
In today's digital landscape, where transformation is not just beneficial but essential, C-suite leaders are confronted with the critical challenge of protecting their organizations from a multitude of cyber threats. The stakes are alarmingly high; a single security breach can result in catastrophic financial losses and irreparable damage to reputation. This article explores ten vital emergency IT support services that not only bolster security but also enable executives to concentrate on strategic initiatives.
How can these services revolutionize the way organizations tackle crises and ensure business continuity in an increasingly unpredictable environment? By understanding the unique challenges posed by cyber threats, leaders can better appreciate the necessity of robust IT support.
As we delve deeper, consider the implications of inadequate cybersecurity measures. Organizations that fail to prioritize these services risk not only their financial stability but also their standing in the marketplace. The right emergency IT support can be a game-changer, allowing businesses to respond swiftly and effectively to any crisis.
In an era where every decision counts, the integration of these services is not just a precaution; it's a strategic imperative.
In today's fast-paced digital landscape, having robust cybersecurity measures is not just an option - it's a necessity. Cyber Solutions provides emergency IT support services through a 24/7 help desk, ensuring immediate access to skilled IT professionals who can swiftly troubleshoot and resolve issues as they arise. This service is vital for minimizing downtime; studies show that companies with emergency IT support services experience:
By having a dedicated team available at all hours, organizations can maintain critical business operations without interruption.
This capability allows C-suite leaders to focus on strategic decision-making rather than being sidetracked by IT emergencies. Furthermore, case studies demonstrate that businesses with emergency IT support services available 24/7 are more likely to comply with industry regulations, experiencing a 45% lower risk of data breaches. This underscores the importance of emergency IT support services in protecting organizational integrity and ensuring continuity.
In a world where cybersecurity threats are ever-evolving, the need for constant vigilance cannot be overstated. Cyber Solutions stands ready to address these challenges effectively, ensuring that your organization remains secure and operational.
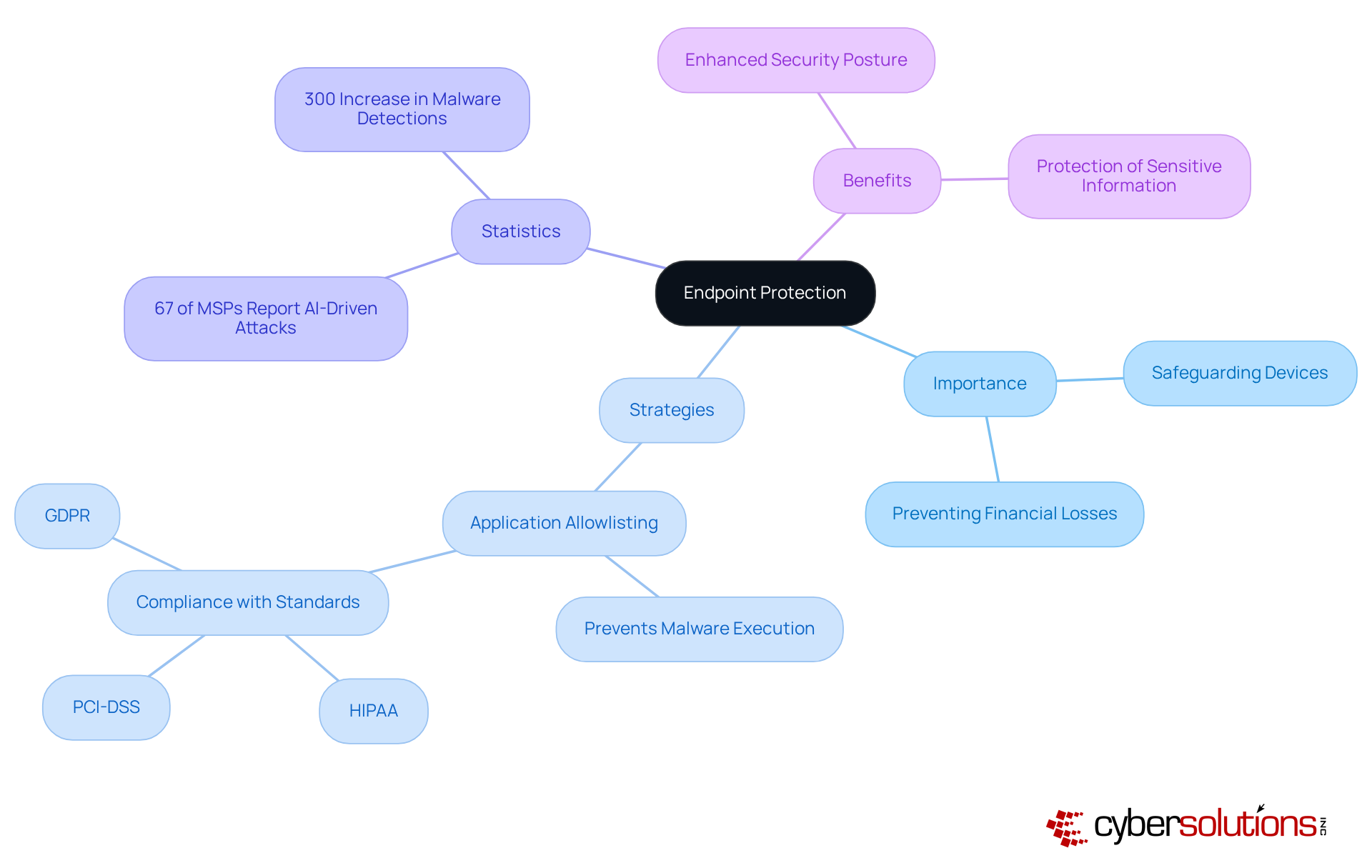
Endpoint protection solutions are essential for safeguarding devices such as laptops, smartphones, and tablets against a growing array of cyber risks. With 67% of Managed Service Providers reporting attacks from AI-driven threats in the past year, the urgency for advanced security measures is undeniable. Effective endpoint protection not only prevents unauthorized access and data breaches but also mitigates the substantial financial losses and reputational damage that can result from compromised devices.
One key strategy in this realm is application allowlisting. This proactive approach prevents malware and unauthorized software from executing, significantly reducing the attack surface. By ensuring that only authorized applications can operate, organizations can thwart ransomware and other harmful software before they inflict damage. Moreover, application allowlisting aids in meeting compliance requirements for standards such as HIPAA, PCI-DSS, and GDPR, ensuring adherence to stringent data protection protocols.
For instance, a study revealed that organizations implementing robust endpoint protection strategies experienced a 300% increase in malware detections, highlighting the effectiveness of these solutions. As cybersecurity expert Mitesh Patel states, "Our mission at Palo Alto Networks is to make each day safer and more secure than the one before." By prioritizing endpoint security and integrating proactive measures like application allowlisting, C-suite leaders can significantly enhance their organization’s overall security posture and protect sensitive information from evolving threats.
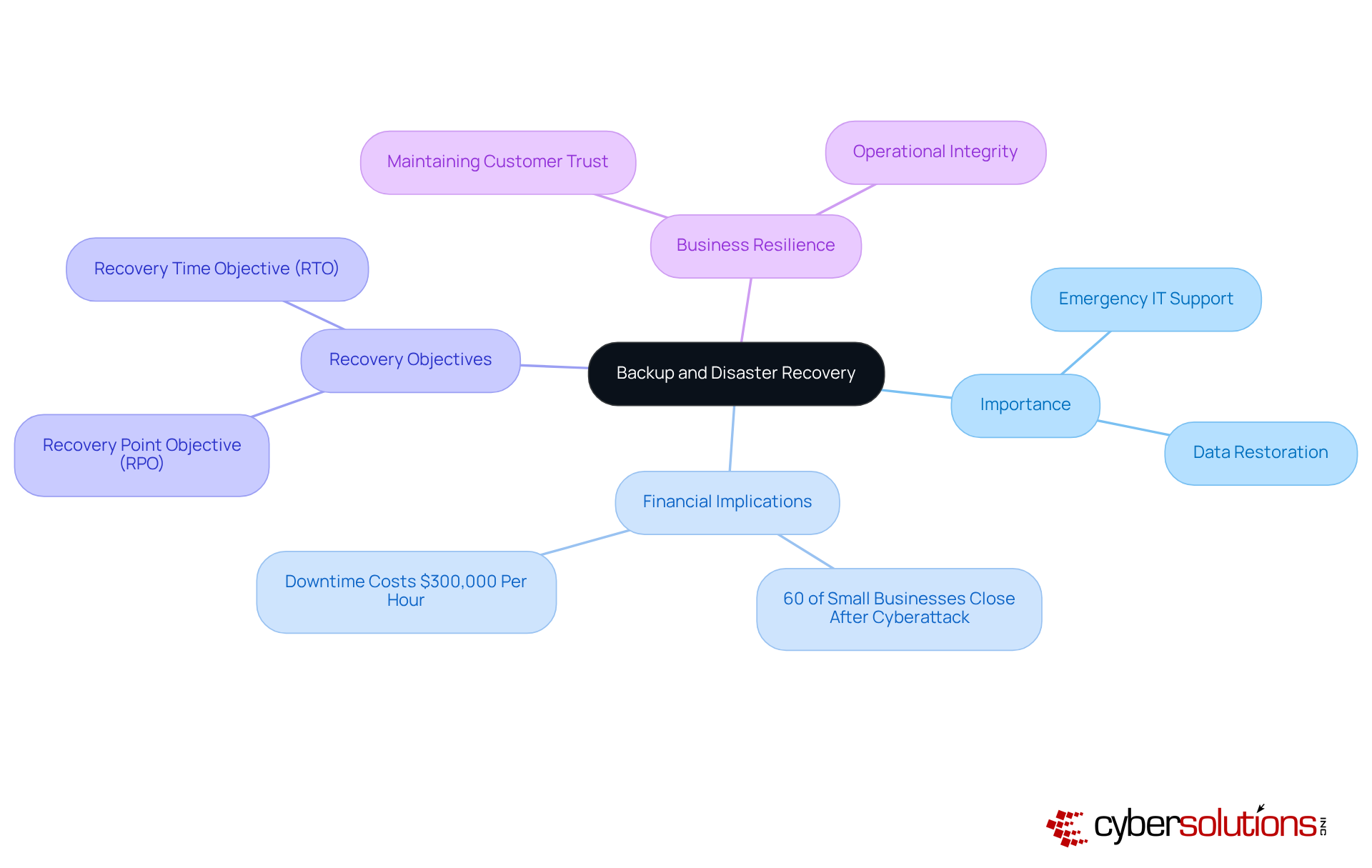
Emergency IT support services, which include backup and disaster recovery, are not just important; they are essential for organizations that need to quickly restore data and operations after disruptions. For C-suite leaders, these solutions form a robust safety net against data loss due to cyberattacks, natural disasters, or hardware failures. Implementing a comprehensive backup plan can drastically reduce downtime. In fact, studies show that 60% of small businesses close within six months of a cyberattack. This statistic underscores the financial implications of effective backup solutions.
Consider real-world examples that demonstrate the power of disaster recovery plans. Organizations with clear recovery objectives - like Recovery Point Objective (RPO) and Recovery Time Objective (RTO) - are better equipped to navigate crises, ensuring they can restore operations within acceptable timeframes. IT professionals stress that a well-structured disaster recovery plan, which includes emergency IT support services, not only safeguards data but also maintains customer trust and operational integrity.
The financial impact of downtime is staggering. Estimates suggest that downtime can cost businesses upwards of $300,000 per hour. Therefore, C-suite leaders must prioritize business continuity planning as well as emergency IT support services. It’s crucial to recognize that robust backup and disaster recovery strategies are not merely IT concerns; they are vital components of overall business resilience. By investing in these services, organizations can protect their financial health and ensure sustained operational success.
Co-managed IT support is not just a trend; it's a strategic necessity for organizations aiming to enhance their crisis response capabilities. By merging the strengths of internal IT teams with the specialized expertise of external service providers, companies can significantly improve their agility in the face of emergency IT support services. This collaborative model empowers C-suite leaders to augment their internal resources, ensuring a more effective and timely response when crises arise.
Consider this: organizations utilizing co-managed IT services have reported a remarkable 25-45% reduction in IT expenses while simultaneously boosting operational efficiency. Moreover, those with proactive disaster recovery plans experience 50% less downtime during critical incidents. This stark statistic underscores the vital role of a robust support system in today’s fast-paced digital environment.
CIOs have observed that leveraging emergency IT support services not only accelerates crisis response times but also frees internal teams to concentrate on strategic initiatives, rather than being bogged down by immediate technical challenges. This dual approach not only mitigates risks but also fortifies overall organizational resilience. In a world where digital threats are ever-evolving, co-managed IT support emerges as an essential strategy for navigating the complexities of the modern landscape.

Engaging a Managed Service Provider (MSSP) is crucial for organizations aiming to leverage advanced protection technologies and specialized expertise without the burden of maintaining extensive in-house resources. In today’s complex cyber landscape, MSSPs provide continuous monitoring, proactive threat detection, and rapid incident response services-essential elements for safeguarding sensitive data. For C-suite leaders, this partnership transcends a mere tactical decision; it embodies a strategic initiative to enhance security while optimizing costs, particularly through flat-rate pricing that simplifies budgeting. Notably, organizations utilizing MSSPs can reduce overall IT expenses by 20-30%, enabling more effective resource allocation.
Recent trends reveal that the MSSP market is on a robust growth trajectory, projected to reach $52.9 billion by 2028, with a compound annual growth rate (CAGR) of 11.5%. This growth is fueled by the increasing complexity of cyber threats and the rising demand for compliance solutions. Alarmingly, 72% of ransomware cases targeting small to midsize enterprises in 2024 involved double-extortion strategies, underscoring the urgent need for enhanced protective measures.
Real-world examples underscore the effectiveness of MSSP partnerships. Organizations adopting Managed Detection and Response (MDR) services report a remarkable 62% reduction in security incidents, showcasing the tangible benefits of outsourcing security functions. Moreover, MSSPs empower companies to concentrate on core business activities while ensuring robust protection against evolving threats. With cybercriminals increasingly targeting SMBs-over 50% of all cyberattacks are directed at this segment-partnering with an MSSP becomes a vital strategy for maintaining resilience and compliance in a challenging environment.
In summary, partnering with MSSPs not only enhances organizational protection but also offers substantial cost savings through flat-rate pricing. This makes it a critical consideration for C-suite leaders navigating the complexities of contemporary cybersecurity.

In today's digital landscape, real-time danger detection systems are not just beneficial; they are essential for identifying potential cyber risks as they arise. This capability allows organizations to respond swiftly and effectively, safeguarding their operations. By utilizing Cyber Solutions' 24/7 network monitoring and alert services, which deliver instant notifications and real-time insights, C-suite leaders can significantly diminish the risk of data breaches and other cyber incidents.
Consider the staggering financial implications: data breaches can cost organizations millions per incident. This proactive approach not only mitigates potential losses but also strengthens the organization’s overall security posture, ensuring compliance with industry regulations. Successful implementations of danger detection, bolstered by Cyber Solutions' advanced intelligence and comprehensive firewall services, have demonstrated effectiveness across various sectors, preventing breaches and enhancing operational resilience.
Cybersecurity specialists emphasize that early detection of risks is crucial for maintaining a robust defense. As Steve Wilson, Chief AI Officer, aptly states, "Security teams need to move faster, and with greater precision." This underscores the necessity for executives to prioritize these systems in their strategic planning. Are you ready to fortify your organization against emerging threats? The time to act is now.
In today's digital age, the importance of cybersecurity in healthcare cannot be overstated. A successful incident response strategy includes emergency IT support services and outlines the critical actions a company must take when a security breach occurs, such as:
For C-suite leaders, particularly CFOs, having a well-defined incident response strategy is essential for minimizing damage and ensuring a swift recovery. This is especially crucial in healthcare, where compliance with HIPAA standards is not just recommended but mandatory.
Investing in incident response capabilities is vital. Organizations should focus on comprehensive documentation, including:
By doing so, they can safeguard their reputation and uphold customer trust amidst cyber challenges. The rapid deployment of an incident response team, ideally within 24 hours, can significantly enhance recovery efforts with emergency IT support services. Case studies have shown that immediate action often leads to successful containment of ransomware threats, demonstrating the effectiveness of proactive strategies.
Such strategies not only ensure continuity of care but also bolster overall cybersecurity confidence. Are you prepared to face the evolving landscape of cyber threats? By prioritizing incident response, healthcare organizations can navigate these challenges effectively, ensuring they remain resilient in the face of adversity.
Vulnerability assessments are crucial for systematically evaluating a company's systems and networks to uncover potential security weaknesses. In today's landscape, where cyber threats are ever-evolving, C-suite leaders must prioritize these assessments to proactively safeguard their enterprises against emerging risks. This approach not only aids in maintaining compliance with industry regulations but also significantly reduces the risk of costly data breaches, which can average around $4.88 million per incident. Entities that conduct frequent vulnerability assessments are better positioned to identify and remediate weaknesses before they can be exploited, thereby protecting their financial health.
Recent trends indicate that 38% of reported vulnerabilities in 2025 were classified as High or Critical severity. This statistic underscores the urgency for organizations to prioritize vulnerability assessments. Cybersecurity professionals emphasize that a robust vulnerability management program is essential. As one expert noted, "Continuous monitoring and quick response to emerging threats are vital for maintaining a strong security posture." Moreover, organizations that frequently evaluate their vulnerabilities are more likely to fulfill compliance requirements, potentially saving them an average of $220,000 in expenses related to noncompliance.
For instance, financial institutions have fortified their defenses through continuous penetration testing and attack surface monitoring, effectively addressing vulnerabilities before they can be exploited. This proactive stance not only strengthens their security frameworks but also instills confidence among stakeholders regarding their commitment to data protection. At Cyber Solutions, we offer customized remediation plans to tackle compliance gaps, ensuring that your entity is equipped with the necessary documentation and processes for CMMC certification. Our expert audit support and continuous management of compliance changes further enhance your cybersecurity posture, allowing for minimal operational disruption. Additionally, our proactive network hardening strategies, including staff training on cybersecurity hygiene, ensure that your entity is well-prepared to defend against potential vulnerabilities.

Compliance as a Service (CaaS) is crucial for organizations striving to navigate the complex regulatory landscape. By outsourcing compliance management, C-suite leaders can focus on core business functions while ensuring they meet legal obligations. This strategic move not only mitigates the risk of non-compliance penalties but also bolsters the organization's reputation as a reliable player in its industry.
Consider this: entities leveraging CaaS have reported a remarkable decrease in compliance-related incidents. In fact, 72% of those implementing comprehensive compliance strategies have experienced fewer breaches. As regulatory frameworks continue to evolve, CaaS providers deliver ongoing support, empowering businesses to stay ahead of compliance demands.
Industry leaders emphasize that effective compliance management is essential for maintaining operational integrity and fostering stakeholder trust. This makes it a top priority for C-suite executives who aim to enhance their company's resilience and competitive edge. With CaaS, organizations can not only safeguard their operations but also position themselves as trustworthy entities in an increasingly scrutinized market.
Cybersecurity is not just a technical necessity; it’s a critical component of organizational integrity, especially in healthcare. With cyberattacks becoming increasingly sophisticated, C-suite leaders must prioritize penetration testing to safeguard their systems against potential breaches. This proactive approach not only identifies vulnerabilities but also demonstrates a robust commitment to cybersecurity, enhancing the organization’s reputation and trustworthiness among clients and stakeholders.
Current trends reveal that approximately 60% of companies conduct regular penetration tests, recognizing their vital role in uncovering essential vulnerabilities. However, many still view testing primarily as a compliance checkbox, which can create a false sense of security. Experts warn that an exclusive focus on compliance may widen the gap between protective measures and actual risk mitigation, leaving organizations vulnerable to advanced threats.
To effectively evaluate defenses against evolving risks, organizations are increasingly adopting Pen Testing as a Service (PTaaS). This innovative model allows for continuous validation without overburdening internal teams. It not only facilitates real-time threat detection but also ensures that assessments evolve alongside the dynamic landscape of cyber threats. By embedding penetration testing into the organizational culture, it shifts from a mere checklist item to an ongoing process of vulnerability discovery, ultimately fortifying defenses against potential breaches.
Cyber Solutions exemplifies a comprehensive cybersecurity strategy that incorporates a layered approach, including:
This strategy not only enhances recovery processes but also fosters strong partnerships with clients. By tailoring penetration testing to specific threat profiles, organizations can further bolster their security effectiveness, concentrating efforts on the areas most susceptible to breaches.
In today’s digital landscape, the importance of proactive strategies in emergency IT support is paramount. C-suite leaders must understand that implementing essential services - like 24/7 help desk support, endpoint protection, and comprehensive disaster recovery plans - not only safeguards their organizations against cyber threats but also bolsters operational resilience. By prioritizing these measures, executives can ensure their companies are equipped to navigate the complexities of modern cybersecurity challenges.
Key insights have surfaced regarding the various facets of emergency IT support services. The critical role of managed security service providers in mitigating risks cannot be overlooked, nor can the necessity of real-time threat detection and incident response strategies. Each element plays a vital role in strengthening an organization’s cybersecurity posture. Furthermore, vulnerability assessments and compliance management are essential for identifying weaknesses and maintaining regulatory adherence, ultimately protecting the organization’s financial health and reputation.
Moving forward, it is crucial for C-suite leaders to take decisive action in fortifying their organizations against potential threats. Investing in robust emergency IT support services and fostering a culture of cybersecurity awareness will not only minimize risks but also position businesses as reliable entities in an increasingly scrutinized market. The time to prioritize these essential services is now - ensuring that the organization remains resilient and secure in the face of evolving challenges.
What is the purpose of Cyber Solutions' 24/7 help desk support?
The purpose of Cyber Solutions' 24/7 help desk support is to provide emergency IT support services, ensuring immediate access to skilled IT professionals who can troubleshoot and resolve issues swiftly, minimizing downtime for organizations.
How does having emergency IT support services impact downtime and IT outages?
Companies with emergency IT support services experience 30% less downtime and 19% fewer IT outages, allowing them to maintain critical business operations without interruption.
What benefits do C-suite leaders gain from having emergency IT support services?
C-suite leaders can focus on strategic decision-making rather than being sidetracked by IT emergencies, which helps improve overall business operations.
How do emergency IT support services affect compliance and data breach risks?
Businesses with 24/7 emergency IT support services are more likely to comply with industry regulations and experience a 45% lower risk of data breaches, thus protecting organizational integrity.
Why is endpoint protection important for devices?
Endpoint protection is essential for safeguarding devices like laptops, smartphones, and tablets against cyber risks, preventing unauthorized access, data breaches, and mitigating financial losses and reputational damage.
What is application allowlisting and how does it enhance security?
Application allowlisting is a proactive strategy that prevents malware and unauthorized software from executing by ensuring that only authorized applications can operate, significantly reducing the attack surface and enhancing overall security.
What are the consequences of not having effective backup and disaster recovery solutions?
Without effective backup and disaster recovery solutions, organizations face the risk of data loss due to cyberattacks, natural disasters, or hardware failures, which can lead to significant downtime and financial losses.
How can a comprehensive backup plan impact a business after a cyberattack?
A comprehensive backup plan can drastically reduce downtime, as studies show that 60% of small businesses close within six months of a cyberattack, highlighting the financial implications of effective backup solutions.
What are Recovery Point Objective (RPO) and Recovery Time Objective (RTO)?
RPO and RTO are clear recovery objectives that help organizations navigate crises by ensuring they can restore operations within acceptable timeframes after disruptions.
What is the financial impact of downtime on businesses?
Estimates suggest that downtime can cost businesses upwards of $300,000 per hour, making it crucial for C-suite leaders to prioritize business continuity planning and emergency IT support services.