
Cybersecurity has emerged as a critical concern for organizations today. With ransomware attacks striking every 11 seconds globally, the need for proactive measures has never been more urgent. Cyber attack simulation exercises present a unique opportunity for leaders to bolster their organization’s defenses against these escalating threats. These simulations not only help identify vulnerabilities but also enhance incident response strategies and cultivate a culture of security awareness.
However, as the landscape of cyber threats continues to evolve, organizations must ask themselves: how can they effectively leverage these simulations to protect their assets while ensuring regulatory compliance and operational resilience? By embracing these exercises, organizations can not only safeguard their critical data but also position themselves as leaders in cybersecurity preparedness.
Cybersecurity is not just a technical concern; it’s a critical imperative for healthcare organizations. With ransomware incidents occurring every 11 seconds globally, the stakes have never been higher. Cyber Solutions Inc. provides a comprehensive suite of cyber threat rehearsal services, which includes a cyber attack simulation exercise to prepare entities for potential cyber dangers. These cyber attack simulation exercises replicate real-world attack scenarios, enabling companies to rigorously assess their defenses and incident response strategies.
In today’s rapidly evolving cyber landscape, organizations must adapt to sophisticated threats. Recent advancements in AI-driven platforms enable security teams to develop and simulate complex threat scenarios in real-time, ensuring continuous exposure validation. This capability is essential as cyber threats evolve at an alarming pace. Regular cyber attack simulation exercises empower organizations to significantly enhance their readiness against these threats.
Moreover, implementing application allowlisting enhances defenses by proactively blocking unauthorized software, minimizing exposure, and ensuring compliance with regulations like HIPAA and GDPR. With 24/7 threat monitoring, Cyber Solutions is committed to protecting businesses from ransomware and phishing attacks, establishing a robust security framework.
Real-world examples underscore the effectiveness of these simulations. Organizations that have participated in a cyber attack simulation exercise report improved response times and heightened awareness of their security vulnerabilities. For instance, healthcare entities, which face the highest breach costs averaging $10.93 million per incident, have found that these drills prepare them for unique challenges, such as the staggering 94% increase in ransomware incidents in recent years.
Investing in a cyber attack simulation exercise not only safeguards assets but also builds resilience against the ever-changing landscape of cyber threats. Are you ready to fortify your organization’s defenses?

Cyber attack simulation exercises are essential for enhancing organizational resilience in today’s digital landscape. Due to the increasing frequency and sophistication of cyber threats, companies must routinely participate in cyber attack simulation exercises to uncover vulnerabilities within their security frameworks. This proactive approach not only prepares teams to manage potential incidents but also fosters a culture of continuous improvement in cybersecurity practices through a cyber attack simulation exercise.
Entities that conduct frequent cyber attack simulation exercises report significant enhancements in their response capabilities and overall security posture. These cyber attack simulation exercises are a critical component of risk management, enabling businesses to adapt to evolving threats and regulatory requirements. The knowledge gained from the cyber attack simulation exercise enhances security protocols, ensuring that teams are better equipped for real-world challenges.
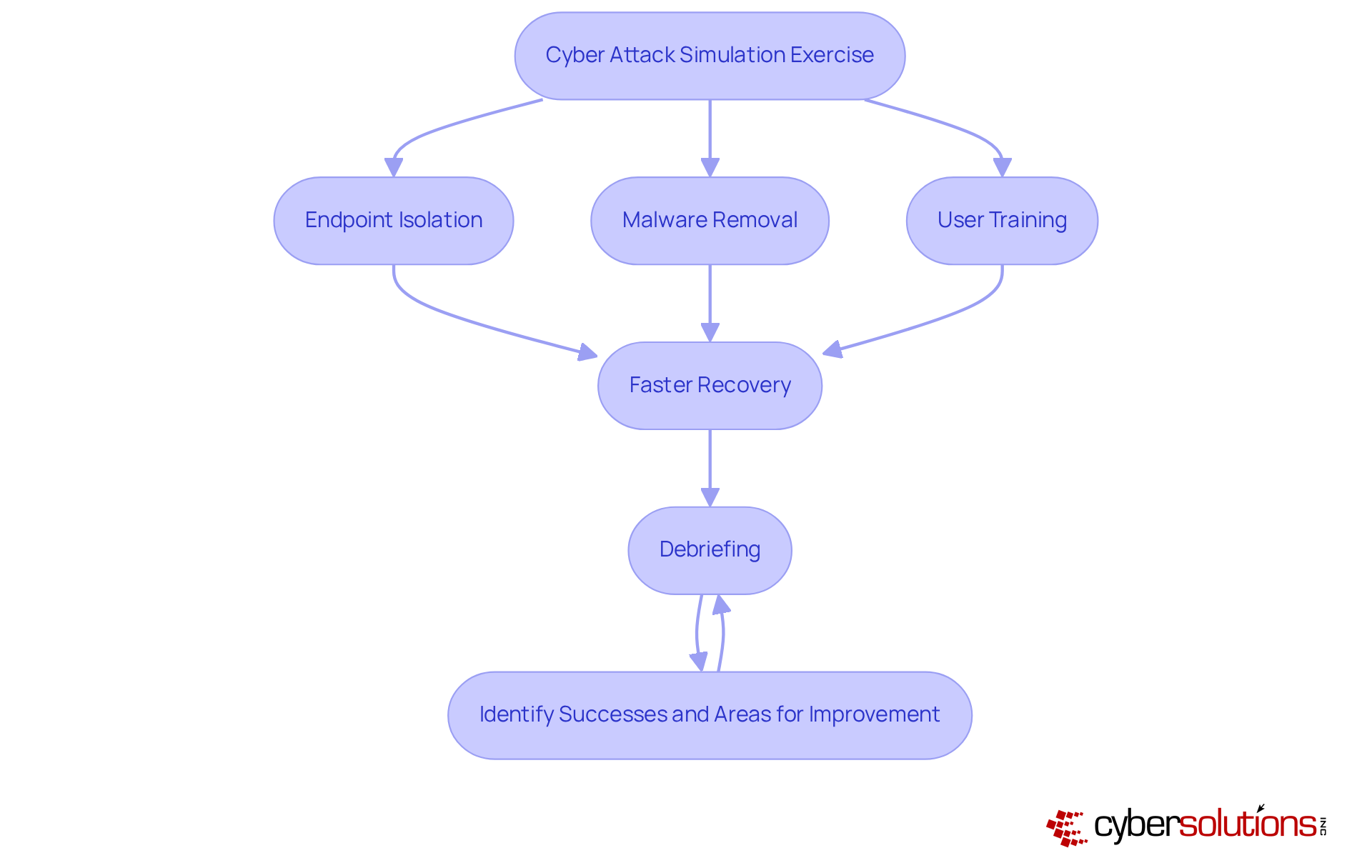
Consider a case study where having an incident response team physically present within a day significantly contained threats. This layered approach included:
This led to a faster recovery. Additionally, conducting thorough debriefings after each cyber attack simulation exercise is vital for identifying successes and areas for improvement.
Ultimately, incorporating a cyber attack simulation exercise cultivates a robust environment, empowering teams to react efficiently under stress while mirroring the complexities of actual breaches. Are your cybersecurity measures up to the challenge? It's time to take action and strengthen your defenses.
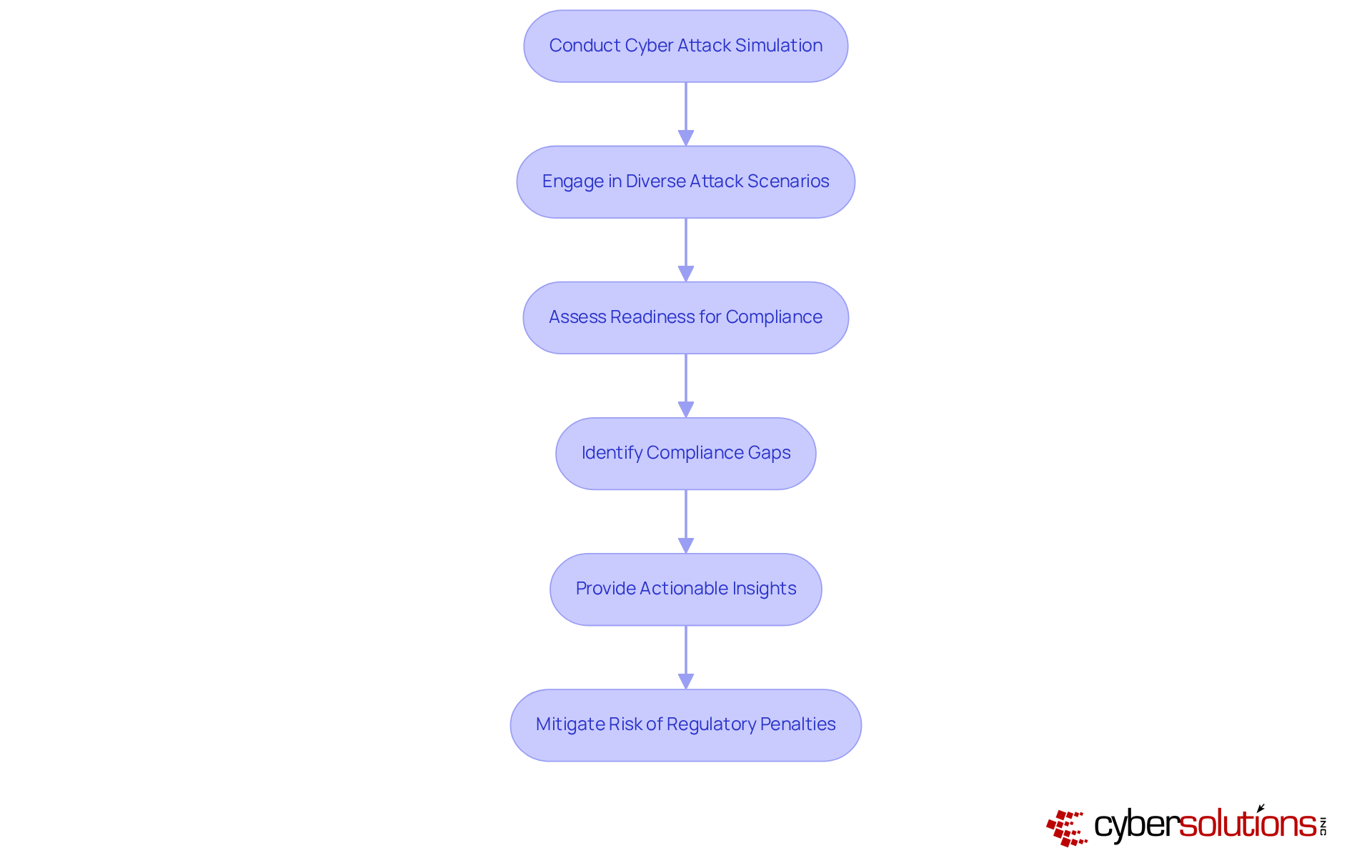
In today's healthcare landscape, conducting a cyber attack simulation exercise is not just beneficial; it is essential. With the increasing frequency and sophistication of cyber threats, organizations must prioritize regulatory adherence across standards like HIPAA, PCI-DSS, and GDPR. By engaging in a cyber attack simulation exercise with diverse attack scenarios, entities can rigorously assess their readiness to meet these compliance requirements.
These cyber attack simulation exercises reveal compliance gaps and provide actionable insights for remediation, significantly mitigating the risk of regulatory penalties. For instance, organizations that regularly engage in a cyber attack simulation exercise report improved threat detection capabilities and enhanced incident response strategies, aligning their security frameworks with industry standards.
As cyber threats continue to evolve, the ongoing assessment facilitated by cyber attack simulation exercises becomes crucial for maintaining compliance and protecting sensitive data. Are you prepared to safeguard your organization against the next wave of cyber threats? Embrace a cyber attack simulation exercise as part of your cybersecurity exercises to ensure compliance and enhance your overall security posture.
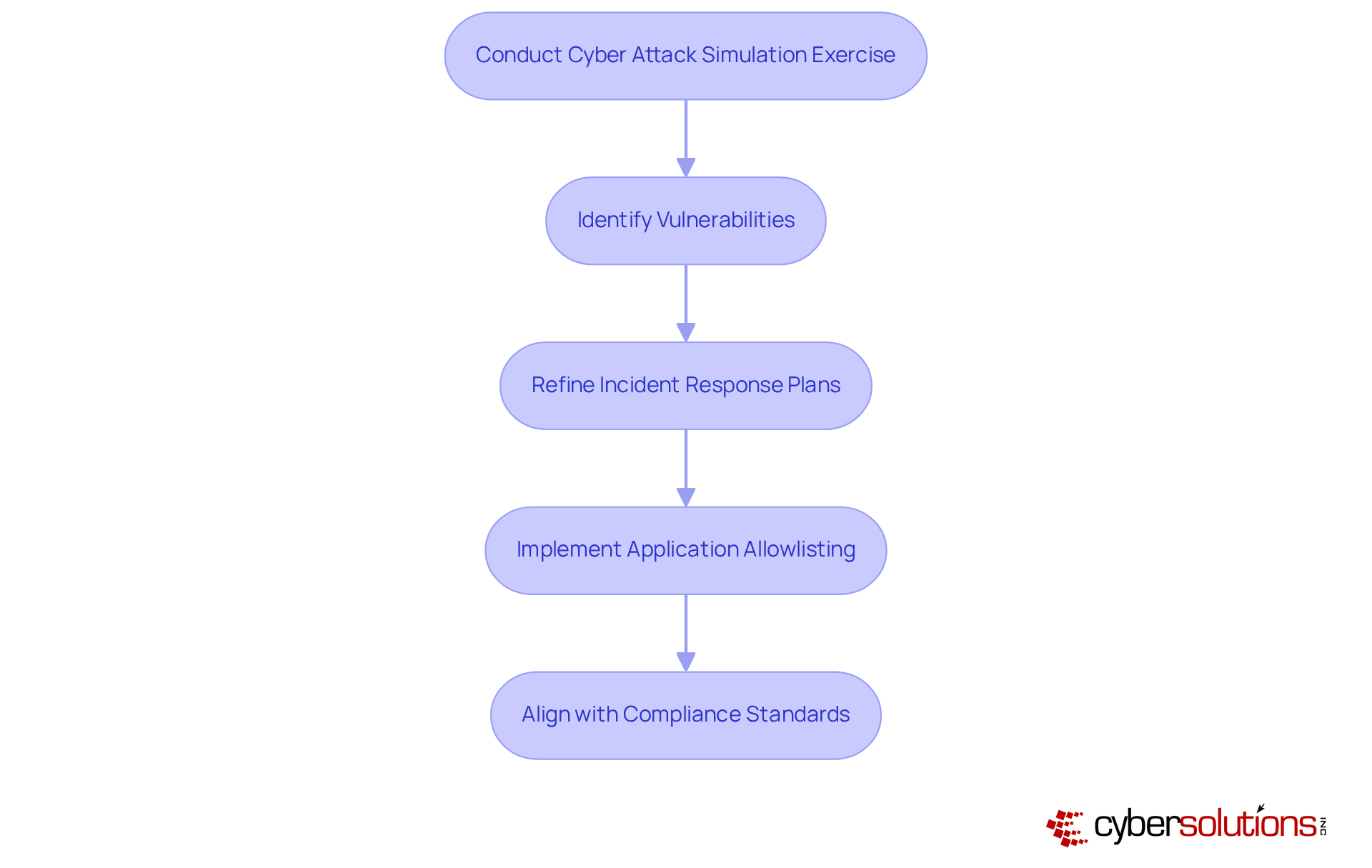
Cybersecurity breaches pose a significant threat to organizations, which is why conducting a cyber attack simulation exercise is an essential method for identifying weaknesses in their systems. These drills, which include a cyber attack simulation exercise to simulate actual threat paths, empower security teams to uncover vulnerabilities that cybercriminals could exploit. Research shows that a substantial percentage of organizations identify critical vulnerabilities through cyber attack simulation exercises, highlighting their vital role in proactive cybersecurity strategies.
For instance, the Cybersecurity for Manufacturing Innovation Institute (CyManII) conducted simulated intrusions that revealed crucial enhancements in the City of Mission's cybersecurity posture. This enabled officials to refine their incident response plans effectively. Such hands-on training not only boosts the technical team's confidence but also enhances communication and decision-making skills among leadership.
Moreover, implementing application allowlisting as part of a comprehensive cybersecurity strategy can significantly fortify defenses. This proactive approach prevents unauthorized applications from executing, thereby reducing the vulnerability surface. It also incorporates features like continuous monitoring of application activity and centralized management of allowlists.
Additionally, aligning with compliance standards such as CMMC ensures that organizations handling federal data adhere to essential cybersecurity practices, thereby reinforcing their overall security framework. In a landscape where threats are ever-evolving, taking these steps is not just advisable; it's imperative.
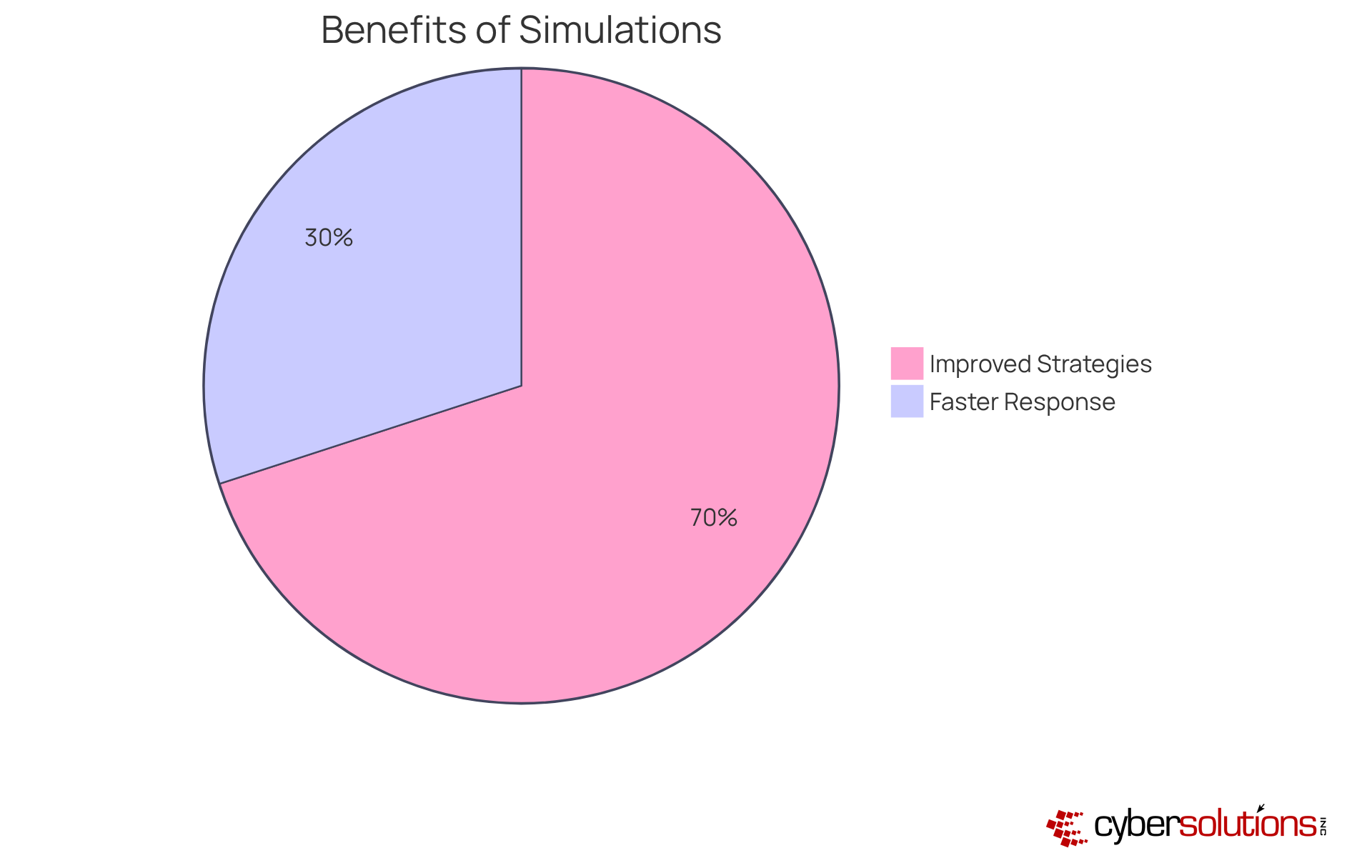
Cyber attack simulation exercises are not just beneficial; they are essential for any organization aiming to safeguard its digital assets. These cyber attack simulation exercises immerse employees in realistic scenarios that mirror potential cyber events, clarifying individual roles during crises and significantly enhancing response times and decision-making capabilities. Organizations that regularly participate in a cyber attack simulation exercise report a staggering 70% reduction in security incidents. This statistic alone underscores the effectiveness of such training methods. Moreover, employees who participate in cyber attack simulation exercises are 30% less likely to fall victim to phishing attempts, illustrating the long-term advantages of fostering a security-conscious workforce.
Consider the City of Mission's experience with the CyManII program. After just two days of the cyber attack simulation exercise, participants observed a significant improvement in their readiness to address real-world threats. This highlights the critical role of practice and muscle memory in developing a cohesive response team. Such training not only equips employees for immediate challenges but also cultivates a culture of security awareness, empowering them to proactively identify and mitigate potential threats.
As cyber threats continue to evolve, the necessity for organizations to invest in cyber attack simulation exercises as realistic training scenarios becomes increasingly evident. Interactive experiences not only enhance employee skills but also instill a sense of responsibility and vigilance. This ultimately leads to a more robust organizational stance against cyber threats. Are you ready to take action and strengthen your cybersecurity posture?

Cyber attack simulation exercises are not just beneficial; they are essential for evaluating and enhancing emergency response plans. In a world where cyber threats are ever-evolving, organizations must participate in a cyber attack simulation exercise to critically assess their response strategies. This iterative approach not only prepares teams for real events but also significantly reduces response times and mitigates potential damage.
Consider this: organizations that conduct incident response drills at least quarterly respond 35% faster to incidents. This statistic underscores the tangible benefits of regular practice. Furthermore, 70% of businesses that engage in practice exercises report improved response strategies, demonstrating the effectiveness of these proactive measures. By involving all essential personnel, including executives, in these exercises, organizations foster teamwork and ensure a comprehensive understanding of roles during a crisis.
As cyber threats continue to advance, those who prioritize cyber attack simulation exercises will be better equipped to navigate the complexities of modern cybersecurity challenges. Additionally, entities with a structured response strategy experience an average breach lifecycle of just 189 days. This statistic emphasizes the critical need for regular testing and updates to response plans to maintain their effectiveness.
In conclusion, the importance of cyber attack simulation exercises cannot be overstated. They are a vital component in safeguarding organizations against the increasing tide of cyber threats.
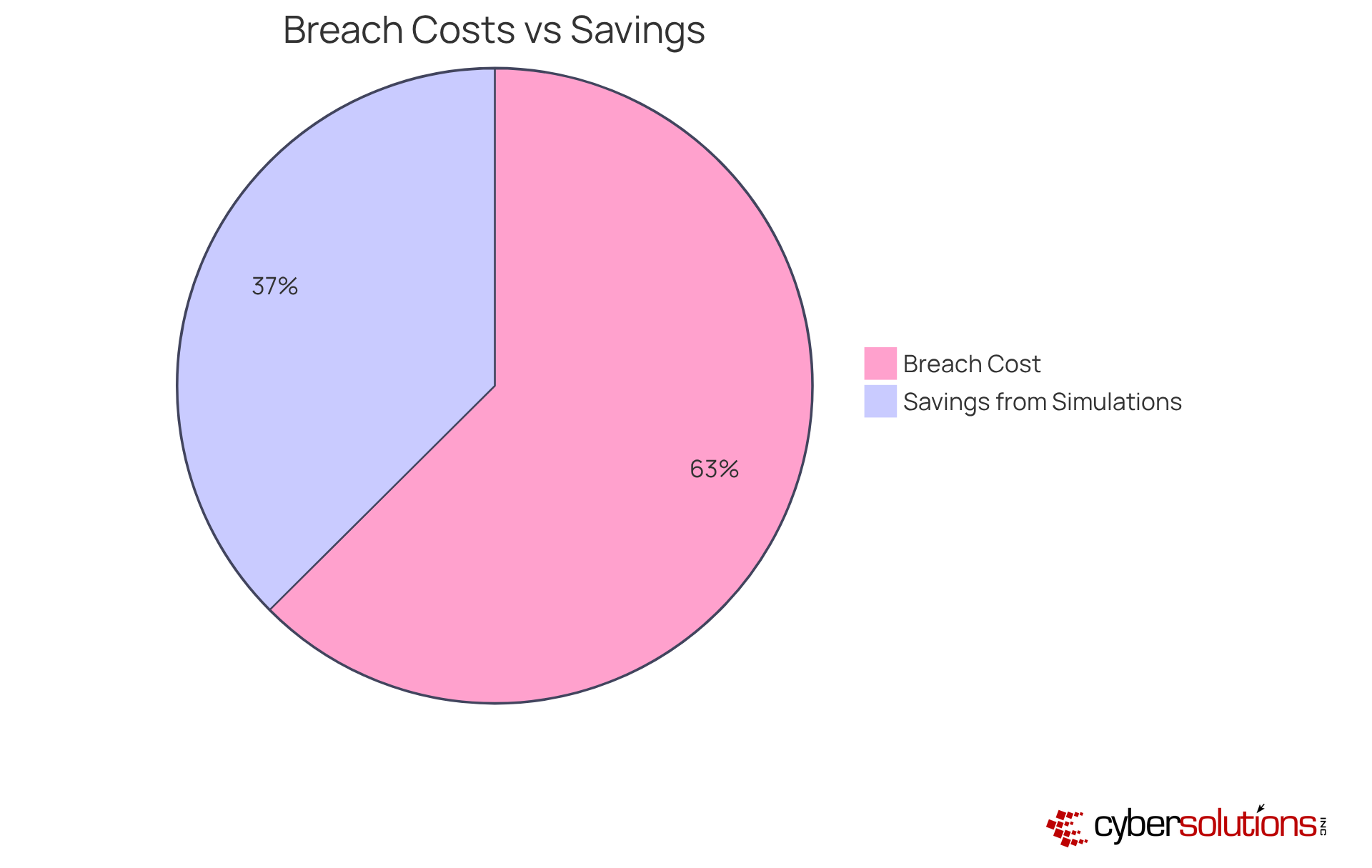
Investing in a cyber attack simulation exercise is not just a precaution; it’s a strategic move that can lead to significant cost reductions by effectively preventing cyber breaches. In today’s landscape, where the average cost of a data breach reached approximately $4.44 million in 2025, the stakes are undeniably high. Organizations can dramatically lower the chances of successful intrusions, which often result in severe financial repercussions, by identifying vulnerabilities and rigorously testing incident response strategies in a cyber attack simulation exercise.
Consider this: entities that regularly conduct intrusion exercises have reported reductions in breach expenses by as much as 61%, translating to savings of around $2.66 million. This proactive approach not only fortifies security measures but also cultivates a culture of readiness through a cyber attack simulation exercise, ensuring that organizations are well-prepared to face the ever-evolving cyber threats.
Moreover, these exercises allow companies to allocate resources more strategically, enhancing their return on investment in cybersecurity initiatives. As the cyber threat landscape continues to grow, can your organization afford to overlook the importance of conducting a cyber attack simulation exercise as a proactive measure? By embracing cyber intrusion exercises, you not only protect your financial well-being but also position your organization as a leader in cybersecurity preparedness.
Cyber attack simulation exercises are crucial for organizations seeking a strategic advantage against evolving cyber threats. In today’s landscape, where cybercriminals are increasingly sophisticated, regularly testing defenses against the latest attack vectors allows businesses to adapt their security measures proactively. This not only strengthens their security posture but also positions them as leaders in cybersecurity resilience.
Consider this: entities that engage in regular tabletop exercises have reported marked improvements in their incident response capabilities. They can identify and rectify vulnerabilities before they become exploitable. With the average cost of a data breach now exceeding $4.88 million, the financial implications of neglecting such exercises are staggering. As cybercriminals leverage advanced tactics, including generative AI, it’s imperative for companies to prioritize cyber attack simulation exercises to stay ahead of potential threats.
Moreover, fostering collaboration between technical and non-technical teams during these exercises enhances overall preparedness. It ensures that all stakeholders are aware of their roles in a crisis. This collaborative approach not only improves incident response but also strengthens the organization’s culture of security awareness. By integrating expert malware eradication and system restoration services from Cyber Solutions, each compromised endpoint is meticulously cleaned, patched, and reimaged as necessary.
This comprehensive strategy not only mitigates risks but also reinforces proactive network hardening techniques and optimizes security configurations. In a world where the stakes are high, investing in a cyber attack simulation exercise is not just a precaution; it’s a necessity for safeguarding the future.
Cyber attack simulation exercises are essential for fostering teamwork among members, significantly enhancing communication and coordination during cyber events. By engaging cross-functional teams in the cyber attack simulation exercise, organizations can dismantle silos and ensure that all participants have a clear understanding of their roles and responsibilities. This collaborative approach not only bolsters response efforts but also cultivates a robust security culture within the organization.
Entities that conduct regular tabletop exercises report improved communication pathways, which are vital during high-pressure situations. These cyber attack simulation exercises allow teams to rehearse emergency response protocols in a realistic environment, greatly improving response times and efficiency. As Christopher Brown, a Single Sign-On Expert, points out, these drills reveal vulnerabilities and weaknesses in security infrastructures that might otherwise remain hidden, ultimately leading to a more resilient organization.
Given that cyber incidents and their associated costs have surged since 2020, the importance of implementing a cyber attack simulation exercise cannot be overstated. Moreover, businesses leveraging AI for prevention have seen average savings exceeding $2 million, underscoring the financial benefits of investing in cybersecurity strategies, including these exercises. Consistent cyber attack simulation exercises not only help organizations stay protected from the repercussions of cyber incidents but also allow them to tailor scenarios to address specific threats, ensuring a comprehensive strategy for incident readiness.
In today's digital landscape, frequent cyber attack simulation exercises are not just beneficial; they're essential for strengthening a company's cybersecurity posture. These exercises yield critical insights into the effectiveness of existing security measures and pinpoint specific areas ripe for improvement. Organizations that engage in continuous drills are significantly better equipped to anticipate and mitigate potential threats, ensuring their defenses remain robust in an ever-evolving cyber environment.
Consider this: firms that conduct regular exercises report a remarkable enhancement in their security protocols. In fact, 72.7% of these entities recognize ransomware as a major threat and adapt their strategies accordingly. Moreover, organizations that conduct a cyber attack simulation exercise can slash incident response times by 30% through improved internal communication protocols. By embedding these drills into their security culture, companies can proactively tackle vulnerabilities, refine their security strategies, and ultimately cultivate a more resilient defense against cyber threats.

Cyber attack simulation exercises are essential in today’s cybersecurity landscape, equipping organizations with the necessary tools to tackle a wide range of digital threats. These exercises are not just beneficial; they are crucial for enhancing resilience, ensuring compliance, and strengthening defenses against increasingly sophisticated cybercriminal tactics.
The numerous advantages of cyber attack simulations cannot be overstated. They help identify vulnerabilities within security frameworks, improve employee training, and refine incident response strategies. By fostering a proactive approach to cybersecurity, organizations that regularly engage in these exercises report significant reductions in security incidents, improved communication during crises, and substantial cost savings by preventing breaches.
As cyber threats continue to rise, the need for organizations to adopt cyber attack simulation exercises becomes increasingly clear. By prioritizing these simulations, businesses not only safeguard their assets but also cultivate a culture of readiness and resilience. Embracing this proactive strategy is vital for any organization aiming to navigate the complexities of modern cybersecurity challenges effectively. The time to act is now-fortify your defenses and ensure preparedness against the next wave of cyber threats.
What are cyber attack simulation services offered by Cyber Solutions Inc.?
Cyber Solutions Inc. provides a comprehensive suite of cyber threat rehearsal services, including cyber attack simulation exercises that replicate real-world attack scenarios to help organizations assess their defenses and incident response strategies.
Why are cyber attack simulations important for organizations?
Cyber attack simulations are essential for enhancing organizational resilience against increasing cyber threats. They help uncover vulnerabilities, improve response capabilities, and foster a culture of continuous improvement in cybersecurity practices.
How do cyber attack simulations enhance cybersecurity preparedness?
Regular participation in cyber attack simulations enables organizations to adapt to evolving threats, improve their security posture, and ensure that teams are better equipped to handle real-world challenges.
What role does AI play in cyber attack simulations?
Recent advancements in AI-driven platforms allow security teams to develop and simulate complex threat scenarios in real-time, ensuring continuous exposure validation as cyber threats evolve.
How can application allowlisting improve cybersecurity defenses?
Implementing application allowlisting proactively blocks unauthorized software, minimizes exposure to threats, and helps ensure compliance with regulations like HIPAA and GDPR.
What benefits have organizations reported after participating in cyber attack simulations?
Organizations that have engaged in cyber attack simulations report improved response times, heightened awareness of security vulnerabilities, and enhanced threat detection capabilities.
How do cyber attack simulations contribute to regulatory compliance?
Cyber attack simulations help organizations rigorously assess their readiness to meet compliance requirements across standards like HIPAA, PCI-DSS, and GDPR, revealing compliance gaps and providing actionable insights for remediation.
What are the outcomes of conducting thorough debriefings after simulations?
Conducting debriefings after cyber attack simulations is vital for identifying successes and areas for improvement, leading to a more effective incident response and enhanced security protocols.
What is the financial impact of cyber threats on healthcare organizations?
Healthcare entities face significant financial risks, with breach costs averaging $10.93 million per incident, highlighting the importance of preparedness through cyber attack simulations.
How can organizations start strengthening their cybersecurity defenses?
Organizations can fortify their defenses by investing in cyber attack simulation exercises as part of their cybersecurity strategy to safeguard assets and build resilience against evolving cyber threats.