
Outsourced IT support has become an essential strategy for businesses navigating the complexities of modern technology. By leveraging external expertise, organizations can enhance operational efficiency while significantly cutting costs associated with IT management.
However, as companies seek these advantages, they must confront critical questions about the true value of outsourcing. How can they effectively balance the benefits of reduced expenses with the potential risks of dependency and loss of control?
This article explores the intricacies of outsourced IT support costs, examining various pricing models, benefits, and challenges that strategic leaders must consider to make informed decisions in an ever-evolving digital landscape.
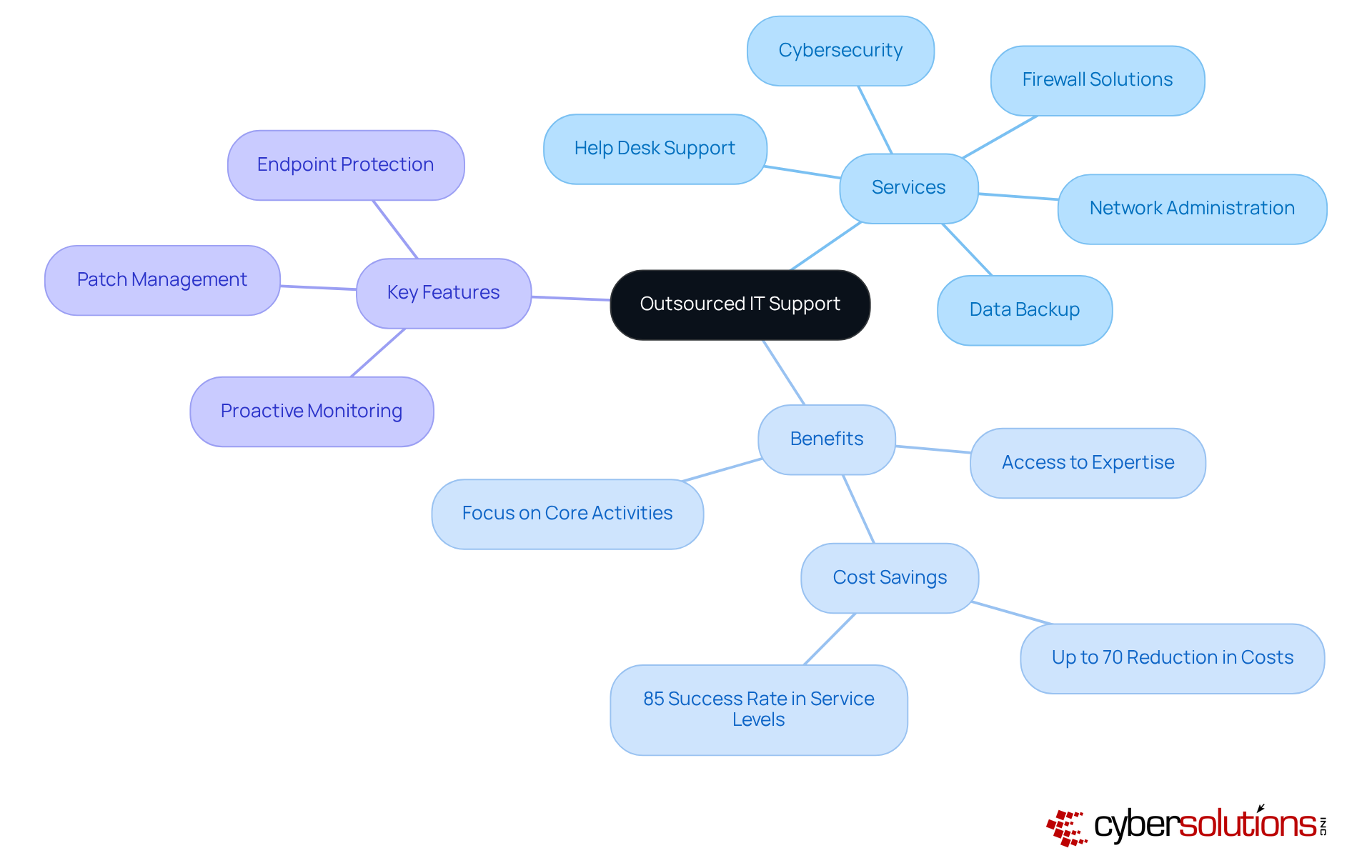
Outsourced IT assistance is essential for modern businesses, as it involves engaging external providers to meet critical IT needs. This includes services such as:
The significance of this approach cannot be overstated. It grants access to specialized expertise that may not exist internally, allowing organizations to stay ahead of technological advancements. In fact, companies utilizing outsourced IT assistance report an impressive 85% success rate in achieving service levels that match or exceed those of in-house teams.
Moreover, outsourcing IT functions can lead to substantial savings on outsourced IT support costs. By avoiding the expenses associated with salaries, benefits, and training for a full-time internal team, businesses can reduce their outsourced IT support costs by up to 70%. This financial efficiency is particularly advantageous in an environment where operational budgets are constantly scrutinized. Notably, 59-70% of companies cite the reduction of outsourced IT support costs as a primary motivation for outsourcing.
Additionally, outsourced IT assistance enables organizations to concentrate on their core business activities. By entrusting IT management to external experts, companies can redirect their resources toward innovation and strategic initiatives. This shift not only boosts operational efficiency but also enhances responsiveness to market demands. Consequently, organizations can adapt more swiftly to technological changes and evolving customer expectations, fostering growth and competitiveness in their respective industries.
Key features of outsourced IT assistance include:
All of which collectively enhance security and operational resilience. In summary, the value of outsourced IT support costs lies in its ability to provide specialized knowledge, reduce overall expenses, and allow businesses to focus on their strategic objectives. This makes it an invaluable asset in today’s fast-paced digital landscape.
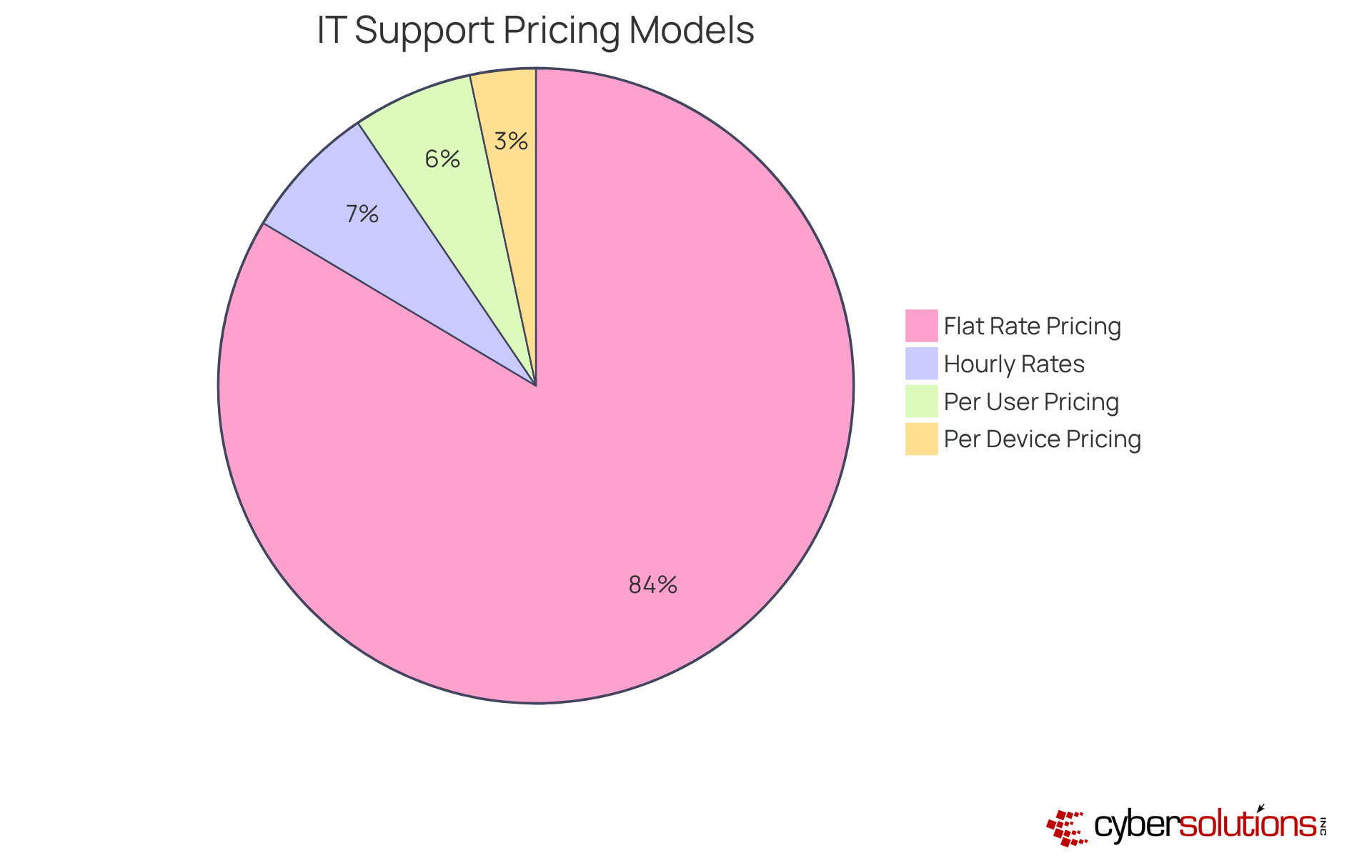
Understanding the outsourced IT support costs associated with IT assistance is crucial for organizations that aim to align their IT expenditures with operational needs and budget constraints. The outsourced IT support costs for these services can vary significantly, influenced by factors such as the range of support, organizational size, and required expertise. As we navigate the evolving landscape of IT support, it’s essential to grasp the prevalent pricing models available:
Looking ahead to 2025, we see a trend toward more customized pricing models that cater to the specific needs of various sectors. An increasing number of organizations are opting for hybrid approaches that blend elements of these models. As companies prioritize cybersecurity and specialized IT services, a solid understanding of outsourced IT support costs will be vital for strategic decision-making.
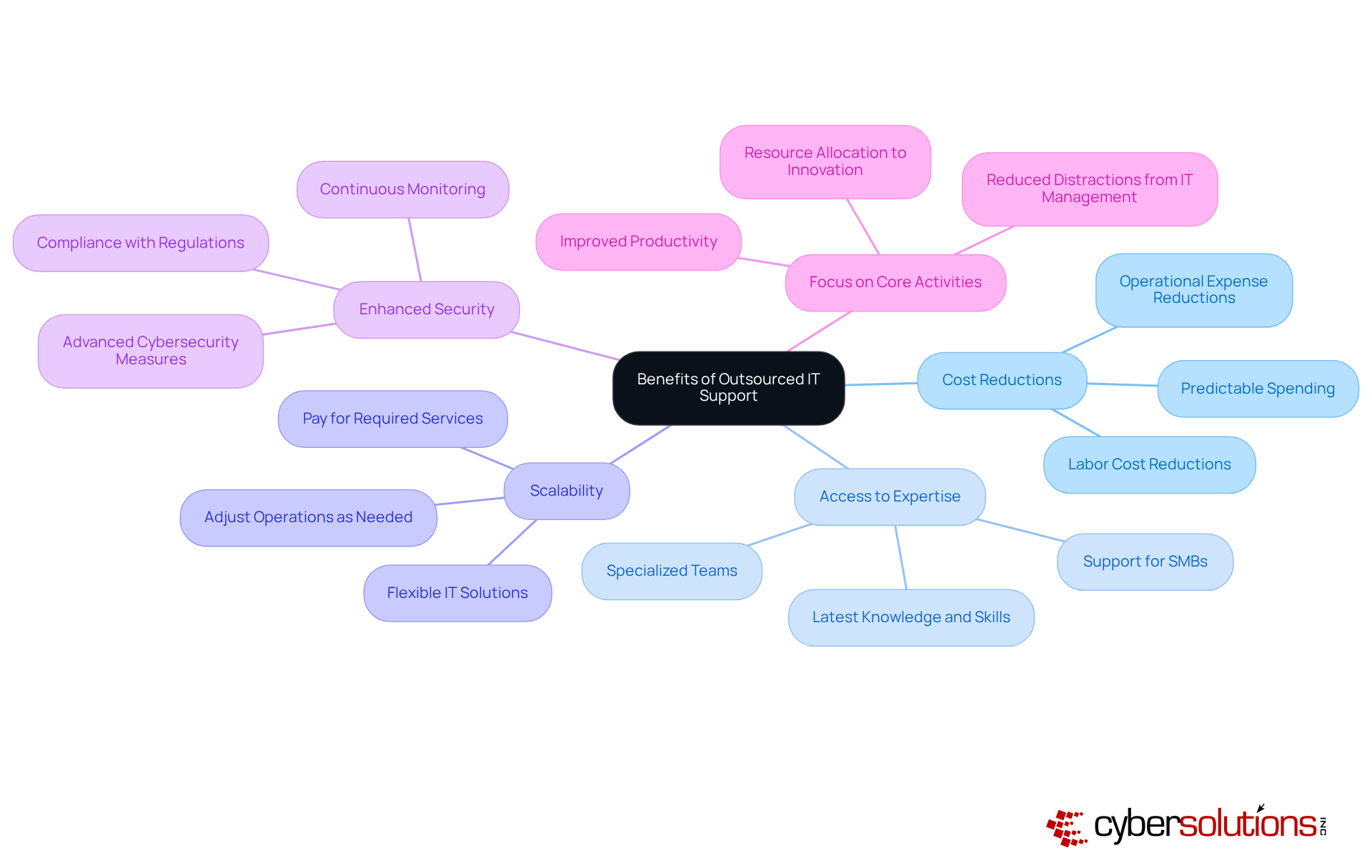
Outsourced IT support is not just a trend; it’s a strategic move that can significantly enhance an organization’s operational efficiency.
By outsourcing, businesses can achieve labor cost reductions of 25% to 45%, significantly lowering their outsourced IT support costs. This enables them to reallocate resources towards innovation and growth initiatives. Organizations report average operational expense reductions of 30% to 60% when outsourcing IT functions, which helps in managing outsourced IT support costs more effectively and provides better financial control and predictability.
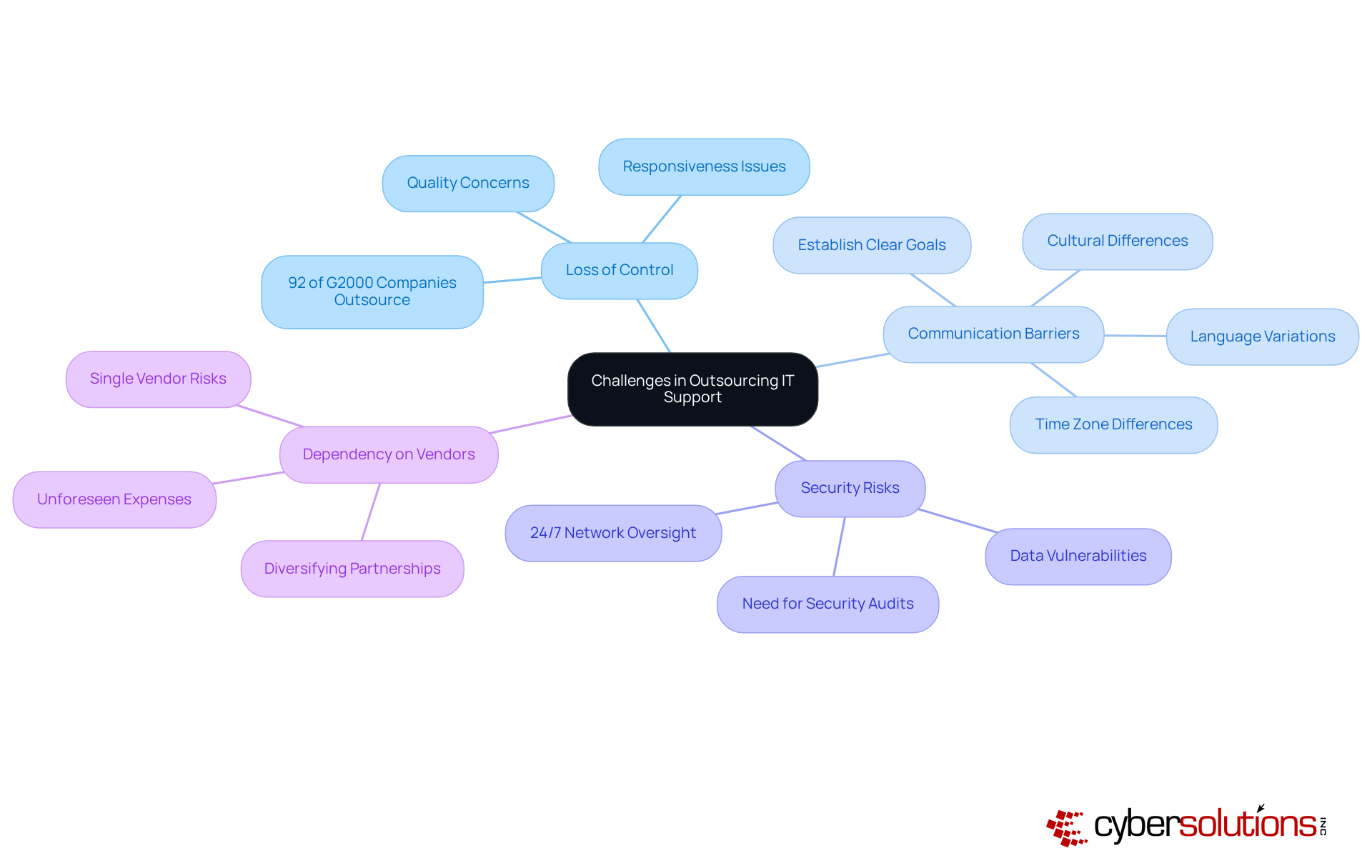
Outsourcing IT support can lead to outsourced IT support costs that are a double-edged sword, offering numerous benefits while also presenting significant challenges that organizations must navigate with care.
Loss of Control: One of the primary concerns is the potential loss of control over IT functions. Organizations often find themselves questioning the quality and responsiveness of services provided by external vendors. In fact, a staggering 92% of G2000 companies rely on IT outsourcing, underscoring the extent of this dependency and the accompanying risks of diminished oversight.
Communication Barriers: Communication can become a hurdle due to variations in time zones, language, and cultural differences. These factors can lead to misunderstandings and delays, complicating assistance delivery and collaboration. To mitigate these challenges, it’s crucial to establish clear project goals and response times from the outset.
Security Risks: Entrusting sensitive data to external providers introduces potential security vulnerabilities. Organizations must implement stringent management and oversight to protect their information. Conducting thorough security audits of potential partners is a recommended strategy before entering any partnership. Additionally, establishing 24/7 network oversight and alert systems can proactively identify anomalies, ensuring that suspicious activities are addressed before they escalate into serious threats.
Dependency on Vendors: Heavy reliance on a single vendor can create significant challenges, especially if that provider fails to meet expectations or if a transition to a new vendor becomes necessary. Diversifying outsourcing partnerships can enhance flexibility and reduce the risks associated with vendor dependency.
Organizations often encounter unforeseen expenses related to modifications or additional support requirements, which can significantly increase their outsourced IT support costs. This highlights the importance of creating clear agreements and expectations from the beginning. Alarmingly, 79% of companies do not conduct comprehensive cost assessments before outsourcing, emphasizing the need for clarity from the outset. Furthermore, leveraging Compliance as a Service (CaaS) can help small and medium-sized businesses access enterprise-level compliance expertise, simplifying the process and protecting against potential penalties.
As industry specialists point out, the risks associated with outsourcing IT functions can be effectively reduced through proactive strategies. Performing comprehensive security audits of potential partners and establishing Non-Disclosure Agreements (NDAs) are essential steps to safeguard sensitive information. Moreover, fostering strong relationships with vendors can enhance communication and service quality, ultimately leading to more successful outsourcing outcomes.
Outsourced IT support has become a strategic necessity for organizations aiming to boost operational efficiency and cut costs. By tapping into external expertise, businesses gain access to specialized knowledge while concentrating on their core activities. This strategy not only drives innovation but also helps companies stay competitive in a fast-changing technological landscape.
The discussion highlights the various dimensions of outsourced IT support, emphasizing its role in achieving significant cost savings—up to 70%—and enhancing operational efficiencies. Different pricing structures, including:
are outlined, enabling organizations to choose the option that best fits their needs. Moreover, the advantages of outsourcing extend beyond financial aspects, incorporating improved security measures and the flexibility to scale services in line with business growth.
Given these insights, it’s essential for strategic leaders to understand the importance of outsourced IT support as a vital element of their operational strategy. Embracing this approach not only reduces the risks tied to in-house IT management but also positions organizations for sustained growth and adaptability. As the landscape evolves, staying informed about the nuances of outsourced IT support costs and benefits will empower leaders to make informed decisions that propel their businesses forward.
What is outsourced IT support?
Outsourced IT support involves engaging external providers to meet critical IT needs for businesses, including services such as help desk support, network administration, cybersecurity, data backup, and firewall solutions.
Why is outsourced IT support important for businesses?
It provides access to specialized expertise that may not be available internally, allowing organizations to keep pace with technological advancements and achieve high service levels, often with an 85% success rate compared to in-house teams.
How can outsourcing IT functions lead to cost savings?
Businesses can reduce their IT support costs by up to 70% by avoiding expenses related to salaries, benefits, and training for a full-time internal team, making it a financially efficient option.
What are the primary motivations for companies to outsource IT support?
A significant motivation is the reduction of outsourced IT support costs, with 59-70% of companies citing it as a key reason for outsourcing.
How does outsourced IT support allow organizations to focus on their core activities?
By entrusting IT management to external experts, companies can redirect their resources towards innovation and strategic initiatives, enhancing operational efficiency and responsiveness to market demands.
What are some key features of outsourced IT assistance?
Key features include proactive monitoring, patch management, and endpoint protection, all of which enhance security and operational resilience.
What overall value does outsourced IT support provide?
It offers specialized knowledge, reduces overall expenses, and enables businesses to concentrate on their strategic objectives, making it an invaluable asset in the fast-paced digital landscape.