
In an era where digital threats are more prevalent than ever, the stakes for effective data and system recovery have reached unprecedented heights. Organizations are confronted with a stark reality: nearly 60% of small to midsize businesses that experience a cyberattack may not survive beyond six months. This underscores the critical importance of robust data recovery strategies. By exploring best practices, companies can not only safeguard sensitive information but also ensure compliance and maintain operational continuity.
As organizations navigate the complexities of the digital landscape, a pressing question arises: how can they effectively prepare for, respond to, and recover from data loss incidents? The answer lies in fortifying their resilience against future threats. By implementing comprehensive data recovery plans, businesses can mitigate risks and enhance their ability to withstand cyber challenges.
In today's digital landscape, the process of data and system recovery for lost, inaccessible, or corrupted information from backup systems or damaged storage devices is more critical than ever. For organizations, efficient information restoration involves data and system recovery, which isn't just about keeping operations running; it's about safeguarding sensitive data and ensuring compliance with industry regulations. As we approach 2025, the rise in cyberattacks and information breaches makes it imperative for companies to prioritize data and system recovery as a core component of their IT strategy.
Consider this: nearly 60% of small and midsize companies that experience a cyberattack cease operations within six months. This statistic underscores the urgent need for robust strategies for data and system recovery. The financial implications are staggering, with the average cost of a security breach in the U.S. exceeding $9 million. Organizations must not only understand but also implement effective strategies for data and system recovery to mitigate these risks.
By focusing on data and system recovery, companies can protect their assets and ensure long-term sustainability in an increasingly complex digital environment. Customized IT services, such as endpoint protection and threat detection, play a vital role in addressing the unique security and compliance needs of sectors like healthcare and finance. These tailored solutions enhance the effectiveness of recovery strategies, allowing organizations to navigate the challenges posed by today's cybersecurity threats with confidence.
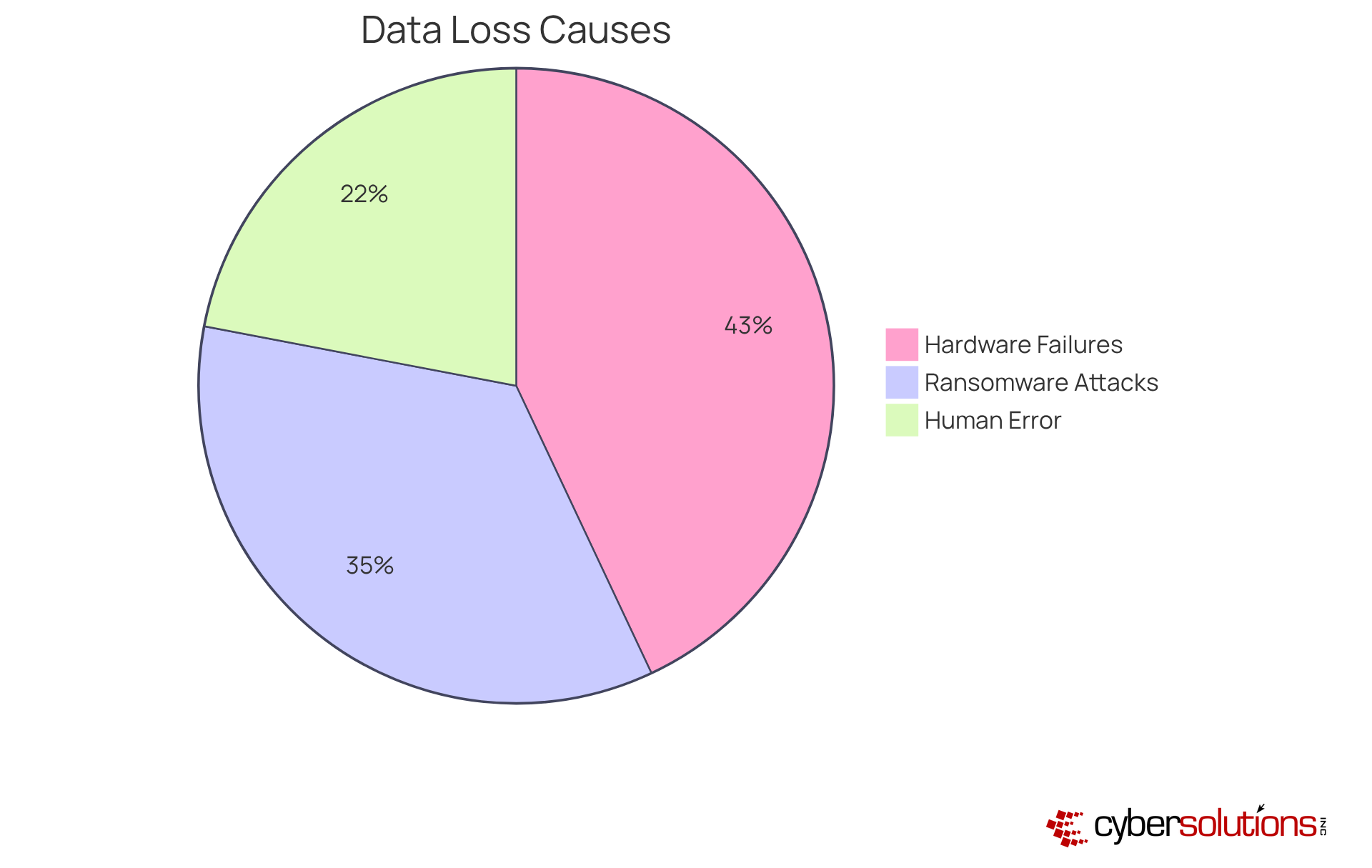
Data deterioration in companies poses a significant threat, stemming from various sources such as hardware failures, human mistakes, cyberattacks, and software corruption. According to the 2025 Data Breach Investigations Report:
To combat these challenges, implementing 24/7 threat monitoring is crucial. This proactive approach helps detect suspicious activities that could arise from human error or hardware issues before they escalate into significant threats. By identifying these common causes, organizations can adopt targeted strategies, such as multifactor authentication (MFA) and continuous monitoring, to mitigate risks and enhance their information protection frameworks.
In an era where data security is paramount, understanding the landscape of cybersecurity threats is essential for organizations. By addressing these vulnerabilities head-on, companies can not only protect their data but also foster trust and reliability in their operations.
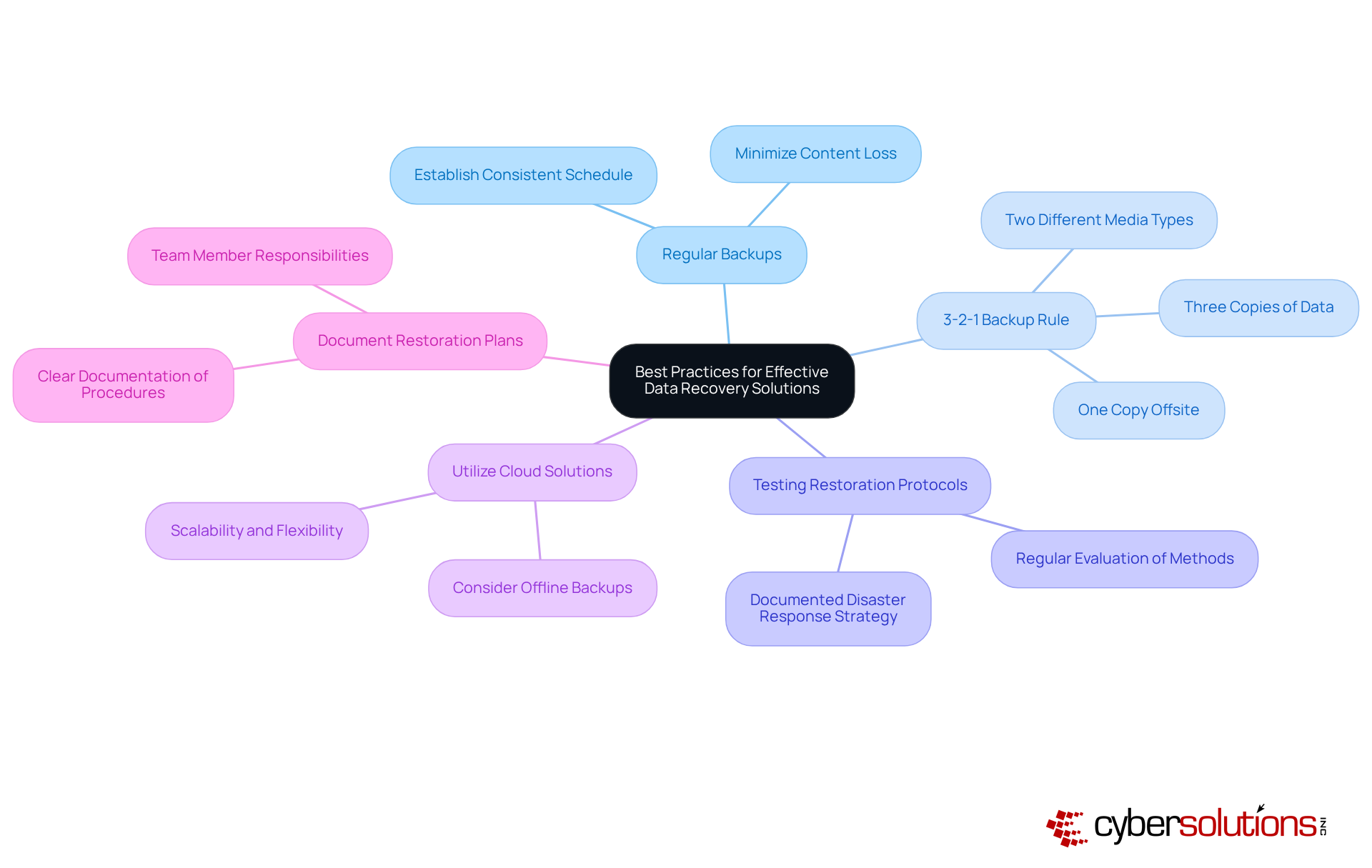
In today’s digital landscape, the importance of effective data and system recovery solutions cannot be overstated. With cyber incidents projected to cost the US $639 billion by 2025, organizations must prioritize robust backup strategies to safeguard their information. This urgency highlights the critical need for best practices in data and system recovery.
Regular Backups: Establish a consistent schedule for saving information, ensuring backups occur frequently enough to minimize potential content loss. This proactive approach is essential in mitigating risks associated with data and system recovery from data breaches.
3-2-1 Backup Rule: Follow the 3-2-1 guideline: maintain three copies of data on two different types of media, with one copy stored offsite. This strategy significantly reduces the risk of data loss due to hardware failures, ransomware attacks, or natural disasters. Recent statistics reveal that 97% of modern ransomware incidents target both primary systems and backup repositories. As Daniel Pearson, CEO of KnownHost, aptly states, "By blending the time-tested 3-2-1 rule with modern advances like immutable storage and intelligent monitoring, companies can create a highly resilient backup architecture that enhances their overall cybersecurity stance."
Testing Restoration Protocols: Testing restoration protocols involves regularly evaluating backup restoration methods to ensure swift and accurate retrieval of data and system recovery. Many organizations overlook this crucial step, which can lead to significant issues if data and system recovery are needed after a breach due to compromised or inaccessible backup data. Alarmingly, only 54% of organizations have a documented disaster response strategy, and half of those test their plans infrequently. Additionally, avoid the common mistake of storing all backups on the same physical network, as this can compromise data and system recovery in the event of a malware attack.
Utilize Cloud Solutions: Embrace cloud-based backup solutions for their scalability and flexibility, facilitating easier access to data during recovery processes. As cloud storage becomes increasingly prevalent, integrating it into backup strategies is vital for enhancing resilience against data loss. However, organizations should also consider offline or air-gapped backups to protect against local disasters.
Document Restoration Plans: Keep clear documentation of restoration procedures and responsibilities to streamline the recovery process during an incident. This ensures that all team members are aware of their roles and can respond promptly when a data failure occurs.
By implementing these best practices, organizations can bolster their resilience against data loss and focus on data and system recovery, ensuring rapid restoration when incidents arise and ultimately protecting their operations and sensitive information.
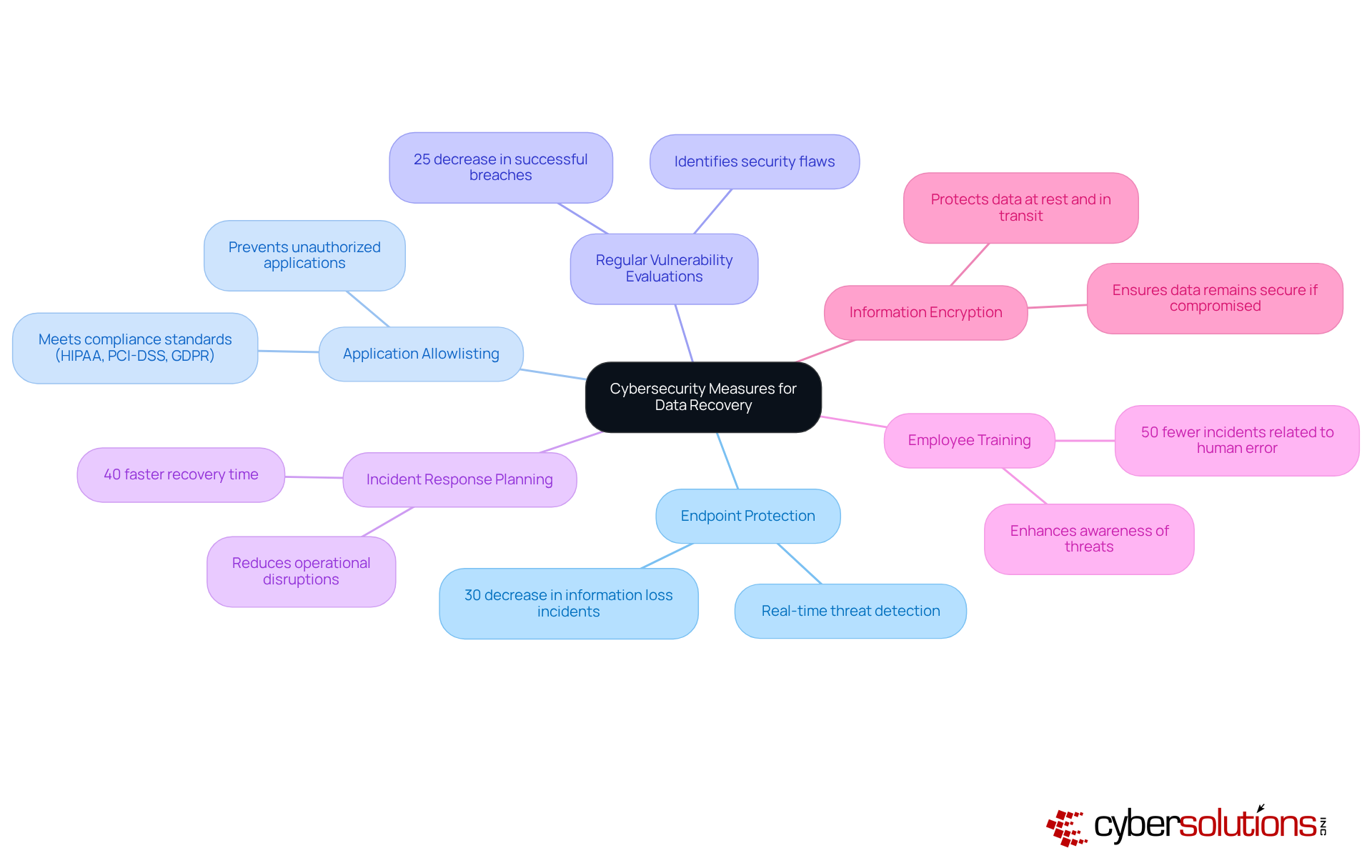
In today's digital landscape, incorporating cybersecurity measures into information recovery strategies is not just important—it's essential for safeguarding sensitive information against emerging threats like ransomware and data breaches. Organizations must take proactive steps to protect their data and ensure compliance with industry standards. Here are several key approaches:
Implementing Endpoint Protection: Advanced endpoint protection solutions are crucial for detecting and responding to threats in real-time. In 2025, entities employing these solutions reported a 30% decrease in information loss incidents due to cyberattacks, underscoring their effectiveness in safeguarding sensitive details.
Application Allowlisting: This proactive cybersecurity strategy prevents unauthorized or malicious applications from executing on systems. By allowing only pre-approved software to operate, companies can significantly reduce the risk of malware and ransomware attacks. This method not only minimizes vulnerabilities but also helps meet compliance requirements for standards like HIPAA, PCI-DSS, and GDPR, ensuring organizations adhere to stringent protection protocols.
Regular Vulnerability Evaluations: Conducting regular vulnerability evaluations helps identify and address security flaws that could lead to information compromise. Organizations that implemented these assessments saw a 25% decrease in successful breaches, highlighting the importance of proactive security measures.
Incident Response Planning: A comprehensive incident response strategy is vital for ensuring quick recovery in the event of a breach or cyberattack. Organizations with well-defined plans reported a 40% faster recovery time, reducing operational disruptions and financial losses.
Employee Training: Ongoing cybersecurity education for staff enhances awareness of potential threats and best practices for information protection. Research indicates that organizations with robust training programs experience 50% fewer incidents related to human error, a leading cause of information breaches.
Information Encryption: Encrypting sensitive information both at rest and in transit protects it from unauthorized access. Even if data is compromised, encryption ensures that it remains secure, significantly lowering the risk of exposure.
By integrating these cybersecurity measures into their information recovery plans, organizations can enhance their overall strategy for data and system recovery and ensure a more robust response to loss incidents. As cybersecurity specialists emphasize, "Prioritizing crucial controls such as information encryption and multifactor authentication can lessen the threat of cyberattacks if they are consistently applied." This holistic approach not only protects data but also strengthens the organization against the increasing sophistication of cyber threats.
In today’s fast-paced digital landscape, the importance of data and system recovery is paramount. Organizations must understand that effective recovery strategies are not just a safety net; they are vital for maintaining operational integrity, safeguarding sensitive information, and ensuring compliance with industry regulations. As cyber threats grow more sophisticated, prioritizing robust data recovery practices is essential for protecting business continuity.
This article underscores several key insights into effective data recovery:
The message is clear: organizations must take proactive steps to strengthen their data recovery strategies. As cyber threats continue to escalate, the time to act is now. By investing in comprehensive recovery solutions and integrating cybersecurity measures, businesses can not only protect their valuable data but also ensure their long-term sustainability in an increasingly complex digital environment. Embracing these best practices will empower organizations to navigate challenges with confidence and resilience, securing their future amid uncertainty.
What is data recovery and why is it important for businesses?
Data recovery is the process of restoring lost, inaccessible, or corrupted information from backup systems or damaged storage devices. It is crucial for businesses as it helps safeguard sensitive data, ensures compliance with industry regulations, and maintains operational continuity.
How prevalent are cyberattacks and what impact do they have on businesses?
Cyberattacks are increasingly common, with nearly 60% of small and midsize companies that experience one ceasing operations within six months. The average cost of a security breach in the U.S. exceeds $9 million, highlighting the financial implications for organizations.
What should companies prioritize in their IT strategy regarding data recovery?
Companies should prioritize data and system recovery as a core component of their IT strategy to mitigate risks associated with cyberattacks and information breaches.
What role do customized IT services play in data recovery?
Customized IT services, such as endpoint protection and threat detection, are essential in addressing the unique security and compliance needs of sectors like healthcare and finance. These tailored solutions enhance the effectiveness of recovery strategies in navigating cybersecurity challenges.
What are the long-term benefits of focusing on data and system recovery?
By focusing on data and system recovery, companies can protect their assets, ensure long-term sustainability, and confidently navigate the complexities of the digital environment.