
In a world where technology is pivotal to business success, C-suite leaders grapple with the formidable task of navigating a complex landscape of IT services. The right computer IT services not only empower organizations to boost operational efficiency but also protect against a growing array of cyber threats. As companies aim to stay ahead of the competition, a pressing question emerges: which essential IT services should executives prioritize to ensure resilience and growth in 2025? This article explores ten critical IT services that can reshape organizational strategies and enhance security in an ever-evolving digital landscape.
In today's fast-paced business environment, the importance of comprehensive computer IT services cannot be overstated. Cyber Solutions Inc. provides 24/7 help desk assistance, a critical component for ensuring operational continuity. This service guarantees that technical issues are resolved swiftly, significantly minimizing downtime and enhancing productivity.
By outsourcing computer IT services, C-suite leaders can concentrate on strategic initiatives, leveraging expert support tailored to their unique organizational needs. The benefits of 24/7 help desk support are substantial; organizations that adopt such services often report improved efficiency and a notable reduction in operational disruptions.
Successful implementations of managed IT support reveal that proactive monitoring and maintenance not only protect against potential issues but also empower businesses to excel in a competitive landscape. Are you ready to elevate your organization's IT strategy and safeguard your operations? Let Cyber Solutions Inc. be your partner in navigating these challenges.
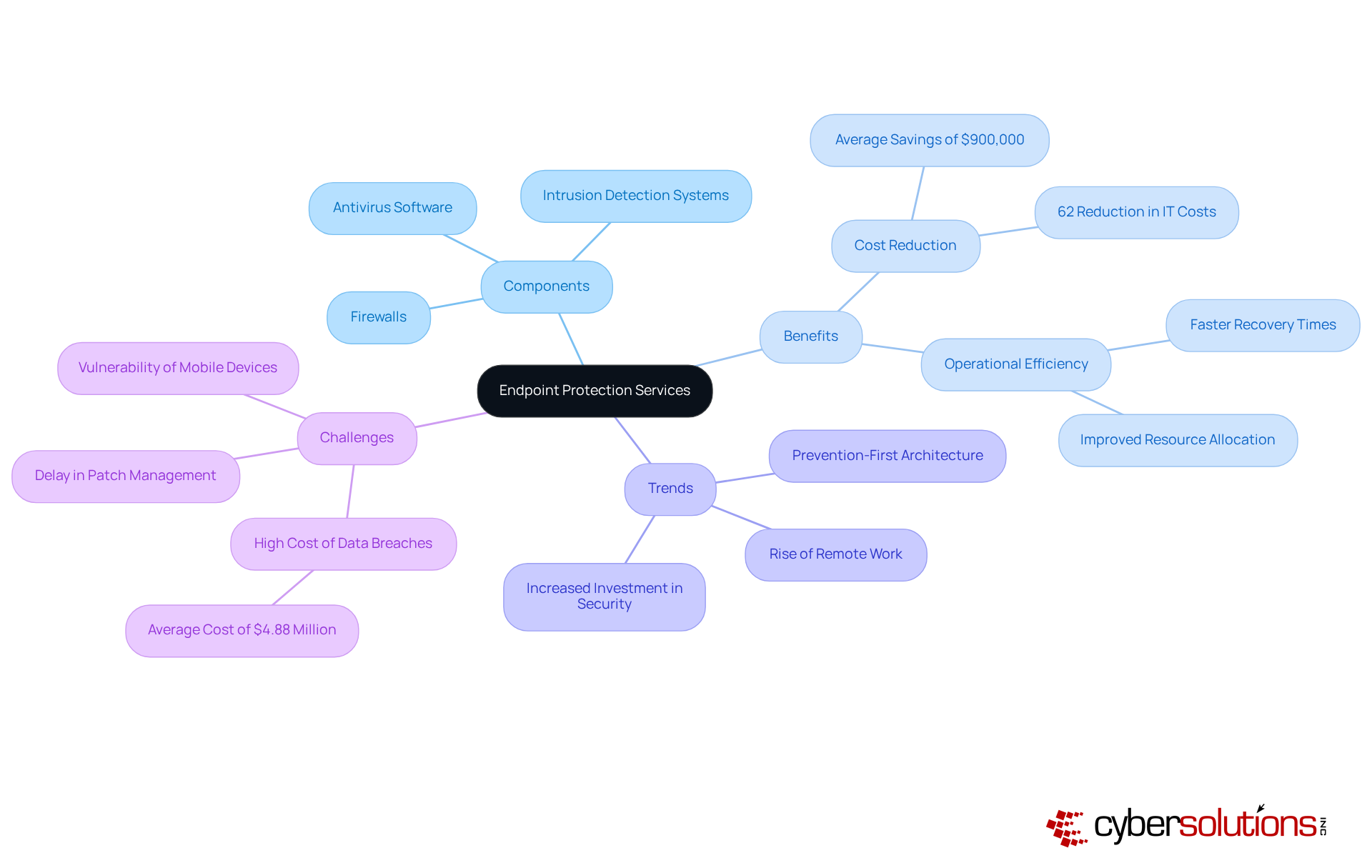
Endpoint Protection Services from Cyber Solutions Inc. represent a vital line of defense in today’s digital landscape. With advanced security measures like antivirus software, firewalls, and intrusion detection systems, these tools are essential for protecting devices against malware, phishing attacks, and other cyber threats. Organizations adopting a comprehensive endpoint protection strategy can significantly reduce the risk of data breaches, which recent studies show can cost an average of approximately $4.88 million per incident. Moreover, businesses that implement secure-by-design endpoints have reported an impressive 62% reduction in IT costs, alongside enhanced operational efficiency.
Cybersecurity specialists emphasize the need to view endpoint protection as a strategic asset rather than merely a cost center. James Millington from IGEL points out that effective endpoint protection can accelerate funding for innovation by improving efficiency and minimizing recovery times from incidents. This perspective is particularly crucial today, as 68% of organizations have experienced at least one successful endpoint attack, underscoring the urgent necessity for robust protective measures.
Current trends reveal a growing acknowledgment of the importance of endpoint protection services, especially with the rise of remote work. Organizations are increasingly investing in solutions that not only defend against immediate threats but also bolster overall resilience. By leveraging advanced technologies and adopting a prevention-first architecture, organizations can ensure their endpoints become a foundation for security and innovation, ultimately fostering a more secure and compliant operational environment.
In today's healthcare landscape, the importance of robust cybersecurity cannot be overstated. Cyber Solutions Inc. offers comprehensive Backup and Disaster Recovery Solutions that not only secure data but also facilitate rapid restoration following any disaster. With regular backups, cloud storage options, and thorough disaster recovery planning, organizations can significantly reduce downtime. In fact, studies reveal that unexpected outages can cost mid-sized companies over $9,000 per minute. This staggering figure underscores the necessity for a proactive approach to disaster recovery, which is not just a technical preference but a critical business imperative.
A well-structured disaster recovery plan enhances organizational continuity by ensuring that vital data is protected and readily accessible. This allows operations to resume swiftly after disruptions, a crucial factor in maintaining trust and efficiency in healthcare services. IT professionals stress the importance of regularly testing and updating recovery plans to identify gaps and ensure effectiveness. Understanding Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) is essential for setting clear goals in disaster recovery efforts.
Cyber Solutions Inc. further strengthens these efforts through its Managed Security Services (MSSP), which include:
For instance, during a recent ransomware attack, Cyber's incident response team swiftly restored 4,500 endpoints, ensuring continuity for healthcare operations. C-Suite leaders must assess their current backup and disaster recovery plans to ensure they are equipped to safeguard organizational resilience and operational integrity. Are you prepared to protect your organization against the ever-evolving cybersecurity threats?

Co-Managed computer IT services from Cyber Solutions Inc. empower organizations to collaborate with external IT experts while retaining control over their internal IT functions. This hybrid model not only enables enterprises to scale their computer IT services according to operational demands but also enhances their overall IT strategy. By merging internal knowledge with external expertise, organizations can significantly improve service delivery and operational efficiency, ultimately maximizing ROI.
The advantages of co-managed computer IT services are evident across various sectors, with companies reporting increased agility and responsiveness to evolving market needs. For instance, organizations leveraging co-managed computer IT services gain access to specialized skills and advanced technologies, including 24/7 IT support and proactive monitoring, without the burden of hiring additional full-time staff. This flexibility is crucial, especially as 62 percent of tech hiring managers indicate a need to expand their teams to support business growth, while 48 percent cite skill gaps in existing staff.
CIOs have observed that adopting a hybrid IT management approach alleviates pressure on internal teams and fosters innovation. As one CIO stated, "The right IT partner doesn’t replace your internal team; it amplifies their efforts and helps them focus on what they do best." By offloading routine tasks to managed service providers (MSPs), internal IT staff can concentrate on strategic initiatives that drive growth. Additionally, the computer IT services provided by Cyber Solutions Inc. help ensure compliance with industry standards like HIPAA and PCI through tailored strategies that address these requirements. This synergy between in-house and external resources ensures that organizations remain competitive in an increasingly complex digital landscape.
Furthermore, Cyber Solutions Inc.'s extensive cybersecurity plan, which incorporates a layered approach to protection, enhances recovery and client collaboration, ensuring that organizations are well-prepared to respond to incidents efficiently. To maximize the benefits of co-managed computer IT services, C-suite leaders should assess their current IT strategy to identify areas where external support could enhance operational efficiency and compliance.

In today's rapidly evolving digital landscape, the importance of robust cybersecurity cannot be overstated. Cyber Solutions Inc. stands at the forefront, offering advanced Threat Detection Services that leverage cutting-edge technology to monitor networks for suspicious activity around the clock. This continuous vigilance ensures that anomalies and potential vulnerabilities are swiftly identified, enabling instant alerts and automated responses to emerging threats.
Such a proactive approach empowers organizations to act quickly, significantly reducing risks and enhancing their protective posture. By safeguarding sensitive information from cyber threats, tailored access controls and restrictions guarantee that only authorized users can access critical systems. As we approach the increasingly dynamic and interconnected threat environment of 2026, the urgency for adopting these technologies becomes paramount.
Consider this: organizations utilizing AI-driven threat detection systems have dramatically cut breach containment times from an average of 322 days to just 214 days. With 67% of entities currently integrating AI into their cybersecurity strategies, it’s clear that AI is proving highly effective in uncovering threats that might otherwise go unnoticed, as confirmed by 70% of cybersecurity experts.
Moreover, our comprehensive firewall and network protection solutions not only bolster safety but also enhance network performance, ultimately boosting employee productivity. A structured response plan is essential for rapid incident management, ensuring that organizations can recover swiftly from potential breaches. In an era where cybersecurity is critical, partnering with Cyber Solutions Inc. is not just a choice; it’s a necessity.
In today's digital landscape, cybersecurity is not just a necessity; it's a critical component of operational integrity for organizations. Cyber Innovations Inc. offers Incident Response Services that ensure your organization is prepared to tackle incidents head-on. With a focus on:
Our dedicated incident response team swiftly identifies, contains, and mitigates threats. This rapid response minimizes damage and restores operations efficiently.
But why is this important? The implications of inadequate incident management can be severe, leading to financial losses and reputational damage. By employing a proactive strategy, Cyber Innovations Inc. not only aids companies in recovering from incidents but also empowers them to learn from these experiences, enhancing their protective measures for the future.
Imagine having a partner that not only responds to threats but also strengthens your overall cybersecurity posture. By acting quickly and leveraging specialized expertise, Cyber Innovations Inc. cultivates strong partnerships with clients, ensuring they are not just reactive but also resilient in the face of evolving cyber threats. Don't wait for an incident to occur; take action now to safeguard your organization.
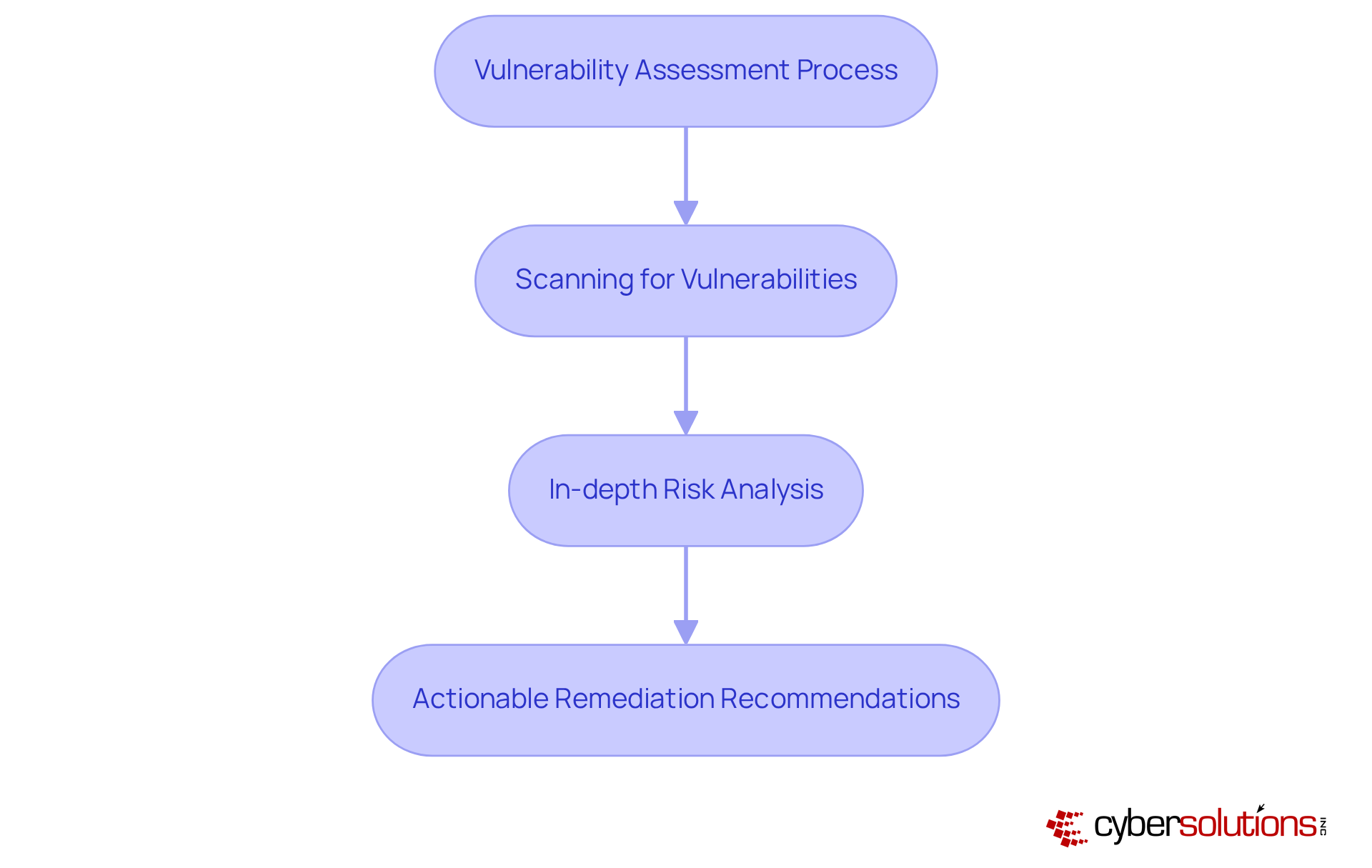
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations handling sensitive data. Cyber Solutions Inc. offers comprehensive Vulnerability Assessment Services designed to uncover potential weaknesses within your IT infrastructure. These assessments include meticulous scanning for vulnerabilities, in-depth risk analysis, and actionable remediation recommendations.
Regular vulnerability evaluations empower organizations to proactively address weaknesses, significantly enhancing their defense posture and ensuring compliance with industry regulations. A recent study by the Ponemon Institute revealed that a staggering 60% of data breaches stem from unpatched vulnerabilities. This statistic underscores the urgent need for ongoing assessments in safeguarding your organization.
Moreover, prioritizing these evaluations not only fortifies defenses against cyber threats but also aligns with compliance mandates such as HIPAA and PCI DSS, which necessitate regular vulnerability assessments to protect sensitive information. By integrating advanced cybersecurity tools like endpoint protection and threat detection into these practices, organizations can effectively mitigate risks and bolster their overall security framework. This proactive approach ensures minimal operational disruption and a robust defense against evolving cyber threats.
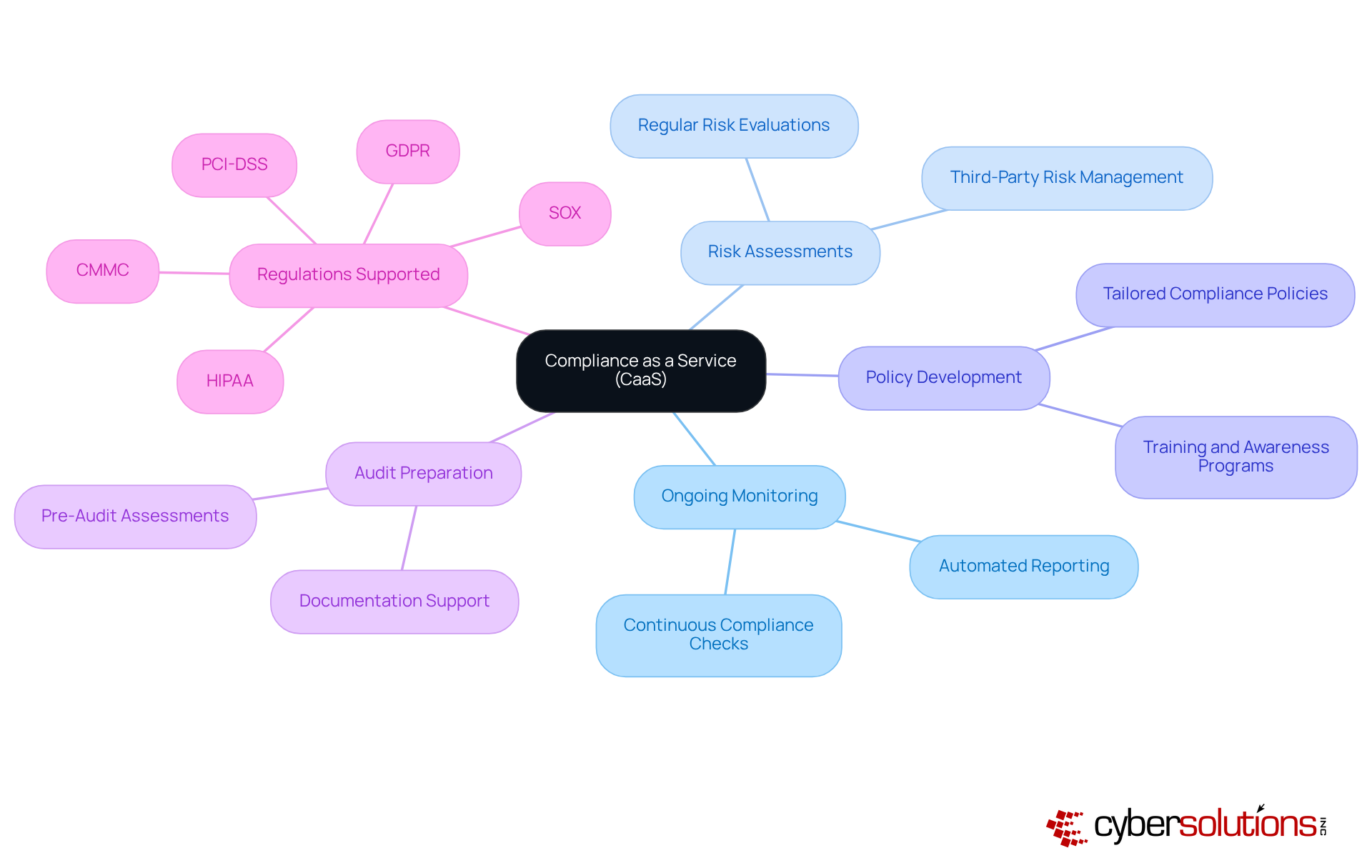
In today's complex regulatory landscape, Compliance as a Service (CaaS) from Cyber Solutions Inc. stands as a vital resource for organizations striving to meet stringent compliance requirements. This comprehensive service not only offers ongoing compliance monitoring and risk assessments but also includes policy development and support for critical regulations such as:
By outsourcing compliance management, companies can significantly reduce the risk of non-compliance and focus on their core operations.
CaaS is particularly advantageous for small and medium-sized businesses, granting them access to enterprise-level compliance expertise without the prohibitive costs of hiring in-house compliance staff. Imagine having a dedicated team of experts ensuring your organization remains compliant with current and future regulatory demands. Our solutions also encompass audit preparation and continuous monitoring, ensuring your entity is always aligned with evolving regulations.
With Cyber Solutions, you can navigate the complexities of compliance with confidence, allowing you to concentrate on what you do best - running your business.
In today's digital landscape, cybersecurity is not just an option; it's a necessity. Penetration testing services from Cyber Solutions Inc. mimic real-world attacks, effectively revealing weaknesses within a company's systems. These assessments are crucial for understanding potential vulnerabilities, enabling organizations to bolster their defenses.
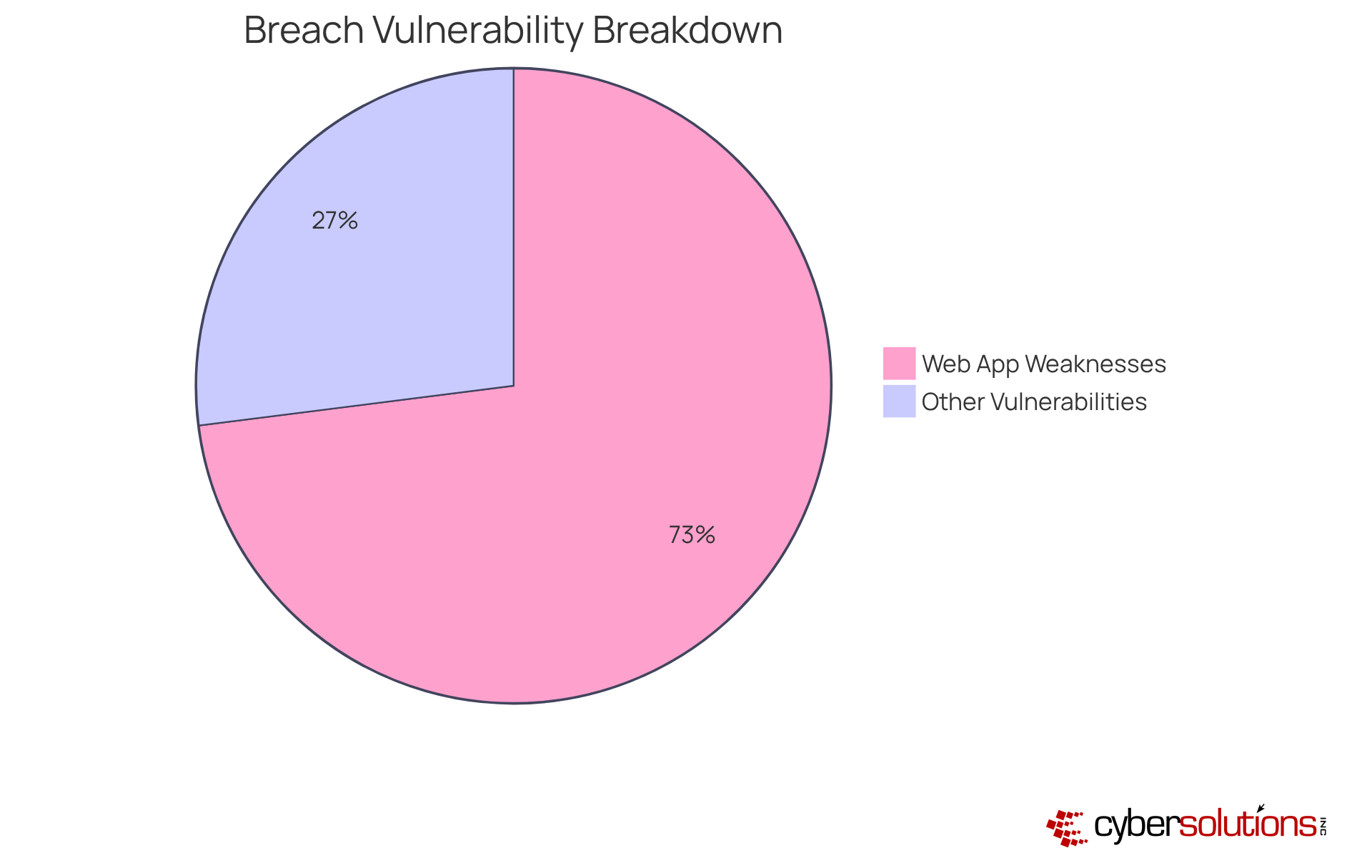
Routine penetration testing is essential. It empowers companies to proactively address vulnerabilities, enhancing their overall security posture. Did you know that 73% of successful data breaches exploit weaknesses in web applications? This statistic underscores the urgent need for thorough testing. Organizations that engage in proactive penetration testing are not only better equipped to face future cybersecurity threats but can also identify and remediate weaknesses before they can be exploited.
Consider the Power School data breach - a stark reminder of how penetration testing could have uncovered critical vulnerabilities, preventing significant data exposure. As the threat landscape continues to evolve, simulating attacks through penetration testing becomes increasingly vital for maintaining robust security measures and ensuring compliance with regulatory frameworks.
In conclusion, investing in penetration testing is not merely a defensive strategy; it's a proactive approach to safeguarding your organization against the ever-growing array of cyber threats.
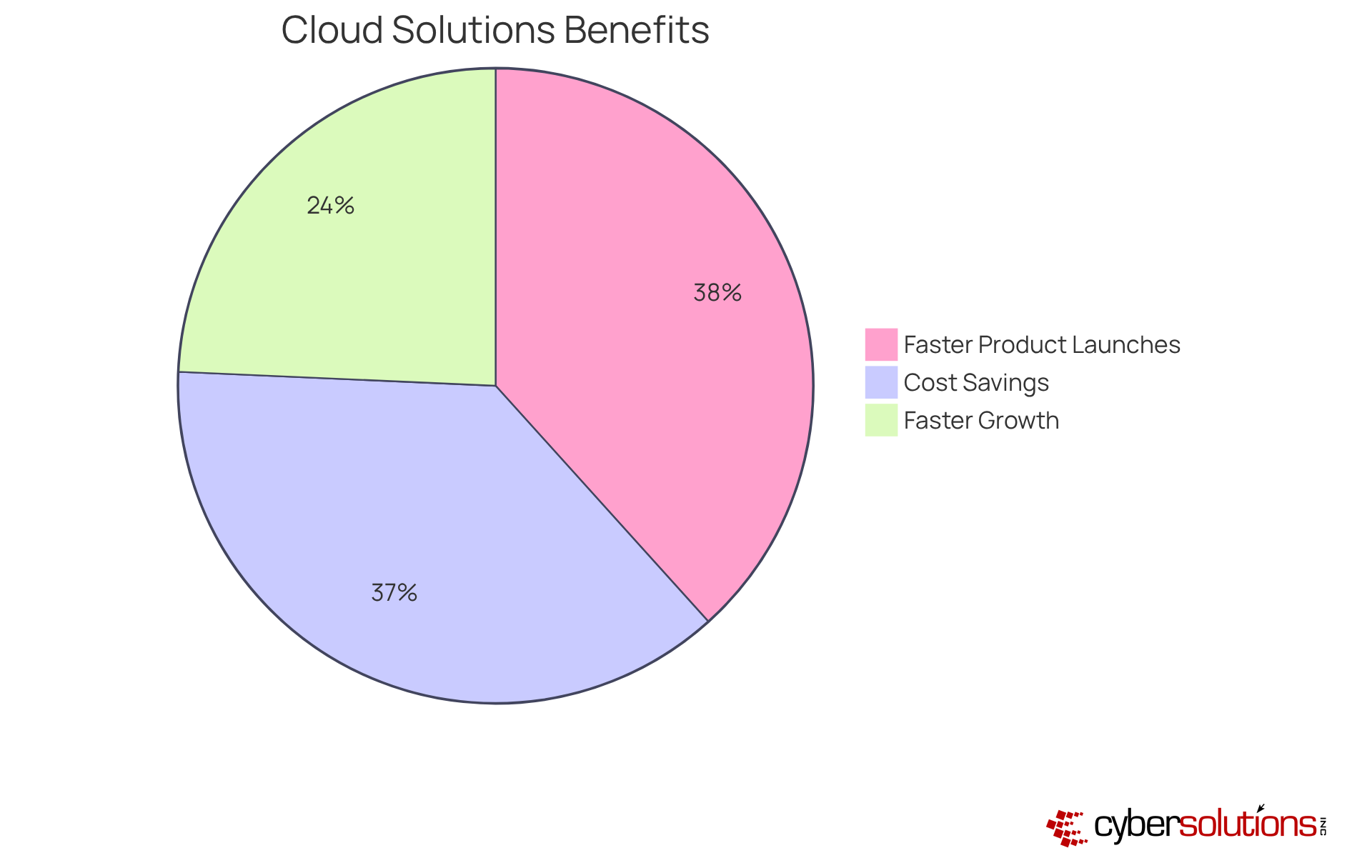
Cyber Solutions Inc. recognizes the critical role of cloud solutions in today’s business landscape. Organizations are increasingly turning to robust cloud offerings to scale operations efficiently, and for good reason. These solutions - spanning cloud storage, computing resources, and collaboration tools - are designed not just to enhance productivity but also to significantly reduce costs. By leveraging cloud technology, businesses can improve agility, streamline operations, and foster innovation, positioning themselves for sustained success.
Moreover, our Compliance as a Service (CaaS) solutions ensure that organizations meet regulatory requirements while utilizing cloud technology. This integration not only boosts operational efficiency but also mitigates risks associated with compliance failures. Consider this:
Such statistics highlight the transformative impact of cloud computing.
IT leaders are increasingly emphasizing that cloud computing has redefined IT departments, turning them into strategic enablers that fuel innovation and optimize operations. This shift allows organizations to respond swiftly to changing market demands, enhancing overall operational efficiency and driving down costs. Real-world examples further illustrate these benefits; for instance, a global manufacturing company saved 40% on IT expenses by migrating its ERP system to the cloud.
As businesses continue to embrace cloud technology, they unlock new opportunities for growth and competitiveness in an increasingly digital landscape. Are you ready to explore how Cyber Solutions can help your organization thrive in this environment?
In today's business landscape, where technology is the backbone of every operation, C-suite leaders must recognize the critical importance of comprehensive IT services to drive organizational success. Cyber Solutions Inc. offers a suite of services that not only enhance operational efficiency but also strengthen cybersecurity, empowering companies to navigate the complexities of modern business with confidence.
This article outlines ten essential IT services, including:
Each service is vital in safeguarding organizational integrity, allowing leaders to concentrate on strategic growth initiatives. From proactive monitoring to incident response, these services enable businesses to minimize risks and bolster resilience against evolving cyber threats.
As organizations look ahead, embracing these IT services transcends a mere tactical decision; it becomes a strategic imperative. By investing in robust IT solutions, C-suite leaders can position their companies for sustained growth and innovation. The time to assess and enhance IT strategies is now-partner with Cyber Solutions Inc. to secure a competitive edge in the ever-evolving digital landscape.
What services does Cyber Solutions Inc. provide for managed IT support?
Cyber Solutions Inc. offers 24/7 help desk assistance, which ensures that technical issues are resolved quickly, minimizing downtime and enhancing productivity.
How does outsourcing IT services benefit C-suite leaders?
By outsourcing IT services, C-suite leaders can focus on strategic initiatives while leveraging expert support tailored to their organization's unique needs, leading to improved efficiency and reduced operational disruptions.
What is the significance of endpoint protection services?
Endpoint Protection Services are essential for defending devices against malware, phishing attacks, and other cyber threats, significantly reducing the risk of data breaches and enhancing operational efficiency.
How can effective endpoint protection impact IT costs?
Organizations that implement secure-by-design endpoints have reported a 62% reduction in IT costs, alongside improved efficiency.
Why is it important to view endpoint protection as a strategic asset?
Viewing endpoint protection as a strategic asset can accelerate funding for innovation by improving efficiency and minimizing recovery times from incidents, which is crucial given the high incidence of endpoint attacks.
What are the key components of Cyber Solutions Inc.'s Backup and Disaster Recovery Solutions?
Their solutions include regular backups, cloud storage options, and thorough disaster recovery planning to secure data and facilitate rapid restoration following disasters.
What is the potential cost of unexpected outages for mid-sized companies?
Unexpected outages can cost mid-sized companies over $9,000 per minute, highlighting the importance of a proactive disaster recovery approach.
What does a well-structured disaster recovery plan ensure?
A well-structured disaster recovery plan ensures that vital data is protected and readily accessible, allowing operations to resume swiftly after disruptions.
What additional services does Cyber Solutions Inc. provide through its Managed Security Services (MSSP)?
Cyber Solutions Inc. offers 24/7 SOC monitoring and rapid incident response strategies as part of its Managed Security Services.
How did Cyber Solutions Inc. respond to a recent ransomware attack?
During a recent ransomware attack, Cyber's incident response team swiftly restored 4,500 endpoints, ensuring continuity for healthcare operations.