Cybersecurity has become a pressing issue for small businesses, increasingly targeted by cybercriminals at alarming rates. The financial implications of cybersecurity are significant, with costs varying widely based on factors such as industry regulations and business size. With a staggering 60% of small businesses failing within six months of a cyberattack, the critical question arises: how can these organizations effectively balance the need for robust cybersecurity measures with their budget constraints?
This article explores the complexities of cybersecurity costs for small businesses, offering valuable insights and strategies to help them navigate this challenging landscape. By understanding the current cybersecurity threats and their implications, small businesses can take proactive steps to safeguard their operations and ensure their longevity in an increasingly digital world.
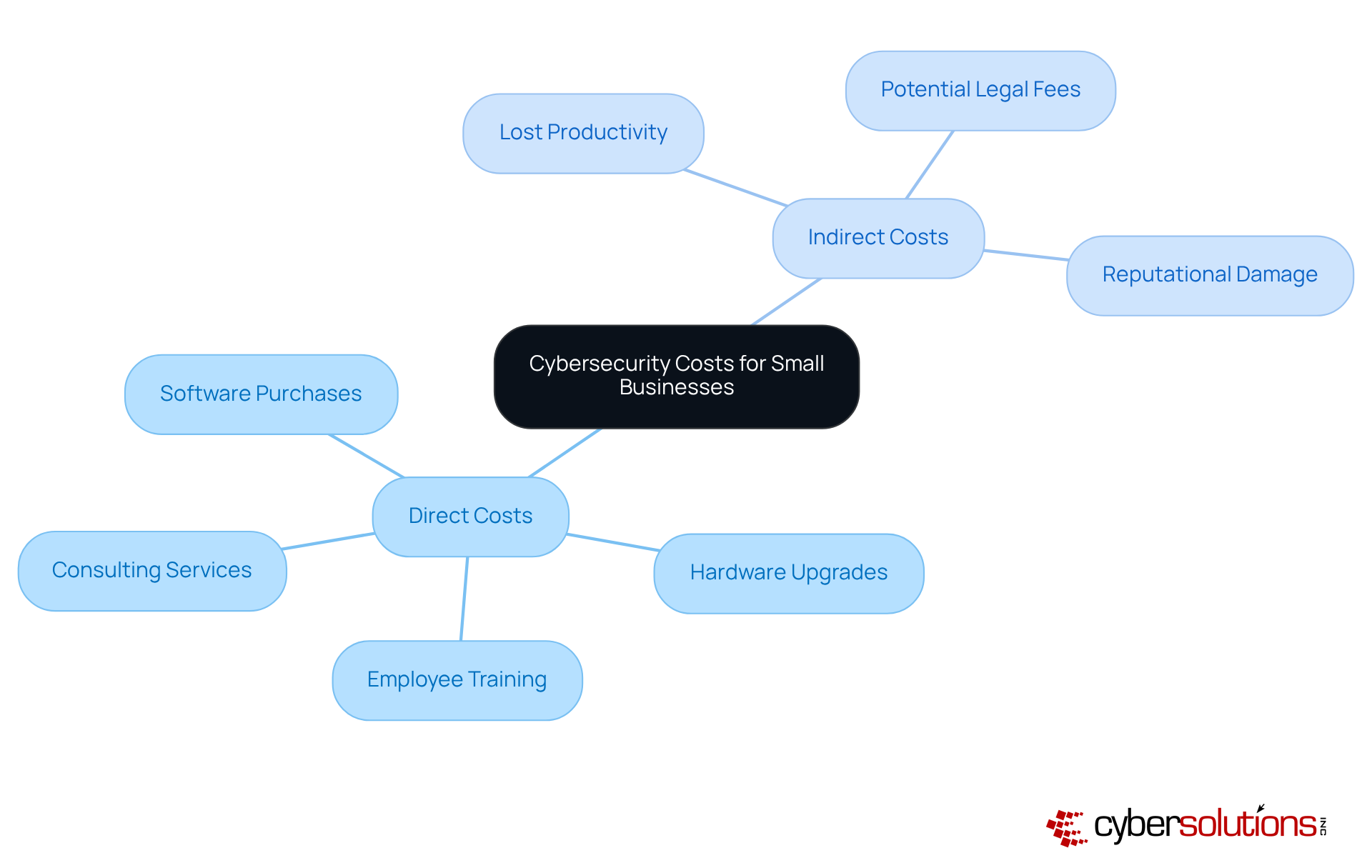
Cybersecurity is not just an option for minor enterprises; it’s a necessity. With minor enterprises facing cyberattacks 210 percent more often than larger firms, the stakes have never been higher. The cost of cybersecurity for small business can be categorized into direct and indirect expenses, both of which can significantly impact operations.
Direct costs encompass essential expenditures such as:
Typically, minor enterprises allocate between $5,000 and $50,000 annually for the cost of cybersecurity for small business, influenced by their size and industry requirements. However, the implications of neglecting cybersecurity can be severe. A data breach can lead to long-term financial repercussions, with costs ranging from $120,000 to $1.24 million. This stark reality underscores the importance of proactive security investments.
Indirect expenses also play a crucial role, including:
Alarmingly, 74% of minor enterprise owners either self-manage their online security or rely on unqualified individuals, which can exacerbate vulnerabilities. How can these businesses mitigate such risks?
Enter Cyber Solutions, offering a flat-rate pricing model that simplifies budgeting and eliminates unexpected IT costs. This model covers everything from email licenses to advanced security services, ensuring comprehensive protection. Additionally, understanding Compliance as a Service (CaaS) is vital for moderate-sized enterprises. CaaS provides robust solutions to meet regulatory requirements, helping organizations remain compliant and shielded from potential penalties.
This comprehensive approach not only safeguards operations but also enhances overall security strategies. By investing in cybersecurity, minor enterprises can protect their assets and ensure a more secure future.
Cybersecurity is not just a technical necessity; it’s a critical investment for small businesses navigating today’s digital landscape. Understanding the factors that influence the cost of cybersecurity for small businesses is essential for making informed decisions and safeguarding sensitive information.
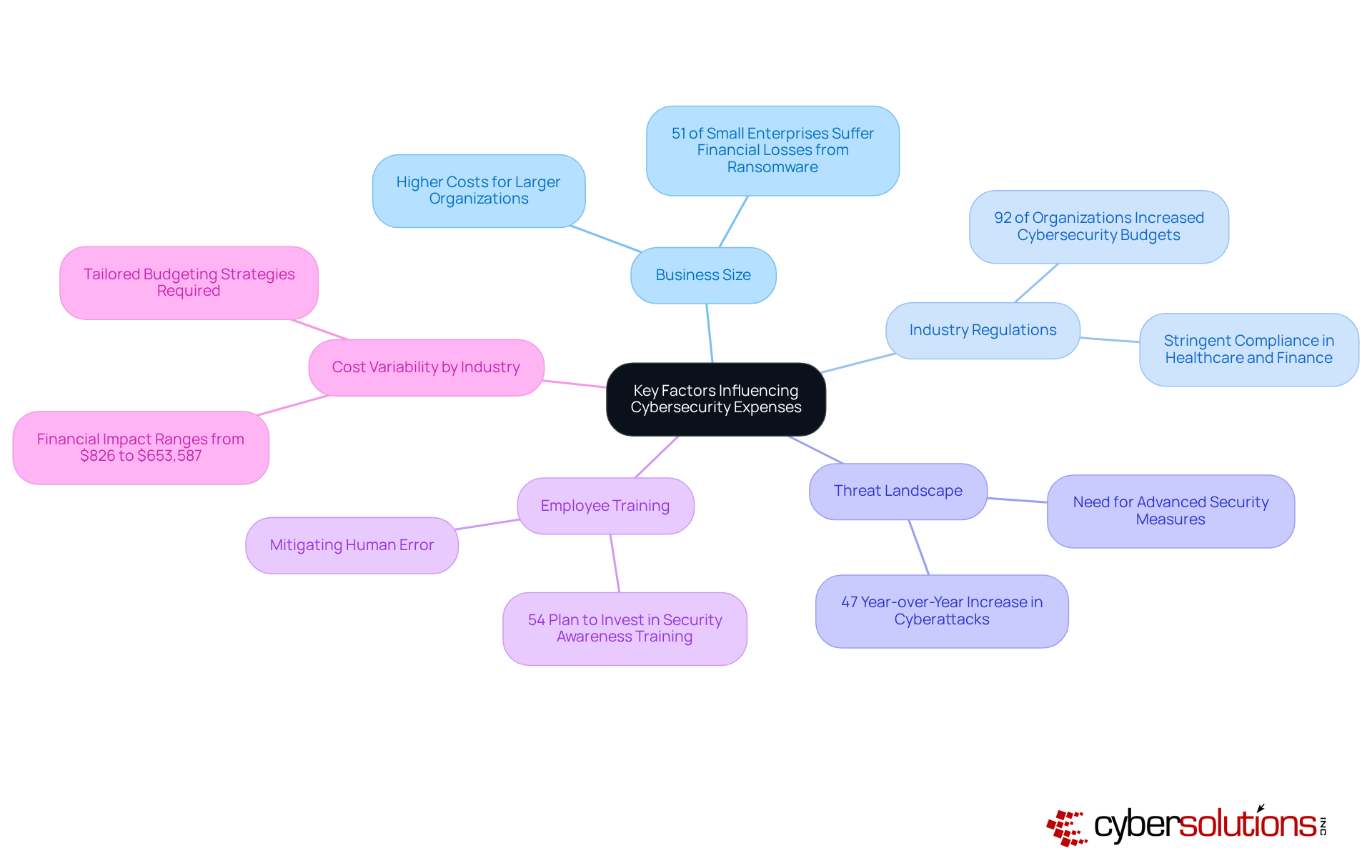
Business size plays a pivotal role in determining the cost of cybersecurity for small businesses. Larger organizations often face higher expenses due to their extensive networks and the volume of sensitive data they manage. For example, a staggering 51% of small enterprises that fall victim to ransomware report significant financial losses, underscoring the heightened risks associated with larger operations.
Industry Regulations further complicate the financial landscape. Compliance requirements differ across sectors, with industries like healthcare and finance facing stringent regulations that demand higher security investments. Approximately 92% of organizations have reported increased budget allocations for cybersecurity, driven by the need to meet regulatory compliance and manage emerging threats. This highlights the substantial financial implications of the cost of cybersecurity for small business requirements.
The Threat Landscape is ever-evolving, compelling organizations to invest in advanced security measures. Small businesses are particularly vulnerable, experiencing a 47% year-over-year increase in cyberattacks, which underscores the cost of cybersecurity for small businesses. This alarming trend necessitates enhanced defenses against increasingly sophisticated threats.
Employee Training is another critical factor. Regular training programs are vital for reducing human error, a leading cause of many breaches. Investing in employee training not only mitigates risks but can also help reduce the cost of cybersecurity for small businesses by preventing incidents before they occur. Notably, 54% of organizations plan to invest in employee security awareness training to strengthen their security posture.
Finally, Cost Variability by Industry must be considered. Different sectors incur varying costs of cybersecurity for small businesses when it comes to online security. For instance, the financial impact of cyberattacks on small enterprises can range from $826 to $653,587, depending on the attack type and sector involved. This variability necessitates tailored budgeting strategies to address the specific risks and compliance needs associated with the cost of cybersecurity for small businesses.
By comprehending these factors, small enterprises can navigate the complexities of cybersecurity funding more effectively, ensuring they allocate resources wisely to protect against potential threats.
To establish a robust cybersecurity budget, small businesses must recognize the critical importance of understanding the cost of cybersecurity for small business to safeguard their digital assets. With cyber threats on the rise, it’s essential to adopt effective strategies that not only protect sensitive information but also ensure business continuity.
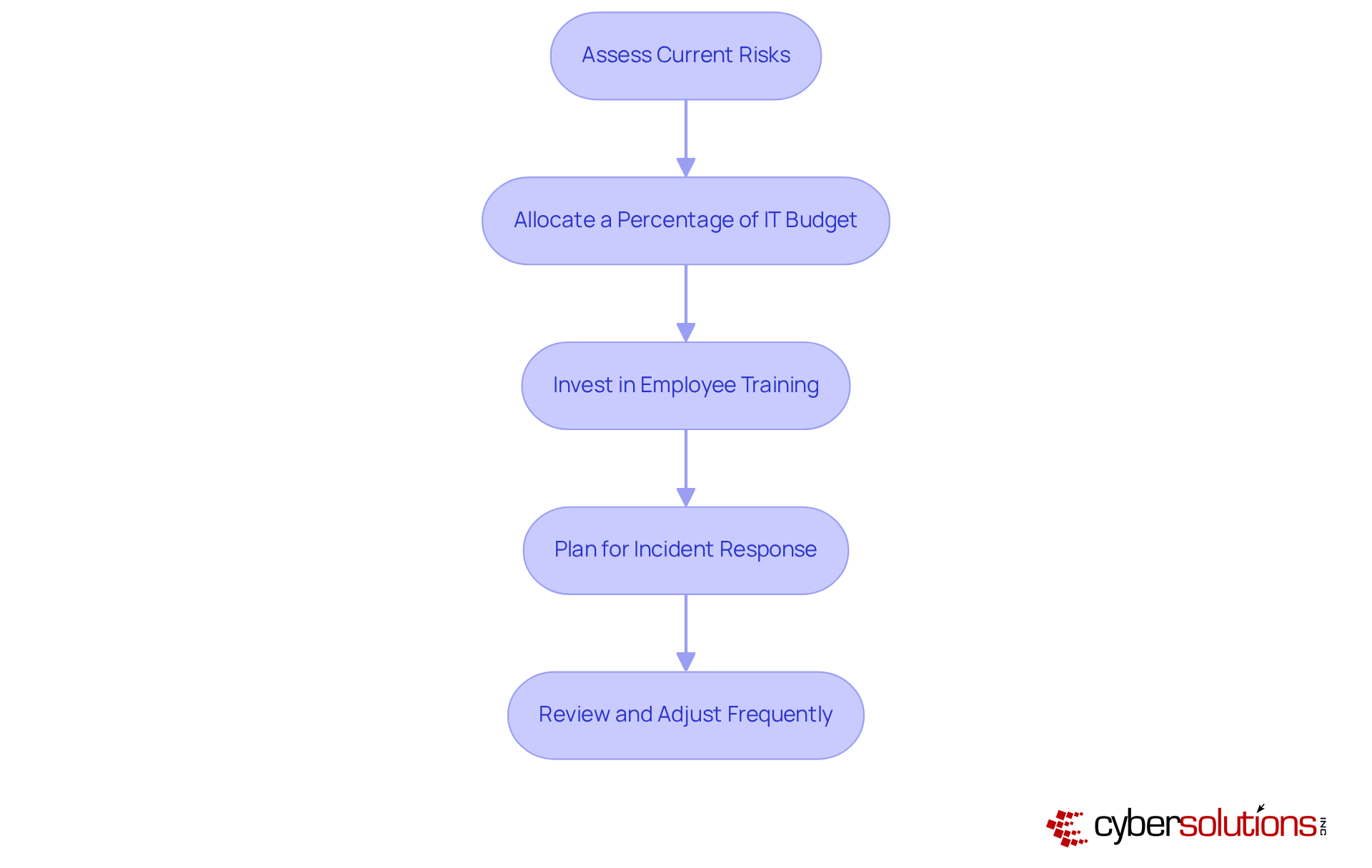
Assess Current Risks: Start with a comprehensive risk assessment to identify vulnerabilities and prioritize areas that need immediate attention. This foundational step is crucial for understanding the specific threats your organization faces.
Allocate a Percentage of IT Budget: It’s wise to allocate 5-10% of your total IT budget to digital security. This ensures that essential security measures are adequately funded, reflecting the growing recognition of cybersecurity's significance in organizational operations. In fact, businesses typically spend around 11% of their IT budgets on security, providing a useful benchmark for your allocation.
Invest in Employee Training: Regular training sessions are vital, as human error is the leading cause of data breaches. Investing in ongoing education for employees can significantly reduce risks and enhance your overall security posture. Remember, "Cybersecurity Awareness Month serves as a reminder that ignoring the problem is usually the most expensive choice."
Plan for Incident Response: Designate funds for incident response and recovery efforts to minimize financial losses in the event of a breach. This planning should cover expenses related to forensic investigations, legal proceedings, and public relations strategies to effectively manage reputational damage. A single breach can demonstrate the cost of cybersecurity for small business, which can range from $50,000 to $250,000 in ransom payments, downtime, and recovery.
Review and Adjust Frequently: Cybersecurity requirements are constantly evolving; therefore, it’s crucial to regularly evaluate and adjust your budget in response to new threats and operational shifts. This proactive approach ensures your organization remains resilient against emerging cyber risks.
The staggering financial consequences of cyber threats on small enterprises emphasize the cost of cybersecurity for small business. In 2025, the cost of cybersecurity for small business is expected to be between $120,000 and $1.24 million due to an average data breach. This figure includes direct expenses like recovery efforts and legal fees, as well as indirect costs such as lost revenue and diminished customer trust. Alarmingly, 60% of small enterprises that suffer a cyberattack are forced to close within six months due to the financial burden.
These statistics underscore the urgent need for small businesses to consider the cost of cybersecurity for small business when investing in robust measures. By taking proactive steps to safeguard their operations, they can mitigate the risk of significant financial losses and protect their future. Cybersecurity isn't just an IT issue; it's a critical business imperative that demands attention and action.

Investing in cybersecurity is not just an option for small businesses; it’s a vital necessity that can determine their survival in an increasingly digital and threat-filled landscape. The multifaceted costs associated with cybersecurity - ranging from direct expenses like software and employee training to indirect costs such as reputational damage - must be understood to make informed financial decisions.
Small businesses face a significantly heightened risk of cyberattacks. Many owners mismanage their security or rely on unqualified individuals, leaving them vulnerable. By adopting a comprehensive approach that includes:
small enterprises can effectively mitigate risks and protect their assets. The staggering potential costs of cyber incidents further emphasize the importance of prioritizing cybersecurity as a core component of business strategy.
The financial implications of neglecting cybersecurity can be devastating, potentially leading to closures within months of an attack. Small businesses must recognize this reality. By embracing a proactive mindset and committing to robust cybersecurity measures, organizations can safeguard their operations and secure a more resilient future. The time to act is now; investing in cybersecurity today can save small businesses from catastrophic losses tomorrow.
Why is cybersecurity important for small businesses?
Cybersecurity is crucial for small businesses because they face cyberattacks 210 percent more often than larger firms, making them more vulnerable to potential threats.
What are the direct costs associated with cybersecurity for small businesses?
Direct costs include software purchases, hardware upgrades, employee training, and consulting services.
How much do small businesses typically spend on cybersecurity annually?
Small businesses typically allocate between $5,000 and $50,000 annually for cybersecurity costs, depending on their size and industry requirements.
What are the potential financial repercussions of neglecting cybersecurity?
Neglecting cybersecurity can lead to severe financial consequences from a data breach, with costs ranging from $120,000 to $1.24 million.
What are some indirect expenses related to cybersecurity for small businesses?
Indirect expenses can include lost productivity during a cyber incident, potential legal fees, and reputational damage.
What percentage of small business owners manage their own online security?
Alarmingly, 74% of small business owners either self-manage their online security or rely on unqualified individuals, which can increase vulnerabilities.
How can small businesses mitigate cybersecurity risks?
Small businesses can mitigate risks by utilizing services like Cyber Solutions, which offers a flat-rate pricing model that covers various security needs and simplifies budgeting.
What is Compliance as a Service (CaaS)?
Compliance as a Service (CaaS) provides robust solutions to help organizations meet regulatory requirements, ensuring they remain compliant and protected from potential penalties.
What benefits does investing in cybersecurity provide for small businesses?
Investing in cybersecurity helps protect business assets, enhances overall security strategies, and ensures a more secure future for the organization.