In today's digital landscape, small businesses are facing an alarming surge in cyber threats, particularly ransomware attacks that can devastate operations and compromise sensitive data. The stakes have never been higher; statistics show that countless organizations have fallen victim to endpoint breaches, underscoring the urgent need for robust protection strategies.
This article explores ten essential tactics that small enterprises can implement to strengthen their defenses against ransomware. It emphasizes not only the necessity of proactive measures but also the critical vulnerabilities that many organizations still overlook.
How ready is your business to tackle these ever-evolving threats?
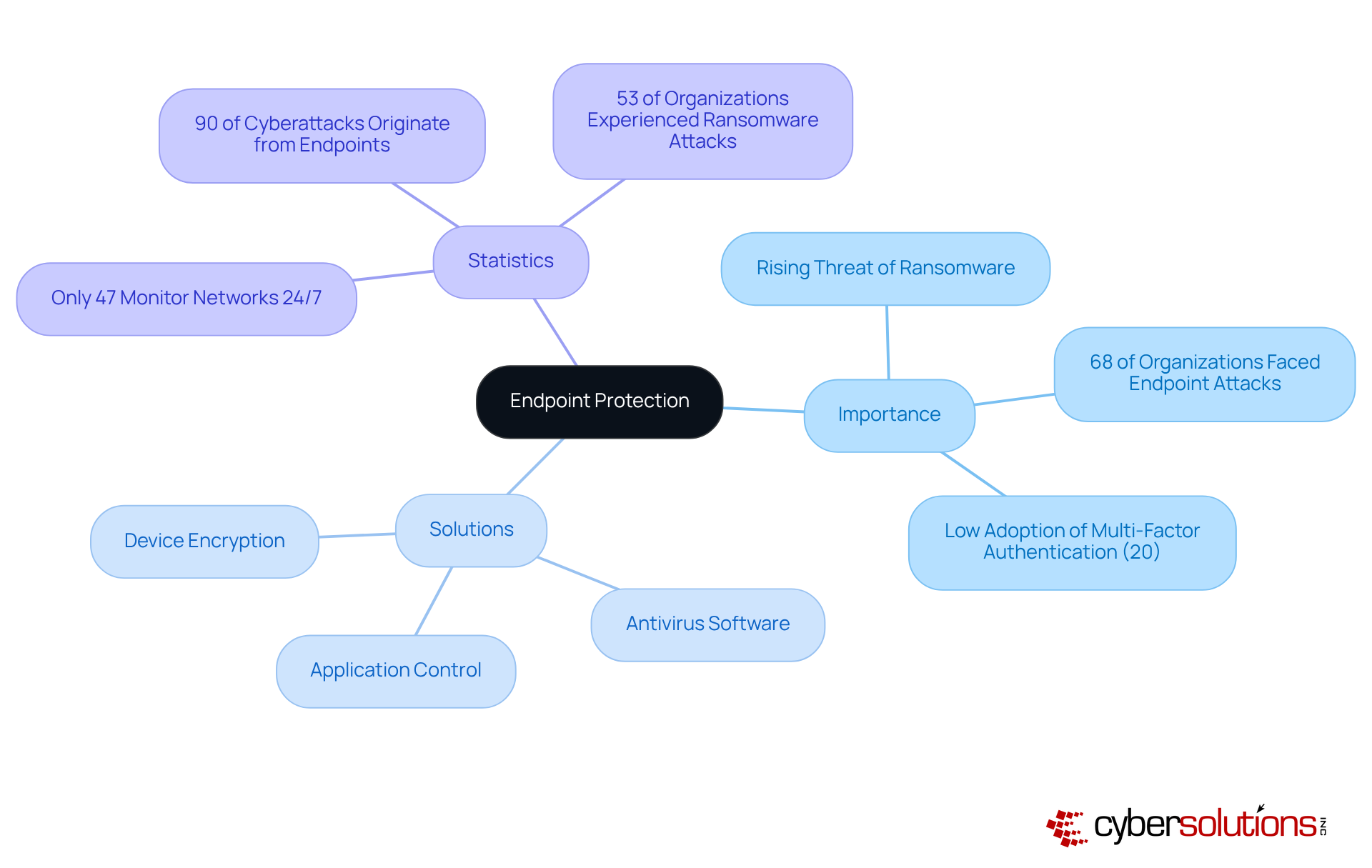
Endpoint protection is not just important; it's essential for small enterprises aiming to defend against the rising tide of ransomware attacks. Did you know that 68% of organizations have faced endpoint attacks that compromised their data? This alarming statistic underscores the necessity of implementing robust protection measures.
Cyber Solutions Inc. stands ready to provide advanced endpoint protection solutions tailored specifically for small businesses. Our offerings include:
All designed to meet your unique needs. These solutions enable early identification and response to threats, safeguarding sensitive data before breaches can occur. Regular updates and continuous monitoring are crucial to maintaining the effectiveness of endpoint protection against ever-evolving threats.
Currently, only 20% of small enterprises have adopted multi-factor authentication, highlighting a significant gap in security measures. By prioritizing endpoint protection, organizations can dramatically reduce their vulnerability to malicious software. This proactive approach not only ensures operational continuity but also protects your bottom line. Don't wait for an attack to happen - take action now to secure your business's future.
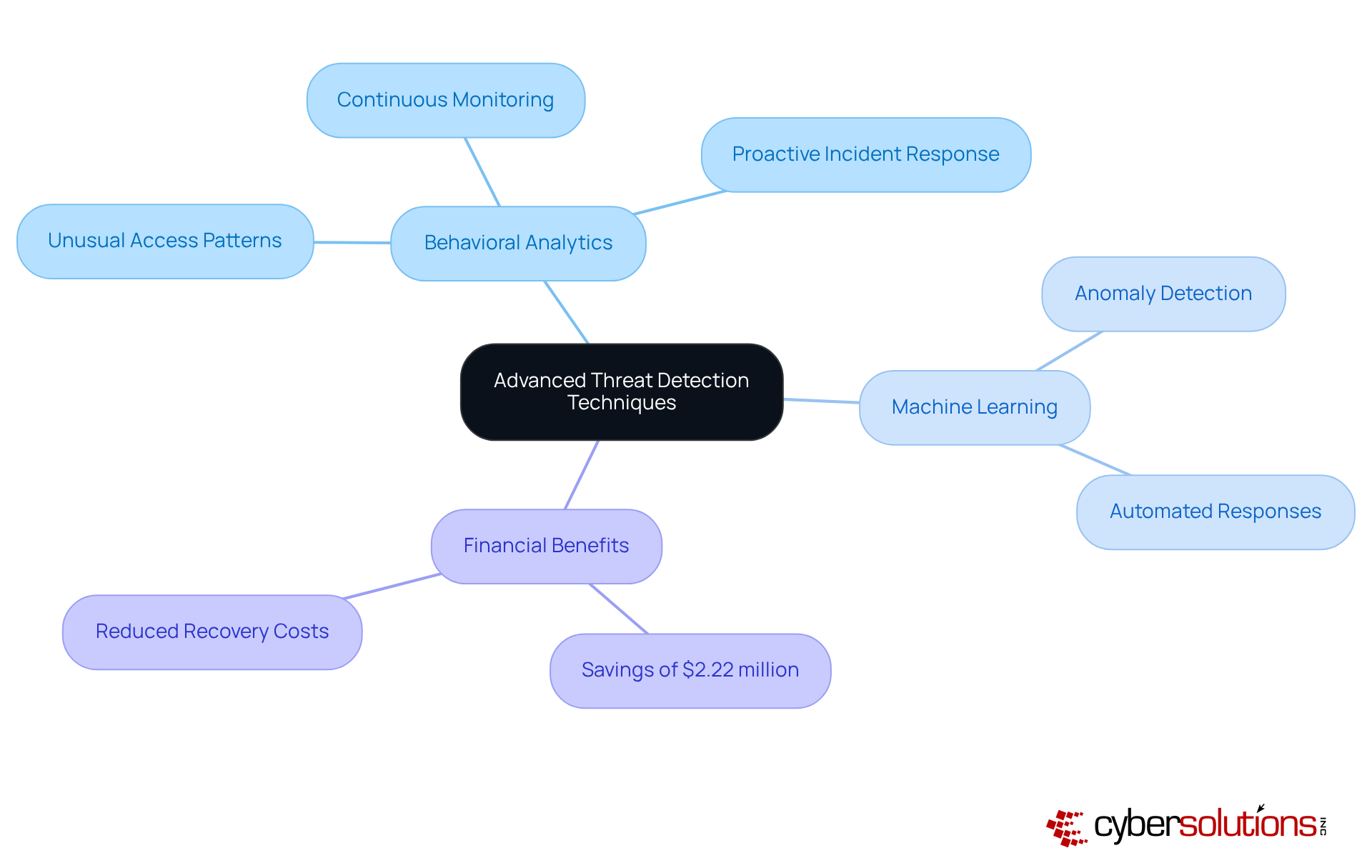
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in the healthcare sector. With the rise of small business ransomware threats, small enterprises must adopt advanced intrusion detection methods, such as behavioral analytics and machine learning, to bolster their defenses against such attacks. These technologies enable organizations to continuously monitor network traffic and user behavior, swiftly identifying anomalies that may signal an impending attack.
For example, behavioral analytics can flag unusual access patterns, like accessing sensitive financial data at odd hours, as highly suspicious. This proactive strategy not only enhances the ability to respond to potential risks from small business ransomware but also significantly reduces damage and recovery costs. In fact, recent findings reveal that organizations leveraging AI and automation in their security measures have saved an average of $2.22 million in breach costs. This underscores the financial benefits of adopting such technologies.
As cyber threats evolve, incorporating behavioral analytics into cybersecurity strategies is becoming essential for early detection and effective incident response. This approach empowers organizations to stay ahead of potential risks. Case studies further support this, demonstrating how quick incident response and a structured strategy can improve cybersecurity, particularly in industries like healthcare. Here, prompt action and specialized knowledge are crucial in mitigating the effects of cyberattacks.
In conclusion, the integration of advanced intrusion detection methods is not just a technical upgrade; it's a vital step toward safeguarding sensitive information and ensuring the resilience of healthcare organizations against the ever-growing threat of cybercrime.
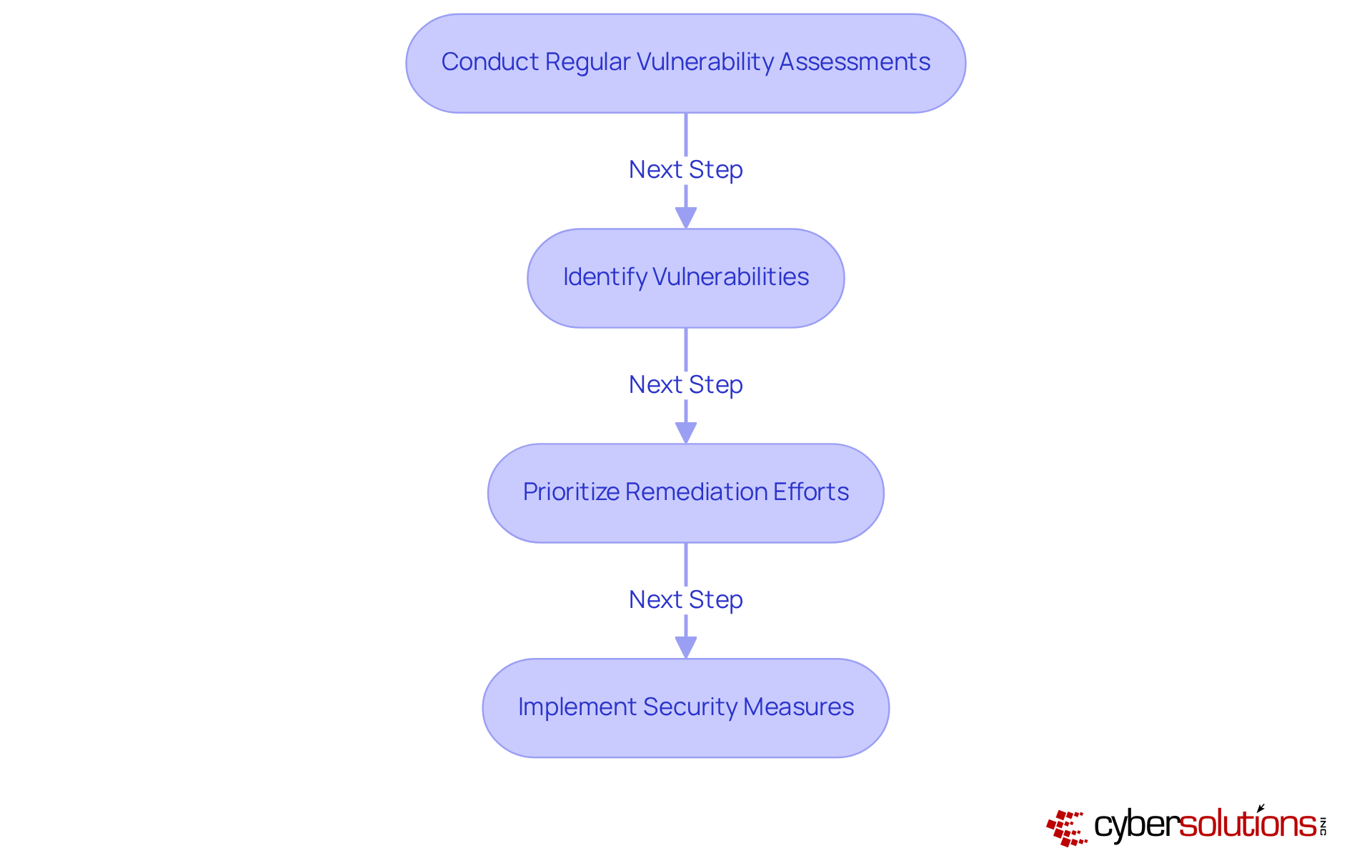
Routine vulnerability evaluations are crucial for small enterprises aiming to proactively identify and address security flaws that could be exploited by small business ransomware. Did you know that over 86% of small and medium-sized enterprises have conducted a cybersecurity risk assessment? Yet, many still struggle with effectively managing vulnerabilities. Cyber Solutions Inc. offers comprehensive vulnerability assessment services tailored to evaluate the security posture of your IT infrastructure. By systematically identifying vulnerabilities and prioritizing remediation efforts, organizations can significantly reduce their risk of small business ransomware attacks.
Cybersecurity professionals stress that without regular assessments, organizations remain vulnerable to potential breaches, which can lead to devastating financial and reputational damage. Real-world examples demonstrate that organizations conducting regular vulnerability evaluations not only enhance their security stance but also build trust with clients by showcasing their commitment to data protection. As the landscape of cyber threats evolves, adopting a proactive approach to vulnerability management is essential for long-term organizational resilience.
In conclusion, investing in routine vulnerability assessments is not just a precaution; it's a strategic move that can safeguard your organization against the ever-changing threats in the cyber landscape.
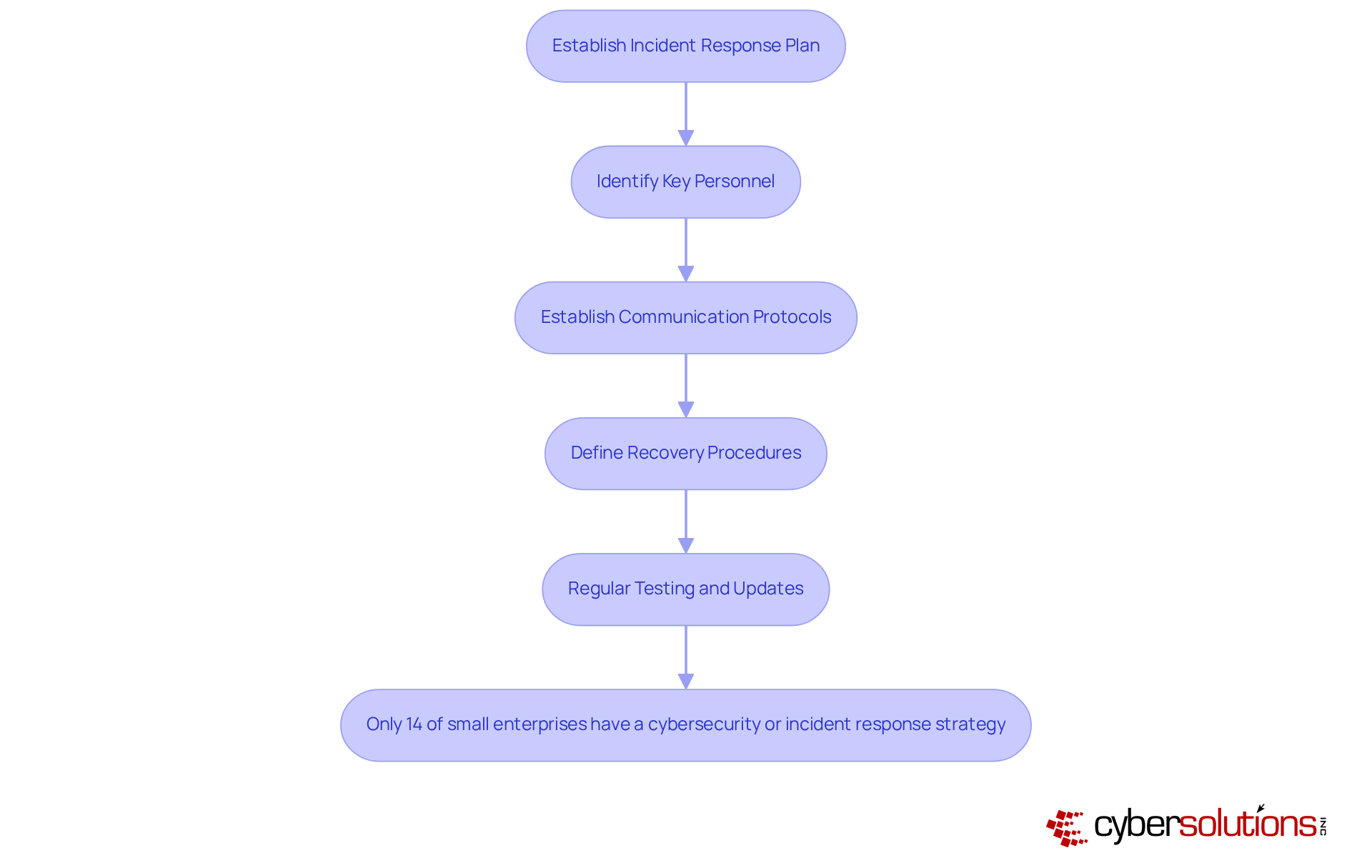
A successful incident response strategy is essential for small enterprises to effectively combat small business ransomware attacks. Cyber Solutions Inc. specializes in assisting organizations in developing tailored incident response plans that clearly delineate the necessary actions during a cyber incident. This involves:
Regular testing and updates to the plan are vital; organizations that conduct such exercises at least semi-annually can reduce breach costs by an average of $1.49 million. Alarmingly, only 14% of small enterprises currently possess a cybersecurity or incident response strategy, leaving a staggering 86% vulnerable to potential breaches.
By proactively preparing and consistently enhancing their incident response strategies, small businesses can significantly mitigate the impact of small business ransomware attacks. It's time for these organizations to take action and safeguard their operations against the ever-evolving landscape of cyber threats.
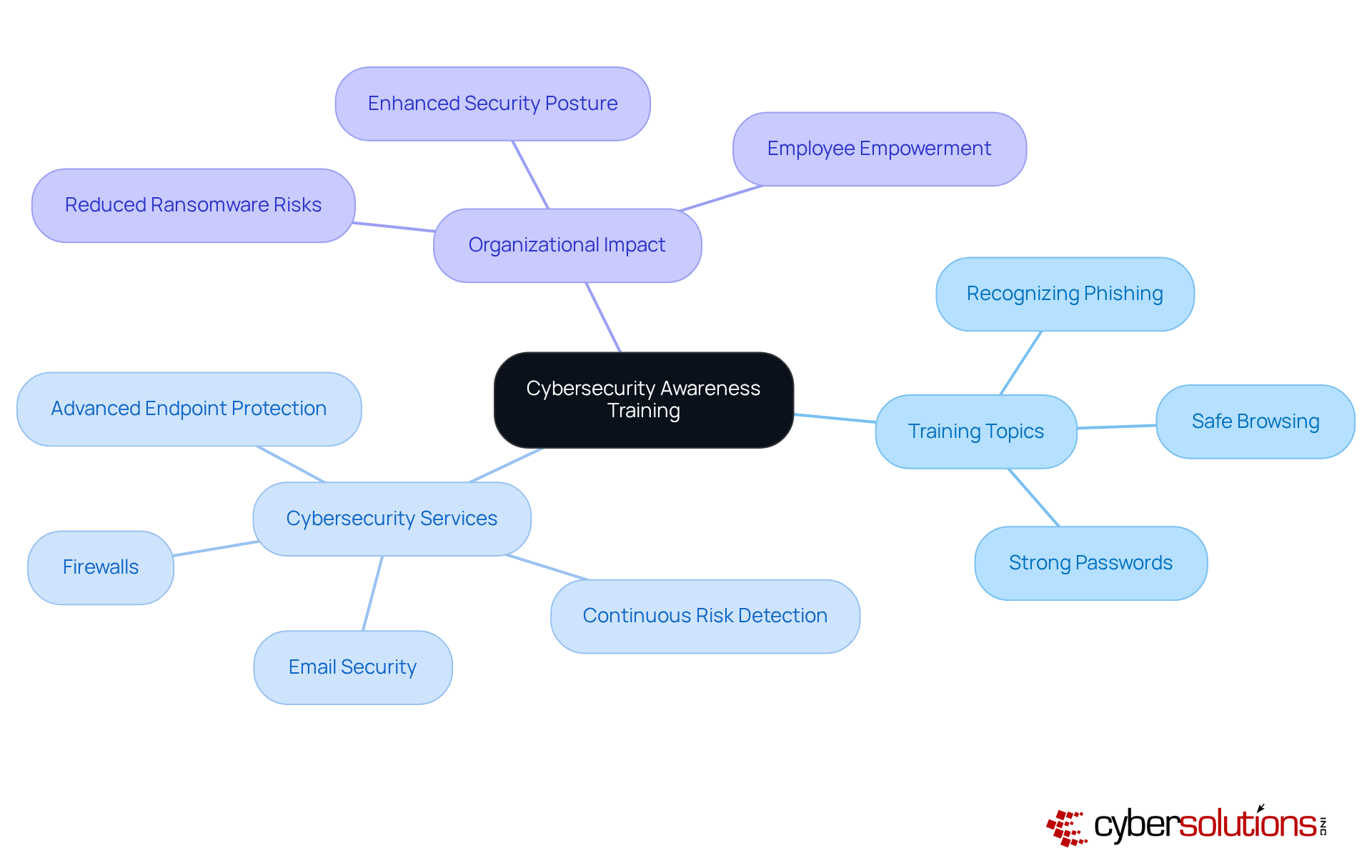
In today's digital landscape, training employees on cybersecurity awareness stands as one of the most effective strategies to thwart ransomware attacks. Cyber Solutions Inc. offers tailored training programs designed to equip staff with the skills to recognize phishing attempts, practice safe browsing, and understand the significance of strong passwords.
But training is just the beginning. Cyber Solutions also provides a comprehensive suite of cybersecurity services, including:
By fostering a culture of security awareness and empowering employees with the knowledge to identify potential threats, organizations can transform their workforce into a formidable first line of defense against cyber risks.
Moreover, with 24/7 threat monitoring, Cyber Solutions ensures that any suspicious activities are swiftly detected and addressed, significantly enhancing the overall security posture of the organization. In an era where cyber threats are ever-evolving, can your organization afford to overlook the importance of cybersecurity training?
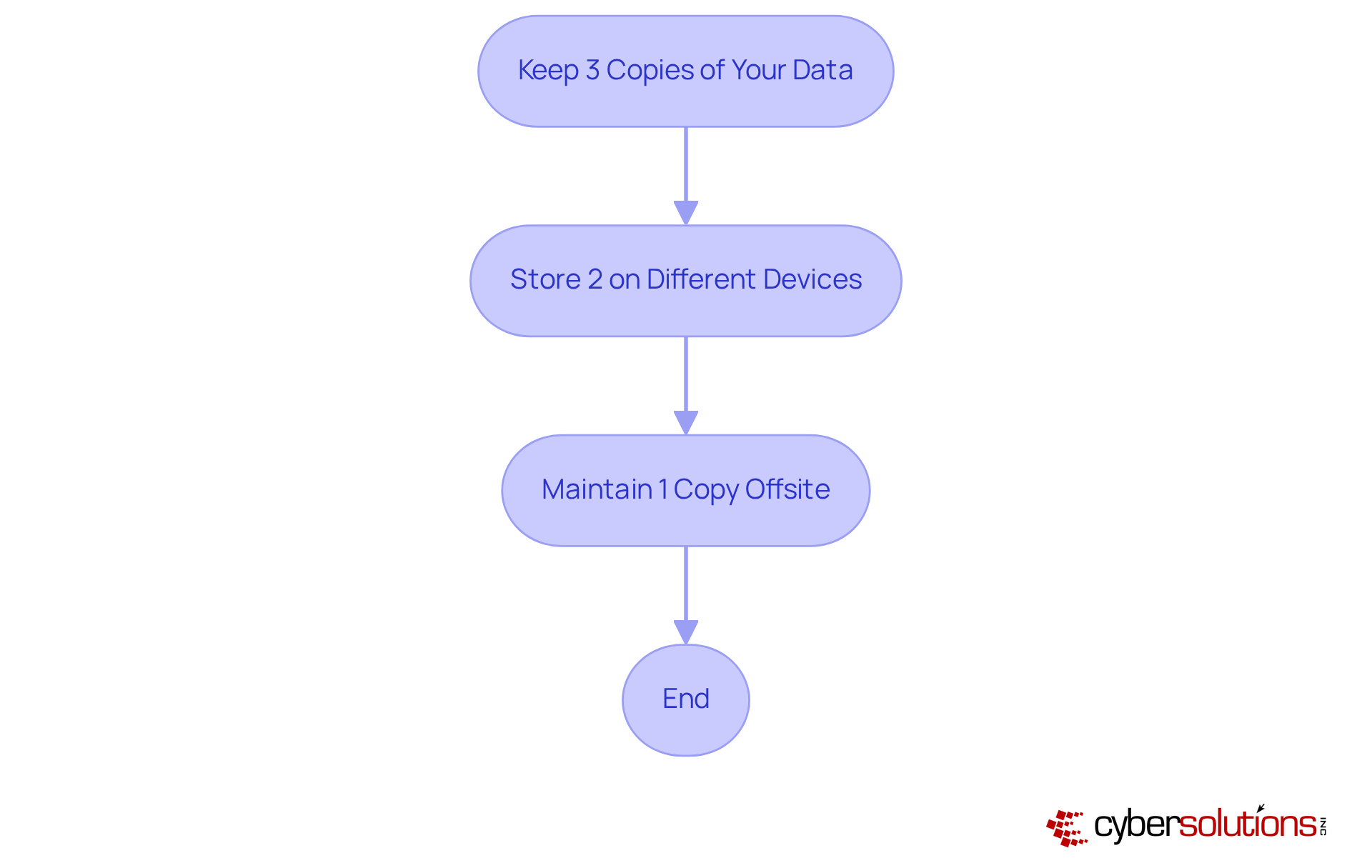
Establishing regular data backup protocols is crucial for minor enterprises aiming to recover swiftly from ransomware attacks. The 3-2-1 backup strategy stands out as a highly recommended approach:
This method not only protects against data loss but also facilitates rapid system restoration, significantly minimizing downtime during an attack.
Despite its effectiveness, research reveals that fewer than 20% of minor enterprises implement this strategy, exposing a significant gap in preparedness. Cybersecurity experts warn that overlooking regular backups can lead to catastrophic outcomes, as many organizations find their backup data inaccessible only after a breach occurs.
Real-world applications of the 3-2-1 strategy demonstrate its resilience. For instance, organizations that diversified their storage solutions across local disks, cloud services, and physical media reported improved data protection and recovery capabilities. A recent case involving Cyber Solutions showcased their rapid incident response, restoring 4,500 endpoints for a healthcare provider, underscoring how the 3-2-1 strategy was pivotal in their recovery process.
By adopting this proactive approach, minor enterprises can fortify their defenses against the escalating threat of ransomware. Are you prepared to safeguard your organization? The time to act is now.
In today's digital landscape, ensuring adherence to cybersecurity regulations is not just important - it's essential for small enterprises to avoid small business ransomware attacks, protect sensitive information, and avoid legal penalties. Cyber Solutions Inc. stands out by simplifying this process through its Compliance as a Service (CaaS) offerings. These services encompass:
By implementing necessary security measures and conducting regular compliance audits, organizations can effectively align their cybersecurity practices with regulatory requirements. This alignment not only enhances their overall security posture but also significantly reduces the risk of attacks from small business ransomware. Have you considered how a robust compliance strategy could safeguard your organization?
Moreover, our CaaS solutions provide vital support for audit preparation, ensuring that organizations are well-equipped to meet compliance standards and mitigate potential penalties. With Cyber Solutions Inc. at your side, you can navigate the complexities of cybersecurity with confidence, knowing that your compliance needs are in expert hands.

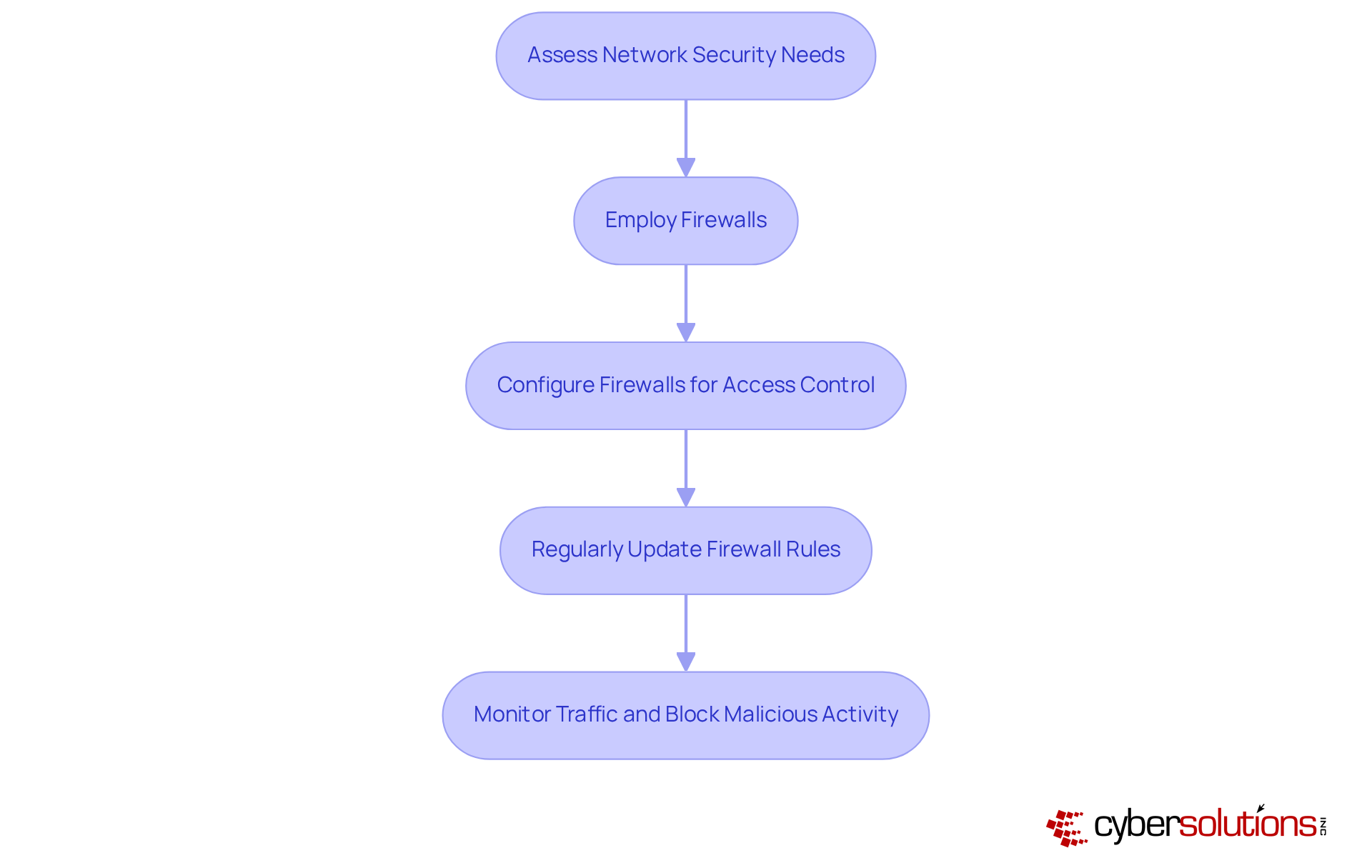
In today's digital landscape, safeguarding enterprise networks is more critical than ever. Cybersecurity threats are rampant, and organizations must take proactive measures to protect themselves. Employing firewalls is essential for defending minor enterprise networks against unauthorized access and potential malware attacks.
Cyber Solutions offers advanced firewall solutions that not only monitor but also filter incoming and outgoing traffic, effectively blocking malicious activity. By configuring firewalls to enforce strict access controls and regularly updating firewall rules, organizations can significantly reduce their risk of malware infiltration. This proactive approach not only protects sensitive data but also fosters trust among clients and stakeholders.
Consider the implications: without robust firewall protection, organizations expose themselves to significant vulnerabilities. Cyber Solutions stands ready to address these challenges, ensuring that your network remains secure against evolving threats. Don't leave your cybersecurity to chance-take action today to fortify your defenses.
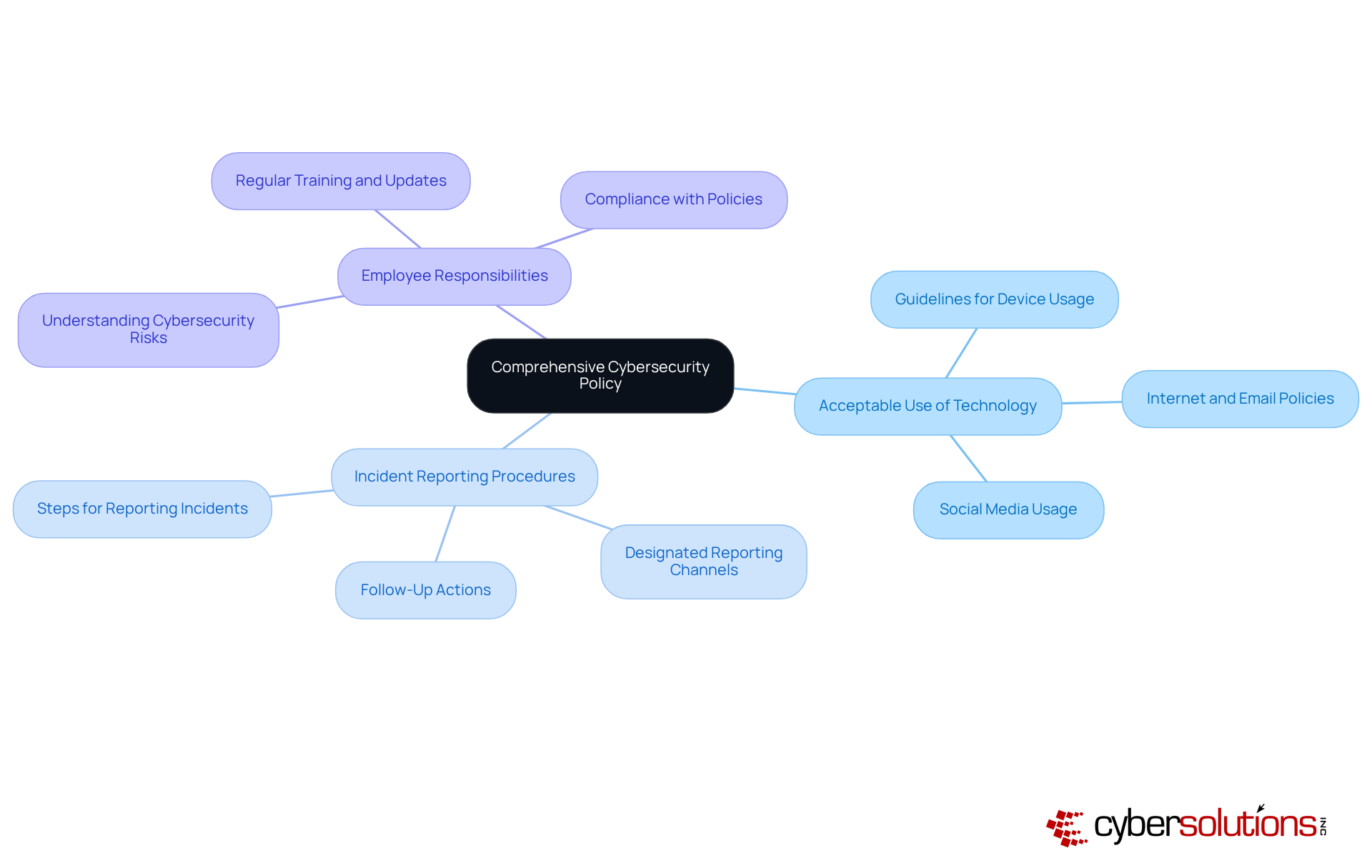
Establishing a robust cybersecurity policy is essential for small businesses to protect against small business ransomware by setting clear guidelines and expectations for their staff. In an era where cyber threats are increasingly sophisticated, organizations must prioritize their defenses. Cyber Solutions Inc. specializes in developing tailored cybersecurity policies that specifically address unique risks and compliance requirements.
Such a policy should encompass:
This ensures that every team member understands their role in safeguarding the organization against cyber attacks. Research indicates that organizations with well-defined cybersecurity policies are significantly better equipped to mitigate risks. For instance, 76% of small enterprises that increased their cybersecurity investments reported heightened concerns over small business ransomware, underscoring the urgent need for strong policies.
Real-world examples further illustrate that organizations implementing comprehensive cybersecurity measures have effectively reduced their vulnerability to ransomware. This highlights the critical importance of proactive risk management in today’s digital landscape. By partnering with Cyber Solutions Inc., small enterprises can fortify their defenses against small business ransomware and navigate the complexities of cybersecurity with confidence.
In today's digital landscape, cybersecurity is not just an option for small enterprises; it's a necessity. Collaborating with a managed security service provider (MSSP) like Cyber Solutions Inc. can significantly enhance your organization's cybersecurity capabilities. With extensive managed security services that include 24/7 monitoring, risk detection, and incident response, Cyber Solutions ensures that your business is well-equipped to face evolving cyber threats.
Consider the unique challenges that small enterprises face in safeguarding their sensitive data. Cyber Solutions offers advanced cybersecurity solutions such as:
These services are designed to protect organizations against the increasing risks of ransomware attacks and other cyber threats. By leveraging the expertise of Cyber Solutions, businesses can access cutting-edge security technologies and resources that might otherwise be beyond their budget.
Why risk your organization's security when you can partner with experts who understand the landscape? With Cyber Solutions, you gain not only robust protection but also peace of mind, knowing that your cybersecurity needs are in capable hands. Don't wait for a breach to occur; take action now to secure your enterprise's future.
In today's digital landscape, the escalating threat of ransomware demands that small businesses prioritize comprehensive cybersecurity strategies. Protecting sensitive data and maintaining operational integrity is not just advisable; it's essential. By implementing effective measures - such as endpoint protection, advanced threat detection, and regular vulnerability assessments - businesses can significantly reduce their risk of falling victim to cyberattacks. The proactive steps outlined here serve as a crucial roadmap for small enterprises aiming to bolster their defenses against the ever-evolving landscape of cyber threats.
Key strategies include:
Each of these elements is vital in creating a resilient cybersecurity posture that safeguards valuable information and fosters trust with clients and stakeholders. Moreover, leveraging partnerships with managed security service providers can enhance the security capabilities of small businesses, granting access to advanced technologies and expertise that may otherwise be out of reach.
Ultimately, the responsibility of protecting an organization from ransomware lies with its leadership. By taking decisive action today - whether through investing in cybersecurity training, implementing regular data backups, or establishing comprehensive cybersecurity policies - small businesses can mitigate risks and secure their future. The time to act is now; the safety and success of your organization depend on it.
Why is endpoint protection essential for small enterprises?
Endpoint protection is essential for small enterprises to defend against the rising tide of ransomware attacks. Statistics show that 68% of organizations have faced endpoint attacks that compromised their data, highlighting the need for robust protection measures.
What solutions does Cyber Solutions Inc. offer for endpoint protection?
Cyber Solutions Inc. offers advanced endpoint protection solutions tailored for small businesses, including antivirus software, application control, and device encryption. These solutions help in early identification and response to threats, safeguarding sensitive data.
What is the importance of regular updates and monitoring in endpoint protection?
Regular updates and continuous monitoring are crucial to maintaining the effectiveness of endpoint protection against ever-evolving threats, ensuring that organizations can respond promptly to new vulnerabilities.
What percentage of small enterprises have adopted multi-factor authentication?
Currently, only 20% of small enterprises have adopted multi-factor authentication, indicating a significant gap in security measures.
How can advanced threat detection techniques benefit small enterprises?
Advanced threat detection techniques, such as behavioral analytics and machine learning, help small enterprises continuously monitor network traffic and user behavior, swiftly identifying anomalies that may signal an impending attack.
What financial benefits can organizations see from leveraging AI and automation in security measures?
Organizations that leverage AI and automation in their security measures have saved an average of $2.22 million in breach costs, highlighting the financial benefits of adopting such technologies.
Why are routine vulnerability assessments important for small enterprises?
Routine vulnerability assessments are crucial for proactively identifying and addressing security flaws that could be exploited by ransomware. They help organizations reduce their risk of attacks and manage vulnerabilities effectively.
What percentage of small and medium-sized enterprises have conducted a cybersecurity risk assessment?
Over 86% of small and medium-sized enterprises have conducted a cybersecurity risk assessment, although many still struggle with effectively managing vulnerabilities.
How do regular vulnerability evaluations enhance an organization's security stance?
Regular vulnerability evaluations enhance an organization's security stance by systematically identifying vulnerabilities and prioritizing remediation efforts, which can significantly reduce the risk of ransomware attacks.
What is the strategic importance of investing in routine vulnerability assessments?
Investing in routine vulnerability assessments is a strategic move that safeguards organizations against the changing threats in the cyber landscape and builds trust with clients by demonstrating a commitment to data protection.