In today's digital landscape, where cyber threats are becoming increasingly sophisticated, the urgency for robust cybersecurity measures is paramount. Endpoint Detection and Response (EDR) stands out as a crucial solution, empowering organizations to monitor, detect, and respond to threats in real-time. This capability not only mitigates the impact of cyberattacks but also safeguards sensitive data and ensures compliance.
However, as organizations strive to implement these advanced solutions, pressing questions arise:
Understanding these intricacies is essential for leaders committed to protecting their organizations.
In today's digital landscape, cybersecurity is not just an option; it's a necessity. To understand what is a edr, one must recognize that Endpoint Detection and Response (EDR) stands at the forefront of this critical defense, continuously monitoring, detecting, and responding to threats on endpoint devices like laptops, desktops, and servers. By gathering and analyzing data from these endpoints, EDR tools can identify harmful actions in real-time, significantly bolstering an organization's security posture.
Unlike traditional antivirus solutions that rely heavily on signature-based detection, EDR employs behavioral analysis and robust incident response capabilities. This proactive approach allows businesses to swiftly mitigate risks, reducing the typical downtime from ransomware attacks, which can extend up to 21 days. As we look ahead to 2025, it's projected that nearly 48% of organizations will implement EDR solutions, which raises the question of what is a edr and underscores their vital role in protecting sensitive data and ensuring compliance with regulatory standards.
Key features of EDR technology include:
These elements make EDR an indispensable part of modern cybersecurity strategies. In a world where threats are ever-evolving, knowing what is a edr and investing in it is not just wise; it's essential for safeguarding your organization's future.
In cybersecurity, understanding what is an EDR is crucial, especially as the complexity and frequency of cyber threats continue to grow. In today’s landscape, organizations must be equipped to identify and respond to risks in real-time. This capability is essential for minimizing potential damage from cyberattacks. Continuous monitoring of endpoint activities allows EDR systems to detect anomalies that may indicate breaches, facilitating swift incident response.
For healthcare organizations, the implications are profound. Compliance with industry regulations is not just a checkbox; it’s a necessity. EDR provides the visibility and reporting required to demonstrate adherence to security standards. Without EDR, organizations face an average cost exceeding $53,000 per cyberattack, highlighting the financial urgency of implementing these solutions.
Real-world examples underscore EDR's effectiveness. Companies that fully deploy EDR tools experience a marked decrease in breach likelihood, particularly when these tools are utilized across all endpoints. Cyber Solutions stands out in this arena, offering expert malware removal and system reconstruction services. We ensure that compromised endpoints are thoroughly cleaned, patched, and reimaged as needed.
Moreover, with Cyber Solutions' 24/7 risk monitoring, suspicious activities are identified and neutralized before they escalate into serious threats. This proactive approach safeguards businesses from ransomware, phishing, and other malware attacks. Ultimately, what is an EDR is not just an option; it’s a critical component of a robust cybersecurity strategy, empowering organizations to protect their assets and maintain trust with clients and stakeholders.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in the healthcare sector. Cyber threats are evolving rapidly, posing significant risks to sensitive patient data and organizational integrity. For Chief Financial Officers (CFOs) in healthcare, navigating these challenges is paramount. To understand what is a EDR, it is important to note that EDR (Endpoint Detection and Response) solutions emerge as a critical component in safeguarding against these threats, offering a robust defense mechanism that combines proactive monitoring with automated response capabilities.
EDR solutions are built around several key components, including:
Data collection agents are installed on endpoint devices to continuously monitor activities, capturing detailed information on processes, network connections, and user behaviors. This information is sent to a centralized management console, where security teams can examine it for potential risks, enabling a proactive security stance.
Centralized management consoles play a pivotal role in streamlining security operations. They provide a unified view of endpoint activities, allowing for efficient monitoring and rapid response to incidents. Organizations employing centralized consoles can significantly decrease their average response time to incidents, which is essential considering that the average duration to recognize and control a breach is about 277 days. By utilizing EDR tools, companies can automate response actions, such as isolating compromised devices and removing malware, thereby containing incidents before they escalate into major breaches.
Furthermore, EDR systems incorporate intelligence feeds that enhance detection capabilities by offering context on recognized risks and weaknesses. This integration enables organizations to remain proactive against emerging dangers, as EDR systems can automatically identify and mitigate potential hazards in real time. What is a EDR includes functions such as:
All of which are essential for maintaining a robust cybersecurity framework. As cyber risks continue to develop, the efficiency of EDR systems in identifying and addressing incidents becomes increasingly crucial for organizations seeking to safeguard their sensitive information and maintain adherence to regulatory standards.
In today's digital age, the importance of robust cybersecurity cannot be overstated, especially in the healthcare sector. As cyber threats evolve, healthcare organizations face unique challenges that demand immediate attention. The development of technologies that answer the question of what is a EDR marks a significant evolution in this landscape. What is a EDR? Initially emerging in response to the limitations of conventional antivirus programs, these solutions have transformed from basic monitoring tools into sophisticated systems capable of advanced behavioral analysis and automated responses.
The early 2010s saw the rise of EDR as cyber dangers became increasingly sophisticated, revealing the inadequacies of signature-based detection methods. Today, when discussing cybersecurity, what is a EDR is not just an option; it is an integral component of comprehensive strategies. With the rise of ransomware and advanced persistent threats (APTs), healthcare organizations must prioritize the adoption of robust endpoint security measures. The continuous improvement of EDR technologies reflects an ongoing arms race between cyber defenders and attackers, underscoring the necessity for organizations to stay ahead of potential threats.
How can healthcare CFOs navigate these complexities? By investing in advanced EDR solutions, they can enhance their organization's security posture, prompting the inquiry of what is a EDR to ensure that sensitive patient data remains protected. The evolution of technologies related to what is a EDR is a testament to the commitment required to combat modern cyber threats effectively. As we move forward, embracing these advancements will be crucial for safeguarding the future of healthcare.
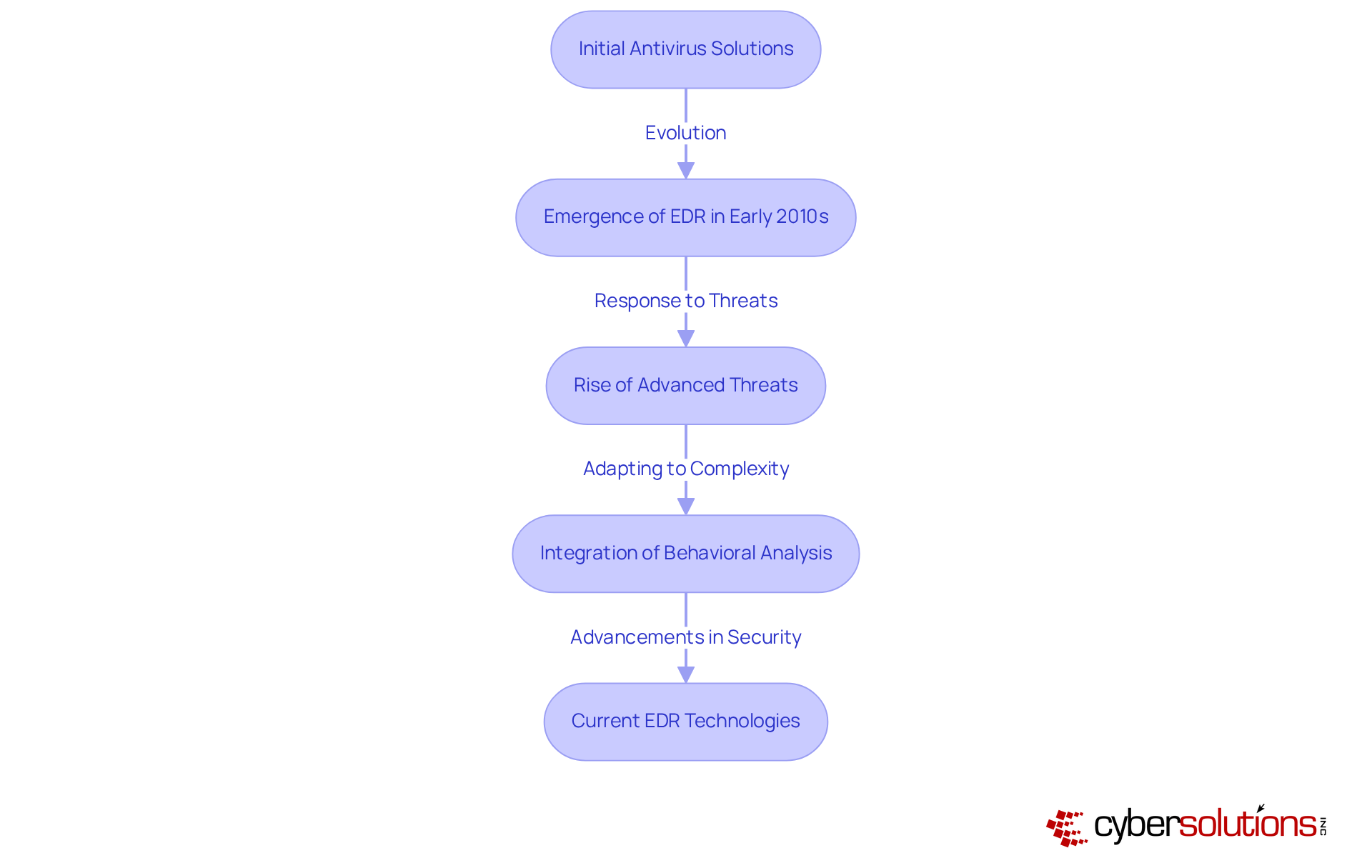
In today’s rapidly evolving cyber landscape, understanding Endpoint Detection and Response (EDR) is not just beneficial; it’s essential for organizations, especially in the healthcare sector, where safeguarding sensitive data is paramount. EDR acts as a critical line of defense, continuously monitoring and responding to threats on endpoint devices. As cyber threats grow more sophisticated, the proactive capabilities of EDR solutions become vital for maintaining organizational integrity and compliance.
The multifaceted nature of EDR includes key features such as:
These elements are crucial in minimizing the impact of cyberattacks, particularly in healthcare, where regulatory compliance is non-negotiable. With the anticipated rise in EDR adoption, organizations must recognize the financial and operational advantages of implementing these solutions to effectively protect their assets.
Investing in EDR technology is not merely a strategic choice; it’s a necessity. Organizations must prioritize the adoption of EDR solutions to stay ahead of potential risks and ensure a robust cybersecurity posture. By embracing EDR, they not only protect sensitive information but also foster trust with clients and stakeholders, ultimately reinforcing their resilience against future cyber challenges.
What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is a cybersecurity solution that continuously monitors, detects, and responds to threats on endpoint devices such as laptops, desktops, and servers. It analyzes data from these endpoints to identify harmful actions in real-time, enhancing an organization's security.
How does EDR differ from traditional antivirus solutions?
Unlike traditional antivirus solutions that primarily use signature-based detection, EDR employs behavioral analysis and robust incident response capabilities. This proactive approach enables faster risk mitigation and reduces downtime from attacks.
What are the key features of EDR technology?
Key features of EDR technology include real-time monitoring, automated threat detection, comprehensive incident response tools, and customizable access controls.
Why is EDR important for organizations?
EDR is crucial for organizations as it significantly bolsters their security posture, protects sensitive data, and ensures compliance with regulatory standards. It is projected that by 2025, nearly 48% of organizations will implement EDR solutions.
What impact can EDR have on ransomware attacks?
EDR can reduce the typical downtime from ransomware attacks, which can last up to 21 days, by swiftly mitigating risks and responding to threats.