The escalating complexity of cybersecurity threats necessitates a robust approach to protecting sensitive information, positioning Privileged Access Management (PAM) as a critical element of any organization’s defense strategy. By regulating access to vital systems and enforcing stringent security protocols, PAM not only reduces risks linked to insider threats but also boosts operational efficiency and ensures compliance with regulatory standards.
As organizations navigate this challenging landscape, a pivotal question arises: how can leaders effectively implement PAM to safeguard their assets while cultivating a culture of accountability and transparency within their teams?
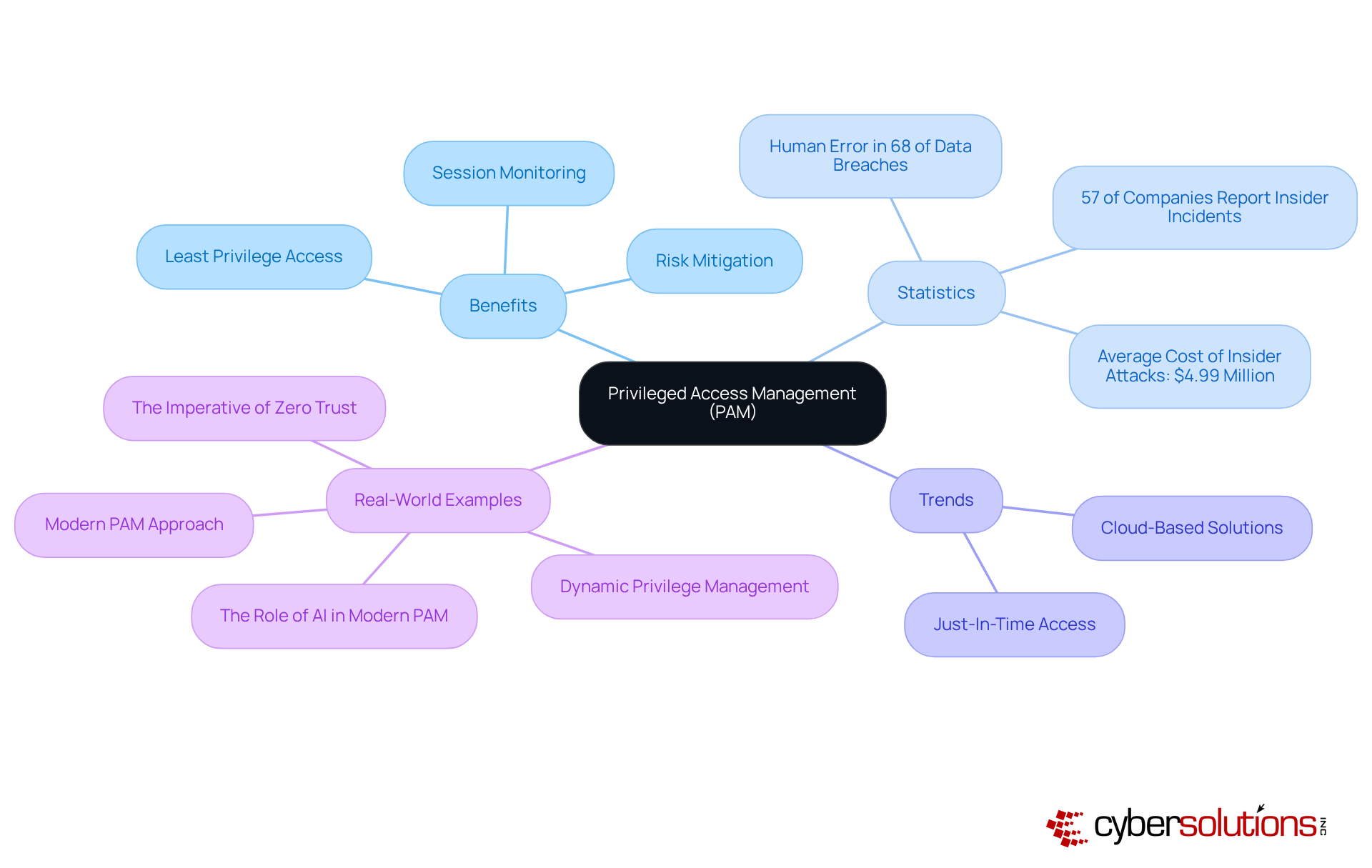
The benefits of privileged access management (PAM) extend beyond being a technical necessity; they are a critical component of an organization’s cybersecurity strategy. With the rise of sophisticated cyber threats, [managing access to sensitive data](https://thehackernews.com/search/label/Privileged Access Management) and critical systems has never been more vital. PAM focuses on controlling elevated rights granted to users, ensuring that only authorized personnel can access sensitive information and execute essential operations. This involves implementing policies for least privilege access, session monitoring, and auditing to thwart unauthorized access and mitigate risks associated with insider threats. Organizations can significantly reduce their attack surface and bolster their overall security posture by leveraging the benefits of privileged access management in managing privileged accounts effectively.
The urgency of PAM is highlighted by concerning statistics:
Effective PAM solutions work seamlessly in the background, applying least privilege automatically, which showcases the benefits of privileged access management by reducing the attack surface and enhancing the overall security posture of organizations.
Recent trends indicate a shift towards cloud-based PAM solutions, reflecting the increasing complexity of hybrid environments. For instance, the implementation of just-in-time (JIT) privileged access minimizes the risk of privilege misuse by granting temporary permissions only when necessary. This approach aligns with the principle of least privilege, ensuring users have the minimum permissions required for the shortest duration.
Real-world examples underscore the effectiveness of PAM strategies. Organizations adopting a universal PAM approach report improved security outcomes, which demonstrate the benefits of privileged access management by treating every user as potentially privileged and extending protections across all identities and access points. This shift is crucial in the face of evolving cyber threats, where attackers target any identity, not just system administrators. As cybersecurity experts emphasize, "Privileged accounts with access to your critical systems and sensitive data are among the most vulnerable elements in cloud setups."
As the cybersecurity landscape evolves, it is crucial to recognize the benefits of privileged access management. Experts assert that organizations must operate under the assumption that no identity or connection is inherently trustworthy, necessitating robust authentication and authorization for every request. By integrating PAM into their overall security strategy, organizations can leverage the benefits of privileged access management to significantly enhance their defenses against cyber threats and ensure compliance with regulatory frameworks.
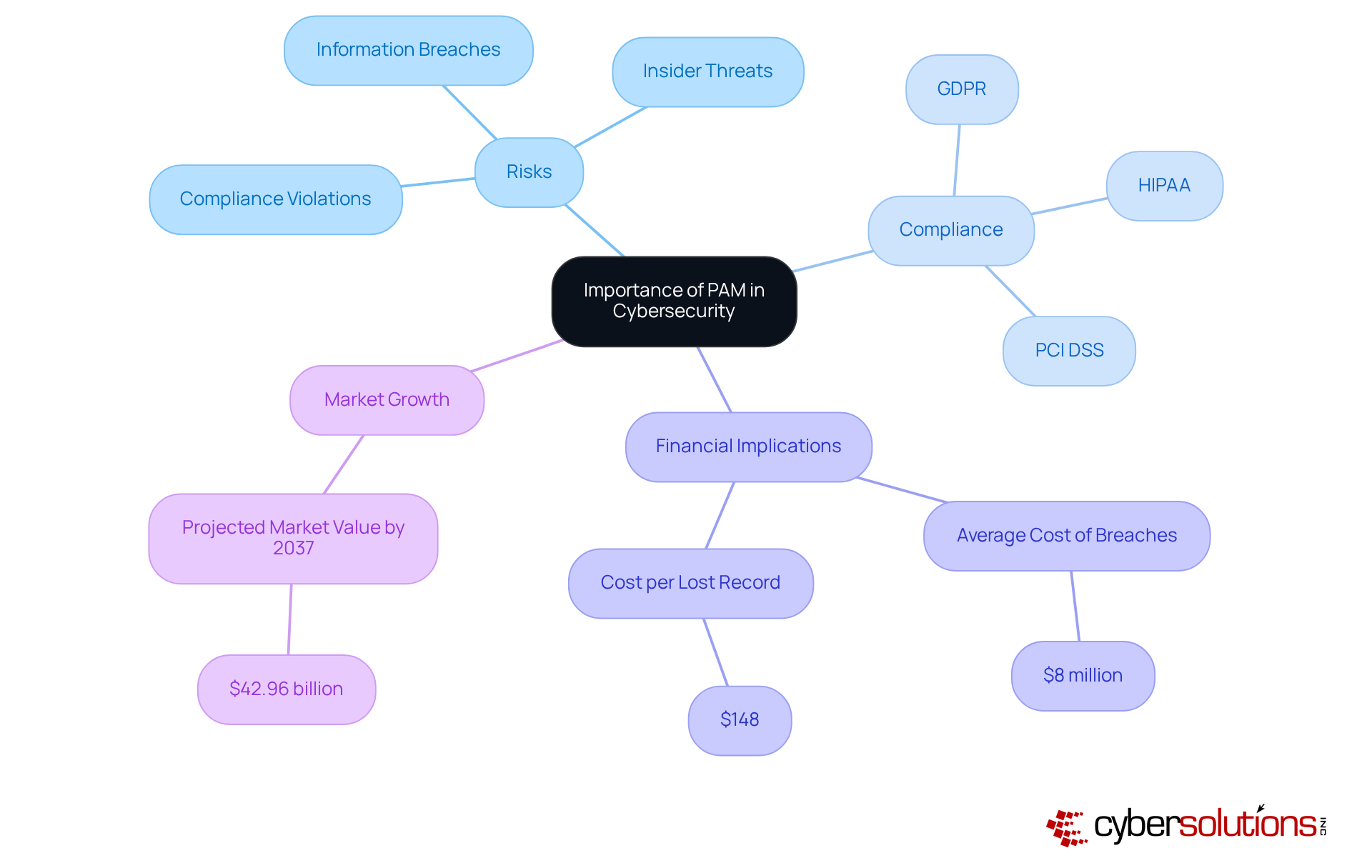
In today's world, the stakes in cybersecurity are higher than ever, especially for organizations that handle sensitive information. The significance of Privileged Access Management (PAM) is paramount, as it highlights the benefits of privileged access management by serving as a frontline defense against a multitude of risks, including information breaches, insider threats, and compliance violations. Alarmingly, a staggering 74% of breaches stem from the misuse of privileged credentials, underscoring the urgent need for robust PAM solutions. As Centrify aptly states, "privileged information misuse is the primary reason for breaches in organizations," which highlights PAM's essential role in safeguarding sensitive data.
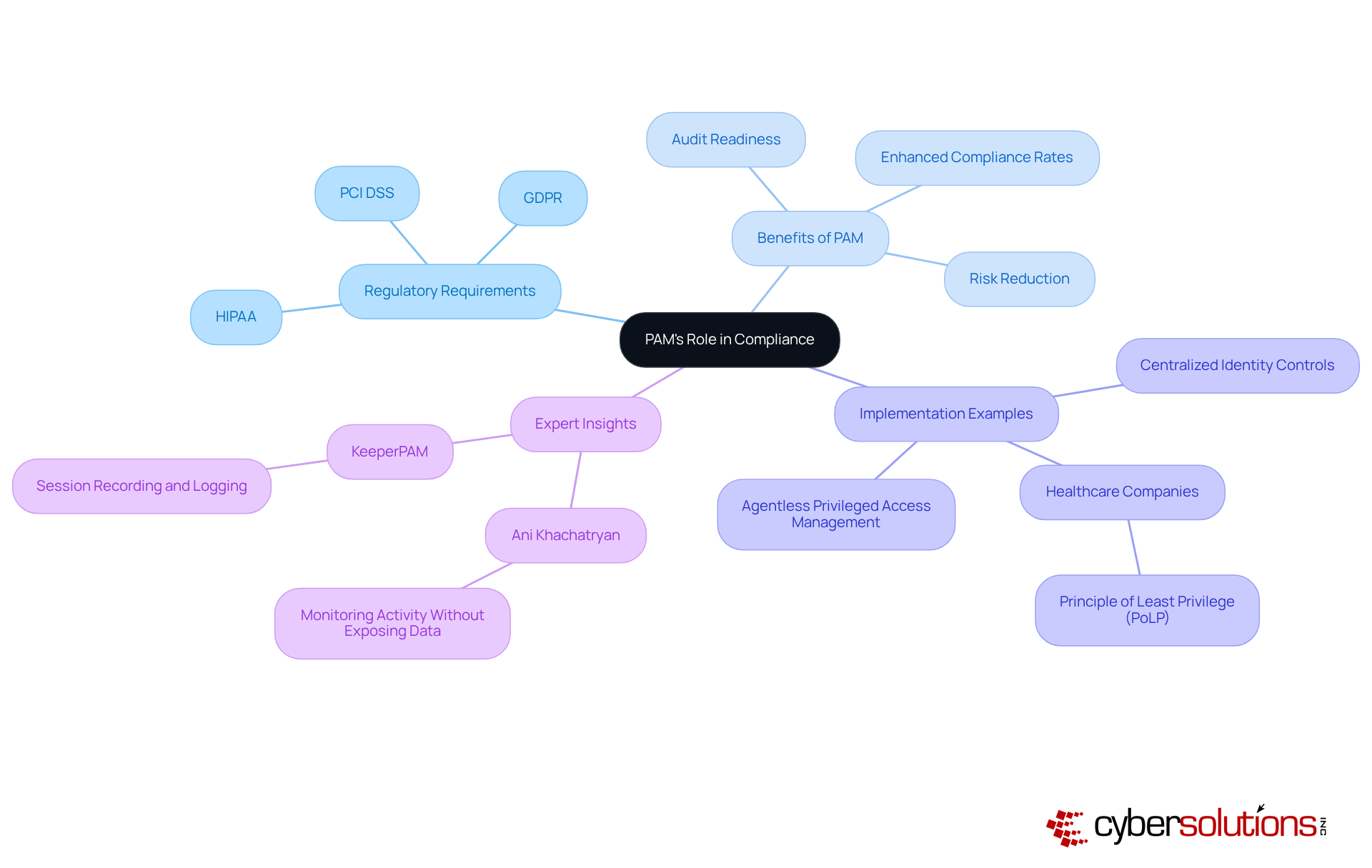
Regulatory frameworks such as GDPR, HIPAA, and PCI DSS impose strict controls over access to sensitive information, positioning PAM not merely as a security measure but as a compliance necessity. By implementing PAM, organizations can proactively manage access rights, monitor user activities, and ensure adherence to regulatory requirements. This not only protects their assets but also preserves their reputation in an increasingly scrutinized environment.
The financial implications of neglecting PAM are significant. The typical cost of a breach in the U.S. hovers around $8 million, with the price per lost or stolen record reaching $148. Clearly, investing in PAM showcases the benefits of privileged access management as a strategic choice that can mitigate potential financial losses while enhancing overall security posture. Furthermore, the PAM market is projected to soar to $42.96 billion by 2037, reflecting the growing recognition of its critical value in the cybersecurity landscape. Organizations must act now to fortify their defenses and ensure compliance in an era where the cost of inaction can be devastating.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations that handle sensitive data. The benefits of privileged access management are evident, as implementing PAM is a critical step in fortifying defenses against the ever-evolving threats that target privileged accounts.
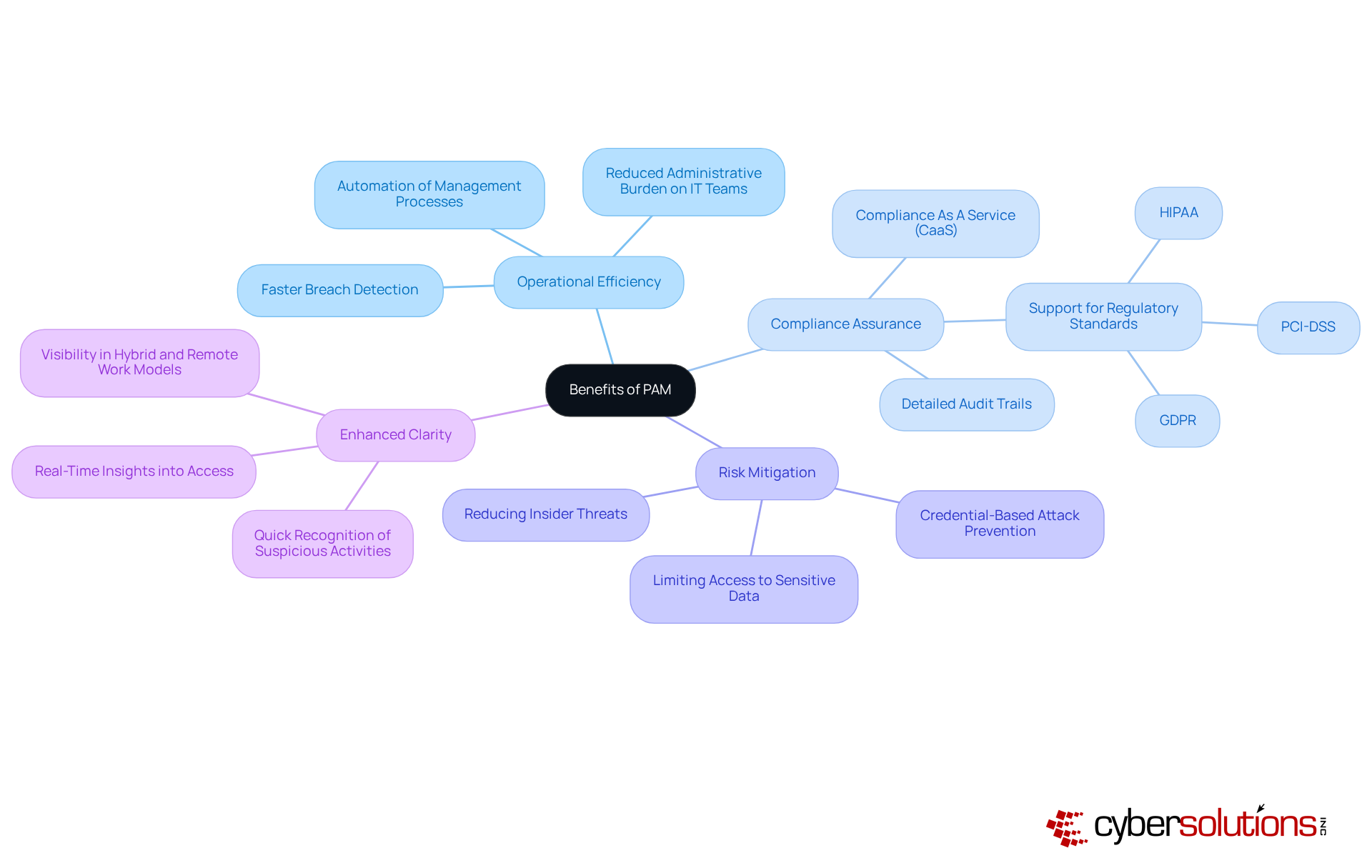
The benefits of privileged access management (PAM) solutions drastically lower the risk of unauthorized access and data breaches by enforcing strict access controls and continuously monitoring user activities. For instance, entities utilizing PAM have reported a reduction in exposure time for privileges from months to mere hours, effectively minimizing the window of opportunity for potential attacks. With 84% of entities experiencing identity-related breaches in the past year, the urgency for implementing PAM is clear.
Operational Efficiency: By automating management processes, PAM alleviates the administrative burden on IT teams, allowing them to concentrate on strategic initiatives rather than routine tasks. This automation not only streamlines operations but also enhances productivity, as IT staff can focus on higher-value projects. Moreover, PAM solutions can assist entities in detecting breaches more rapidly, as it takes an average of 197 days for them to identify a data breach.
Compliance Assurance: PAM plays a crucial role in helping organizations adhere to regulatory requirements by generating detailed audit trails and ensuring that control measures are consistently enforced. This capability is vital for maintaining compliance with standards such as HIPAA, PCI-DSS, and GDPR, which mandate rigorous oversight of privileged accounts. Furthermore, with the incorporation of Compliance As A Service (CaaS), organizations can obtain end-to-end solutions for regulatory compliance, including expert audit assistance and continuous monitoring, ensuring they stay aligned with evolving compliance standards. As noted by Kaylee Palak, failure to comply can result in legal consequences, reputational damage, and costly fines.
Risk Mitigation: By limiting entry to sensitive data and systems, PAM significantly reduces the potential impact of insider threats and credential-based attacks. Implementing PAM is a proactive measure to safeguard critical assets.
Enhanced Clarity: PAM solutions provide real-time insights into who possesses access to critical systems, allowing organizations to quickly recognize and react to suspicious activities. This visibility is crucial for sustaining a secure environment, especially as businesses adapt to hybrid and remote work models.
In summary, the integration of PAM showcases the benefits of privileged access management, as it not only fortifies security but also enhances operational efficiency and compliance assurance, making it an indispensable component of modern cybersecurity strategies.
The benefits of privileged access management extend beyond being a technical necessity; they serve as a cornerstone for compliance and regulatory adherence in today’s intricate business environment. With regulations like GDPR, HIPAA, and PCI DSS mandating robust controls to safeguard sensitive information, PAM solutions become indispensable. They ensure that only authorized users gain access to critical systems and data, significantly reducing the risk of data breaches and the substantial penalties that follow. Organizations employing PAM have reported enhanced compliance rates, demonstrating the benefits of privileged access management through improved audit readiness with comprehensive activity logs and reports that meet regulatory standards.
As we look ahead to 2025, the significance of PAM will only grow. Regulatory scrutiny is set to intensify, and recent enforcement actions serve as a stark reminder of the financial repercussions of non-compliance. Substantial penalties await those who fail to adhere to these standards. PAM not only simplifies compliance processes but also demonstrates the benefits of privileged access management by cultivating a culture of accountability and transparency, which is essential for maintaining stakeholder trust.
Numerous organizations have adeptly utilized PAM to navigate the complexities of regulatory adherence. For instance, healthcare companies have implemented PAM to enforce the Principle of Least Privilege (PoLP), ensuring employees access only the information necessary for their roles. This strategy not only bolsters security but also aligns with compliance mandates, reflecting a commitment to safeguarding sensitive patient data.
Expert insights further highlight the strategic importance and benefits of privileged access management in regulatory compliance. Industry leaders assert that adopting PAM solutions not only fortifies security frameworks but also positions organizations as responsible stewards of sensitive information. By embracing PAM, businesses can enhance their security posture while effectively managing compliance obligations, ultimately realizing the benefits of privileged access management and fostering trust with clients and stakeholders.
Understanding the benefits of Privileged Access Management (PAM) is crucial for leaders determined to strengthen their organizations against the rising tide of cyber threats. In today’s landscape, where breaches are increasingly common, implementing PAM allows organizations to manage access to sensitive data and critical systems effectively. This ensures that only authorized personnel receive elevated rights, significantly reducing risks associated with insider threats while enhancing operational efficiency and compliance with regulatory frameworks.
Key insights reveal the vital role PAM plays in minimizing the attack surface, streamlining operations, and ensuring adherence to regulations like GDPR and HIPAA. The statistics underscore the urgency of adopting PAM solutions, with a notable percentage of breaches linked to the misuse of privileged credentials. Moreover, the shift towards cloud-based PAM solutions and the implementation of just-in-time access reflect a proactive response to the evolving cybersecurity landscape.
Given these considerations, organizations must prioritize integrating PAM into their cybersecurity strategies. By doing so, they not only protect their critical assets but also cultivate a culture of accountability and transparency. The financial and reputational risks of neglecting PAM highlight its necessity in today’s complex environment. Leaders must act decisively to implement PAM, ensuring their organizations are equipped to tackle the challenges of modern cybersecurity threats while maintaining compliance and operational integrity.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity strategy focused on controlling elevated rights granted to users, ensuring that only authorized personnel can access sensitive information and execute critical operations.
Why is PAM important for organizations?
PAM is important because it helps manage access to sensitive data and critical systems, reducing the attack surface and bolstering overall security posture against sophisticated cyber threats and insider-related security incidents.
What are some key components of PAM?
Key components of PAM include implementing policies for least privilege access, session monitoring, and auditing to prevent unauthorized access and mitigate risks associated with insider threats.
What statistics highlight the urgency of implementing PAM?
Statistics indicate that 57% of companies experience over 20 insider-related security incidents annually, and compromised privileged credentials are a leading cause of catastrophic data loss, making PAM a board-level priority.
How do effective PAM solutions operate?
Effective PAM solutions work seamlessly in the background, applying least privilege automatically to reduce the attack surface and enhance overall security without disrupting user operations.
What recent trends are observed in PAM solutions?
There is a trend towards cloud-based PAM solutions and the implementation of just-in-time (JIT) privileged access, which grants temporary permissions only when necessary, aligning with the principle of least privilege.
What benefits do organizations experience by adopting a universal PAM approach?
Organizations that adopt a universal PAM approach report improved security outcomes by treating every user as potentially privileged and extending protections across all identities and access points.
What assumption should organizations operate under regarding identities and connections?
Organizations should operate under the assumption that no identity or connection is inherently trustworthy, necessitating robust authentication and authorization for every request.
How can PAM enhance an organization's defenses against cyber threats?
By integrating PAM into their overall security strategy, organizations can significantly enhance their defenses against cyber threats and ensure compliance with regulatory frameworks.