In today’s competitive business landscape, integrating managed IT solutions is not just beneficial; it’s essential for maintaining operational efficiency and security. Organizations in Maine are navigating a complex technological environment, facing a multitude of options aimed at enhancing their cybersecurity posture and streamlining IT management. But with so many solutions available, how can business leaders pinpoint the most effective services that truly align with their unique needs?
This article delves into ten essential managed IT solutions that not only safeguard assets but also empower organizations to thrive in an increasingly digital world. By understanding the current landscape of cybersecurity threats and the implications for their operations, leaders can make informed decisions that bolster their defenses and drive success.
In today's digital landscape, the importance of cybersecurity cannot be overstated. Cyber Solutions Inc. stands at the forefront, providing a comprehensive range of managed IT solutions in Maine and cybersecurity solutions designed to protect businesses from emerging threats. With offerings such as:
they ensure that organizations can focus on their core operations without compromising their security.
The unique challenges faced by businesses today require a robust defense strategy. Cyber Solutions leverages advanced technologies and expert knowledge to create tailored solutions that enhance ROI, boost efficiency, and minimize costly downtime. This makes them an ideal partner for small to medium enterprises in Maine that are navigating the complexities of managed IT solutions Maine.
By choosing Cyber Solutions, organizations not only safeguard their assets but also position themselves for growth in a secure environment. Are you ready to elevate your cybersecurity posture? Let Cyber Solutions help you build a resilient defense against digital threats.
Acme IT Services stands out in the realm of IT support, delivering customized solutions that meet the unique needs of various industries. In today’s fast-paced environment, businesses require specific strategies to enhance operational efficiency and bolster security. Acme’s comprehensive suite featuring managed IT solutions Maine, cloud solutions, and advanced cybersecurity measures positions them as a versatile partner for organizations throughout Maine.
The importance of tailored IT solutions cannot be overstated. Industry experts assert that effective IT support must align with the specific needs of businesses. As one expert noted, 'Quality in a product is not what you put into it; it's what the client or customer derives from it.' This perspective highlights the necessity for IT solutions to be adaptable and responsive to the evolving demands of different sectors.
Current trends indicate a growing recognition of the value of customized IT solutions. Many organizations are prioritizing options that not only address immediate challenges but also support long-term strategic goals. For example, companies that leverage tailored IT support have reported significant gains in productivity and operational resilience, underscoring the value of investing in bespoke IT solutions.
In today's fast-paced digital landscape, organizations cannot afford interruptions. TechGuard Solutions offers managed IT solutions in Maine, providing powerful cloud services and bolstered by 24/7 IT assistance to ensure seamless operations. Their managed IT solutions in Maine are not just scalable and flexible; they empower organizations to swiftly adapt to evolving demands while implementing stringent security measures.
With continuous support, TechGuard addresses issues promptly, significantly reducing downtime and enhancing overall operational efficiency. This proactive strategy safeguards operational continuity and positions organizations to excel in a competitive environment. Did you know that 89% of customers prefer companies that provide round-the-clock IT support? This statistic underscores the critical nature of reliable IT services in maintaining a competitive edge.
In today's digital age, cybersecurity is not just an option; it's a necessity, especially in healthcare. SecureNet provides advanced endpoint protection and cybersecurity solutions that are essential for shielding organizations from a multitude of cyber threats. With comprehensive services that include real-time monitoring, advanced threat detection, and swift incident response, SecureNet empowers entities to promptly address vulnerabilities and safeguard sensitive data.
Consider the case of a healthcare provider that utilized SecureNet's solutions. During a ransomware attack, they reported a significant reduction in incident response time, showcasing the effectiveness of proactive measures. This example underscores the critical need for organizations to enhance their security stance, particularly as studies indicate that 90% of cyberattacks originate from compromised endpoint devices.
As the cybersecurity landscape continues to evolve, the integration of real-time monitoring and threat detection becomes increasingly crucial. Organizations must implement robust cybersecurity strategies that not only protect their assets but also enhance operational resilience. By adopting SecureNet's offerings, healthcare organizations can effectively navigate the complexities of cyber threats, ensuring that they remain one step ahead in the fight against cybercrime.
ComplianceTech stands at the forefront of guiding organizations through the complex landscape of regulatory compliance. In an era where adherence to industry standards is non-negotiable, their innovative solutions simplify compliance processes, enabling entities to meet critical regulations like HIPAA, PCI-DSS, and GDPR without straining their resources. By leveraging ComplianceTech's expertise, organizations can focus on growth while ensuring they remain compliant.
Current trends reveal a significant shift towards automation and streamlined processes in compliance solutions. Organizations are increasingly adopting technology-driven approaches to manage compliance efficiently. Have you considered how simplifying compliance can not only alleviate operational burdens but also enhance overall organizational agility? Industry specialists emphasize that this shift is not just beneficial; it’s essential for staying competitive.
Successful compliance examples are particularly evident in sectors like healthcare, where adherence to HIPAA is crucial. Companies that have implemented robust compliance frameworks report improved patient trust and reduced legal risks. Similarly, enterprises in the financial sector demonstrate that effective PCI-DSS compliance can lead to increased customer trust and lower transaction costs. Isn’t it time to evaluate how your organization measures up?
In the realm of data protection, GDPR compliance has emerged as a cornerstone for organizations engaging with the EU market. Companies prioritizing GDPR adherence not only mitigate risks associated with data breaches but also position themselves as trustworthy entities in the eyes of consumers. How does your organization ensure compliance in this critical area?
As the compliance landscape continues to evolve, the importance of effective compliance solutions cannot be overstated. Organizations adopting these solutions are better equipped to navigate regulatory challenges while concentrating on their primary goals. Are you ready to take the next step in enhancing your compliance strategy?
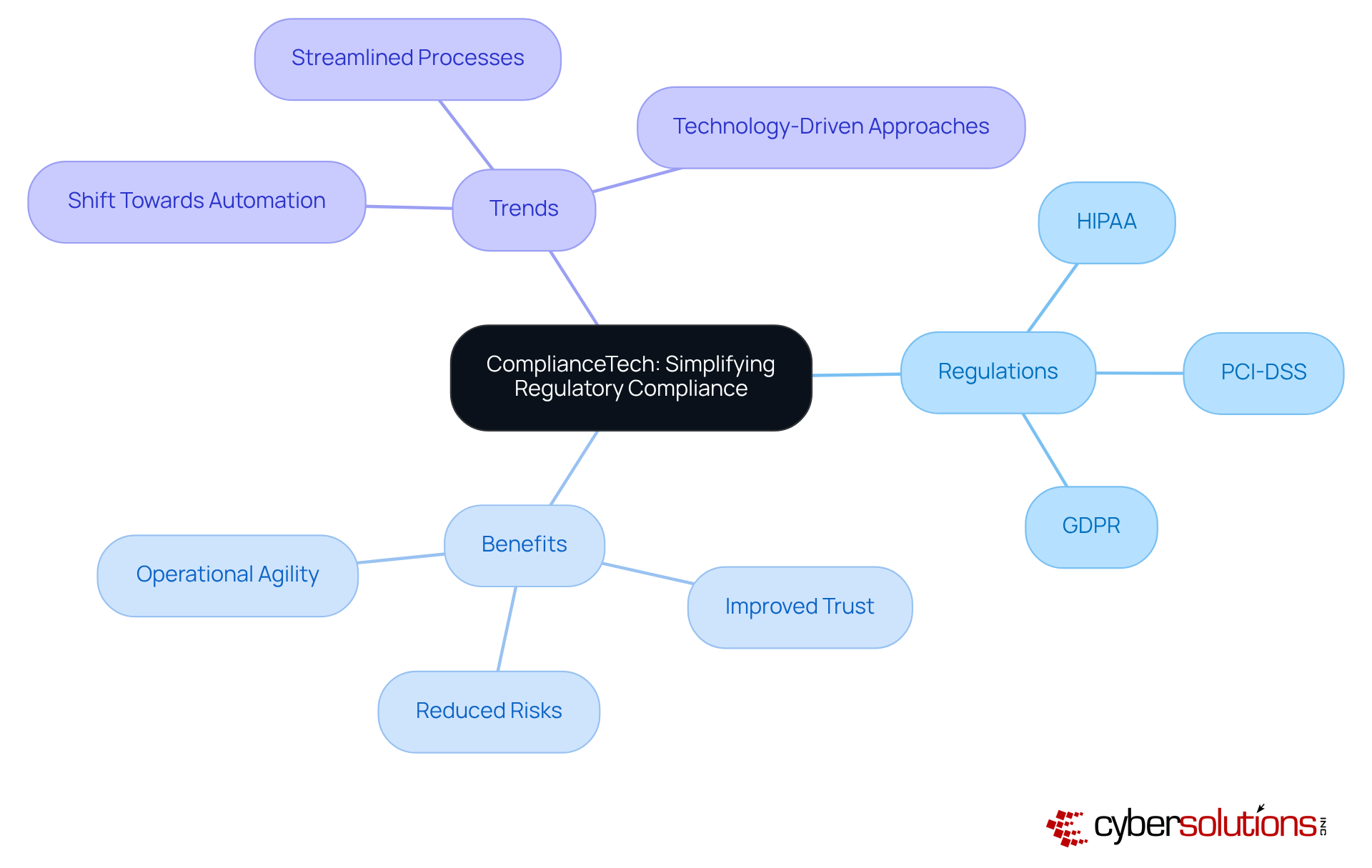
Disaster Recovery Pros stands at the forefront of solutions designed to ensure continuity and resilience against unexpected disruptions. In today’s fast-paced environment, organizations must prioritize essential services like data backup, comprehensive recovery planning, and thorough risk assessments. These offerings empower businesses to recover swiftly from incidents, significantly reducing downtime and enhancing operational stability.
As we look ahead to 2025, the latest trends in continuity solutions underscore the necessity of integrating cloud-based disaster recovery options. These innovations can cut recovery times by up to 70%, positioning them as a vital component of modern strategies. Companies equipped with a tested disaster recovery plan are 2.5 times more likely to recover quickly from a disaster compared to those without. This statistic alone highlights the critical importance of proactive risk assessment in recovery planning.
Connor Toohey, a Product Support Engineer, aptly states, "A robust disaster recovery strategy isn’t a luxury; it’s a fundamental continuity requirement in the digital era." By partnering with Disaster Recovery Pros, organizations not only safeguard their operations but also enhance their performance during crises. This collaboration ensures they remain competitive and resilient in an increasingly unpredictable landscape.
In today's digital age, the significance of cybersecurity cannot be overstated. Organizations face an ever-evolving landscape of cyber threats that demand proactive measures. SafeGuard IT stands out by providing managed IT solutions in Maine that offer protective services designed to keep companies ahead of potential risks. Their comprehensive suite of services includes continuous monitoring, threat intelligence, and incident response planning - essential components for effectively mitigating risks in this complex environment.
Threat intelligence plays a crucial role in enabling businesses to anticipate and counteract potential attacks before they occur. Continuous monitoring delivers real-time insights into network activity, facilitating swift detection and remediation of vulnerabilities. As cybersecurity expert Mohammed Khalil aptly notes, "The entities that perform best against cyber threats are those that internalize these lessons and act on them." This proactive approach not only fortifies defenses but also cultivates a culture of awareness within the organization.
Current trends reveal a growing recognition of the value of threat intelligence among businesses, particularly in enhancing operational resilience. Organizations that implement continuous monitoring report significant improvements in incident response times and overall protection effectiveness. For instance, entities utilizing these resources have experienced a marked decline in the frequency and impact of cyber incidents, underscoring the tangible benefits of investing in proactive protective measures.
In conclusion, SafeGuard IT's proactive managed IT solutions in Maine represent more than just a defensive strategy; they embody a strategic advantage that empowers organizations to navigate the complexities of modern cybersecurity threats with confidence.
Strategic IT planning is essential for organizations seeking to boost growth and operational efficiency. Insight IT Consulting stands out by providing managed IT solutions in Maine that tailor technology initiatives to align with organizational objectives. Their comprehensive services encompass IT evaluations, technology strategy, and implementation support, empowering organizations to maximize their IT investments effectively.
Consider the successful examples of technology planning that underscore its significant impact. Organizations that prioritize the alignment of technology with their strategic goals often witness remarkable enhancements in operational efficiency and customer satisfaction. Industry experts emphasize that aligning technology with organizational goals is not merely beneficial; it is crucial for sustainable growth.
Current trends in strategic IT planning spotlight the integration of emerging technologies, such as AI and cloud solutions, to foster innovation and efficiency. With digital transformation initiatives now a priority for 87% of executives, the necessity for effective technology planning has never been more pressing. By harnessing the expertise of Insight IT Consulting and utilizing managed IT solutions in Maine, organizations can adeptly navigate these complexities and position themselves for enduring success.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in the healthcare sector. With the rise in cyber threats, healthcare organizations face unique challenges that demand immediate attention. Innovate IT is at the forefront of driving digital transformation, offering innovative technology solutions that include cloud migration, automation, and data analytics. These services empower organizations to enhance operational efficiency and improve customer engagement, crucial in a field where trust and security are paramount.
Moreover, Cyber Solutions provides tailored IT services designed to meet the specific security and compliance needs of various industries, including healthcare, finance, manufacturing, and government. By integrating advanced tools such as:
organizations can effectively safeguard their operations against evolving cyber threats. This proactive approach not only protects sensitive data but also ensures compliance with industry regulations, which is vital for maintaining credibility and trust.
By partnering with Innovate IT and leveraging the expertise of Cyber Solutions, organizations can stay ahead of the competition and adapt to changing market demands. The combination of innovative technology and robust cybersecurity measures positions businesses to thrive in an increasingly complex environment. Are you ready to take the necessary steps to protect your organization and enhance your operational capabilities? The time to act is now.
In today's rapidly evolving technological landscape, the importance of comprehensive IT assessments cannot be overstated. Assessment Solutions offers in-depth evaluations that empower businesses to gain critical insights into their technology infrastructure. Their services - ranging from audits to performance evaluations and compliance checks - are essential for identifying vulnerabilities and optimizing IT strategies.
Recent trends indicate a growing recognition among organizations regarding the significance of routine assessments. In fact, 84% of IT professionals believe that such evaluations will be a major focus in the coming years. These audits not only bolster security but also enhance operational efficiency, ensuring that technology investments align with organizational goals.
Consider this: companies that implement thorough performance evaluations often report a significant reduction in operational disruptions and an increase in overall productivity. By leveraging Assessment Solutions, businesses can proactively address potential risks and strengthen their resilience against evolving cyber threats. This proactive approach ultimately drives success in an increasingly competitive landscape.
In today's intricate digital landscape, the importance of managed IT solutions for businesses in Maine is paramount. These services not only boost operational efficiency but also deliver essential security measures to shield organizations from emerging cyber threats. By harnessing tailored IT support, comprehensive cybersecurity services, and proactive disaster recovery strategies, businesses can fortify their resilience and maintain a competitive edge in their industries.
As we delve into the realm of managed IT solutions, key players like Cyber Solutions, Acme IT Services, and TechGuard Solutions showcase the diverse offerings available to organizations. From advanced endpoint protection to streamlined compliance processes, each service is vital in strengthening business infrastructure. The insights gathered underscore the necessity for businesses to invest in customized IT solutions that cater to their unique needs, ultimately driving growth and operational success.
As the digital landscape evolves, organizations must take action: prioritize robust managed IT solutions that not only protect assets but also foster growth. Embracing these services is not merely a strategic advantage; it is a fundamental requirement for thriving in today's competitive environment. Assess your current IT strategies and consider how adopting innovative solutions can enhance resilience and operational capabilities. The time to act is now-secure the future of your business with the right managed IT solutions.
What services does Cyber Solutions Inc. provide?
Cyber Solutions Inc. offers a comprehensive range of managed IT solutions and cybersecurity services, including 24/7 help desk assistance, endpoint protection, email safety, firewalls, backup and disaster recovery, co-managed IT support, and managed protection solutions.
Who can benefit from Cyber Solutions' services?
Small to medium enterprises in Maine can benefit from Cyber Solutions' services, as they help organizations focus on their core operations while ensuring robust security against digital threats.
What are the advantages of choosing Cyber Solutions?
Choosing Cyber Solutions allows organizations to safeguard their assets, enhance return on investment (ROI), boost efficiency, minimize costly downtime, and position themselves for growth in a secure environment.
What distinguishes Acme IT Services from other IT support providers?
Acme IT Services stands out by delivering customized IT solutions tailored to the unique needs of various industries, enhancing operational efficiency and security.
Why are tailored IT solutions important for businesses?
Tailored IT solutions are important because they align with the specific needs of businesses, addressing immediate challenges while supporting long-term strategic goals, thereby improving productivity and operational resilience.
What services does TechGuard Solutions offer?
TechGuard Solutions offers managed IT solutions in Maine, including powerful cloud services and 24/7 IT support to ensure seamless operations for organizations.
How does TechGuard Solutions enhance operational efficiency?
TechGuard Solutions enhances operational efficiency by providing continuous IT support that addresses issues promptly, significantly reducing downtime and safeguarding operational continuity.
What is the significance of 24/7 IT support according to customer preferences?
The significance of 24/7 IT support is highlighted by the statistic that 89% of customers prefer companies that provide round-the-clock IT support, indicating its critical nature in maintaining a competitive edge.