
In an age where cyber threats loom larger than ever, the significance of cybersecurity compliance has reached a critical juncture for organizations worldwide. C-suite leaders are not just facing an increasingly complex regulatory landscape; they are also tasked with understanding and implementing effective compliance strategies. This is not merely a legal obligation - it is essential for safeguarding digital assets and maintaining customer trust.
With the average cost of non-compliance soaring to millions, organizations must ask themselves: how can executives effectively navigate this intricate web of regulations while ensuring their organizations remain resilient against emerging threats? The stakes are high, and the need for robust cybersecurity measures has never been more pressing.
Adhering to cybersecurity and compliance is not just a regulatory obligation; it’s a cornerstone of protecting digital assets against ever-evolving cyber threats. In today’s landscape, businesses face a myriad of standards designed to safeguard sensitive information and uphold customer trust. For C-suite executives, grasping the nuances of these regulations is crucial, as it directly influences risk management strategies and financial health.
As we approach 2025, the stakes are higher than ever. Organizations that fail to adhere to compliance face staggering consequences, with an average cost of $4.61 million stemming from regulatory violations. These penalties can manifest as hefty fines and lasting damage to reputation, underscoring the imperative for leaders to weave adherence into their broader business strategies.
Consider this: 85% of executives report an increase in the complexity of regulatory requirements, which can stifle operational efficiency and hinder growth. Real-world examples illustrate the gravity of non-compliance; entities that miss compliance deadlines not only incur financial penalties but also risk losing customer trust and market position.
Thus, prioritizing cybersecurity and compliance transcends mere legal necessity; it emerges as a strategic imperative for sustainable business success. By integrating robust cybersecurity measures, organizations can not only protect their assets but also foster a culture of trust and reliability in an increasingly digital world.

Key regulations and standards related to cybersecurity and compliance, such as HIPAA, PCI-DSS, GDPR, and NIST frameworks, are essential in safeguarding sensitive information. Why is this crucial? Because the stakes are incredibly high in healthcare, where patient trust and data integrity are paramount. For instance, HIPAA enforces stringent regulations on patient data protection, requiring entities to implement comprehensive risk management strategies, encrypt electronic protected health information (ePHI), and utilize multi-factor authentication for system access. Notably, updates to HIPAA in 2025 will introduce stricter encryption requirements and faster breach notifications, underscoring the urgent need for organizations to adapt swiftly to these regulatory changes.
On the other hand, PCI-DSS focuses on securing credit card transactions. Organizations that adhere to these standards report significantly fewer data breaches. Consider this: firms that successfully meet PCI-DSS requirements not only enhance customer confidence but also face lower financial penalties. This highlights the tangible benefits of compliance, making a compelling case for adherence.
The NIST Cybersecurity Framework is also set for updates in 2025, responding to evolving threats and the growing complexity of cyber risks. C-suite executives must familiarize themselves with these changing regulations to ensure their organizations implement the necessary policies and technologies for cybersecurity and compliance. Consistent training and updates on these standards are vital for maintaining adherence and adapting to shifts in the regulatory landscape. Ultimately, this fosters a culture of security and resilience within the organization.

In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations navigating complex regulatory environments. A thorough risk assessment is the first step in identifying vulnerabilities and regulatory gaps, laying the groundwork for a tailored regulatory framework. This framework should encompass policies, procedures, and training programs that align with specific requirements, ensuring that all employees are equipped to uphold these standards.
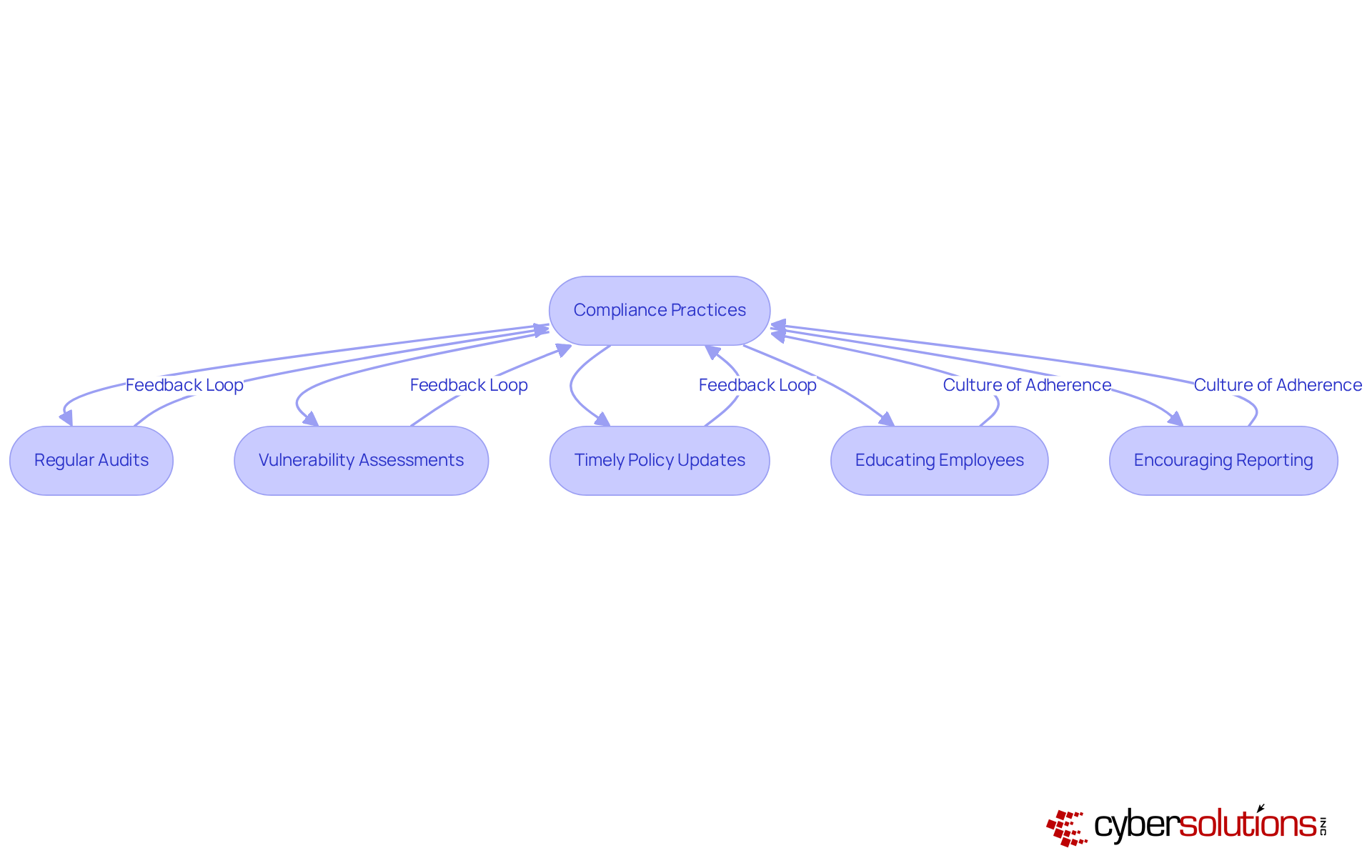
Regular audits and assessments are not just best practices; they are essential for maintaining adherence to established policies. By fostering a culture of continuous improvement, organizations can adapt to evolving threats and regulations. Moreover, leveraging technology - such as automated monitoring tools - can significantly streamline the adherence process, making it easier to maintain and report on regulatory status.
Engaging outside specialists can provide invaluable insights and support, helping organizations navigate the complexities of the regulatory landscape more effectively. Thriving organizations demonstrate that these practices not only enhance compliance but also strengthen their overall cybersecurity posture. In a progressively regulated environment, being proactive in these areas equips organizations to manage risks more effectively and safeguard their operations.
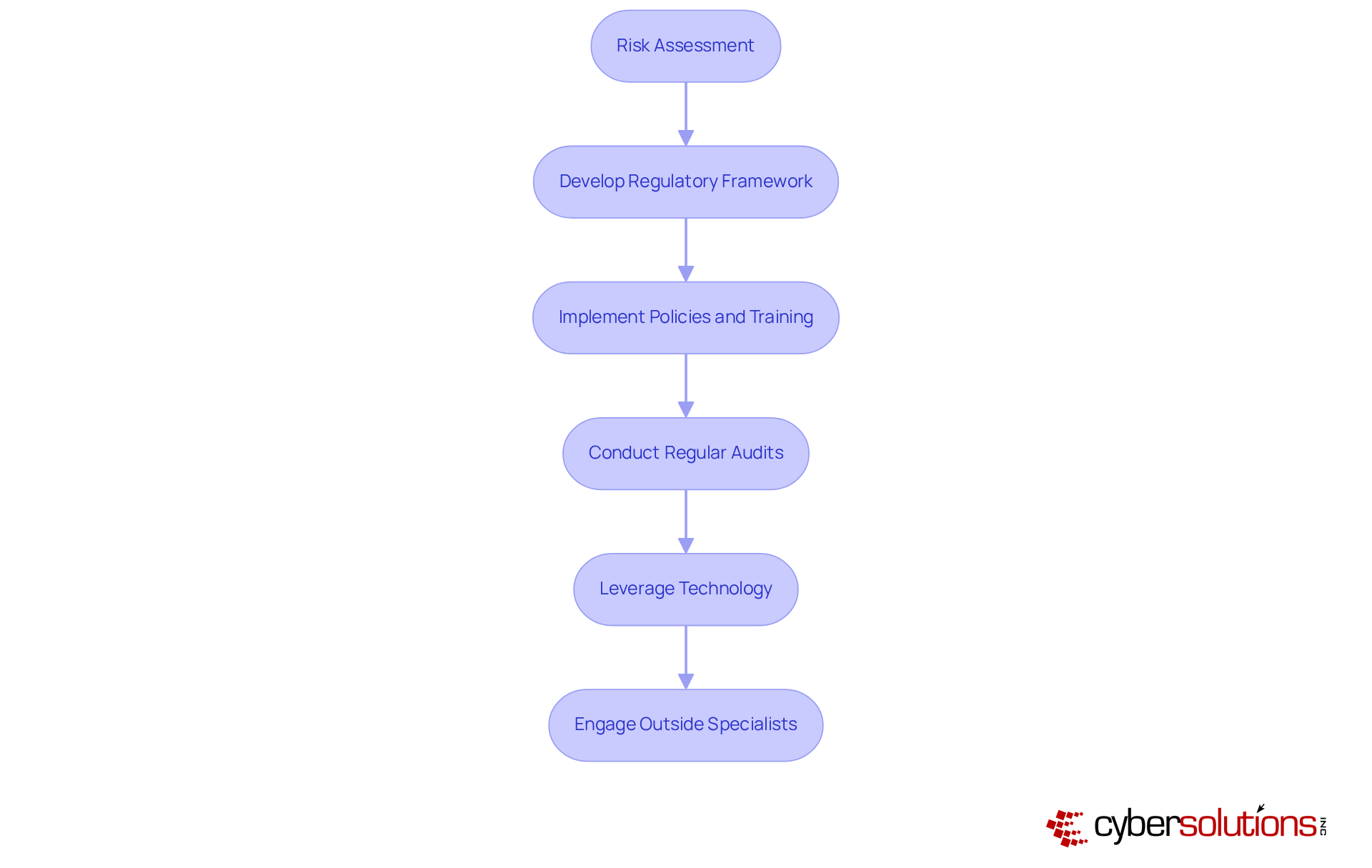
Effective adherence management is not just a task; it requires a proactive and continuous strategy. Organizations must develop a comprehensive oversight monitoring plan that includes:
to ensure both cybersecurity and compliance with evolving regulations. Utilizing management software for regulations is crucial - it enables real-time monitoring and reporting, allowing organizations to swiftly identify and address regulatory issues.
Moreover, fostering a culture of adherence is essential. This can be achieved by:
Adjusting adherence practices based on audit results and regulatory changes is vital for maintaining a robust regulatory stance, especially as 21% of C-suite executives now prioritize regulatory adherence as a strategic focus.
As organizations navigate the complexities of cybersecurity and compliance in 2025, integrating advanced compliance management tools will be key to enhancing operational efficiency and mitigating risks. Are you ready to elevate your adherence strategy?
Prioritizing cybersecurity and compliance is not just a legal obligation; it’s a strategic necessity that underpins the resilience and success of modern organizations. In an increasingly complex digital landscape, C-suite leaders must recognize that effective compliance is integral to safeguarding assets, maintaining customer trust, and ensuring sustainable growth.
Understanding key regulations such as HIPAA, PCI-DSS, and GDPR is critical. Organizations must implement robust compliance strategies that include:
By fostering a culture of adherence and leveraging technology, organizations can mitigate risks and enhance their overall cybersecurity posture.
As we look toward the challenges of 2025 and beyond, embracing cybersecurity compliance should be viewed as a proactive strategy rather than a reactive measure. Leaders are encouraged to take decisive action now-investing in training, updating policies, and utilizing the latest compliance management tools-to ensure their organizations are not only compliant but also positioned for long-term success in an increasingly regulated environment.
What is cybersecurity compliance?
Cybersecurity compliance refers to adhering to various regulations and standards designed to protect sensitive information and safeguard digital assets from cyber threats.
Why is cybersecurity compliance important for businesses?
It is crucial for protecting digital assets, maintaining customer trust, and influencing risk management strategies and financial health. Non-compliance can lead to significant financial penalties and damage to reputation.
What are the potential consequences of failing to adhere to cybersecurity compliance?
Organizations that fail to comply may face an average cost of $4.61 million due to regulatory violations, which can include hefty fines and loss of customer trust.
How has the complexity of regulatory requirements changed for executives?
85% of executives report an increase in the complexity of regulatory requirements, which can negatively impact operational efficiency and hinder business growth.
What real-world impacts can non-compliance have on organizations?
Entities that miss compliance deadlines not only incur financial penalties but also risk losing customer trust and their market position.
How can organizations benefit from prioritizing cybersecurity and compliance?
By integrating robust cybersecurity measures, organizations can protect their assets and foster a culture of trust and reliability, which is essential for sustainable business success in a digital world.