
In today's world, where cyber threats are not just common but increasingly sophisticated, organizations must prioritize the creation of a robust cyber response plan. The stakes are high, and this guide outlines five essential steps leaders can take to establish an effective incident response framework. By doing so, organizations can navigate the complexities of cybersecurity challenges with confidence. Yet, with only a small fraction of companies fully prepared to handle incidents, one pressing question remains: how can leaders ensure their organizations are not among the unprepared when a cyber crisis strikes?
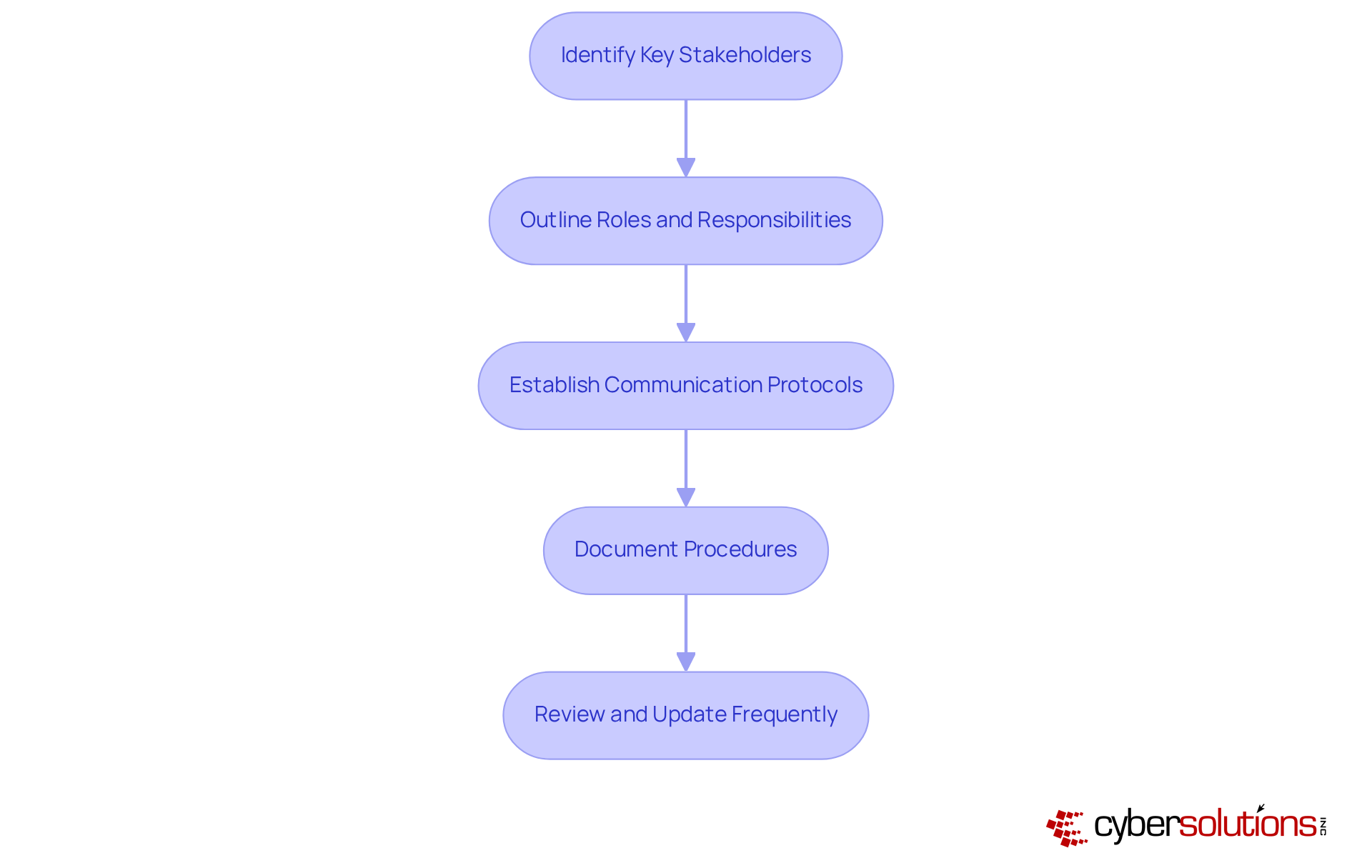
To effectively define your incident response plan, it’s crucial to follow these essential steps:
Identify Key Stakeholders: Involve all relevant parties in the response process, including IT personnel, management, legal advisors, and external partners. This multidisciplinary approach ensures comprehensive coverage of all aspects of incident management.
Outline Roles and Responsibilities: Clearly define the roles of each team member during an incident. Specify who will lead the response, manage communications with stakeholders, and oversee technical operations. Clarity in these roles is vital; organizations with well-defined responsibilities are better equipped to respond effectively.
Establish Communication Protocols: Develop a robust communication plan that outlines how information will be shared both internally and externally during an incident. This plan should include updated contact lists and escalation procedures to guarantee timely and accurate information flow.
Document Procedures: Create comprehensive documentation detailing the specific actions to be taken in response to various incidents, such as data breaches or ransomware attacks. This should encompass guidelines for detection, analysis, containment, eradication, and recovery. Notably, only 55% of organizations currently have a thoroughly documented crisis management plan, highlighting a significant gap in preparedness.
Review and Update Frequently: Treat the action plan as a dynamic document that requires regular evaluations and revisions to address organizational changes and emerging threats. Organizations that conduct frequent assessments and tabletop exercises are more likely to maintain readiness and adapt effectively to new challenges. In fact, only 30% of companies perform tabletop exercises, indicating a critical area for improvement.
By adhering to these steps, organizations can enhance their cyber response plan, ensuring they are better prepared to manage cyber threats and mitigate potential harm.
Preparation for an effective cyber response plan is essential in today’s rapidly evolving cybersecurity landscape. With healthcare organizations facing unique challenges, understanding how to effectively utilize a cyber response plan can mean the difference between a minor setback and a major crisis.
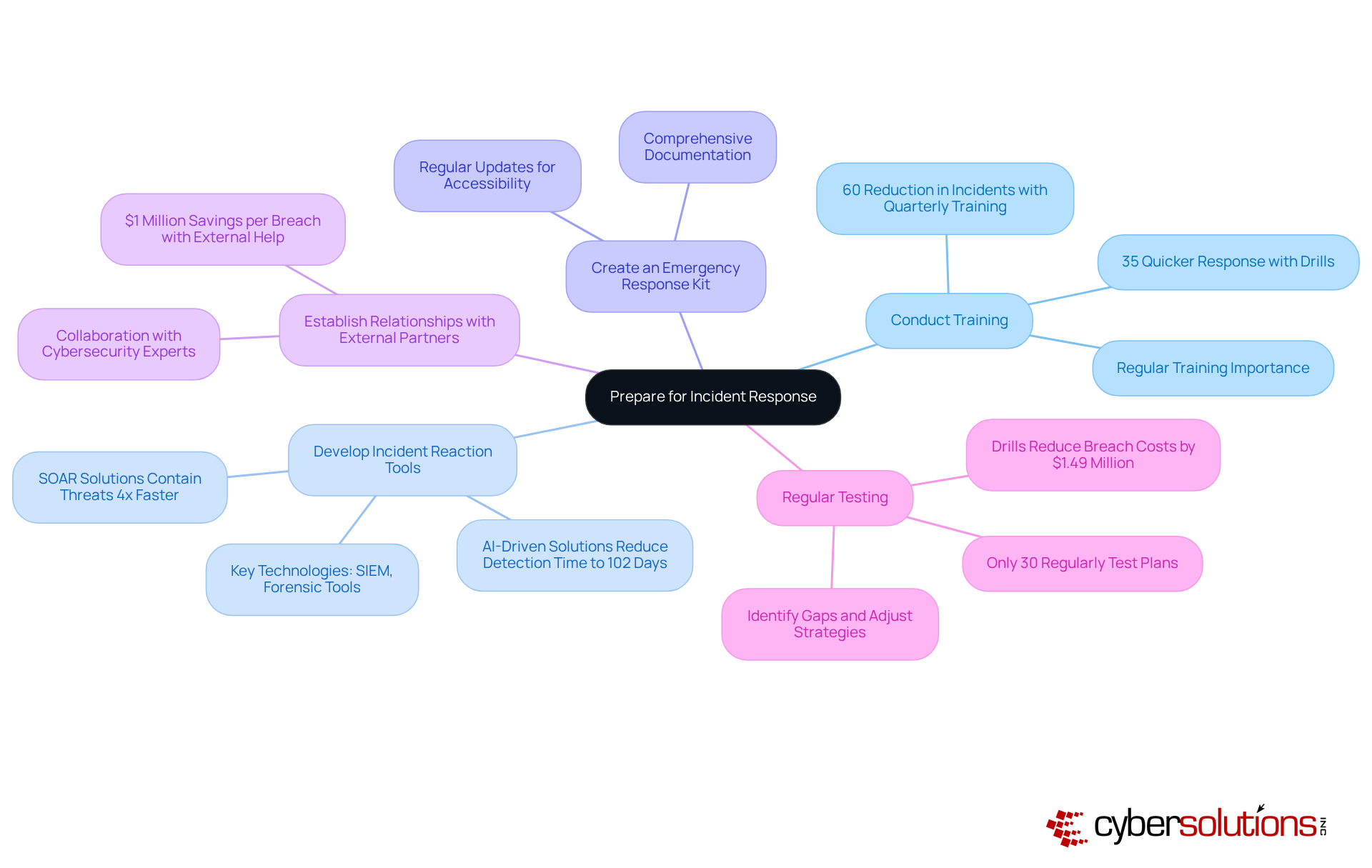
Conduct Training: Regular training for your crisis management team and all staff is crucial. Clearly outlining roles and responsibilities during an event, along with employing tabletop exercises that mimic real-world situations, can significantly enhance preparedness. Did you know that groups performing emergency drills at least once every three months react 35% quicker to situations? This statistic underscores the importance of consistent training.
Develop Incident Reaction Tools: Equip your team with essential tools for detection, analysis, and action. Key technologies include Security Information and Event Management (SIEM) systems, forensic tools, and communication platforms. Organizations utilizing AI-driven security solutions can decrease compromise detection time to an average of 102 days. This highlights the significance of sophisticated tools in contemporary emergency response.
Create an Emergency Response Kit: Assemble a comprehensive kit that includes all necessary documentation, contact lists, and tools required during an emergency. Ensure this kit is easily accessible and regularly updated, allowing your team to act swiftly and effectively when an incident occurs.
Establish Relationships with External Partners: Identify and cultivate relationships with external cybersecurity experts, legal advisors, and law enforcement agencies. These collaborations can provide essential assistance during an event. In fact, entities that engage external cybersecurity companies save an average of $1 million per breach. Isn’t it time to consider how these partnerships could bolster your response efforts?
Regularly test your cyber response plan by conducting frequent drills and simulations to evaluate its effectiveness in incident management. Alarmingly, only 30% of organizations regularly test their plans, leaving many unaware of their effectiveness. Regular testing not only identifies gaps but also allows for adjustments based on outcomes, ensuring that your response strategy remains robust and effective against evolving threats.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially in healthcare. With increasing threats, organizations must develop a cyber response plan to take proactive measures in safeguarding their systems. Here’s how to effectively detect and analyze incidents:
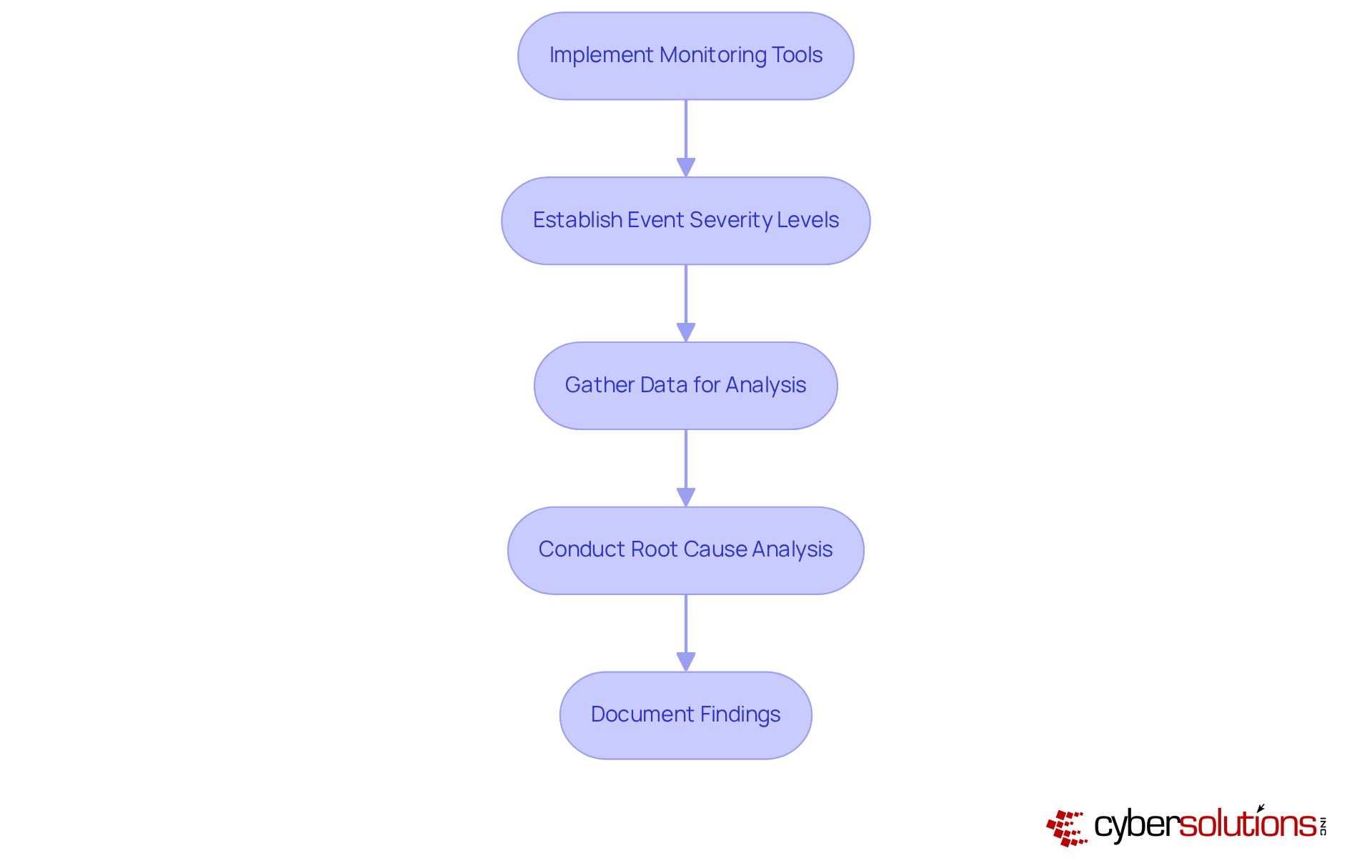
Implement Monitoring Tools: Utilize automated monitoring tools, such as those offered by Cyber Solutions, to continuously scan for unusual activities or anomalies within your network and systems. This proactive approach is essential; organizations with a strong cyber response plan and robust monitoring capabilities can detect breaches significantly faster.
Establish Event Severity Levels: Clearly define what constitutes minor, moderate, or severe occurrences. This classification helps prioritize responses based on potential impact, ensuring that crucial events receive immediate attention. For instance, 38% of firms with more than 500 staff have adopted such severity classifications, underscoring their significance in efficient event management.
Gather Data for Analysis: Collect relevant data from logs, alerts, and user reports to thoroughly examine occurrences. Essential details may include timestamps, impacted systems, and user actions preceding the event. Organizations that uphold extensive logging practices can significantly enhance their event analysis capabilities.
Conduct Root Cause Analysis: After identifying an occurrence, perform a root cause analysis to understand how it happened and which vulnerabilities were exploited. This step is vital for preventing future incidents and enhancing overall security posture.
Document Findings: Maintain detailed records of the occurrence detection and analysis process. This documentation is essential for post-event evaluations and can guide future event management strategies. Notably, entities that record their response procedures can shorten breach lifecycles by an average of 69 days compared to those that do not.
By adhering to these steps, organizations can significantly improve their event detection and analysis abilities, ultimately leading to a more efficient cyber response plan for their cybersecurity strategies.
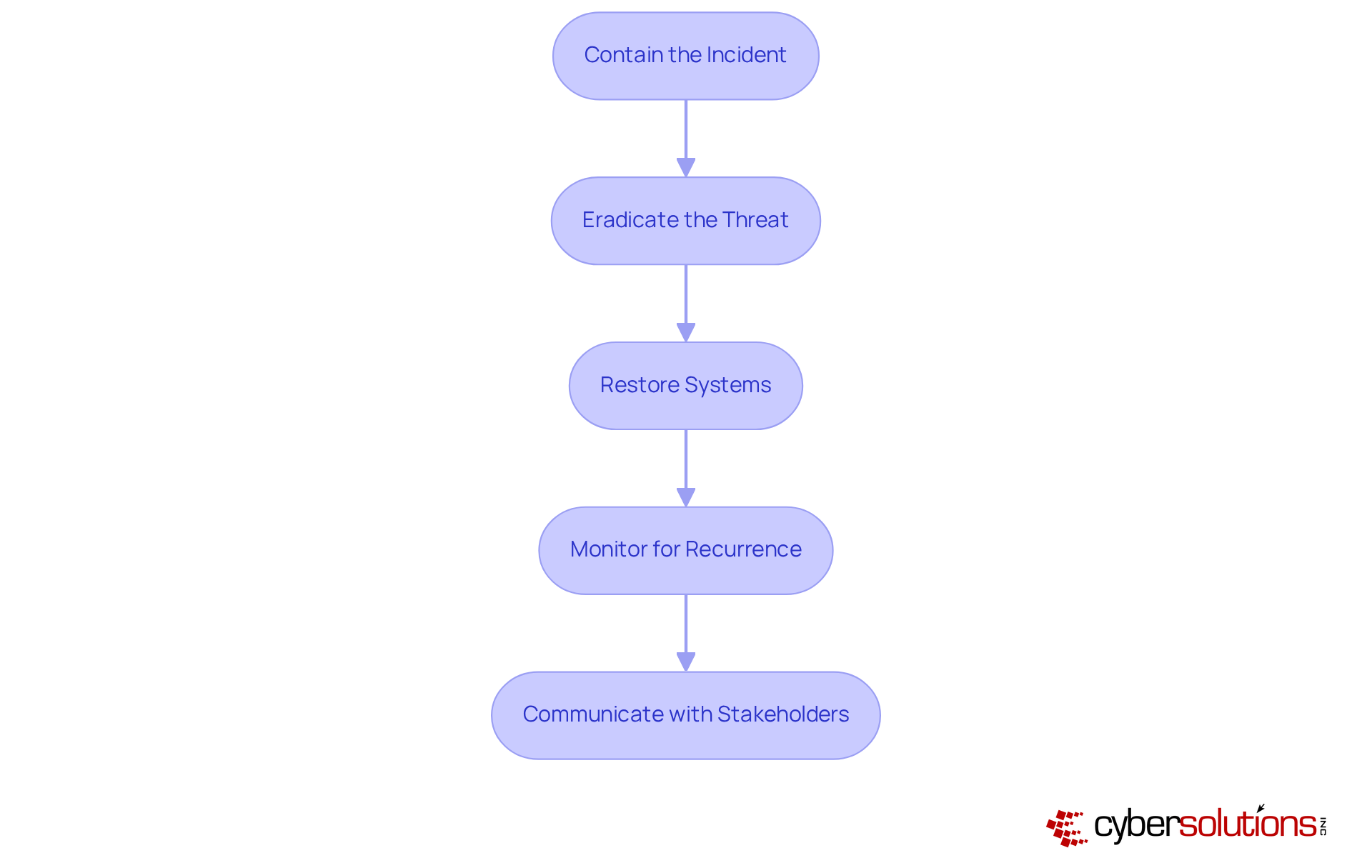
In today's digital landscape, the importance of robust cybersecurity measures cannot be overstated. Organizations face an ever-evolving array of threats, which makes having an effective cyber response plan essential for survival. To effectively contain, eradicate, and recover from cybersecurity incidents, organizations should implement the following steps:
In 2025, almost 1 in 4 small and mid-sized enterprises (SMBs) faced a ransomware event, highlighting the crucial requirement for effective crisis management strategies. Cybersecurity leaders emphasize that a cyber response plan is not developed in the moment; it is earned through repetition, review, and refinement. Regular training and simulations can enhance an organization's readiness for its cyber response plan, enabling faster response times and minimizing the impact of incidents. In fact, companies that conduct monthly security training reduce the chances of incidents by 60%. As Sean Blanton observes, '258 days-that’s the average duration to identify and manage an incident. That’s nearly nine months of exposure, emphasizing the urgency of effective strategies for addressing situations. Case studies illustrate that organizations with strong response strategies, like those executed by Cyber Solutions, are better prepared to manage breaches, ultimately protecting their operations.
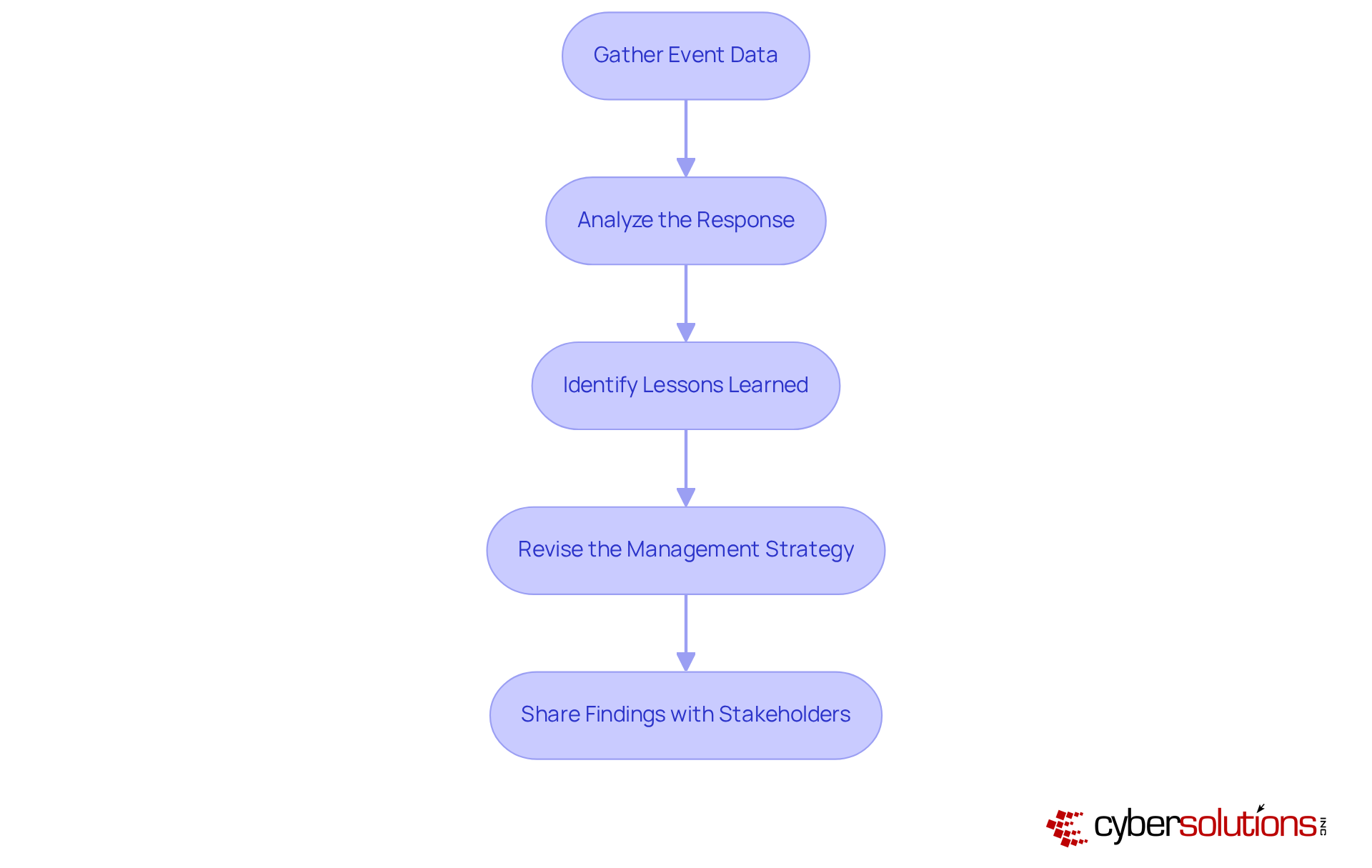
To conduct an effective post-incident review, it’s essential to follow these steps:
Gather Event Data: Start by collecting comprehensive data from the event, including timelines, actions taken, and communications. This foundational information is crucial for a thorough review.
Analyze the Response: Evaluate how the situation was managed, identifying strengths and weaknesses. Key elements to consider include reaction time, communication efficiency, and adherence to the cyber response plan. Notably, organizations that conduct emergency exercises at least once every three months respond 35% quicker to events, underscoring the importance of readiness. For instance, a healthcare provider that swiftly assembled a crisis management team within a day illustrates how prompt action can mitigate threats and reduce damage.
Identify Lessons Learned: Document essential insights from the incident, focusing on areas for improvement in both the response process and the incident management plan. A significant 68% of incidents in 2025 involved a human element, highlighting the urgent need for enhanced training and awareness.
Revise the Management Strategy: Based on the review findings, adjust the management strategy to address identified vulnerabilities and improve future actions. Organizations without a documented cyber response plan faced an average lifecycle of 241 days for security incidents, highlighting the necessity of proactive updates. Furthermore, thorough documentation, including risk assessments and compliance reports tailored to HIPAA standards, is vital for audit readiness.
Share Findings with Stakeholders: Communicate the results of the post-incident review with all relevant stakeholders, ensuring that lessons learned are disseminated and understood throughout the organization. Clear internal communication protocols can prevent 21% more secondary breaches caused by mismanaged response efforts.
Building an effective cyber response plan is not just advisable; it’s essential for organizations determined to protect their operations from the escalating threat of cyber incidents. A structured approach-one that includes defining an incident response plan, preparing for potential incidents, detecting and analyzing threats, containing and eradicating issues, and conducting thorough post-incident reviews-can significantly bolster an organization’s resilience against these threats.
Consider this: Are all stakeholders actively involved in your planning process? Establishing clear communication protocols and regularly updating your response plan to adapt to evolving challenges are critical steps. Moreover, the importance of training staff, utilizing advanced detection tools, and maintaining robust external partnerships cannot be overstated. Organizations that engage in these practices are far more likely to respond effectively and mitigate the impact of cyber incidents.
As cyber threats continue to evolve, leaders must prioritize the development and maintenance of a robust cyber response plan. Fostering a culture of preparedness and continuous improvement not only safeguards assets but also builds trust with stakeholders and clients. The time to act is now-invest in a comprehensive cyber response strategy to secure a resilient future.
What are the essential steps to define an incident response plan?
The essential steps include identifying key stakeholders, outlining roles and responsibilities, establishing communication protocols, documenting procedures, and reviewing and updating the plan frequently.
Who should be involved in the incident response process?
All relevant parties should be involved, including IT personnel, management, legal advisors, and external partners to ensure comprehensive coverage of incident management.
Why is it important to outline roles and responsibilities in an incident response plan?
Clearly defining roles is vital because organizations with well-defined responsibilities are better equipped to respond effectively during an incident.
What should a communication protocol include during an incident?
A communication protocol should include updated contact lists and escalation procedures to guarantee timely and accurate information flow both internally and externally.
What types of incidents should the documented procedures cover?
The documented procedures should cover various incidents, such as data breaches and ransomware attacks, detailing guidelines for detection, analysis, containment, eradication, and recovery.
How often should the incident response plan be reviewed and updated?
The incident response plan should be treated as a dynamic document requiring regular evaluations and revisions to address organizational changes and emerging threats.
What is the significance of conducting training for the crisis management team?
Regular training enhances preparedness by clearly outlining roles and responsibilities and employing tabletop exercises that mimic real-world situations, improving response times.
What tools are essential for incident response?
Essential tools include Security Information and Event Management (SIEM) systems, forensic tools, and communication platforms.
What is an emergency response kit, and what should it include?
An emergency response kit is a comprehensive collection of necessary documentation, contact lists, and tools required during an emergency, which should be easily accessible and regularly updated.
Why is it important to establish relationships with external partners in cybersecurity?
Cultivating relationships with external cybersecurity experts, legal advisors, and law enforcement can provide essential assistance during an event and may save organizations significant costs during breaches.
How can organizations test their cyber response plan?
Organizations should regularly test their cyber response plan by conducting drills and simulations to evaluate its effectiveness in incident management and identify any gaps.