
In today's digital landscape, the threat of cyberattacks looms larger than ever, making robust security measures not just important, but essential for C-suite leaders responsible for safeguarding sensitive information. As we move into 2025, organizations face a myriad of cybersecurity challenges, and dark web scanners have emerged as critical tools in this fight. These scanners provide invaluable insights into potential data breaches and compromised credentials, helping leaders stay one step ahead of the ever-evolving risks that lurk in the shadows of the internet.
But with so many options available, how can executives determine which scanners deliver the most effective protection? The stakes are high, and the consequences of inaction can be devastating. It's time for leaders to take a proactive stance in their cybersecurity strategies, ensuring they have the right tools to combat these threats head-on.
In today’s digital landscape, the importance of cybersecurity cannot be overstated, especially for healthcare organizations. With cyber threats evolving at an alarming rate, CFOs face unique challenges in safeguarding sensitive data. Cyber Solutions offers a cutting-edge deep web scanner and dark web scanners that vigilantly monitor the concealed corners of the internet for any compromised data associated with your organization. This tool not only alerts you to potential breaches but also delivers actionable insights to effectively mitigate risks. By employing sophisticated algorithms combined with expert human analysis, the scanner safeguards your sensitive information, enabling you to concentrate on your core business operations without the persistent anxiety of cyber threats.
Alongside deep web surveillance, Cyber Solutions provides thorough 24/7 network oversight services that identify irregularities and possible weaknesses in real-time. This ongoing observation guarantees that suspicious activities are recognized and handled before they develop into serious threats. Organizations employing dark web scanners together with network oversight have reported significant enhancements in their cybersecurity stance. For instance, companies that adopted such oversight have been able to detect and respond to data breaches before they escalate, thereby minimizing potential damage. The proactive nature of concealed web oversight, combined with robust network alerts and customized access controls, is vital in today’s environment, where cybercriminals are becoming more sophisticated and relentless.
Specialists in cybersecurity stress the importance of deep web monitoring as a crucial element of a strong security strategy. They observe that being aware of compromised credentials and sensitive information on the concealed web enables organizations to take proactive measures, such as changing passwords and strengthening security protocols, ultimately decreasing the risk of data breaches and financial losses.
In light of recent developments, including the discontinuation of Google's hidden web report tool, the importance of reliable dark web scanners cannot be overstated. Google’s decision to phase out its service due to user feedback about its limitations underscores the need for tools that provide clear, actionable steps for organizations. Cyber Solutions' dark web scanners, along with our 24/7 network monitoring services that include tailored restrictions, act as a vital line of defense, ensuring organizations remain vigilant and prepared against the ever-present risks lurking in the shadows of the internet.
In today’s digital landscape, cybersecurity is not just a necessity; it’s a critical imperative for safeguarding sensitive information. 'Have I Been Pwned?' serves as an essential, complimentary service that empowers users to verify if their email addresses or passwords have been compromised in security breaches. By simply entering an email address, users can swiftly determine whether their information has been exposed, allowing them to take immediate action to protect their accounts.
This tool is particularly vital for C-suite leaders, who face the daunting task of securing both personal and corporate data in an increasingly hostile environment. With over 1 billion compromised accounts monitored, 'Have I Been Pwned?' stands out as a crucial resource for executives aiming to mitigate risks associated with information breaches. Cybersecurity experts stress the importance of proactive measures; regular checks can significantly lower the chances of falling victim to cyber threats.
Consider the impact: C-suite leaders who have effectively utilized 'Have I Been Pwned?' have not only enhanced their personal security but also fortified their organizations against potential breaches. This showcases the tool's efficacy in protecting sensitive details and underscores the necessity of integrating such resources into a comprehensive cybersecurity strategy. Are you ready to take the necessary steps to safeguard your information?
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for C-suite executives. Aura's dark web scanners provide essential oversight of personal information, notifying users when sensitive details appear on the dark web. This capability is vital for safeguarding identities and personal data from cybercriminals, who increasingly target high-profile individuals.
With real-time alerts and comprehensive monitoring, Aura empowers users to act swiftly against potential threats. This proactive approach underscores the critical role of personal cybersecurity in corporate governance. As the exposure of personal data continues to escalate, leaders must recognize that their identities are prime targets for cyberattacks.
Incorporating tools like Aura not only enhances personal security but also fortifies the overall cybersecurity posture of organizations by utilizing dark web scanners. By prioritizing personal cybersecurity, executives can protect themselves and their companies from the devastating impacts of data breaches.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for healthcare organizations. Identity Guard stands out with its robust dual protection strategy, merging deep web surveillance with identity theft protection. This service uses dark web scanners to continuously scan for compromised personal information, delivering real-time alerts to users. Not only does it monitor potential threats, but it also provides identity theft insurance and recovery services, ensuring users are informed and shielded from financial repercussions.
For C-suite leaders, this comprehensive security approach is essential for safeguarding both personal and corporate information. As identity theft and cyber threats grow increasingly sophisticated, organizations must prioritize proactive measures to mitigate risks associated with identity fraud and information breaches. Cyber Solutions enhances this protective framework with a layered approach that includes endpoint isolation, malware removal, and user training, further bolstering security configurations and promoting staff cyber hygiene.
Their 24/7 threat monitoring is crucial, as it detects and halts suspicious activities before they escalate into serious threats, effectively safeguarding against ransomware and phishing attacks. This thorough strategy is vital, particularly as identity fraud incidents are exacerbated by AI, extensive information exposure, and inconsistent protection standards. By adopting these measures, healthcare organizations can not only protect their assets but also foster trust and confidence among their stakeholders.
In today's digital landscape, cybersecurity is not just a technical concern; it's a critical priority for C-suite leaders, especially in healthcare. Firefox Monitor serves as an essential browser-based tool that alerts users if their email addresses have been compromised in recognized security breaches. By utilizing the extensive database from 'Have I Been Pwned?', it offers timely notifications that empower leaders to take immediate action to secure their accounts.
This tool is particularly vital for executives who frequently engage with web applications, as they face unique challenges in safeguarding their online activities from potential threats. With the increasing frequency of data breaches, how can leaders ensure their organizations remain secure? Firefox Monitor provides a proactive solution, allowing leaders to stay informed and act swiftly in the face of evolving cybersecurity risks.
By integrating such tools into their cybersecurity strategy, C-suite leaders can not only protect their personal information but also uphold the integrity of their organizations. In a world where every click can lead to a security breach, taking advantage of resources like Firefox Monitor is not just advisable - it's imperative.
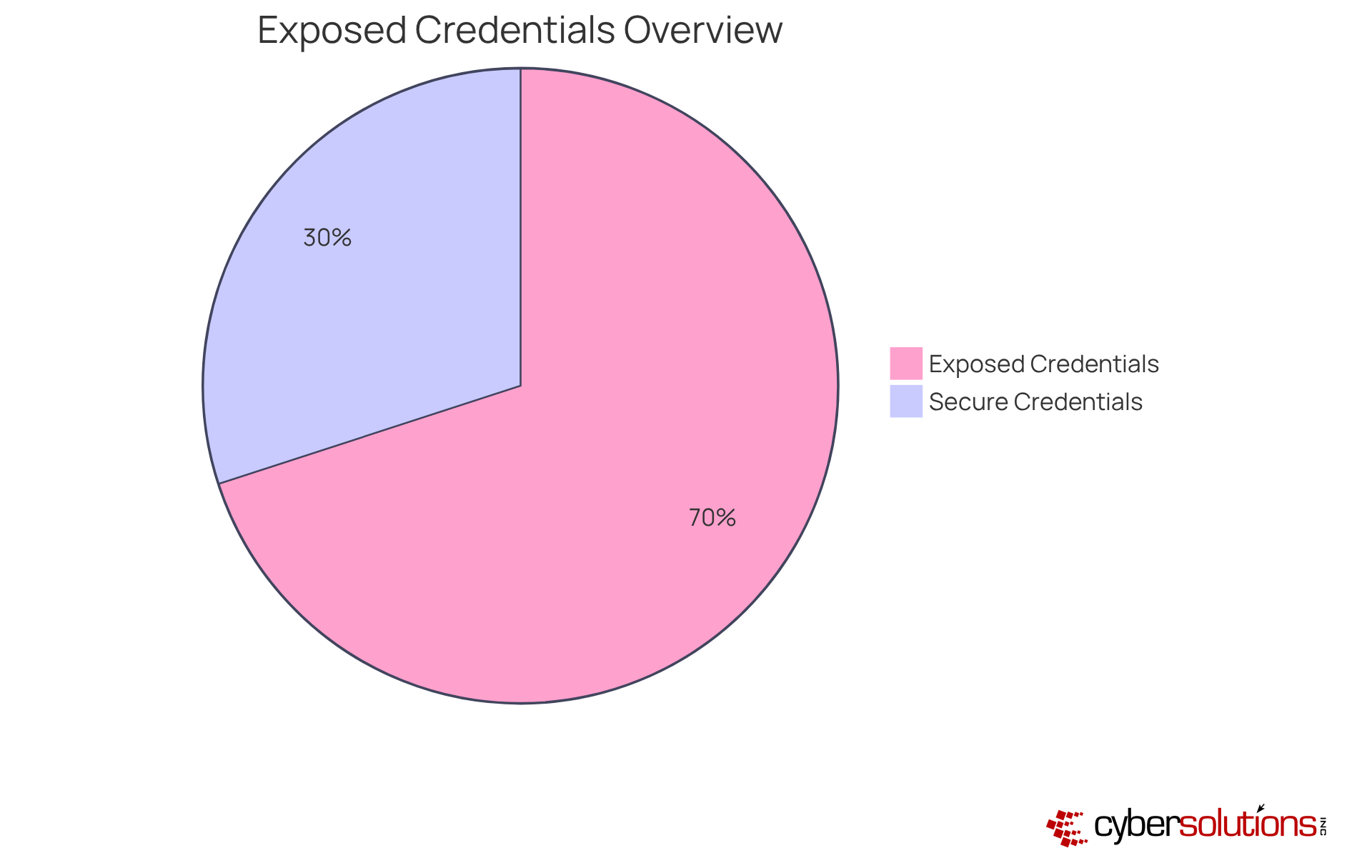
In today's digital landscape, the urgency of cybersecurity cannot be overstated. With over 1.8 billion credentials compromised in just the first half of 2025, organizations face a relentless tide of threats that demand immediate attention. Dehashed specializes in using dark web scanners to track credentials, alerting users when their personal information, including email addresses and passwords, surfaces in security breaches. This proactive service is essential for organizations managing sensitive data, enabling them to swiftly mitigate risks and safeguard their assets.
For C-suite leaders, understanding the pervasive threats posed by credential theft is crucial for ensuring organizational security and compliance. Cyber Solutions emphasizes the importance of 24/7 network oversight and alerts to identify anomalies and potential vulnerabilities. This vigilance allows organizations to take prompt action against threats such as ransomware and phishing attacks. Cybersecurity experts stress that rapid response to detected breaches is vital; organizations must act immediately to revoke access and enforce password resets to minimize potential damage. Alarmingly, 50% of organizations take three days or longer to revoke access after employee departures, highlighting the critical need for timely action.
As Ariel Parnes, COO of Mitiga, aptly states, "Companies must incorporate insights gained from dark web scanners into their internal oversight." Tailored access controls and the adaptability of Cyber Solutions' services are indispensable for addressing evolving threats. As the landscape of cyber threats continues to shift, integrating deep web monitoring into security strategies is no longer optional; it is essential for protecting valuable corporate information. Organizations must prioritize these measures to ensure their defenses are robust and responsive.
In today's digital landscape, cybersecurity is not just an option; it's a necessity. MyPwd emerges as a powerful password management tool, equipped with dark web scanners that utilize artificial intelligence to monitor the deep and concealed web for any leaked passwords tied to user accounts. This proactive strategy ensures organizations receive timely alerts when compromised passwords are detected, allowing for swift action to mitigate potential security breaches.
For C-suite leaders, employing a password manager like MyPwd, which features web scanning, is essential for safeguarding sensitive corporate information and maintaining a strong security posture. Organizations that have adopted MyPwd report enhanced security practices, underscoring the tool's effectiveness in navigating the ever-evolving landscape of cyber threats. Cybersecurity experts consistently stress the importance of robust password practices; after all, a single compromised password can expose significant vulnerabilities.
By integrating advanced tools such as MyPwd, executives can fortify their organizations against potential cyberattacks, ensuring resilience in the face of growing threats. The stakes are high, and the time to act is now.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially for organizations handling sensitive information. Dashlane seamlessly integrates password management with deep web oversight, offering a powerful security solution that alerts users when their passwords appear on the deep web. This proactive strategy not only fortifies password security through features like password generation and secure storage but also keeps users informed of potential threats.
Organizations can significantly enhance their cybersecurity frameworks by leveraging Cyber Solutions' 24/7 threat monitoring. This comprehensive approach ensures that sensitive information is protected from ransomware, phishing, and other malware attacks. For C-suite leaders, Dashlane emerges as an indispensable tool in navigating the complexities of cybersecurity, empowering them to safeguard their organizations against evolving digital threats while maintaining operational efficiency.
As the landscape of integrated password management solutions evolves, Dashlane stands out for its ability to tackle the pressing challenges executives face in protecting their organizations' critical information. Are you ready to take the necessary steps to secure your organization? With Dashlane, you can confidently navigate the intricate world of cybersecurity, ensuring that your sensitive data remains protected.
In today's digital landscape, the importance of cybersecurity cannot be overstated. Intelligence X serves as a powerful search engine and information repository, enabling organizations to scrutinize compromised information from diverse sources, including through dark web scanners. By delivering comprehensive insights into leaks and breaches, it empowers C-suite leaders to grasp the extent of their exposure and make informed decisions. This tool not only deepens the understanding of cybersecurity threats but also plays a pivotal role in strategic decision-making.
Organizations leveraging Intelligence X have successfully pinpointed vulnerabilities and mitigated risks associated with breaches, demonstrating its effectiveness in real-world applications. Cybersecurity specialists emphasize that comprehending information leaks is vital for organizations aiming to bolster their defenses and respond proactively to emerging threats. Current trends reveal an increasing dependence on advanced breach analysis tools, which are essential for navigating the complexities of cybersecurity today.
By utilizing Intelligence X, leaders can stay ahead of potential threats, ensuring their organizations are well-prepared to confront the evolving challenges in cybersecurity. Are you ready to take the necessary steps to protect your organization?
In today’s digital landscape, the threat of information leaks is more pressing than ever. Hashcast stands out by focusing on the critical issue of employee email and password exposure as identified by dark web scanners. This targeted approach allows organizations to quickly identify and mitigate potential threats, effectively protecting sensitive data. For C-suite leaders, leveraging Hashcast isn’t just a precaution; it’s a vital strategy for safeguarding their organization’s information and ensuring compliance with regulatory standards.
Cybersecurity experts stress the importance of investing in proactive data security measures, especially considering that over 70% of firms have executive credentials exposed to dark web scanners. This alarming statistic underscores the urgency for organizations to enhance their defenses. By adopting advanced monitoring solutions like Hashcast, businesses can not only fortify their security posture but also stay ahead of emerging threats.
Ultimately, the question remains: can your organization afford to overlook such a critical aspect of cybersecurity? With Hashcast, you can take decisive action to protect your valuable information and maintain a robust security framework.
The importance of dark web scanners in protecting sensitive information is paramount for C-suite leaders today, especially as cyber threats grow more sophisticated. These tools are not just optional; they are essential components of a robust cybersecurity strategy, proactively identifying vulnerabilities and equipping organizations with the insights necessary to safeguard their assets effectively.
As we delve into ten essential dark web scanners, several key insights emerge. From Cyber Solutions' comprehensive protection and real-time alerts to the intuitive interface of 'Have I Been Pwned?', each tool presents unique features designed to enhance security. Moreover, the integration of password management solutions like MyPwd and Dashlane underscores the necessity of a multi-faceted approach in the fight against cyber threats. These resources empower executives to act swiftly against potential breaches, ensuring that both personal and corporate data remain secure.
In a landscape where cybercriminals are increasingly adept, the message is clear: organizations must prioritize the adoption of advanced monitoring tools and proactive cybersecurity measures. By leveraging these dark web scanners, leaders can not only strengthen their defenses but also foster a culture of vigilance within their organizations. The time to act is now-protecting sensitive information is not merely a necessity; it is imperative for maintaining trust and integrity in our interconnected world.
What is the purpose of Cyber Solutions' dark web scanner?
Cyber Solutions' dark web scanner monitors the concealed corners of the internet for compromised data associated with organizations, alerting them to potential breaches and providing actionable insights to mitigate risks.
How does the dark web scanner enhance cybersecurity for organizations?
The scanner employs sophisticated algorithms and expert human analysis to safeguard sensitive information, allowing organizations to focus on their core operations without the anxiety of cyber threats.
What additional services does Cyber Solutions offer alongside the dark web scanner?
Cyber Solutions provides 24/7 network oversight services that identify irregularities and weaknesses in real-time, ensuring that suspicious activities are recognized and addressed before they escalate into serious threats.
Why is deep web monitoring considered important by cybersecurity specialists?
Deep web monitoring helps organizations become aware of compromised credentials and sensitive information, enabling them to take proactive measures like changing passwords and strengthening security protocols, thus reducing the risk of data breaches.
What recent development has highlighted the need for reliable dark web scanners?
The discontinuation of Google's hidden web report tool has underscored the importance of dark web scanners that provide clear, actionable steps for organizations to remain vigilant against cyber threats.
What is 'Have I Been Pwned?' and how does it function?
'Have I Been Pwned?' is a complimentary service that allows users to check if their email addresses or passwords have been compromised in security breaches by simply entering their email address.
Who can benefit from using 'Have I Been Pwned?'?
C-suite leaders can particularly benefit from this tool as it helps secure both personal and corporate data against potential breaches.
How does using 'Have I Been Pwned?' enhance security for executives?
Regular checks with 'Have I Been Pwned?' can significantly lower the chances of falling victim to cyber threats, thereby enhancing personal security and fortifying organizations against breaches.
What is the role of Aura's dark web scanner?
Aura's dark web scanner provides oversight of personal information, notifying users when sensitive details appear on the dark web, which is crucial for safeguarding identities from cybercriminals.
Why is personal cybersecurity important for C-suite executives?
Personal cybersecurity is critical for C-suite executives as their identities are prime targets for cyberattacks, and protecting personal data also fortifies the overall cybersecurity posture of their organizations.