
In an era where cyber threats are more pronounced than ever, small and medium-sized businesses (SMBs) stand at a pivotal crossroads. The demand for robust IT services that bolster both security and operational efficiency is more urgent than it has ever been. This article explores ten essential IT services for SMBs that not only safeguard sensitive data but also streamline operations, allowing businesses to concentrate on growth rather than vulnerabilities.
How can organizations effectively navigate the complexities of cybersecurity while ensuring they remain competitive in a swiftly evolving digital landscape?
In today's digital landscape, cybersecurity is not just a luxury; it's a necessity for small and medium-sized enterprises (SMEs). Cyber Solutions Inc. recognizes this urgency and offers a comprehensive suite of SMB IT services tailored specifically for SMEs. Their services include:
By addressing the unique needs of various industries, Cyber Solutions empowers organizations to operate securely and efficiently. This enables them to focus on their core operations without the complexities of IT management. The proactive strategy employed by Cyber Solutions not only enhances operational efficiency but also significantly mitigates the risk of cyber attacks. In an era where threats are ever-evolving, ensuring resilience is paramount.
As industry leaders emphasize, effective SMB IT services are essential for SMEs to thrive. These services deliver strategic value that aligns technology with organizational objectives, ultimately enhancing overall protection. With Cyber Solutions, organizations can navigate the complexities of cybersecurity with confidence, ensuring they remain secure in an increasingly digital environment.
In 2025, endpoint protection is not just important; it’s essential for safeguarding business data against a myriad of cyber risks. With strong protective measures implemented across all devices connected to the network - computers, mobile devices, and servers - organizations can significantly bolster their defenses. Cyber Solutions Inc. stands at the forefront, offering advanced endpoint protection solutions that leverage real-time threat detection and response capabilities. This proactive approach is crucial for preventing unauthorized access and data breaches. Notably, companies that have embraced comprehensive endpoint protection measures, including application allowlisting, have reported a remarkable decline in incidents. In fact, 62% of small enterprises have seen fewer cyber occurrences when supported by dedicated IT teams.
Why is application allowlisting considered the gold standard in cybersecurity? It proactively blocks malware and unauthorized software from executing, effectively reducing the attack surface and minimizing vulnerabilities. This strategy not only helps organizations comply with stringent regulations like HIPAA, PCI-DSS, and GDPR but also thwarts ransomware and other malicious software from infiltrating systems. Key features of application allowlisting include centralized management and continuous monitoring - both vital for effective endpoint protection. Regular updates and ongoing vigilance empower organizations to stay ahead of emerging threats. As cybercriminals increasingly target endpoints, which are responsible for 90% of successful cyberattacks, businesses must adopt a proactive stance. Current trends indicate that integrating advanced endpoint detection and response (EDR) solutions can enhance overall security by identifying and mitigating risks before they escalate.
The rise of remote work has further underscored the necessity for companies to protect their endpoints. A staggering 92% of remote employees use personal tablets or smartphones for work tasks, often without adequate protective measures. By prioritizing endpoint protection and investing in real-time threat detection, SMB IT services can significantly fortify the defenses of small and medium-sized businesses against potential data breaches, ensuring sensitive information remains secure in an increasingly complex digital landscape. To enhance security further, organizations should implement regular training for employees on recognizing phishing attempts and understanding the risks associated with weak passwords. Additionally, Cyber Solutions Inc. offers 24/7 network surveillance and alert services, ensuring that suspicious activities are detected and addressed before they evolve into serious threats, thereby safeguarding operational processes.

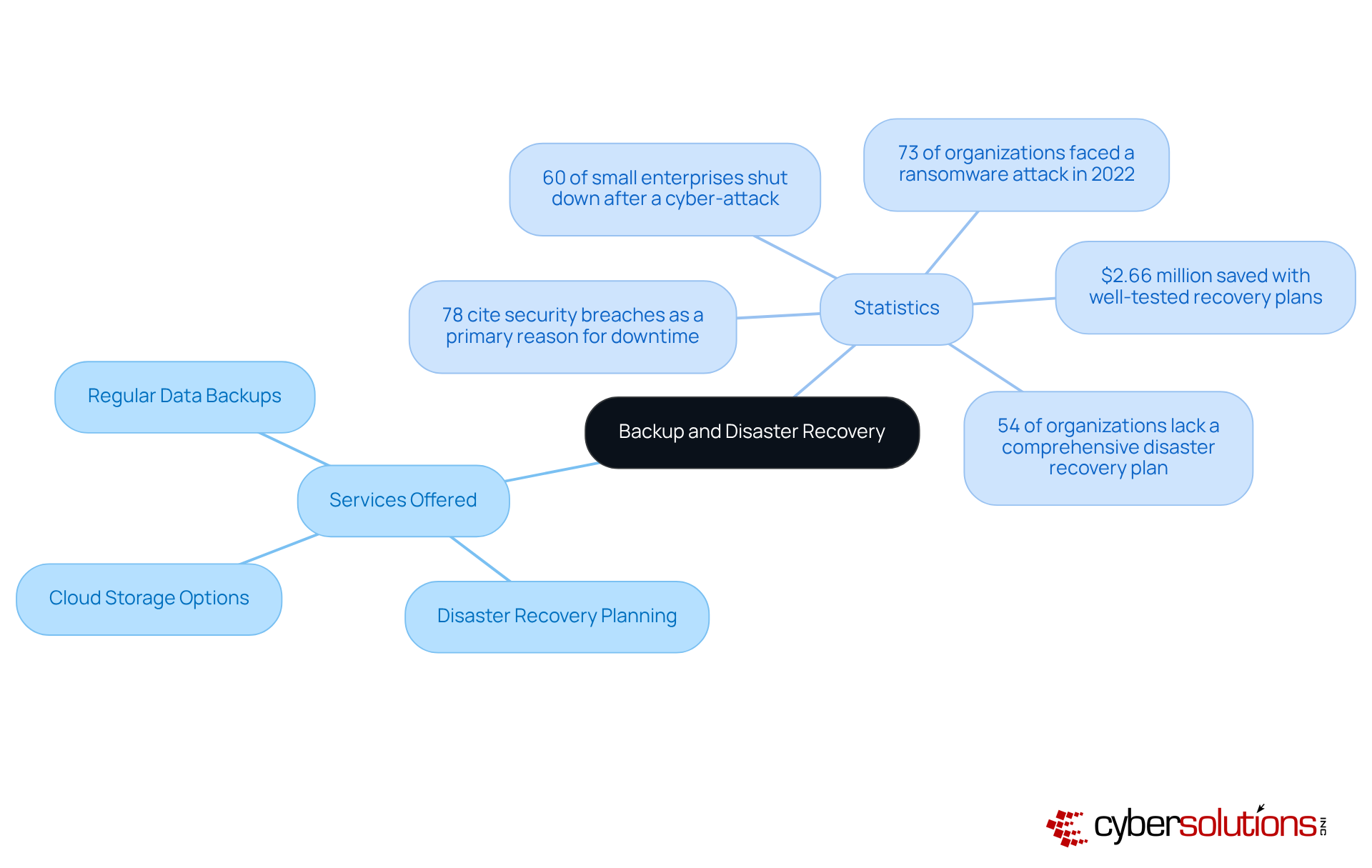
Backup and disaster recovery solutions are not just important; they are essential for maintaining operational continuity in the face of unforeseen challenges like data breaches, natural disasters, or system failures. Cyber Solutions Inc. offers comprehensive backup services, including:
These services empower companies to swiftly recover lost data and continue operations with minimal downtime. Did you know that organizations with well-tested recovery plans can save an average of $2.66 million during disasters? This statistic underscores the financial benefits of preparedness.
The necessity of establishing a strong disaster recovery strategy is further emphasized by alarming statistics:
Industry leaders stress that a robust continuity plan is not merely a safeguard but a strategic advantage. By prioritizing disaster recovery, SMB IT services can help businesses protect their assets, maintain customer trust, and ultimately safeguard their reputation and financial stability.
To ensure effective operational continuity, organizations should regularly test their backup solutions and develop comprehensive recovery plans that are well-documented and updated. This proactive approach not only reduces risks but also improves operational resilience, enabling organizations to thrive even in the face of adversity.
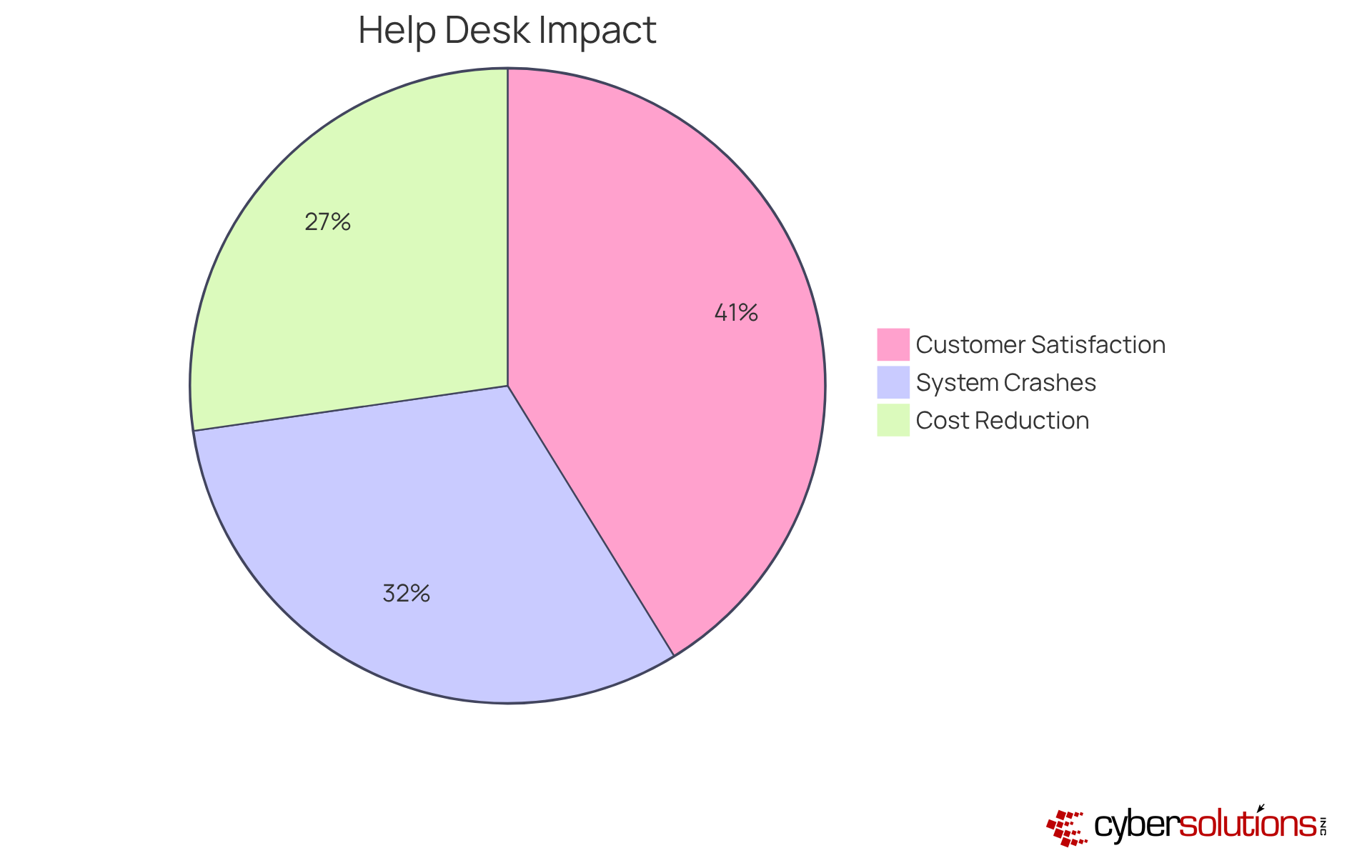
Access to 24/7 help desk support is not just beneficial; it’s essential for minimizing downtime and swiftly resolving technical issues. Cyber Solutions Inc. provides around-the-clock support to tackle any IT-related challenges, ensuring organizations maintain productivity and avoid costly interruptions. Did you know that system crashes account for 52% of downtime instances? Timely troubleshooting can significantly mitigate these impacts, making immediate support crucial.
Whether addressing software glitches or hardware failures, smb IT services provided by a dedicated help desk team empower small and medium-sized businesses to operate seamlessly. This allows employees to concentrate on their core responsibilities without the burden of unresolved IT problems. Current trends reveal that organizations prioritizing immediate IT assistance can cut downtime costs by up to 45%. This statistic reinforces the necessity of investing in robust help desk services.
By leveraging these resources, organizations not only enhance operational efficiency but also boost customer satisfaction. In fact, 68% of customers report a positive perception of brands that offer proactive service notifications. Investing in smb IT services, particularly a reliable help desk, is not merely a choice; it’s a strategic move that can transform your organization’s productivity and reputation.
Managed protection services are crucial for safeguarding small and medium-sized enterprises (SMEs) against the ever-evolving landscape of cyber risks. Cyber Solutions Inc. provides a comprehensive suite of security services, including:
These services utilize advanced technologies and expert knowledge to help businesses identify and mitigate potential threats before they escalate into significant issues.
In 2025, small and medium-sized businesses are confronted with numerous challenges, including a staggering rise in cyberattacks. On average, organizations experience nearly 1,900 attacks weekly - a 75% increase from the previous year. The financial ramifications are severe; the global average cost of a data breach has surged to $4.88 million, underscoring the urgent need for effective protective measures.
By leveraging SMB IT services, SMBs can ensure they have a dedicated response team ready to act swiftly in the event of an incident, thereby minimizing operational disruptions and protecting their reputation. For instance, organizations utilizing Managed Detection and Response (MDR) services have reported a remarkable 62% reduction in annual incidents, demonstrating the effectiveness of these proactive strategies. Furthermore, the enhanced ROI from these services enables businesses to allocate resources more efficiently.
Practical examples highlight the importance of these services: manufacturers that adopted managed protection solutions can identify and respond to incidents 50% faster than those without such support. This capability is vital, especially as ransomware attacks in the manufacturing sector increased by 40% last year, leading to significant downtime and financial losses.
The rapid incident response strategies employed by Cyber Solutions, which include on-site assistance and a layered recovery approach, further bolster the protective measures of organizations, particularly in sensitive sectors like healthcare.
In conclusion, as cyber risks continue to evolve, small and medium-sized businesses must prioritize SMB IT services to enhance their security posture and ensure compliance with regulatory requirements. By doing so, they can concentrate on their core operations while effectively navigating the complexities of cybersecurity.
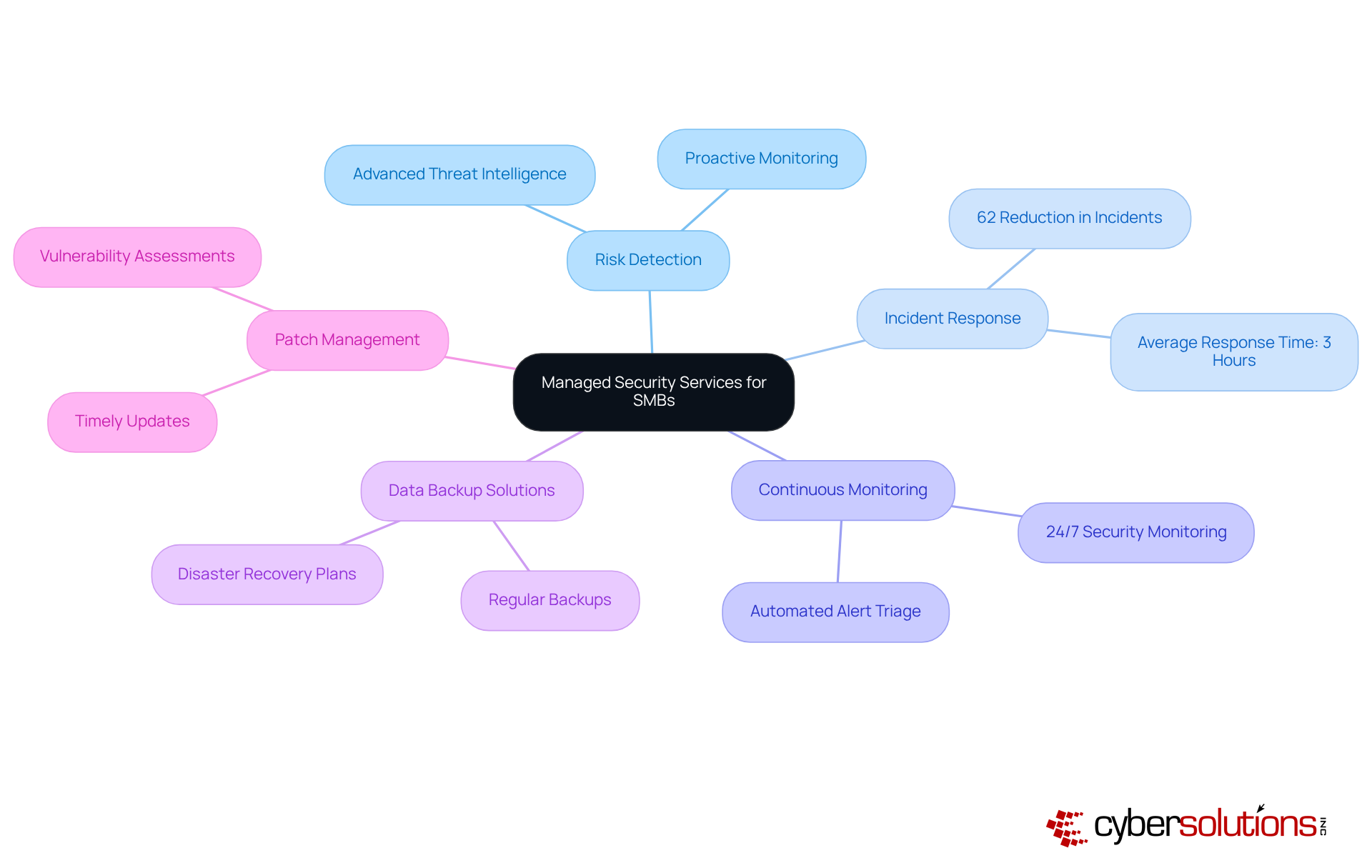
In today's digital landscape, efficient threat identification is essential for the survival of small and medium-sized enterprises (SMEs), and utilizing smb it services can greatly enhance this capability. Cyber Solutions Inc. stands at the forefront, utilizing cutting-edge monitoring technologies that continuously analyze network traffic and user behavior. This real-time analysis enables the swift identification of suspicious activities, allowing businesses to respond proactively and mitigate potential breaches before they escalate into significant incidents.
Consider this: in 2024, a staggering 94% of SMBs faced at least one cyberattack. This statistic underscores the urgent need for proactive cybersecurity measures. By implementing robust security detection systems, organizations not only safeguard sensitive data but also enhance compliance with industry regulations. Regular risk evaluations and timely updates to protective protocols are crucial for adapting to the rapidly evolving cyber environment.
A recent case study illustrates this point vividly. It highlighted how a proactive risk detection system successfully thwarted a ransomware attack on a manufacturing company, preserving operational integrity and avoiding costly downtime. As cyber threats become increasingly sophisticated, small and medium-sized businesses must prioritize smb it services to effectively recognize and address breaches early.
Are you ready to take action? Embrace the future of cybersecurity with Cyber Solutions Inc. and ensure your organization is equipped to face the challenges ahead.
An effective incident response plan is not just beneficial; it’s essential for minimizing the impact of security incidents on small and medium-sized enterprises (SMEs). With Cyber Solutions Inc., organizations gain access to structured incident response services that outline precise steps for detecting, responding to, and recovering from cyber incidents. This comprehensive process involves:
Consider this: organizations equipped with a well-defined incident response strategy can drastically reduce their average response time to incidents. This is often critical in preventing further damage. In fact, those that implement thorough incident response plans can significantly mitigate costs, downtime, and compliance risks associated with breaches.
Current data reveals that 31% of companies face breaches or attacks at least once a week. This statistic underscores the urgent need for SMB IT services to prioritize incident response planning. Alarmingly, only 14% of companies express confidence in their team’s ability to manage cybersecurity risks, highlighting a substantial gap in readiness. By establishing a robust incident response plan, organizations can act swiftly to protect sensitive information and ensure compliance with regulatory requirements, ultimately safeguarding their operations and reputation.
Frequent assessments and revisions of these strategies are not just recommended; they are essential. Such practices enable organizations to adapt to evolving risks and enhance their overall protection stance. Are you prepared to take the necessary steps to fortify your organization against cyber threats?
Vulnerability assessments are crucial for identifying weaknesses within an organization's IT infrastructure, especially in today's digital landscape. Cyber Solutions Inc. conducts thorough evaluations of systems, applications, and networks to pinpoint potential vulnerabilities. This proactive approach empowers companies to implement essential protective measures, significantly reducing risks associated with cyber threats.
Regular assessments not only strengthen security posture but also ensure compliance with industry regulations. This is increasingly vital, considering that 60% of cyber breaches stem from third-party vendors. As we look ahead to 2025, the landscape of vulnerability assessment tools is evolving, emphasizing automation and real-time monitoring. This evolution enables organizations to address vulnerabilities more efficiently.
By prioritizing these assessments, organizations can effectively safeguard sensitive data, maintain customer trust, and enhance their operational resilience in a rapidly changing digital environment. Are you ready to take the necessary steps to protect your organization from potential cyber threats?
Compliance as a Service (CaaS) is essential for SMB IT services that support small and medium-sized businesses grappling with intricate regulatory requirements. In today’s landscape, where compliance is non-negotiable, Cyber Solutions offers CaaS to help organizations navigate regulations like HIPAA, PCI-DSS, and GDPR. This comprehensive service encompasses:
By outsourcing compliance management to SMB IT services, small and medium-sized businesses can concentrate on their core operations while significantly reducing the risk of non-compliance and the associated penalties.
But that’s not all-our Incident Response services are meticulously designed to swiftly identify, contain, and mitigate threats, ensuring operational continuity even in the face of cyberattacks.
With proactive measures such as application allowlisting, we bolster your cybersecurity posture by preventing unauthorized software from executing. This not only reduces vulnerabilities but also ensures compliance with stringent data protection protocols.
Are you ready to enhance your compliance strategy and safeguard your business against evolving threats?
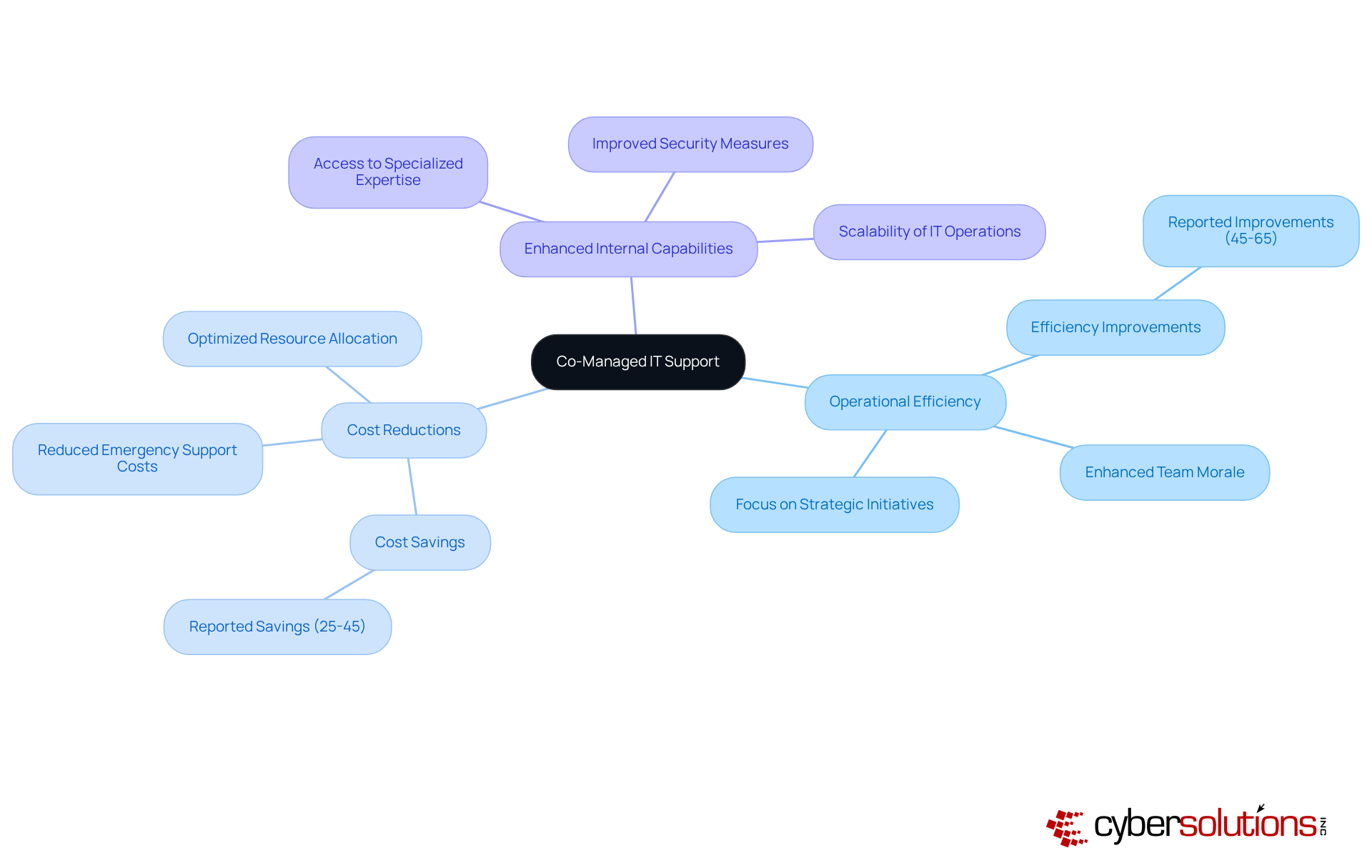
Co-managed IT support stands as a vital strategy for small and medium-sized businesses seeking to enhance their SMB IT services and internal IT capabilities. In today’s rapidly evolving digital landscape, partnering with Cyber Solutions Inc. allows organizations to seamlessly integrate additional resources and specialized expertise into their existing IT teams. This collaboration not only enables effective scaling of IT operations but also significantly strengthens security and operational responsiveness.
Consider this: companies utilizing co-managed IT services often report operational efficiency improvements of 45-65% and cost reductions of 25-45% within the first year of implementation. This hybrid model empowers internal teams to concentrate on strategic initiatives while routine tasks are managed externally, fostering improved morale and job satisfaction. As SMBs navigate the complexities of modern IT environments, utilizing SMB IT services becomes essential for maintaining a robust and agile IT infrastructure that adapts to changing business demands.
In today’s digital landscape, the significance of robust IT services for small and medium-sized businesses (SMBs) is paramount. Cyber Solutions Inc. provides a comprehensive suite of services tailored to bolster security and operational efficiency, enabling organizations to thrive amidst the complexities of modern technology. By prioritizing managed IT support, businesses can concentrate on their core operations, confidently entrusting their cybersecurity needs to seasoned experts.
Essential services include:
Each of these components is crucial for safeguarding data, minimizing downtime, and ensuring business continuity. Moreover, strategies like vulnerability assessments and incident response planning are vital for pinpointing weaknesses and swiftly addressing security incidents, ultimately protecting the organization’s reputation and financial stability.
To effectively navigate the evolving landscape of cybersecurity, SMBs must invest in these IT services. This investment not only enhances their security posture but also positions them for long-term success. Embracing these solutions is not merely a defensive measure; it is a strategic imperative that empowers businesses to innovate and grow while confidently managing the risks associated with the digital age.
What services does Cyber Solutions Inc. offer for small and medium-sized businesses (SMBs)?
Cyber Solutions Inc. offers a comprehensive suite of IT services for SMBs, including 24/7 help desk support, advanced cybersecurity solutions (such as endpoint protection, email security, and firewalls), and robust backup and disaster recovery options.
How does Cyber Solutions Inc. enhance operational efficiency for SMEs?
By addressing the unique needs of various industries, Cyber Solutions Inc. empowers organizations to operate securely and efficiently, allowing them to focus on their core operations without the complexities of IT management.
Why is endpoint protection important for businesses?
Endpoint protection is essential for safeguarding business data against cyber risks by implementing strong protective measures across all devices connected to the network, thus significantly bolstering defenses against unauthorized access and data breaches.
What is application allowlisting and why is it considered the gold standard in cybersecurity?
Application allowlisting is a proactive security measure that blocks malware and unauthorized software from executing, reducing the attack surface and minimizing vulnerabilities. It helps organizations comply with regulations and prevents ransomware and other malicious software from infiltrating systems.
What are the key features of application allowlisting?
Key features include centralized management and continuous monitoring, which are vital for effective endpoint protection, along with regular updates and ongoing vigilance to stay ahead of emerging threats.
How does Cyber Solutions Inc. support backup and disaster recovery for SMBs?
Cyber Solutions Inc. offers comprehensive backup services, including regular data backups, cloud storage options, and detailed disaster recovery planning to ensure operational continuity in the face of unforeseen challenges.
What are the financial benefits of having a well-tested disaster recovery plan?
Organizations with well-tested recovery plans can save an average of $2.66 million during disasters, highlighting the financial advantages of preparedness.
What statistics emphasize the importance of disaster recovery for small enterprises?
Statistics show that 60% of small enterprises shut down within six months of facing a cyber-attack, and 78% of companies identify security breaches as the primary reason for downtime.
How can organizations improve their operational resilience?
Organizations can improve operational resilience by regularly testing their backup solutions, developing comprehensive recovery plans that are well-documented and updated, and prioritizing disaster recovery strategies.