
In today's fast-paced world, seamless communication is not just important; it's essential for organizational success. Yet, the threat of disruptions is more pronounced than ever. As businesses navigate a complex digital landscape, the need for effective voice disaster recovery strategies becomes critical.
This article explores ten essential strategies that not only protect communication systems but also bolster resilience against unexpected challenges. How can organizations prepare for potential crises while ensuring operational continuity? The answers lie in proactive planning and innovative solutions that tackle both current and emerging threats.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially for organizations reliant on seamless communication. Cyber Solutions Inc. stands at the forefront, offering a comprehensive suite of voice disaster recovery services that ensure business continuity during unforeseen disruptions. Their tailored solutions include:
All designed to preserve operational efficiency and secure interactions in crisis situations.
As organizations increasingly recognize the critical need for strong disaster response strategies, Cyber Solutions distinguishes itself by leveraging cutting-edge technologies. These innovations facilitate smooth interactions and swift restoration, addressing the growing demand for voice disaster recovery solutions. In 2025, market trends indicate that organizations will prioritize protecting their communication channels from potential disruptions. Key features of Cyber Solutions' offerings, such as automated backup triggers and environment snapshots, are essential for minimizing downtime and ensuring rapid service restoration.
Moreover, the proactive approach of incorporating disaster response plan readiness evaluations into employee onboarding highlights Cyber Solutions' commitment to sustaining operational resilience. Industry leaders emphasize the necessity of developing disaster response strategies that focus on partial restoration rather than complete failover. This strategic shift enables organizations to maintain essential operations even amid significant disruptions, a crucial consideration as businesses face escalating cyber threats and regulatory pressures.
Experts suggest that integrating disaster restoration hooks into CI/CD pipelines can further enhance response strategies, ensuring alignment with production states and minimizing operational impact. With a steadfast dedication to innovation and excellence, Cyber Solutions Inc. is well-positioned to lead the charge in disaster recovery, helping organizations navigate the complexities of modern IT environments while ensuring their networks remain secure and robust.
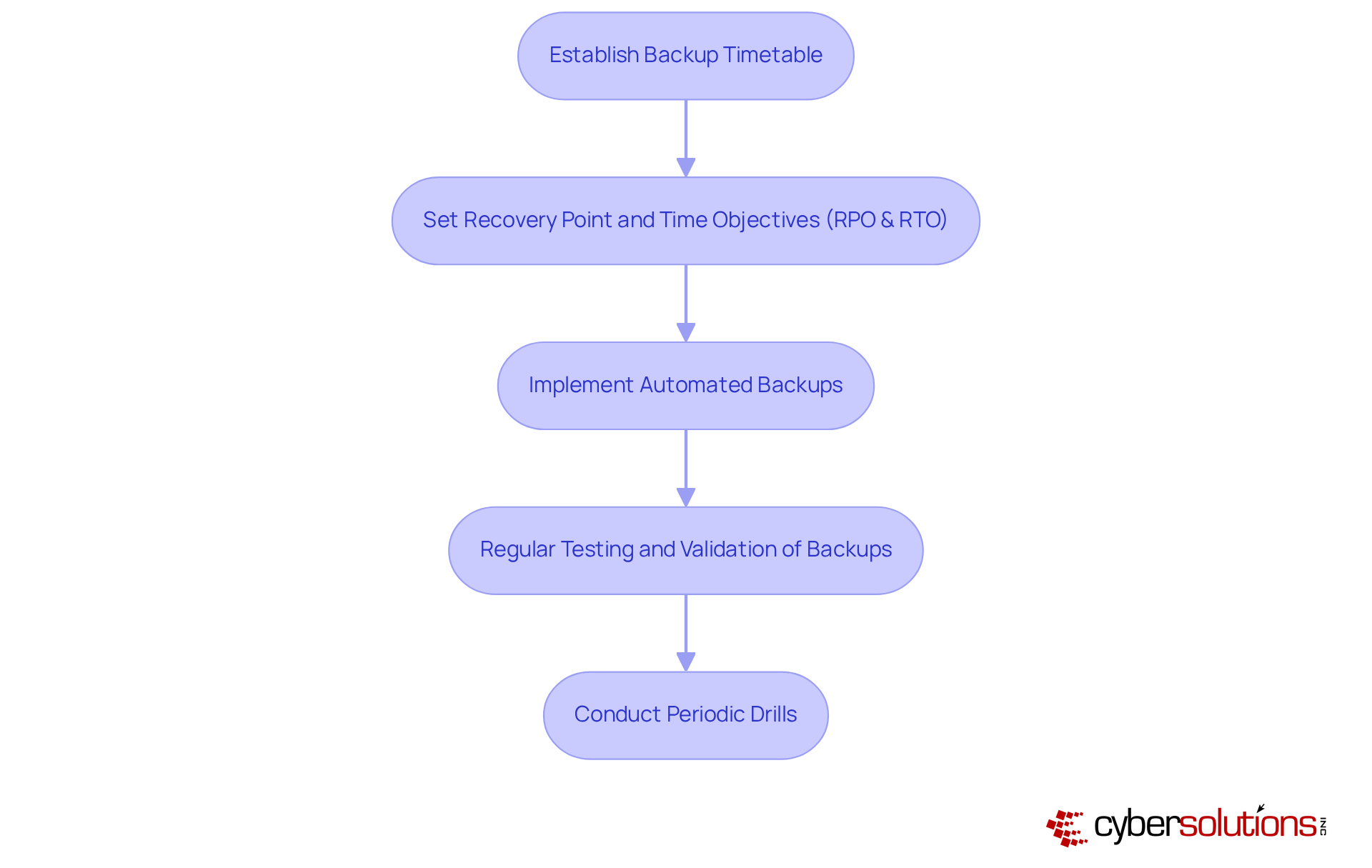
To ensure the reliability of audio exchanges, organizations must prioritize regular backups of their audio platforms. This is not just a best practice; it’s a necessity. By creating a timetable for automated backups, organizations can secure their audio data, ensuring effective voice disaster recovery and making it easily accessible for rapid recovery in the event of a system failure. Cloud-based solutions significantly bolster the reliability of these backups, offering scalable storage options and advanced security features like encryption and multi-factor authentication. These measures protect data integrity and minimize potential downtime, allowing organizations to maintain seamless communication.
Optimal methods for audio data backup involve establishing clear Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) that are essential for effective voice disaster recovery tailored to the organization’s unique needs. This alignment ensures that backup frequency corresponds with the criticality of the data, facilitating efficient resource allocation. Regular testing and validation of backup processes are essential to confirm their effectiveness. Periodic drills simulating real-world scenarios can help identify and address weaknesses in the backup strategy, ensuring preparedness.
Consider organizations like RiverCom 911 and Morgan County E-911, which have successfully implemented automated audio data backups. Their approach has enhanced operational efficiency and reliability. By adopting a comprehensive backup strategy that combines both on-premises and cloud-based solutions for voice disaster recovery, these entities have strengthened their defenses against data loss, ensuring business continuity even during unexpected disruptions. As we approach 2025, the importance of robust backup practices for audio systems cannot be overstated. It’s essential for organizations to act proactively to safeguard their vital interactions.
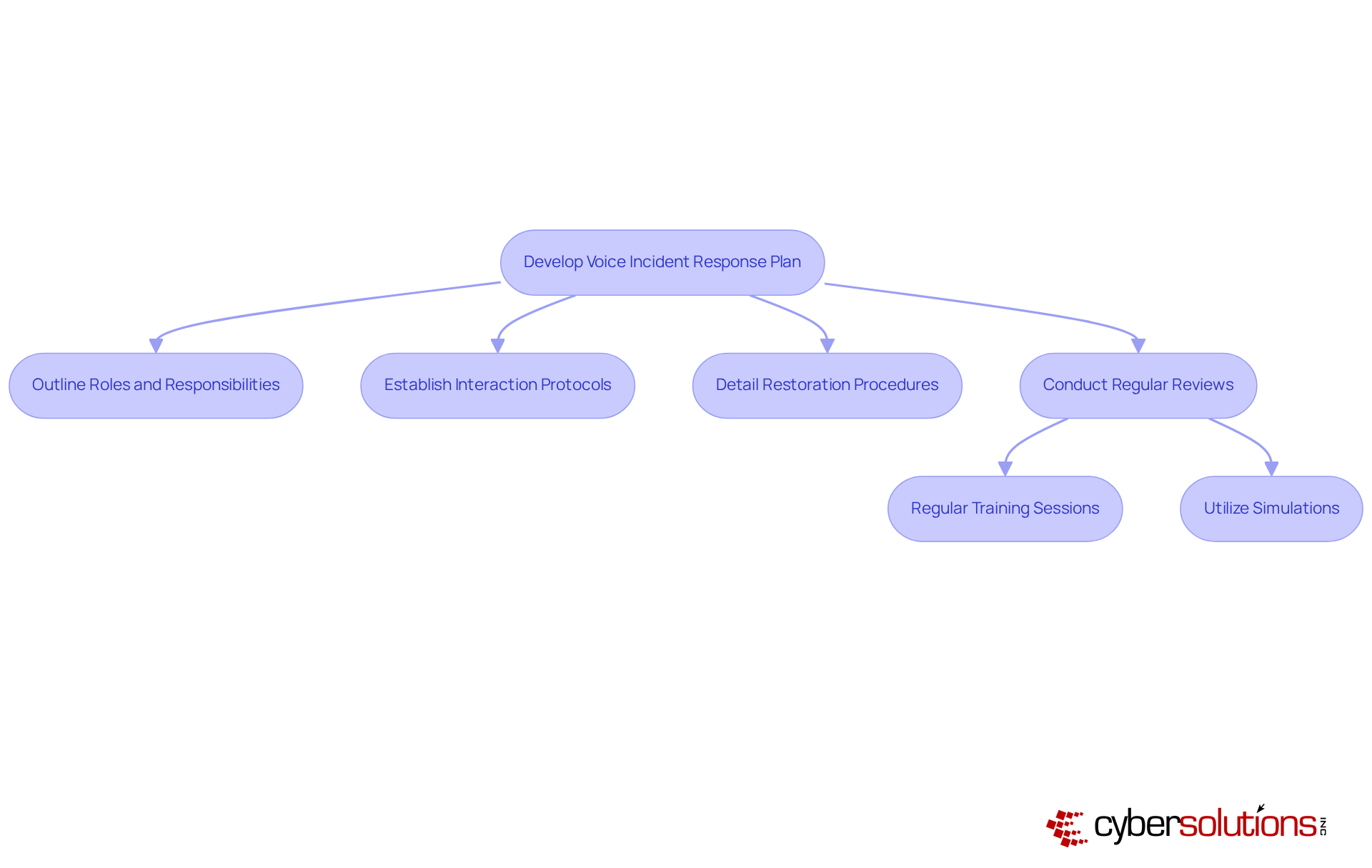
A well-organized incident response plan is essential for minimizing downtime during voice disaster recovery situations. This plan must clearly outline roles and responsibilities, establish interaction protocols, and detail restoration procedures. Regular reviews and updates are crucial, ensuring that all team members are familiar with their roles. This level of preparedness enables a rapid and synchronized response to incidents affecting communication, which is crucial for effective voice disaster recovery and significantly reduces operational interruptions.
Consider this: organizations that have implemented voice disaster recovery plans have reported a remarkable decrease in downtime, with some achieving restoration in under 10 minutes after an audio incident. Best practices include:
By prioritizing these strategies, companies can bolster their resilience against communication disruptions, safeguarding operations and maintaining customer trust.
Transitioning to cloud-based audio solutions is not just a technological upgrade; it’s a critical enhancement of an organization’s voice disaster recovery capabilities, particularly when facing cybersecurity threats like ransomware. These networks enable seamless call redirection, ensuring uninterrupted communication during outages. With integrated redundancy and failover features, cloud solutions guarantee that communication services remain operational even during unforeseen interruptions.
Consider the case study on ransomware response, which illustrates how companies have significantly improved their interaction capabilities through these frameworks, particularly after implementing a layered cybersecurity strategy. Statistics reveal that enterprise cloud telephony is projected to grow by 9.7% from 2022 to 2032, underscoring a growing recognition of its advantages. Moreover, organizations that adopt these solutions can realize up to 50% savings by eliminating expensive on-premise hardware while enhancing operational flexibility.
As industry experts emphasize, the benefits of cloud communication systems are hard to ignore, particularly in today’s fast-paced business environment where resilience and adaptability are paramount. With the PSTN switch-off looming in 2025, transitioning to cloud-based solutions is essential for maintaining a competitive communication infrastructure and ensuring security against evolving threats. Are you ready to embrace this shift and safeguard your organization’s future?

Training employees on sound recovery protocols is not just beneficial; it’s essential for effective disaster response. Regular training sessions are crucial for familiarizing staff with the procedures necessary for effective voice disaster recovery. This training encompasses understanding voice disaster recovery, which includes:
When staff are well-equipped, organizations can significantly decrease downtime and maintain operational continuity.
In today’s landscape, where cybersecurity threats loom large, the implications for healthcare organizations are profound. By investing in comprehensive training, organizations not only safeguard their operations but also enhance their resilience against potential disruptions. The proactive approach of training staff ensures that they are prepared to handle crises efficiently, ultimately protecting both the organization and its stakeholders.

Routine disaster restoration exercises are essential for validating the effectiveness of voice restoration plans. These exercises must simulate various scenarios, allowing teams to practice their responses and identify any weaknesses in the plan. Industry experts recommend conducting these drills at least quarterly to ensure ongoing readiness. Organizations that prioritize regular testing not only bolster their preparedness but also cultivate a culture of resilience.
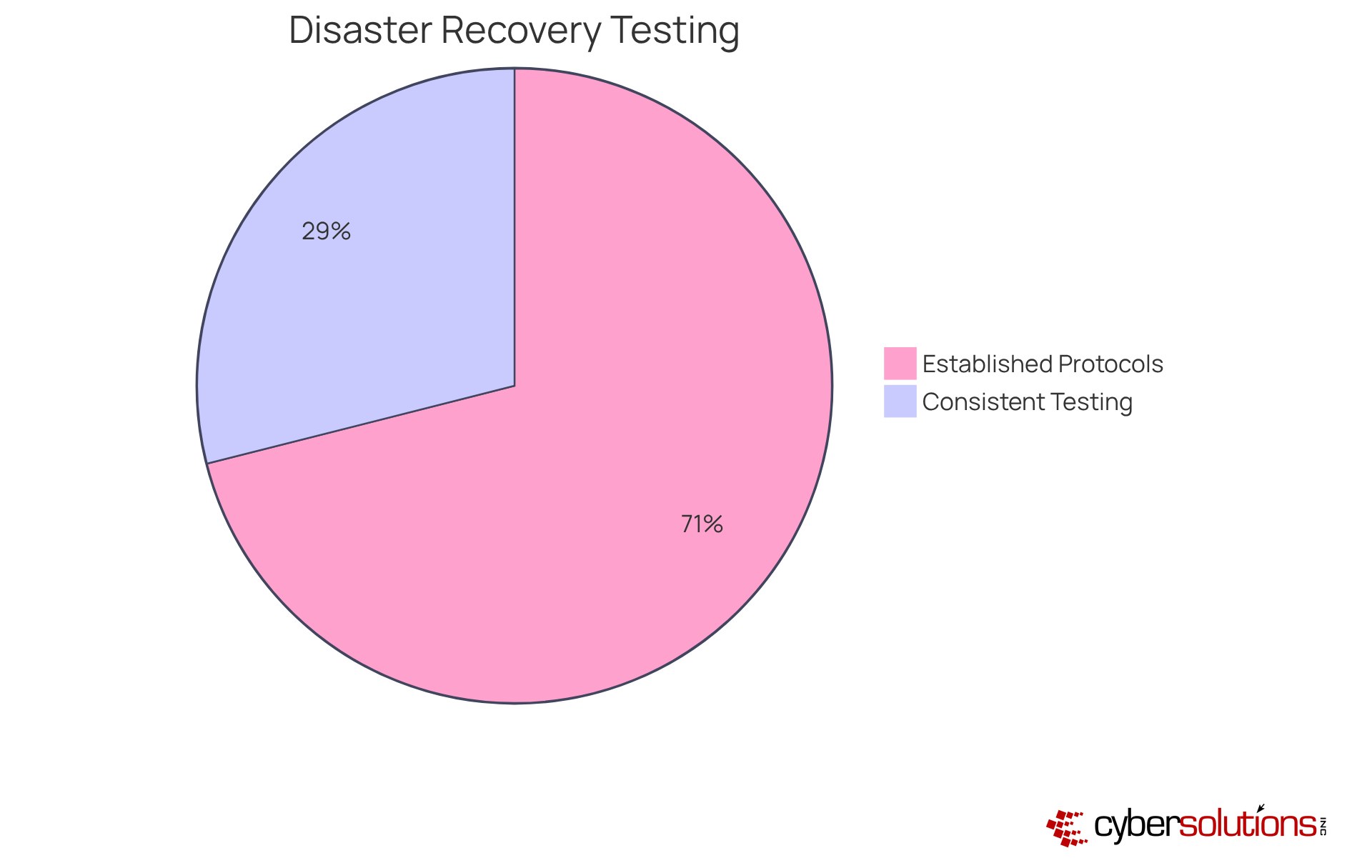
Consider this: companies that conduct drills report a remarkable 30% improvement in response times during actual incidents. Yet, a survey reveals that while 54% of organizations have established protocols for testing their restoration plans, only 22% carry out these tests consistently. By continuously refining their voice disaster recovery procedures through drills, organizations can confidently equip themselves to manage real-world disruptions effectively when they arise.
Implementing multi-vendor audio solutions is not just a strategic choice; it’s a vital step toward enhancing redundancy and resilience within voice disaster recovery for information systems. By collaborating with various providers, organizations can effectively ensure voice disaster recovery to safeguard against service disruptions. Imagine this: if one vendor encounters an outage, others can seamlessly implement voice disaster recovery to maintain service continuity. This approach not only boosts reliability but also offers flexibility in managing communication services, particularly in the context of voice disaster recovery across diverse platforms.
Consider the example of UPS, which has successfully integrated multiple audio providers to enhance operational efficiency and reliability. This real-world application showcases the tangible benefits of such redundancy. Industry leaders further emphasize that a robust multi-vendor strategy, particularly through voice disaster recovery, can significantly mitigate risks associated with single points of failure, ultimately leading to enhanced organizational resilience.
As Simon Sinek aptly noted, "Leadership is not about being in charge. It's about taking care of those in your charge." This highlights the critical importance of ensuring uninterrupted service for essential operations, especially regarding voice disaster recovery. Additionally, with the multi-vendor support services market projected to grow from USD 57.22 billion in 2025 to USD 68.52 billion by 2030, investing in diverse communication solutions, particularly voice disaster recovery, is not just beneficial; it’s essential for maintaining service continuity and navigating the complexities of compliance and data sovereignty.
In today’s digital landscape, implementing robust monitoring solutions for audio systems is not just beneficial; it’s essential for early detection of potential threats and operational issues. Organizations must leverage advanced tools like the Keepnet Vishing Simulator, which trains individuals to recognize and respond to phishing attempts via phone. This tool provides real-time analytics and alerts for unusual activities, such as call drops or unauthorized access attempts.
Continuous monitoring is crucial. It ensures that suspicious activities are detected and halted before they escalate into serious threats, thereby protecting businesses from ransomware, phishing, and other malware attacks. For instance, Teknosa, a leading retail firm, effectively reduced risks related to scams involving audio communication by implementing comprehensive monitoring solutions. They noted a substantial decrease in response times to incidents, showcasing the effectiveness of proactive measures.
Statistics reveal that early threat identification in auditory exchanges can lessen the impact of security breaches by as much as 70%. This underscores the importance of being proactive in cybersecurity. Additionally, organizations must remain vigilant against number spoofing, a significant concern in vishing attacks. By doing so, they can enhance their security posture and ensure uninterrupted service delivery.
In today’s digital landscape, incorporating robust cybersecurity measures into audio communications is not just important—it's essential. With threats like hacking and data breaches looming, organizations must prioritize the implementation of encryption protocols. These protocols are crucial for safeguarding audio data from interception and unauthorized access. Additionally, reliable access controls are necessary to ensure that only authorized individuals can access sensitive audio technology, significantly reducing the risk of insider threats.
Moreover, application allowlisting plays a vital role in preventing unauthorized software from running, thereby enhancing the security of communication platforms. This practice ensures compliance with standards such as HIPAA, PCI-DSS, and GDPR. By permitting only pre-approved applications to operate, organizations can substantially lower the risk of malware and ransomware attacks that could compromise audio interactions. Regular security assessments are also critical for identifying vulnerabilities within audio platforms and ensuring adherence to industry standards. Industry experts agree that proactive measures like these can greatly bolster an organization's voice disaster recovery strategy, ensuring that sensitive communications remain protected even during a cyber incident.
Furthermore, 24/7 network monitoring and alert services are indispensable for detecting anomalies and potential vulnerabilities in real-time. This continuous oversight allows for swift action to prevent interruptions or breaches, ensuring that audio networks remain secure. Optimal strategies for securing communication systems include:
Financial institutions, for instance, have successfully adopted audio security solutions to combat these threats, demonstrating the effectiveness of a comprehensive cybersecurity strategy.
As cyber threats continue to evolve, integrating advanced security measures into audio communications will be crucial for maintaining the integrity and confidentiality of sensitive information. By focusing on these strategies, companies can not only protect their communication infrastructure but also enhance their overall cybersecurity posture.
In today's digital landscape, adhering to regulations like HIPAA, PCI-DSS, and GDPR is not just important—it's essential for safeguarding communication platforms that handle sensitive information. Organizations must remain vigilant regarding these industry standards. Why? Because compliance not only mitigates legal risks but also fortifies the overall security framework of communication systems.
By implementing robust compliance measures, such as Streamlined Compliance as a Service (CaaS), businesses can significantly enhance their voice disaster recovery strategies. This ensures that their voice disaster recovery systems are resilient to potential threats. Such a proactive approach not only protects sensitive data but also builds trust with clients and stakeholders, reinforcing the organization's unwavering commitment to security and regulatory adherence.
Moreover, a layered cybersecurity strategy is vital. This includes:
These are crucial for maintaining audit readiness and enhancing overall operational integrity. In a world where cybersecurity threats are ever-evolving, organizations must act decisively to protect their assets and uphold their reputations.
In today’s fast-paced world, where seamless communication is essential, the importance of effective voice disaster recovery strategies cannot be overstated. Organizations must understand that a robust disaster recovery plan is not just a safety net; it’s a critical element of operational resilience. By prioritizing voice disaster recovery, businesses can protect their communication channels from unexpected disruptions, ensuring they remain operational even in challenging circumstances.
Several key strategies contribute to a comprehensive voice disaster recovery framework:
These are all vital tactics that enhance an organization’s crisis response capabilities. Additionally, integrating cybersecurity measures and adhering to industry regulations strengthens the overall security posture, safeguarding sensitive communications.
Investing in effective voice disaster recovery strategies is essential for organizations navigating the complexities of modern communication environments. By acting proactively to implement these best practices, businesses not only bolster their resilience against potential threats but also demonstrate their commitment to maintaining uninterrupted service and protecting their stakeholders’ interests. Are you ready to embrace these strategies and prepare for the unexpected?
What services does Cyber Solutions Inc. offer for voice disaster recovery?
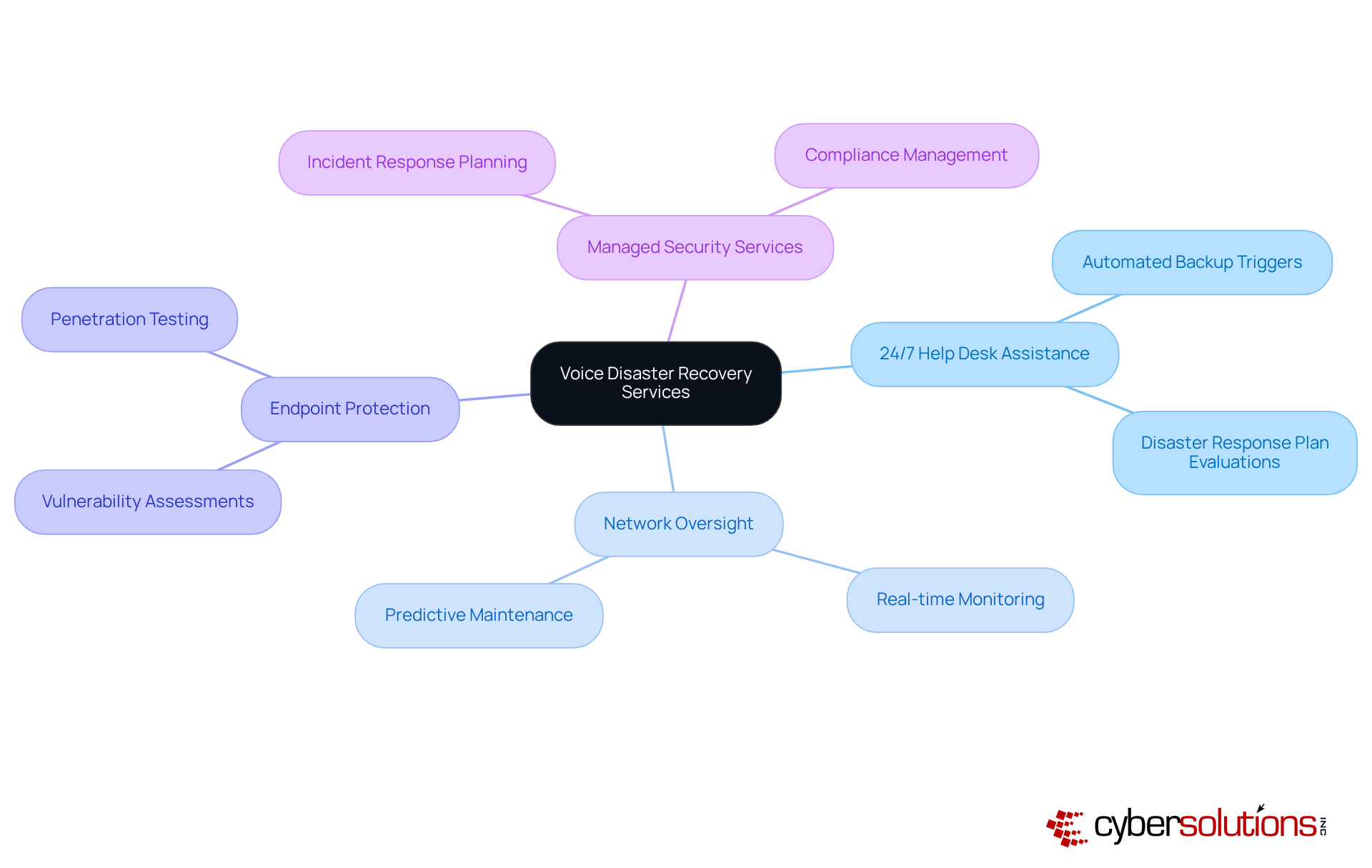
Cyber Solutions Inc. offers a comprehensive suite of voice disaster recovery services, including 24/7 help desk assistance, network oversight, endpoint protection, and managed security services.
Why is cybersecurity important for organizations reliant on communication?
Robust cybersecurity is crucial for organizations that depend on seamless communication, as it helps ensure business continuity during unforeseen disruptions.
What innovative technologies does Cyber Solutions leverage for disaster recovery?
Cyber Solutions utilizes cutting-edge technologies to facilitate smooth interactions and swift restoration, addressing the demand for effective voice disaster recovery solutions.
What key features are included in Cyber Solutions' offerings?
Key features include automated backup triggers and environment snapshots, which minimize downtime and ensure rapid service restoration.
How does Cyber Solutions incorporate disaster response into employee onboarding?
They include disaster response plan readiness evaluations in employee onboarding to emphasize the importance of operational resilience.
What is the strategic shift recommended for disaster response strategies?
Industry leaders recommend focusing on partial restoration rather than complete failover to maintain essential operations during significant disruptions.
How can organizations enhance their disaster response strategies?
Integrating disaster restoration hooks into CI/CD pipelines can enhance response strategies by ensuring alignment with production states and minimizing operational impact.
What is the significance of regular voice system backups?
Regular backups are necessary to ensure data integrity and effective voice disaster recovery, making audio data easily accessible for rapid recovery in case of system failure.
What are Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO)?
RPO and RTO are essential metrics for effective voice disaster recovery that help organizations align backup frequency with the criticality of their data.
How can organizations test their backup processes?
Organizations should conduct periodic drills simulating real-world scenarios to identify and address weaknesses in their backup strategy.
Can you provide examples of organizations that have successfully implemented audio data backups?
RiverCom 911 and Morgan County E-911 have successfully implemented automated audio data backups, enhancing their operational efficiency and reliability.
What is the purpose of a voice incident response plan?
A voice incident response plan outlines roles and responsibilities, establishes interaction protocols, and details restoration procedures to minimize downtime during voice disaster recovery situations.
How can organizations ensure their incident response plan is effective?
Regular reviews, updates, and training sessions for staff, along with simulations to test response effectiveness, are essential for maintaining an effective incident response plan.