
The rise of hybrid work models has fundamentally transformed organizational operations, but it has also ushered in a wave of cyber threats. As businesses navigate this intricate landscape, the urgency for effective hybrid work security strategies cannot be overstated. This article explores ten essential strategies that not only bolster cybersecurity but also empower organizations to excel in a digital-first environment.
How can companies protect their sensitive data and uphold trust with stakeholders amid these evolving challenges? The answers lie in embracing proactive measures that provide robust defenses against the ever-expanding spectrum of cyber risks.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated. As organizations adapt to hybrid work environments, the need for hybrid work security services has surged. Cyber Solutions Inc. excels in delivering these essential services, offering a comprehensive suite that includes:
These offerings are crucial for organizations navigating the complexities of hybrid work security.
The alarming rise in cyber risks, marked by a staggering 238% increase in assaults aimed at remote workers, underscores the importance of hybrid work security. This reality underscores the necessity for strong cybersecurity measures. By leveraging advanced technologies and expert insights, Cyber Solutions empowers businesses to maintain operational efficiency while safeguarding sensitive information.
Their proactive cybersecurity services - such as:
not only enhance security but also cultivate a culture of vigilance among employees. This approach significantly reduces the risk of incidents. In fact, organizations investing in cybersecurity training have reported up to a 70% decrease in security-related risks, highlighting the critical role of proactive measures in today’s digital environment.
As leaders prioritize cybersecurity, Cyber Solutions emerges as a trusted partner, ensuring that businesses can thrive securely in an ever-evolving landscape. "Investing in cybersecurity is not just a necessity; it's a strategic imperative for organizations aiming to protect their assets and maintain trust in a digital-first world," emphasizes a leading cybersecurity expert.

Implementing endpoint protection is not just important; it’s essential for hybrid work security and securing devices in today’s environments. With the rise of remote work, organizations face unprecedented cybersecurity threats that demand immediate attention. In fact, by 2025, 85% of Americans will recognize the necessity of antivirus protection, yet many still operate without it. This gap between awareness and action underscores a critical vulnerability that organizations cannot afford to ignore.
Regular updates and patches are vital. They equip devices with the latest security measures, significantly reducing vulnerabilities that cybercriminals may exploit. Cybersecurity specialists advocate for a proactive strategy, emphasizing the importance of ongoing monitoring and swift response capabilities to tackle potential risks. How prepared is your organization to respond to these threats?
Successful case studies reveal that entities employing comprehensive antivirus and firewall strategies have significantly mitigated risks associated with hybrid work security for remote work devices. By ensuring a secure operational environment, these organizations not only protect their assets but also foster trust among their stakeholders. It’s time to take action and prioritize endpoint protection to safeguard your organization’s future.

Advanced risk detection systems are essential for organizations aiming to recognize dangers in real-time. These systems leverage machine learning and behavioral analytics to pinpoint anomalies and potential threats, enabling swift responses that mitigate risks. Continuous monitoring ensures that suspicious activities are detected and addressed before they escalate into serious issues, protecting companies from ransomware, phishing, and other malware attacks.
Moreover, regularly reviewing risk intelligence reports helps businesses stay ahead of emerging threats, ensuring their defenses remain robust and up-to-date. The presence of a rapid incident response team, available within 24 hours, is crucial for minimizing damage. This approach includes:
This facilitates a quicker and more comprehensive recovery.
In today's landscape, where cybersecurity threats are ever-evolving, organizations must prioritize hybrid work security systems to protect their operations and maintain trust with stakeholders.

Establishing compliance protocols is crucial for navigating the complex regulatory landscape of hybrid work security environments. Organizations must implement policies that align with essential regulations such as HIPAA, PCI-DSS, and GDPR. With Cyber Solutions' Compliance As A Service (CaaS), this process becomes streamlined, offering comprehensive solutions that include:
Routine audits and evaluations, supported by our CaaS offerings, not only ensure adherence to these standards but also significantly reduce the risk of penalties, enhancing the organization's reputation. Have you considered how compliance impacts your organization’s credibility? Furthermore, our Incident Response services play a vital role in mitigating the effects of cyber challenges. They empower organizations to swiftly identify, contain, and alleviate risks, all while maintaining business continuity.
In today’s digital age, the stakes are high. Organizations that prioritize compliance and cybersecurity while implementing hybrid work security not only protect themselves but also build trust with their stakeholders. Don’t leave your organization vulnerable - partner with Cyber Solutions to navigate these challenges effectively.
In today's digital landscape, the importance of cybersecurity cannot be overstated. Conducting regular cybersecurity training is essential for empowering employees to recognize and respond to potential threats. Topics such as:
are crucial components of this training. By fostering a culture of awareness regarding safety, healthcare organizations can significantly reduce the likelihood of successful cyberattacks.
Consider this: how prepared is your team to handle a cyber threat? The unique challenges faced by CFOs in healthcare demand a proactive approach to cybersecurity. By investing in comprehensive training, organizations not only protect sensitive data but also build a resilient workforce capable of navigating the complexities of modern cyber threats.
Ultimately, promoting a culture of cybersecurity awareness is not just a best practice; it's a necessity. The stakes are high, and the consequences of inaction can be devastating. Equip your employees with the knowledge they need to safeguard your organization against potential breaches.
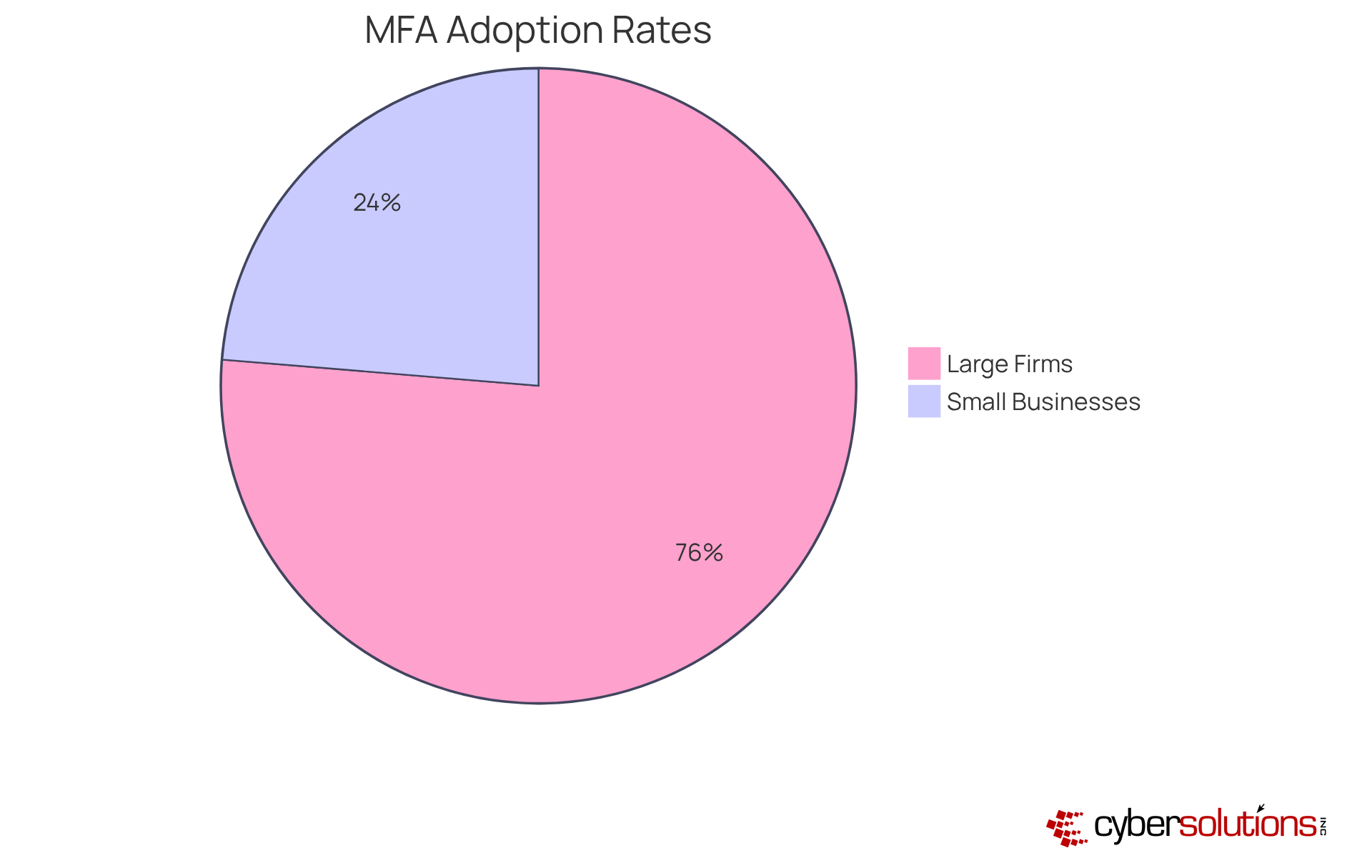
Implementing multi-factor authentication (MFA) is not just a recommendation; it’s a necessity for strengthening hybrid work security and access controls in today’s environments. By requiring users to present two or more verification factors, MFA significantly reduces the risk of unauthorized access. Cybersecurity leaders assert that MFA not only bolsters security but also cultivates a culture of accountability among users.
Consider this: over 99.9% of compromised accounts lack Multi-Factor Authentication (MFA) protection, according to Microsoft. This statistic underscores the critical importance of MFA in preventing unauthorized access. Organizations must prioritize the adoption of authenticator apps and biometric verification methods. In fact, 95% of employees using MFA do so via software, adding an essential layer of protection against potential breaches.
Effective MFA strategies involve consistent training for staff on the significance of these measures. It’s worth noting that 33% of entities find MFA bothersome, which highlights the necessity for efficient training to alleviate user resistance. Moreover, organizations should recognize the disparity in MFA adoption rates:
By integrating these strategies, organizations can significantly reduce the likelihood of unauthorized access incidents. This proactive approach ensures hybrid work security within a more secure operational framework in an increasingly digital landscape.
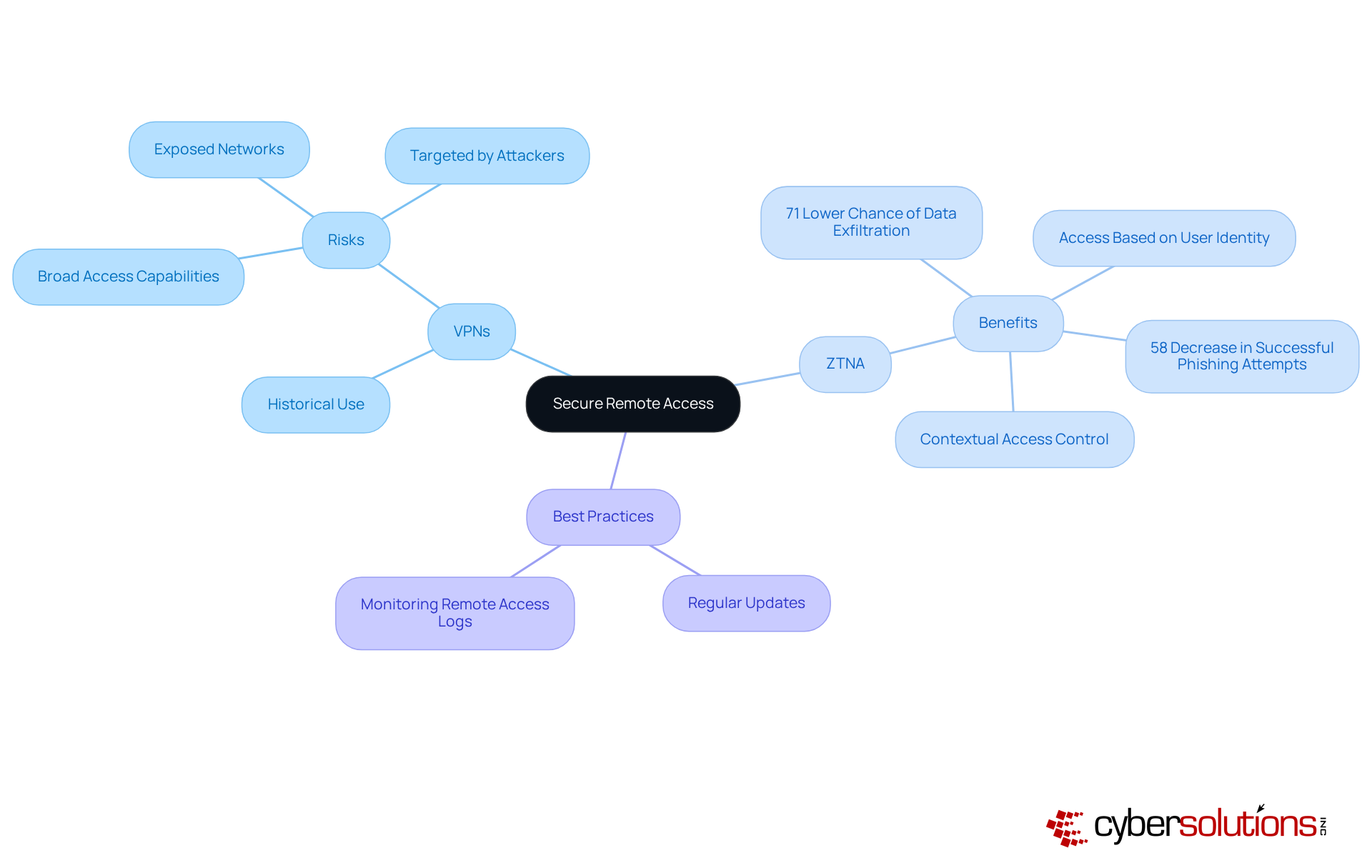
Securing remote access is not just important; it’s essential for hybrid work security and safeguarding corporate networks in today’s environment. Organizations must adopt Virtual Private Networks (VPNs) and Zero Trust Network Access (ZTNA) to ensure that only authorized users can access sensitive information.
While VPNs have historically been the go-to solution, they are increasingly viewed as inadequate. Their broad access capabilities can expose networks to significant risks if credentials are compromised. In contrast, ZTNA enhances security by allowing access based on user identity, device health, and contextual signals. This approach significantly minimizes the chances of breaches. In fact, entities employing ZTNA report a 71% lower chance of information exfiltration and a 58% decrease in successful phishing attempts.
Regularly updating access controls and monitoring remote access logs are essential practices that help identify and mitigate potential threats. Cybersecurity leaders emphasize that adopting a Zero Trust strategy not only strengthens resilience against cyberattacks but also enhances overall visibility and control over remote users, thereby improving hybrid work security. By prioritizing these secure access measures, organizations can effectively protect their sensitive data and maintain compliance in an increasingly complex digital landscape.
Routine assessments are essential for effectively identifying weaknesses within a company. These audits not only evaluate the effectiveness of current protective measures but also highlight potential vulnerabilities and ensure compliance with regulatory requirements. By systematically examining these measures, organizations can significantly bolster their defenses against cyber threats.
Consider this: the average cost of a breach for U.S. entities reached $4.88 million in 2024. This staggering figure underscores the financial imperative for robust protective measures. Moreover, organizations that conduct regular audits can proactively identify and address vulnerabilities, thereby reducing the likelihood of breaches and operational disruptions.
Successful vulnerability assessments, such as the recent achievement in cybersecurity maturity by the U.S. Department of Agriculture, demonstrate the power of a structured audit process. This approach not only enhances incident response plans but also cultivates a culture of continuous improvement in security posture. Ultimately, it safeguards sensitive information and maintains stakeholder trust.
In today's digital landscape, employing encryption is not just a precaution; it's a necessity for safeguarding sensitive information from unauthorized access, especially when managing Protected Health Information (PHI). With the rise in cybersecurity threats, healthcare organizations face unique challenges that demand robust solutions. Advanced encryption protocols must be implemented for both information at rest and in transit, ensuring that even if data is intercepted, it remains unreadable.
Moreover, integrating multi-factor authentication (MFA) and strong access control measures can significantly bolster the protection of sensitive information. These strategies not only enhance security but also instill confidence among stakeholders. Regularly reviewing and revising encryption standards is essential, as is developing a comprehensive response plan for potential incidents. This proactive approach not only preserves data integrity but also ensures adherence to HIPAA’s stringent timelines.
Are your current security measures sufficient to combat the evolving threats in healthcare? By prioritizing encryption and access controls, organizations can effectively mitigate risks and safeguard their most valuable assets.

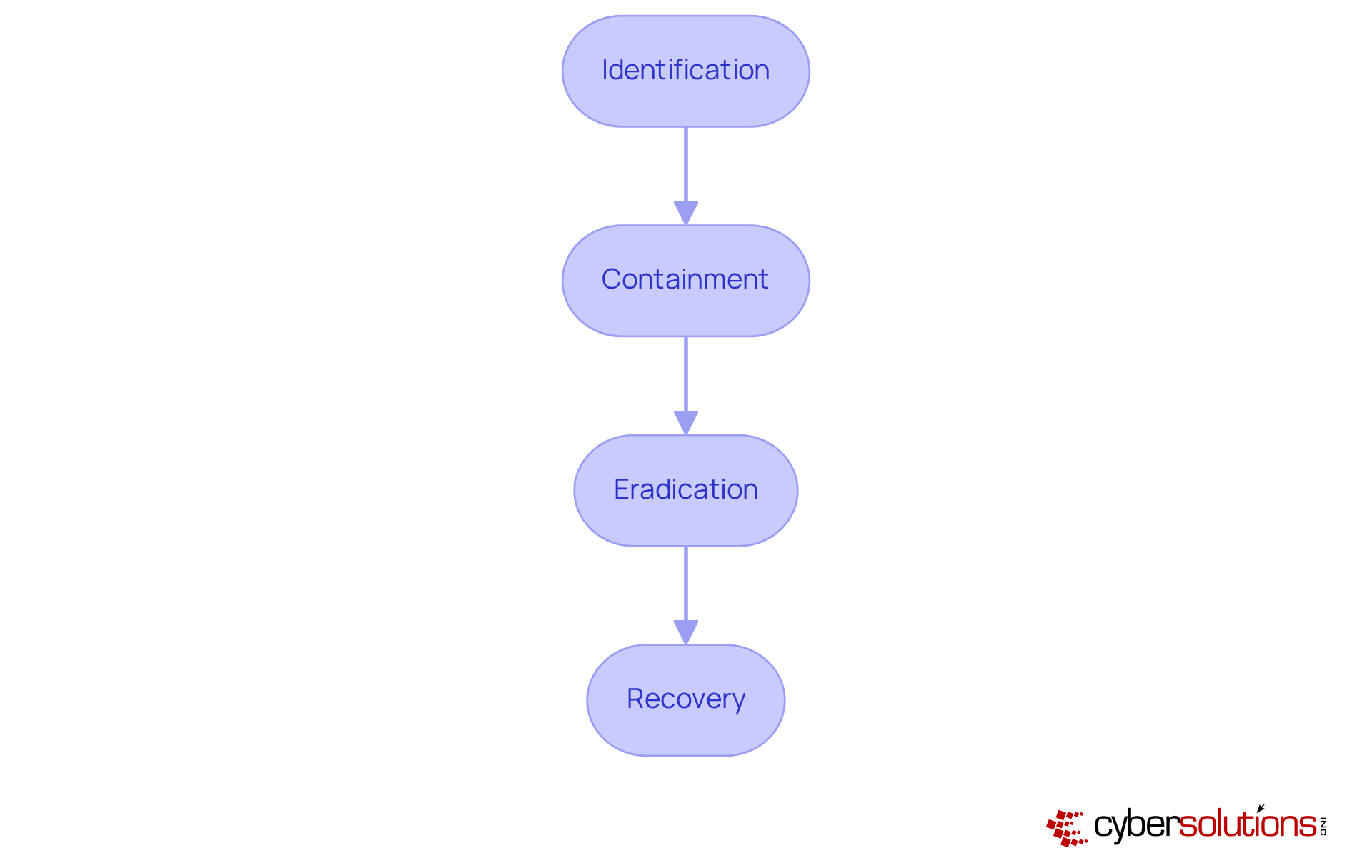
Establishing a robust incident response plan is not just a best practice; it’s essential for effectively managing security breaches in healthcare settings, where compliance with HIPAA standards is critical. Why is this so important? The healthcare sector faces unique challenges, making it a prime target for cyber threats. A well-defined incident response plan should clearly outline the steps to take during a cyber incident, including:
Frequent testing and updates of the incident response plan are crucial. Organizations that conduct annual drills and simulations significantly improve their readiness. Consider this: a study revealed that entities with well-tested incident response plans experienced 50% less downtime during breaches compared to those without. Cybersecurity specialists emphasize that ongoing enhancement of these strategies, informed by insights from previous incidents, is vital for adapting to evolving risks.
Engaging stakeholders throughout the planning process fosters a collaborative approach, enhancing the plan's effectiveness. Thorough documentation, including risk assessments, compliance reports tailored to HIPAA standards, and breach reporting procedures, is paramount. The Cybersecurity and Infrastructure Security Agency (CISA) also underscores the importance of prompt patching and practicing incident response plans to mitigate risks.
With the average cost of a data breach soaring to $4.56 million, maintaining a proactive stance is essential for safeguarding operations and reputation. By prioritizing security awareness training and specialized incident response expertise, organizations can further reduce the risk of human error and ensure swift, effective responses to security threats. Is your organization prepared to face these challenges head-on?
The importance of implementing effective hybrid work security strategies is paramount in today’s digital landscape. As organizations shift to hybrid work models, prioritizing robust cybersecurity measures is essential to protect sensitive information and maintain operational integrity. By adopting comprehensive solutions that include endpoint protection, real-time threat detection, compliance protocols, and employee training, businesses can foster a safer working environment that builds trust and resilience against cyber threats.
Key strategies highlighted throughout this article include the necessity of multi-factor authentication, secure remote access, regular security audits, and data encryption. Each of these elements is crucial in safeguarding corporate networks and ensuring compliance with regulatory requirements. Organizations that invest in these proactive measures not only mitigate risks but also empower their employees to recognize and respond to potential threats effectively.
In a landscape where cyber threats are increasingly sophisticated, decisive action is essential. Organizations must embrace these hybrid work security strategies to protect their assets and maintain trust with stakeholders. By prioritizing cybersecurity, businesses can navigate the complexities of the digital realm, ensuring a secure and resilient future for their operations.
What services does Cyber Solutions Inc. offer for hybrid work security?
Cyber Solutions Inc. offers a comprehensive suite of services including managed IT support, endpoint protection, and compliance services, all aimed at enhancing security in hybrid work environments.
Why is hybrid work security becoming increasingly important?
The importance of hybrid work security has surged due to a significant increase in cyber risks, with a reported 238% rise in attacks targeting remote workers, highlighting the need for robust cybersecurity measures.
What proactive cybersecurity services does Cyber Solutions provide?
Cyber Solutions provides proactive cybersecurity services such as 24/7 IT support, threat detection, data backup solutions, and user training to enhance security and foster a culture of vigilance among employees.
How does cybersecurity training impact security risks?
Organizations that invest in cybersecurity training have reported up to a 70% decrease in security-related risks, demonstrating the effectiveness of proactive measures in mitigating threats.
What is the importance of endpoint protection in hybrid work environments?
Endpoint protection is essential for securing devices in hybrid work settings, as it helps organizations address unprecedented cybersecurity threats and reduces vulnerabilities that cybercriminals may exploit.
What strategies are recommended for effective endpoint protection?
Effective endpoint protection strategies include implementing regular updates and patches, ongoing monitoring, and swift response capabilities to tackle potential risks.
How do advanced risk detection systems enhance cybersecurity?
Advanced risk detection systems utilize machine learning and behavioral analytics to identify anomalies and potential threats in real-time, enabling swift responses to mitigate risks.
What role does a rapid incident response team play in cybersecurity?
A rapid incident response team is crucial for minimizing damage during a cybersecurity incident, providing services like endpoint isolation, malware removal, and user training for quicker recovery.
Why should organizations regularly review risk intelligence reports?
Regularly reviewing risk intelligence reports helps organizations stay ahead of emerging threats and ensures that their cybersecurity defenses remain robust and up-to-date.