
The regulatory landscape is becoming increasingly complex, with businesses struggling to keep up with a multitude of compliance requirements, including GDPR, HIPAA, and PCI-DSS. As organizations work to maintain operational integrity amidst these evolving standards, the significance of managed IT compliance services is paramount. How can businesses not only protect themselves from the risks of non-compliance but also turn these services into a strategic advantage in a competitive market?
In today’s environment, the stakes are high. Non-compliance can lead to severe penalties, reputational damage, and operational disruptions. Organizations must navigate these challenges with precision and foresight. Managed IT compliance services offer a pathway to not only meet regulatory demands but also enhance overall business resilience.
By leveraging these services, companies can streamline their compliance processes, reduce risks, and focus on their core operations. This proactive approach not only safeguards against potential pitfalls but also positions businesses to thrive in a landscape where compliance is increasingly scrutinized.
In conclusion, the importance of managed IT compliance services cannot be overstated. They are not merely a safeguard against non-compliance; they are a strategic asset that can drive competitive advantage. As the regulatory landscape continues to evolve, organizations must prioritize these services to ensure their long-term success.
The regulatory landscape has transformed into a complex web of requirements, driven by rapid technological advancements, heightened consumer expectations, and evolving legal frameworks. Organizations now face the daunting task of navigating a multitude of regulations, including GDPR, HIPAA, and PCI-DSS, each imposing distinct adherence obligations. The emergence of data privacy laws across various jurisdictions adds another layer of complexity, compelling businesses to balance local compliance with the demands of global operations. This intricate environment underscores the necessity for a robust regulatory strategy, encompassing services such as risk assessments and policy development offered by Cyber Solutions.
Experts assert that a proactive approach is essential for organizations to effectively tackle these challenges. Adjusting to the shifting demands of GDPR, HIPAA, and PCI-DSS is not merely a legal obligation; it’s a strategic necessity that can enhance brand reputation and foster customer trust. How prepared is your organization to meet these evolving standards?
Technological advancements are pivotal in this adherence journey. Automation and AI tools are increasingly leveraged to streamline regulatory processes, minimize manual errors, and ensure real-time monitoring of regulatory changes. Companies that successfully integrate these technologies into their regulatory frameworks can significantly boost their operational efficiency and risk management capabilities.
Successful examples abound, particularly in the healthcare sector, where organizations have implemented robust adherence programs to comply with HIPAA regulations. These initiatives often feature comprehensive staff training, regular audits, and advanced data protection technologies to safeguard sensitive information. Such proactive measures not only ensure compliance but also cultivate a culture of responsibility and trust within the organization.
In this rapidly evolving regulatory landscape, managed IT compliance service providers, such as Cyber Solutions, emerge as vital partners for organizations striving to navigate the complexities of compliance while maintaining operational integrity. Are you ready to take the next step in fortifying your compliance strategy?
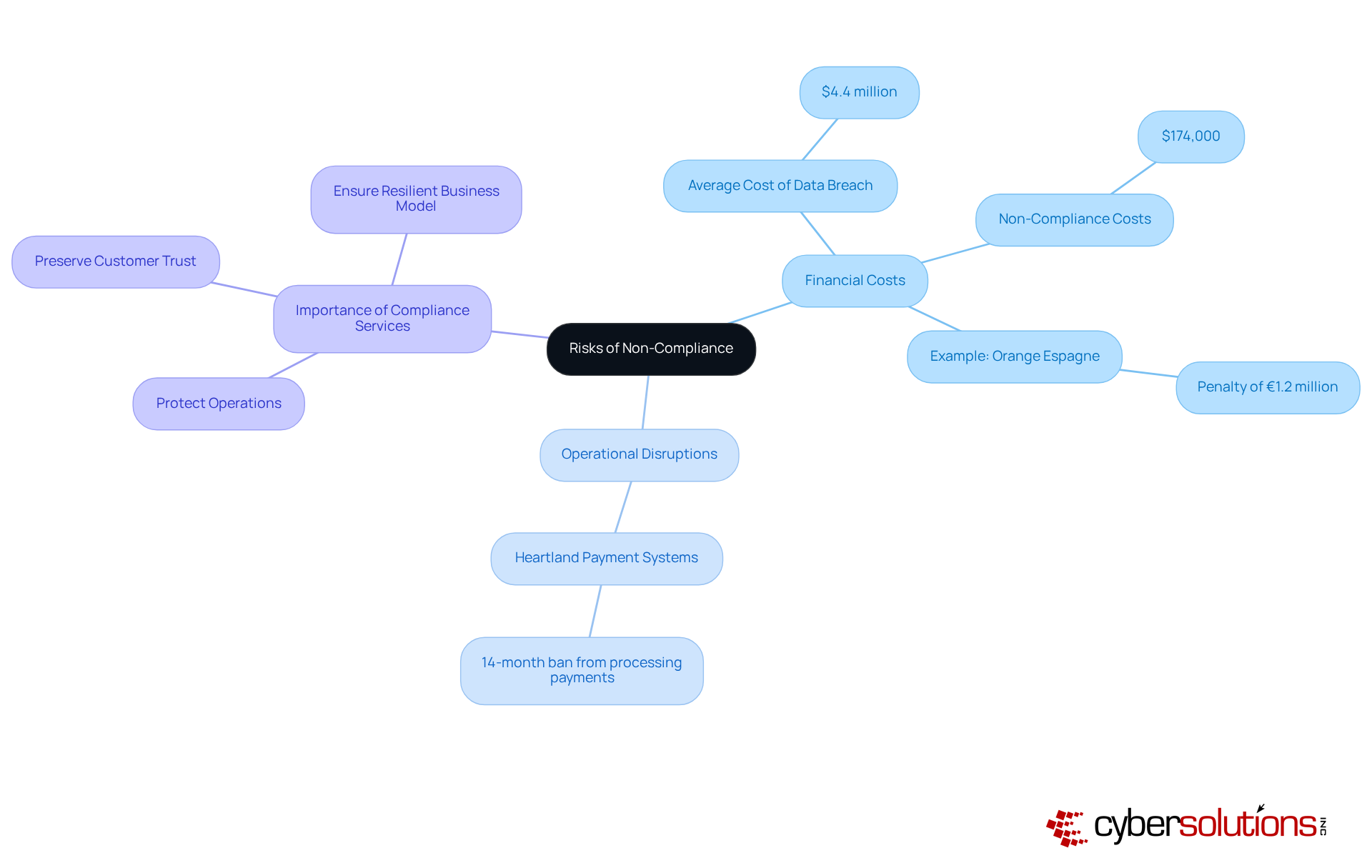
Non-compliance poses serious risks that can jeopardize a company's future. With the average cost of a data breach projected to soar to $4.4 million by 2025, organizations must recognize the additional $174,000 in costs tied to non-compliance. Take, for example, the €1.2 million penalty imposed on Orange Espagne for multiple GDPR violations; this case starkly illustrates the financial perils at stake. Moreover, operational disruptions from data breaches can cripple business functionality. Heartland Payment Systems experienced this firsthand, enduring a 14-month ban from processing credit card payments following a major breach in 2008.
The expenses associated with rectifying regulatory failures often far exceed the resources required for proactive regulatory management. By acknowledging these uncertainties, companies can grasp the critical importance of managed IT compliance services. Such services not only protect operations but also preserve customer trust, ensuring a resilient business model in an increasingly complex cybersecurity landscape.
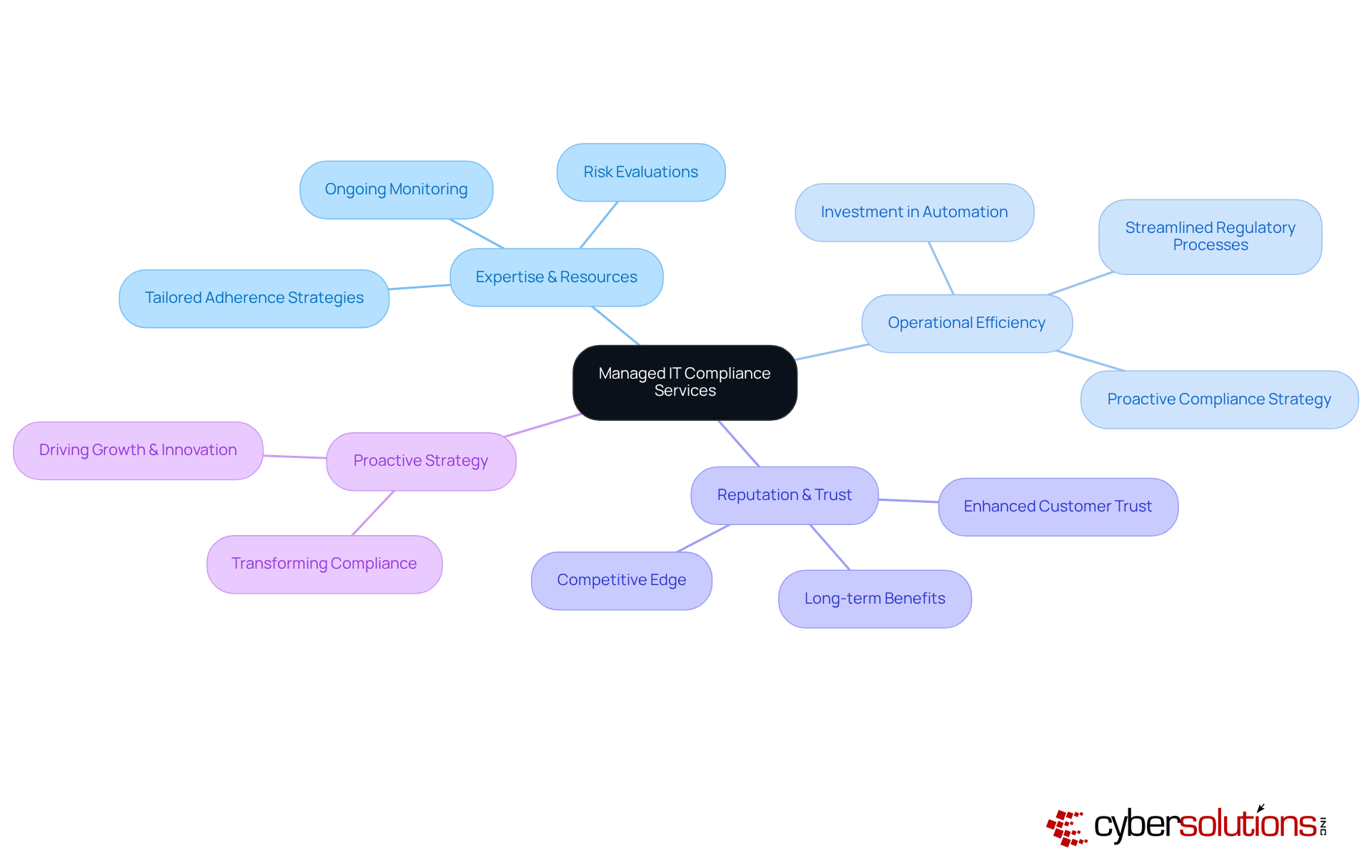
Outsourcing regulatory management is crucial for organizations aiming to navigate the complex legal landscape effectively while focusing on their core operations. Managed IT compliance service offers essential expertise and resources, including ongoing monitoring, risk evaluations, and tailored adherence strategies that align with industry standards. In 2025, companies prioritizing regulatory compliance will not only safeguard their operations but also enhance their reputation and build customer trust - key elements for securing a competitive edge.
Consider this: organizations that have embraced outsourcing for regulatory compliance report significant improvements in operational efficiency. In fact, 82% plan to invest more in automation to streamline regulatory processes. This shift transforms compliance from a reactive obligation into a proactive strategy that drives growth and innovation. Industry leaders assert that viewing regulatory adherence as a strategic asset rather than a burden can yield substantial long-term benefits, such as reduced costs linked to breaches and increased stakeholder confidence.
By leveraging a managed IT compliance service, businesses can ensure they remain agile and resilient in an increasingly regulated environment. Are you ready to take your compliance strategy to the next level?
In today's complex regulatory landscape, various sectors face unique challenges that demand tailored adherence solutions. For instance, healthcare entities must navigate stringent regulations concerning patient data privacy, while financial institutions grapple with rigorous anti-money laundering laws. Did you know that in 2025, 42% of entities recognized robust encryption and key management as vital facilitators of their digital sovereignty objectives? This statistic underscores the significance of customized regulatory strategies.
The managed IT compliance service can provide these tailored strategies, ensuring organizations stay compliant while minimizing threats. By personalizing adherence solutions, companies not only fulfill their legal obligations but also enhance operational efficiency and mitigate the risk of costly compliance failures. This customized approach is essential for organizations striving to excel in their respective fields while effectively navigating the complexities of regulatory requirements.
Leaders in healthcare and finance have expressed that such tailored strategies significantly improve compliance outcomes. This reinforces the necessity of adapting solutions to fit industry-specific needs. As the regulatory landscape continues to evolve, organizations must prioritize personalized adherence strategies to safeguard their operations and maintain a competitive edge.

Navigating the maze of regulatory compliance is no longer just an option for businesses; it has become a fundamental necessity for success. Managed IT compliance services are essential in helping organizations effectively meet the ever-evolving landscape of regulatory requirements. This ensures they remain competitive while safeguarding their operations and reputation.
The growing complexity of regulations such as GDPR, HIPAA, and PCI-DSS cannot be overlooked. The risks associated with non-compliance are significant, including hefty financial penalties and operational disruptions. By outsourcing compliance management, organizations can enhance efficiency and foster a culture of trust. Tailored compliance solutions that meet industry-specific needs can transform the way businesses operate.
As the regulatory environment continues to evolve, it’s crucial for businesses to recognize the importance of proactive compliance strategies. Investing in managed IT compliance services not only mitigates risks but also positions organizations for long-term success in an increasingly competitive marketplace. Embracing these services is not merely about compliance; it’s about transforming regulatory challenges into opportunities for growth and innovation.
What factors have contributed to the complexity of regulatory requirements?
The complexity of regulatory requirements has been driven by rapid technological advancements, heightened consumer expectations, and evolving legal frameworks.
What are some key regulations that organizations must navigate?
Organizations must navigate various regulations, including GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI-DSS (Payment Card Industry Data Security Standard).
Why is a robust regulatory strategy necessary for organizations?
A robust regulatory strategy is necessary to effectively manage the multitude of regulations, including conducting risk assessments and developing policies, which can enhance brand reputation and foster customer trust.
How can organizations prepare for evolving regulatory standards?
Organizations can prepare by adopting a proactive approach to adjust to the shifting demands of regulations like GDPR, HIPAA, and PCI-DSS, which is essential for legal compliance and strategic advantage.
What role do technological advancements play in regulatory compliance?
Technological advancements, particularly automation and AI tools, help streamline regulatory processes, minimize manual errors, and ensure real-time monitoring of regulatory changes, boosting operational efficiency and risk management.
Can you provide an example of successful regulatory compliance in a sector?
In the healthcare sector, organizations have implemented robust adherence programs to comply with HIPAA regulations, featuring comprehensive staff training, regular audits, and advanced data protection technologies.
How can managed IT compliance service providers assist organizations?
Managed IT compliance service providers, such as Cyber Solutions, can help organizations navigate the complexities of compliance while maintaining operational integrity, offering essential services to fortify compliance strategies.