
In today’s world, where cyber threats are more prevalent than ever, the onus of protecting an organization’s digital assets increasingly rests on the shoulders of C-suite leaders. The evolving landscape of information security demands a keen understanding of essential security services, which are crucial for maintaining operational integrity and ensuring compliance with regulatory standards. This article explores ten vital security services that not only bolster an organization’s defenses but also empower executives to navigate the complexities of modern cybersecurity.
Are leaders truly prepared to confront the challenges posed by the ever-changing threat landscape, or is there a critical gap that needs addressing?
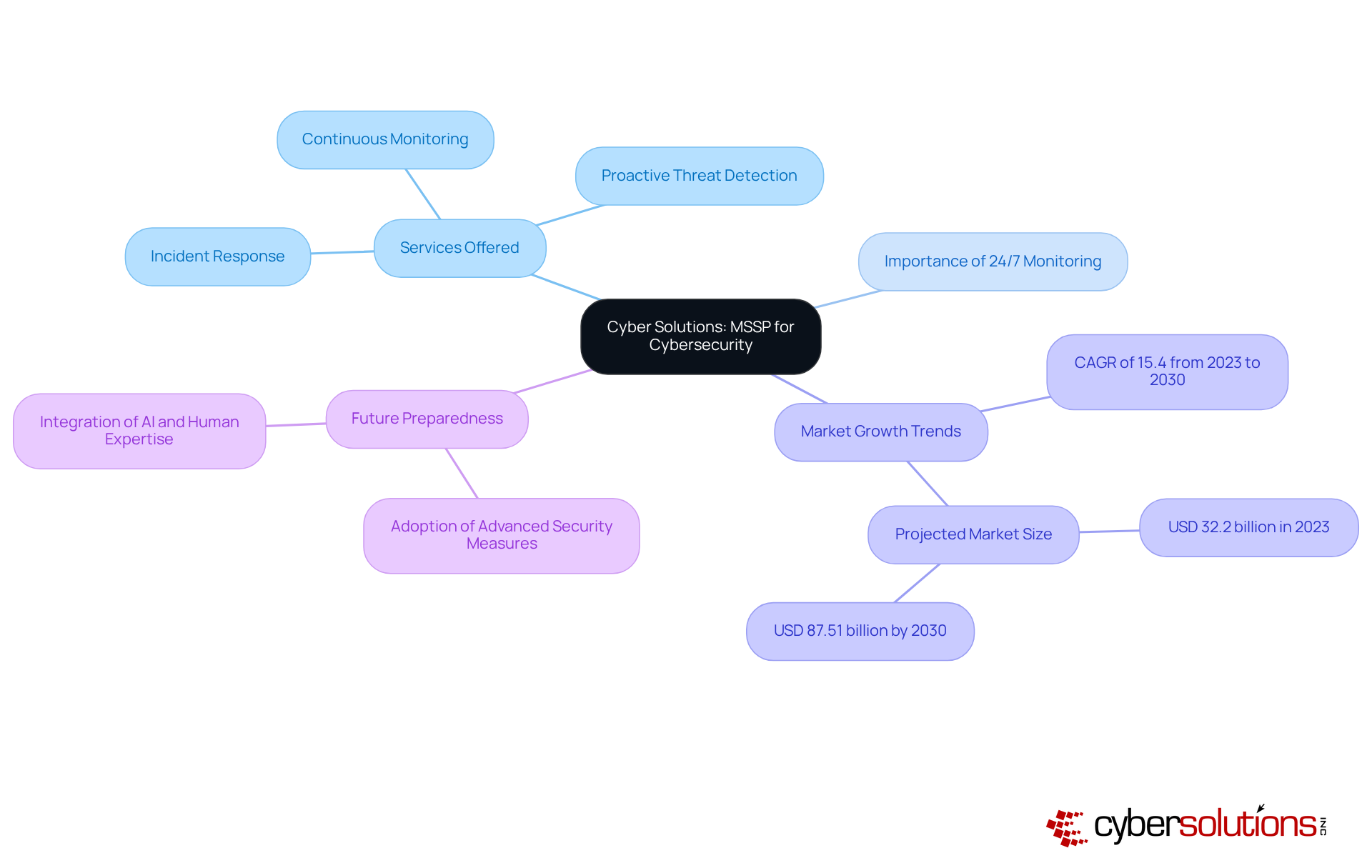
Cybersecurity is no longer just an IT concern; it’s a fundamental aspect of operational integrity for organizations across all sectors. As cyber threats evolve, the need for robust security measures has never been more pressing. Cyber Solutions Inc. stands at the forefront as a leading Managed Security Service Provider (MSSP), offering a comprehensive suite of services designed to fortify organizations against the ever-changing landscape of cyber risks.
With cutting-edge technologies and expert insights, Cyber Solutions delivers continuous 24/7 monitoring, proactive threat detection, and rapid incident response capabilities. This holistic approach not only safeguards sensitive data but also ensures compliance with stringent regulatory requirements. For C-suite leaders committed to effective risk management and operational resilience, Cyber Solutions is an indispensable ally.
The significance of 24/7 monitoring and alerts cannot be overstated; it is a critical line of defense against cyberattacks. Research indicates that companies leveraging managed protection services are significantly better equipped to mitigate risks. By 2025, a substantial percentage of organizations are expected to adopt these services, reflecting a growing recognition of the necessity for expert oversight in cybersecurity.
Recent trends underscore the urgency for businesses to adopt advanced protective measures. The global managed protection services market is projected to grow at a compound annual growth rate (CAGR) of 15.4% from 2023 to 2030, driven by escalating cyber threats and the increasing demand for sophisticated security solutions. C-suite leaders must remain vigilant and informed about these developments to navigate the complexities of modern cybersecurity effectively.
In conclusion, as the cyber threat landscape continues to evolve, organizations must prioritize their cybersecurity strategies. Cyber Solutions Inc. offers the expertise and resources necessary to not only protect against current threats but also to prepare for future challenges. Are you ready to take the next step in securing your organization?
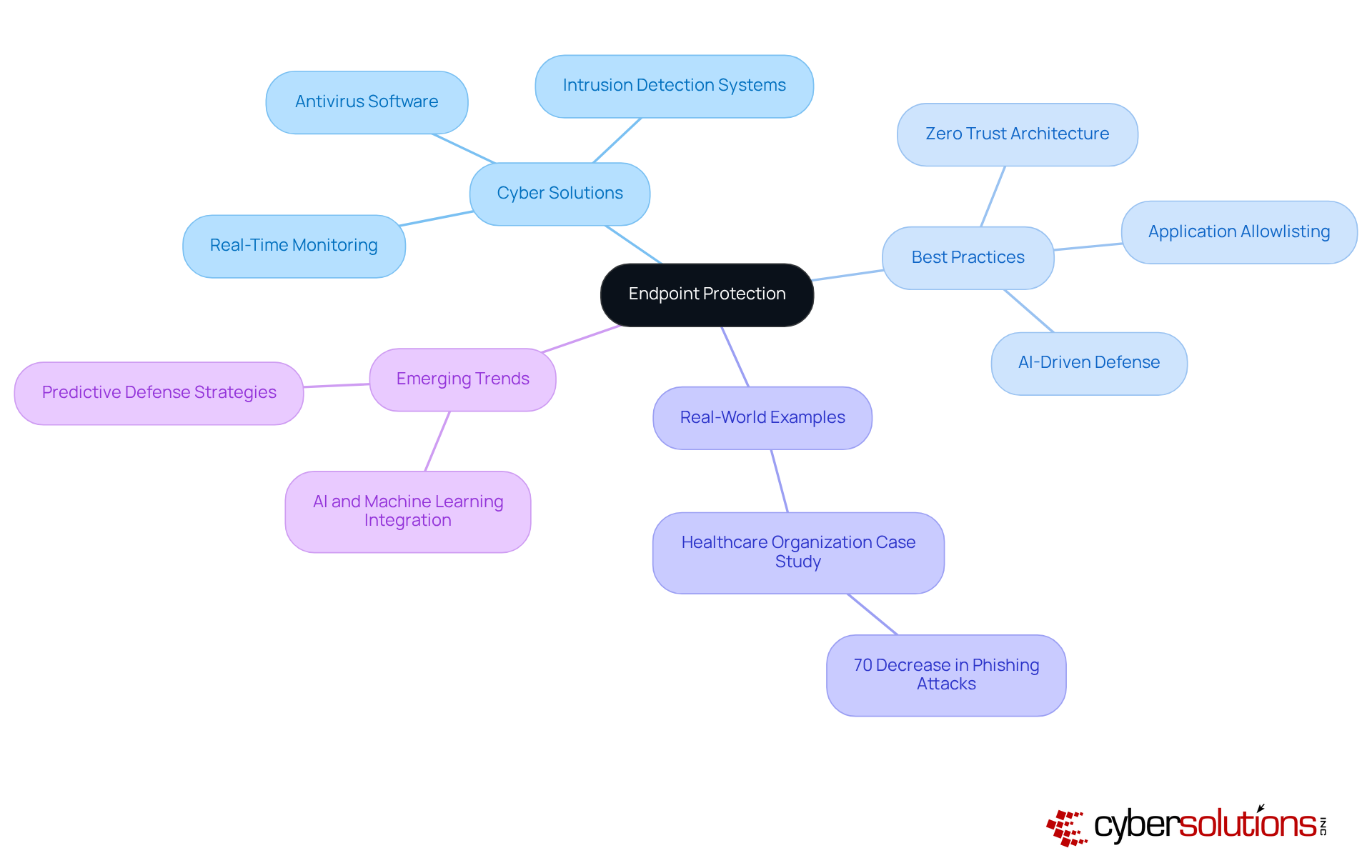
Endpoint protection stands as a cornerstone of modern cybersecurity, particularly vital for safeguarding devices like laptops, smartphones, and tablets that connect to corporate networks. As we look ahead to 2025, the landscape of cyber risks targeting endpoint devices has evolved dramatically, with sophisticated attacks increasingly exploiting vulnerabilities. Cyber Solutions offers advanced endpoint protection solutions, including antivirus software, intrusion detection systems, and real-time monitoring, which are crucial in mitigating these risks.
Current best practices emphasize a multi-layered approach to endpoint protection. This includes implementing Zero Trust architectures, which enforce strict access controls and continuous verification of users and devices. A key component of this strategy is application allowlisting, which proactively prevents unauthorized or malicious applications from executing. This approach not only reduces the attack surface and minimizes vulnerabilities but also ensures compliance with regulatory standards such as HIPAA, PCI-DSS, and GDPR by enforcing strict control over software usage.
Organizations can easily manage and update allowlists across all devices from a centralized dashboard, streamlining control and policy enforcement. Furthermore, organizations are adopting AI-driven defense posture management to provide continuous risk evaluation and automated remediation, ensuring that endpoint protections adapt to emerging threats.
Real-world examples illustrate the effectiveness of robust endpoint security measures. For instance, companies leveraging advanced endpoint detection and response (EDR) solutions have reported significant reductions in breach incidents. In one notable case, a healthcare organization that implemented comprehensive endpoint protection, including application allowlisting, experienced a 70% decrease in successful phishing attacks, safeguarding sensitive patient data and maintaining compliance with regulatory standards.
As cyber risks continue to evolve, securing endpoint devices remains essential. The incorporation of AI and machine learning into endpoint protection solutions is a rising trend, enhancing threat detection capabilities and facilitating proactive defense strategies. By prioritizing endpoint protection and incorporating application allowlisting, organizations can not only protect sensitive information but also ensure business continuity in an increasingly complex digital landscape.
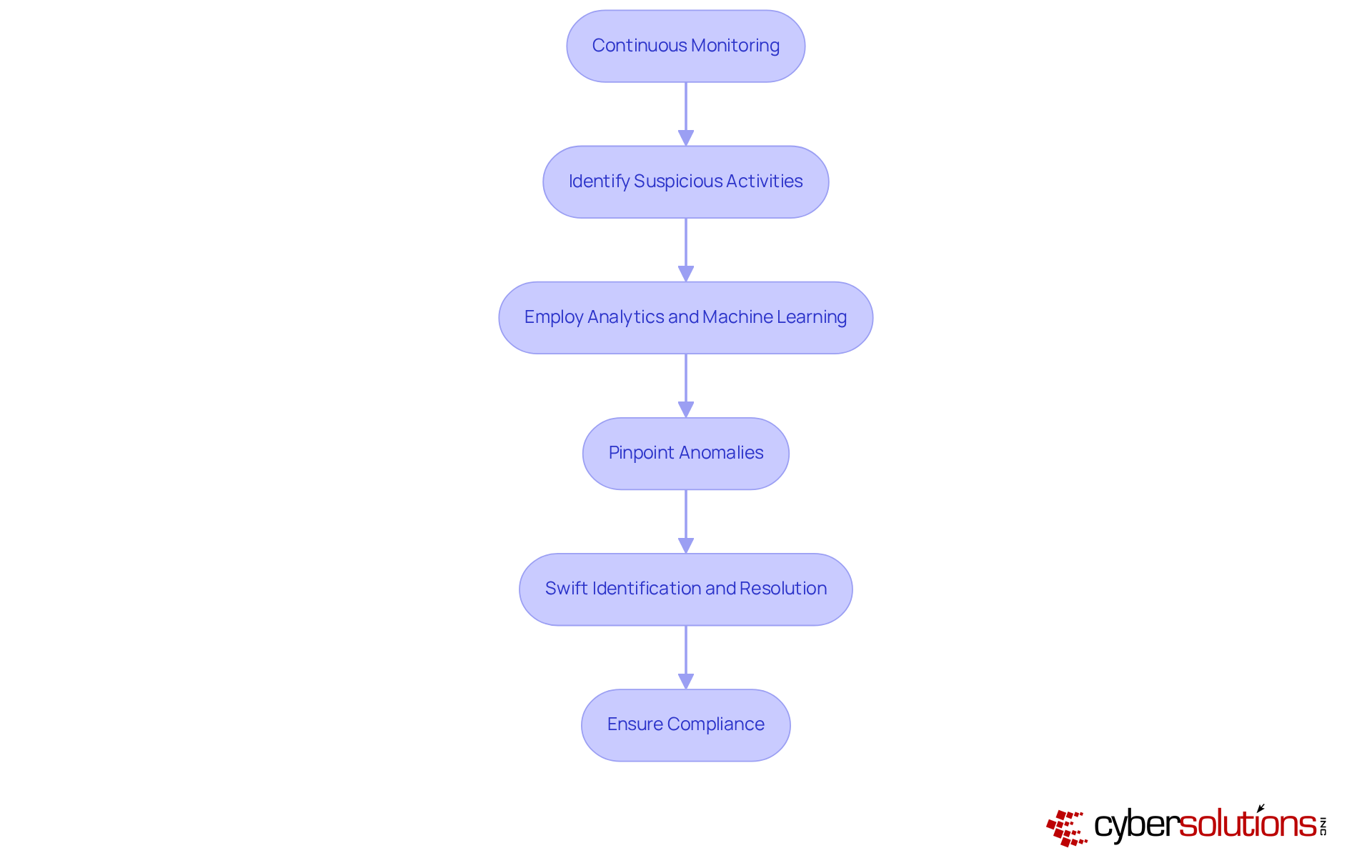
In today's digital landscape, the importance of security services in information security is paramount, especially in healthcare. Threat detection is crucial and is part of the security services in information security, involving the continuous monitoring of networks and systems to identify suspicious activities that may indicate a security breach. Cyber Solutions employs sophisticated analytics and machine learning algorithms to pinpoint anomalies and potential risks in real-time. This proactive approach not only facilitates swift identification and resolution of threats but also ensures compliance with stringent cybersecurity standards necessary for safeguarding Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) by implementing security services in information security.
For healthcare organizations, the implications of failing to address these threats can be severe. By maintaining eligibility for lucrative government contracts through mandatory compliance, organizations can mitigate risks and enhance their security services in information security to prevent costly data breaches. This not only protects the integrity of their operations but also safeguards their reputation in a highly competitive field.
Moreover, our commitment to providing security services in information security, including rapid incident response strategies and 24-hour on-site support, enhances recovery efforts and fosters strong partnerships with clients. This ultimately leads to a more resilient cybersecurity posture, ensuring that organizations are well-equipped to face the evolving challenges of the digital age. Are you ready to strengthen your cybersecurity measures and protect your organization from potential threats?
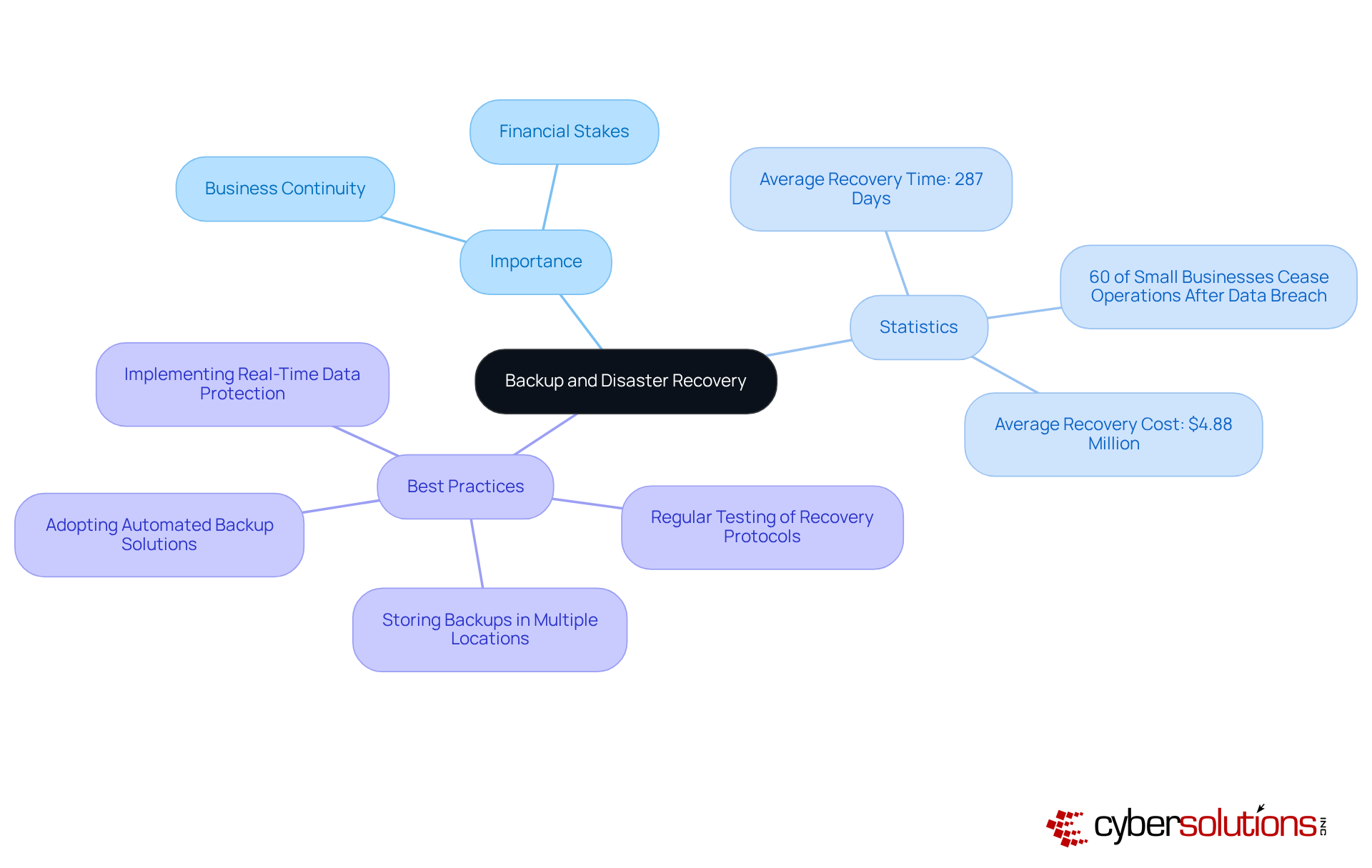
Backup and disaster recovery solutions are not just important; they are essential for ensuring business continuity in the face of rising cyber risks. Cyber Solutions provides a comprehensive suite of backup services, including regular data backups, off-site storage, and rapid recovery options. Coupled with our Managed Security Services (MSSP), which offer 24/7 SOC monitoring and threat response, we stand ready to protect your business.
Did you know that 60% of small businesses cease operations within six months following a data breach? This statistic underscores the urgency of implementing effective recovery strategies. In 2024, the average recovery time after a cyber event was approximately 287 days-a duration that can severely impact operational efficiency and financial stability.
Organizations that adopt robust backup and disaster recovery plans can significantly reduce downtime. For instance, companies facing prolonged data loss incur an average recovery cost of $4.88 million. This highlights the financial stakes involved. Practical examples show that entities successfully bouncing back from cyber events often cite their readiness and ability to recover essential data quickly as crucial factors in minimizing operational interruptions.
Current best practices for disaster recovery planning include:
By prioritizing these strategies, businesses can enhance their resilience against data loss and ensure a swift return to regular operations following an incident. As Sabrina Hafner, Director of Quality and Marketing, aptly states, "In 2025, a smart backup and disaster recovery strategy is not a technical preference-it’s a business essential.
A robust response strategy is essential for businesses aiming to navigate and recover from cyber events effectively. Cyber Solutions provides tailored security services in information security that encompass preparation, detection, containment, and recovery strategies. By implementing a well-defined response strategy, organizations can significantly reduce the average cost of a data breach - often exceeding millions of dollars - while protecting sensitive information and maintaining customer trust. This proactive approach not only secures financial interests but also strengthens the overall security posture.
Real-world examples underscore the importance of swift event management. Organizations that embraced rapid response techniques managed breaches more effectively, minimizing damage and quickly resuming operations. Cybersecurity experts emphasize that security services in information security, including a structured response process, can mitigate risks and improve recovery times, highlighting the necessity of having a solid plan in place.
Moreover, insights from specialists reveal that organizations with comprehensive crisis management strategies and security services in information security are better equipped to address the complexities of modern cyber threats. Industry leaders stress that the ability to respond swiftly and effectively to incidents is crucial for maintaining operational continuity and protecting against reputational harm. By investing in incident response capabilities, organizations not only bolster their resilience against cyber threats but also demonstrate a commitment to safeguarding their stakeholders' interests.
In today's digital landscape, vulnerability evaluations are essential for identifying weaknesses that cybercriminals may exploit. Cyber Solutions conducts comprehensive assessments to evaluate a firm's security posture and the effectiveness of its security services in information security, pinpointing potential vulnerabilities across systems, applications, and processes. Notably, organizations that regularly perform these evaluations have reported a significant decrease in successful cyberattacks, underscoring the effectiveness of proactive security measures.
By addressing vulnerabilities before they can be exploited, businesses can dramatically reduce their risk of cyber incidents and strengthen their overall security framework. This proactive strategy not only protects financial assets but also enhances compliance with regulatory standards, ensuring that companies utilize security services in information security to remain resilient against the ever-evolving cyber threats.
Are you prepared to safeguard your organization? With Cyber Solutions, you can take decisive action to fortify your defenses and navigate the complexities of cybersecurity with confidence.
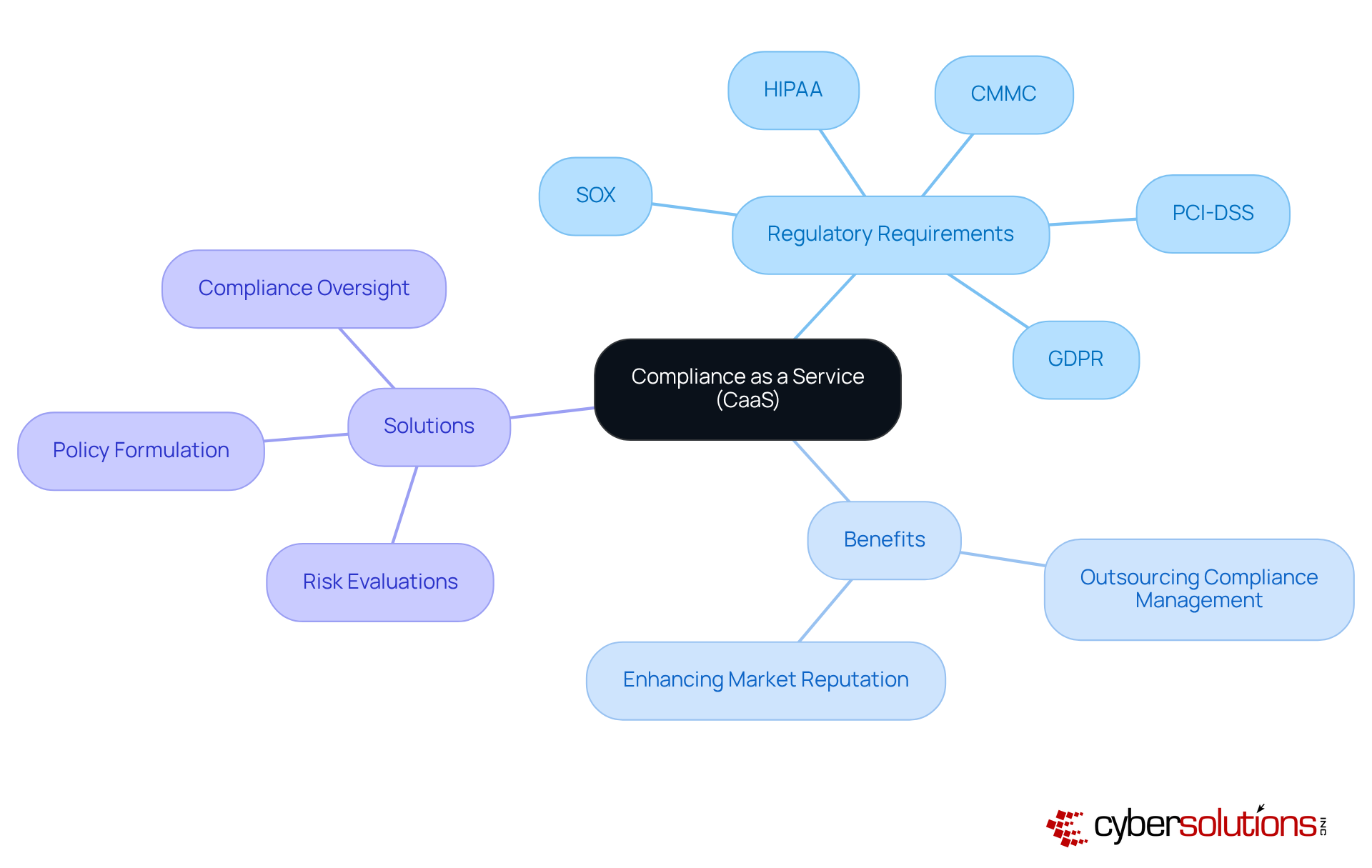
Compliance as a Service (CaaS) is essential for organizations navigating the intricate landscape of regulatory requirements. In today’s world, where regulations like HIPAA, PCI-DSS, CMMC, SOX, and GDPR are ever-present, Cyber Solutions stands out by offering comprehensive CaaS that not only helps businesses meet these critical standards but also protects them from potential penalties.
By outsourcing compliance management, companies can concentrate on their core operations while simultaneously enhancing their market reputation. Our solutions include:
This strategic approach is particularly advantageous for small and medium-sized businesses, granting them access to enterprise-level compliance expertise without the hefty costs of maintaining in-house staff.
In a climate where regulatory standards are constantly evolving, our CaaS solutions simplify the compliance process, allowing entities to stay aligned with current and future regulations. Are you ready to elevate your compliance strategy and safeguard your organization against regulatory challenges?
In today's digital landscape, cybersecurity is not just a necessity; it's a critical component of any organization's defense strategy. Penetration testing serves as a vital method for proactively identifying vulnerabilities within a company's security framework. By simulating attacks, Cyber Solutions assesses the effectiveness of current security measures and highlights areas that require improvement.
Regular penetration tests do more than just fortify defenses against cyber threats; they ensure that organizations are prepared to respond effectively to potential attacks, safeguarding their financial interests. Did you know that companies conducting penetration tests can uncover an average of 5.33 vulnerabilities per minute? This statistic underscores the importance of these assessments in maintaining robust security.
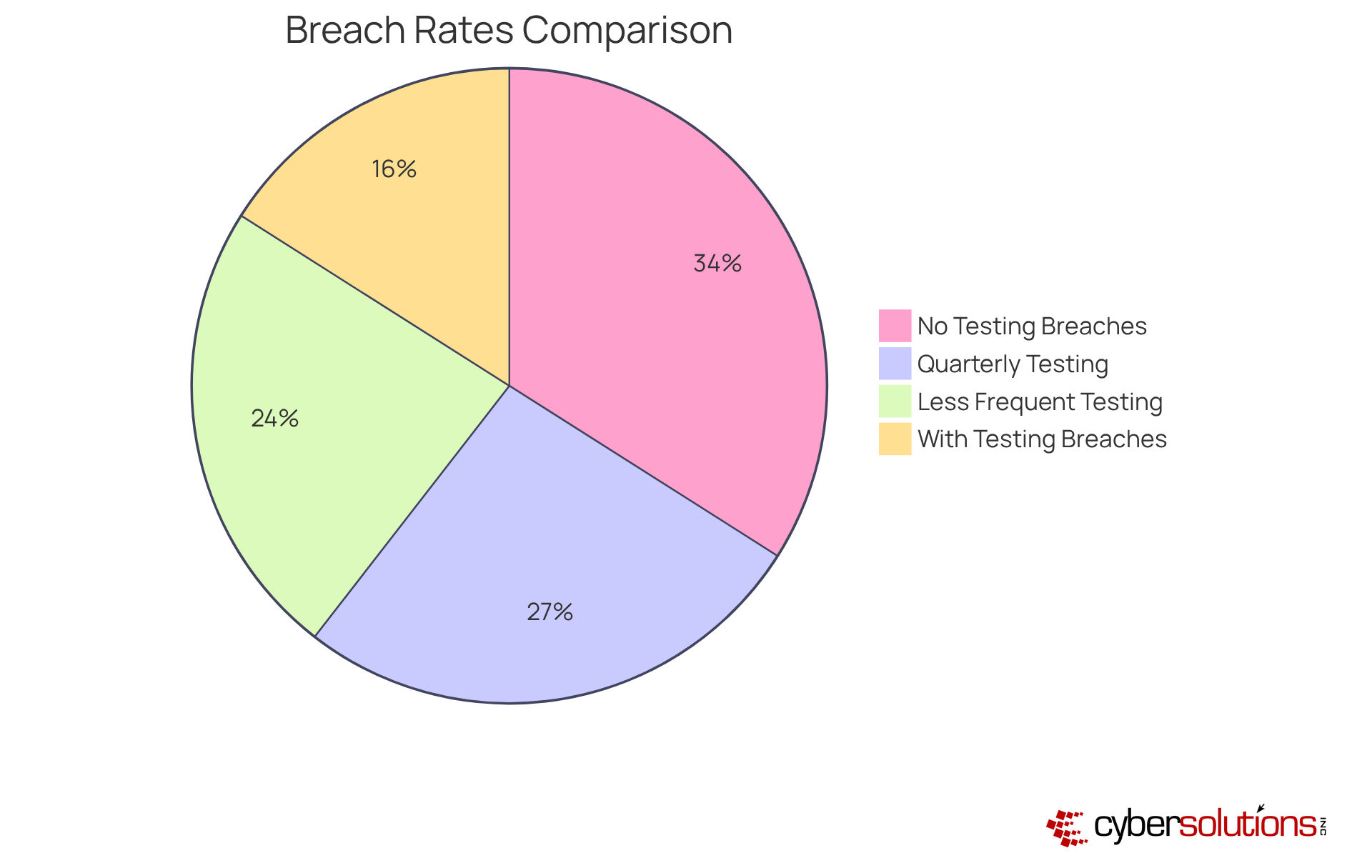
Moreover, a study reveals that 68% of organizations that experienced breaches had not conducted a penetration test in the year prior to the incident. This alarming figure highlights the critical need for regular evaluations. Real-world examples further illustrate this point: organizations that engage in frequent simulated attacks have significantly reduced their breach rates. In fact, those testing quarterly experience a 53% lower breach rate compared to those who test less frequently.
This proactive approach not only enhances security posture but also fosters trust with customers and stakeholders. In essence, penetration testing is an indispensable element of security services in information security, forming a comprehensive cybersecurity strategy that ensures organizations remain resilient in the face of evolving threats.
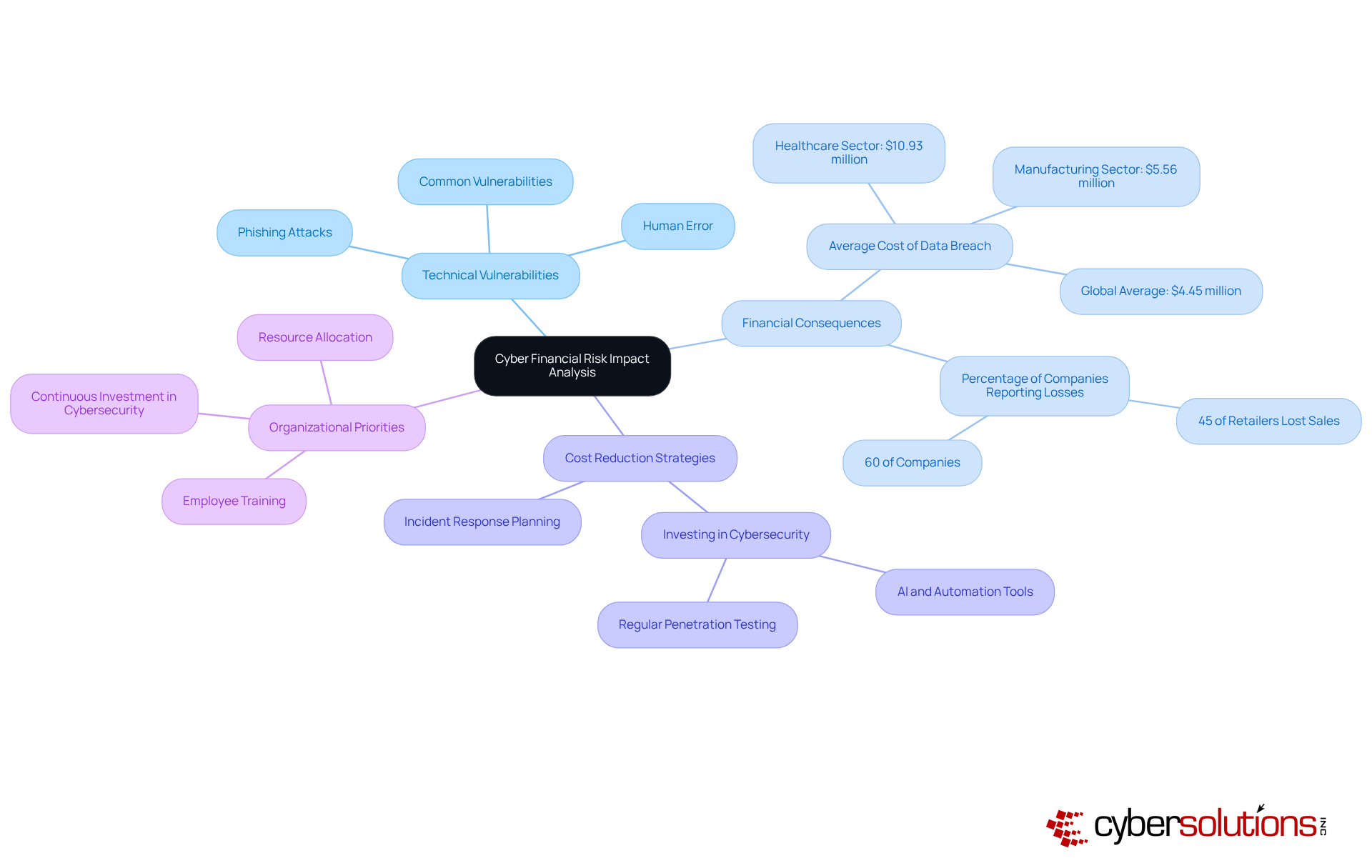
Cyber Financial Risk Impact Analysis stands as a critical service that connects technical vulnerabilities with their financial consequences. In today’s landscape, where cyber threats loom large, understanding these risks is paramount. By quantifying potential costs associated with cyber incidents, Cyber Solutions empowers organizations to make informed decisions regarding their cybersecurity investments.
This analysis allows businesses to prioritize initiatives based on financial risk, ensuring resources are allocated effectively to mitigate threats. For example, organizations that conduct comprehensive financial risk evaluations can significantly reduce the average cost of a data breach, which currently hovers around $4.45 million globally. By proactively identifying and addressing vulnerabilities, they can safeguard their financial health.
Financial analysts emphasize the necessity of grasping these risks, as a staggering 60% of companies report that cyber incidents lead to substantial financial losses, impacting their overall budget and operational efficiency. By integrating Cyber Financial Risk Impact Analysis into their cybersecurity strategy, companies not only bolster their defense mechanisms but also enhance their security services in information security to protect their profits against the escalating costs of cyber incidents.
In a world where the stakes are high, can your organization afford to overlook the financial implications of cyber threats?
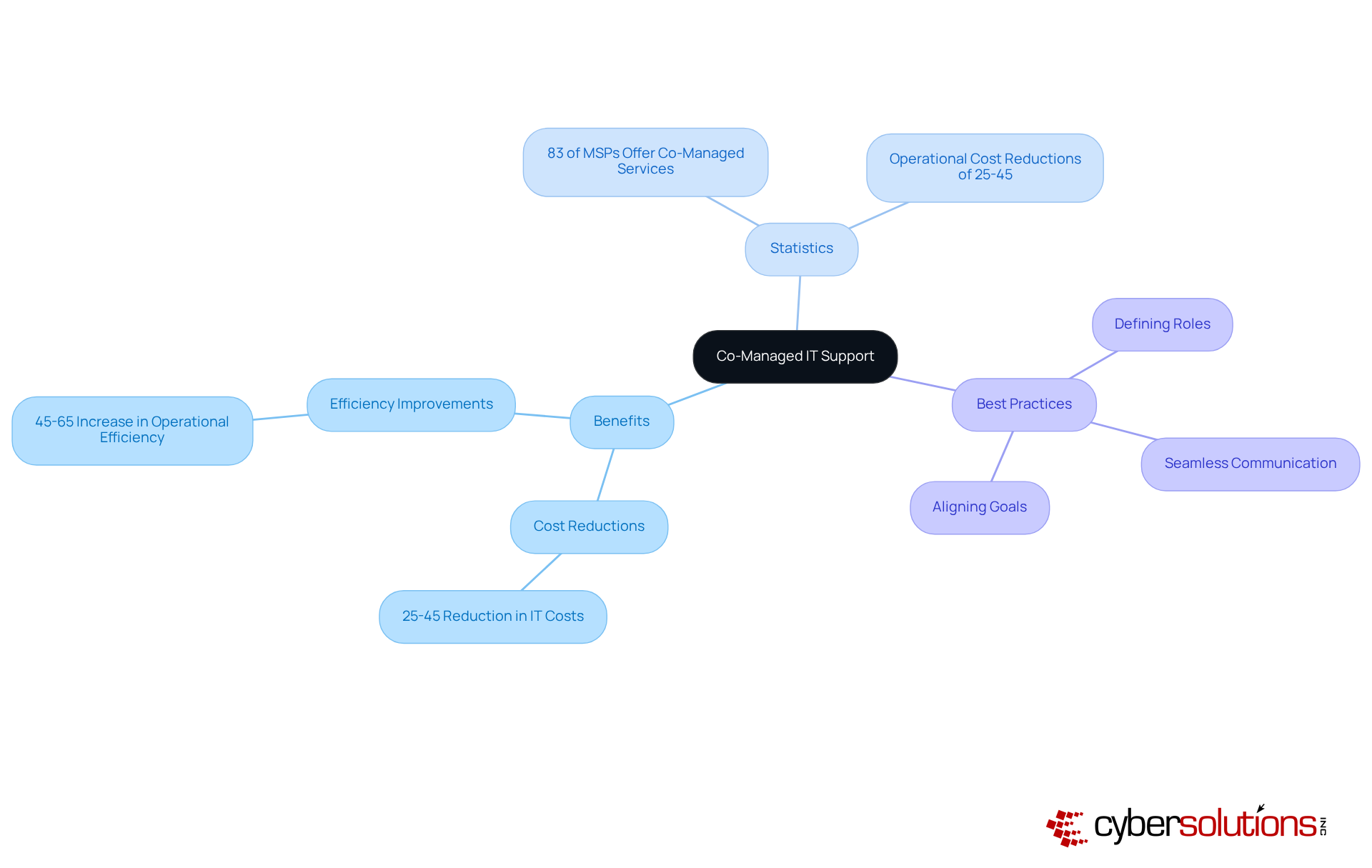
Co-managed IT support has become a crucial strategy for companies looking to enhance their cybersecurity capabilities by utilizing security services in information security without the financial strain of full-time hires. By partnering with Cyber Solutions, internal IT teams can tap into specialized expertise, advanced resources, and cutting-edge cybersecurity tools. This collaborative approach not only allows organizations to maintain control over their IT operations but also significantly strengthens their security services in information security against ever-evolving cyber threats.
Recent trends reveal that around 83% of managed service providers (MSPs) now offer co-managed IT services, highlighting a growing acknowledgment of its value. Organizations that adopt this model report operational cost reductions of 25-45% while simultaneously boosting efficiency by 45-65%. For example, Crowleys DFK, a leading Irish Chartered Accounting firm, successfully implemented a co-managed IT strategy to enhance its cybersecurity framework and achieve ISO 27001 certification, showcasing the tangible benefits of external collaboration.
To effectively enhance internal teams with external expertise, organizations should focus on:
By embracing these best practices, companies can redistribute IT workloads efficiently, allowing internal staff to concentrate on high-value projects while external partners handle routine tasks. This synergy not only mitigates risks but also positions organizations for long-term success in an increasingly complex digital landscape. Furthermore, adopting a layered recovery approach can bolster incident response capabilities, ensuring a more resilient cybersecurity framework. Organizations are encouraged to assess their current IT strategies and consider co-managed solutions to enhance their security services in information security.
As organizations face an increasingly complex cyber threat landscape, the significance of comprehensive security services is paramount. C-suite leaders must understand that cybersecurity is not just an IT issue; it’s integral to operational integrity and organizational resilience. By prioritizing robust security measures, such as those provided by Cyber Solutions Inc., businesses can significantly bolster their defenses against evolving cyber risks.
The article outlines ten essential security services critical for effective information security management. These include:
Each of these elements plays a vital role in safeguarding sensitive information and ensuring business continuity. Moreover, proactive strategies like vulnerability assessments and penetration testing are crucial for identifying weaknesses before they can be exploited. Backup and disaster recovery solutions are indispensable for maintaining operational stability in the event of a cyber incident.
In a landscape where cyber threats are not just probable but inevitable, organizations are urged to take decisive action. Embracing these essential security services is not merely a recommendation; it is a necessity for protecting financial assets, maintaining compliance, and ensuring long-term success. C-suite leaders must critically evaluate their current cybersecurity strategies and consider investing in comprehensive solutions that address both present and future challenges. The time to act is now-secure your organization and foster a resilient cybersecurity posture that can withstand the tests of an unpredictable digital landscape.
What is Cyber Solutions Inc.?
Cyber Solutions Inc. is a leading Managed Security Service Provider (MSSP) that offers a comprehensive suite of cybersecurity services designed to protect organizations from evolving cyber threats.
What services does Cyber Solutions provide?
Cyber Solutions provides continuous 24/7 monitoring, proactive threat detection, rapid incident response capabilities, and advanced endpoint protection, among other services.
Why is 24/7 monitoring important?
24/7 monitoring is crucial as it serves as a critical line of defense against cyberattacks, allowing organizations to quickly identify and respond to potential threats.
What is the projected growth of the managed protection services market?
The global managed protection services market is projected to grow at a compound annual growth rate (CAGR) of 15.4% from 2023 to 2030, driven by increasing cyber threats and demand for sophisticated security solutions.
What is endpoint protection and why is it important?
Endpoint protection safeguards devices such as laptops, smartphones, and tablets that connect to corporate networks. It is essential because these devices are often targeted by sophisticated cyberattacks.
What are some best practices for endpoint protection?
Best practices include implementing a multi-layered approach, using Zero Trust architectures, enforcing application allowlisting, and adopting AI-driven defense posture management.
How does application allowlisting enhance security?
Application allowlisting prevents unauthorized or malicious applications from executing, reducing vulnerabilities and ensuring compliance with regulatory standards.
What role does threat detection play in cybersecurity?
Threat detection involves continuous monitoring of networks to identify suspicious activities that may indicate a security breach, allowing for swift identification and resolution of threats.
How does Cyber Solutions utilize technology for threat detection?
Cyber Solutions employs sophisticated analytics and machine learning algorithms to pinpoint anomalies and potential risks in real-time.
What are the implications of failing to address cybersecurity threats in healthcare?
Failing to address threats can lead to costly data breaches, loss of eligibility for government contracts, and damage to an organization's reputation.
What support does Cyber Solutions offer for incident response?
Cyber Solutions provides rapid incident response strategies and 24-hour on-site support to enhance recovery efforts and strengthen cybersecurity posture.