
In today's world, where cyber threats are more prevalent than ever, understanding the complexities of vulnerability scanning is crucial for C-suite leaders. This automated process goes beyond being a mere technical task; it acts as a frontline defense, empowering organizations to pinpoint and address security weaknesses before they can be exploited. With the alarming rise in cybersecurity breaches, a pressing question arises: how can executives ensure their organizations are not just compliant, but truly resilient against evolving threats?
This guide explores the mechanics of vulnerability scanning, its vital role in risk management, and the best practices that can protect sensitive information while enhancing financial stability. By delving into these aspects, we aim to equip leaders with the knowledge needed to navigate the intricate landscape of cybersecurity effectively.
Cybersecurity is not just a technical necessity; it’s a critical component of healthcare that can make or break an organization. With the staggering rise in breaches - 809 reported in 2023 alone, a 136% increase from the previous year - healthcare providers face unique challenges that demand immediate attention. To understand how vulnerability scanning works, it emerges as an essential automated process designed to pinpoint security weaknesses across software, systems, and networks. This proactive approach allows organizations to learn how vulnerability scanning works, enabling them to identify vulnerabilities before they can be exploited, safeguarding sensitive information and ensuring compliance with industry standards. After all, maintaining stakeholder confidence is paramount, and the cost of a breach can exceed $4.5 million, making risk management not just advisable but essential.
Statistics reveal that 84% of companies harbor significant risks, with half of these potentially addressable through straightforward software updates. This highlights the financial repercussions of neglecting risk management. By conducting routine security assessments, organizations can significantly reduce operational risks and bolster their financial stability, avoiding incidents that could lead to severe reputational damage.
In addition to vulnerability scanning, application allowlisting stands out as a gold standard in cybersecurity. This method actively blocks malware and unauthorized programs, effectively shrinking the attack surface and minimizing vulnerabilities. By permitting only authorized applications to run, organizations can thwart ransomware and other malicious software, ensuring compliance with stringent regulations like HIPAA, PCI-DSS, and GDPR.
For C-suite executives, understanding how vulnerability scanning works in conjunction with application allowlisting is crucial, as these elements directly impact the organization’s risk management and financial health. Furthermore, Compliance as a Service (CaaS) provides comprehensive solutions to meet regulatory requirements, offering continuous monitoring and audit preparation support - especially beneficial for highly regulated industries. This holistic approach to cybersecurity not only enhances protection but also simplifies compliance efforts, enabling organizations to navigate complex regulatory landscapes with greater ease.
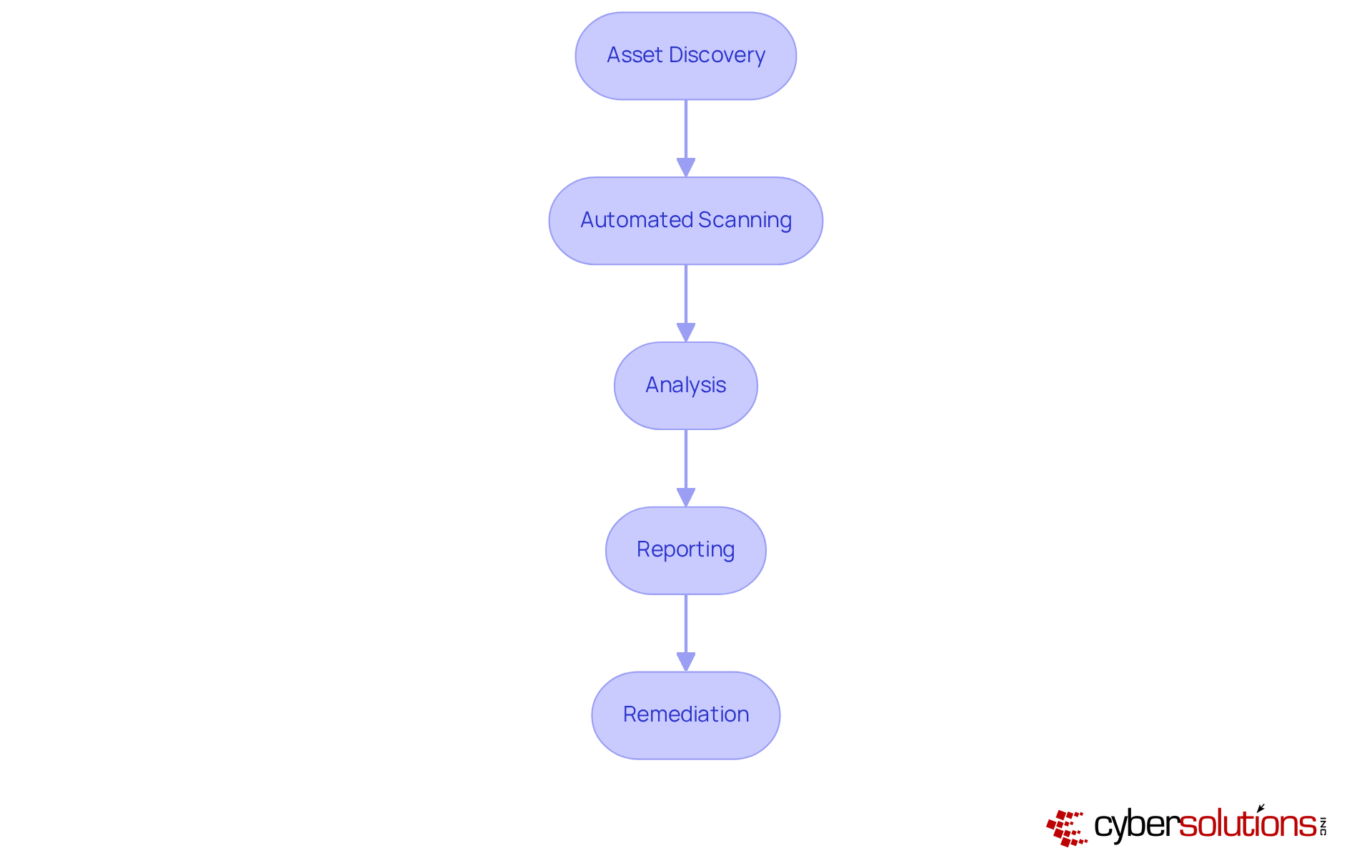
Vulnerability scanning is a critical process for maintaining a secure IT environment, and it encompasses several essential steps:
Asset Discovery: This initial step is all about identifying every device and application within the network that needs scanning. Efficient asset identification lays the groundwork for a robust risk management strategy. Organizations that prioritize asset discovery significantly enhance their security posture, ensuring that no critical assets slip through the cracks. With 74% of companies reporting an uptick in insider threats, the importance of solid asset discovery processes has never been clearer.
Automated tools are used in the process of how does vulnerability scanning work, examining the identified assets for known vulnerabilities. This includes checking for outdated software, misconfigurations, and other security flaws. By 2025, organizations are expected to average around 30 minutes for a security assessment, thanks to advancements in assessment technology and methodologies. Gartner research predicts that the cybersecurity market will soar to $212 billion by year-end, underscoring the growing significance of effective risk management.
Analysis: Once scanning is complete, the results are evaluated to gauge the severity of identified weaknesses based on their potential impact and exploitability. Understanding how does vulnerability scanning work is crucial for effectively prioritizing remediation efforts.
Reporting: Detailed reports are generated, outlining the identified weaknesses, their associated risk levels, and recommended remediation steps. These reports serve as vital communication tools for stakeholders, ensuring decision-makers are well-informed about the organization's security status.
Remediation: The final step involves applying corrections or mitigations for the identified weaknesses, followed by re-scanning to confirm how does vulnerability scanning work in resolving the issues. This cyclical process is essential for maintaining a strong security stance, as ongoing monitoring and remediation help organizations stay ahead of evolving threats.
Integrating asset discovery into risk assessment processes not only boosts the effectiveness of security measures but also aligns with best practices recommended by cybersecurity experts. Organizations that weave thorough asset discovery into their risk management strategies are better equipped to proactively identify and address potential threats. As Soros pointed out, cost-effective, user-friendly solutions are a top priority for leaders when selecting new partners, highlighting the pressing need for efficient vulnerability management.
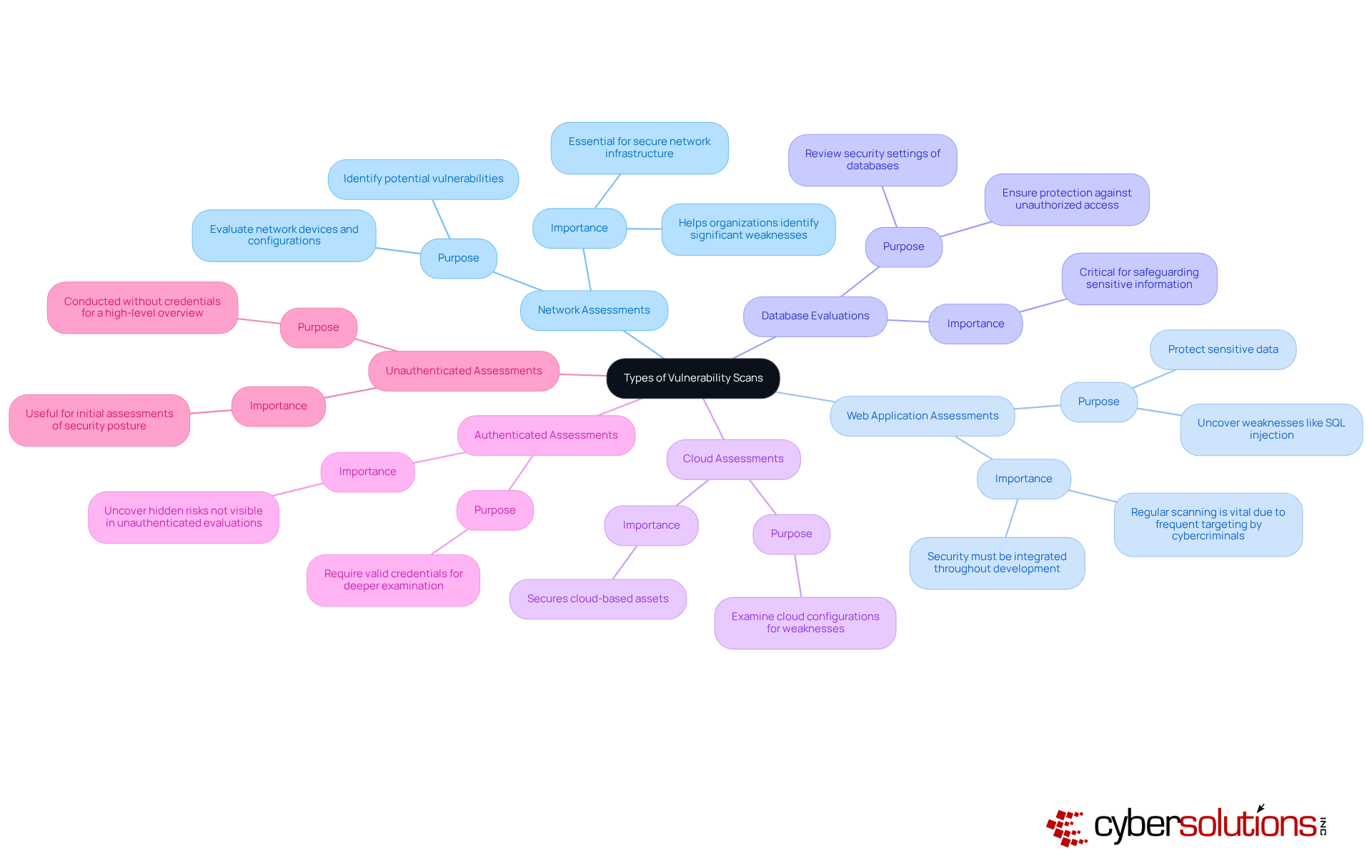
In today’s cybersecurity landscape, it is crucial for organizations to understand how does vulnerability scanning work to effectively protect their assets. These scans can be categorized into several types, each tailored to address specific security needs:
Network Assessments: These evaluations scrutinize the security of network devices and configurations, pinpointing potential vulnerabilities that attackers could exploit. They are essential for maintaining a secure network infrastructure. As Mohammed Khalil notes, organizations that swiftly identify their most significant weaknesses are better positioned to safeguard their assets.
Web Application Assessments: Focused on web applications, these evaluations uncover weaknesses such as SQL injection and cross-site scripting. Given that cybercriminals frequently target web applications, regular scanning is vital for protecting sensitive data. Henri Alfonso emphasizes that security must be integrated at every stage of development to prevent last-minute fixes.
Database Evaluations: These assessments review the security settings and configurations of databases, ensuring that sensitive information is protected against unauthorized access and vulnerabilities.
Cloud Assessments: With the growing reliance on cloud environments, these evaluations examine cloud configurations for misconfigurations and weaknesses, helping to secure cloud-based assets.
Authenticated Assessments: By requiring valid credentials, authenticated assessments provide a deeper examination of vulnerabilities that may not be visible in unauthenticated evaluations. This thorough approach is essential for uncovering hidden risks within a company’s systems.
Unauthenticated Assessments: Conducted without credentials, these evaluations offer a high-level overview of potential weaknesses, making them useful for initial assessments of a business’s security posture.
Looking ahead to 2025, a significant percentage of organizations are expected to employ a combination of these scans to bolster their cybersecurity strategies, particularly in understanding how does vulnerability scanning work to identify and mitigate risks across various environments. Optimal methods for assessing network vulnerabilities include regular evaluations, prioritizing critical issues, and integrating results into the overall security management framework. A study highlights that the average cost of a financial breach is approximately $5.9 million, underscoring the importance of proactive risk management.
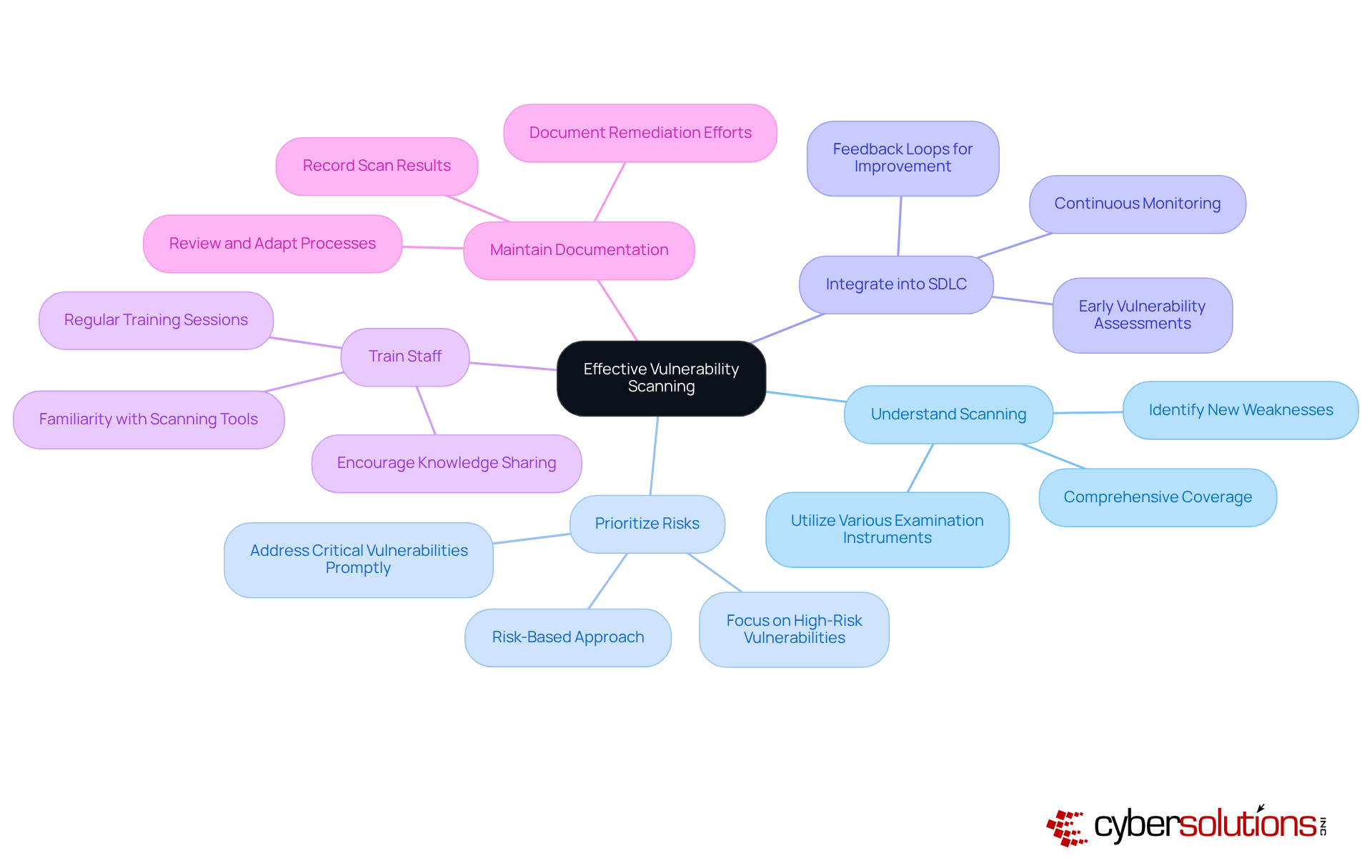
To ensure effective vulnerability scanning, organizations must understand how vulnerability scanning works and recognize the critical importance of cybersecurity in today’s landscape. Regular scanning is essential; knowing how vulnerability scanning works allows for the identification of new weaknesses as they arise. Next, it’s crucial to Prioritize Risks - adopting a risk-based approach helps organizations focus on vulnerabilities that could have the most significant impact.
Integrating analysis into the Software Development Lifecycle (SDLC) is another vital practice. By incorporating vulnerability assessments early in the development process, organizations can learn how vulnerability scanning works to catch vulnerabilities before they become problematic. Additionally, it’s important to understand how vulnerability scanning works; utilizing various examination instruments ensures comprehensive coverage of the environment and minimizes blind spots.
Moreover, organizations should Train Staff effectively. Understanding how vulnerability scanning works is essential for ensuring that IT personnel are well-versed in the latest scanning tools and techniques, which maximizes the effectiveness of vulnerability management efforts. Finally, maintaining thorough documentation of scan results and remediation efforts is key. Regularly reviewing these processes allows organizations to adapt to evolving threats.
By following these best practices, organizations can significantly enhance their cybersecurity resilience.
Understanding the mechanisms of vulnerability scanning is crucial for C-suite leaders who want to strengthen their organizations against cyber threats. In today’s landscape, where data breaches are alarmingly frequent, this automated process not only identifies security weaknesses but also plays a vital role in ensuring compliance and protecting sensitive information. Executives must prioritize cybersecurity measures, making vulnerability scanning an essential component of their organizational strategy.
This article explores the key processes involved in vulnerability scanning, such as:
It highlights the necessity of integrating these practices within the software development lifecycle and adopting a risk-based approach to prioritize vulnerabilities effectively. Furthermore, the discussion on various types of scans - ranging from network assessments to authenticated evaluations - underscores the need for a customized strategy that addresses specific security concerns within an organization.
Ultimately, the importance of vulnerability scanning goes beyond mere compliance; it represents a critical investment in an organization’s resilience against cyber threats. By embracing effective scanning strategies and fostering a culture of cybersecurity awareness, businesses can not only safeguard their assets but also improve their overall financial health. C-suite leaders are urged to champion these initiatives, ensuring their organizations are proactive rather than reactive in the face of evolving cybersecurity challenges.
What is vulnerability scanning?
Vulnerability scanning is an automated process designed to identify security weaknesses across software, systems, and networks. It helps organizations discover vulnerabilities before they can be exploited.
Why is vulnerability scanning important in healthcare?
Vulnerability scanning is crucial in healthcare due to the significant rise in data breaches, with 809 reported in 2023. It helps organizations safeguard sensitive information, ensure compliance with industry standards, and maintain stakeholder confidence.
What are the financial implications of neglecting risk management?
The cost of a data breach can exceed $4.5 million. Additionally, 84% of companies face significant risks, with many of these risks potentially addressable through simple software updates, highlighting the financial repercussions of neglecting risk management.
How can routine security assessments benefit organizations?
Conducting routine security assessments can significantly reduce operational risks and bolster financial stability, helping organizations avoid incidents that may lead to severe reputational damage.
What is application allowlisting, and how does it enhance cybersecurity?
Application allowlisting is a cybersecurity method that actively blocks malware and unauthorized programs by permitting only authorized applications to run. This approach minimizes vulnerabilities and shrinks the attack surface, helping to thwart ransomware and other malicious software.
Why should C-suite executives understand vulnerability scanning and application allowlisting?
C-suite executives should understand these concepts because they directly impact the organization’s risk management and financial health, influencing overall cybersecurity strategy and compliance efforts.
What is Compliance as a Service (CaaS)?
Compliance as a Service (CaaS) provides comprehensive solutions to meet regulatory requirements, offering continuous monitoring and audit preparation support, particularly beneficial for industries with strict regulations.
How does a holistic approach to cybersecurity benefit organizations?
A holistic approach to cybersecurity enhances protection and simplifies compliance efforts, enabling organizations to navigate complex regulatory landscapes more effectively.