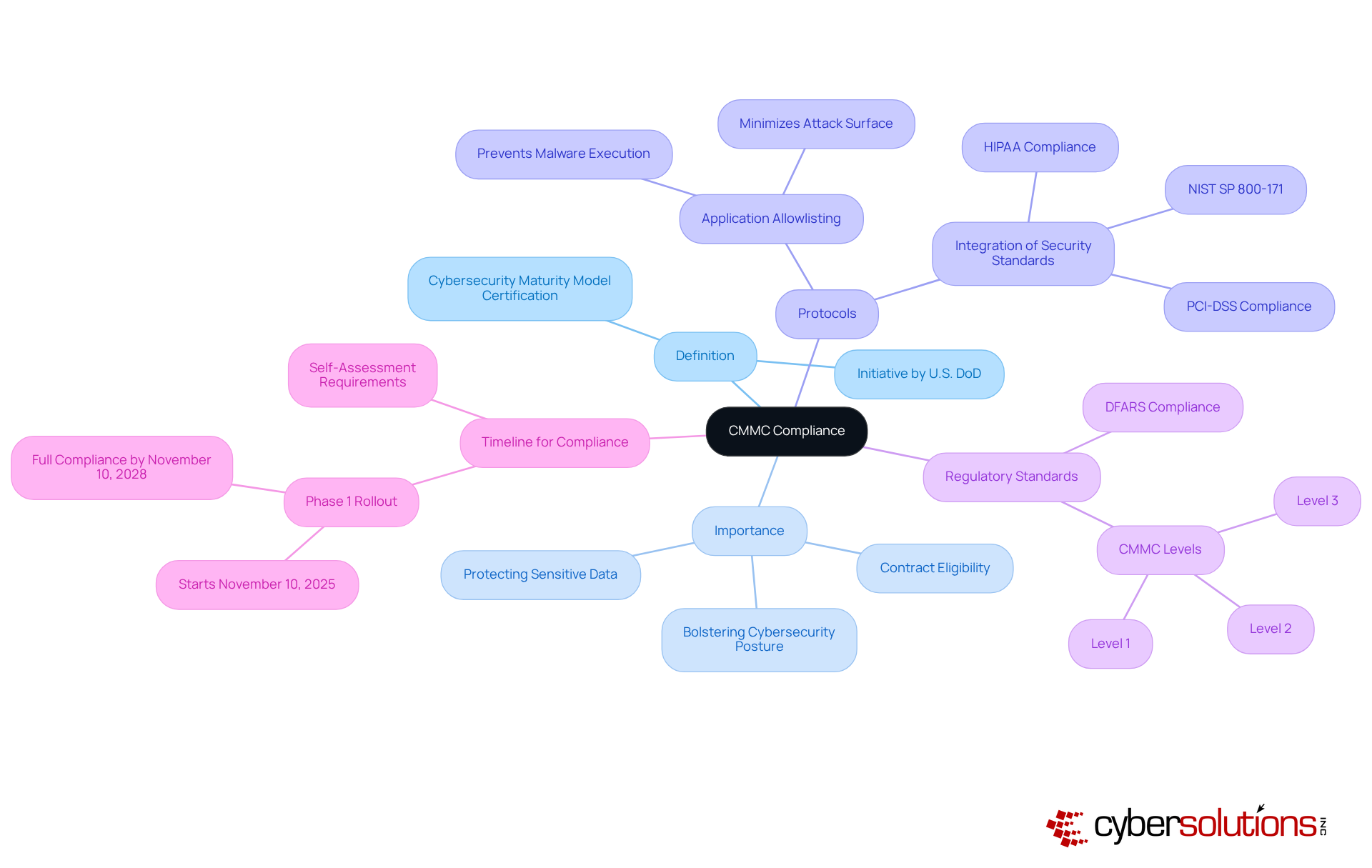
The CMMC compliance definition refers to the Cybersecurity Maturity Model Certification (CMMC), which is not just a framework; it’s a critical initiative by the U.S. Department of Defense (DoD) aimed at bolstering the cybersecurity posture of organizations handling Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). With escalating cybersecurity threats, this framework introduces several tiers of adherence, ensuring that contractors implement robust security protocols to protect sensitive data.
A cornerstone of these protocols is application allowlisting, which effectively prevents malware and unauthorized software from executing. This proactive measure minimizes the attack surface and helps organizations comply with stringent regulatory standards, including HIPAA and PCI-DSS. By integrating various information security standards and best practices, such as those from NIST SP 800-171, the CMMC offers a comprehensive strategy for data protection.
Starting November 10, 2025, the CMMC compliance definition will require all DoD contractors to adhere to these mandatory standards, marking a significant shift in digital security regulations within the defense industrial sector. This transition underscores the urgent need for organizations to enhance their cybersecurity frameworks. Non-compliance could jeopardize contract eligibility and disrupt operational continuity. As the certification framework evolves, it’s crucial for companies to understand the CMMC compliance definition and prepare for the full compliance phase, which will be in effect by November 10, 2028.
Moreover, Cyber Solutions stands ready to assist with Compliance as a Service (CaaS), offering businesses comprehensive solutions to meet regulatory requirements. From assessments and policy creation to monitoring and audit readiness, Cyber Solutions ensures that organizations remain compliant and secure in an increasingly complex cybersecurity landscape.
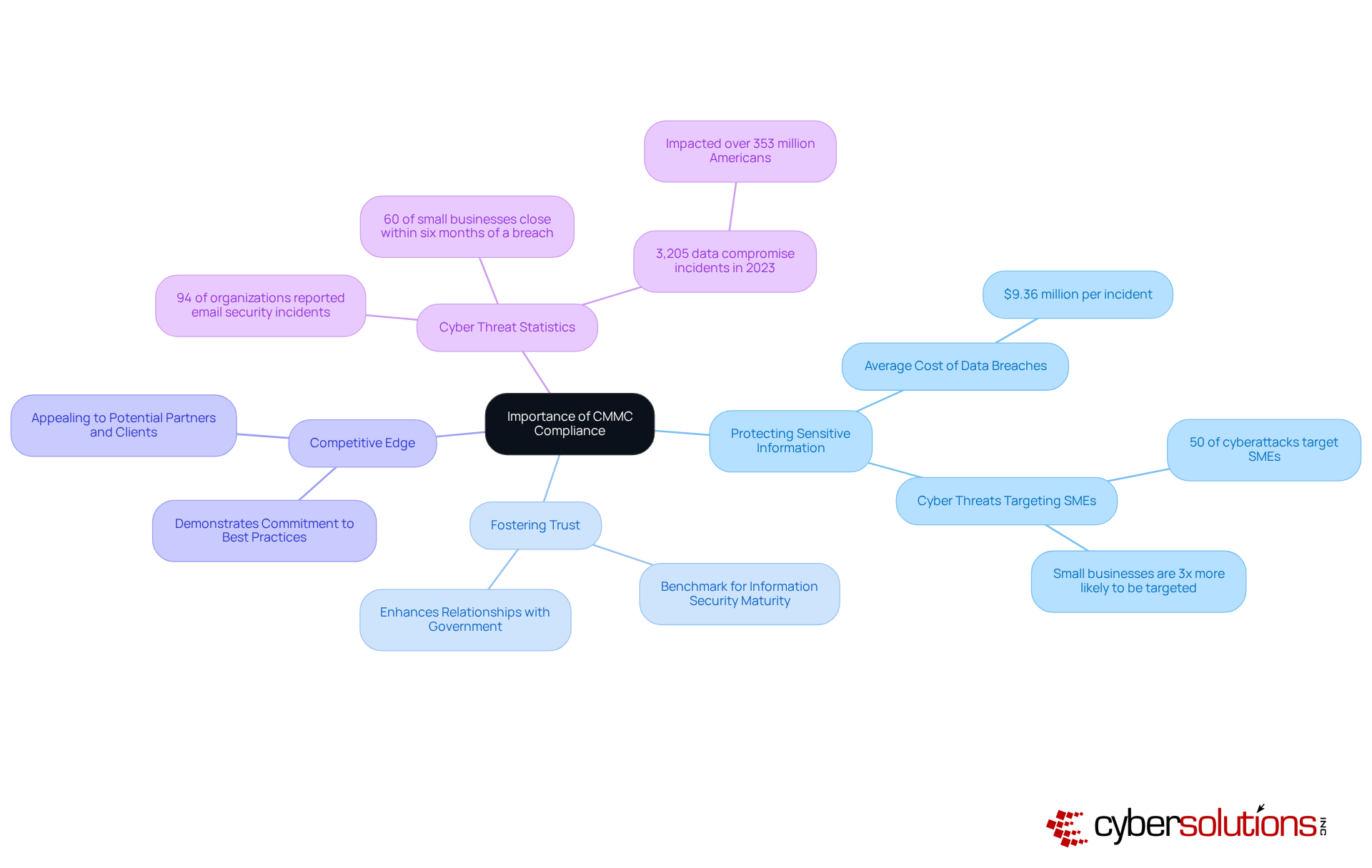
Meeting the required standards is not just important; it’s essential for entities looking to collaborate with the Department of Defense (DoD). Why? Because it ensures their capability to protect sensitive information against ever-evolving cyber threats. The CMMC compliance definition goes beyond mere contractual obligations; it establishes a benchmark for information security maturity, fostering trust between contractors and the government. By adhering to established guidelines, companies can significantly diminish the risk of data breaches, which, according to recent data, can cost American enterprises an average of $9.36 million per incident. This staggering figure underscores the critical need for robust online security practices, especially considering that small businesses are three times more likely to be targeted by cybercriminals than their larger counterparts.
Moreover, adhering to cybersecurity standards enhances a company’s competitive edge. It demonstrates a commitment to best practices in cybersecurity, making organizations more appealing to potential partners and clients. In a landscape where 94% of organizations reported email security incidents in the past year, this commitment is more than just a checkbox; it’s a strategic advantage. In an age marked by increasingly sophisticated cyber threats, adhering to the CMMC compliance definition is not merely a regulatory requirement; it’s a strategic necessity for safeguarding national security and ensuring long-term operational sustainability. Organizations that embrace the CMMC compliance definition and cybersecurity maturity model standards are better equipped to navigate the complexities of cybersecurity, ultimately leading to greater resilience and trust in their operations.
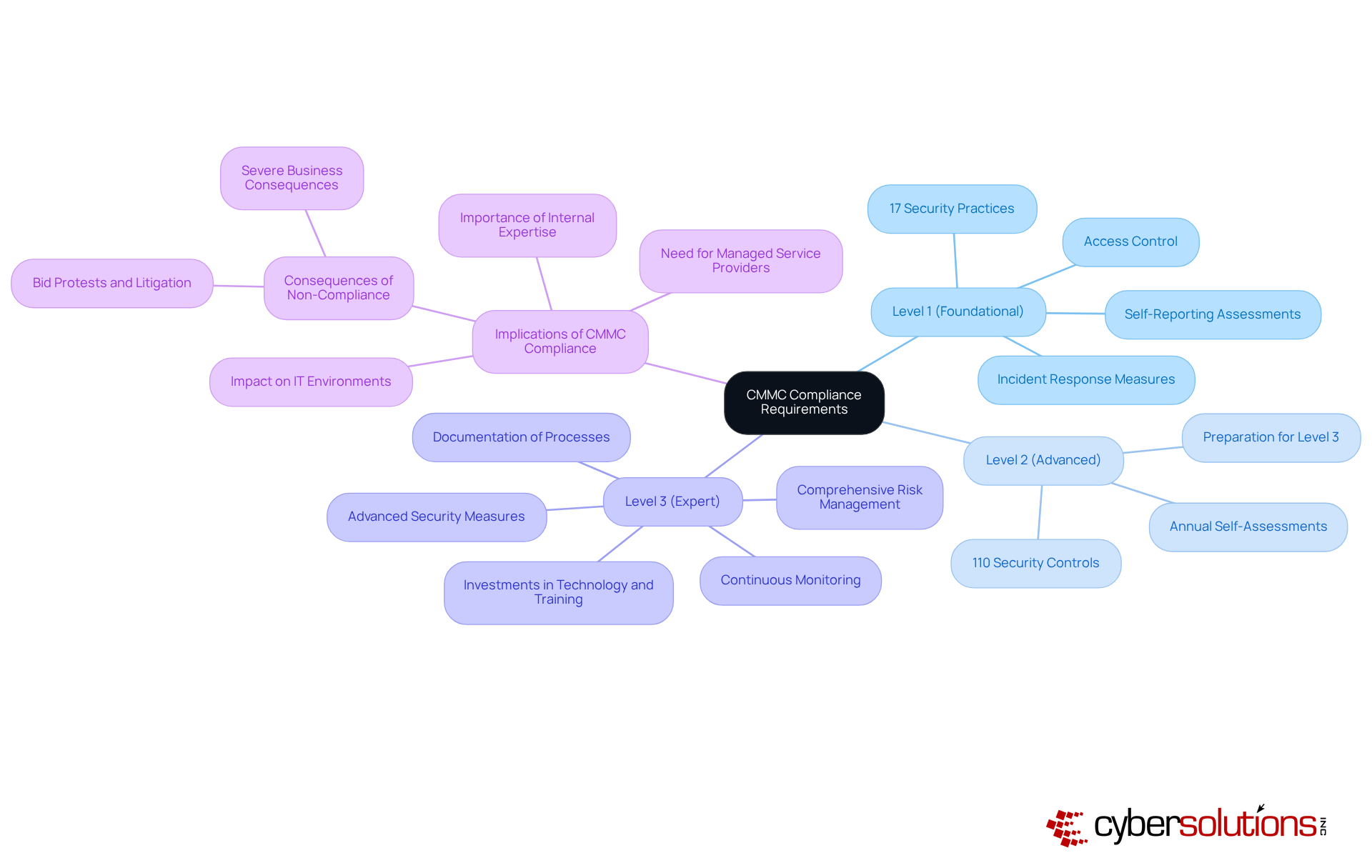
The CMMC compliance definition is essential for safeguarding sensitive information in federal contracting, organized into three distinct levels, each with specific requirements.
Level 1 (Foundational): This entry-level tier focuses on basic cyber hygiene practices crucial for protecting Federal Contract Information (FCI). Organizations must implement 17 security practices, including access control and fundamental incident response measures. Compliance at this level is vital; companies may need to pass assessments even through self-reporting, especially in the event of a data breach.
Level 2 (Advanced): Targeting entities managing Controlled Unclassified Information (CUI), Level 2 mandates the execution of all 110 security controls outlined in NIST SP 800-171. This level acts as a critical transitional phase, preparing entities for the more stringent requirements of Level 3. Companies are required to conduct annual self-assessments to ensure adherence to these controls, which are essential for maintaining a competitive edge in defense contracting.
Level 3 (Expert): The highest tier, Level 3, requires organizations to implement advanced security measures and demonstrate a comprehensive understanding of risk management. This includes rigorous security protocols and continuous monitoring to effectively protect CUI. Achieving Level 3 compliance necessitates a thorough evaluation of existing cybersecurity practices, meticulous documentation of processes, and potential investments in technology and training.
Organizations aiming for compliance across these levels must brace for significant changes in their IT environments, including the integration of managed service providers or cloud solutions to meet evolving federal security requirements. As the urgency for cybersecurity maturity model certification increases, understanding the CMMC compliance definition and its implications is crucial for maintaining contractor status and mitigating risks associated with non-compliance.
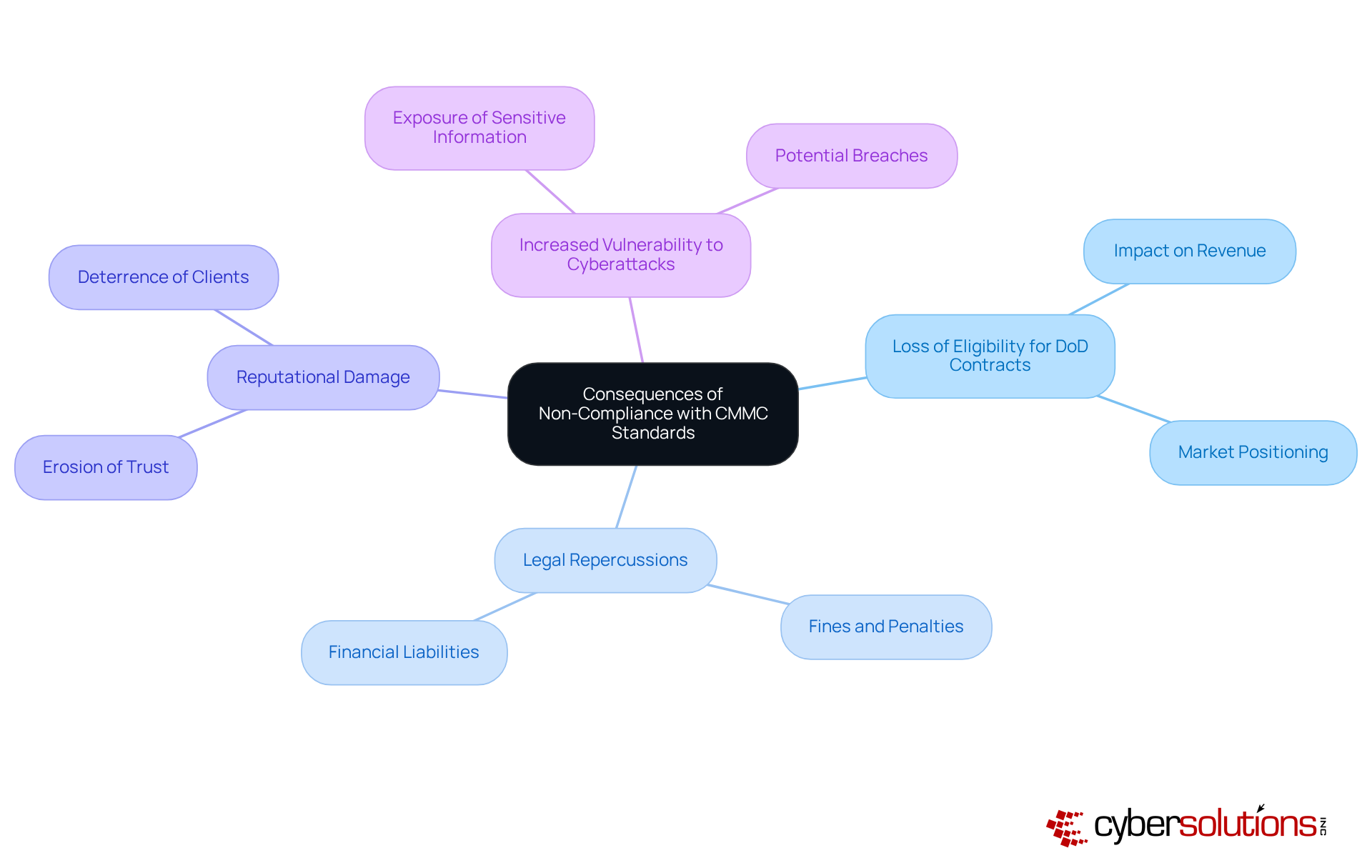
Failure to adhere to the CMMC compliance definition poses significant risks for organizations, especially in the defense contracting sector. The most critical consequence? The potential loss of eligibility to bid on or retain Department of Defense (DoD) contracts. This can drastically impact revenue streams and market positioning. With nearly 80,000 firms requiring certification and only about 70 authorized assessors available, many companies are facing delays and increased costs, jeopardizing their contracts.
Legal repercussions are another pressing concern. Companies may incur fines and penalties for misrepresenting their adherence status, leading to substantial financial liabilities. Moreover, the reputational damage from non-compliance can deter prospective clients and partners, eroding trust and credibility in the marketplace. Inadequate security measures linked to non-compliance also heighten vulnerability to cyberattacks, exposing sensitive information to potential breaches. Alarmingly, only around 200 companies have been evaluated by approved external entities for adherence, underscoring the urgency for organizations to prioritize their security initiatives.
Application allowlisting is vital in this context. It proactively prevents malware and unauthorized software from executing, thereby reducing vulnerabilities and helping businesses meet compliance requirements. Key features of application allowlisting, such as centralized management and continuous monitoring, enhance security by ensuring that only approved applications can run, further safeguarding operations.
Given these high stakes and the expectation of increased enforcement of cybersecurity regulations into 2026, it is imperative for organizations to grasp the CMMC compliance definition to achieve certification. This is essential not only to protect their operations but also to maintain their competitive edge.
Understanding CMMC compliance is not just important; it’s essential for organizations involved in defense contracting. This framework, initiated by the U.S. Department of Defense, is a direct response to escalating cybersecurity threats. It underscores the necessity for companies to adopt robust security practices to remain eligible for government contracts.
CMMC compliance is structured into levels, from foundational to expert, each dictating specific security requirements. The stakes are high: non-compliance can lead to significant financial losses, legal issues, and damage to reputation. Embracing these standards not only protects sensitive data but also strengthens an organization’s competitive edge in the marketplace.
The importance of CMMC compliance transcends mere regulatory adherence; it is a strategic necessity for organizations aiming to succeed in a complex cybersecurity landscape. Companies must actively engage with compliance initiatives, utilizing available resources and expertise to navigate evolving requirements effectively. By doing so, they not only protect their operations but also enhance the overall security of national defense, fostering trust and resilience in their business practices.
What is CMMC compliance?
CMMC compliance refers to the Cybersecurity Maturity Model Certification, an initiative by the U.S. Department of Defense aimed at improving the cybersecurity posture of organizations that handle Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
Why was the CMMC framework introduced?
The CMMC framework was introduced to address escalating cybersecurity threats and to ensure that contractors implement robust security protocols to protect sensitive data.
What are the key components of the CMMC framework?
Key components of the CMMC framework include application allowlisting, which prevents malware and unauthorized software from executing, and adherence to various information security standards and best practices, such as those from NIST SP 800-171.
When will CMMC compliance become mandatory for DoD contractors?
CMMC compliance will become mandatory for all DoD contractors starting November 10, 2025.
What are the consequences of non-compliance with CMMC standards?
Non-compliance with CMMC standards could jeopardize contract eligibility and disrupt operational continuity for organizations.
What is the full compliance phase for CMMC?
The full compliance phase for CMMC will be in effect by November 10, 2028.
How can organizations prepare for CMMC compliance?
Organizations can prepare for CMMC compliance by understanding the requirements, enhancing their cybersecurity frameworks, and seeking assistance from service providers like Cyber Solutions.
What services does Cyber Solutions offer to assist with CMMC compliance?
Cyber Solutions offers Compliance as a Service (CaaS), which includes assessments, policy creation, monitoring, and audit readiness to help organizations meet regulatory requirements.