
In a world where digital threats are more prevalent than ever, the significance of managed security services companies cannot be overstated. Organizations are increasingly challenged by the complexities of cybersecurity, and a select group of providers is stepping up as leaders, offering innovative solutions tailored to the diverse needs of various industries.
This article delves into ten managed security services companies that are set to make a substantial impact in 2025, showcasing their unique offerings and the critical benefits they provide.
With the stakes at an all-time high, how can businesses effectively choose the right partner to navigate the ever-evolving landscape of cyber threats?
In today's digital age, the importance of cybersecurity in healthcare cannot be overstated. With increasing threats targeting sensitive patient information, healthcare organizations face unique challenges that demand immediate attention. In the managed security services companies landscape, Cyber Solutions Inc. stands out by offering a comprehensive range of cybersecurity solutions tailored specifically for sectors like healthcare, finance, and government.
Their offerings include:
This integrated approach not only enhances operational efficiency but also allows organizations to concentrate on their core functions while Cyber Solutions expertly navigates their IT complexities and security challenges. As of 2025, approximately 45% of healthcare entities and 38% of financial institutions are utilizing managed security services companies, highlighting the critical role these customized cybersecurity measures play in ensuring compliance and safeguarding sensitive information.
With a strong emphasis on personalized assistance and deep industry expertise, Cyber Solutions has established itself as a trusted partner for businesses maneuvering through the intricate landscape of contemporary IT environments. Are you ready to fortify your organization against the evolving cybersecurity threats? Let Cyber Solutions guide you in securing your digital assets and maintaining compliance in an increasingly complex world.
Cybersecurity is not just a technical necessity; it’s a critical component of operational integrity in healthcare. As cyber threats evolve, organizations must adapt to safeguard sensitive patient data and comply with stringent regulations. IBM Protection is at the forefront of managed security services companies, leveraging advanced technologies to tackle the ever-changing landscape of cyber risks.
With services like AI-powered risk detection and incident management, IBM equips healthcare entities to enhance their protective measures. The market for managed security services companies is projected to grow at a compound annual growth rate (CAGR) of 12% from 2025 to 2032, underscoring the urgent demand for innovative cybersecurity solutions. This growth is particularly evident in the healthcare sector, which is also expected to expand at a CAGR of 12%, driven by increasing regulatory pressures and the imperative for robust patient data protection.
IBM's commitment to innovation empowers organizations to proactively defend against cyber threats while ensuring compliance with industry standards. Their extensive experience across various sectors, especially healthcare and finance, enables them to deliver tailored security solutions that align with specific business objectives. For instance, the integration of AI-driven risk detection significantly enhances incident response capabilities, allowing companies to react swiftly to potential breaches and minimize risk exposure.
As the MSS market continues to expand, IBM's strategic focus on AI technologies positions them as a leader among managed security services companies in delivering comprehensive analytics and incident response solutions. This ensures that clients can effectively navigate the complexities of modern cybersecurity challenges. Are you ready to elevate your organization's cybersecurity posture? With IBM, you can stay ahead of the curve and protect what matters most.

In today's digital landscape, cybersecurity is not just a necessity; it's a critical component of operational integrity for organizations across all sectors. Secureworks excels in proactive danger detection and incident response, equipping businesses with essential tools and expertise to effectively combat cyber risks. Their state-of-the-art operations center (SOC) leverages real-time threat intelligence, enabling the identification and neutralization of potential risks before they escalate into significant issues.
Looking ahead to 2025, the average response time for incident response services is expected to improve, allowing businesses to recover swiftly from breaches and maintain operational continuity. This proactive approach not only strengthens the protective stance of organizations but also significantly enhances overall business resilience. Many organizations have effectively harnessed Secureworks' SOC capabilities, resulting in decreased downtime and improved incident management. This highlights the importance of their comprehensive protection solutions in navigating the complex cybersecurity landscape.

In today's digital landscape, the importance of cybersecurity cannot be overstated. AT&T Cybersecurity stands at the forefront, merging its telecommunications expertise with cutting-edge protective solutions to offer a distinctive approach among managed security services companies. This integration is crucial for organizations navigating the complex and ever-evolving realm of cyber threats.
Their comprehensive suite of services encompasses:
All tailored to meet the specific needs of businesses. With a robust network infrastructure, AT&T ensures real-time monitoring and swift response capabilities, empowering organizations to defend against attacks while maintaining uninterrupted communication. This strategic alignment not only enhances operational efficiency but also fortifies the overall security posture of businesses.
As we look ahead to 2025, the sophistication of cyber threats continues to escalate. Organizations are increasingly recognizing that effective network protection is vital for ensuring business continuity and safeguarding sensitive information. The significance of integrated cybersecurity solutions offered by managed security services companies is paramount, as they provide the necessary tools to combat these advanced threats head-on.
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially for organizations navigating complex regulatory environments. Trustwave stands out as a leading provider of managed protection solutions, seamlessly integrating compliance management with robust defense options. Their comprehensive offerings include:
As we look ahead to 2025, a staggering percentage of businesses will face penalties for non-compliance, with the average cost of a data breach soaring to $4.88 million. This alarming statistic underscores the critical need for effective compliance strategies. Trustwave's expertise in navigating intricate regulatory frameworks, such as HIPAA and PCI-DSS, positions them as a trusted ally for organizations aiming to bolster their protective measures while ensuring adherence to regulations.
Consider this: organizations that conduct regular vulnerability assessments significantly enhance their protection frameworks. This proactive approach not only improves risk visibility but also accelerates issue detection. Trustwave's commitment to compliance management empowers businesses to mitigate risks effectively, helping them avoid costly penalties. In a challenging regulatory landscape, partnering with Trustwave is not just beneficial; it’s essential for safeguarding your organization’s future.
In today's digital landscape, the importance of robust cybersecurity cannot be overstated. Verizon Managed Security Services leverages its extensive network infrastructure to deliver tailored security solutions that meet the unique challenges faced by businesses. Their offerings include:
All designed to protect organizations from the ever-evolving cyber threats.
By harnessing global network visibility, Verizon can swiftly detect and counter risks in real-time. This proactive approach not only strengthens security but also enhances operational efficiency, positioning Verizon as a trusted partner for companies seeking reliable managed solutions. Recent success stories underscore how Verizon's proactive risk detection has enabled organizations to effectively mitigate threats, reinforcing the critical need for comprehensive protective measures in today's cyber environment.
As cyber risks continue to escalate, the emphasis on immediate detection and incident management remains paramount. This focus solidifies Verizon's leadership in the managed security sector, paving the way for businesses to thrive securely in 2025 and beyond.
In today's digital landscape, cybersecurity is not just an option; it's a necessity for businesses across all sectors. BT Managed Security Services stands at the forefront, delivering tailored cybersecurity solutions that address the unique challenges organizations face. With a robust global presence, BT offers a comprehensive suite of services, including:
This ensures that businesses can navigate the complexities of modern threats.
As cyber risks evolve, organizations must grapple with the implications of these threats on their operations and compliance. BT's deep understanding of the specific challenges faced by businesses allows them to craft solutions that not only enhance security but also ensure adherence to ever-changing regulations. This dual focus on safety and compliance positions BT as a vital partner among managed security services companies in the security landscape.
Moreover, BT's commitment to innovation and a customer-centric approach underscores its role as a key player in the cybersecurity arena. In an environment where threats are increasingly sophisticated, the demand for effective cybersecurity strategies has never been more urgent. BT is poised to meet this demand, providing organizations with the tools they need to protect their assets and maintain trust with their stakeholders.
In today's digital landscape, cybersecurity is not just a necessity; it's a critical component for any organization, especially in healthcare. NTT Security stands out with its cutting-edge cybersecurity solutions and a robust customer-centric approach. Their offerings include:
By leveraging advanced technologies like AI and machine learning, NTT Security provides proactive protective measures that evolve alongside emerging threats. This dedication to innovation and client satisfaction not only enhances organizational cybersecurity postures but also positions NTT as a reliable partner for enterprises navigating the complexities of modern digital environments.
As organizations increasingly adopt AI-powered solutions, NTT's focus on integrating these technologies into their offerings reflects current trends in cybersecurity for 2025. This ensures that clients remain resilient against advanced cyber risks, empowering them to thrive in an ever-changing landscape. Are you ready to fortify your defenses with a partner that understands the intricacies of cybersecurity?
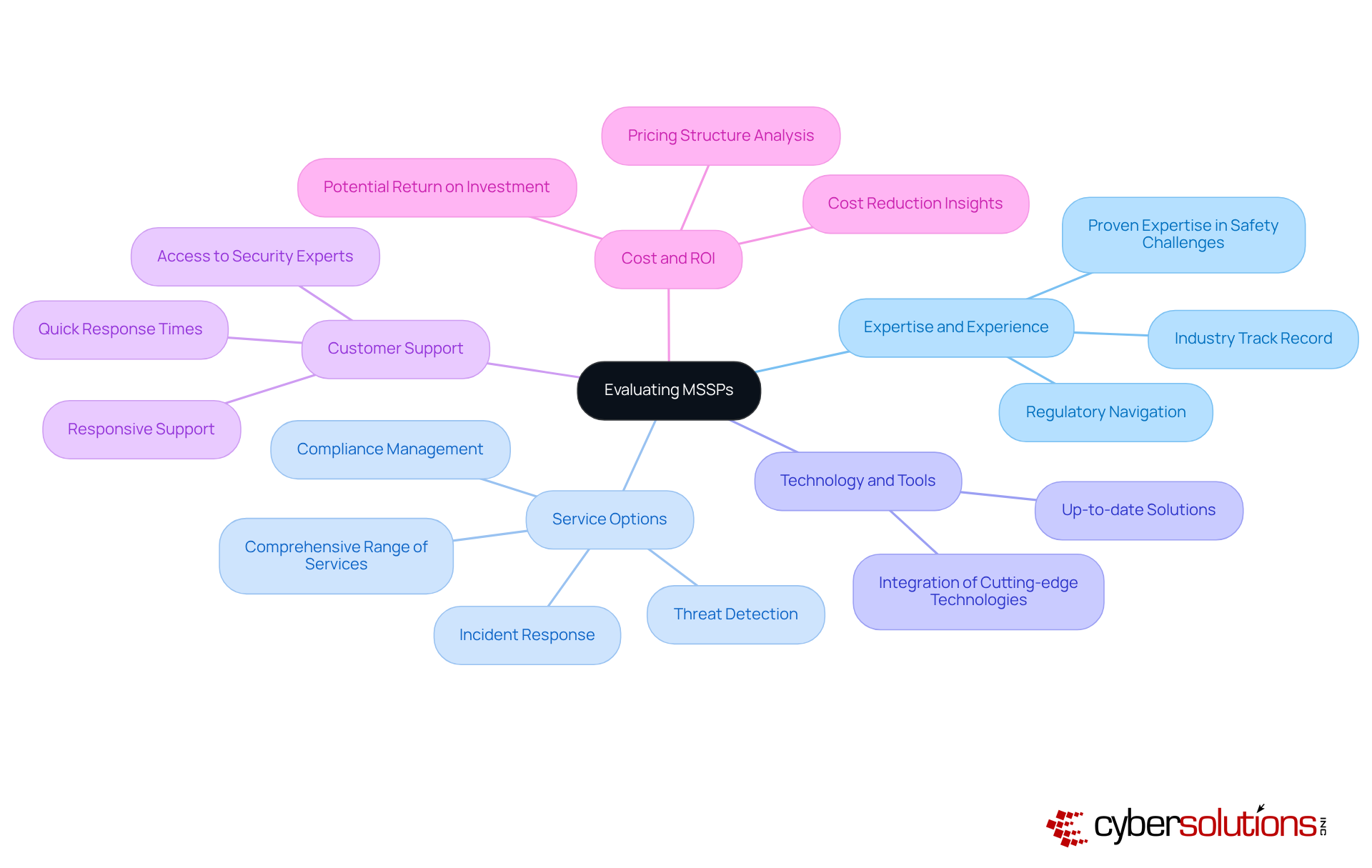
Choosing the right managed security services companies is crucial for organizations aiming to bolster their security posture. With the ever-evolving landscape of cyber threats, it’s essential to evaluate several critical factors to ensure you select a partner that meets your specific security needs.
Expertise and Experience: Assessing the MSSP's track record within your industry is vital. A provider with proven expertise in addressing unique safety challenges can significantly enhance your organization’s resilience against threats. In fact, by 2025, 60% of enterprises will prioritize expertise when partnering with MSSPs, especially in navigating complex regulatory environments. Are you ready to align with a provider that understands your industry's intricacies?
Service Options: Ensure that the MSSP offers a comprehensive range of services tailored to your protection needs. This should encompass essential capabilities such as threat detection, incident response, and compliance management. As demand for specialized services grows, organizations are increasingly seeking managed security services companies that can provide advanced solutions to meet their evolving security requirements.
Technology and Tools: Evaluate the technologies and tools employed by the MSSP to protect your organization. It’s crucial that these solutions are up-to-date and effective, given the rapid evolution of cyber threats. The integration of cutting-edge technologies can significantly enhance the MSSP's ability to mitigate risks and respond to incidents promptly.
Customer Support: The level of customer support provided by the MSSP is a key consideration. Look for providers that offer responsive support, including quick response times and access to security experts. By 2025, 96% of businesses will consider predictability in IT budgets as extremely important when working with MSSPs. Is your potential partner equipped to provide the support you need?
Cost and ROI: Analyze the MSSP's pricing structure and evaluate the potential return on investment. It’s essential to ensure that the services offered deliver tangible benefits to your organization. Research indicates that entities collaborating with MSSPs can reduce overall IT expenses by 20-30%, underscoring the importance of assessing the cost-effectiveness of the services provided.
By focusing on these essential elements, companies can make informed decisions when selecting managed security services companies, ensuring they partner with a provider that aligns with their security goals and operational requirements.
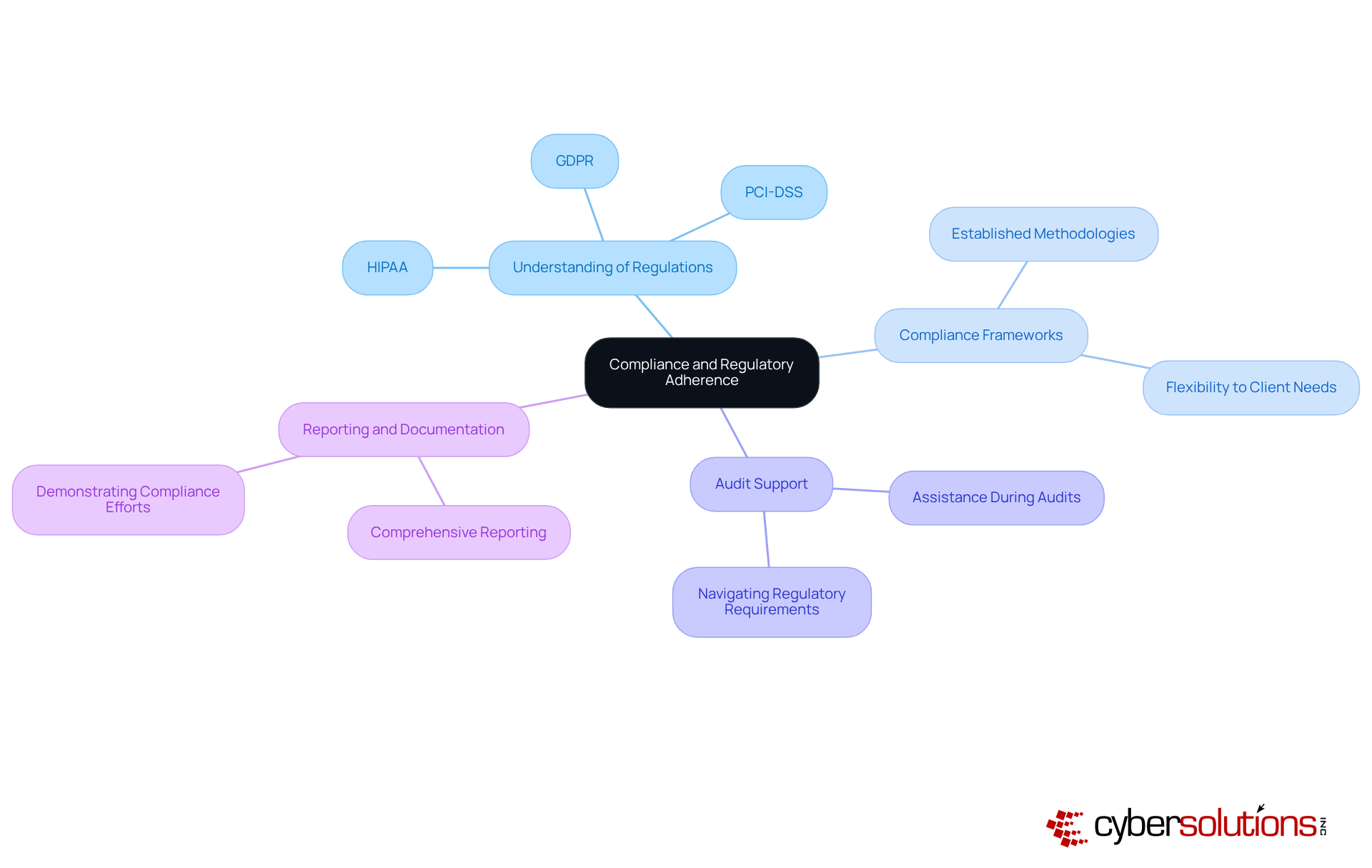
Compliance and regulatory adherence are not just important; they are essential for organizations, particularly in highly regulated sectors like healthcare and finance. As cybersecurity threats continue to evolve, the need for robust compliance measures becomes increasingly critical. When selecting a managed security service provider (MSSP), organizations must prioritize several key factors:
By focusing on these compliance-related factors, organizations can choose managed security services companies that not only enhance their security posture but also ensure adherence to vital regulatory requirements. This strategic selection fosters trust and resilience in their operations.
The landscape of managed security services is evolving rapidly, underscoring the critical importance of cybersecurity in today’s digital age. Companies like Cyber Solutions Inc., IBM Security, Secureworks, and others are at the forefront, delivering innovative solutions tailored to the unique needs of various industries. As organizations increasingly recognize the necessity of robust cybersecurity measures - especially in sectors like healthcare and finance - the role of these managed services companies becomes indispensable. Their expertise not only enhances security protocols but also ensures compliance with complex regulatory frameworks, allowing businesses to concentrate on their core operations.
Key insights have emerged regarding the capabilities and strengths of various managed security services providers:
As the demand for managed security services continues to grow, organizations must evaluate potential partners with care. Factors such as expertise, service options, technology, customer support, and cost-effectiveness are crucial in selecting the right MSSP. By prioritizing these elements, businesses can enhance their security posture and navigate the complexities of the cyber threat landscape more effectively. Embracing the right managed security services provider is not merely a strategic decision; it is essential for safeguarding assets and ensuring long-term operational resilience in an increasingly digital world.
What cybersecurity services does Cyber Solutions Inc. offer?
Cyber Solutions Inc. offers a comprehensive range of cybersecurity services, including 24/7 help desk assistance, endpoint protection, backup and disaster recovery, compliance as a solution (CaaS), and co-managed IT support.
Why is cybersecurity particularly important in healthcare?
Cybersecurity is crucial in healthcare due to the increasing threats targeting sensitive patient information, which poses unique challenges that require immediate attention to ensure compliance and safeguard data.
How does Cyber Solutions Inc. help organizations focus on their core functions?
By providing integrated cybersecurity solutions, Cyber Solutions Inc. allows organizations to concentrate on their core functions while managing IT complexities and security challenges.
What is the projected growth of managed security services companies in the healthcare sector?
The market for managed security services companies in the healthcare sector is expected to grow at a compound annual growth rate (CAGR) of 12% from 2025 to 2032.
What advanced technologies does IBM Security utilize for cybersecurity?
IBM Security leverages advanced technologies such as AI-powered risk detection and incident management to enhance protective measures against cyber threats.
How does Secureworks enhance incident response capabilities?
Secureworks enhances incident response capabilities through its state-of-the-art operations center (SOC), which uses real-time threat intelligence to identify and neutralize potential risks before they escalate.
What benefits do organizations experience by using Secureworks' services?
Organizations using Secureworks' services experience decreased downtime and improved incident management, which strengthens their overall business resilience and protective stance.
What is the importance of compliance in cybersecurity for organizations?
Compliance is essential in cybersecurity as it helps organizations meet regulatory requirements and protect sensitive information from cyber threats, ensuring operational integrity.