
An Incident Response Plan (IRP) is not merely a formal document; it serves as a vital framework that empowers organizations to adeptly navigate the turbulent waters of cybersecurity threats.
In a landscape where cyberattacks are becoming increasingly sophisticated, the necessity of a well-structured IRP is undeniable. It provides businesses with a roadmap for swift detection, response, and recovery from incidents.
Yet, with nearly half of organizations lacking a documented plan, one must ask: can businesses truly afford to overlook this essential strategy in an era where every second counts during a breach?
The stakes are high, and the time to act is now.
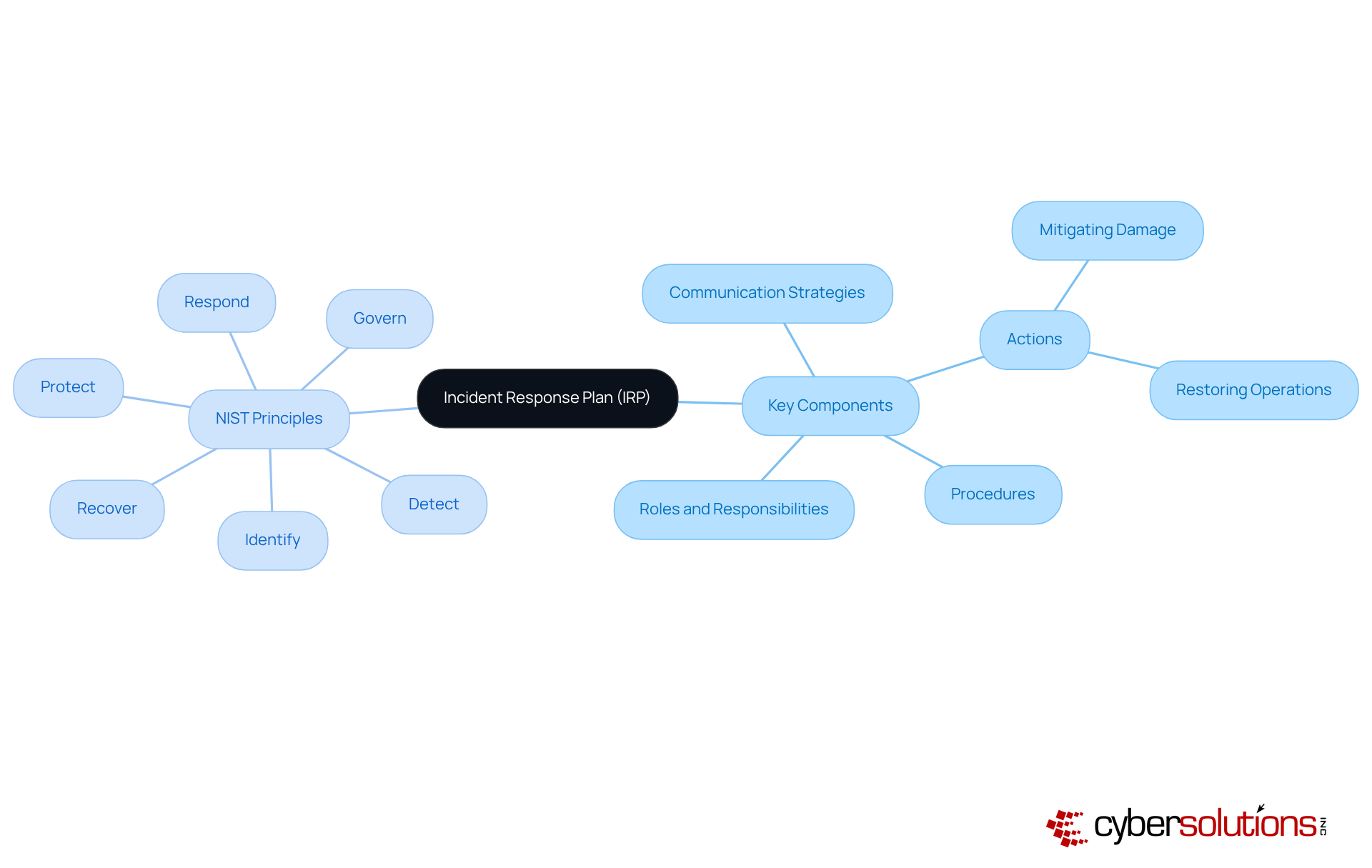
An IR plan is not just a formal document; it’s a vital strategy that outlines the procedures and protocols a company must follow in response to cybersecurity events. In today’s landscape, where cyber threats are increasingly sophisticated, having an IR plan is essential for guiding teams in detecting, responding to, and recovering from security breaches or attacks. This plan typically includes predefined roles and responsibilities, communication strategies, and specific actions aimed at mitigating damage and restoring normal operations.
By establishing an IR plan, companies can ensure a coordinated and effective response to incidents, significantly reducing potential impacts on business continuity and data integrity. Consider this: organizations with an IRP experience an average breach lifecycle of 258 days, compared to just 189 days for those without one. Alarmingly, 45% of entities currently lack a documented IR plan, underscoring the urgent need for businesses to prioritize this critical aspect of their cybersecurity strategy.
According to NIST, effective response to an event is guided by six principles:
Implementing automated IR playbooks can lead to substantial cost savings, averaging $2.22 million per breach. This highlights not only the operational but also the financial benefits of a well-structured IR plan. In a world where every second counts, can your organization afford to be without one?
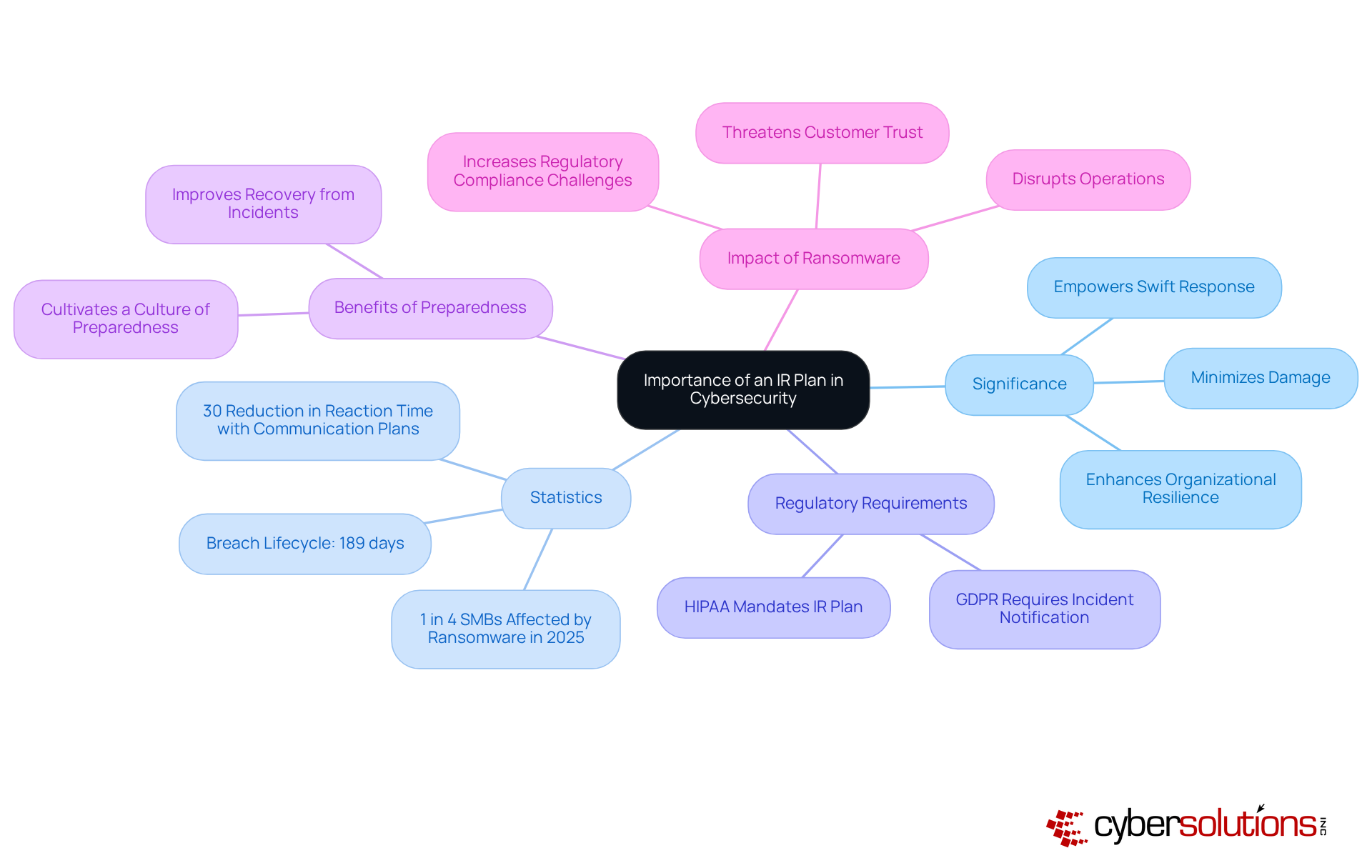
In today’s landscape of sophisticated cyber threats, the significance of an IR plan in cybersecurity cannot be overstated. A well-defined IR plan empowers organizations to respond swiftly to incidents, minimizing potential damage and operational disruptions. Did you know that organizations with a formal IRP experience a breach lifecycle averaging just 189 days? This is significantly shorter than those without such plans. Furthermore, regulatory frameworks like HIPAA and GDPR mandate the existence of an IR plan, making it not just a best practice but a necessity across various industries.
A successful IRP cultivates a culture of preparedness, ensuring that every employee knows their role during a cybersecurity incident. For instance, businesses with established communication plans can reduce their reaction time by 30%. This statistic underscores the tangible benefits of maintaining an organized approach. Organizations that have adopted an IR plan report enhanced resilience, showcasing notable improvements in their ability to recover from incidents and uphold operational integrity.
The rise in ransomware attacks, affecting nearly 1 in 4 small and mid-sized companies in 2025, highlights the urgent need for robust response strategies. By investing in an IR plan, organizations not only protect their assets and reputation but also equip themselves to navigate the complexities of regulatory compliance effectively. As George Chapman, a Senior Security Consultant, aptly puts it, "A tested plan and a trusted partner can make all the difference between quick recovery and lasting damage." In summary, having a comprehensive IR plan is crucial for defending against cyber threats and ensuring long-term organizational resilience.
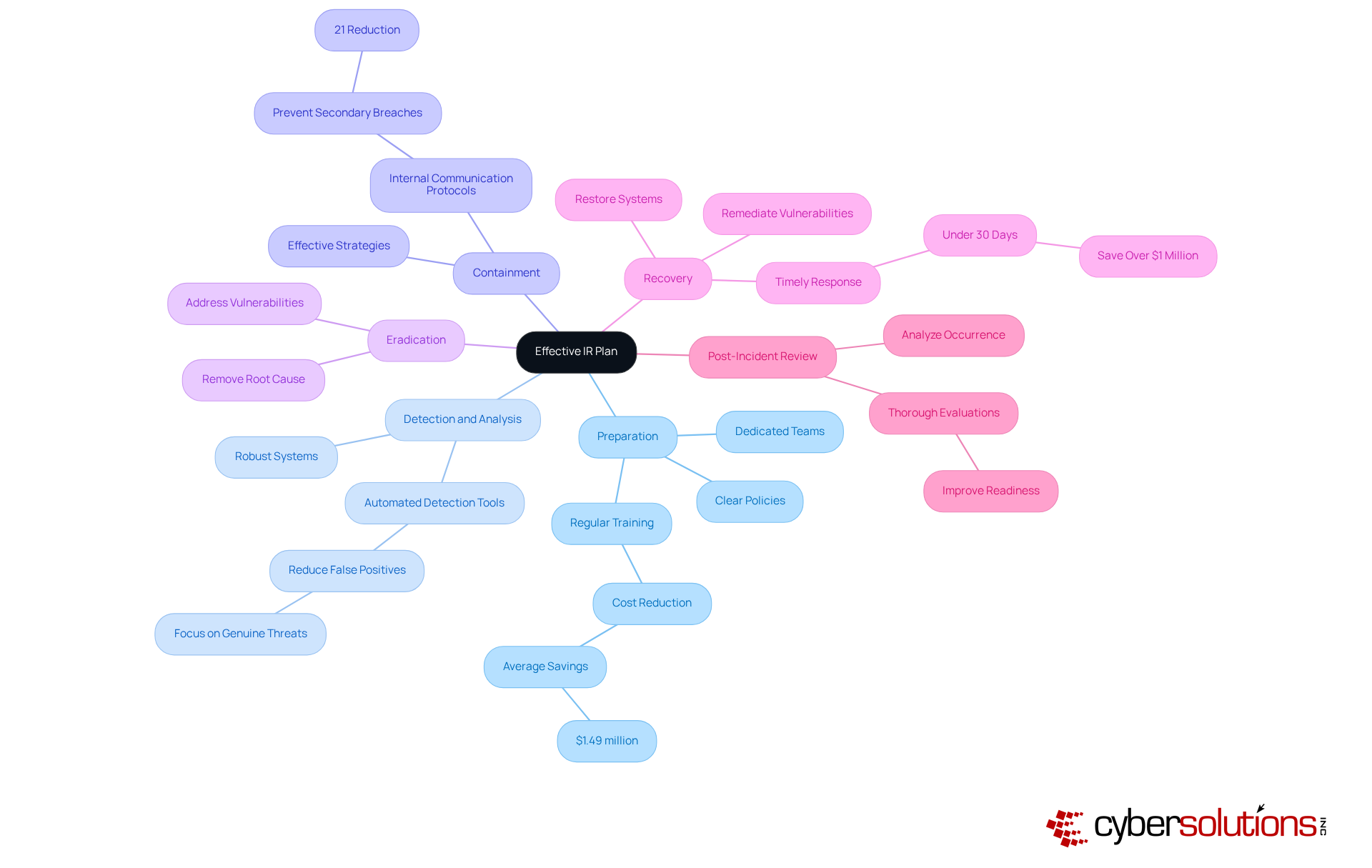
An effective ir plan is crucial for organizations aiming to navigate cybersecurity events with efficiency and confidence. In today’s landscape, where threats are ever-evolving, having a robust IR plan can mean the difference between a minor incident and a catastrophic breach. Here are the key components that work together to ensure a comprehensive response:
Preparation: Establishing clear policies and assembling dedicated teams equipped with the right tools is essential for effective management of cybersecurity situations. Organizations that engage in regular training and simulations can reduce breach costs by an average of $1.49 million. Are you prepared to face the challenges ahead?
Detection and Analysis: Implementing robust systems for the prompt identification and evaluation of incidents is vital. Companies that utilize automated detection tools can significantly reduce false positives, allowing their teams to concentrate on genuine threats. How quickly can your organization identify a potential breach?
Containment: Effective strategies must be in place to limit the spread of an event and prevent further damage. Organizations with clear internal communication protocols can prevent 21% more secondary breaches caused by mismanaged responses. Is your communication strategy up to par?
Eradication: This step involves removing the root cause of the incident from the environment, ensuring that vulnerabilities are addressed. Without this, the same issues may resurface, leading to further complications.
Recovery: Restoring systems and operations to normal is vital. During this phase, organizations should ensure that all vulnerabilities are remediated. Those that address breaches in under 30 days save more than $1 million compared to those with extended resolution times. Can your organization afford to wait?
Post-Incident Review: Analyzing the occurrence afterward is critical for learning and enhancing future responses. High-performing security teams conduct thorough post-mortem evaluations after each event, improving their readiness for future threats. What lessons can your team learn from past incidents?
Each of these components plays a crucial role in mitigating the impact of cybersecurity events and enhancing the overall security posture of an organization. By prioritizing an effective IR plan, organizations can not only protect their assets but also build trust with their stakeholders.
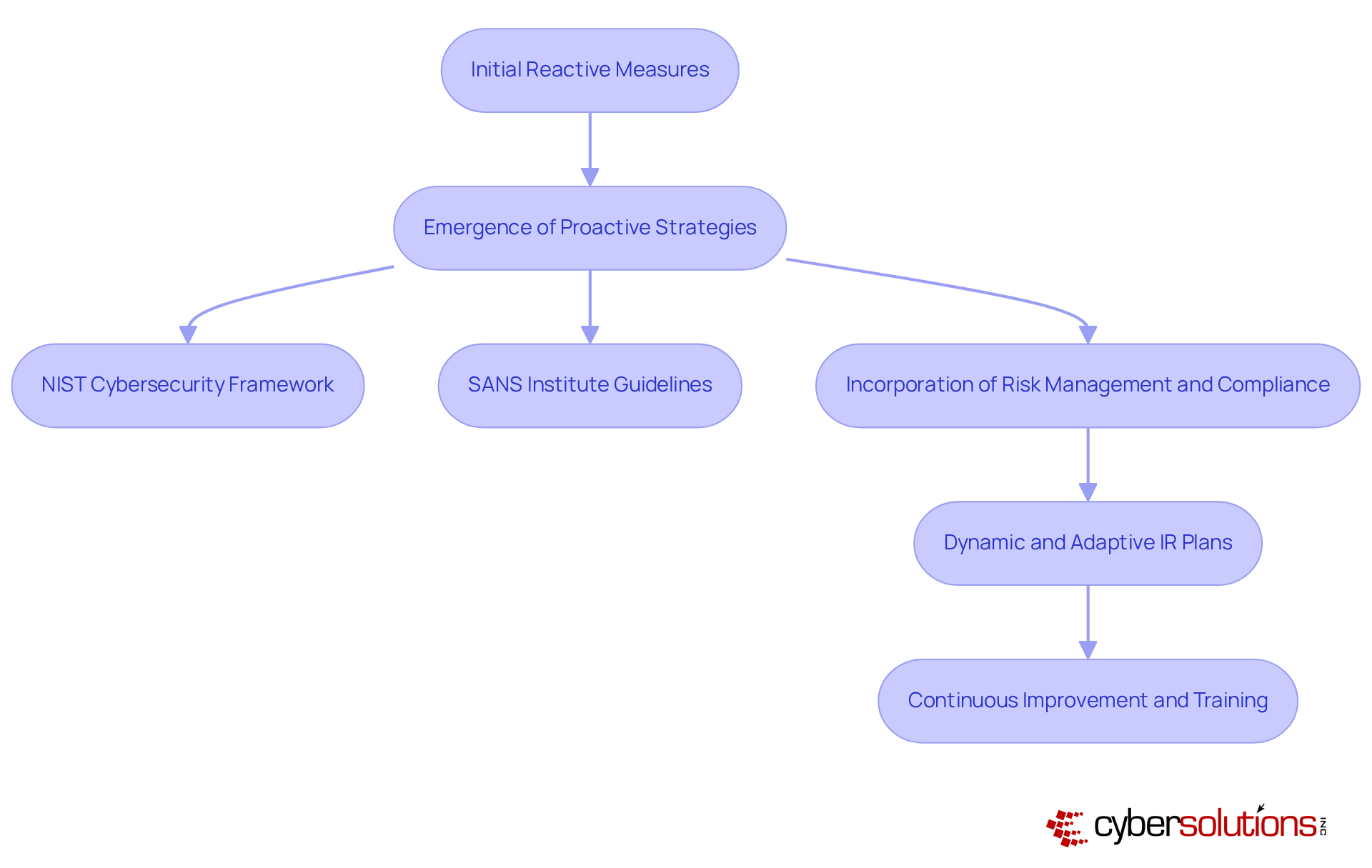
The evolution of the IR plan is profoundly influenced by the escalating complexity of cyber threats and the increasing recognition of the necessity for structured responses. Initially, emergency measures were predominantly reactive, often triggered only after breaches occurred. However, as cyber threats advanced, organizations began to embrace proactive strategies. Frameworks such as the NIST Cybersecurity Framework and guidelines from the SANS Institute have equipped organizations with systematic approaches to managing incidents.
Over time, the focus has shifted from merely responding to incidents to incorporating risk management, compliance, and continuous improvement into the response process. Today, the IR plan is not static; it is a dynamic document that must adapt alongside emerging threats and technologies. This evolution underscores the critical need for regular updates and training to ensure their effectiveness in an ever-evolving cybersecurity landscape.
In the healthcare sector, where sensitive data is at stake, the implications of these developments are significant. Cyber Solutions can play a pivotal role in addressing these challenges, ensuring that organizations are not only prepared to respond but also to anticipate and mitigate risks effectively.
An Incident Response Plan (IRP) is not just a document; it’s a vital framework that guides organizations through the intricate landscape of cybersecurity threats. In an era where swift detection and response are paramount, a well-structured IRP ensures that business continuity and data integrity remain intact. Alarmingly, many organizations still lack a documented IR plan, making it imperative for businesses to prioritize this critical aspect of their cybersecurity strategy.
The importance of an IR plan cannot be overstated. It minimizes damage from cyber threats and encompasses essential components such as:
Each of these elements is crucial in bolstering an organization’s resilience against attacks while ensuring compliance with regulatory requirements. Moreover, the evolution of IR plans signifies a shift from reactive measures to proactive strategies, highlighting the necessity for continuous improvement in response protocols.
Investing in a robust Incident Response Plan is not merely a precaution; it’s a strategic imperative for organizations that aim to protect their assets and reputation. As cyber threats evolve, so too must the strategies to manage them. Organizations must take proactive steps by developing, updating, and regularly testing their IR plans. The question remains: can your organization afford to be without a comprehensive IR plan? The time to act is now.
What is an Incident Response Plan (IRP)?
An IRP is a vital strategy that outlines the procedures and protocols a company must follow in response to cybersecurity events, helping teams detect, respond to, and recover from security breaches or attacks.
Why is having an IRP essential for companies?
An IRP is essential because it ensures a coordinated and effective response to incidents, significantly reducing potential impacts on business continuity and data integrity.
What are some key components of an IRP?
Key components of an IRP typically include predefined roles and responsibilities, communication strategies, and specific actions aimed at mitigating damage and restoring normal operations.
How does the presence of an IRP affect the breach lifecycle?
Organizations with an IRP experience an average breach lifecycle of 258 days, compared to just 189 days for those without one, highlighting the importance of having a documented plan.
What percentage of entities currently lack a documented IRP?
Alarmingly, 45% of entities currently lack a documented IRP, indicating a significant gap in cybersecurity preparedness.
What are the six principles of effective incident response according to NIST?
The six principles are Govern, Identify, Protect, Detect, Respond, and Recover.
What financial benefits can automated IR playbooks provide?
Implementing automated IR playbooks can lead to substantial cost savings, averaging $2.22 million per breach, emphasizing the operational and financial advantages of a well-structured IR plan.
Can organizations afford to be without an IRP?
In a world where every second counts, organizations cannot afford to be without an IRP, as it is crucial for effective incident management and minimizing damage.