
In today's digital landscape, the importance of a robust cybersecurity strategy cannot be overstated, especially for organizations navigating the complexities of the Cybersecurity Maturity Model Certification (CMMC). Creating a comprehensive System Security Plan (SSP) is essential, as it serves not only as a blueprint for safeguarding sensitive information but also enhances compliance and operational resilience. With evolving threats and increasing regulatory demands, leaders must ask themselves: how can they ensure their SSP remains effective and relevant?
This guide provides a step-by-step approach to developing, maintaining, and updating an SSP, empowering organizations to bolster their cybersecurity posture. By addressing these challenges head-on, organizations can secure their future in an increasingly competitive landscape.
A System Security Plan (SSP) is not just a document; it’s a vital component in safeguarding sensitive information, especially Controlled Unclassified Information (CUI). In today’s landscape, where cybersecurity threats loom large, having a robust SSP acts as a strategic roadmap for implementing essential security controls. This is crucial for compliance with frameworks like the Cybersecurity Maturity Model Certification (CMMC).
Organizations that neglect to establish an effective SSP risk not only vulnerabilities but also potential contract losses and reputational harm. How can leaders ensure they’re not left behind? By recognizing the significance of an SSP, they can allocate resources wisely and prioritize cybersecurity initiatives that align with their organizational goals. Companies that have successfully implemented SSPs have reported enhanced governance and improved cybersecurity resilience, positioning themselves favorably in competitive bidding processes.
As the enforcement of CMMC compliance intensifies, the importance of a well-crafted CMMC SSP cannot be overstated. It is foundational for maintaining eligibility for Department of Defense contracts and ensuring long-term operational success. In a world where cybersecurity is paramount, can your organization afford to overlook the necessity of a comprehensive SSP?
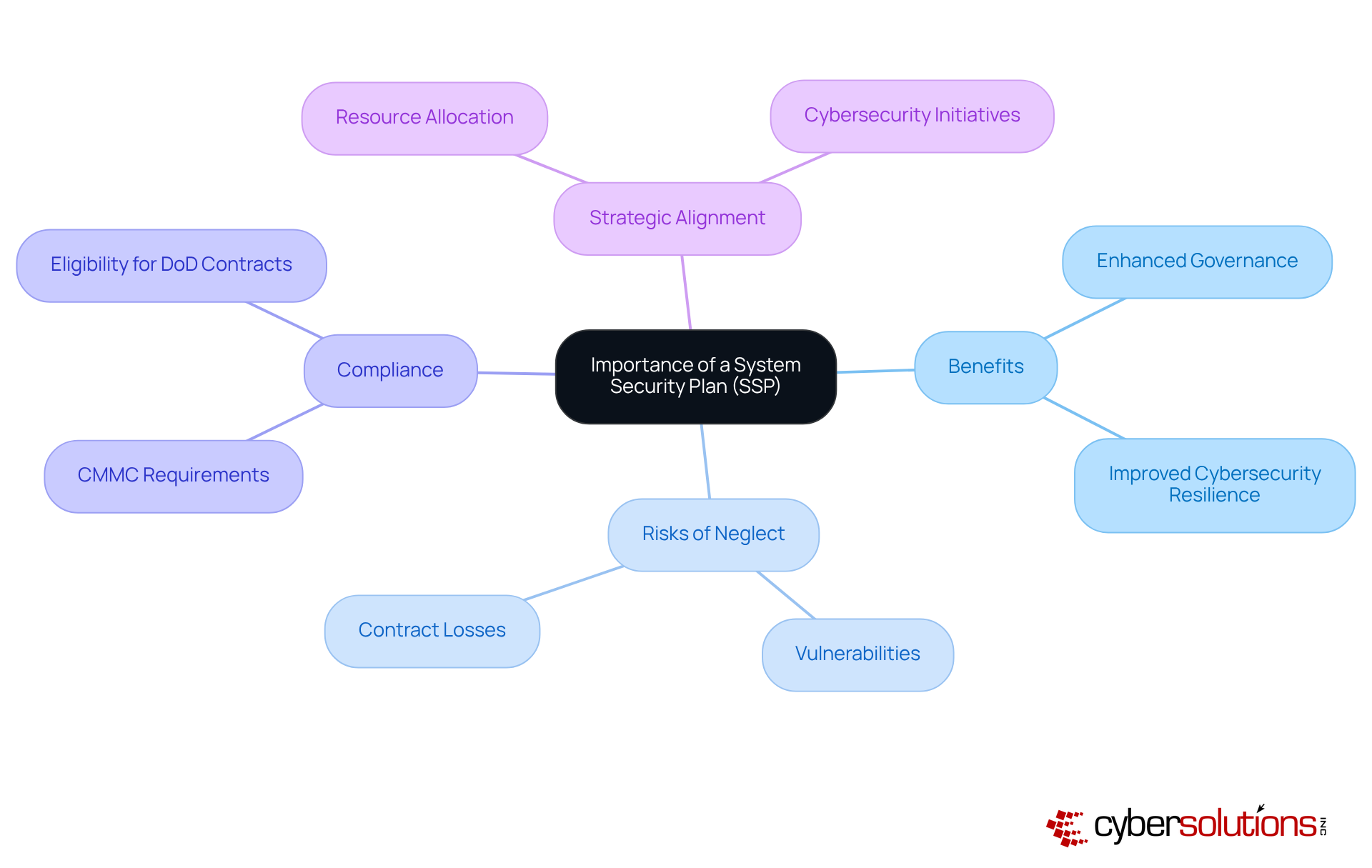
Creating a robust CMMC SSP is not just a regulatory requirement; it’s a critical step in safeguarding your organization against the ever-evolving landscape of cybersecurity threats. In today’s digital age, where data breaches can lead to devastating consequences, understanding the key components of the CMMC SSP is essential for any organization.
System Identification: Begin by clearly defining the system boundaries. Detail all hardware, software, and network components involved. This clarity is crucial for comprehending the extent of protective measures required.
Protection Control Implementation: Document the specific protective measures currently in place to safeguard the system. This should encompass both technical and administrative controls that align with the CMMC SSP and NIST standards, ensuring a comprehensive defense strategy.
Roles and Responsibilities: Assign clear roles for personnel accountable for maintaining and implementing protective measures. This ensures accountability and effective management of security practices, fostering a culture of security within the organization.
Risk Assessment: Conduct a thorough risk assessment to identify potential vulnerabilities and threats. This proactive approach is crucial for mitigating risks before they can be exploited, ultimately protecting your organization’s assets.
Compliance Requirements: Outline the regulatory requirements that your entity must adhere to, including the CMMC SSP and NIST standards. Detail how your organization plans to meet these obligations, reinforcing your commitment to compliance.
Plans of Action and Milestones (POA&Ms): Include a plan for addressing any identified gaps in security controls, along with a timeline for remediation. This illustrates a dedication to ongoing enhancement and adherence to CMMC SSP standards.
Mock Audit Preparation: Conduct a mock audit to ensure your entity is fully prepared for the official CMMC SSP assessment. This proactive measure allows you to address any remaining issues before the actual evaluation.
Continuous Management: Establish a procedure for the continuous oversight of CMMC modifications and assistance in those changes to uphold standards over time.
By concentrating on these elements, your organization can create a thorough CMMC SSP that not only meets regulatory requirements but also enhances its overall protective stance. Leveraging tailored remediation strategies and expert guidance throughout this process can significantly enhance the effectiveness of your CMMC SSP, ensuring that your organization is well-prepared for CMMC audits and compliance assessments.
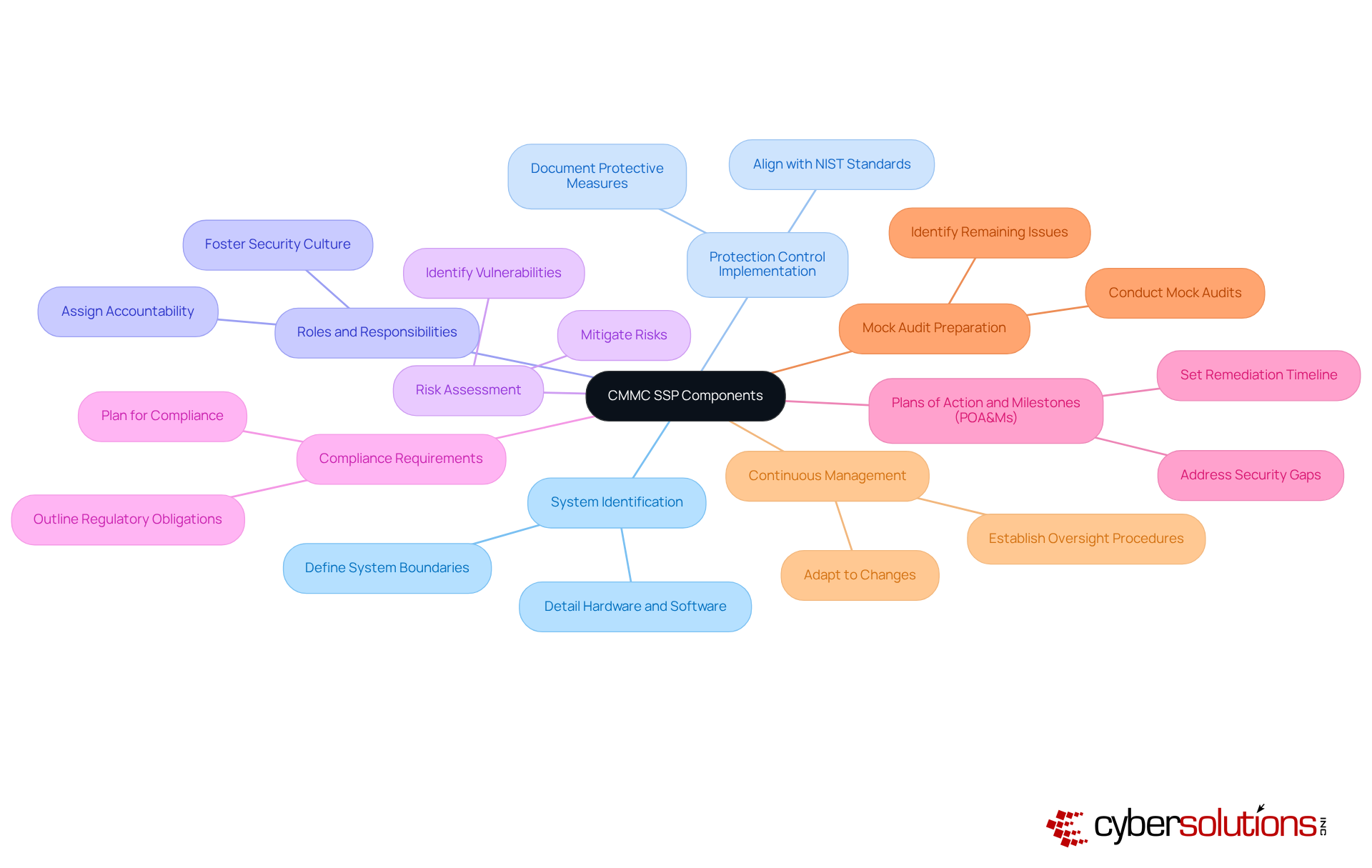
Drafting your SSP involves several key steps that are essential for enhancing your cybersecurity posture:
Conduct a Self-Assessment: Start by evaluating your current protective stance. This assessment is crucial, as 90% of cyber incidents stem from human error, underscoring the need for a thorough review to identify areas for improvement. The typical expense of a data breach reached a record peak of $4.88 million in 2025, highlighting the financial consequences of inadequate protective measures. Cyber Solutions can assist in this phase by pinpointing gaps in your systems and providing a roadmap to achieve CMMC compliance.
Define System Boundaries: Clearly outline the components included in your system, encompassing all hardware and software. This step is vital for creating a comprehensive protective framework, as defining system boundaries helps mitigate risks related to unauthorized access.
Document Protection Measures: List all protective measures currently in place, detailing their implementation. This documentation not only aids in compliance but also serves as a reference for ongoing safety assessments. Contractors must maintain their CMMC level for all information systems used in contract performance, reinforcing the importance of thorough documentation. Cyber Solutions emphasizes the necessity for comprehensive documentation, including safety policies and procedures, to demonstrate adherence during audits.
Assign Responsibilities: Designate personnel responsible for each aspect of the SSP. Ensuring accountability is essential, as entities with clear roles are better positioned to respond effectively to security incidents.
Create a POA&M: Develop a Plan of Action and Milestones (POA&M) to address any gaps identified during the self-assessment. This plan should incorporate specific timelines for execution, enabling organized progress toward compliance. Tailored remediation strategies from Cyber Solutions can guide this process, ensuring your entity effectively addresses compliance gaps.
Conduct a Mock Audit: Perform a mock audit to ensure your entity is fully prepared for the official CMMC assessment. This step helps identify any remaining issues that need to be resolved before the official evaluation.
Review and Revise: Regularly review the SSP to ensure it remains current and effective. Ongoing updates are essential to reflect changes in the entity or regulatory requirements, as the cybersecurity landscape is constantly evolving. Statistics suggest that entities that frequently refresh their protective measures are more capable of addressing new threats. Cyber Solutions also provides ongoing management for CMMC changes, offering assistance as your entity adapts to new regulatory requirements.
By adhering to these steps, entities can significantly enhance their security posture and ensure alignment with the CMMC SSP requirements, ultimately safeguarding sensitive information and preserving operational integrity.
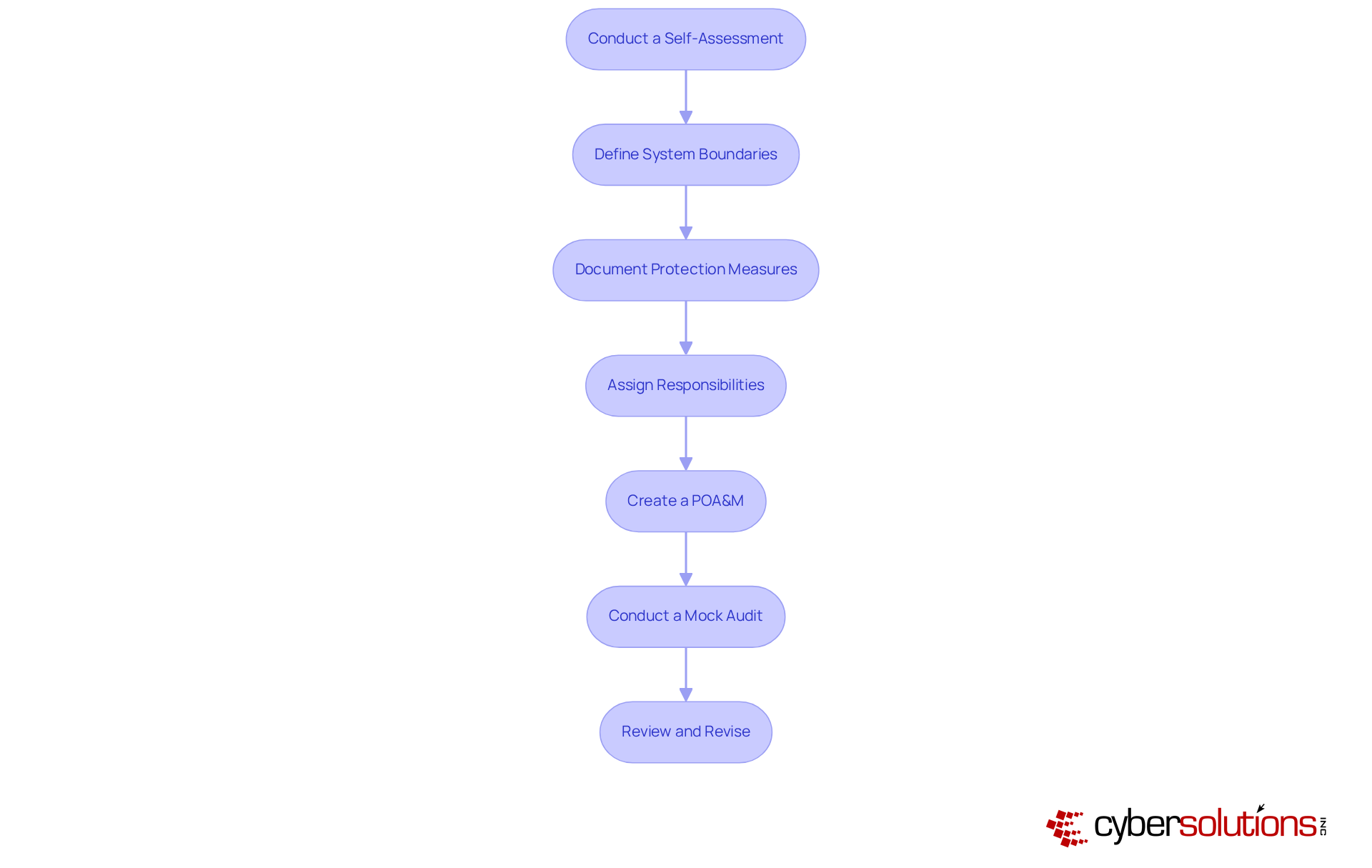
To ensure your CMMC SSP remains effective and compliant, it’s crucial to implement best practices that address the evolving landscape of cybersecurity threats.
Regular Reviews: Schedule periodic reviews of the SSP to evaluate its effectiveness and relevance. Entities that perform regular evaluations are better equipped to adjust to changing threats and regulatory demands. In fact, 89% of entities indicate that regulatory complexity has adversely affected their IT management. Are you among those who could benefit from a more proactive approach?
Update for Changes: Revise the SSP whenever there are significant changes to system architecture, personnel, or regulatory requirements. This proactive method is essential, especially considering that 70% of entities encountered significant disruptions due to data breaches. Agility in compliance practices is not just beneficial; it’s necessary.
Conduct Ongoing Training: Provide regular training for staff on their roles and responsibilities related to the SSP. Ongoing education is vital in reducing the human element in cybersecurity breaches, which constitute 60% of incidents. Are your employees prepared to maintain protective protocols?
Monitor Compliance: Implement continuous monitoring practices to ensure that security controls are functioning as intended and that the organization remains compliant with applicable regulations. Organizations that prioritize continuous adherence efforts can save an average of three to five hours per week on regulatory tasks through automation, enhancing operational efficiency. Isn’t it time to streamline your compliance efforts?
Document Changes: Maintain thorough records of all updates and revisions to the SSP, creating an audit trail that shows continuous adherence efforts. This documentation is essential for sustaining certification, as CMMC mandates yearly confirmations of adherence from a senior official. Are you ready to ensure accountability and readiness for audits?
By adhering to these practices, organizations can significantly enhance the effectiveness of their CMMC SSP and ensure continuous compliance. This ultimately safeguards sensitive information and maintains eligibility for DoD contracts.
Creating a comprehensive System Security Plan (SSP) is not just a task; it’s a vital strategy for organizations aiming to strengthen their cybersecurity defenses and achieve compliance with the Cybersecurity Maturity Model Certification (CMMC). In today’s digital landscape, where threats are ever-present, the importance of an SSP cannot be overstated. This guide not only underscores the necessity of an SSP but also lays out a structured approach to developing and maintaining one that aligns seamlessly with organizational goals and regulatory requirements.
Key components of an effective SSP encompass:
By adhering to a step-by-step process for drafting the SSP, organizations can systematically tackle vulnerabilities, bolster their security posture, and prepare for compliance audits. Regular updates and ongoing training are essential to adapt to the rapidly evolving cybersecurity landscape, ensuring that the SSP remains relevant and effective.
Ultimately, investing time and resources into creating and maintaining a robust SSP transcends mere compliance; it’s about protecting sensitive information and preserving operational integrity in an increasingly complex digital world. Leaders must prioritize these efforts, recognizing that a well-crafted SSP is foundational to their organization’s resilience against cyber threats and a competitive advantage in the marketplace. Are you ready to take the necessary steps to safeguard your organization?
What is a System Security Plan (SSP)?
A System Security Plan (SSP) is a vital document that outlines the security controls and measures necessary to protect sensitive information, particularly Controlled Unclassified Information (CUI).
Why is an SSP important for organizations?
An SSP acts as a strategic roadmap for implementing essential security controls, ensuring compliance with cybersecurity frameworks like the Cybersecurity Maturity Model Certification (CMMC) and safeguarding against vulnerabilities that could lead to contract losses and reputational harm.
What are the consequences of neglecting to establish an effective SSP?
Organizations that fail to establish an effective SSP risk facing vulnerabilities, potential contract losses, and damage to their reputation.
How can leaders ensure they prioritize cybersecurity initiatives?
Leaders can recognize the significance of an SSP to allocate resources wisely and prioritize cybersecurity initiatives that align with their organizational goals.
What benefits have companies reported from implementing SSPs?
Companies that have successfully implemented SSPs have reported enhanced governance and improved cybersecurity resilience, which helps them position themselves favorably in competitive bidding processes.
What role does an SSP play in CMMC compliance?
A well-crafted CMMC SSP is foundational for maintaining eligibility for Department of Defense contracts and ensuring long-term operational success in the context of increasing CMMC compliance requirements.
Can organizations afford to overlook the necessity of a comprehensive SSP?
In a world where cybersecurity is paramount, organizations cannot afford to overlook the necessity of a comprehensive SSP, as it is crucial for protecting sensitive information and ensuring compliance with relevant frameworks.