
Understanding the complexities of cybersecurity is more crucial than ever. As public charging stations become commonplace in everyday settings, the risks associated with compromised USB ports - known as juice jacking - pose significant threats to businesses that rely on these convenient power sources. This emerging cyber threat not only jeopardizes sensitive data but also challenges operational integrity.
Organizations must delve into the implications of juice jacking to uncover effective strategies for protection. With the increasing sophistication of cyberattacks, how can businesses effectively safeguard themselves against this hidden danger? By addressing these concerns head-on, companies can fortify their defenses and ensure the safety of their critical information.
In today's digital landscape, it is essential to understand what juice jacking means, as the importance of robust cybersecurity cannot be overstated, especially for organizations that rely on public charging stations. Cyber Solutions Inc. offers sophisticated endpoint security, featuring real-time monitoring and threat detection specifically designed to mitigate the risks associated with unauthorized charging. By implementing comprehensive security measures - such as antivirus software and intrusion detection systems - organizations can significantly reduce the chances of malware installation and data theft.
Consider the implications: in high-risk environments like airports and cafes, the threat of data theft is prevalent. Businesses that have adopted real-time monitoring solutions have reported a marked decrease in security incidents, showcasing the effectiveness of these technologies. Cybersecurity specialists emphasize that ongoing surveillance is crucial in protecting against threats, as juice jacking means not only involves juice theft but also enhances the overall security posture of the organization.
By prioritizing real-time threat detection, companies can effectively shield sensitive information and maintain operational integrity in an increasingly interconnected world. The proactive strategy offered by Cyber Solutions Inc. is essential for any organization looking to navigate the complexities of modern cybersecurity threats.
Juice jacking means a sophisticated cyber threat that arises when devices connect to compromised USB power ports. This attack exploits the dual functionality of USB ports, which provide both power and data transfer capabilities, allowing attackers to install malware or extract sensitive information while devices charge. The risk is particularly pronounced in high-traffic areas like airports and hotels, where public charging stations are commonly used. Security experts warn that these public USB ports can be manipulated to facilitate unauthorized data access, posing significant risks for organizations that rely on such power solutions.
Data indicates that a considerable number of devices fall victim to public USB power ports, with reports highlighting how easily attackers can introduce malware. The FBI has issued warnings about the potential for malware to lock devices and compromise passwords, underscoring the necessity for vigilance. As Deputy District Attorney Luke Sisak aptly noted, "a free charge could end up draining your bank account," emphasizing the serious dangers associated with public charging points. Real-world cases illustrate the consequences of charging-related theft, with organizations facing data breaches and operational disruptions due to these attacks.
Cybersecurity professionals emphasize that understanding what juice jacking means is crucial for effectively mitigating risks. Implementing robust security measures - such as using USB blockers and steering clear of public power stations - can significantly reduce the likelihood of becoming a target. Additionally, opting for standard plug outlets instead of USB charging stations and investing in a USB condom can further bolster security. As the threat landscape evolves with increasingly sophisticated malware targeting smartphones, businesses must prioritize cybersecurity awareness and training to safeguard sensitive data from exploitation.
Government organizations, including the Transportation Security Administration (TSA), have raised significant concerns about the risks associated with beverage theft, particularly in public spaces like airports and shopping centers. These warnings highlight that juice jacking means the dangers associated with using public USB charging stations, where cybercriminals can exploit vulnerabilities to install malware on devices. The TSA has specifically cautioned travelers against plugging their devices into these ports, highlighting that juice jacking means being aware of potential risks.
To combat these threats, companies must prioritize educating their staff about what juice jacking means and the risks linked to mobile device charging fraud. By fostering a culture of cybersecurity awareness, organizations empower their workforce to recognize and avoid potential threats. This proactive approach not only safeguards sensitive information but also bolsters overall organizational security. As incidents of beverage theft continue to emerge, it is crucial for companies to stay vigilant and adopt effective strategies to mitigate these risks.
In addition to employee training, implementing a rapid incident response strategy is essential. Cyber Solutions underscores the importance of having a 24-hour on-site response team capable of acting swiftly to contain threats and minimize damage. A layered recovery approach - including endpoint isolation, malware removal, and user training - can further enhance security configurations and ensure a more comprehensive recovery from incidents. For example, utilizing a portable charging battery can help circumvent malicious charging ports, while employing a USB cable with disconnected data communication pins can prevent phone hijacking, which is what juice jacking means, by harmful charging stations. Although the FCC has indicated that it hasn't identified any real-world attacks linked to power theft, understanding these risks remains vital for maintaining robust cybersecurity.
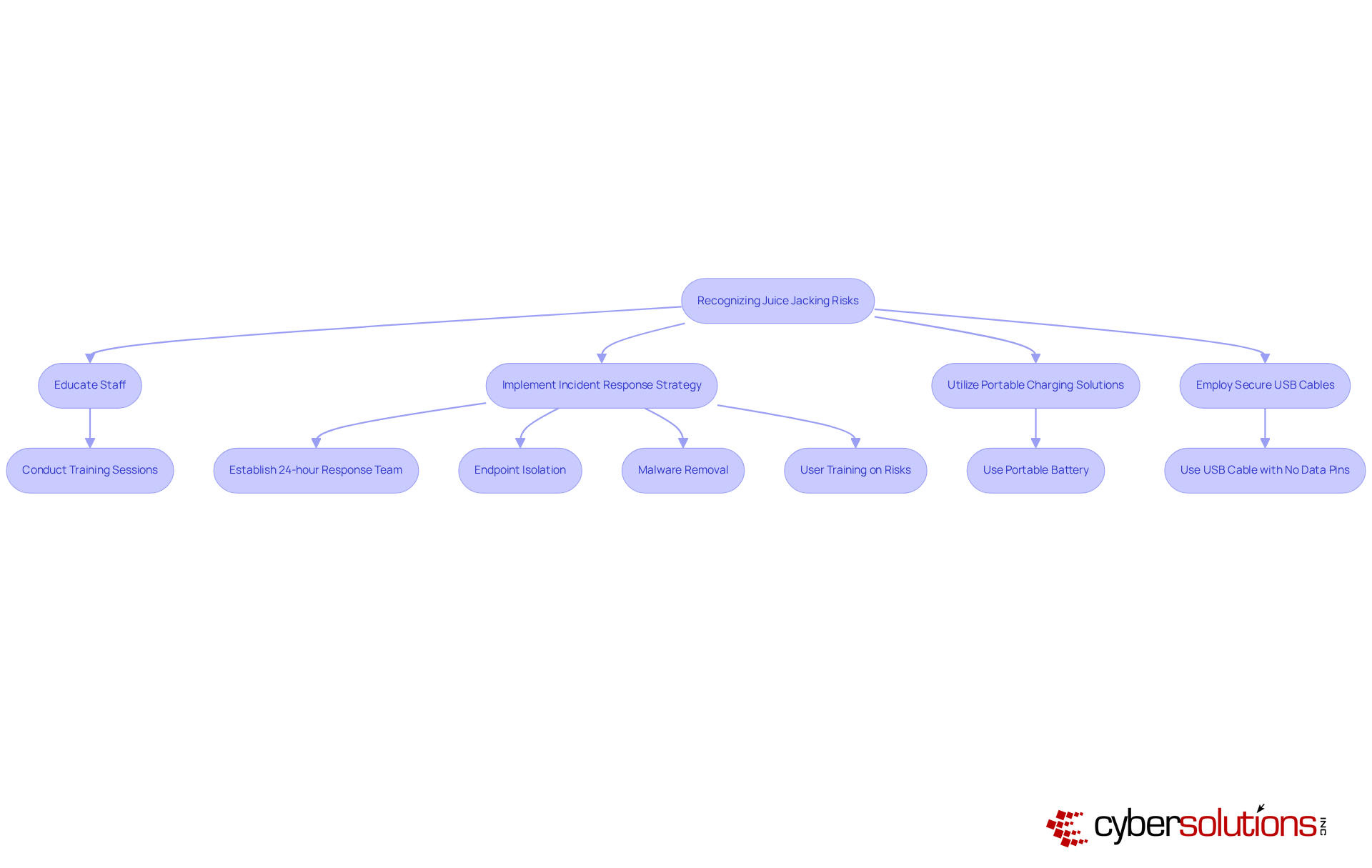
To effectively mitigate the risks associated with juice jacking means that organizations must adopt a comprehensive strategy that addresses this pressing cybersecurity threat.
Encourage Personal Chargers: Employees should be strongly advised to use their own chargers and avoid public USB ports whenever possible. This straightforward practice can significantly reduce exposure to potential threats.
Implement USB Information Blockers: Investing in USB information blockers is essential. These devices allow for powering while preventing any information transfer, effectively safeguarding against unauthorized access and information theft. As Gurpreet Thathy, Director of Cyber Security & Electronic Countermeasures, asserts, 'USB data blockers effectively protect devices from cyber threats, particularly what juice jacking means via public USB ports.'
Educate on Safe Powering Practices: Regular training sessions are crucial to emphasize the importance of using AC outlets instead of public power stations. This not only enhances security but also cultivates a culture of cybersecurity awareness within the organization. The FBI and FCC have warned that public USB charging stations can be exploited for malicious activities, highlighting the need for vigilance.
Regular Software Updates: Keeping device software up to date is vital for addressing vulnerabilities that could be exploited during a power theft attack. Organizations should establish a routine for checking and applying updates to all devices.
By implementing these strategies, companies can significantly reduce the likelihood of being targeted by malicious attacks, ensuring that their sensitive information remains protected in an increasingly mobile and interconnected environment. While charging theft may seem largely theoretical, adopting these precautions can effectively eliminate the risk.
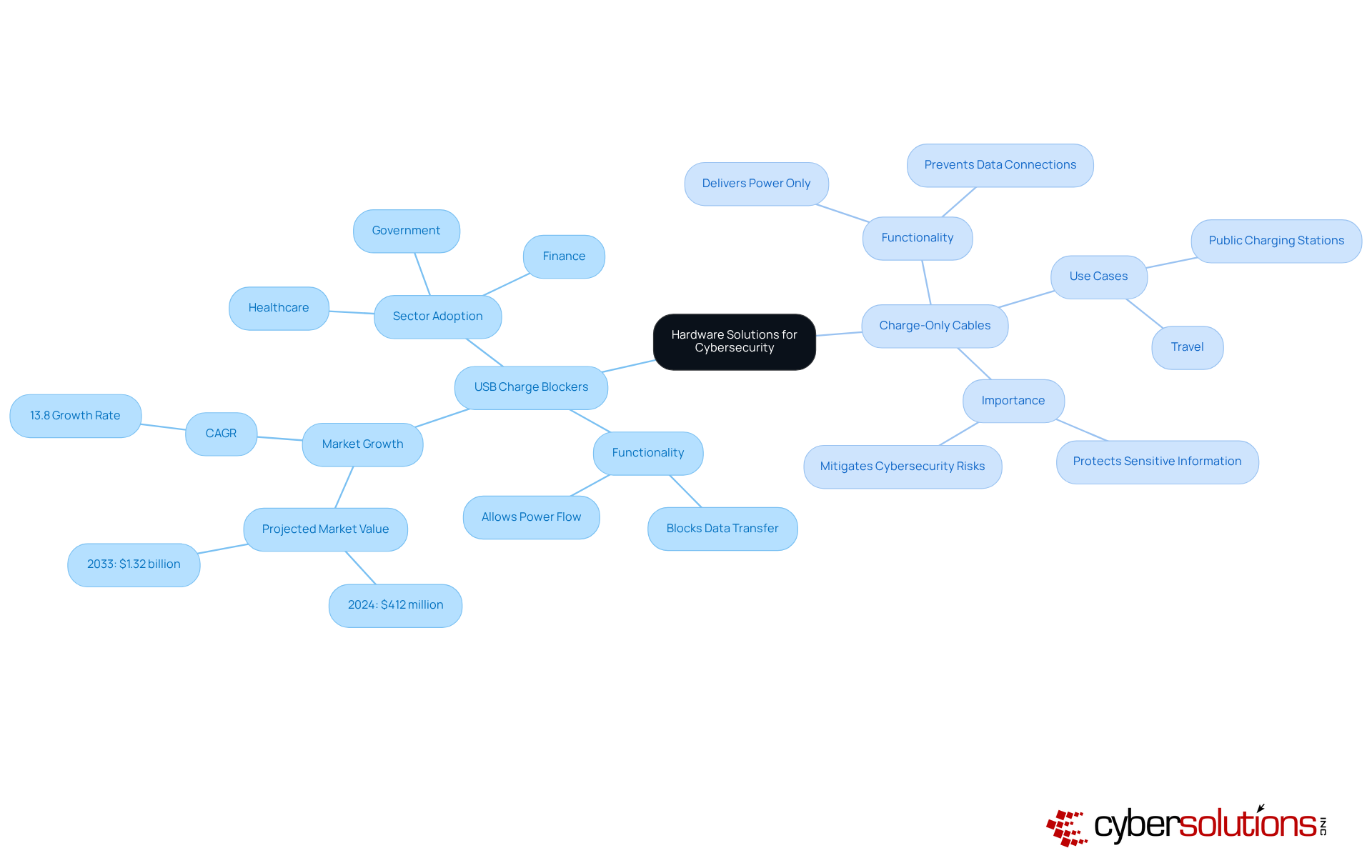
In today’s digital landscape, the importance of cybersecurity cannot be overstated, especially in the healthcare sector. Hardware solutions like USB charge blockers and charge-only cables are essential in safeguarding against what juice jacking means, a growing threat in public charging environments. USB power blockers allow electricity to flow while blocking data transfer, which is an important measure in understanding what juice jacking means, as they effectively prevent unauthorized access to devices. This dual functionality is crucial for protecting sensitive information in high-risk areas where cyberattacks are more likely to occur.
Charge-only cables serve a similar purpose, designed specifically to deliver power without enabling data connections. For individuals and organizations alike, these tools are vital for maintaining the integrity of sensitive details. Investing in such solutions not only enhances an organization’s security posture but also aligns with increasing regulatory demands and privacy awareness. In sectors like healthcare and finance, the adoption of USB blockers is becoming a standard practice as part of comprehensive endpoint security strategies, reflecting the urgent need to mitigate risks associated with public power sources.
The market for USB information blockers is projected to reach $1.32 billion by 2033, with a compound annual growth rate (CAGR) of 13.8%. This growth is driven by escalating concerns over information security and privacy. Real-world examples underscore the effectiveness of these solutions; organizations in high-risk sectors have successfully integrated charge-only cables into their public charging stations, significantly lowering the risk of data breaches.
Cybersecurity leaders advocate for the use of USB data blockers as a proactive measure against malware installation and data theft. By reinforcing the importance of these hardware solutions, organizations can better navigate the complexities of today’s cybersecurity challenges. Are you prepared to take action and protect your sensitive information? The time to invest in robust cybersecurity measures is now.
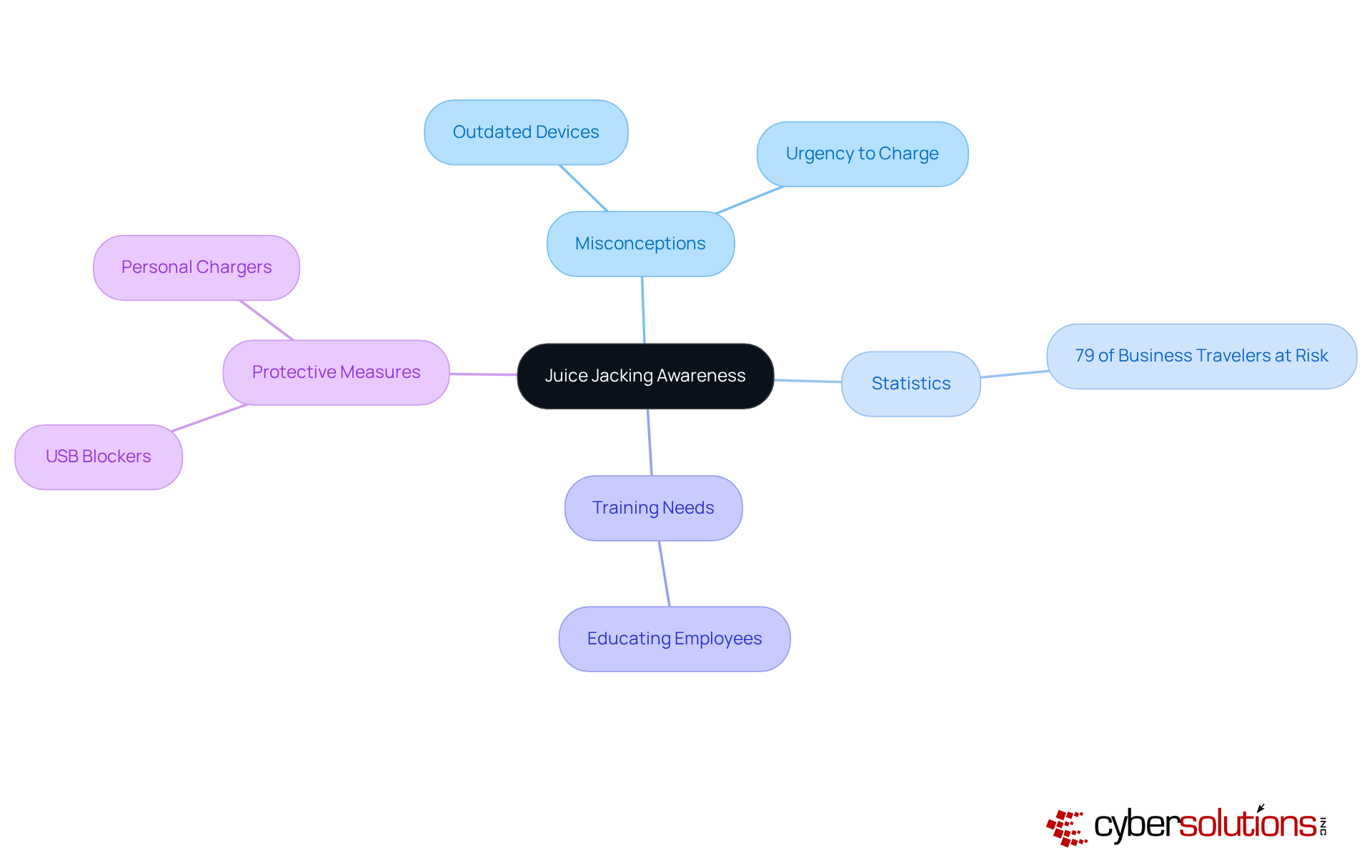
Juice theft has emerged as a pressing concern in our increasingly digital world, often portrayed in movies and news reports as a significant threat. Yet, misconceptions persist, with many dismissing it as an exaggerated risk. Did you know that a staggering 79% of business travelers unknowingly expose themselves to potential attacks by using public USB ports or power stations? This alarming statistic underscores the critical need for organizations to conduct training sessions aimed at raising awareness about device theft risks and educating employees on the importance of opting for personal chargers over public power sources.
Real-world examples further illustrate the consequences of these misconceptions. Many individuals underestimate the threat, mistakenly believing that only outdated devices are at risk. In truth, even the latest smartphones can fall prey to power theft, as attackers exploit users' urgency to charge their devices, often neglecting security concerns. This reality highlights the necessity of cultivating a cybersecurity-aware culture within organizations. As one expert aptly noted, "Juice theft is akin to pickpocketing in the digital era, occurring while your phone is charging at public stations." By addressing these misunderstandings and providing accurate information, companies can develop a more informed workforce that recognizes what juice jacking means and prioritizes cybersecurity strategies to protect sensitive information. Moreover, organizations should advocate for the use of USB blockers as an additional protective measure to mitigate risks.
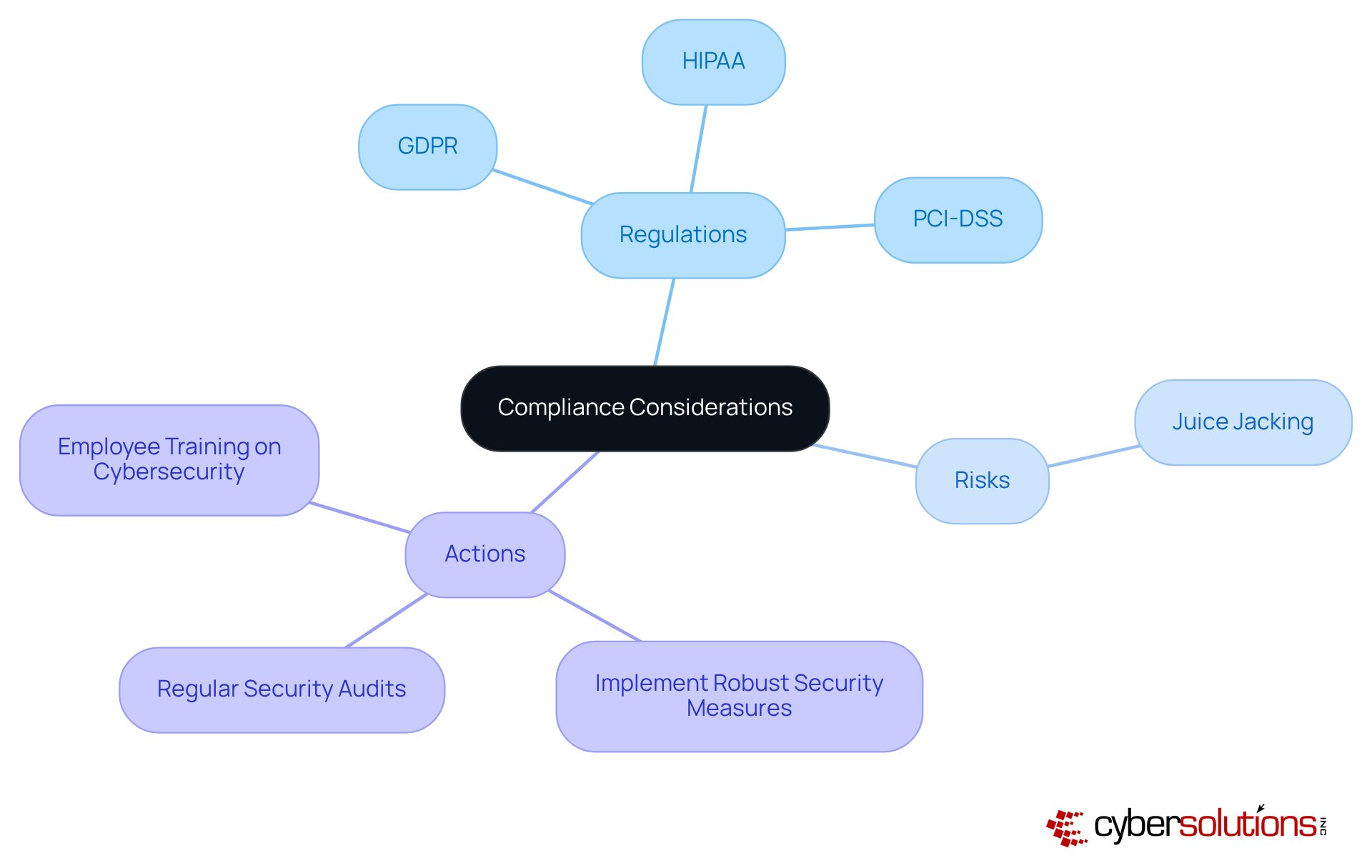
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations handling sensitive information. Compliance regulations such as GDPR, HIPAA, and PCI-DSS mandate that businesses implement robust security measures to safeguard this data. However, challenges such as juice jacking means pose significant risks, potentially leading to breaches that violate these critical regulations.
Organizations must recognize that juice jacking means public charging stations can introduce vulnerabilities into their cybersecurity frameworks. It is essential for companies to ensure their cybersecurity policies comprehensively address these risks to maintain compliance and protect sensitive information. By doing so, they not only adhere to regulations but also foster trust with their clients and stakeholders.
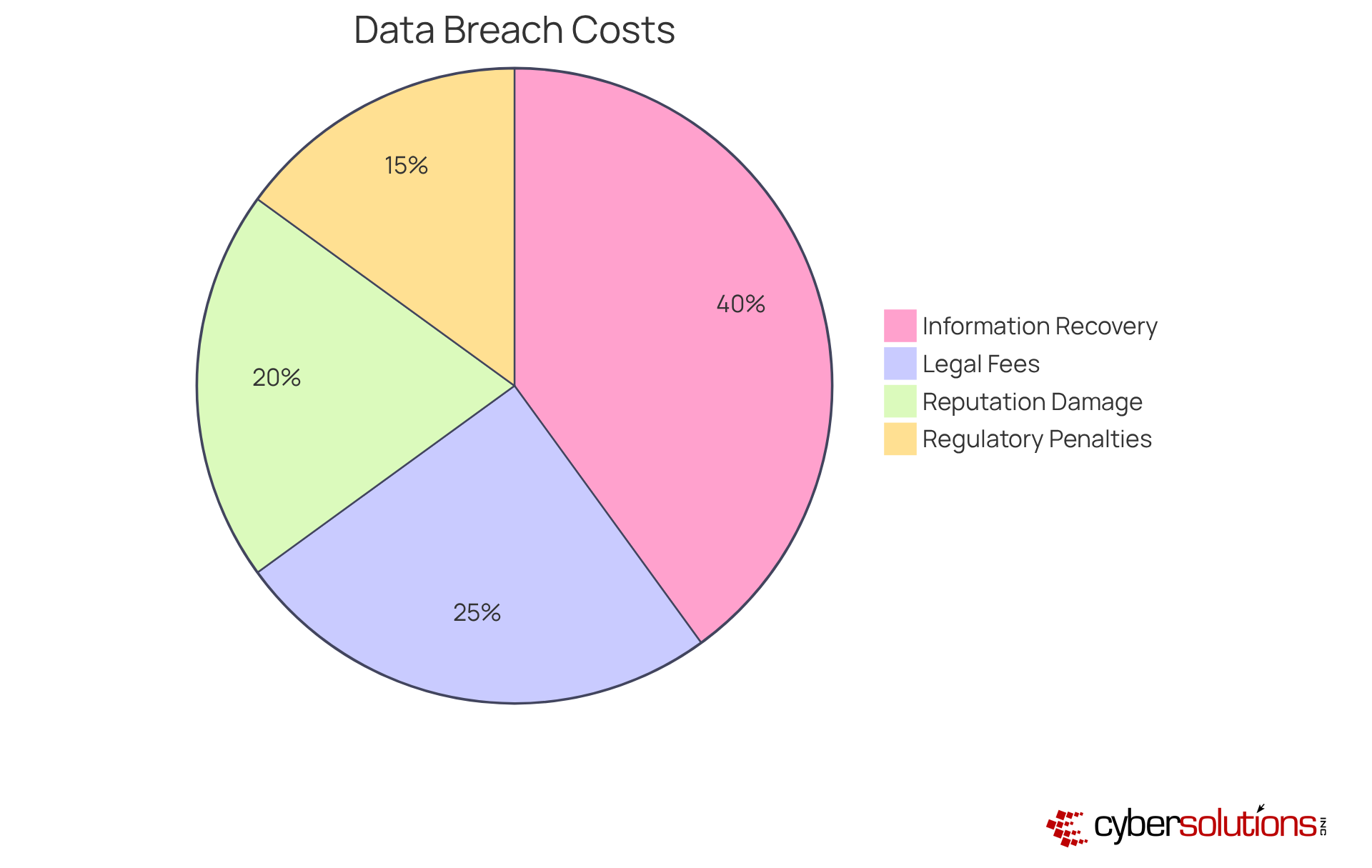
Juice theft incidents can lead to substantial financial repercussions for companies, including costs tied to information recovery, legal fees, and damage to reputation. Did you know that the average cost of a data breach across all sectors reached approximately $4.88 million in 2024? This marks a 10% increase from the previous year. In the financial sector alone, this figure escalated to about $6.08 million, highlighting the severe economic impact of such breaches.
Organizations facing charging attacks often grapple with not just the immediate recovery expenses but also long-term financial setbacks stemming from diminished customer trust and potential regulatory penalties. Investing in preventive measures, such as robust cybersecurity protocols and comprehensive employee training, is essential for mitigating these risks. By understanding the financial implications of data theft, companies can better justify their cybersecurity investments and protect their bottom line.
To effectively counter unauthorized charging attacks, organizations must recognize the critical importance of a robust incident response strategy. This strategy should encompass specific procedures for identifying, containing, and recovering from such events, ensuring that organizations are prepared to act swiftly. Communication strategies for promptly informing stakeholders are essential, as timely updates can significantly mitigate the impact of an incident.
Regular testing and updates of the incident response plan are not just beneficial; they are crucial. Organizations that conduct incident response drills at least quarterly respond 35% faster to incidents. Yet, alarmingly, 70% of businesses rarely or never test their incident response plans, leaving significant gaps in their preparedness. This oversight can have dire consequences, especially in an era where cybersecurity threats are ever-evolving.
By prioritizing these protocols, companies can enhance their resilience against power theft threats and ensure a swift recovery should an incident occur. The time to act is now-investing in a comprehensive incident response strategy is not just a recommendation; it’s a necessity for safeguarding organizational integrity.
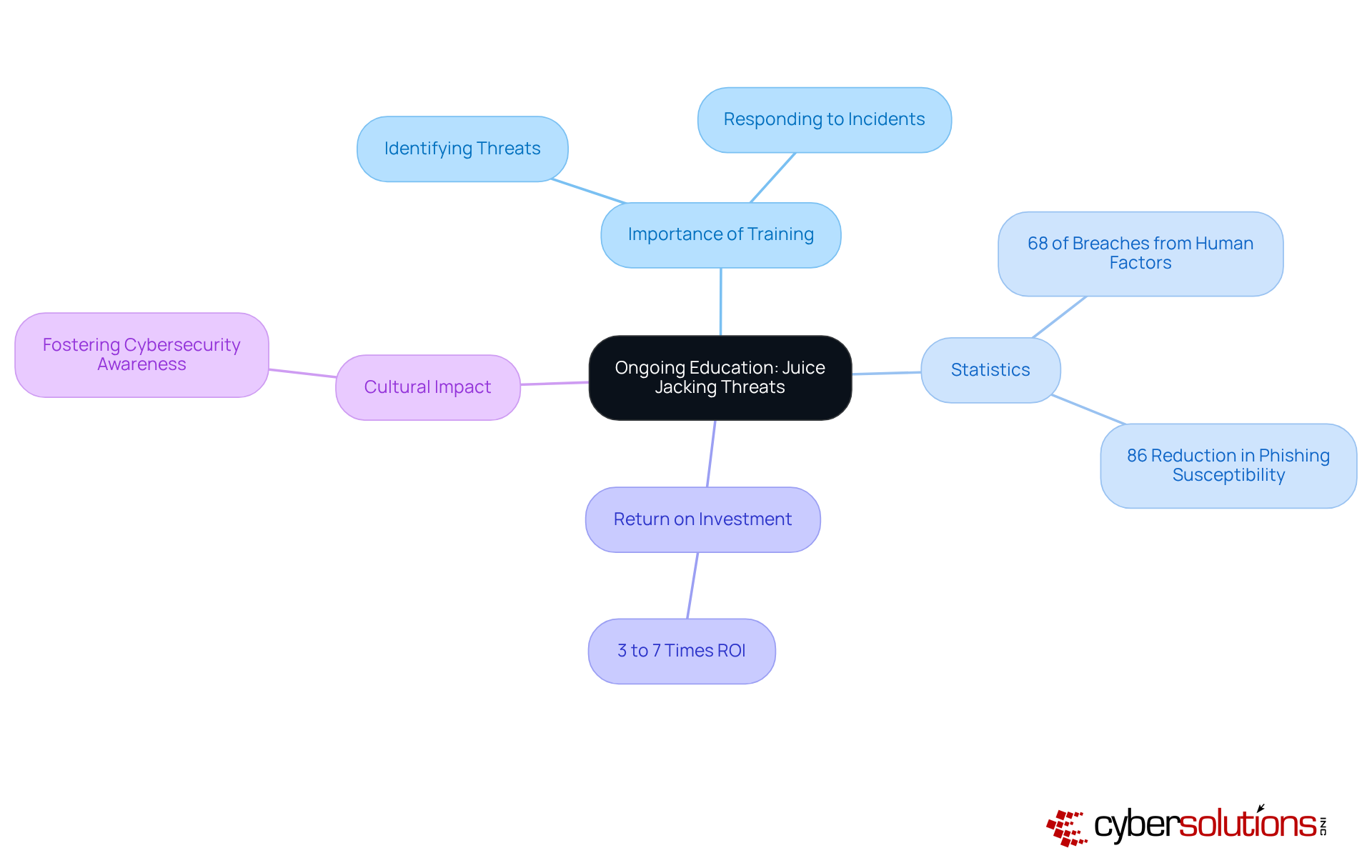
To effectively combat beverage theft, organizations must recognize the critical role of ongoing education and training for their employees. In today’s landscape, where a staggering 68% of security breaches in 2024 stemmed from human factors, it’s essential to keep staff informed about the latest threats and best practices for device security. Regular workshops and seminars not only equip employees with the knowledge to identify and respond to potential incidents, but also foster a culture of cybersecurity awareness regarding what juice jacking means.
Consider this: effective training can reduce employee susceptibility to phishing attacks by up to 86%. This statistic underscores the necessity of investing in comprehensive training programs. Organizations that prioritize such initiatives often see a remarkable return on investment, ranging from 3 to 7 times, reinforcing the value of employee education. By empowering their workforce, businesses enhance their overall security posture, enabling employees to take proactive steps in safeguarding their devices.
In conclusion, fostering a culture of cybersecurity awareness is not just a preventive measure; it’s a strategic imperative for organizations aiming to protect their assets and maintain trust in an increasingly digital world.
Understanding juice jacking is not just important; it’s essential for businesses navigating a digital landscape filled with public charging stations. This sophisticated cyber threat poses significant risks - not only to individual devices but also to sensitive organizational data. The potential operational and financial repercussions are staggering. Therefore, organizations must adopt comprehensive cybersecurity strategies and prioritize employee education to mitigate these risks effectively.
Key insights throughout this article underscore the necessity of:
By fostering a culture of cybersecurity awareness, organizations can significantly enhance their defenses against juice jacking incidents and bolster their overall security posture.
Ultimately, the responsibility for safeguarding sensitive information rests with each organization. By prioritizing robust cybersecurity measures and staying informed about the ever-evolving threat landscape, businesses can protect their assets and maintain trust with clients and stakeholders. Now is the time for companies to take decisive action and invest in the necessary tools and training to combat juice jacking effectively.
What is juice jacking?
Juice jacking is a cyber threat that occurs when devices connect to compromised USB power ports, allowing attackers to install malware or extract sensitive information while the devices charge.
Why is juice jacking a concern in public places?
Juice jacking is particularly concerning in high-traffic areas like airports and hotels, where public charging stations are commonly used, making it easier for attackers to exploit vulnerabilities and gain unauthorized access to devices.
How can organizations protect themselves against juice jacking?
Organizations can protect themselves by implementing robust security measures such as antivirus software, intrusion detection systems, using USB blockers, avoiding public charging stations, and opting for standard plug outlets instead.
What are some recommended practices to mitigate the risks of juice jacking?
Recommended practices include using a portable charging battery, employing USB cables with disconnected data communication pins, and educating staff about the risks associated with mobile device charging fraud.
What actions have government organizations taken regarding juice jacking?
Government organizations, including the Transportation Security Administration (TSA), have raised concerns about the risks of juice jacking and have cautioned travelers against using public USB charging stations.
How does Cyber Solutions Inc. help organizations with endpoint protection?
Cyber Solutions Inc. offers advanced endpoint protection that includes real-time monitoring and threat detection to mitigate the risks associated with unauthorized charging and enhance overall cybersecurity posture.
What impact does real-time monitoring have on security incidents?
Organizations that have adopted real-time monitoring solutions have reported a marked decrease in security incidents, demonstrating the effectiveness of these technologies in protecting sensitive information.
Why is ongoing surveillance important in cybersecurity?
Ongoing surveillance is crucial in cybersecurity to continuously protect against evolving threats, including juice jacking, and to maintain the integrity of sensitive data within organizations.