
The Cybersecurity Maturity Model Certification (CMMC 1.0) stands as a pivotal framework, not merely a regulatory hurdle for defense contractors. In an era where cyber threats are becoming increasingly sophisticated, understanding and implementing CMMC compliance is essential for organizations that seek to secure government contracts and safeguard sensitive information. Yet, many organizations find themselves struggling to navigate this intricate landscape.
What best practices can lead to successful compliance and ultimately strengthen an organization's cybersecurity posture? By addressing these challenges head-on, organizations can not only meet regulatory requirements but also enhance their overall security framework, ensuring they are well-equipped to face evolving threats.
The Cybersecurity Maturity Model Certification (CMMC 1.0) stands as a pivotal framework established by the Department of Defense (DoD) to bolster the cybersecurity posture of entities within the defense industrial base. In an era where cyber threats are increasingly sophisticated, understanding this model is not just beneficial - it's essential. It comprises multiple levels, each designed with specific practices and processes aimed at safeguarding Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). For organizations seeking government contracts, compliance with CMMC 1.0 is more than a regulatory checkbox; it’s a strategic necessity that fosters trust and enhances operational resilience.
This tiered approach requires organizations to demonstrate their ability to protect sensitive information through a series of defined practices. By prioritizing CMMC 1.0 standards, defense contractors not only enhance their security measures but also significantly mitigate the risk of data breaches. Consider this: how can an organization thrive in a competitive landscape if it fails to protect its most critical assets? The answer is clear - meeting CMMC 1.0 standards is not merely a requirement; it’s a commitment to excellence in cybersecurity.
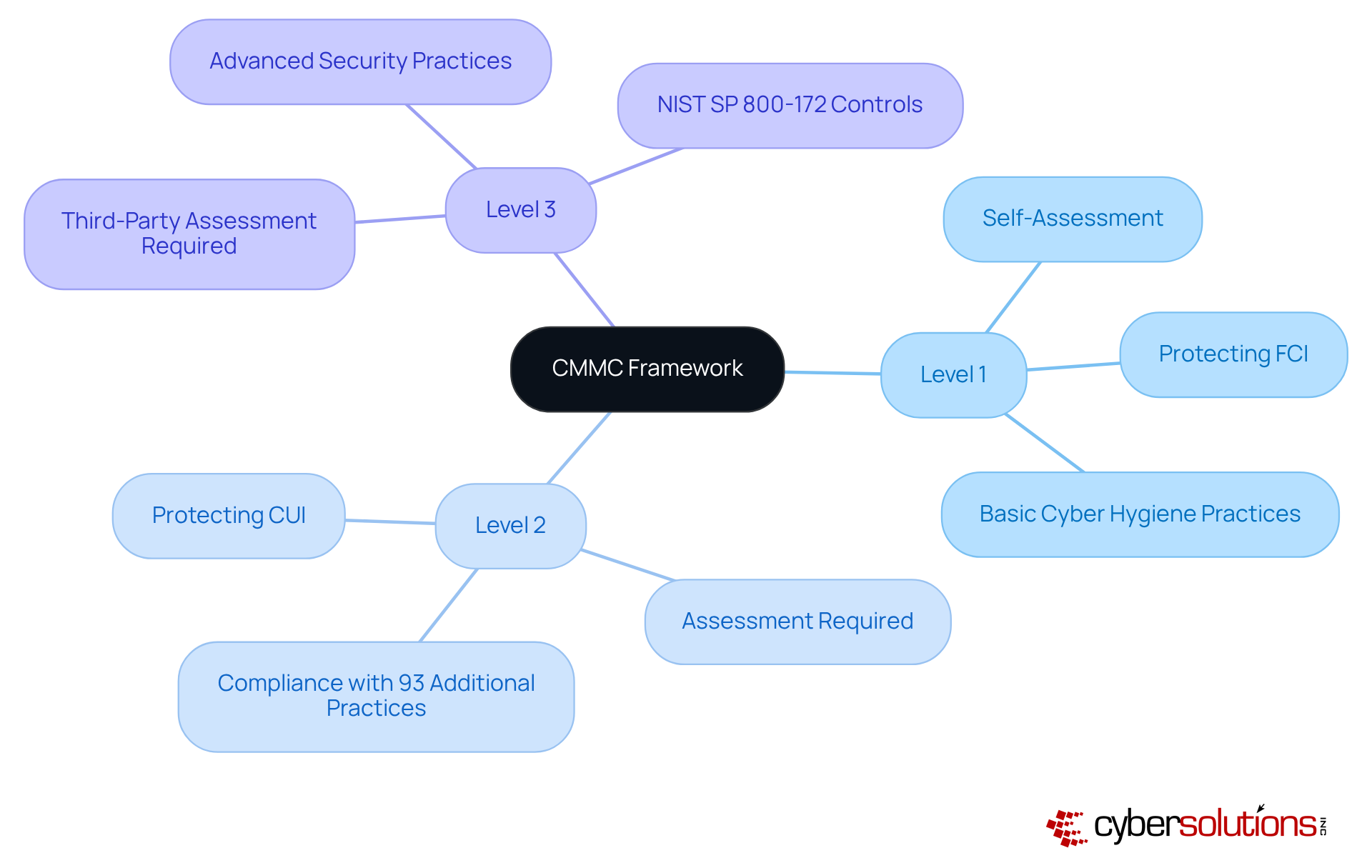
CMMC compliance is crucial for safeguarding sensitive information, structured into three distinct levels, each tailored to the sensitivity of the data handled. Level 1 focuses on the basic safeguarding of Federal Contract Information (FCI), mandating 17 essential practices that establish fundamental cybersecurity hygiene. Level 2 builds upon this foundation by introducing additional practices designed to protect Controlled Unclassified Information (CUI), necessitating a more robust security posture. Finally, Level 3 represents the most advanced tier, requiring organizations to implement 110 practices that align with NIST SP 800-171 standards, ensuring comprehensive protection against sophisticated threats.
A critical component of achieving compliance at any level is the implementation of application allowlisting. This proactive cybersecurity measure prevents unauthorized or malicious applications from executing, significantly reducing the attack surface and minimizing vulnerabilities. For Level 1, application allowlisting aids in establishing fundamental protective practices by ensuring only authorized software can operate. At Level 2, it enhances protection for CUI by further limiting the applications that can execute, thereby reinforcing security measures. Finally, for Level 3, application allowlisting is essential in meeting the extensive requirements of NIST SP 800-171, ensuring comprehensive protection against sophisticated threats.
Organizations must carry out a comprehensive evaluation of their existing cybersecurity status to ascertain the suitable level of adherence based on the sensitivity of the information they handle. This assessment is essential for creating a customized adherence strategy that aligns with operational capabilities and risk management goals. By 2025, numerous entities are actively seeking adherence to CMMC 1.0, with a substantial number anticipated to shift to Level 2 as the criteria become obligatory. Comprehending these levels and their implications is crucial for entities seeking to uphold eligibility for Department of Defense contracts and protect sensitive information effectively.

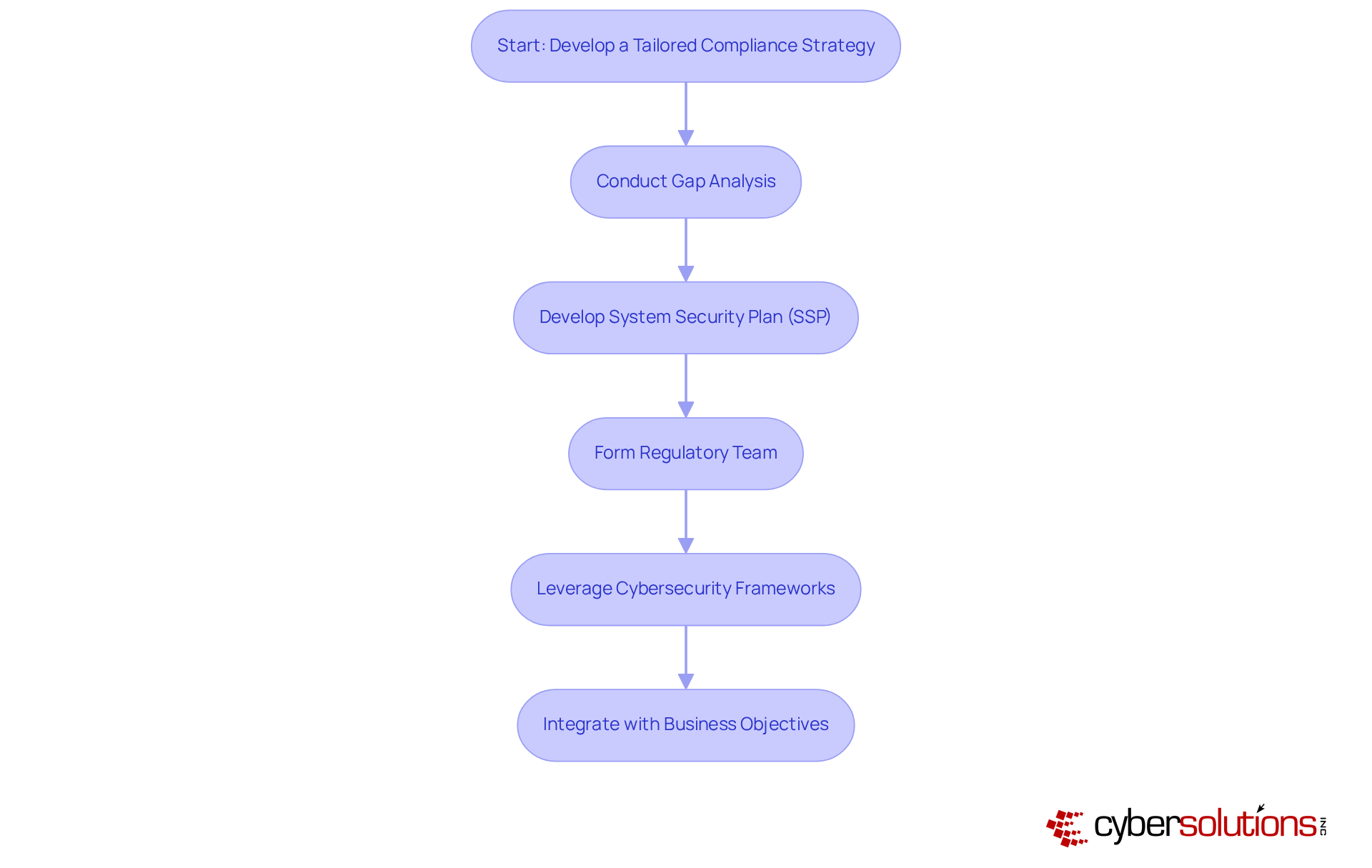
Creating a customized adherence strategy is essential for organizations aiming to bolster their cybersecurity posture. It all begins with a thorough gap analysis to pinpoint current vulnerabilities and areas that need enhancement. This crucial step not only uncovers gaps between existing cybersecurity practices and the requirements of CMMC 1.0 but also lays the groundwork for a robust regulatory framework. Following the gap analysis, organizations should develop a System Security Plan (SSP) that clearly outlines the specific practices and controls necessary for compliance. Forming a dedicated regulatory team is vital for overseeing the execution of this strategy, ensuring that all stakeholders remain engaged and informed throughout the process.
Leveraging established cybersecurity frameworks, such as NIST SP 800-171, can significantly enhance adherence efforts by providing a solid foundation for aligning protective measures with CMMC 1.0 standards. This alignment is critical, especially considering that nearly 80,000 companies will require Level 2 certification by 2025. Therefore, timely and effective adherence strategies are imperative. By integrating adherence initiatives with broader business objectives, organizations can ensure their strategies not only meet regulatory standards but also strengthen their overall security posture and operational efficiency.
Case studies underscore the importance of gap analysis. For instance, defense contractors facing challenges in achieving Level 2 standards due to a shortage of qualified resources illustrate the need for comprehensive evaluations. Engaging with Certified Third-Party Assessment Organizations (C3PAOs) can further streamline this process, ensuring that organizations are well-prepared for the evolving regulatory landscape.
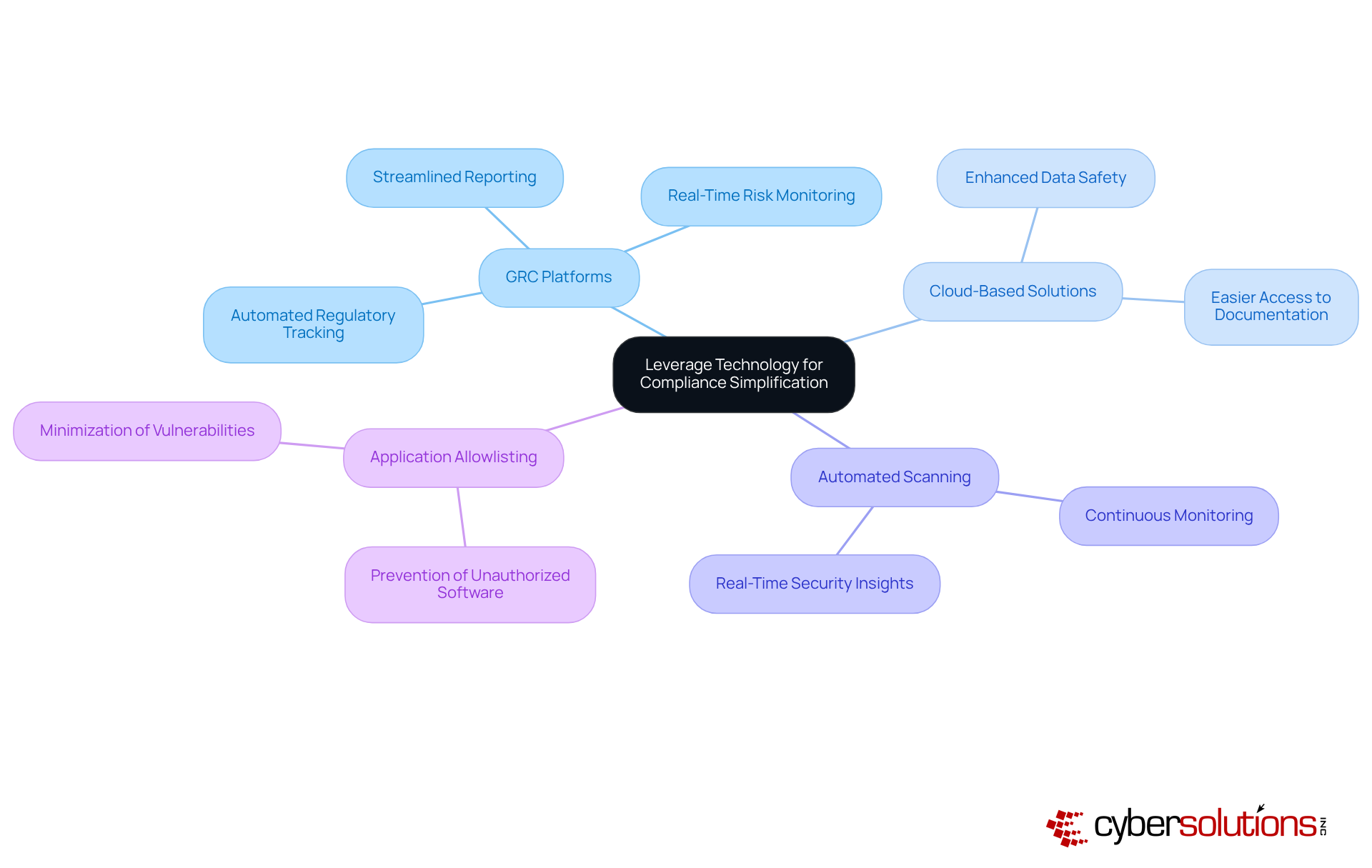
In today’s digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations striving to meet the requirements of CMMC 1.0 compliance. With the rise of sophisticated cyber threats, healthcare organizations face unique challenges that demand immediate attention. By leveraging advanced technological solutions, these entities can simplify their CMMC 1.0 adherence efforts and fortify their defenses against potential breaches.
Implementing Governance, Risk, and Compliance (GRC) platforms stands out as a pivotal strategy. These platforms automate regulatory tracking and reporting, significantly alleviating the administrative burden associated with manual processes. Additionally, cloud-based protection solutions enhance data safety while facilitating easier access to essential regulatory documentation. But that’s not all - automated vulnerability scanning and continuous monitoring systems provide real-time insights into an organization’s security posture, ensuring compliance with stringent standards.
Achieving CMMC 1.0 Level 3 adherence is not just about meeting requirements; it’s about demonstrating a commitment to cybersecurity that can offer a competitive edge in securing federal contracts. Incorporating application allowlisting as a proactive measure further strengthens cybersecurity by preventing unauthorized software from executing, thereby minimizing vulnerabilities.
By integrating these technologies into their compliance strategy, organizations can streamline their processes and enhance their responsiveness to emerging threats. The result? A robust security framework that not only meets compliance standards but also instills confidence in stakeholders and clients alike.
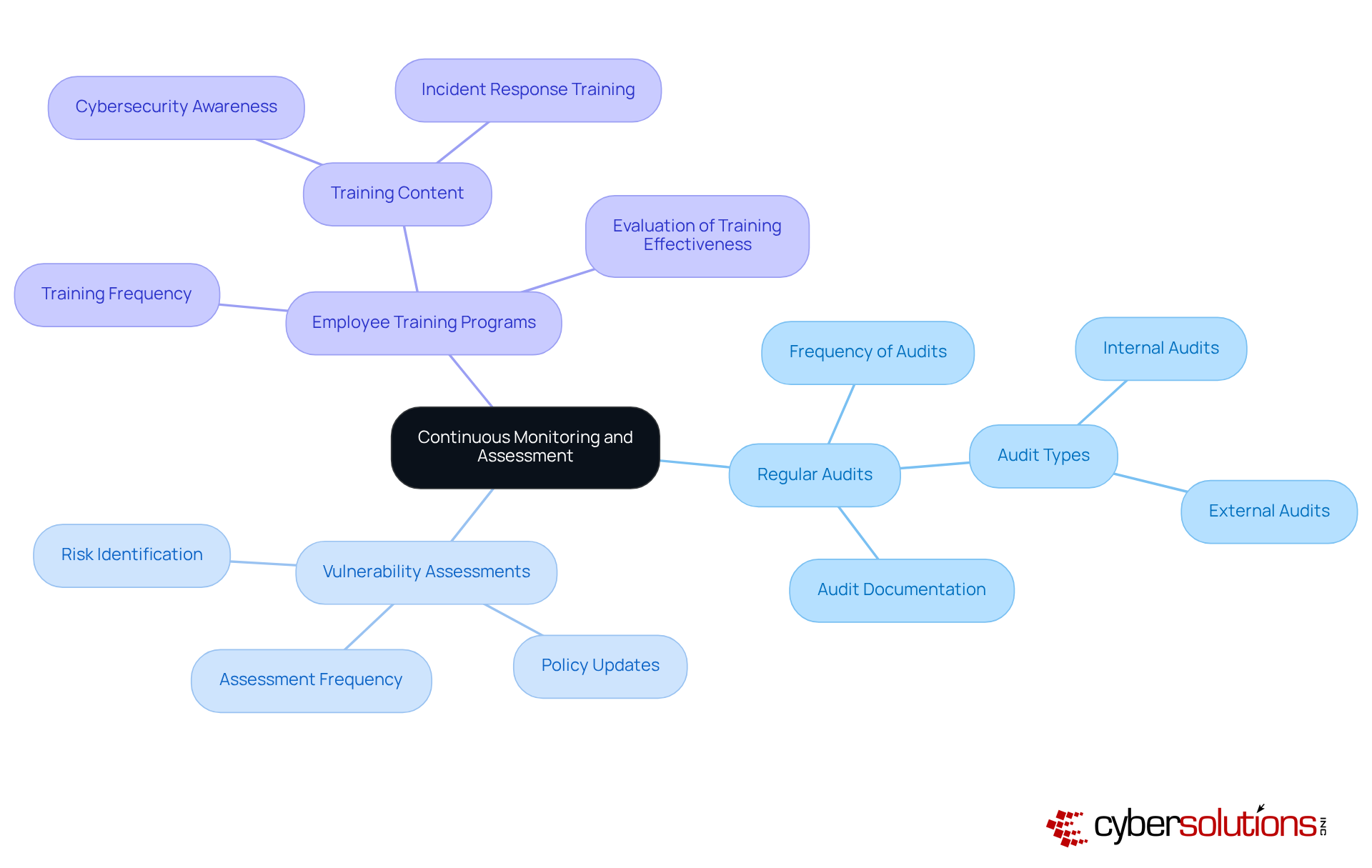
In today’s digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations handling sensitive data. To effectively implement continuous monitoring and assessment, entities must establish a robust framework that includes:
This framework should be tailored to evaluate the effectiveness of implemented controls, ensuring alignment with CMMC 1.0 requirements.
Statistics reveal that entities with revenue surpassing $1 billion typically conduct six or more audits each year. This highlights the significance of frequent assessments in upholding regulations and safeguarding against potential threats. By employing automated tools, organizations can significantly enhance their ongoing monitoring capabilities, allowing them to identify and respond to possible threats in real-time.
Moreover, regular updates to policies and procedures based on findings from these assessments are crucial for adapting to the ever-evolving cybersecurity threats. By fostering a culture of continuous improvement and vigilance, organizations can not only achieve compliance but also strengthen their overall security posture. This proactive approach mitigates risks associated with non-compliance and enhances operational resilience, ensuring that organizations are well-equipped to face the challenges of the digital age.
Achieving compliance with the Cybersecurity Maturity Model Certification (CMMC 1.0) is not merely a regulatory necessity for organizations within the defense industrial base; it stands as a strategic imperative that significantly enhances cybersecurity and builds trust with stakeholders. In today’s landscape, understanding the framework and its tiered levels is crucial. It provides a clear roadmap for safeguarding sensitive information and aligning with government standards. Organizations must recognize that compliance is a commitment to excellence in cybersecurity, vital for thriving in a competitive environment.
This article outlines essential best practices for achieving CMMC 1.0 compliance, including:
Each of these practices contributes to a comprehensive approach to cybersecurity that not only meets regulatory expectations but also fortifies an organization’s defenses against evolving cyber threats. By conducting thorough gap analyses, forming dedicated compliance teams, and utilizing advanced technology solutions, organizations can streamline their compliance efforts and enhance their overall security posture.
In conclusion, the journey toward CMMC 1.0 compliance presents both challenges and opportunities. Organizations must embrace these best practices not only to comply with regulations but also to strengthen their operational resilience and secure a competitive edge in the marketplace. By prioritizing cybersecurity and fostering a culture of continuous improvement, entities can ensure they are well-prepared to navigate the complexities of the digital landscape, ultimately safeguarding their most critical assets and maintaining trust with their clients and partners.
What is the Cybersecurity Maturity Model Certification (CMMC) and why is it important?
The CMMC is a framework established by the Department of Defense to enhance the cybersecurity posture of entities within the defense industrial base. It is essential for safeguarding Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) amid increasing cyber threats. Compliance with CMMC is crucial for organizations seeking government contracts, as it fosters trust and enhances operational resilience.
How is CMMC structured in terms of compliance levels?
CMMC compliance is structured into three levels: Level 1 focuses on basic safeguarding of FCI with 17 essential practices; Level 2 builds on this by adding practices to protect CUI; and Level 3 requires organizations to implement 110 practices aligned with NIST SP 800-171 standards for comprehensive protection against advanced threats.
What role does application allowlisting play in CMMC compliance?
Application allowlisting is a critical cybersecurity measure that prevents unauthorized applications from executing. For Level 1, it establishes fundamental protective practices; for Level 2, it enhances CUI protection; and for Level 3, it is essential for meeting the extensive requirements of NIST SP 800-171.
How can organizations determine the appropriate CMMC compliance level for them?
Organizations must conduct a comprehensive evaluation of their existing cybersecurity status to determine the suitable level of adherence based on the sensitivity of the information they handle. This assessment helps create a customized strategy that aligns with their operational capabilities and risk management goals.
What is the anticipated trend regarding CMMC compliance by 2025?
By 2025, many entities are expected to actively seek adherence to CMMC 1.0, with a significant number anticipated to move to Level 2 as the criteria become mandatory for eligibility in Department of Defense contracts and effective protection of sensitive information.