
The rise in cyber threats has made it imperative for organizations to adopt robust incident response strategies. The NIST Incident Response Framework stands out as a leading guide in this arena. This structured approach not only equips organizations to manage cybersecurity events effectively but also enhances their overall resilience against potential breaches.
However, despite its proven effectiveness, many organizations struggle with implementation and preparedness. How can businesses ensure they are not just compliant but truly ready to tackle the complexities of cybersecurity incidents? This question is crucial as the landscape of cyber threats continues to evolve, demanding a proactive stance from all sectors, particularly in healthcare.
Organizations must recognize that the stakes are high. A single breach can lead to significant financial losses, reputational damage, and regulatory penalties. Therefore, understanding the unique challenges faced by CFOs and other leaders is essential. By addressing these challenges head-on, organizations can not only comply with regulations but also fortify their defenses against future incidents.
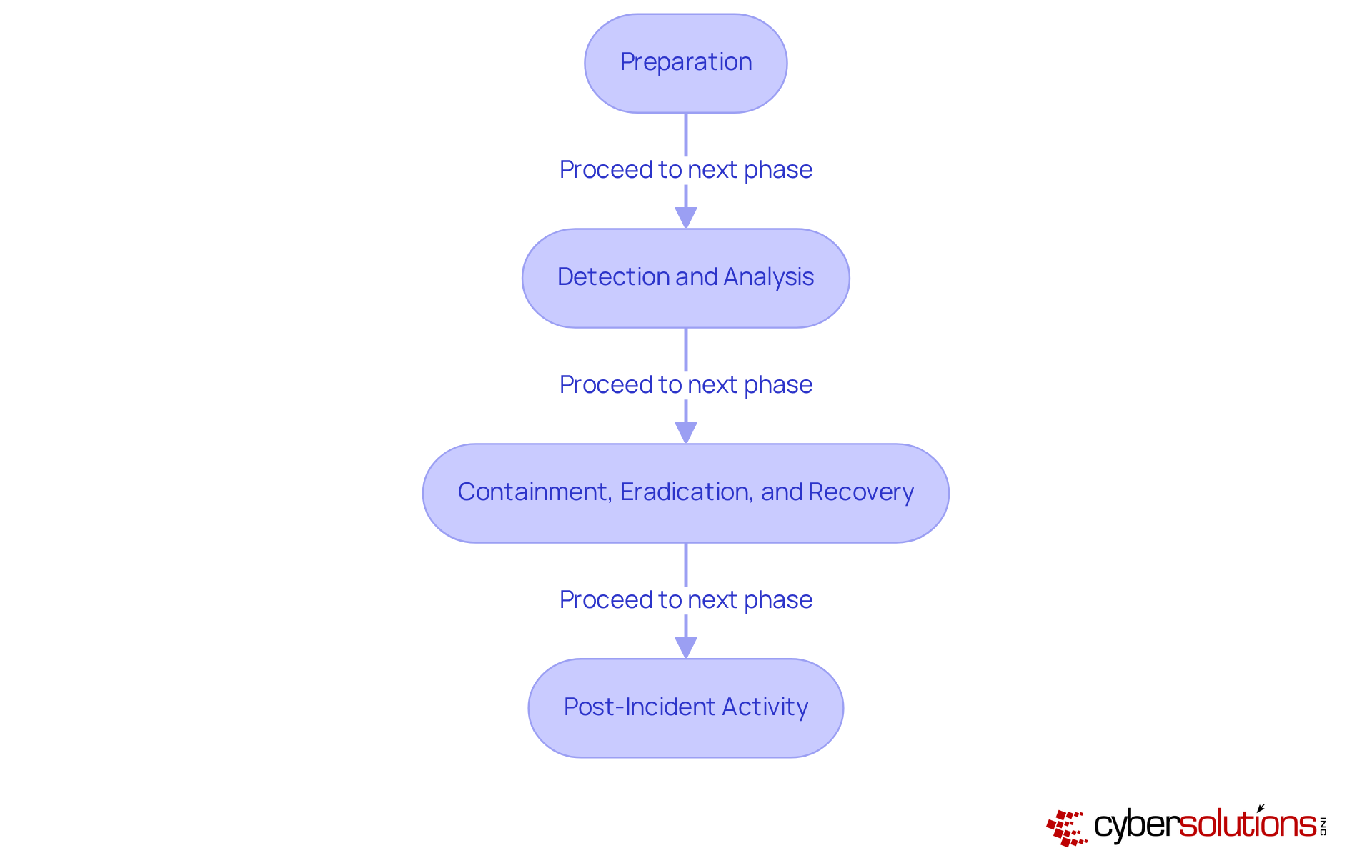
The NIST incident response process offers a comprehensive and structured approach for organizations to effectively manage cybersecurity events. This framework is divided into four essential phases: Preparation, Detection and Analysis, Containment, Eradication, and Recovery, and Post-Incident Activity. Each phase is vital for developing a robust crisis management strategy that not only addresses immediate threats but also adheres to regulatory compliance standards.
Preparation: This phase focuses on establishing and training a crisis management team, developing policies, and ensuring that necessary tools and resources are available. By incorporating application allowlisting during this phase, organizations can ensure that only approved applications run, significantly reducing the risk of unauthorized software execution. Regular response testing is crucial, as it can substantially lower breach costs, underscoring the importance of readiness.
Detection and Analysis: Rapid detection is critical; NIST emphasizes that speed is paramount in minimizing losses. Organizations should implement continuous monitoring to identify anomalies and potential events early. Application allowlisting plays a key role here by blocking unauthorized applications, thus preventing potential breaches before they escalate. This is particularly important given that successful breaches occur in 1 out of every 39 attack attempts.
Containment, Eradication, and Recovery: Once an event is detected, prompt containment becomes the priority to prevent further damage. Application allowlisting ensures that only trusted applications run during recovery efforts. Following containment, eradication efforts must confirm that threats do not persist. Recovery involves reinstating processes and operations, focusing on gaining insights from the event to enhance future actions.
Post-Incident Activity: This stage entails examining the incident to understand its root causes and documenting the remedial actions taken. Organizations should gather data and metadata from system logs to refine their event management strategies and bolster their overall cybersecurity posture. Application allowlisting contributes by providing insights into application usage and potential vulnerabilities.
Real-world implementations of the NIST framework showcase its effectiveness. For instance, entities that have adopted these guidelines report improved event management capabilities and a culture of continuous improvement. By familiarizing yourself with the NIST incident response process and integrating application allowlisting, you lay a solid foundation for mastering crisis management and enhancing your organization's resilience against cyber threats.
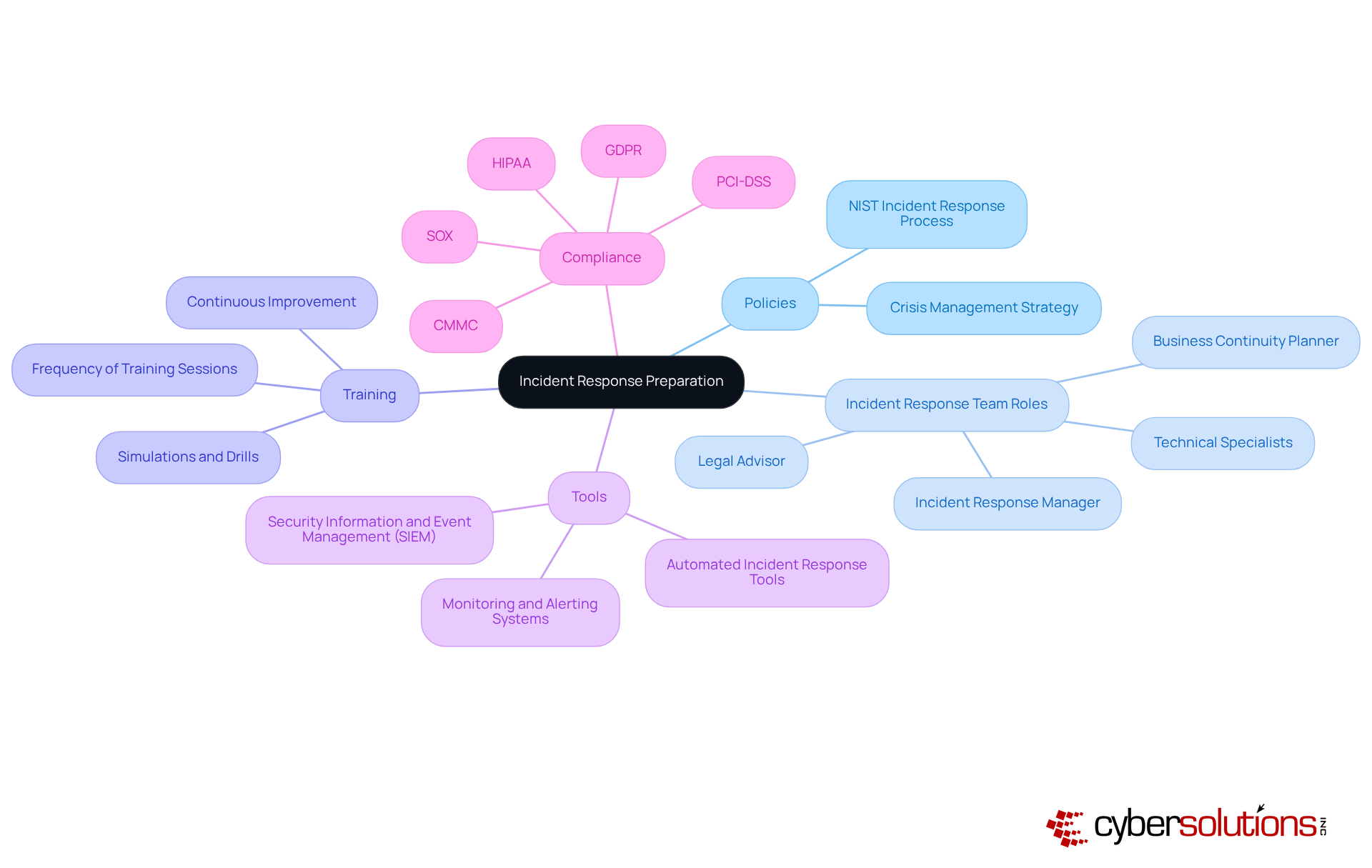
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. To effectively prepare for emergencies, organizations must establish comprehensive guidelines that clearly outline the NIST incident response process for managing various situations. This includes defining distinct roles and responsibilities within an Incident Response Team (IRT) as outlined in the NIST incident response process, which should comprise members from diverse departments such as IT, legal, and communications.
Frequent training sessions are essential to ensure that all team members are well-versed in their roles and the emergency action plan. Notably, organizations with a formal crisis management strategy experience a significantly shorter breach lifecycle: 189 days compared to 258 days for those without a plan. Investing in tools and resources that enhance event detection and handling, such as Security Information and Event Management (SIEM) systems, is crucial.
With 68% of response teams feeling unprepared for actual cyberattacks, adopting the NIST incident response process can greatly improve response effectiveness, minimize potential damage, and ensure compliance with industry regulations like HIPAA, PCI-DSS, CMMC, SOX, and GDPR. By fostering a culture of preparedness and continuous improvement, organizations can navigate the complexities of event management more effectively. Leveraging Cyber Solutions' expertise in Compliance as a Service (CaaS) ensures that they meet all necessary standards.
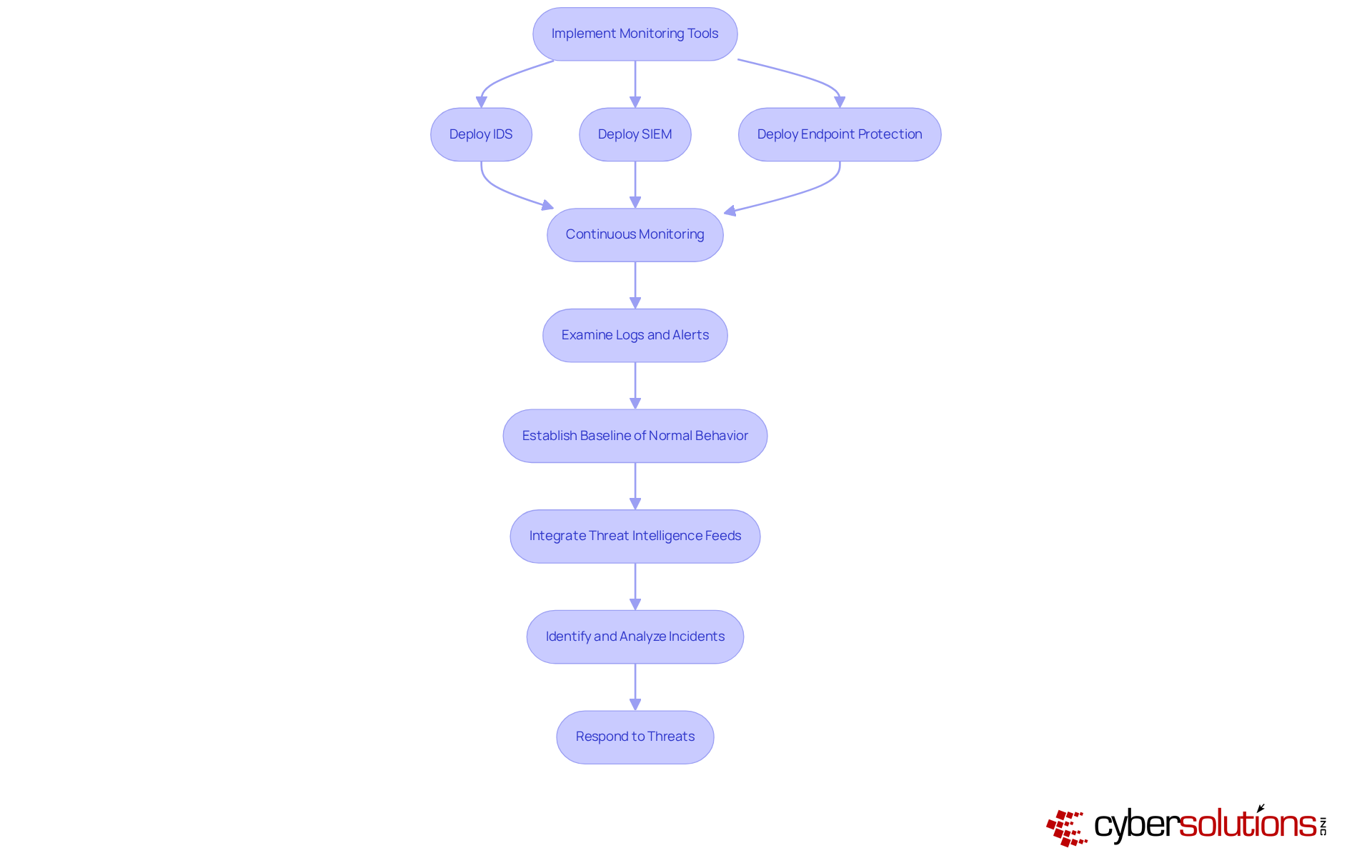
In today's digital landscape, effective monitoring tools are not just beneficial; they're essential for the early identification of cybersecurity events. Organizations must deploy a robust combination of intrusion detection systems (IDS), SIEM solutions, and endpoint protection tools to ensure continuous monitoring of network traffic and system activities. With Cyber Solutions' 24/7 monitoring services, businesses can swiftly detect anomalies and potential vulnerabilities in real-time, enabling prompt action to prevent costly downtime or breaches.
Consistently examining logs and alerts generated by these tools is vital for recognizing suspicious activities that may indicate a security event. Establishing a baseline of normal network behavior is crucial for distinguishing between legitimate activities and potential threats. Furthermore, integrating threat intelligence feeds significantly enhances the detection capabilities of your monitoring tools. By actively identifying and analyzing occurrences, organizations can respond more quickly, minimizing the potential impact of security breaches.
Are you prepared to safeguard your organization against the ever-evolving cybersecurity threats? With the right monitoring tools in place, you can not only protect your assets but also foster a culture of security awareness within your organization.
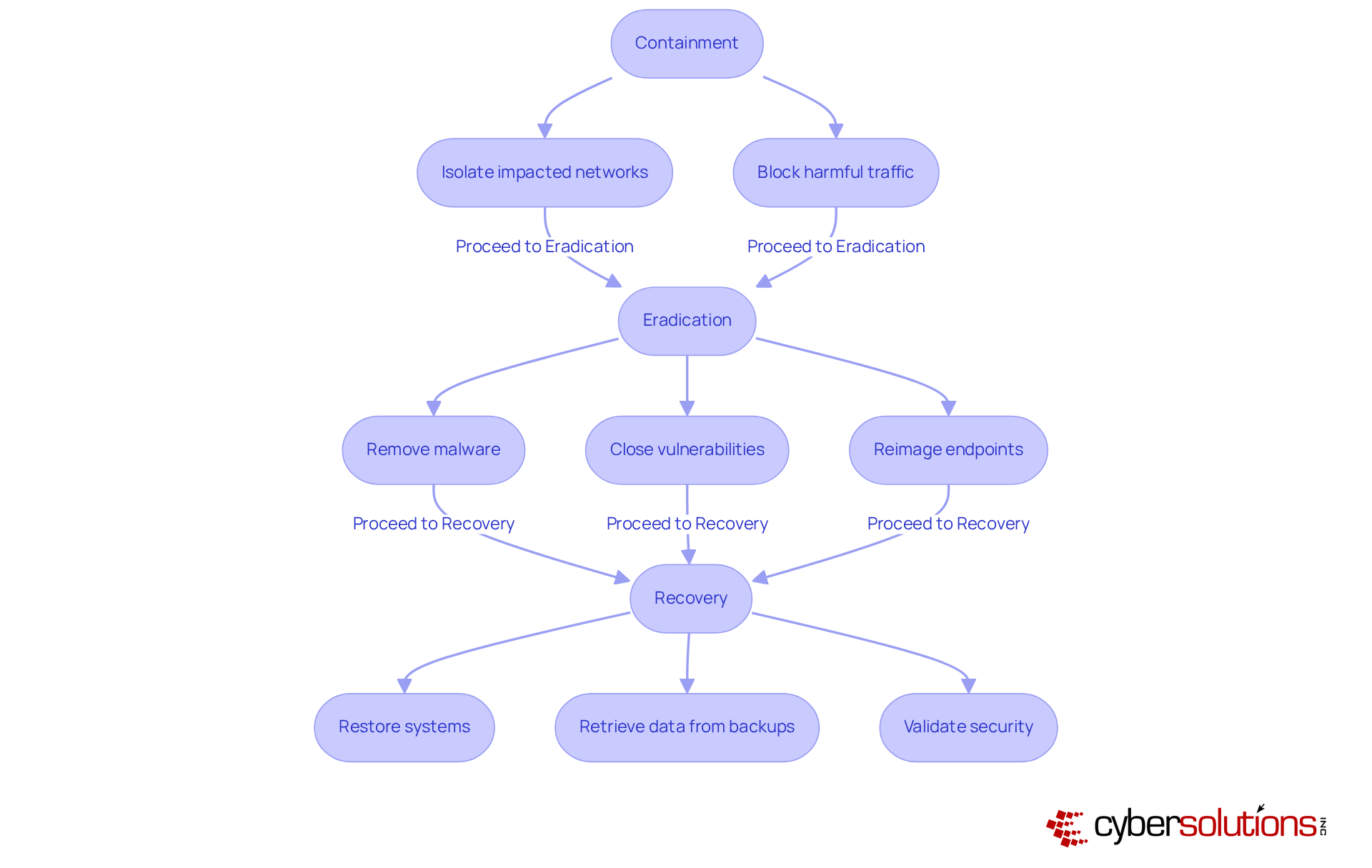
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in the healthcare sector. Cyber threats are evolving rapidly, posing unique challenges that CFOs must navigate to protect sensitive patient data and maintain operational integrity. Upon detecting a cybersecurity incident, it is crucial to follow the NIST incident response process to contain the threat swiftly and mitigate further damage. This involves isolating impacted networks and blocking any harmful traffic.
Following containment, the eradication phase begins, which is critical for ensuring that all traces of malware are removed, vulnerabilities are closed, and the threat is entirely eliminated. Cyber Solutions excels in expert malware removal and platform reconstruction services, ensuring that each compromised endpoint is cleaned, patched, and reimaged where necessary. Steps are taken to close potential attack vectors, update security configurations, and optimize endpoint protections.
Recovery then focuses on restoring systems to normal operations, which may include retrieving data from verified backups and validating the security of systems before they are brought back online. It is crucial to record every action taken during the NIST incident response process, as this information will guide future occurrences and enhance the overall security stance. By applying these techniques effectively, companies can greatly lessen the effect of occurrences and attain quicker recovery times.
Statistics show that entities performing emergency practice exercises at least quarterly can react to events 35% quicker, highlighting the importance of readiness in reducing disruption and ensuring resilience. Moreover, organizations lacking a recorded occurrence management strategy experience a 258-day average breach lifecycle, which emphasizes the essential requirement for the NIST incident response process. The worldwide mean expense of a data breach in 2024 was $4.88 million, underscoring the financial consequences of insufficient crisis management strategies.
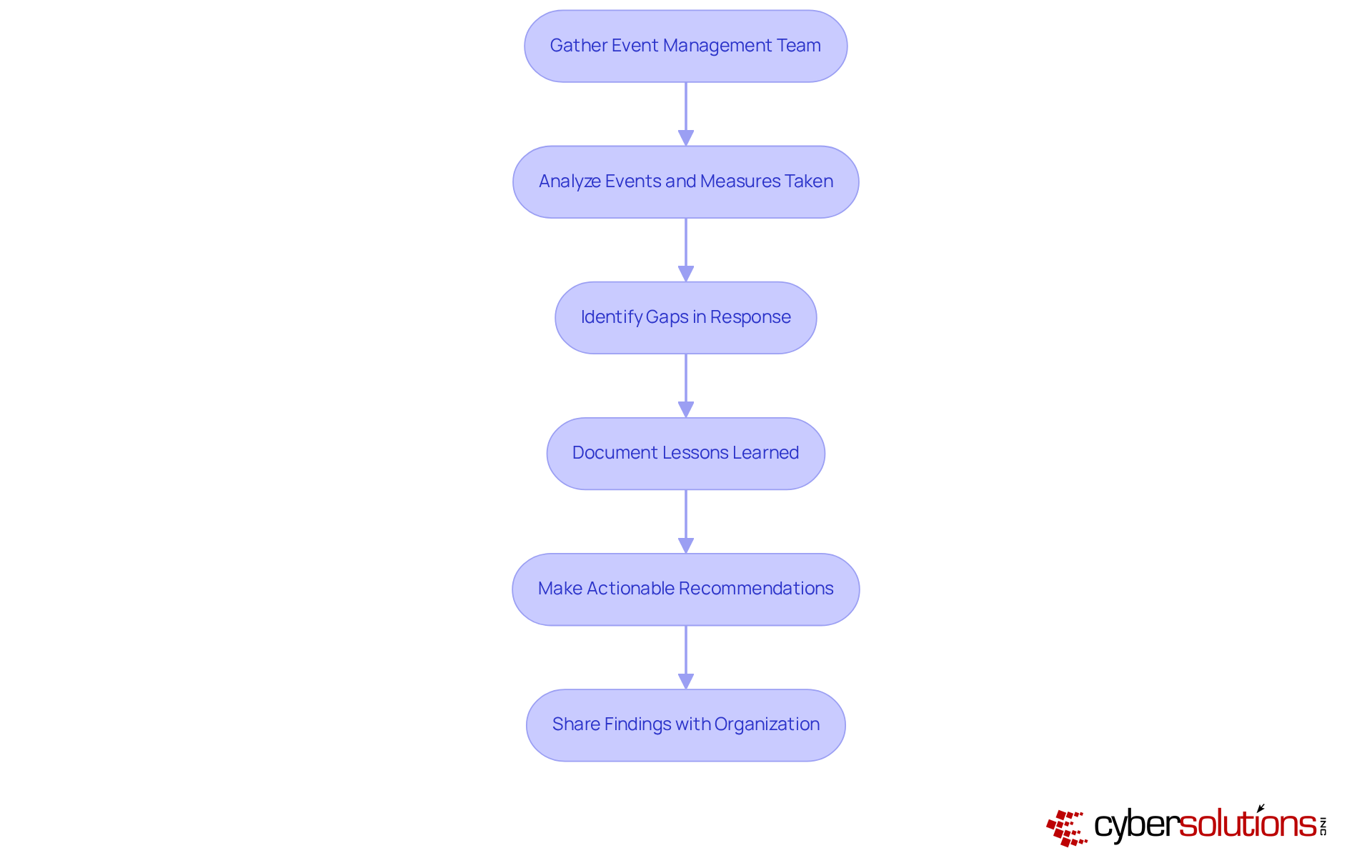
Addressing an occurrence is just the beginning; conducting a thorough post-event analysis is crucial as part of the NIST incident response process. This process involves gathering the event management team and relevant stakeholders to dissect what transpired, the measures taken, and their effectiveness. By examining the timeline of events, identifying gaps in the response, and documenting lessons learned, organizations can gain invaluable insights. This evaluation should culminate in actionable recommendations aimed at enhancing incident management strategies and preparing for future events. Sharing these findings with the broader organization not only boosts awareness but also fosters readiness. By continuously learning from past incidents, organizations can fortify their incident response capabilities in line with the NIST incident response process and significantly diminish the likelihood of future occurrences.
In today's digital landscape, the NIST Incident Response Process stands as an essential framework for organizations determined to manage cybersecurity incidents effectively. This structured approach - encompassing preparation, detection, containment, eradication, recovery, and post-incident review - empowers organizations to respond to threats decisively while ensuring compliance with regulatory standards.
Key strategies emerge from this framework:
Moreover, conducting thorough post-incident analyses is invaluable; these reviews yield insights that enable organizations to refine their incident management strategies and strengthen their overall security posture.
As cyber threats evolve, adopting the NIST Incident Response Process is not merely advisable - it's imperative for organizations committed to safeguarding their assets and maintaining operational integrity. By investing in the right tools, cultivating a culture of preparedness, and learning from past incidents, organizations can build resilience against future cyber challenges. Prioritizing these practices not only ensures compliance with industry regulations but also fosters a proactive stance in the ever-changing cybersecurity landscape.
What is the NIST Incident Response Framework?
The NIST Incident Response Framework is a structured approach for organizations to manage cybersecurity events, divided into four phases: Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Incident Activity.
What is the focus of the Preparation phase in the NIST framework?
The Preparation phase focuses on establishing and training a crisis management team, developing policies, and ensuring the availability of necessary tools and resources, including application allowlisting to reduce the risk of unauthorized software execution.
Why is rapid detection important in the Detection and Analysis phase?
Rapid detection is critical to minimizing losses during a cybersecurity event. Continuous monitoring helps identify anomalies and potential threats early, while application allowlisting blocks unauthorized applications to prevent breaches.
What actions are taken during the Containment, Eradication, and Recovery phase?
In this phase, the priority is to promptly contain the detected event to prevent further damage. This includes ensuring only trusted applications run during recovery, confirming that threats are eradicated, and reinstating processes while gaining insights for future improvements.
What does the Post-Incident Activity phase involve?
The Post-Incident Activity phase involves examining the incident to understand its root causes, documenting remedial actions, and gathering data from system logs to refine event management strategies and enhance cybersecurity posture.
How does application allowlisting contribute to the NIST incident response process?
Application allowlisting helps by ensuring that only approved applications run during the various phases of incident response, thereby reducing the risk of unauthorized software execution and potential breaches.
What are the benefits of establishing an Incident Response Team (IRT)?
An IRT, comprising members from diverse departments, ensures clear roles and responsibilities in managing incidents. Frequent training helps team members understand their roles, contributing to a shorter breach lifecycle and improved response effectiveness.
How does the NIST incident response process help with regulatory compliance?
The NIST incident response process helps organizations comply with industry regulations such as HIPAA, PCI-DSS, CMMC, SOX, and GDPR by providing a structured approach to incident management and enhancing preparedness.
What is the significance of investing in tools like SIEM systems?
Investing in tools such as Security Information and Event Management (SIEM) systems enhances event detection and handling, which is crucial for effective incident response and minimizing potential damage.
What is the impact of having a formal crisis management strategy?
Organizations with a formal crisis management strategy experience a significantly shorter breach lifecycle, averaging 189 days compared to 258 days for those without a plan, indicating improved response effectiveness and preparedness.