In today's digital landscape, where security is non-negotiable, grasping the various types of digital certificates is essential for C-suite leaders committed to protecting their organizations. These certificates form the backbone of secure online communications, ensuring compliance, safeguarding sensitive data, and fostering trust with clients and partners. Yet, as cyber threats evolve and regulatory demands intensify, how can executives adeptly manage the complexities of digital certificate oversight? This article delves into ten vital digital certificate types that every leader must understand, emphasizing their importance and the strategic benefits they provide in navigating the challenges of modern cybersecurity.
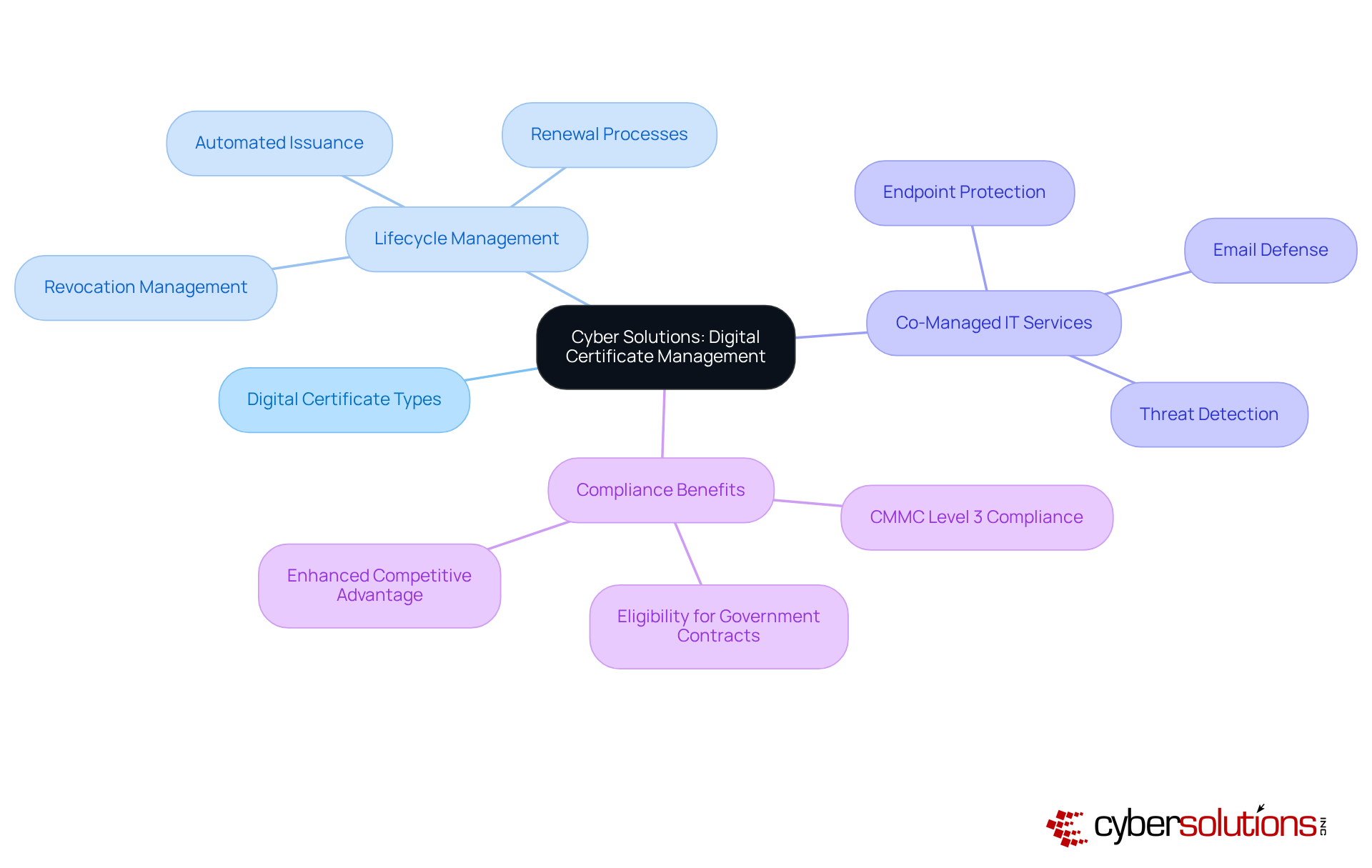
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially for enterprises navigating complex compliance requirements. Cyber Solutions Inc. stands at the forefront, offering a comprehensive range of digital certificate types and management services designed to enhance protection and ensure compliance. Their automated lifecycle management of digital certificate types allows organizations to efficiently issue, renew, and revoke certificates, significantly reducing the risk of certificate-related outages. This proactive strategy not only fortifies overall cybersecurity posture but also enables clients to concentrate on their core operations, free from the burdens of IT complexities.
Moreover, as part of their Co-Managed IT Services, Cyber Solutions provides advanced cybersecurity measures, including:
These services are crucial for businesses striving to stay ahead of evolving cyber threats. By achieving compliance with CMMC Level 3 standards, organizations not only protect sensitive federal data but also secure eligibility for lucrative government contracts. This commitment to cybersecurity not only enhances their competitive advantage but also reinforces their reputation in the industry.
Clients have reported significant improvements in their security posture and compliance readiness, underscoring the effectiveness of Cyber Solutions' offerings. Are you ready to elevate your organization's cybersecurity strategy? With Cyber Solutions, you can safeguard your operations and thrive in an increasingly complex digital environment.
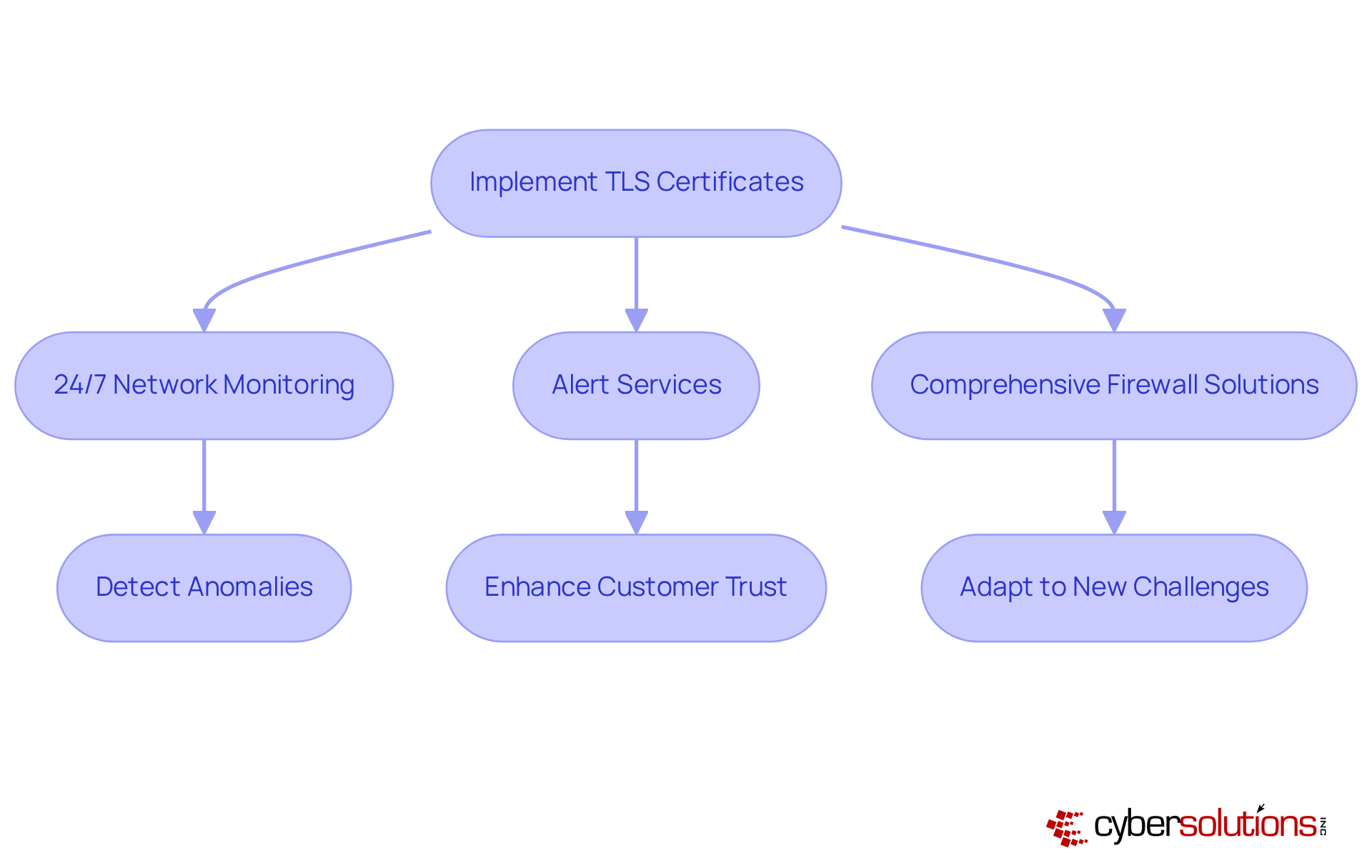
Transport Layer Security (TLS) credentials are not just important; they are essential for establishing secure connections over the internet. By encrypting data exchanged between clients and servers, TLS ensures that sensitive information remains confidential and protected from eavesdropping. However, implementing TLS certificates is only the beginning. C-suite leaders must prioritize 24/7 network monitoring and alert services to detect anomalies and potential vulnerabilities in real-time.
This proactive approach not only safeguards organizations against cyber threats but also enhances customer trust by ensuring that all data transactions are secure and monitored. Comprehensive firewall and network security solutions, including cutting-edge threat intelligence and tailored access controls, further bolster this protection, adapting to new challenges as businesses grow.
Consider the potential repercussions of TLS mismanagement: operational disruptions and reputational harm. These risks underscore the necessity of maintaining valid credentials and automating management processes to adhere to evolving regulatory standards. In a landscape where cybersecurity threats are ever-present, the time to act is now.
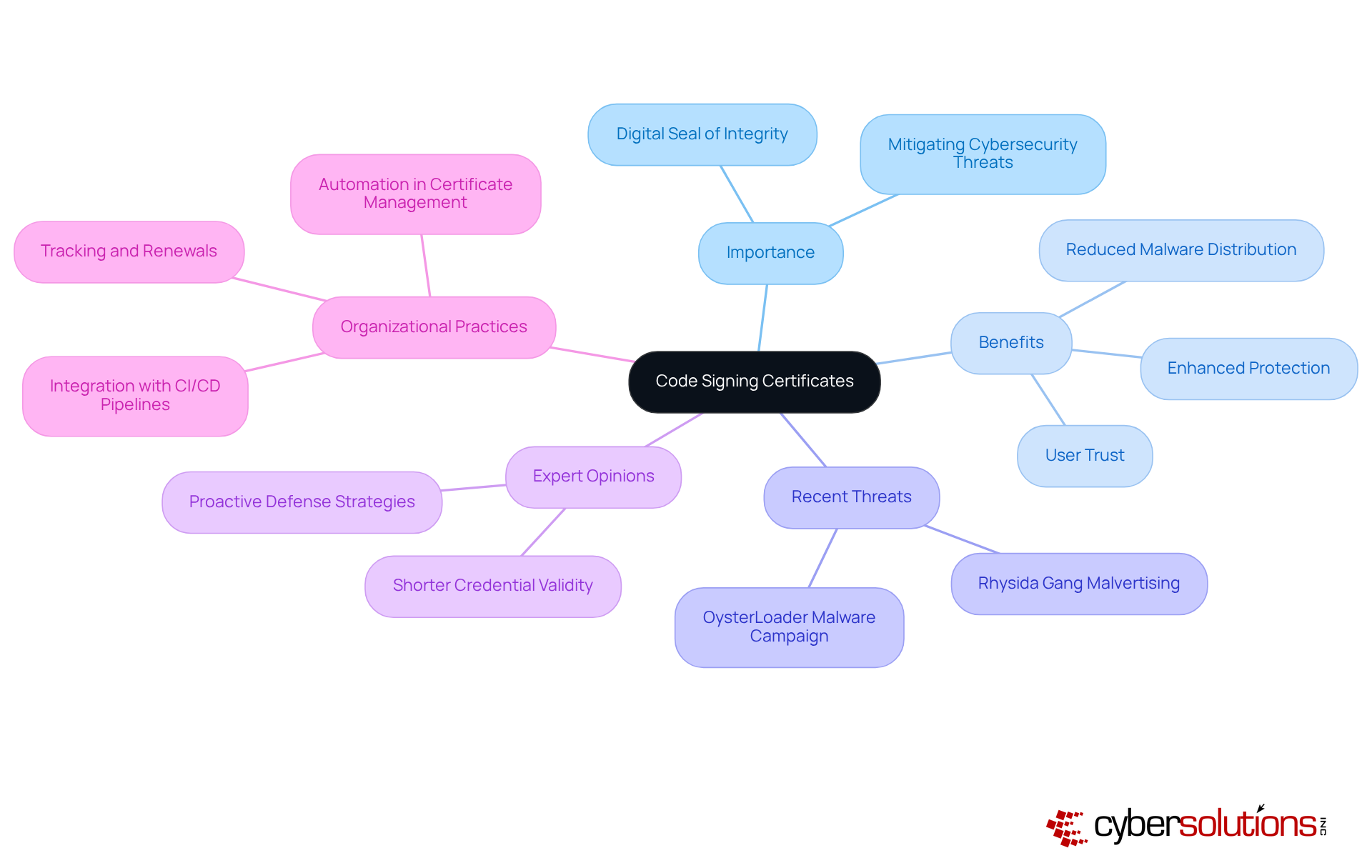
Code signing certificates are crucial for software developers, serving as a digital seal of integrity for applications. In an era where cybersecurity threats loom large, implementing code signing practices significantly bolsters software protection, mitigates the risk of malware distribution, and fosters trust among users. Recent incidents, such as the malvertising tactics employed by the Rhysida gang, underscore the urgent need for robust code signing measures. This gang has adeptly targeted users by masquerading as legitimate software downloads, illustrating the dire consequences of unprotected software that can lead to widespread malware infections.
The integration of code signing not only enhances protection but also plays a pivotal role in reducing malware distribution rates. Organizations that have adopted code signing within their development processes report a notable decline in malware infiltration incidents. This trend is particularly relevant as the industry shifts towards shorter credential lifecycles, which encourage more frequent updates and bolster safety practices.
Experts stress the significance of code signing in preserving software integrity. As one industry leader noted, "Shorter credential validity may seem like additional effort, but it encourages everyone toward improved practices, enhanced key protection, faster updates, and stricter control over the signing process." This proactive stance is vital in today’s threat landscape, where cyberattacks are increasingly prevalent.
Organizations employing code signing tools have successfully thwarted malware distribution attempts, showcasing the effectiveness of this protective measure. By ensuring their software is signed and verified, these entities not only protect their clients but also strengthen their overall security posture, making code signing an indispensable practice in modern software development.
Client credentials are essential for verifying devices and users accessing protected systems, providing a robust layer of security. In an era where cyber threats are increasingly sophisticated, requiring client credentials ensures that only authorized devices connect to networks, significantly mitigating the risk of unauthorized access and potential data breaches. This is particularly critical in compliance-heavy sectors like healthcare and finance, where stringent regulatory requirements demand top-notch security measures.
Consider this: organizations that have adopted client certificates report a notable decline in unauthorized access incidents. By utilizing certificate-based authentication (CBA), these entities effectively eliminate common vulnerabilities linked to traditional password systems, such as phishing and credential theft. Cybersecurity experts emphasize that CBA not only enhances protection but also streamlines user access, creating a seamless experience for employees while fortifying defenses against cyber threats.
As industry specialists point out, the transition to client credentials represents a proactive approach to safeguarding sensitive information. Integrating client credentials into security protocols not only meets compliance mandates but also bolsters the overall security posture of organizations. In a landscape where cyber threats are evolving, leveraging client credentials is a strategic move that C-suite executives must prioritize to protect their organizations from emerging digital risks.
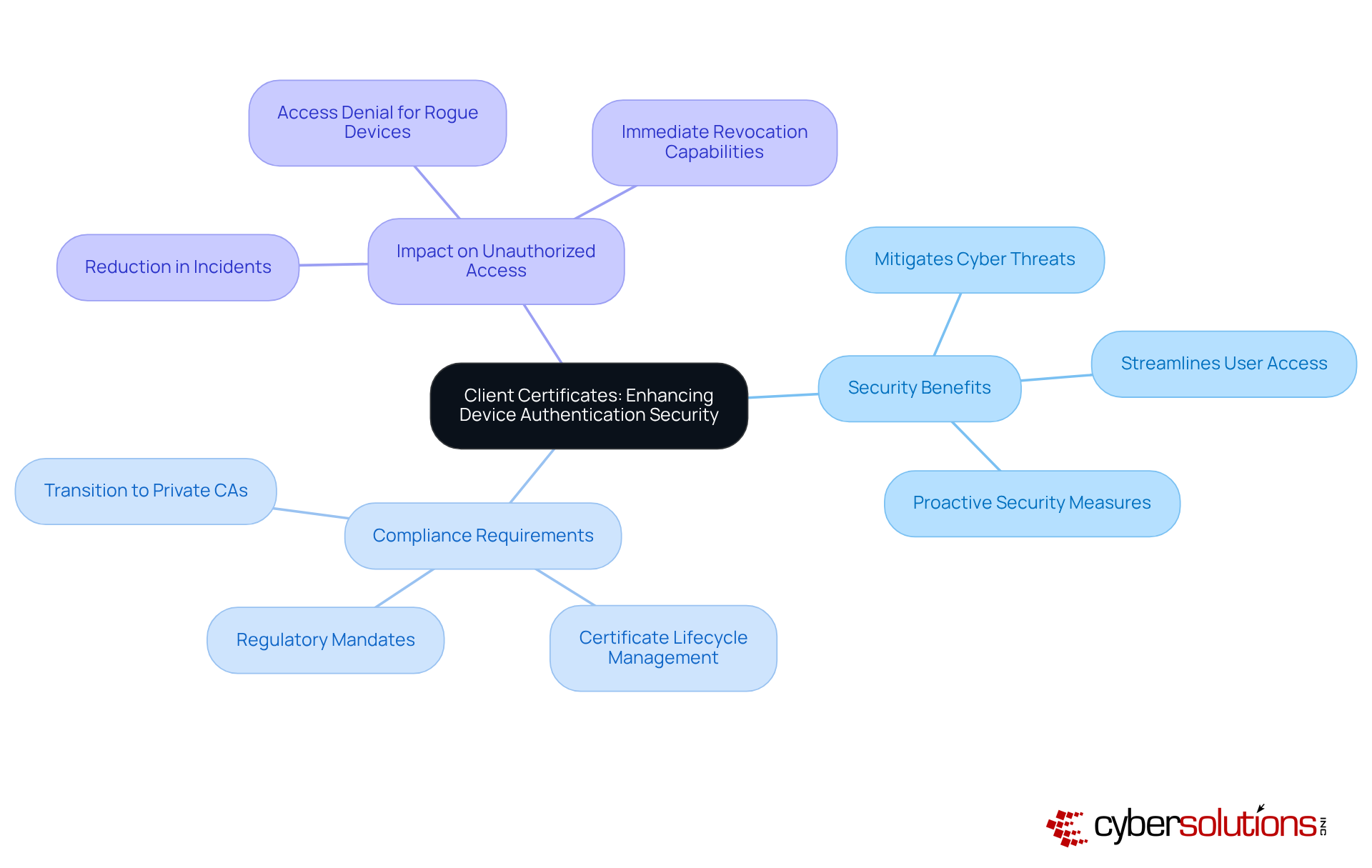
Email credentials, often referred to as S/MIME credentials, play a crucial role in encrypting and digitally signing email communications. These credentials ensure that sensitive information shared via email remains confidential and that the sender's identity is consistently verified. For organizations handling sensitive data, deploying S/MIME credentials is essential, providing robust protection against phishing attempts and unauthorized access.
Recent trends reveal a troubling increase in phishing attacks, particularly targeting corporate email accounts due to their potential to expose sensitive information. A notable example involved a data-theft operation that exploited OAuth tokens, allowing attackers to access sensitive data from various organizations. This incident underscores the urgent need for enhanced email protection measures. S/MIME credentials provide a scalable solution by utilizing digital certificate types to encrypt messages and apply digital signatures, effectively safeguarding against phishing while ensuring the integrity of the content during transmission.
Experts emphasize the necessity of implementing layered protective measures, including S/MIME credentials, to secure sensitive communications. As noted by Actalis, "Using S/MIME credentials not only safeguards against phishing and spoofing - it also assists organizations in fulfilling data protection obligations, such as those outlined in the EU’s GDPR." Furthermore, recent updates to S/MIME standards, which mandate stronger encryption algorithms, significantly bolster the security framework, making it increasingly challenging for unauthorized parties to access sensitive information.
Organizations that have successfully integrated S/MIME credentials report a marked decrease in phishing incidents, demonstrating their effectiveness in protecting sensitive email information. For instance, a case study on the implementation of S/MIME credentials in email systems revealed a substantial reduction in successful phishing attempts. By adopting S/MIME credentials, businesses not only fortify their defenses against cyber threats but also enhance trust with clients and partners, showcasing their commitment to secure communications. Additionally, it is vital for organizations to prepare for the upcoming requirement that S/MIME credentials include the 'Given Name' and 'Surname' attributes in the Subject Name field after July 16, 2025, to ensure compliance with evolving standards.
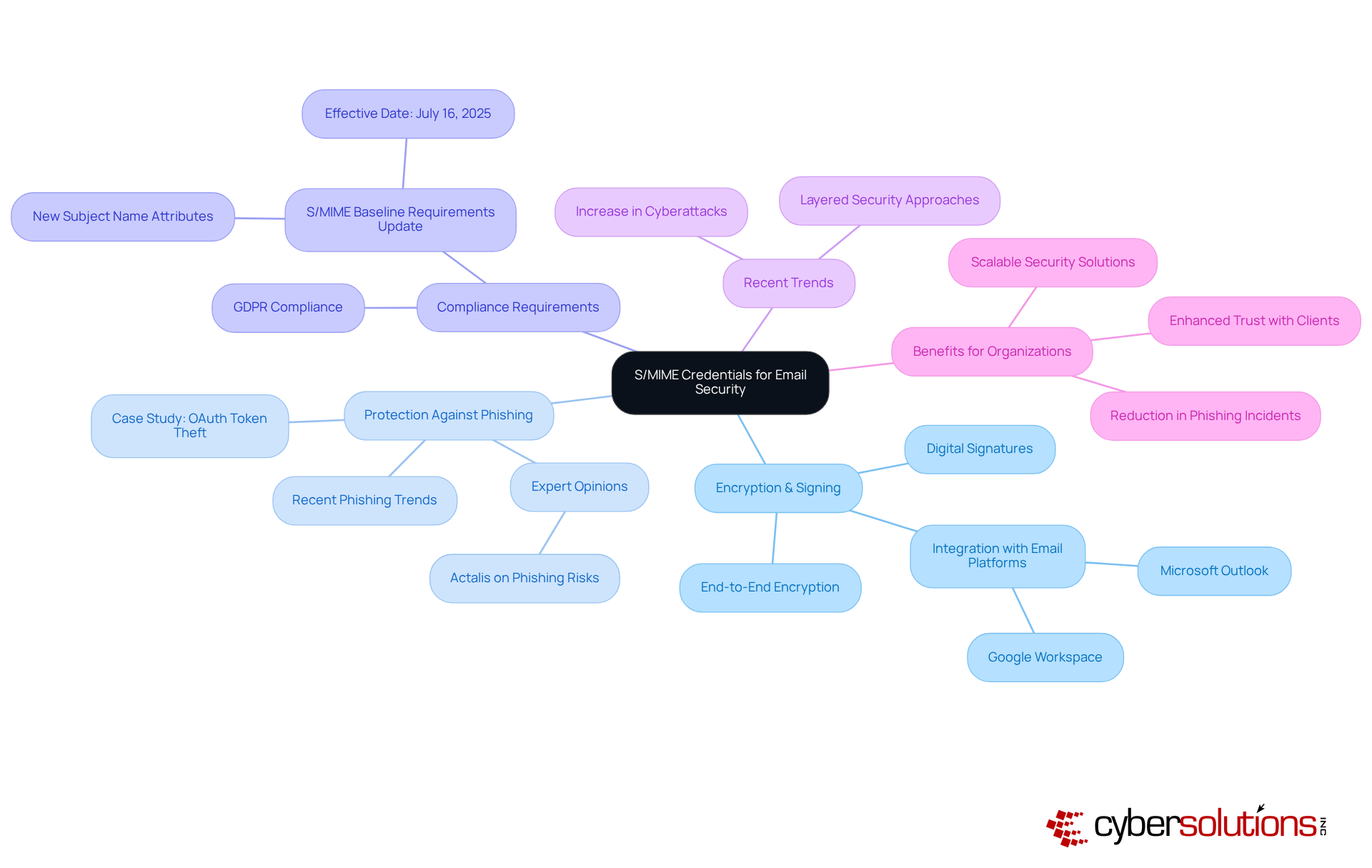
In the realm of cybersecurity, the stakes have never been higher. Digital certificate types, such as Authority (CA) documents provided by reliable entities, play a pivotal role in verifying identities and fostering trust in digital communications. These documents assure individuals that the organizations they interact with are legitimate, significantly enhancing the trustworthiness of online transactions. For example, digital certificate types, such as SSL certificates, not only help organizations comply with standards like HIPAA, PCI-DSS, and GDPR but also boost search engine visibility and maintain user trust in online interactions.
As we navigate today’s cybersecurity landscape, the importance of robust digital protection measures cannot be overstated. Application allowlisting stands out as a proactive strategy that prevents unauthorized software from executing, effectively reducing the attack surface and minimizing risks associated with malware and ransomware. This approach is essential for compliance assurance and bolsters the overall safety posture of organizations.
Industry leaders emphasize the critical role of digital certificate types and CA credentials in building trust. Leo Grove, CEO of SSL.com, notes that reliable protection of digital certificate types is vital for entities engaged in digital transactions. As the digital landscape evolves, the significance of CAs grows, especially with the emergence of technologies like AI and IoT, which present new security challenges. By prioritizing partnerships with established CAs and implementing comprehensive cybersecurity strategies, C-suite leaders can enhance their organization’s credibility and ensure secure communications, ultimately fostering greater trust among clients and stakeholders.
Moreover, with upcoming changes in TLS authentication durations-reducing from 398 days to 200 days in 2026-organizations must remain vigilant in maintaining compliance and security. Are you prepared to adapt to these changes and safeguard your digital transactions?
Object-signing credentials are essential in the realm of digital security, particularly for those distributing software and digital content. They ensure that files remain unaltered since their signing, safeguarding the integrity and authenticity of products. In an age where cyber threats are rampant, utilizing these credentials not only protects intellectual property but also fosters greater user trust.
Many organizations across diverse sectors have recognized the importance of object-signing credentials in enhancing software integrity. Tech firms, for instance, frequently employ these credentials to verify that their applications remain unchanged during distribution. This practice not only secures the software but also reassures users that they are downloading legitimate products, a crucial factor in today’s digital landscape.
Experts emphasize the necessity of confirming the authenticity of digital objects through these credentials. They argue that object-signing credentials provide a robust method for ensuring that software and files are genuine, significantly reducing the risk of malware and unauthorized alterations. This verification process is vital for maintaining a secure digital environment, especially as cyber threats continue to evolve.
The impact of object-signing credentials on digital content integrity is profound. They act as a digital fingerprint, enabling users to verify the source and integrity of the content they engage with. This verification is particularly critical in industries like finance and healthcare, where the authenticity of digital documents is paramount.
Recent incidents of digital content manipulation underscore the urgent need for object-signing credentials. For example, breaches involving compromised software repositories have exposed vulnerabilities in traditional signing methods. By adopting object-signing credentials, organizations can mitigate these risks, ensuring that any tampering is quickly detected and that the integrity of their digital assets is preserved.
In conclusion, object-signing credentials are indispensable for organizations committed to maintaining the integrity and authenticity of their digital content. Their implementation not only protects intellectual property but also enhances confidence in the security of software and files.

In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in sectors like healthcare where sensitive data is at stake. Extended Validation (EV) credentials are one of the digital certificate types that represent the pinnacle of SSL validation, necessitating a thorough verification process to confirm an entity's identity. Unlike standard credentials, EV credentials prominently display the entity's name in the address bar of high-security web browsers, serving as a powerful trust signal to users. This visual cue not only enhances the perceived legitimacy of a website but also significantly boosts customer confidence, making it an essential asset for organizations striving to establish a robust online presence.
The rigorous vetting process for EV approvals ensures that only legitimate enterprises can obtain them, effectively mitigating the risk of cybercriminals exploiting the system. As a result, websites featuring EV credentials are statistically less likely to be associated with phishing attacks. One Certification Authority even reported no phishing incidents for sites utilizing EV SSL. This level of assurance is particularly crucial for industries like finance and healthcare, where trust is paramount due to the sensitive nature of the data involved. Furthermore, EV SSL validations help businesses comply with significant standards such as PCI-DSS and HIPAA/HITECH, further bolstering their credibility.
Cybersecurity specialists underscore the importance of EV credentials in fostering a secure online environment. For instance, one expert noted that EV SSL equips site visitors with essential information to distinguish between legitimate sites and potential frauds, thereby undermining the effectiveness of social engineering attacks. Moreover, visible EV credentials can enhance site transactions and usage, as customers are more inclined to engage with a site they perceive as secure.
Real-world examples illustrate the effectiveness of EV credentials in enhancing online reputation. Organizations that have adopted EV SSL have reported improved customer trust and higher conversion rates, as the visible security indicators communicate a commitment to protecting user data. In a competitive digital environment, investing in EV credentials is not just about compliance; it’s a strategic initiative to enhance brand perception and foster customer loyalty. Notably, the cost difference between EV and OV documents among different digital certificate types remains minimal, making EV accessible for many companies.
In summary, adopting EV credentials is a proactive measure for C-suite leaders looking to bolster their entity's online trust and reputation. By ensuring that their websites are equipped with these robust protective measures, businesses can significantly enhance customer confidence and safeguard their digital assets.

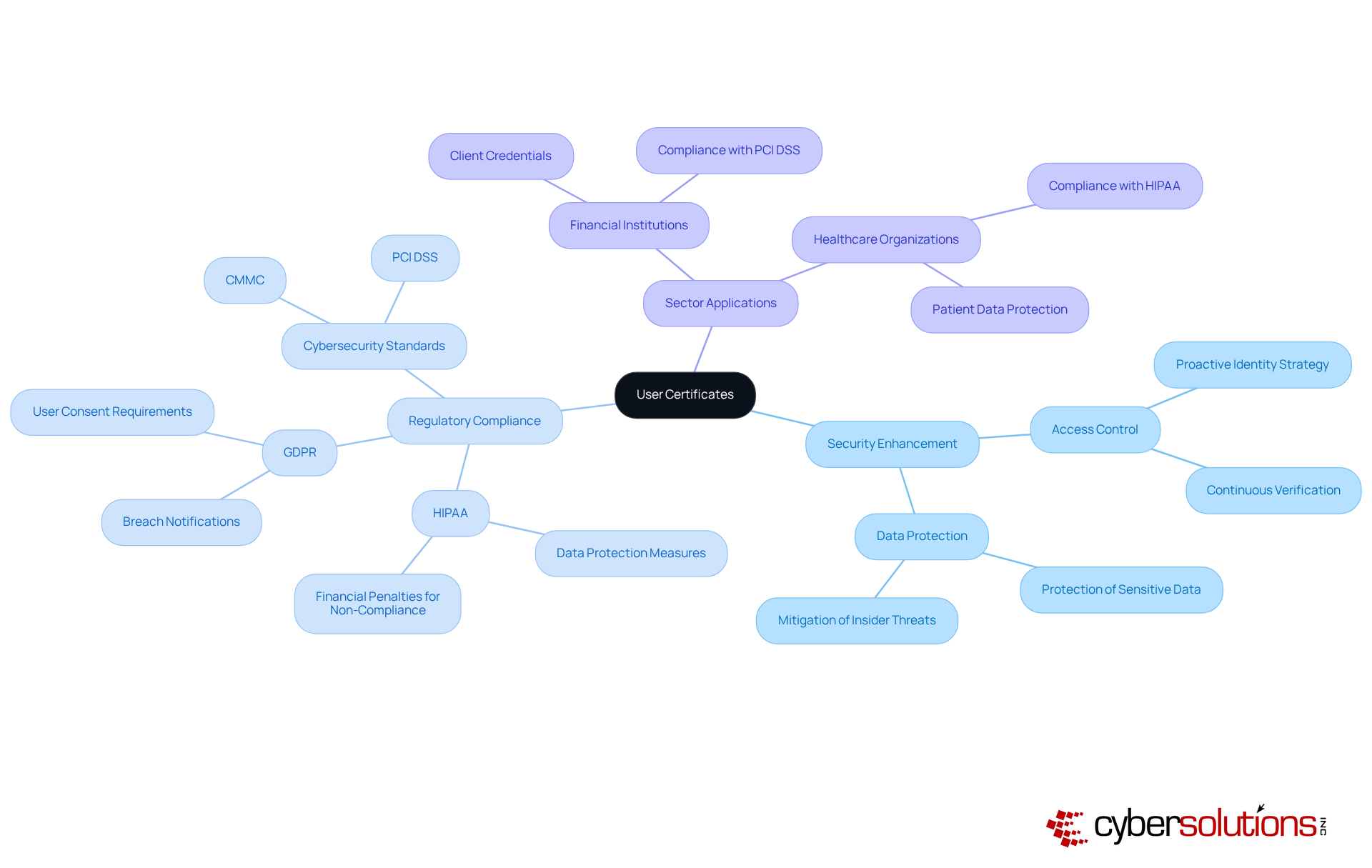
Digital credentials are essential assets that verify distinct individuals within a company, significantly enhancing protection and regulatory adherence. In today’s landscape, where cybersecurity threats loom large, organizations must ensure that only authorized personnel gain access to sensitive information and critical systems. This not only strengthens security measures but also aligns with regulatory requirements for data protection, such as those outlined in HIPAA and GDPR, as well as stringent cybersecurity standards necessary for safeguarding Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
Expert opinions underscore the importance of participant credentials in modern access control strategies. Industry leaders assert that a proactive identity strategy is vital for continuously verifying all users - both human and machine - without friction. This approach is increasingly recognized as a best practice in the ever-evolving landscape of cybersecurity.
Organizations across various sectors have successfully adopted access credentials to bolster their access control systems. For example, financial institutions have embraced client credentials to meet strict compliance standards, ensuring that only authenticated individuals can access sensitive financial information. Similarly, healthcare organizations utilize client credentials to protect patient data, thereby complying with HIPAA regulations and avoiding hefty penalties for non-compliance. Furthermore, maintaining eligibility for lucrative government contracts necessitates adherence to essential cybersecurity standards, making participant credentials a crucial component of federal data protection strategies.
The impact of client certificates on regulatory compliance is significant. By establishing a robust framework for authentication, entities can substantially reduce the risk of unauthorized access and data breaches. This not only enhances their security posture but also fosters trust with clients and stakeholders, showcasing a commitment to protecting sensitive information. As regulatory environments continue to evolve, integrating user credentials into access control strategies will be imperative for organizations aiming to maintain compliance and safeguard their assets.
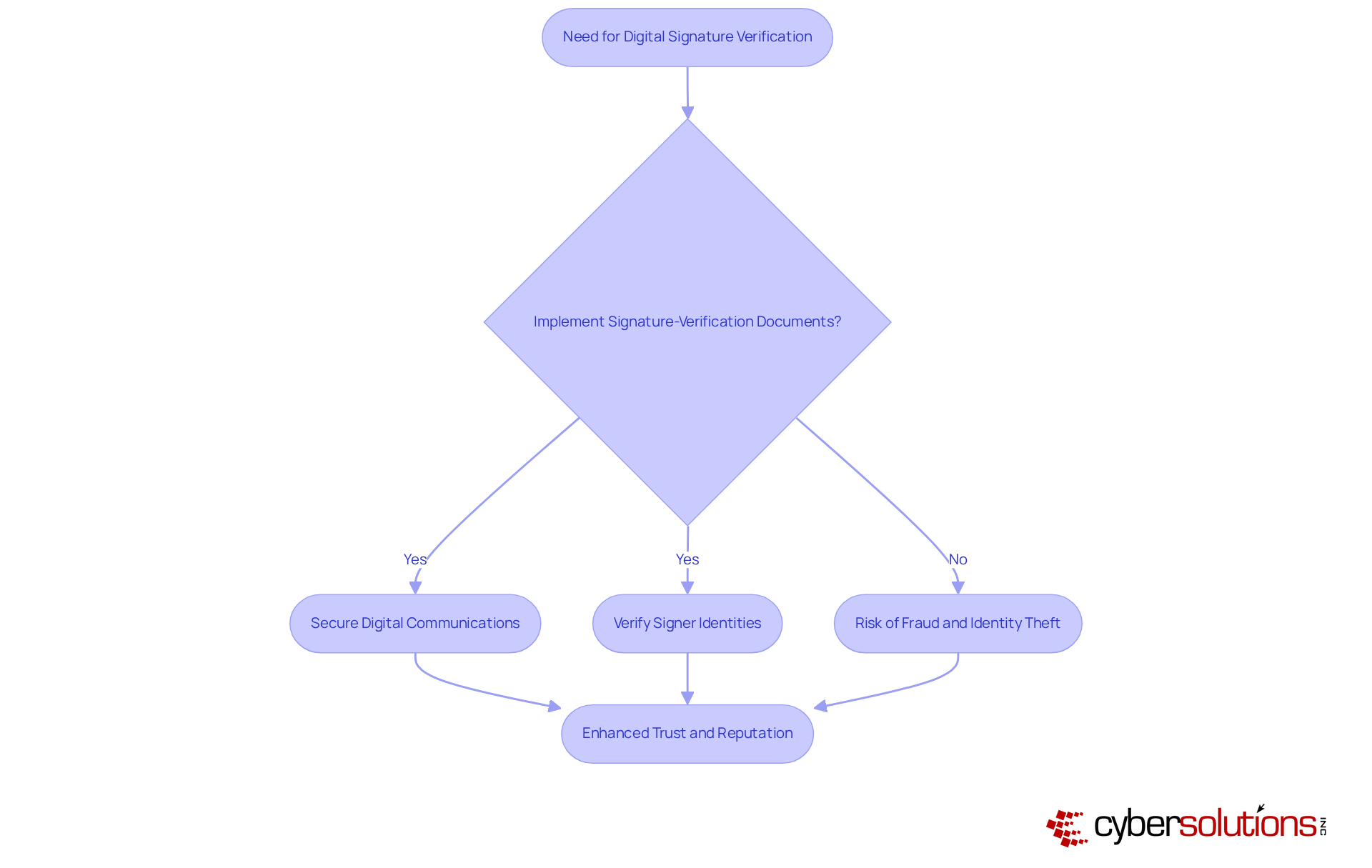
In today's digital landscape, the authenticity of digital signatures is paramount. Signature-verification documents play a crucial role in confirming the legitimacy of these signatures attached to files and transactions. By implementing these digital certificate types, organizations can secure their digital communications and verify the identities of the signers. This verification is essential for maintaining trust in digital transactions and protecting against fraud.
Consider the implications: as cyber threats continue to evolve, the need for robust security measures becomes increasingly critical. Organizations that neglect to implement signature-verification risk exposing themselves to potential fraud and identity theft. The stakes are high, and the consequences of inaction can be severe.
So, how can organizations effectively address these challenges? By adopting signature-verification documents, they can bolster their cybersecurity framework, ensuring that every transaction is both secure and trustworthy. This proactive approach not only safeguards sensitive information but also fosters confidence among stakeholders, ultimately enhancing the organization's reputation in the digital realm.
Understanding the various types of digital certificates is crucial for C-suite leaders who are determined to fortify their organization's cybersecurity framework. These certificates play a pivotal role in ensuring secure communications, protecting sensitive data, and establishing trust in digital transactions. By prioritizing digital certificate management, executives can significantly bolster their organization's resilience against cyber threats and ensure compliance with evolving regulatory standards.
Different types of digital certificates - such as TLS, code signing, and client certificates - each serve unique functions in safeguarding data and verifying identities. The proactive adoption of these certificates not only mitigates risks but also fosters customer confidence, ultimately leading to a competitive edge in the marketplace. Organizations that effectively implement digital certificate strategies report improved security postures and compliance readiness, reinforcing their commitment to protecting sensitive information.
In today's rapidly evolving digital landscape, the importance of robust cybersecurity measures cannot be overstated. C-suite leaders must take decisive action by investing in comprehensive digital certificate management solutions. This investment not only protects their organizations from emerging threats but also enhances their reputation and trustworthiness in the eyes of clients and stakeholders. Embracing these protective measures is not merely a compliance requirement; it is a strategic initiative that can drive business success and resilience in the face of cyber challenges.
What services does Cyber Solutions Inc. offer for digital certificate management?
Cyber Solutions Inc. offers a comprehensive range of digital certificate types and management services, including automated lifecycle management to efficiently issue, renew, and revoke certificates, thereby reducing the risk of certificate-related outages.
How do the services provided by Cyber Solutions enhance cybersecurity?
The services enhance cybersecurity by fortifying the overall security posture of organizations, allowing them to focus on core operations while managing IT complexities. They also include advanced cybersecurity measures such as endpoint protection, email defense, and threat detection.
What is the significance of achieving CMMC Level 3 compliance?
Achieving CMMC Level 3 compliance is crucial for organizations as it protects sensitive federal data and secures eligibility for lucrative government contracts, enhancing both competitive advantage and industry reputation.
Why are Transport Layer Security (TLS) certificates important?
TLS certificates are essential for establishing secure online connections by encrypting data exchanged between clients and servers, ensuring that sensitive information remains confidential and protected from eavesdropping.
What are the consequences of TLS mismanagement?
TLS mismanagement can lead to operational disruptions and reputational harm, highlighting the necessity of maintaining valid credentials and automating management processes to meet evolving regulatory standards.
What role do code signing certificates play in software development?
Code signing certificates serve as a digital seal of integrity for applications, significantly bolstering software protection, mitigating the risk of malware distribution, and fostering trust among users.
How can code signing practices impact malware distribution?
Implementing code signing practices can lead to a notable decline in malware infiltration incidents, as it enhances protection and ensures that software is verified and trusted.
What is the importance of shorter credential lifecycles in code signing?
Shorter credential lifecycles encourage more frequent updates and improved safety practices, which enhance key protection and stricter control over the signing process, vital in today's threat landscape.
How have organizations benefited from employing code signing tools?
Organizations that employ code signing tools have successfully thwarted malware distribution attempts, showcasing the effectiveness of this protective measure in strengthening their overall security posture.