
Understanding the Cybersecurity Maturity Model Certification (CMMC) is essential for business leaders navigating the intricate world of federal contracting. This framework, established by the U.S. Department of Defense, sets stringent cybersecurity standards that determine contractors' eligibility to bid on government contracts. As the cybersecurity landscape grows increasingly perilous, one pressing question arises: how can organizations ensure compliance while safeguarding their competitive edge in a constantly evolving regulatory environment?
In today’s climate, the stakes are high. Organizations face a barrage of cyber threats that can jeopardize not only their operations but also their reputations. The implications for businesses are profound, as non-compliance can lead to significant financial penalties and loss of contracts. Therefore, understanding and implementing the CMMC is not just a regulatory requirement; it’s a strategic imperative.
Cyber Solutions can effectively address these challenges by providing tailored strategies that align with the CMMC requirements. By investing in robust cybersecurity measures, organizations can not only comply with regulations but also enhance their resilience against potential threats. This proactive approach not only protects sensitive information but also fosters trust with clients and partners, ultimately securing a competitive advantage in the marketplace.
The Cybersecurity Maturity Model Certification (CMMC) is a vital framework established by the U.S. Department of Defense (DoD) to bolster the online security posture of entities within the defense industrial base (DIB). This certification integrates various security standards and best practices into a cohesive process that evaluates an organization's capability to safeguard sensitive information, particularly Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
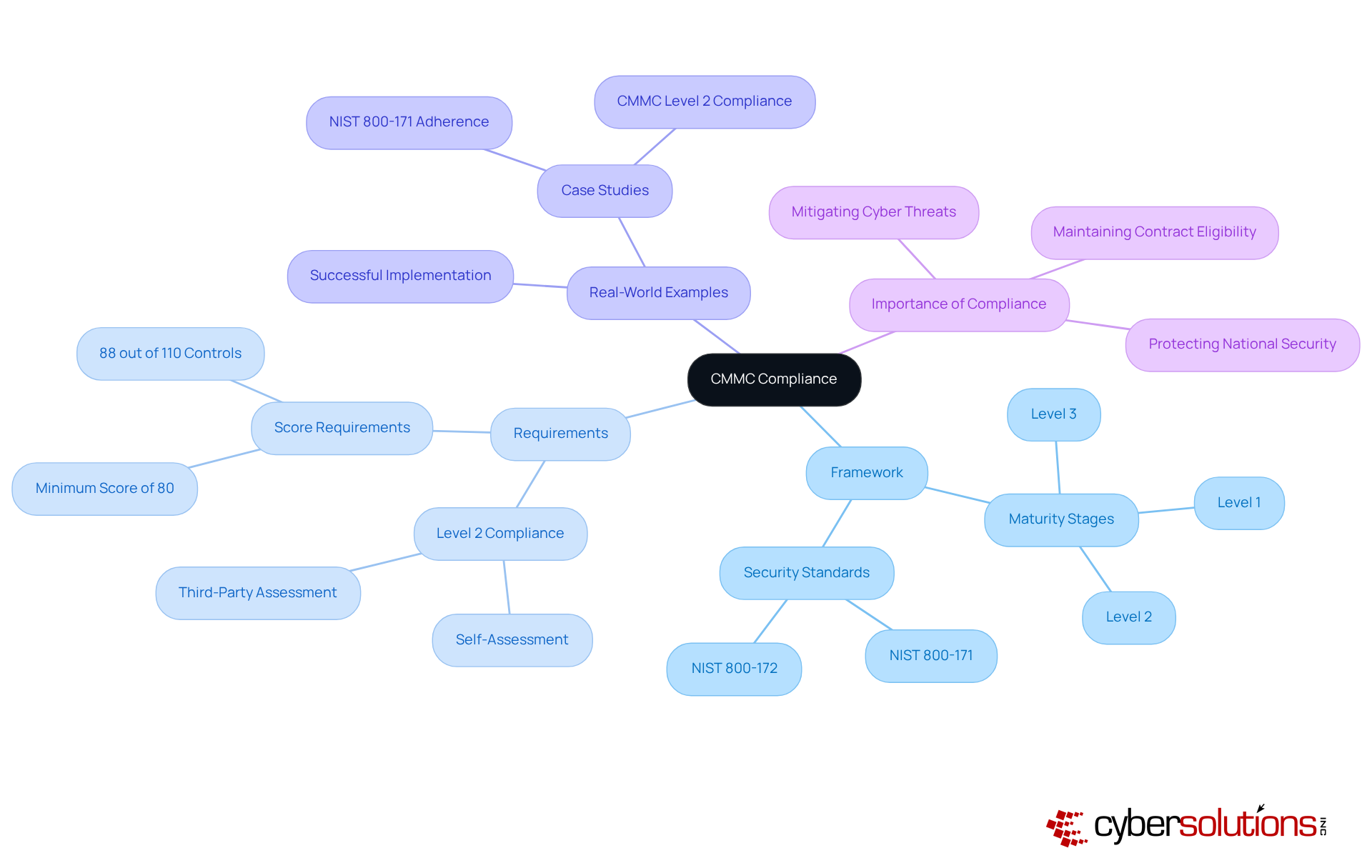
Adhering to the CMMC is not merely a matter of ticking boxes; it demands that organizations showcase their cyber defense capabilities through a structured, tiered framework of maturity stages. Each level presents specific requirements that must be met to qualify for DoD contracts. Starting November 10, 2025, compliance with Level 2 becomes mandatory for contractors handling CUI, necessitating a minimum score of 80% (88 out of 110 controls) for conditional certification. This phased implementation highlights the urgency for organizations to prepare, as non-compliance could lead to disqualification from contract opportunities.
Real-world examples underscore the critical need for adherence to these standards. For instance, a defense contractor successfully implemented the NIST 800-171/CMMC Level 2 adherence program, significantly enhancing their security posture and readiness for DoD contracts. Such proactive initiatives are essential, especially considering that nearly 80,000 firms will require Level 2 certification, while only about 70 organizations are authorized to conduct assessments.
The importance of compliance with these standards cannot be overstated. It not only ensures adherence to rigorous cybersecurity practices but also mitigates risks associated with cyber threats, thereby protecting national security interests. As the cybersecurity landscape evolves, organizations must remain vigilant and proactive in their compliance efforts to maintain eligibility for military contracts.
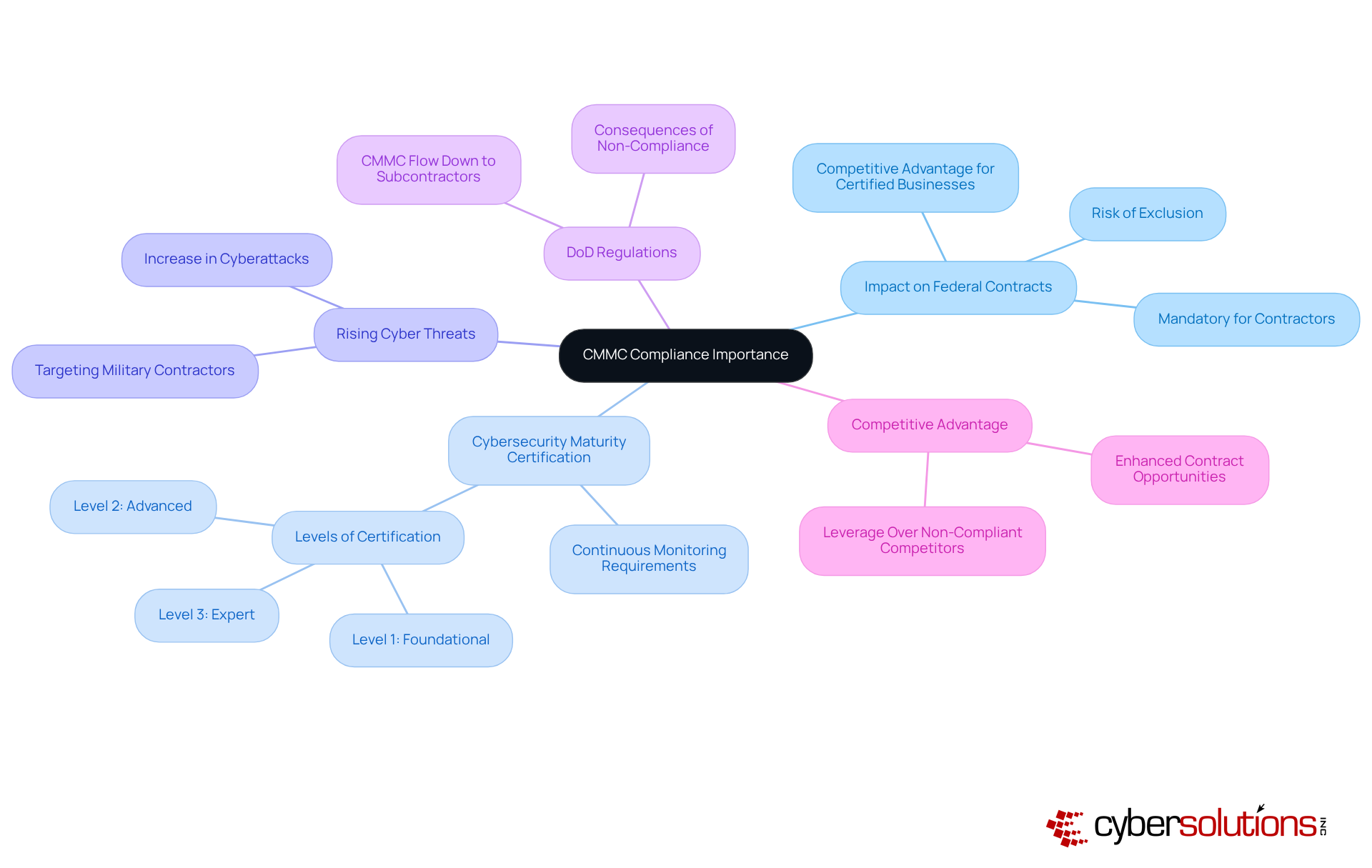
Compliance with the cybersecurity framework is not just important; it’s essential for contractors in the military sector. Why? Because it directly impacts their ability to bid on and maintain federal contracts. The Department of Defense (DoD) mandates that all contractors, including subcontractors, achieve specific levels of cybersecurity maturity certification. This certification demonstrates their capability to protect sensitive information against the rising tide of cyber threats. In 2025, the military sector has witnessed a significant surge in cyberattacks, with statistics revealing a considerable increase in incidents targeting military contractors. This alarming trend underscores the urgent need for robust digital security measures.
By enforcing cybersecurity regulations, the DoD aims to establish a consistent security framework across the military supply chain. This ensures that all parties involved in military contracts adhere to rigorous security standards. Such an initiative not only safeguards sensitive data but also strengthens the overall resilience of the defense industrial base against cyber threats.
Experts agree that the CMMC compliance meaning indicates that adherence to the cybersecurity maturity model is no longer optional; it’s a prerequisite for qualifying for federal contracts. Businesses that fail to meet these criteria risk exclusion from bidding processes, as primary contractors increasingly evaluate their supplier networks based on compliance status. Case studies reveal that certified businesses enjoy a competitive advantage, often securing contracts more easily than their non-compliant counterparts. As the landscape evolves, understanding the CMMC compliance meaning is crucial for contractors aiming to navigate the complexities of federal contracting effectively.
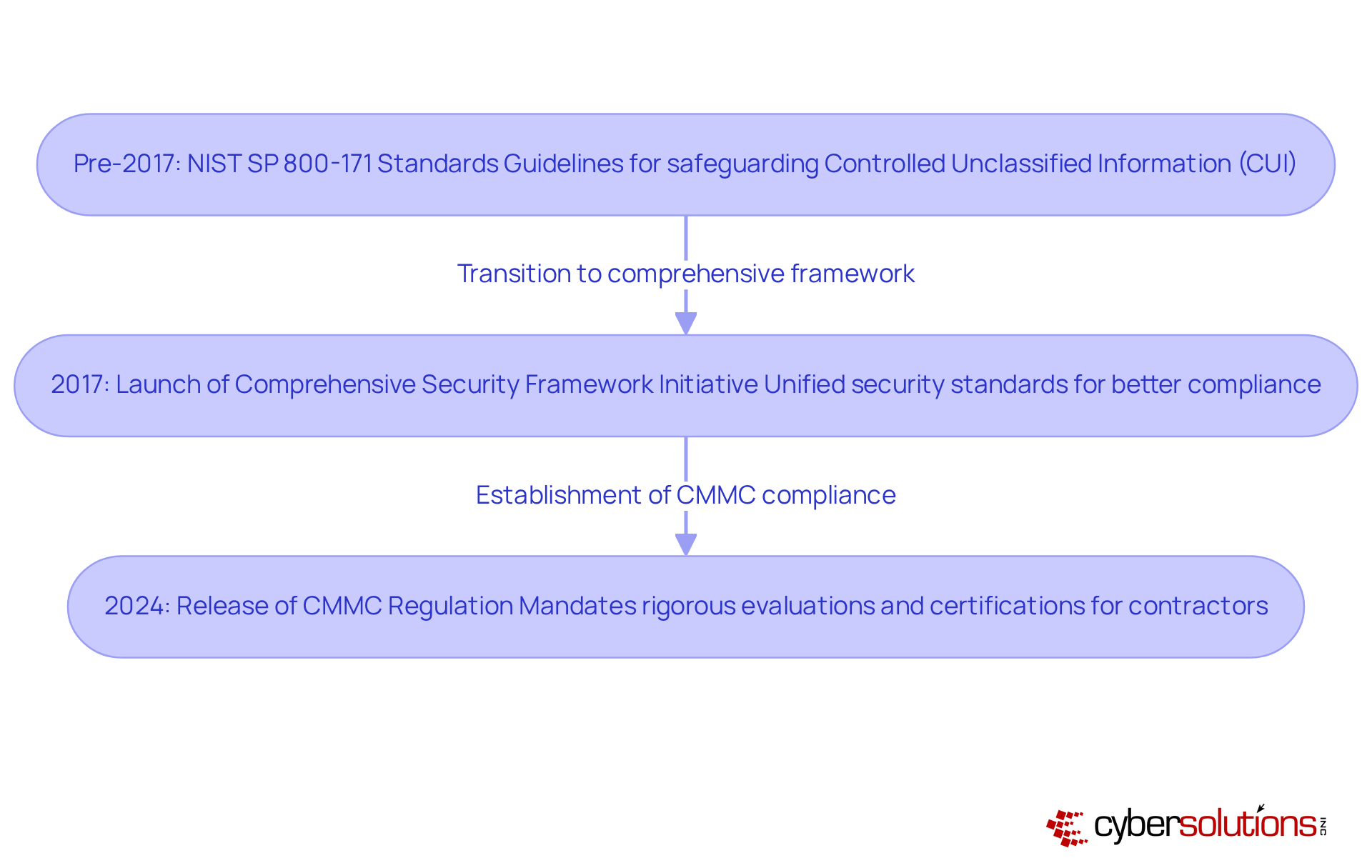
The increasing awareness of cybersecurity vulnerabilities within the defense industrial sector underscores the urgent need for robust security measures. Before the cybersecurity framework was implemented, the Department of Defense (DoD) relied heavily on various standards, particularly NIST SP 800-171, which provided guidelines for safeguarding Controlled Unclassified Information (CUI). However, these standards often hinged on self-reported compliance, leading to significant inconsistencies and enforcement gaps.
In light of escalating digital threats and data breaches, the DoD launched a program in 2017 aimed at establishing a more comprehensive and enforceable security framework. This initiative sought to unify disparate security standards into a cohesive certification process, enhancing accountability and ensuring that all contractors meet minimum security requirements. The culmination of this effort was the release of the Cybersecurity Maturity Model Certification regulation in 2024, which signifies the cmmc compliance meaning as a pivotal shift in security practices within the defense industry. This regulation mandates rigorous evaluations and certifications that contractors must achieve to remain eligible for government contracts.
As cybersecurity threats continue to evolve, it is imperative for organizations within the defense sector to adapt and comply with these new standards. Are you prepared to meet these challenges head-on? The future of your contracts may depend on it.
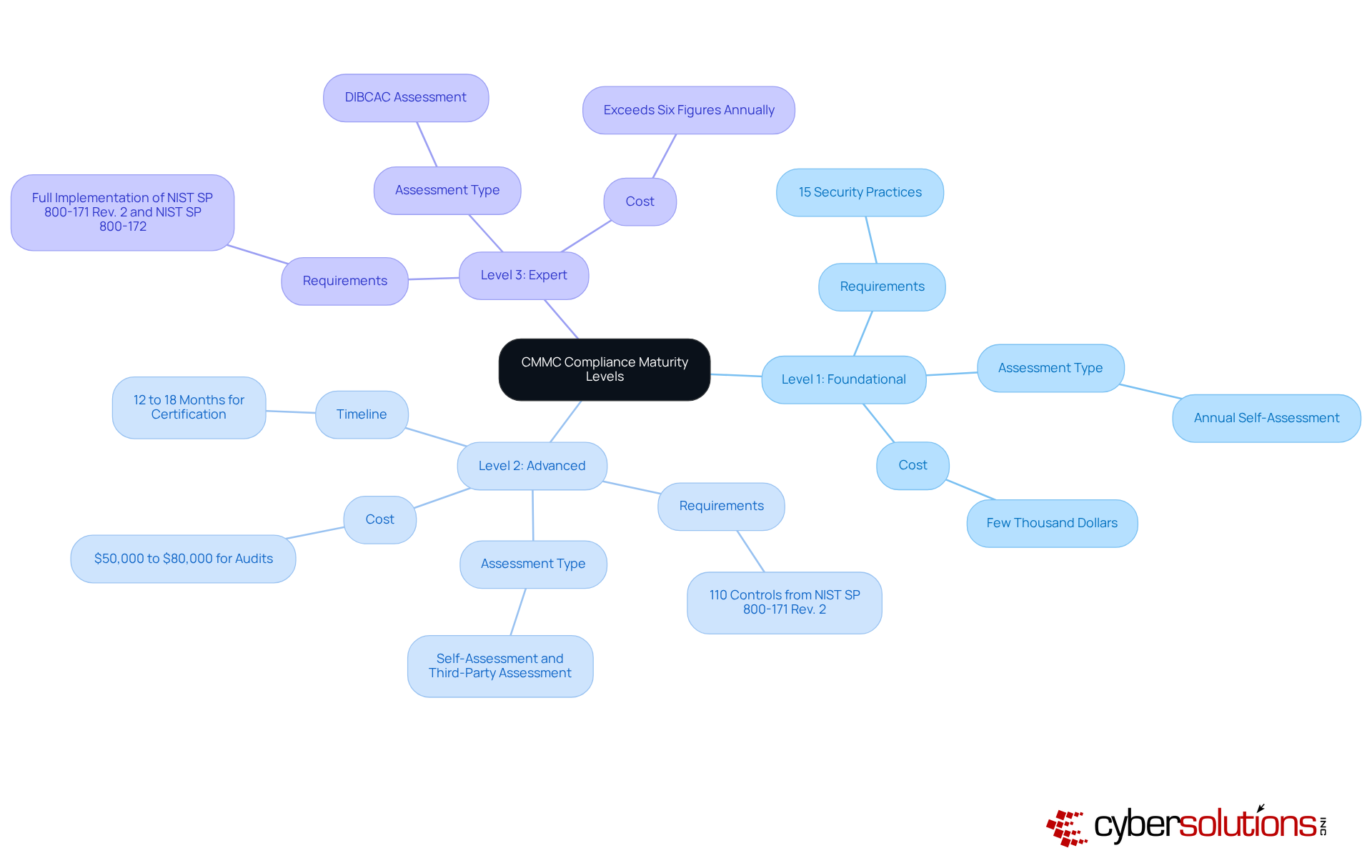
In today's digital landscape, the importance of robust cybersecurity measures cannot be overstated, especially for organizations handling sensitive information. Adherence to the cybersecurity framework is organized into three maturity tiers, each with escalating demands for security measures that are crucial for safeguarding Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
Level 1: Foundational
At this initial stage, organizations must implement 15 specific practices designed to protect FCI, focusing on essential security measures. An annual self-assessment against Level 1 requirements is mandatory, with results posted in the Supplier Performance Risk System (SPRS). Customized remediation strategies are vital here, as organizations must address regulatory gaps through policy updates and process enhancements. Are you prepared to meet these foundational requirements?
Level 2: Advanced
Building on these foundational practices, Level 2 introduces additional requirements aimed at protecting CUI. Organizations must implement all 110 controls outlined in NIST SP 800-171 Revision 2. Furthermore, they need to prepare for third-party assessments, which typically take 12 to 18 months and can cost between $50,000 and $80,000. Expert audit assistance is essential at this level, ensuring organizations are fully prepared for the official assessment and can address any outstanding issues. As of late 2025, only around 200 companies had achieved CMMC certification, while estimates suggest that up to 80,000 firms will require Level 2 certification by the end of the phased rollout in 2028. How will your organization navigate these challenges?
Level 3: Expert
The final tier, designated as Expert, requires organizations to demonstrate a comprehensive cybersecurity posture through advanced risk management and incident response capabilities. Assessments are conducted by the Defense Contract Management Agency's Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). Understanding these levels and their specific requirements is crucial for contractors aiming to secure DoD contracts and maintain compliance in an increasingly regulated environment. By achieving certification, organizations not only protect their business but also enhance their competitive advantage in the defense contracting industry. Are you ready to elevate your cybersecurity measures to the expert level?
Understanding CMMC compliance is not just essential; it’s a strategic imperative for business leaders in the defense sector. This framework serves as both a regulatory requirement and a competitive edge, crucial for safeguarding sensitive information and ensuring eligibility for federal contracts. The urgency to comply is heightened by the impending mandatory requirements for contractors handling Controlled Unclassified Information (CUI), with Level 2 compliance becoming essential by November 2025.
Key points throughout this discussion highlight the significance of CMMC compliance:
In light of the evolving cybersecurity landscape, the importance of CMMC compliance cannot be overstated. Organizations must prioritize their compliance efforts, not only to protect sensitive data but also to secure their position within the defense contracting ecosystem. As the landscape continues to change, staying informed and prepared for these compliance requirements will be crucial for success. Embracing the CMMC framework is not merely about meeting regulatory standards; it represents a commitment to fostering a robust cybersecurity culture that ultimately strengthens national security and the integrity of the defense industrial base.
What is CMMC compliance?
CMMC compliance refers to the adherence to the Cybersecurity Maturity Model Certification, a framework established by the U.S. Department of Defense to enhance the cybersecurity of entities in the defense industrial base.
Why was the CMMC framework created?
The CMMC framework was created to bolster the online security posture of organizations within the defense industrial base by integrating various security standards and best practices to protect sensitive information.
What types of information does CMMC focus on safeguarding?
CMMC focuses on safeguarding Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
How does the CMMC framework evaluate organizations?
The CMMC framework evaluates organizations through a structured, tiered framework of maturity stages, where each level has specific requirements that must be met to qualify for DoD contracts.
When does compliance with CMMC Level 2 become mandatory?
Compliance with CMMC Level 2 becomes mandatory for contractors handling CUI starting November 10, 2025.
What is the minimum score required for conditional certification at Level 2?
A minimum score of 80% (88 out of 110 controls) is required for conditional certification at Level 2.
What are the consequences of non-compliance with CMMC?
Non-compliance with CMMC could lead to disqualification from contract opportunities with the Department of Defense.
How many firms are expected to require Level 2 certification?
Nearly 80,000 firms are expected to require Level 2 certification.
How many organizations are authorized to conduct CMMC assessments?
Approximately 70 organizations are authorized to conduct CMMC assessments.
What are the benefits of adhering to CMMC standards?
Adhering to CMMC standards ensures rigorous cybersecurity practices, mitigates risks associated with cyber threats, and protects national security interests.