
In today's digital age, the landscape of cybersecurity is increasingly complex. Endpoints - such as desktops, laptops, and mobile devices - are prime targets for cybercriminals. With nearly 70% of breaches projected to be linked to compromised devices by 2025, the need for robust endpoint protection is more critical than ever. This article explores the essential components and evolving strategies of endpoint protection, revealing how businesses can strengthen their defenses against sophisticated cyber threats. But with a plethora of solutions available, how can organizations identify the right fit for their unique security needs?
The endpoint protection definition highlights its role as a critical line of defense against the ever-evolving landscape of cyber threats, making it not just a necessity. With endpoints - desktops, laptops, and mobile devices - often being prime targets for cyberattacks, they represent vulnerable entry points into an organization’s network. In fact, projections for 2025 indicate that approximately 70% of breaches will be linked to compromised devices. This statistic underscores the urgent need for effective protection strategies.
A comprehensive endpoint protection definition combines essential tools like antivirus software, firewalls, and intrusion detection systems, all designed to safeguard sensitive data and maintain operational integrity. Current trends reveal a shift towards advanced solutions such as Endpoint Detection and Response (EDR), which not only detect but also respond to threats in real-time, significantly enhancing an organization’s defensive posture. Moreover, robust firewall and network protection measures, such as those provided by Cyber Solutions, ensure businesses are shielded from a wide array of cyber risks, including ransomware and phishing, through proactive monitoring and incident response.
Consider the real-world impact of these strategies. Organizations leveraging managed EDR solutions benefit from expert oversight of alerts and incidents, allowing them to focus on core operations while ensuring that critical risks are addressed promptly. The integration of artificial intelligence in device protection enhances behavioral analytics, enabling proactive threat identification and automated responses to emerging risks. As cyber threats continue to evolve, the importance of a comprehensive strategy for endpoint protection definition becomes increasingly clear.
To stay ahead, organizations must embrace multi-layered defense mechanisms that blend traditional security measures with innovative technologies. This approach ensures resilience against sophisticated attacks. Continuous monitoring and alert services, like those offered by Cyber Solutions, are vital for detecting anomalies and potential vulnerabilities. Additionally, tailored access controls and restrictions ensure that only authorized users can access sensitive data, thereby protecting both devices and the broader network.

The evolution of device security is not just a trend; it’s a necessity driven by rapid technological advancements and the increasing complexity of cyber threats. Organizations can no longer rely solely on traditional antivirus solutions that focus on detecting known malware. As cybercriminals employ sophisticated tactics such as zero-day exploits and ransomware, the limitations of these legacy systems have become glaringly apparent. Today’s protection systems leverage cutting-edge technologies like Endpoint Detection and Response (EDR) and machine learning algorithms, enabling real-time threat identification and mitigation.
This shift from reactive to proactive security measures is crucial for organizations aiming to safeguard against the ever-changing landscape of cyber threats. Consider this: the detection and response market is projected to experience significant growth by 2025, driven by the urgent need for comprehensive security solutions that can adapt to evolving attack vectors. Recent statistics reveal that 34 percent of retailers reported experiencing a breach in the past year, highlighting the pressing need for a clear endpoint protection definition and robust strategies.
Organizations are increasingly adopting EDR systems, which harness AI-driven capabilities to enhance risk detection and response. These solutions not only minimize the attack surface but also utilize collective intelligence to bolster overall security posture. Recent advancements underscore that modern EDR tools are designed to expedite response operations significantly, allowing companies to maintain operational continuity amid new challenges. The proactive defense mechanisms provided by these technologies are essential for organizations navigating the complexities of today’s cybersecurity landscape.

In today’s digital landscape, the importance of robust cybersecurity in healthcare cannot be overstated. With the rise of sophisticated cyber threats, healthcare organizations face unique challenges that demand a multi-layered defense strategy to protect sensitive data and maintain operational integrity.
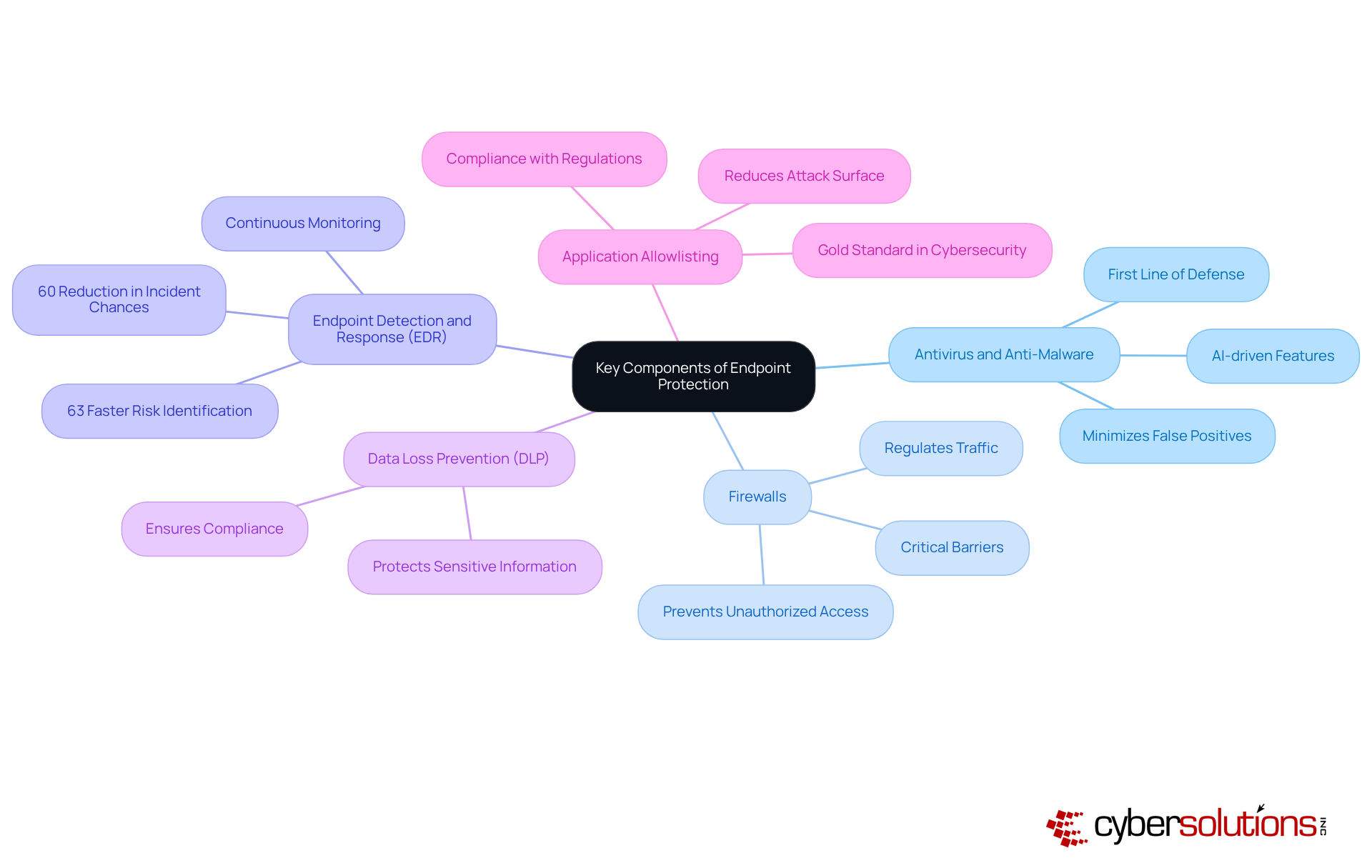
Antivirus and Anti-Malware Software serve as the first line of defense, essential for detecting and removing harmful software. Modern antivirus solutions now leverage AI-driven features, enhancing detection rates and minimizing false positives. But is your organization equipped with the latest technology?
Firewalls act as critical barriers between trusted internal networks and untrusted external environments. By regulating incoming and outgoing traffic, they prevent unauthorized access, safeguarding your organization’s assets.
Endpoint Detection and Response (EDR) solutions offer continuous monitoring and immediate response capabilities. Organizations using SentinelOne's Singularity Endpoint can identify risks 63% faster and reduce incident chances by 60%. This highlights the effectiveness of proactive risk detection and response strategies. Are you ready to enhance your incident response?
Data Loss Prevention (DLP) technologies protect sensitive information from unauthorized access and potential exfiltration, ensuring compliance with regulatory standards. Regular Patch Management is equally crucial; keeping software updated with the latest protective patches closes vulnerabilities that attackers could exploit.
Application Allowlisting stands out as a gold standard in cybersecurity. By allowing only pre-approved software to run, it significantly reduces the attack surface and helps organizations comply with regulations like HIPAA, PCI-DSS, and GDPR. This proactive approach not only observes application activity but also guarantees prompt threat detection and prevention, strengthening your overall defense.
Implementing these components can dramatically enhance your security posture. Companies utilizing advanced EDR solutions have reported a 55% reduction in mean time to respond (MTTR) to incidents. This comprehensive approach not only mitigates risks but also empowers organizations to maintain operational efficiency in an increasingly complex threat environment.
However, user awareness remains a significant challenge in effectively protecting devices. Continuous training and education are essential to address this issue. Are you investing in your team’s cybersecurity knowledge?
In today’s digital landscape, the endpoint protection definition emphasizes the importance of robust security measures. Organizations face a myriad of cybersecurity threats that can jeopardize sensitive data and operational integrity. To effectively combat these challenges, it’s crucial to evaluate various endpoint protection solutions, each offering distinct features and benefits:
Choosing the right protection measure is essential and should be based on factors such as organizational size, industry regulations, and specific security requirements. For instance, the average cost of a data breach hovers around USD 4.27 million, while the financial impact of a successful endpoint attack has surged from USD 7.1 million to USD 8.94 million. This stark reality underscores the financial imperative of investing in a robust endpoint protection definition. Furthermore, organizations must consider potential hidden costs associated with implementation and ongoing support when evaluating their options. By thoroughly assessing their needs, businesses can select a solution that not only addresses their security challenges but also aligns with their operational objectives.
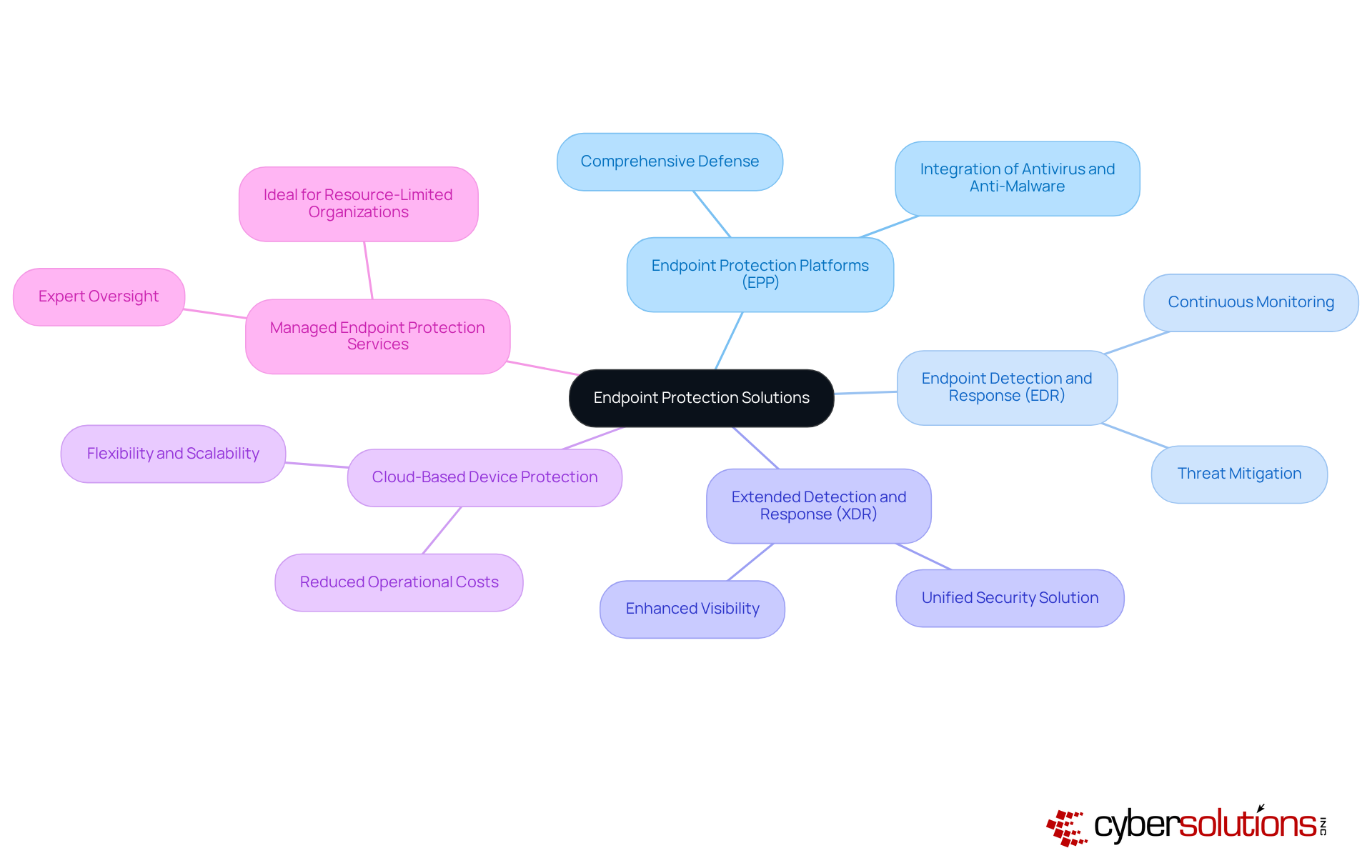
Endpoint protection stands as a crucial pillar in the fight against the ever-evolving landscape of cyber threats that target organizational networks. With endpoints being prime targets for attacks, the need for comprehensive protection strategies has never been more urgent. This article underscores the multifaceted nature of endpoint protection, which includes not only traditional antivirus solutions but also advanced technologies like Endpoint Detection and Response (EDR) and AI-driven tools.
Organizations must adopt a layered defense approach that integrates various protective measures, such as:
The evolution of endpoint protection reflects an urgent shift from reactive to proactive security measures, enabling organizations to swiftly identify and respond to potential threats. The financial repercussions of inadequate protection further emphasize the necessity of investing in robust endpoint solutions tailored to specific organizational needs.
Given these insights, it is imperative for businesses to prioritize endpoint protection as a fundamental aspect of their cybersecurity strategy. As cyber threats continue to evolve, organizations must remain vigilant and proactive in their defense efforts. By embracing advanced technologies and fostering a culture of cybersecurity awareness, businesses can significantly bolster their resilience against emerging threats, safeguarding sensitive data and maintaining operational integrity.
What is endpoint protection?
Endpoint protection refers to a critical line of defense against cyber threats, focusing on safeguarding devices such as desktops, laptops, and mobile devices that are often targeted by cyberattacks.
Why is endpoint protection important?
Endpoint protection is important because endpoints are vulnerable entry points into an organization’s network, with projections indicating that about 70% of breaches by 2025 will be linked to compromised devices.
What tools are included in a comprehensive endpoint protection strategy?
A comprehensive endpoint protection strategy includes tools such as antivirus software, firewalls, and intrusion detection systems, all designed to protect sensitive data and maintain operational integrity.
What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is an advanced solution that not only detects threats but also responds to them in real-time, significantly enhancing an organization’s defensive capabilities.
How do managed EDR solutions benefit organizations?
Managed EDR solutions provide expert oversight of alerts and incidents, allowing organizations to focus on their core operations while ensuring that critical risks are addressed promptly.
What role does artificial intelligence play in endpoint protection?
Artificial intelligence enhances endpoint protection by improving behavioral analytics, enabling proactive threat identification, and automating responses to emerging risks.
What is a multi-layered defense mechanism in endpoint protection?
A multi-layered defense mechanism combines traditional security measures with innovative technologies to ensure resilience against sophisticated cyberattacks.
Why is continuous monitoring important in endpoint protection?
Continuous monitoring is vital for detecting anomalies and potential vulnerabilities, helping organizations stay ahead of evolving cyber threats.
How can organizations protect sensitive data within their networks?
Organizations can protect sensitive data by implementing tailored access controls and restrictions to ensure that only authorized users can access it.