In today’s digital landscape, cybersecurity isn’t just a technical issue; it’s a critical business imperative for C-Suite leaders. With the rise in cyber threats, executives must prioritize essential measures to safeguard their organizations. The Cybersecurity Maturity Model Certification (CMMC) outlines crucial controls that can significantly enhance security and ensure compliance.
Consider the implications of neglecting these controls. Access management, incident response plans, and regular audits are not merely recommendations; they are vital components in protecting sensitive data and maintaining regulatory adherence. For healthcare organizations, the stakes are even higher, as breaches can lead to severe financial and reputational damage. How prepared is your organization to face these challenges?
Implementing CMMC controls positions your organization favorably for government contracts while bolstering overall security. By taking proactive steps now, you can mitigate risks and demonstrate your commitment to cybersecurity. Don’t wait for a breach to act—prioritize these essential controls today.
In summary, the landscape of cybersecurity threats is evolving, and C-Suite leaders must adapt accordingly. By focusing on the implementation of CMMC controls, you not only protect your organization but also enhance its credibility and competitiveness in the market. Are you ready to take the necessary steps to secure your organization’s future?
In today's world, cyber threats are more prevalent than ever, making the safeguarding of sensitive information a paramount responsibility for C-suite leaders in healthcare organizations. The implementation of Cybersecurity Maturity Model Certification (CMMC) controls presents a unique opportunity for executives to not only protect their data but also enhance their operational integrity and competitive advantage. Yet, a pressing question arises: how can leaders effectively navigate the intricate landscape of cybersecurity while ensuring compliance and minimizing risks?
This article explores ten essential CMMC controls designed to empower C-suite leaders, enabling them to fortify their organizations against evolving threats and achieve compliance with confidence. By understanding these controls, healthcare executives can take proactive steps to mitigate risks and safeguard their organizations in an increasingly complex digital environment.
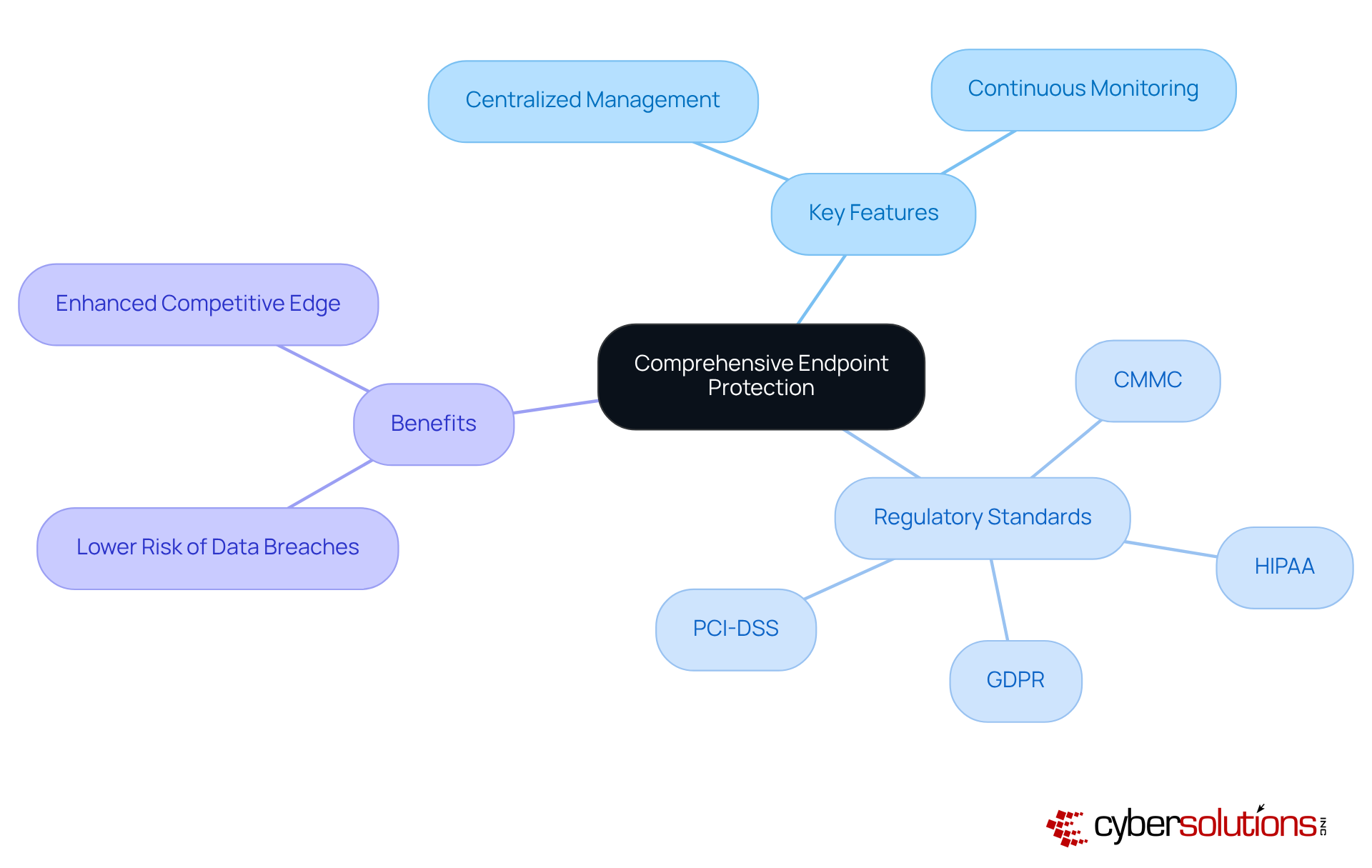
In today's digital age, cybersecurity is not just an option; it's a necessity, especially in healthcare. Cyber Solutions offers comprehensive endpoint protection that includes advanced threat detection and response capabilities, alongside application allowlisting. This proactive approach ensures that only approved applications can execute on all endpoints—laptops, desktops, and mobile devices—effectively preventing unauthorized software and malware from compromising your systems.
Key features of application allowlisting include:
By adopting these measures, healthcare organizations can significantly lower their risk of data breaches. Are you aware of the potential consequences of a breach? Not only can it lead to financial losses, but it can also damage your reputation and erode patient trust.
Moreover, implementing these strategies improves alignment with regulatory requirements and ensures adherence to strict cybersecurity standards, including:
This ultimately safeguards sensitive information and upholds operational integrity. By positioning your entity favorably for securing federal contracts, you can enhance your competitive edge in the healthcare sector. Don't wait until it's too late—take action now to protect your organization.
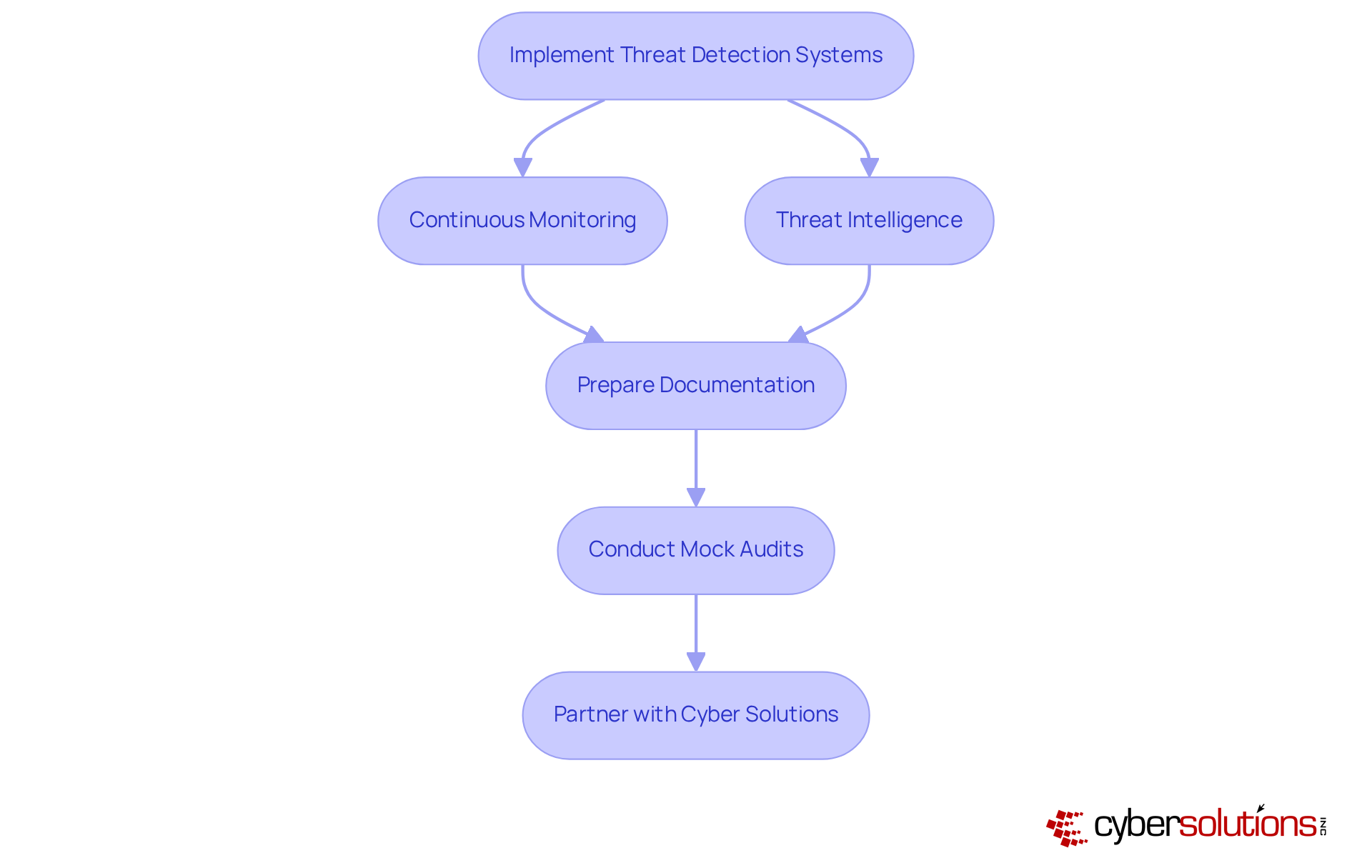
Implementing robust threat detection systems is not just a necessity; it’s a critical component for ensuring compliance with CMMC controls. In today’s landscape, where threats are ever-evolving, organizations must leverage advanced analytics and machine learning to detect potential threats in real-time. This ensures that your entity meets the stringent cybersecurity standards required for CMMC Level 3, including the necessary CMMC controls. Continuous monitoring of network activity, coupled with threat intelligence, allows organizations to respond swiftly to incidents, minimizing potential damage.
But it doesn’t stop there. Preparing thorough documentation and conducting mock audits are crucial steps in demonstrating adherence to CMMC controls. This proactive approach not only enhances your cybersecurity posture but also helps maintain eligibility for lucrative government contracts. In a competitive defense contracting industry, this can provide a significant edge.
Are you ready to elevate your cybersecurity strategy? By partnering with Cyber Solutions, you can effectively address the unique challenges posed by today’s cybersecurity threats. Don’t wait for an incident to occur; take action now to safeguard your organization’s future.
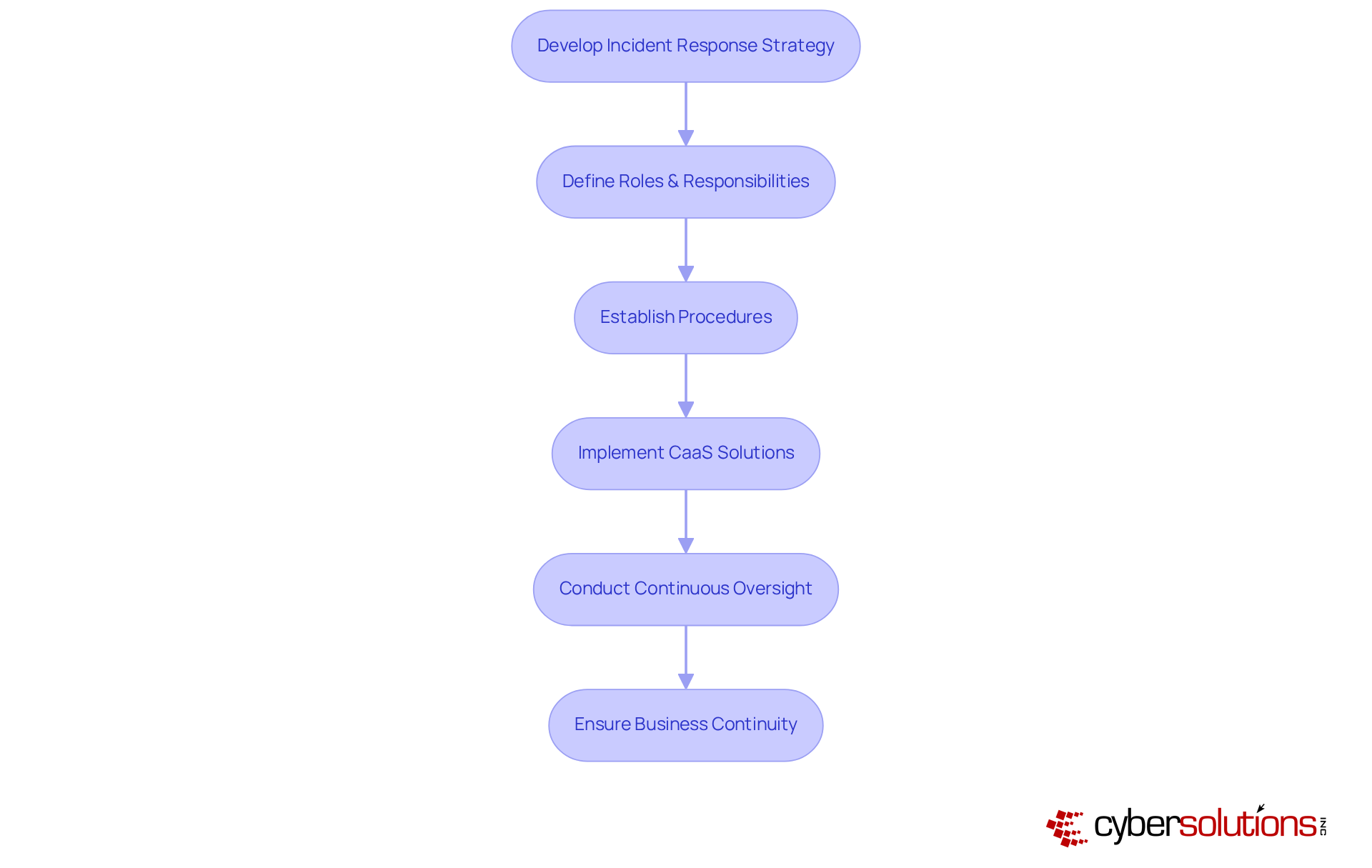
An effective incident response strategy is not just a best practice; it’s a cornerstone of regulatory adherence in today’s complex cybersecurity landscape. Cyber Solutions empowers organizations to develop customized incident response strategies that clearly define roles, responsibilities, and procedures for addressing security incidents. Our Incident Response services swiftly identify, contain, and mitigate threats, ensuring business continuity while restoring your systems. This proactive readiness not only minimizes the impact of incidents but also demonstrates compliance with regulatory requirements, enabling organizations to recover quickly and effectively.
Incorporating our Compliance as a Service (CaaS) solutions enhances your preparedness for audits through continuous oversight and risk evaluations. With the ever-evolving nature of cyber threats, can your organization afford to be unprepared? By partnering with Cyber Solutions, you can navigate these challenges with confidence, ensuring that your incident response strategy is robust and effective. Let us help you safeguard your organization’s future.
In today's digital landscape, regular vulnerability evaluations are not just important; they are essential for maintaining compliance with the CMMC controls. These evaluations systematically identify and categorize vulnerabilities within a company's IT infrastructure, enabling proactive remediation strategies. By addressing vulnerabilities before they can be exploited, organizations not only bolster their defenses but also align with CMMC controls that emphasize continuous monitoring and risk management.
Organizations that prioritize regular vulnerability evaluations often see significant improvements in their security frameworks. For example, a healthcare organization that conducted biannual evaluations successfully mitigated risks during a sophisticated cyberattack, protecting sensitive patient data. Conversely, a financial institution that overlooked regular assessments faced dire consequences, including a data breach that led to substantial financial losses and regulatory penalties.
Data shows that companies implementing proactive security measures, such as regular vulnerability assessments, can cut breach costs by an average of 48%. Furthermore, organizations that integrate CMMC controls and these evaluations into their compliance strategies demonstrate a commitment to cybersecurity, which is crucial for maintaining customer trust and meeting regulatory requirements. By making vulnerability evaluations a priority, organizations can effectively enhance their defenses against evolving cyber threats and ensure compliance with regulatory standards.
In today's complex regulatory landscape, Compliance as a Service (CaaS) emerges as a vital solution for organizations striving to meet their regulatory obligations. Cyber Solutions stands at the forefront, offering continuous support and expert guidance to ensure that all necessary controls are not only implemented but also rigorously maintained. This innovative service alleviates the burdens of regulatory management, allowing organizations to focus on their core operations while confidently adhering to relevant standards.
Consider the unique challenges faced by CFOs in the healthcare sector. With the increasing frequency of cyber threats and stringent compliance requirements, the stakes have never been higher. Organizations must navigate a maze of regulations while safeguarding sensitive patient data. How can they effectively manage these demands without compromising their operational efficiency?
Cyber Solutions provides the answer. By leveraging CaaS, organizations can streamline their compliance processes with CMMC controls, ensuring they stay ahead of regulatory changes and cyber threats. This proactive approach not only enhances security but also fosters a culture of compliance that permeates the organization. With Cyber Solutions, healthcare entities can transform compliance from a daunting obligation into a strategic advantage.
In today’s digital landscape, cybersecurity training is not just important; it’s essential for empowering employees to recognize and respond to potential threats. With the rise of sophisticated cyberattacks, healthcare organizations face unique challenges that demand immediate attention. Cyber Solutions offers customized training programs designed to equip personnel with best practices for maintaining safety and adhering to regulatory standards.
Our proven certification process begins with a thorough assessment of your current cybersecurity posture. We identify gaps and provide a clear roadmap for compliance, ensuring that your organization is not only aware of potential risks but also prepared to tackle them head-on. By fostering a culture of security awareness and implementing tailored remediation tactics, organizations can significantly reduce the risk of human errors—often a leading cause of security incidents.
Moreover, we understand that the cybersecurity landscape is constantly evolving. That’s why we offer ongoing oversight for compliance changes and sector-specific solutions, guaranteeing that your organization remains compliant and secure. Our expert guidance during the official assessment ensures that your entity is fully prepared to achieve certification, addressing any outstanding concerns efficiently.
Are you ready to take the next step in safeguarding your organization? Let Cyber Solutions be your partner in navigating the complexities of cybersecurity, ensuring that you not only meet compliance standards but also protect your most valuable assets.
Access controls, including CMMC controls, are not just a regulatory requirement; they are a critical line of defense in the ever-evolving landscape of cybersecurity threats, especially in healthcare. With sensitive data at risk, organizations must ensure that only authorized personnel can access this information. Cyber Solutions specializes in implementing role-based access controls (RBAC) and multi-factor authentication (MFA), enhancing safety and compliance. By limiting access to essential information, organizations can effectively safeguard their data and ensure compliance with CMMC controls.
In today’s digital age, the implications of inadequate access controls can be severe. Healthcare organizations face unique challenges, including the need to protect patient information while ensuring compliance with CMMC controls and stringent regulations. Cyber Solutions understands these challenges and offers tailored solutions that not only address security concerns but also foster trust with patients and stakeholders alike.
Are you prepared to protect your organization from potential breaches? By partnering with Cyber Solutions, you can implement robust access controls that mitigate risks and enhance your security posture. Don’t leave your sensitive data vulnerable—take action now to ensure that your organization is equipped to handle the complexities of cybersecurity.

Frequent evaluations are essential for maintaining standards and ensuring the effectiveness of protective measures in today’s cybersecurity landscape. Organizations that prioritize consistent auditing not only comply with CMMC controls but also significantly enhance their overall security posture. Did you know that businesses conducting regular audits report a notable improvement in identifying vulnerabilities and responding to threats? This proactive approach can ultimately reduce the risk of data breaches and compliance violations. In fact, statistics indicate that entities focusing on audits can cut compliance-related incidents by as much as 50%. This underscores the tangible benefits of such practices.
Cyber Solutions offers comprehensive audit services tailored to assess a company's compliance with cybersecurity standards. These audits provide a thorough evaluation of current practices, pinpointing areas for improvement and ensuring that organizations remain compliant with evolving regulations. With CMMC Level 2 adherence requiring a robust framework of 110 protective measures across 15 domains, regular audits serve as a proactive strategy to identify gaps and strengthen protocols.
Moreover, organizations that prioritize regular audits often find themselves better equipped to navigate the complexities of regulatory updates. By implementing a continuous monitoring mechanism, they can swiftly adapt to changes in regulatory requirements, safeguarding sensitive information while enhancing their competitive edge in the market. Additionally, adopting a layered cybersecurity approach—incorporating endpoint isolation, malware removal, and user training—can further enhance security measures, ensuring minimal operational disruption.
Addressing feedback from the assessor's report and submitting a Plan of Action and Milestones (POA&M) post-audit are crucial components of the regulatory process that ensure ongoing compliance with CMMC controls. Furthermore, integrating application allowlisting into the cybersecurity strategy actively prevents unauthorized software from executing, thereby improving assurance and reducing vulnerabilities. In summary, incorporating regular audits into compliance strategies is not merely a best practice; it is a fundamental aspect of a resilient cybersecurity framework.
Data encryption stands as a cornerstone in the fight against cyber threats, particularly in the healthcare sector where sensitive information is at stake. With the rise of sophisticated cyberattacks, organizations must prioritize robust encryption protocols to protect data both at rest and in transit. For example, employing end-to-end encryption standards like AES-256 can drastically reduce the risk of data breaches, as this method is widely recognized for its effectiveness in securing sensitive information.
Moreover, regulatory frameworks mandate the use of cryptographic methods to protect Controlled Unclassified Information (CUI), underscoring the critical role of encryption in compliance strategies. Achieving Level 3 compliance not only demonstrates a commitment to cybersecurity but also enhances eligibility for lucrative government contracts, assuring federal agencies of an organization’s capability to safeguard sensitive data.
The successful implementation of encryption protocols has led to a notable decrease in data breach incidents, showcasing the effectiveness of these measures in bolstering overall security. By prioritizing data encryption, organizations not only meet compliance standards but also fortify their defenses against ever-evolving cyber threats, ensuring the integrity and confidentiality of their sensitive information.
In a landscape where the stakes are high, can your organization afford to overlook the importance of data encryption? The time to act is now.
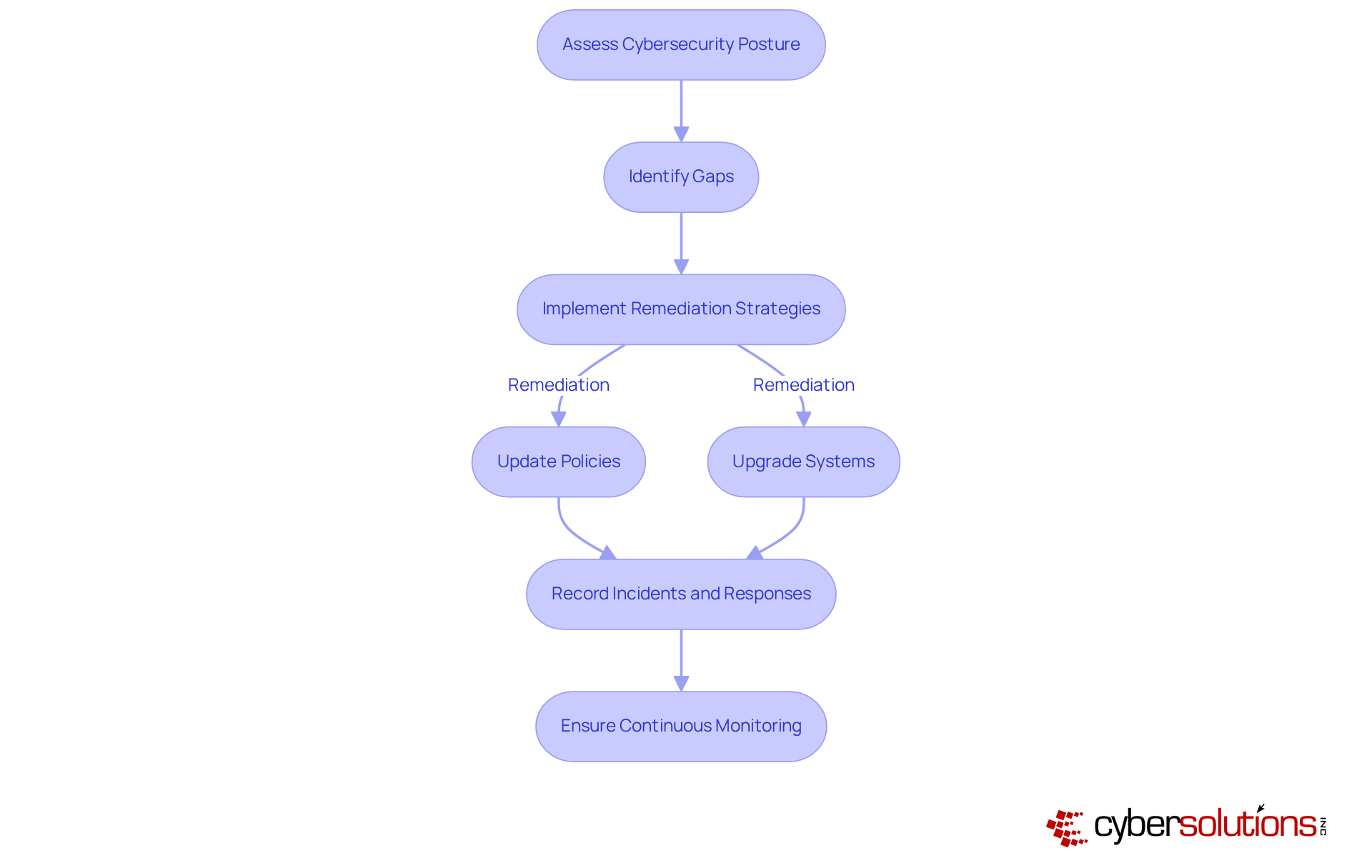
In today's digital landscape, cybersecurity is not just a necessity; it's a critical component of regulatory compliance, especially in healthcare. Incident reporting plays a vital role in this process, enabling organizations to respond swiftly and effectively to breaches. Cyber Solutions specializes in developing clear reporting protocols that foster accountability and transparency, ensuring that your organization is always prepared.
Our proven approach begins with a thorough assessment of your current cybersecurity posture, pinpointing any gaps that may exist. From there, we implement tailored remediation strategies, which include essential policy updates and system upgrades. By meticulously recording incidents and responses, organizations can glean valuable insights from past occurrences, enhancing their security protocols and improving adherence to CMMC controls.
Moreover, our Compliance as a Service (CaaS) solutions offer continuous monitoring and support. This ensures that your organization remains audit-ready and can adeptly manage any incidents that may arise. With Cyber Solutions by your side, you can navigate the complexities of cybersecurity with confidence, knowing that you have the expertise and resources to protect your organization effectively.
In today’s healthcare landscape, cybersecurity isn’t just a regulatory checkbox; it’s a crucial strategy for protecting sensitive information. With the threat landscape becoming more complex, organizations must prioritize:
These elements are essential not only for compliance but also for maintaining operational integrity.
Key strategies like:
are fundamental in achieving CMMC compliance. These measures safeguard against potential breaches while enhancing an organization’s competitive edge in securing government contracts. Moreover, continuous training and regular audits are vital, fostering a culture of security awareness and ensuring vigilance against emerging threats.
The stakes in cybersecurity are higher than ever. Organizations must act decisively to implement these controls and strategies, transforming compliance from a daunting task into a strategic advantage. By doing so, they not only protect their sensitive data but also build trust with patients and stakeholders, paving the way for a resilient and secure operational future. The time to act is now—embracing these essential CMMC controls is imperative for any organization committed to cybersecurity excellence.
What is the importance of cybersecurity in healthcare?
Cybersecurity is essential in healthcare to protect sensitive information, prevent data breaches, and maintain patient trust.
What comprehensive services does Cyber Solutions offer for endpoint protection?
Cyber Solutions provides advanced threat detection and response capabilities, along with application allowlisting, to ensure that only approved applications can execute on all endpoints.
What are the key features of application allowlisting?
Key features include centralized management for easy updates and continuous monitoring to detect unauthorized software attempts.
How does implementing these cybersecurity measures benefit healthcare organizations?
These measures significantly lower the risk of data breaches, improve compliance with regulatory requirements, and safeguard sensitive information.
Which regulatory standards does Cyber Solutions help organizations comply with?
Cyber Solutions helps organizations comply with CMMC controls, HIPAA, PCI-DSS, and GDPR.
What role does threat detection play in CMMC control implementation?
Robust threat detection systems are critical for ensuring compliance with CMMC controls, allowing organizations to detect potential threats in real-time.
How can organizations prepare for CMMC compliance?
Organizations can prepare by leveraging advanced analytics, conducting thorough documentation, and performing mock audits to demonstrate adherence to CMMC controls.
What is the significance of having an incident response plan?
An incident response plan is essential for regulatory adherence, as it defines roles, responsibilities, and procedures for addressing security incidents, minimizing their impact.
How does Cyber Solutions assist with incident response strategies?
Cyber Solutions helps organizations develop customized incident response strategies that quickly identify, contain, and mitigate threats to ensure business continuity.
What is Compliance as a Service (CaaS) and how does it benefit organizations?
CaaS enhances preparedness for audits through continuous oversight and risk evaluations, ensuring organizations are ready to meet regulatory requirements.