
In today's world, where cyber threats are more prevalent than ever, robust cybersecurity measures have evolved from a technical necessity to a strategic imperative, especially for healthcare organizations. The stakes are high; sensitive patient data is constantly at risk, and the consequences of a breach can be devastating. Managed services security companies like Cyber Solutions provide a comprehensive suite of solutions that not only protect this vital information but also enhance operational efficiency.
As healthcare leaders navigate the complexities of compliance and risk management, they must ask themselves: how can partnering with specialized services empower their organizations to effectively tackle the evolving landscape of cybersecurity? The answer lies in leveraging the expertise of firms like Cyber Solutions, which are equipped to safeguard both reputation and patient trust.
By understanding the unique challenges faced by CFOs in the healthcare sector, organizations can make informed decisions that prioritize security without compromising on care. Cyber Solutions stands ready to assist in this critical endeavor, ensuring that healthcare providers can focus on what they do best - caring for patients - while leaving the intricacies of cybersecurity to the experts.
In today's digital age, cybersecurity is not just an IT issue; it's a critical concern for healthcare organizations that often rely on managed services security companies. With the rise of sophisticated cyber threats, CFOs face unique challenges in safeguarding sensitive patient data and ensuring compliance with stringent regulations. Cyber Solutions Inc. stands out with a robust suite of managed protection services designed to shield enterprises from these emerging risks.
Their offerings include:
This service simplifies the complexities of regulatory requirements such as HIPAA, PCI-DSS, and GDPR, allowing healthcare organizations to focus on what they do best - providing quality care. Moreover, their incident response solutions are engineered to quickly identify, contain, and mitigate threats, ensuring operational continuity in the face of adversity.
By leveraging advanced technologies and expert knowledge, managed services security companies like Cyber Solutions empower organizations to navigate the intricate landscape of cybersecurity effectively. This enables organizations to maintain a robust security posture while concentrating on their core operations. In a world where cyber threats are ever-evolving, partnering with Cyber Solutions is not just a choice; it's a necessity for any healthcare organization committed to protecting its patients and its reputation.
In today's digital landscape, cybersecurity is not just an option; it's a necessity for healthcare organizations. With the rise of cyber threats, including ransomware and phishing attacks, the stakes have never been higher. Cyber Solutions offers 24/7 help desk support, ensuring that businesses have immediate access to expert assistance for any IT or security-related issues. This service, combined with our ongoing network surveillance, allows for the quick identification and response to potential risks, significantly reducing downtime and protecting sensitive information.
Our proactive approach includes instant alerts and real-time insights, enabling swift action against anomalies and vulnerabilities. Organizations can feel confident knowing that expert assistance is readily available, enhancing their overall security posture. But how prepared is your organization to face these evolving threats? Tailored access controls and restrictions are essential to ensure that only authorized users can access sensitive information.
To bolster your cybersecurity strategy, consider regularly assessing and modifying your access controls to adapt to changing risks. By doing so, you not only safeguard your data but also demonstrate a commitment to maintaining the highest standards of security in an increasingly complex environment.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated. Cyber Solutions offers strong endpoint protection that effectively safeguards devices against a myriad of cyber risks, including malware, ransomware, and phishing attacks. With 90% of successful cyberattacks and up to 70% of data breaches originating from endpoint devices, the urgency for organizations to implement enhanced protective measures is clear.
Adopting a proactive strategy for endpoint protection, such as application allowlisting, significantly reduces the risk of data breaches while ensuring compliance with industry regulations. Organizations that have invested in comprehensive endpoint protection, including allowlisting, have reported substantial reductions in successful attacks. This proactive approach not only fortifies defenses but also instills confidence in stakeholders.
Statistics reveal that 68% of organizations have encountered endpoint attacks that compromised their data or IT infrastructure. This alarming figure underscores the pressing need for companies to bolster their security posture. By prioritizing endpoint protection and employing strategies like application allowlisting, organizations can safeguard sensitive information, maintain business continuity, and foster a secure operational environment.
In conclusion, the evolving threat landscape necessitates a decisive response. Cyber Solutions stands ready to assist organizations in navigating these challenges, ensuring that they are equipped to protect their endpoints and secure their operations.

In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in healthcare. Cyber Solutions leverages advanced risk detection technologies to proactively identify and mitigate cyber risks. By continuously monitoring network activity and assessing potential threats, organizations can significantly reduce the time it takes to detect and respond to cyber dangers. This is crucial in an environment where threats evolve rapidly.
The implications for healthcare organizations are profound. A proactive approach not only enhances security but also ensures compliance with regulatory requirements. Timely responses can prevent incidents from escalating into major breaches, safeguarding sensitive patient data and maintaining trust. Efficient risk identification strategies empower businesses to foster a culture of security awareness, which is essential in today’s interconnected world.
Moreover, by anticipating potential threats, organizations can allocate resources more effectively and implement robust risk management practices. This not only reinforces their overall cybersecurity posture but also preserves customer confidence. In a sector where data integrity is paramount, Cyber Solutions stands ready to help organizations navigate these challenges effectively, ensuring a secure future for healthcare.
In today's complex regulatory environment, Compliance as a Service (CaaS) from Cyber Solutions empowers organizations to navigate the intricate landscape of regulatory adherence with confidence. By outsourcing compliance management, businesses can align seamlessly with industry standards like HIPAA, PCI-DSS, and GDPR, alleviating the burden of maintaining extensive in-house resources. This strategic approach not only mitigates the risks associated with non-compliance but also allows organizations to concentrate on their core objectives.
As compliance specialist Marc Haskelson notes, adopting a proactive strategy towards compliance is essential for organizations aiming to safeguard their operations and bolster resilience against potential legal challenges. Moreover, companies that implement CaaS solutions frequently report enhanced operational efficiency and reduced costs tied to compliance management. This reinforces the idea that investing in compliance is not just a necessity; it's an investment in the future of the brand.
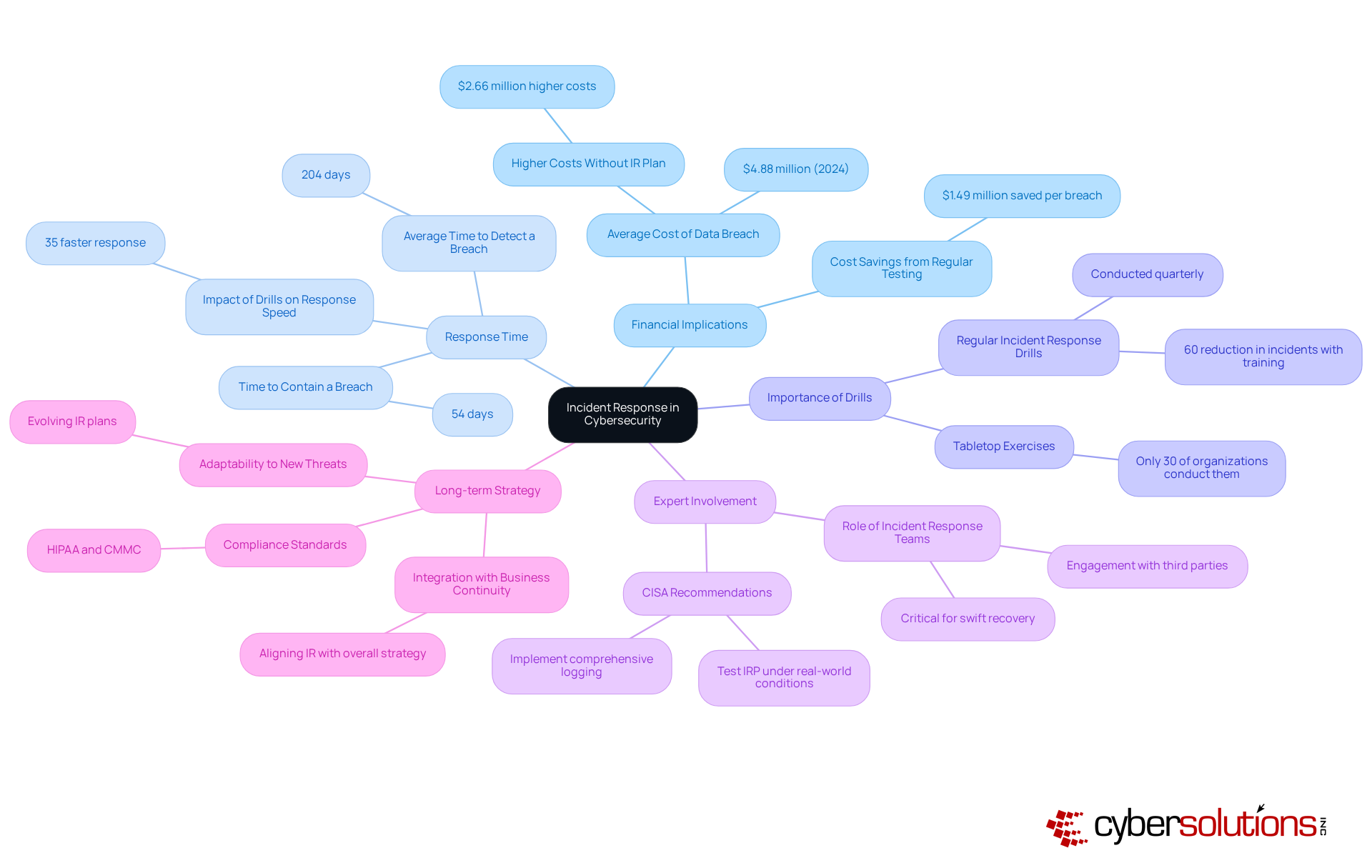
Cyber Solutions offers extensive incident response services that empower organizations to recover swiftly from cyber incidents. In the ever-evolving digital landscape, where the average cost of a data breach reached a staggering $4.88 million in 2024, having a well-structured incident response plan is not just beneficial - it's essential. The financial implications of downtime can be overwhelming, especially for companies lacking a dedicated incident response team, which face breach costs that are $2.66 million higher than those with established protocols. Rapid recovery not only mitigates immediate losses but also preserves customer trust and operational integrity.
Consider this: organizations that conduct regular incident response drills can react 35% faster to incidents, significantly reducing the duration and impact of breaches. Take, for instance, the healthcare provider that Cyber Solutions assisted during a ransomware attack. Their swift action, coupled with the presence of an incident response team within 24 hours, helped contain the threat and restore operations ahead of schedule. This case underscores the critical importance of immediate action, specialized expertise, and a structured response plan when facing ransomware. Moreover, companies that implement changes based on past incidents can reduce future incident rates by an impressive 50%.
Expert insights reveal that incorporating incident response planning into the overall strategy is vital for resilience. This approach allows organizations to shift from crisis to control effectively. By prioritizing incident response, organizations can not only recover swiftly but also enhance their long-term protective stance, ensuring compliance with standards such as HIPAA and CMMC.
In conclusion, the landscape of cybersecurity threats is daunting, but with the right strategies in place, organizations can navigate these challenges effectively. Cyber Solutions stands ready to assist in fortifying your defenses and ensuring a robust incident response plan is in place.
In today’s digital landscape, the importance of cybersecurity cannot be overstated, especially in healthcare. Cyber Solutions performs extensive vulnerability evaluations to identify and address flaws within an organization's IT infrastructure. By routinely evaluating systems and applications, businesses can proactively tackle vulnerabilities, significantly lowering the risk of cyberattacks. This continuous assessment process is essential for maintaining a robust protection framework and ensuring compliance with evolving regulatory standards, such as CMMC Level 3.
Achieving compliance at this level demonstrates a commitment to cybersecurity and the ability to protect sensitive federal data, which is crucial for maintaining eligibility for lucrative government contracts. Currently, about 68% of entities prioritize regular evaluations, recognizing their vital role in detecting potential risks before they can be exploited. Implementing optimal methods, such as maintaining an asset inventory and prioritizing risks, further enhances the efficiency of these evaluations. This proactive approach allows organizations to stay ahead of emerging cyber threats and strengthen their overall protective stance.
Are you ready to fortify your organization against cyber threats? Cyber Solutions is here to help you navigate these challenges effectively.
In today's digital landscape, cybersecurity is not just an option; it's a necessity for organizations aiming to thrive. Employing managed services security companies, such as Cyber Solutions, significantly enhances defensive capabilities and operational efficiency. With access to cutting-edge technologies and expert insights, organizations can effectively navigate the ever-evolving threats they face.
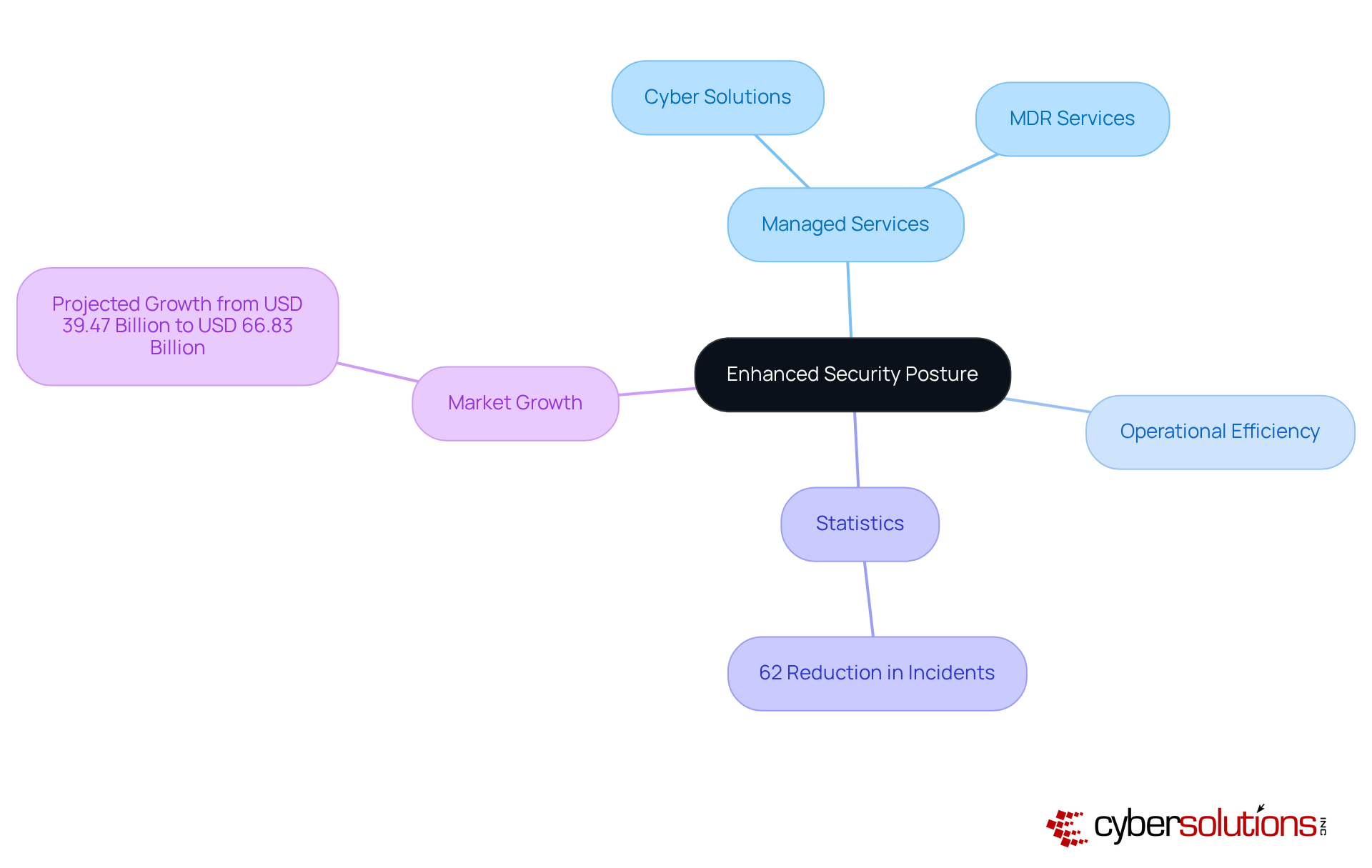
A robust protection framework does more than just shield sensitive information; it fosters business growth and innovation. For instance, organizations leveraging Managed Detection and Response (MDR) services have seen a remarkable 62% reduction in annual incidents. This statistic underscores the effectiveness of proactive measures in streamlining operations. IT leaders consistently emphasize that investing in cyber defense is crucial for operational efficiency. Many have noted that insufficient protection budgets hinder their ability to safeguard critical assets.
The market for managed services security companies is projected to grow from USD 39.47 billion in 2025 to USD 66.83 billion by 2030, reflecting a growing recognition of cybersecurity as a vital component of operational success. By integrating managed protection services, companies can not only mitigate risks but also simplify processes, ultimately transforming IT into a powerful, ROI-generating asset.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated. Managed services security companies, such as Cyber Solutions, provide companies with a cost-efficient strategy to bolster their cybersecurity measures while simplifying budgeting through a flat-rate pricing model. This model ensures predictable monthly expenses, eliminating unexpected IT costs and surprises. As a result, businesses can allocate their resources more effectively, reducing the need for internal resources that often lead to high costs associated with recruiting, training, and retaining personnel. This shift not only yields significant financial savings but also ensures that strong protective measures remain firmly in place.
The financial repercussions of cyber incidents can be staggering. Organizations without managed protection frequently face steep recovery costs, operational disruptions, and potential regulatory fines. In fact, companies that engage managed services security companies can save an average of 25% compared to managing operations internally, benefiting from fixed service levels that mitigate unforeseen expenses from breaches.
Consider this: companies that have outsourced their cybersecurity functions report enhanced operational clarity and improved compliance, which further strengthens client relationships and builds trust. The critical importance of immediate action and specialized expertise is underscored by case studies demonstrating effective ransomware response strategies. By employing a layered approach - including endpoint isolation, malware removal, and user training - organizations not only safeguard their digital assets but also promote tangible results such as cost optimization and enhanced efficiency. This proactive cybersecurity strategy guarantees minimal operational disruption and fosters strong partnerships, enabling businesses to focus on growth and innovation while maintaining a robust protective stance.

In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in critical sectors like healthcare. With the rise of sophisticated cyber threats, healthcare organizations face unique challenges that demand tailored protective solutions provided by managed services security companies. Cyber Solutions understands these challenges and provides customized IT services designed to ensure compliance with stringent regulations while safeguarding sensitive data.
Our extensive cybersecurity offerings include:
These solutions proactively prevent malware and unauthorized software from executing, significantly enhancing the effectiveness of security measures. By addressing the specific vulnerabilities of each sector, we not only minimize risks but also foster trust with our clients.
As healthcare organizations navigate an increasingly complex threat landscape, partnering with managed services security companies ensures they can operate securely. Our personalized approach not only meets regulatory requirements but also empowers organizations to focus on their core mission - delivering quality care to patients. Don't leave your cybersecurity to chance; let Cyber Solutions fortify your defenses today.
In today's rapidly evolving cybersecurity landscape, the critical role of managed services security companies, particularly Cyber Solutions, stands out. With sophisticated cyber threats on the rise, organizations - especially in the healthcare sector - must prioritize robust protection to safeguard sensitive data and maintain compliance with stringent regulations. Cyber Solutions not only provides essential security measures but also allows businesses to focus on their core operations, ensuring they can navigate the complexities of cybersecurity effectively.
Key benefits of partnering with managed services security companies include:
By leveraging advanced technologies and expert insights, organizations can significantly reduce their exposure to cyber risks while improving operational efficiency. The proactive strategies offered empower businesses to identify vulnerabilities, respond swiftly to incidents, and ensure compliance with industry standards, ultimately safeguarding vital assets and maintaining customer trust.
As cyber threats continue to evolve, the importance of collaborating with managed services security companies cannot be overstated. Organizations are urged to take proactive steps in fortifying their cybersecurity measures and to consider the long-term advantages of such partnerships. Embracing these managed services not only protects critical assets but also positions businesses for sustainable growth and innovation in an increasingly digital world.
What services does Cyber Solutions Inc. offer for cybersecurity?
Cyber Solutions Inc. offers a suite of managed security services including 24/7 help desk support, endpoint protection, and compliance as a service (CaaS).
How does Cyber Solutions help with compliance?
Cyber Solutions simplifies regulatory requirements such as HIPAA, PCI-DSS, and GDPR through their compliance as a service (CaaS), allowing healthcare organizations to focus on providing quality care.
What is the significance of 24/7 help desk support?
The 24/7 help desk support ensures immediate access to expert assistance for IT or security-related issues, facilitating quick identification and response to potential risks, thus reducing downtime and protecting sensitive information.
What types of cyber threats does endpoint protection guard against?
Endpoint protection safeguards devices against various cyber threats, including malware, ransomware, and phishing attacks.
Why is endpoint protection crucial for organizations?
Endpoint protection is crucial because 90% of successful cyberattacks and up to 70% of data breaches originate from endpoint devices, making it essential for organizations to implement robust protective measures.
What proactive strategy can organizations employ for endpoint protection?
Organizations can adopt application allowlisting as a proactive strategy to significantly reduce the risk of data breaches while ensuring compliance with industry regulations.
What statistics highlight the need for enhanced endpoint protection?
Statistics indicate that 68% of organizations have encountered endpoint attacks that compromised their data or IT infrastructure, underscoring the urgent need for improved security measures.
How does Cyber Solutions empower organizations in cybersecurity?
By leveraging advanced technologies and expert knowledge, Cyber Solutions helps organizations navigate the complex landscape of cybersecurity, enabling them to maintain a robust security posture while focusing on their core operations.