
In today's world, where data breaches and cyber threats loom large, organizations are confronted with the formidable task of navigating intricate regulatory landscapes. Cybersecurity compliance services are not just a checkbox to tick; they offer a strategic opportunity to bolster data protection and cultivate trust with clients. But how can companies ensure they are not only compliant but also resilient against the ever-evolving threats?
This article explores four best practices that can significantly enhance the success of cybersecurity compliance initiatives, steering organizations toward a more secure future. By understanding the current landscape of cybersecurity threats, healthcare organizations can better appreciate the implications for their operations. With the right Cyber Solutions in place, they can effectively tackle these challenges head-on.
Organizations must recognize the critical importance of cyber security compliance services in adhering to key regulatory frameworks like HIPAA, PCI-DSS, and GDPR. These frameworks set forth specific requirements that dictate how sensitive data must be handled and protected. For example, HIPAA enforces stringent controls over healthcare data, while PCI-DSS is dedicated to securing payment card information. Understanding these frameworks is essential for companies to effectively evaluate their regulatory obligations, and utilizing cyber security compliance services can help avoid costly penalties.
Moreover, identifying the overlaps between various regulations can streamline compliance efforts and reduce redundancy in processes. By grasping the nuances of these frameworks, organizations can not only enhance their data protection strategies but also foster trust with their clients and stakeholders. In a landscape where cybersecurity threats are ever-evolving, being proactive about cyber security compliance services is not just a necessity; it's a strategic advantage.
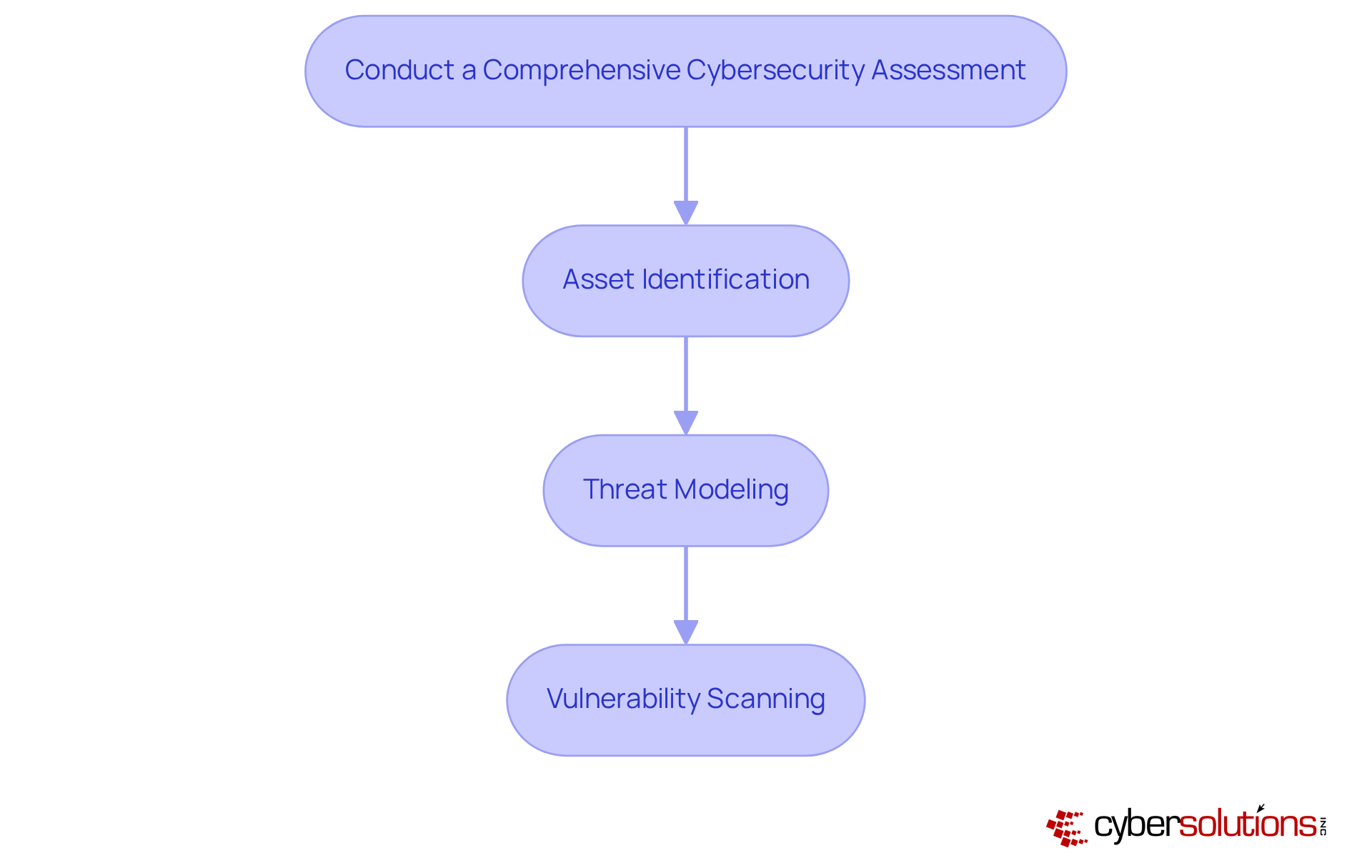
Cybersecurity is not just a technical requirement; it’s a critical necessity for healthcare organizations. With the increasing frequency and sophistication of cyber threats, CFOs face unique challenges that demand immediate attention. A thorough cybersecurity assessment is essential, involving the evaluation of existing security measures, identification of vulnerabilities, and understanding of potential threats. Organizations should leverage industry-standard methodologies, such as the NIST Cybersecurity Framework, to guide their assessments effectively.
This assessment process should encompass:
By establishing a baseline of their cybersecurity posture, entities can prioritize areas for enhancement and allocate resources efficiently. Addressing identified gaps with customized remediation strategies - such as policy updates, system upgrades, and process improvements - is crucial for achieving conformity with CMMC.
Frequent evaluations not only help organizations adapt to evolving threats but also ensure that they meet regulatory obligations through cybersecurity compliance services. Have you considered how a mock audit can prepare your organization for the official CMMC evaluation? This proactive step ensures that you are thoroughly equipped to demonstrate adherence during audits. Specialized advice and assistance from cybersecurity compliance services are vital for obtaining certification and managing ongoing compliance effectively.
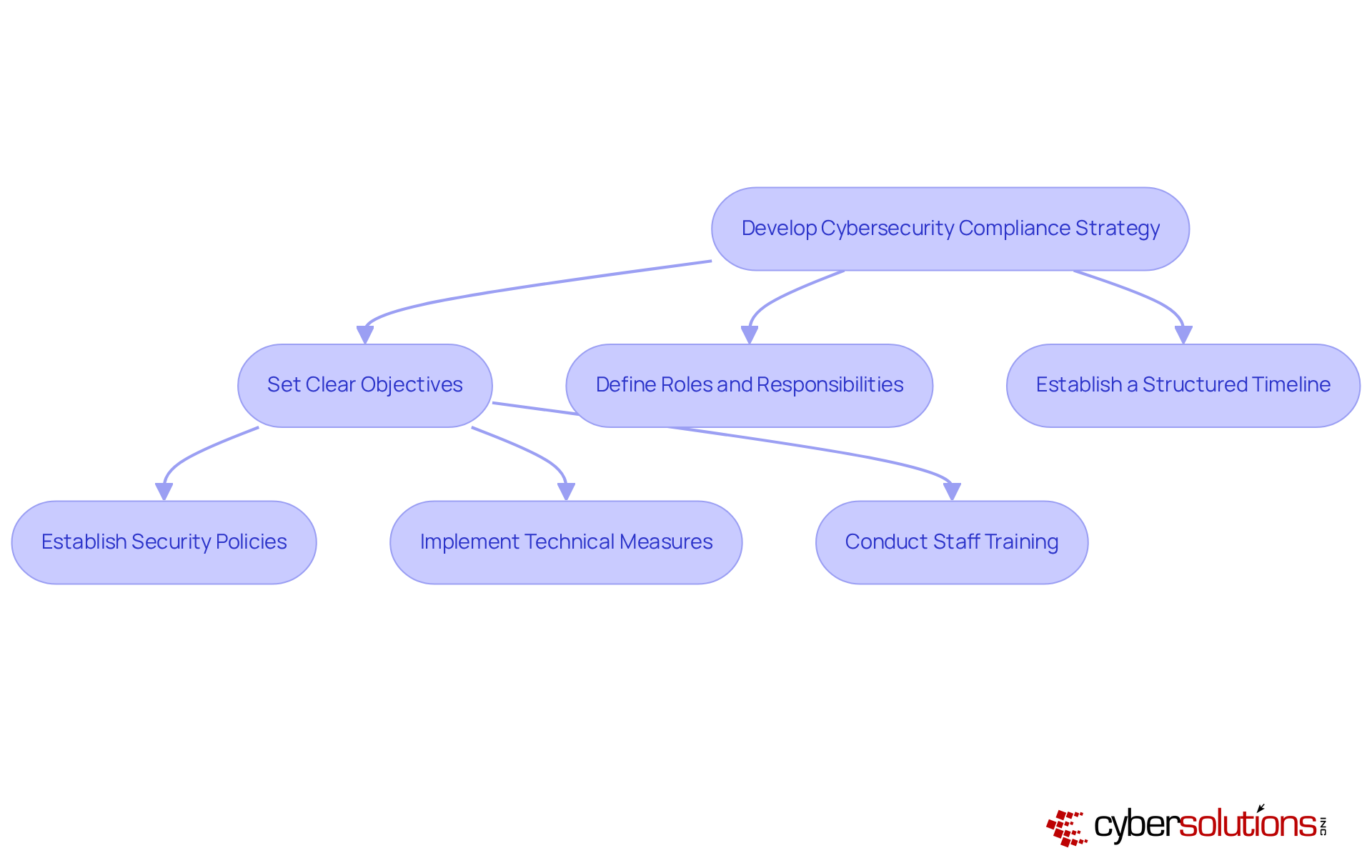
To effectively navigate the complexities of cybersecurity regulations in 2026, organizations must develop a tailored plan that incorporates cyber security compliance services and aligns with their specific legal obligations and overarching business goals. This strategy should include:
Essential components involve establishing robust security policies, implementing technical measures, and conducting regular staff training to foster a culture of cyber security compliance services.
Utilizing automation tools for cyber security compliance services can significantly streamline processes, ensuring ongoing adherence to rules while alleviating the burden of manual tasks. In fact, organizations that embrace automation can save an average of 3 to 5 hours each week on regulatory activities, enhancing efficiency and allowing teams to focus on strategic initiatives. As industry leaders emphasize, aligning regulatory strategies with business objectives by utilizing cyber security compliance services not only mitigates risks but also strengthens overall operational resilience.
For instance, organizations that have successfully integrated their cybersecurity strategies with regulatory requirements have reported improved visibility into risks and faster responses through cyber security compliance services. This alignment is vital, as 76% of organizations leverage technology for risk assessments, highlighting the necessity of a proactive approach in today’s dynamic threat landscape. By customizing their regulatory strategies and utilizing cyber security compliance services, organizations can bolster their security posture while effectively managing regulatory costs, ultimately positioning themselves for success in a competitive marketplace.
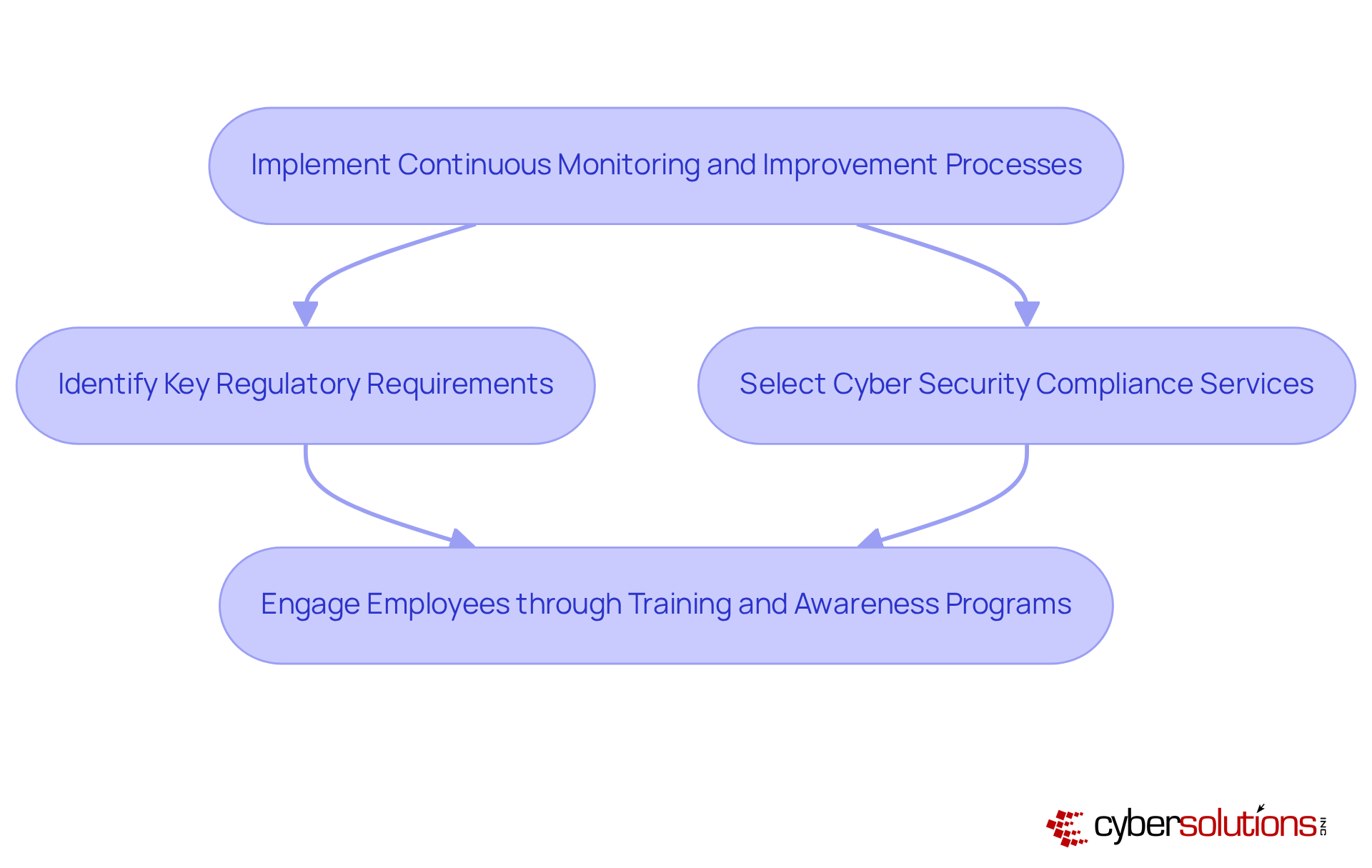
Ongoing monitoring is essential for evaluating the effectiveness of cyber security compliance services and their adherence efforts. Organizations must leverage automated tools to monitor adherence status, detect anomalies, and facilitate real-time incident response. This proactive approach enables organizations to swiftly adapt to evolving compliance environments and emerging threats through cyber security compliance services. Did you know that 21% of C-suite executives have identified regulatory adherence as their top strategic priority? This statistic reflects a growing emphasis on governance at the executive level. Furthermore, automation tools significantly enhance adherence tracking efficiency, with 65% of regulatory professionals indicating that automation is crucial for reducing complexity and costs.
To implement automated tools effectively, companies should start by:
Engaging employees through ongoing training and awareness programs is vital; it fosters a culture of continuous improvement and strengthens the overall security posture of the organization. As entities prepare for 2026, the focus will shift from mere policy documentation to demonstrating genuine security performance, making the integration of cyber security compliance services even more critical. By adopting these practices, organizations can ensure compliance while effectively managing risks in an increasingly complex environment.
In today’s digital landscape, the importance of cybersecurity compliance services cannot be overstated. Organizations are navigating an increasingly complex web of regulations, making it essential to prioritize compliance. By understanding key frameworks like HIPAA, PCI-DSS, and GDPR, companies can effectively manage their obligations while protecting sensitive data. This proactive stance not only mitigates risks but also builds trust with clients and stakeholders, giving organizations a strategic edge in a competitive market.
To thrive amidst these challenges, organizations must adopt essential best practices. The following are critical steps:
Each of these elements ensures that organizations not only meet regulatory requirements but also adapt to evolving threats. By leveraging automation tools and fostering a culture of compliance, businesses can streamline their efforts, reduce costs, and enhance operational resilience.
As the regulatory environment continues to evolve, remaining vigilant and proactive in compliance efforts is crucial. Embracing these best practices safeguards against potential penalties and strengthens the overall security posture. Organizations that take action now to enhance their compliance strategies will reap long-term benefits, ensuring they are prepared for future challenges. In an increasingly digital world, the time to act is now.
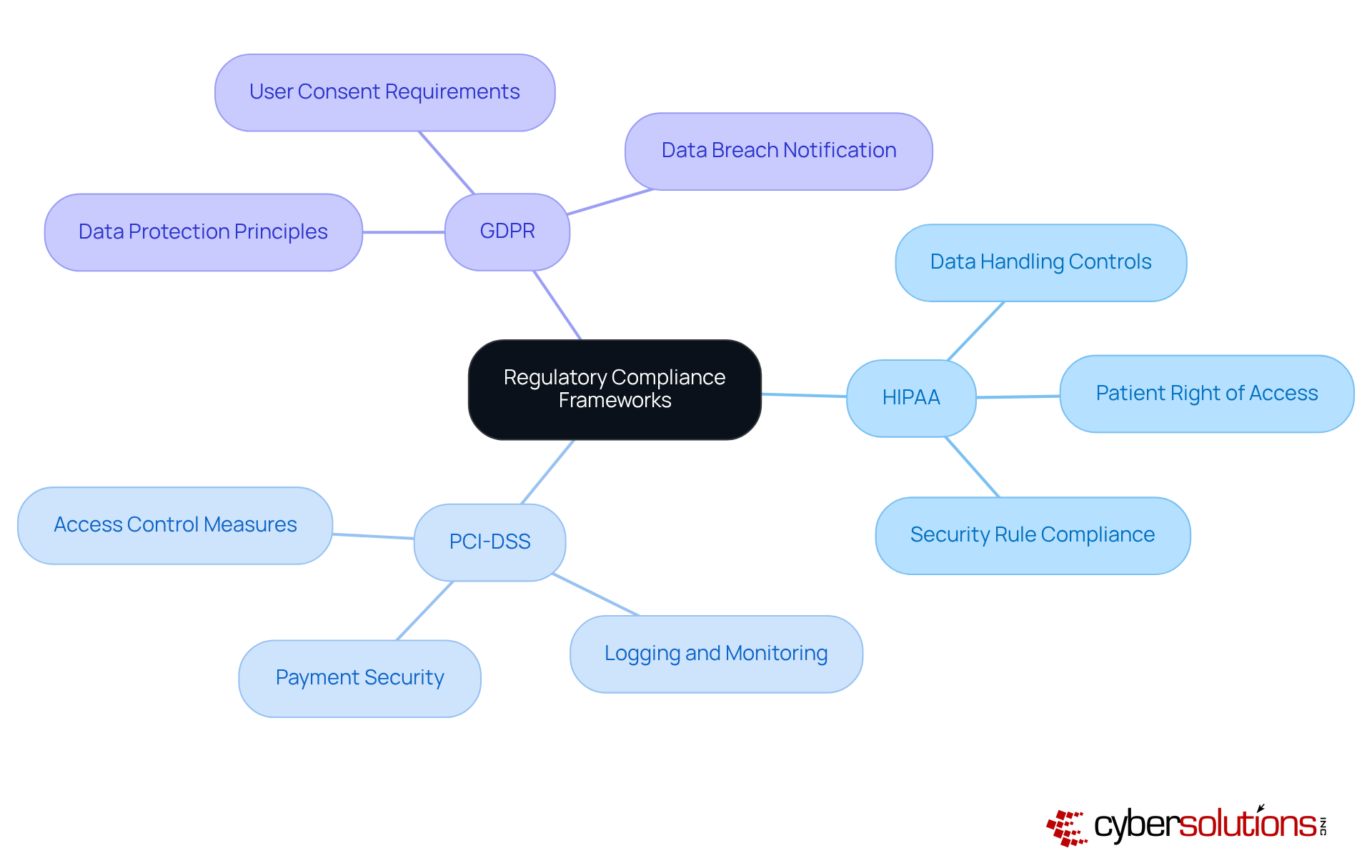
What are regulatory compliance frameworks in the context of cybersecurity?
Regulatory compliance frameworks are sets of guidelines and requirements that organizations must follow to protect sensitive data. Key frameworks include HIPAA, PCI-DSS, and GDPR, each dictating how specific types of data should be handled and secured.
What is HIPAA and what does it regulate?
HIPAA (Health Insurance Portability and Accountability Act) enforces stringent controls over healthcare data, ensuring that sensitive health information is properly protected.
What is PCI-DSS and its purpose?
PCI-DSS (Payment Card Industry Data Security Standard) is dedicated to securing payment card information, setting requirements for organizations that handle credit card data to protect it from breaches.
How can organizations benefit from understanding regulatory compliance frameworks?
Organizations that understand these frameworks can effectively evaluate their regulatory obligations, enhance their data protection strategies, and avoid costly penalties associated with non-compliance.
What is the advantage of identifying overlaps between various regulations?
Identifying overlaps between different regulations can streamline compliance efforts and reduce redundancy in processes, making it easier for organizations to meet their obligations.
Why is being proactive about cybersecurity compliance services important?
Being proactive about cybersecurity compliance services is crucial due to the ever-evolving nature of cybersecurity threats. It not only helps in meeting regulatory requirements but also serves as a strategic advantage in fostering trust with clients and stakeholders.