
In today's digital landscape, where email is a cornerstone of communication, the risks associated with it have surged, particularly for healthcare organizations. C-suite leaders must prioritize email security training - not just to protect sensitive information but to bolster their organization's resilience against escalating cyber threats. The stakes are high, and the challenge is clear: how can leaders effectively define objectives, assess vulnerabilities, and implement training that resonates with executives?
To address these pressing concerns, it’s essential to understand the current cybersecurity landscape. Healthcare organizations face unique challenges, including the handling of sensitive patient data and compliance with stringent regulations. These factors make them prime targets for cybercriminals. Leaders must ask themselves: Are their current training methods sufficient to combat these threats?
Implementing engaging and impactful email security training is not merely a checkbox exercise; it’s a strategic imperative. By leveraging data, statistics, and real-world case studies, organizations can create training programs that not only inform but also inspire action. This approach transforms the way executives perceive cybersecurity, shifting it from a mere obligation to a vital component of their organizational strategy.
In conclusion, the path forward is clear. Leaders must take decisive action to enhance their email security training, ensuring it is comprehensive and impactful. By doing so, they can fundamentally change their organization’s approach to cybersecurity, safeguarding not just data, but the very integrity of their operations.
Identify Key Threats: In today's digital landscape, healthcare organizations face a myriad of email threats, including phishing, business email compromise (BEC), and malware. By evaluating these specific threats, you can tailor your training initiatives to address the most pressing risks effectively.
Set SMART Goals: Establishing Specific, Measurable, Achievable, Relevant, and Time-bound (SMART) objectives is crucial for your development initiative. For example, aim to reduce phishing click rates by 50% within six months. This goal not only reflects a commitment to measurable improvement but also demonstrates accountability.
Align with Business Objectives: It's essential that your development goals align with broader business objectives, such as enhancing compliance with critical regulations like GDPR and HIPAA. This alignment is vital for C-suite leaders, as it showcases the program's value and relevance to the organization.
Engage Stakeholders: Involving key stakeholders-such as IT, compliance, and executive leadership-is critical for gathering insights and fostering support for your educational objectives. This collaborative approach enhances the program's relevance and efficiency, ultimately strengthening your organization's stance on communication protection.

Conduct Surveys and Assessments: Implementing surveys or quizzes is essential to evaluate the current knowledge of electronic correspondence protection among C-suite leaders. This should include inquiries on identifying phishing attempts and understanding communication protection protocols, laying the groundwork for development needs. Notably, 70% of individuals recognize the dangers of unfamiliar connections in messages yet continue to click on them. This statistic underscores the urgent need for effective instruction.
Analyze Past Incidents: Reviewing historical security incidents related to email breaches is crucial for pinpointing common vulnerabilities and knowledge gaps. This analysis will guide the creation of targeted educational material, ensuring it addresses specific weaknesses. For instance, the healthcare industry faces a susceptibility rate of 41.9% to deceptive online tactics, highlighting the necessity for customized educational programs in this sector.
Employ Simulation Attacks: Implementing simulated deceptive attacks is vital for assessing employees' ability to recognize and respond to potential threats. This hands-on approach provides real-time insights into vulnerabilities, demonstrating the effectiveness of education and identifying areas for improvement. Organizations that conduct awareness programs report a reduction in phishing risk of over 40% within just 90 days, making this a critical component of education.
Gather Employee Feedback: Collecting opinions from employees about their experiences with electronic communication protection is essential. Understanding their perspectives can reveal key areas that require further attention in development, fostering a culture of continuous improvement in communication protection practices. As cybersecurity professionals assert, "Without the right training, your users are the weakest link," emphasizing the importance of ongoing education.

Interactive Workshops: In today's rapidly evolving cybersecurity landscape, organizing workshops that foster active participation is crucial. These sessions encourage C-suite leaders to engage deeply with the material, particularly in grasping the significance of advanced cybersecurity solutions like endpoint protection and threat detection. By facilitating discussions and scenario-based learning, we empower leaders to understand the pressing need for robust security measures.
E-Learning Modules: To accommodate the busy schedules of executives, developing concise e-learning modules is essential. These modules can be completed at their convenience and should integrate multimedia components - such as videos and quizzes - to enhance engagement. Focusing on critical areas like communication protection and firewalls ensures that sensitive information remains safeguarded, making the learning experience both relevant and impactful.
Real-World Case Studies: Utilizing case studies of recent email security breaches serves to illustrate the dire consequences of inadequate email security training. This approach not only makes the education relatable but also highlights the necessity for comprehensive cybersecurity solutions, such as email security training, offered by Cyber Solutions. By examining real incidents, we highlight the tangible risks that organizations face, prompting a reevaluation of their security strategies.
Gamification: Introducing gamified elements, such as leaderboards or rewards for completing educational modules, can significantly motivate participation. This strategy creates a competitive learning environment that reinforces the importance of staying ahead of evolving cyber threats. By making learning engaging and rewarding, we encourage a proactive approach to cybersecurity education.

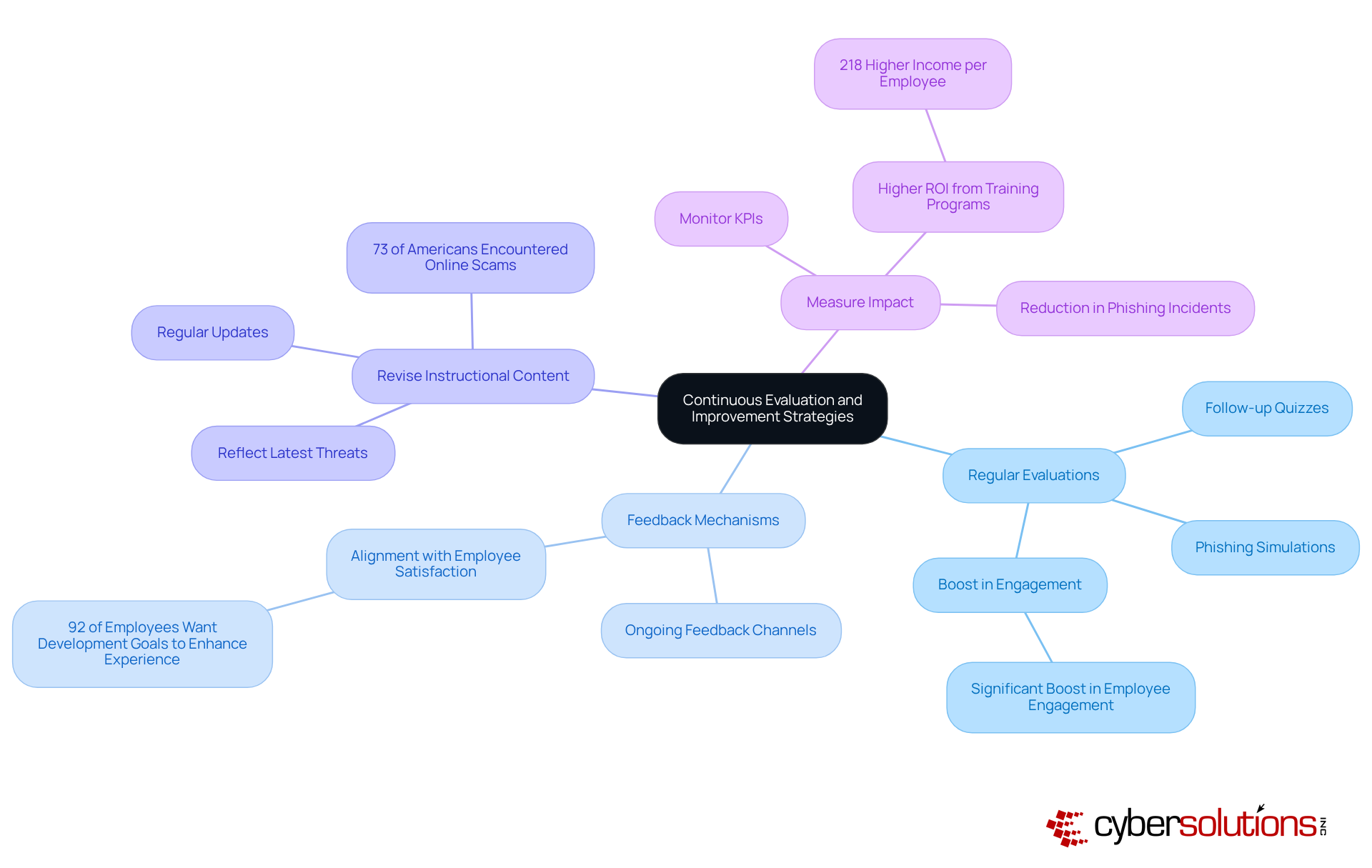
Regular Evaluations: It's crucial to implement regular assessments to evaluate the effectiveness of your email protection enhancement program. Consider follow-up quizzes or phishing simulations to measure knowledge retention and pinpoint areas for improvement. Research indicates that organizations conducting regular assessments see a significant boost in employee engagement and retention of vital safety practices.
Feedback Mechanisms: Establishing strong channels for ongoing feedback from participants is essential. This feedback is invaluable for refining the educational content and delivery. A study reveals that 92% of employees believe development goals should enhance their experience, underscoring the importance of aligning digital protection learning objectives with employee satisfaction.
Revise Instructional Content: Regularly reviewing and updating instructional materials is necessary to reflect the latest communication threats and best practices. Keeping content current is vital, especially considering that nearly 73% of Americans have encountered an online scam or attack. This statistic highlights the need for relevant education in digital communication protection.
Measure Impact: Monitoring key performance indicators (KPIs) such as the reduction in phishing incidents and improved reporting rates is essential for assessing the program's impact on your organization's safety posture. Organizations that effectively measure training outcomes often report a higher return on investment, with those implementing comprehensive email security training programs achieving 218% higher income per employee compared to those without such training.
Developing an effective email security training program is not just a necessity; it’s a strategic imperative for C-suite leaders determined to protect their organizations from escalating cyber threats. By clearly defining objectives, assessing current knowledge, selecting engaging training methods, and implementing continuous evaluation strategies, leaders can significantly bolster their organization’s email security posture. This proactive approach not only mitigates vulnerabilities but also cultivates a culture of security awareness across the organization.
Key steps include:
Utilizing interactive workshops, e-learning modules, and real-world case studies can make training more relatable and effective. Regular evaluations and feedback mechanisms are crucial for refining training content, ensuring it remains relevant in the face of evolving threats.
Ultimately, prioritizing email security training transcends mere compliance; it empowers employees to serve as the first line of defense against cyber threats. By investing in robust training programs, organizations can mitigate risks and enhance their overall security posture, making email security a cornerstone of their operational strategy.
What are the key threats that healthcare organizations face regarding email security?
Healthcare organizations face several email threats, including phishing, business email compromise (BEC), and malware.
How can organizations tailor their email security training initiatives?
Organizations can tailor their training initiatives by evaluating specific threats they face, allowing them to address the most pressing risks effectively.
What does SMART stand for in the context of setting goals for email security training?
SMART stands for Specific, Measurable, Achievable, Relevant, and Time-bound.
Can you provide an example of a SMART goal for email security training?
An example of a SMART goal is to aim for a 50% reduction in phishing click rates within six months.
Why is it important to align email security training goals with broader business objectives?
Aligning training goals with broader business objectives, such as compliance with regulations like GDPR and HIPAA, is vital as it showcases the program's value and relevance to the organization.
Who should be involved in the development of email security training initiatives?
Key stakeholders such as IT, compliance, and executive leadership should be involved to gather insights and foster support for educational objectives.
What is the benefit of engaging stakeholders in email security training development?
Engaging stakeholders enhances the program's relevance and efficiency, ultimately strengthening the organization's stance on communication protection.