
In today's world, where digital threats are more sophisticated than ever, the importance of cyber risk assessments is paramount, especially for organizations that manage sensitive data. These assessments are essential for pinpointing vulnerabilities and prioritizing cybersecurity initiatives, ultimately protecting critical information systems. Yet, a pressing question arises: how can organizations ensure their cyber risk assessments not only comply with standards but also adapt to the constantly changing landscape of cyber threats?
Exploring best practices in this area reveals strategies that not only bolster security but also cultivate a culture of continuous improvement in cybersecurity resilience. By understanding the current cybersecurity threat landscape, healthcare organizations can better navigate the unique challenges they face. Cyber Solutions can provide the necessary tools and insights to address these challenges effectively, ensuring that organizations remain vigilant and prepared.
In today's digital landscape, cybersecurity is not just an option; it's a necessity for healthcare organizations. Cyber risk assessments are crucial for identifying weaknesses and potential threats that could jeopardize sensitive information systems. These cyber risk assessments provide a structured framework for understanding the risks associated with digital operations, which enables organizations to effectively prioritize their cybersecurity initiatives.
Regular evaluations through cyber risk assessments ensure compliance with industry regulations and significantly bolster overall security posture. For example, a healthcare entity that conducts routine cybersecurity assessments can enhance the protection of patient information, thereby preventing costly breaches and preserving client trust. Moreover, cyber risk assessments align cybersecurity expenditures with actual threats, ensuring that resources are allocated efficiently.
As cyber threats evolve, organizations that prioritize cyber risk assessments can proactively address emerging challenges, safeguarding their operations and confidential information. The growing trend towards cybersecurity-as-a-service underscores the importance of cyber risk assessments, providing companies with flexible, outsourced solutions to manage their cyber threats on a pay-as-you-go basis. Are you ready to take the necessary steps to protect your organization?
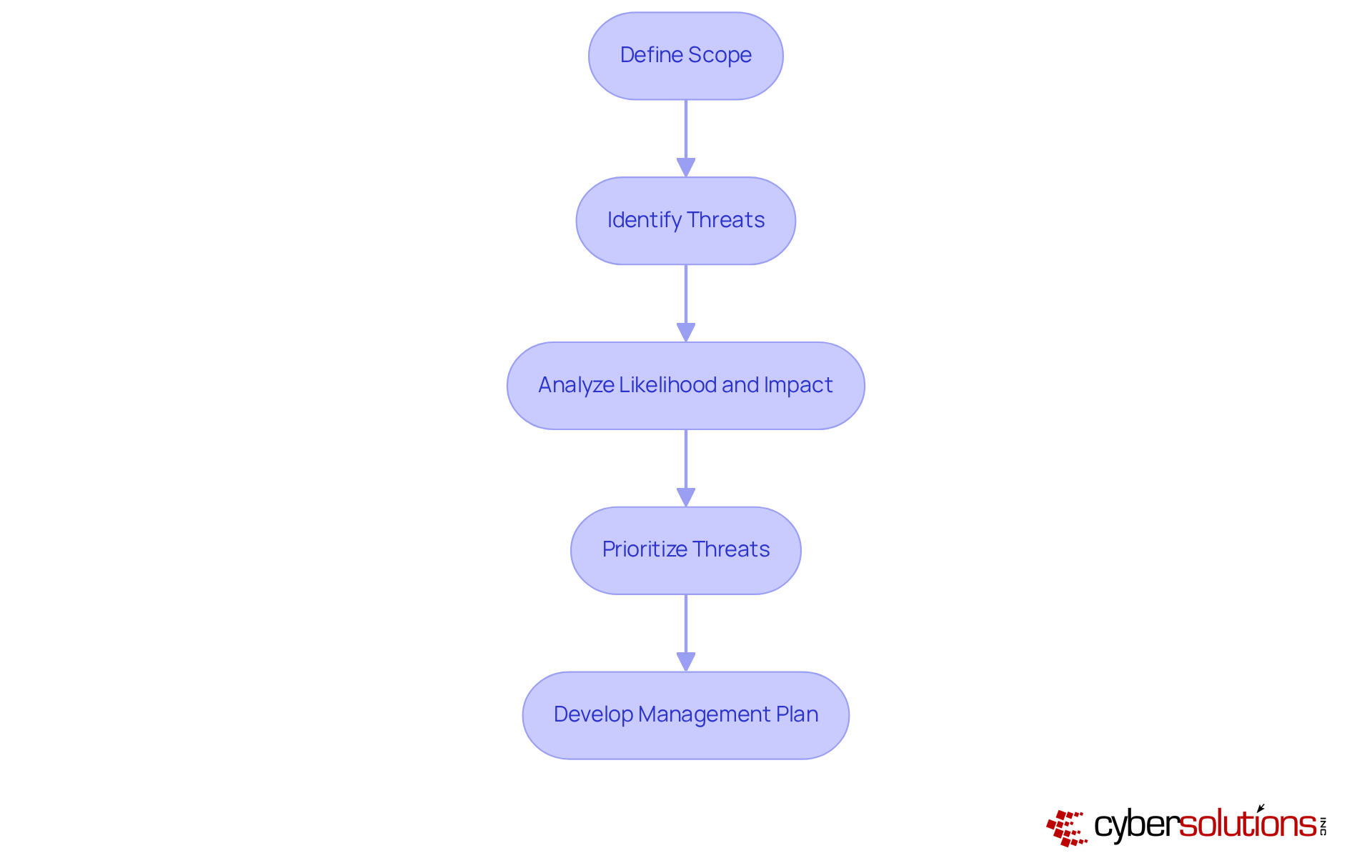
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations handling sensitive information. To effectively evaluate cyber threats, entities must adopt a structured framework for cyber risk assessments that encompasses essential steps:
For instance, a financial organization may prioritize threats related to data breaches, given the sensitive nature of the information it manages. By implementing this structured approach, companies can effectively address their cybersecurity needs through cyber risk assessments, ensuring a robust defense against evolving threats. Statistics reveal that entities employing systematic cyber risk assessments experience a significant reduction in the likelihood of successful attacks, underscoring the effectiveness of this methodology in enhancing overall security posture.
Moreover, organizations should consider the NIST SP 800-30 methodology as a guiding framework for their cyber risk assessments, ensuring alignment with established best practices. A layered strategy - including endpoint isolation, malware removal, and user training - can further bolster recovery efforts and foster strong partnerships with security providers. Continuous oversight of hazards is crucial to adapt to the evolving threat environment and maintain an efficient management strategy.
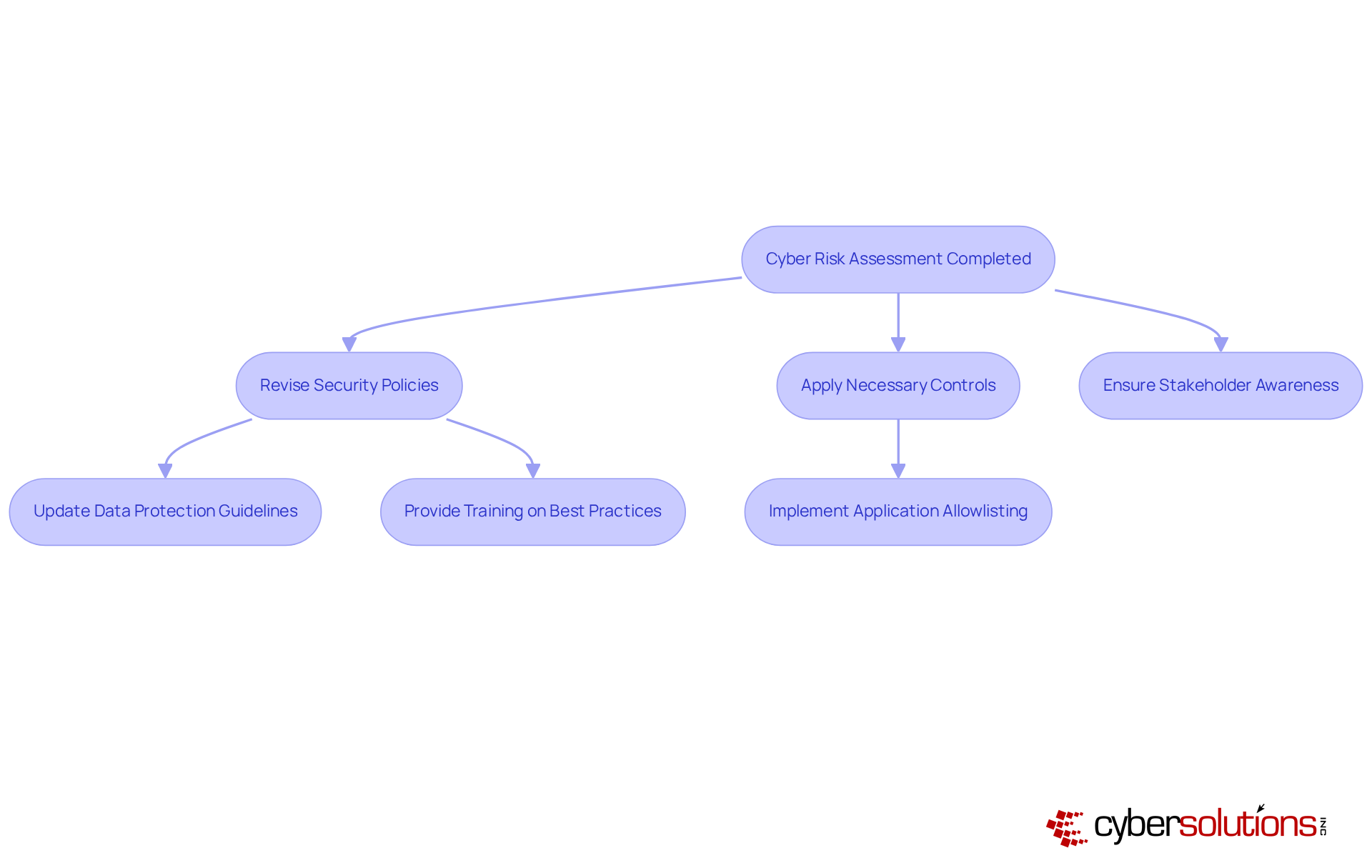
Cybersecurity is not just a technical issue; it’s a critical component of organizational integrity, especially in healthcare. Once cyber risk assessments are completed, it’s essential to weave those findings into the entity's cybersecurity strategy and compliance initiatives. This involves:
For instance, if an evaluation reveals weaknesses in data handling procedures, the organization must update its data protection guidelines and provide training to staff on best practices. Additionally, implementing application allowlisting can significantly bolster security by proactively preventing unauthorized software from executing. This approach reduces the attack surface and minimizes vulnerabilities.
Statistics reveal that 83% of entities faced over one data breach in 2022, underscoring the urgency of revising security policies post-evaluation. Furthermore, aligning these findings with compliance requirements, such as HIPAA or GDPR, not only protects assets but also mitigates potential legal repercussions. As specialists like Jason White emphasize, "cyber threats remain a major issue for companies across all sectors." This highlights the pressing need for entities to integrate cyber risk assessments and threat evaluation results into their compliance frameworks, ensuring they are not just reactive but proactive in their cybersecurity posture.
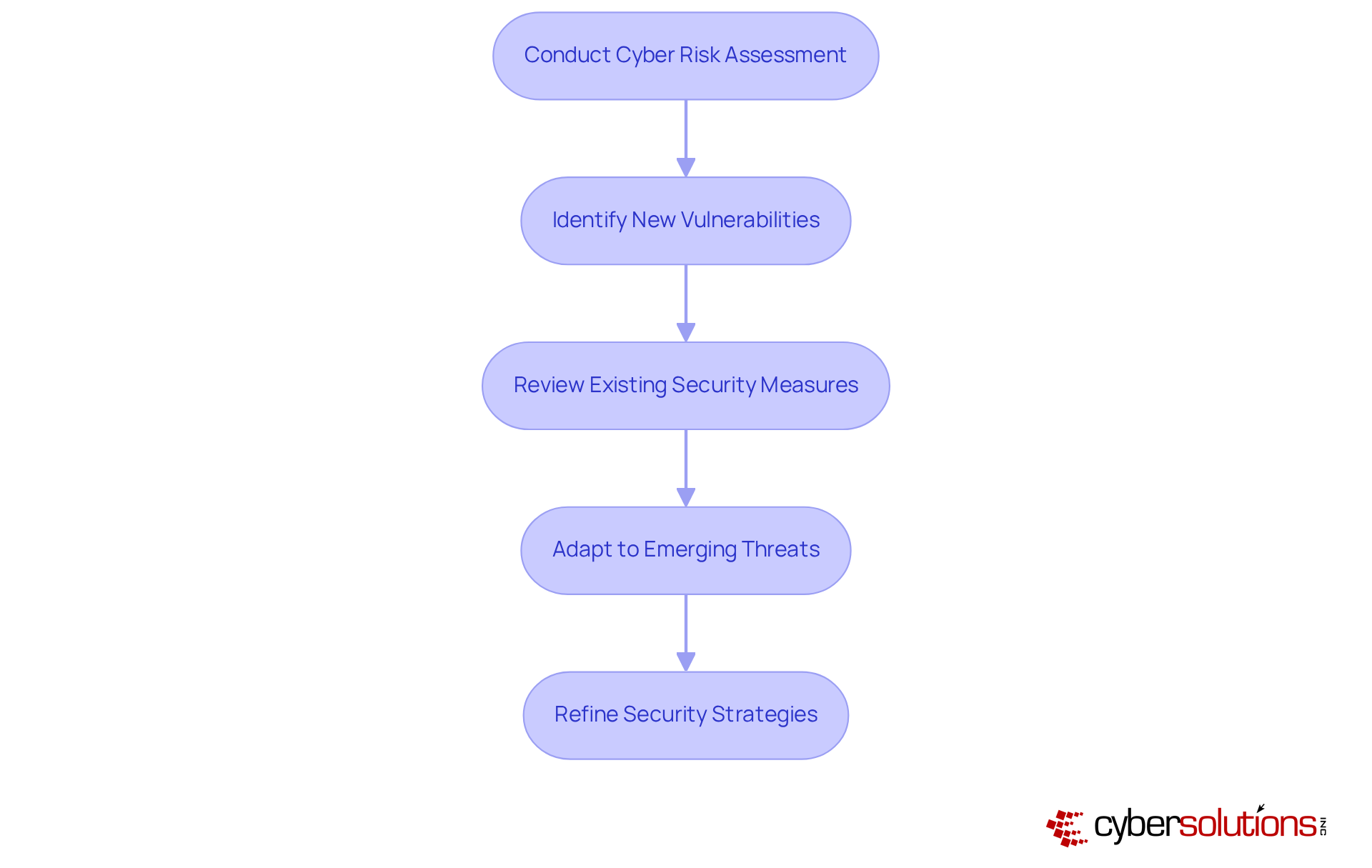
To effectively manage cyber risks, organizations must prioritize cyber risk assessments as part of their routine security evaluations. Ideally, these should occur annually or more frequently, depending on operational needs and the evolving threat landscape. Such evaluations should encompass not only the identification of new vulnerabilities but also a thorough review of the effectiveness of existing security measures.
Consider a manufacturing firm that regularly assesses its digital security posture. This proactive approach allows it to swiftly adapt to emerging threats, such as the alarming 78% increase in ransomware attacks targeting industrial control systems in 2023. By leveraging insights from cyber risk assessments, organizations can continuously refine their security strategies, ensuring resilience against increasingly sophisticated threats.
This proactive stance not only mitigates risks but also enhances the overall security posture, fostering a culture of continuous improvement in cybersecurity practices. In a world where cyber threats are ever-present, can your organization afford to overlook the importance of regular security evaluations?
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. With sensitive patient data at stake, organizations face unique challenges that demand immediate attention. Cyber risk assessments are not just a best practice; they are essential for identifying vulnerabilities and potential threats that could compromise critical information systems.
By adopting a structured approach to these evaluations, healthcare organizations can prioritize their cybersecurity efforts effectively. This ensures that resources are allocated where they are needed most, while also maintaining compliance with industry regulations. Regular assessments keep organizations informed of evolving threats and foster continuous improvement in security measures.
Statistics reveal a pressing need for these practices. Organizations that engage in routine evaluations significantly reduce their risk of data breaches and enhance their overall security posture. Isn't it time to ask: how prepared is your organization to face the ever-changing threat landscape?
The call to action is clear: organizations must prioritize cyber risk assessments as a fundamental part of their cybersecurity strategy. By doing so, they not only protect sensitive information but also cultivate a proactive culture that adapts to emerging threats. The future of cybersecurity hinges on a commitment to regular assessments and the integration of their findings into comprehensive security frameworks, ensuring resilience against the sophisticated challenges that lie ahead.
Why are cyber risk assessments important for healthcare organizations?
Cyber risk assessments are crucial for identifying weaknesses and potential threats to sensitive information systems, enabling organizations to prioritize cybersecurity initiatives effectively.
How do cyber risk assessments benefit compliance and security?
Regular evaluations through cyber risk assessments ensure compliance with industry regulations and significantly enhance the overall security posture of an organization.
What is an example of how cyber risk assessments can protect patient information?
A healthcare entity that conducts routine cybersecurity assessments can enhance the protection of patient information, preventing costly breaches and preserving client trust.
How do cyber risk assessments help in resource allocation for cybersecurity?
Cyber risk assessments align cybersecurity expenditures with actual threats, ensuring that resources are allocated efficiently to address the most pressing risks.
How do cyber risk assessments assist organizations in addressing emerging cyber threats?
Organizations that prioritize cyber risk assessments can proactively address evolving challenges, safeguarding their operations and confidential information.
What is the trend towards cybersecurity-as-a-service, and how does it relate to cyber risk assessments?
The trend towards cybersecurity-as-a-service highlights the importance of cyber risk assessments by providing companies with flexible, outsourced solutions to manage their cyber threats on a pay-as-you-go basis.