
In today's digital landscape, the importance of cybersecurity cannot be overstated, especially in the healthcare sector. Leaders must incorporate essential components into a NIST incident response plan to ensure effective cybersecurity management. A comprehensive plan that includes preparation, detection, compliance, and continuous improvement strategies is crucial for organizations aiming to bolster their resilience against evolving cyber threats.
Healthcare organizations face unique challenges, from safeguarding sensitive patient data to ensuring compliance with regulatory standards. The implications of inadequate cybersecurity can be severe, leading to data breaches that compromise patient trust and incur significant financial penalties. Therefore, it is imperative for leaders to recognize these challenges and take proactive measures to address them.
By implementing a robust incident response plan, organizations can minimize the impact of security incidents and enhance their overall cybersecurity posture. This plan not only prepares teams for potential threats but also fosters a culture of continuous improvement, ensuring that strategies evolve alongside emerging cyber risks.
In conclusion, the integration of a NIST incident response plan is not just a best practice; it is a necessity for healthcare organizations committed to protecting their assets and maintaining patient trust. Leaders must act decisively to implement these strategies, ensuring their organizations are well-equipped to face the challenges of today's cyber landscape.
In a world where cyber threats are more prevalent than ever, organizations are tasked with the critical responsibility of protecting their sensitive information amidst a complex regulatory environment. A well-structured NIST incident response plan is not just a guideline; it serves as a vital framework that enables leaders to manage cybersecurity incidents effectively and bolster operational resilience. As the stakes continue to rise, how can organizations ensure their incident response strategies are compliant and adaptable to the swiftly changing threat landscape?
This article explores the ten essential elements of a NIST incident response plan, providing leaders with the insights necessary to strengthen their defenses and respond with agility in the face of adversity. By understanding these elements, organizations can not only navigate the challenges posed by cyber threats but also position themselves to thrive in an increasingly digital world.
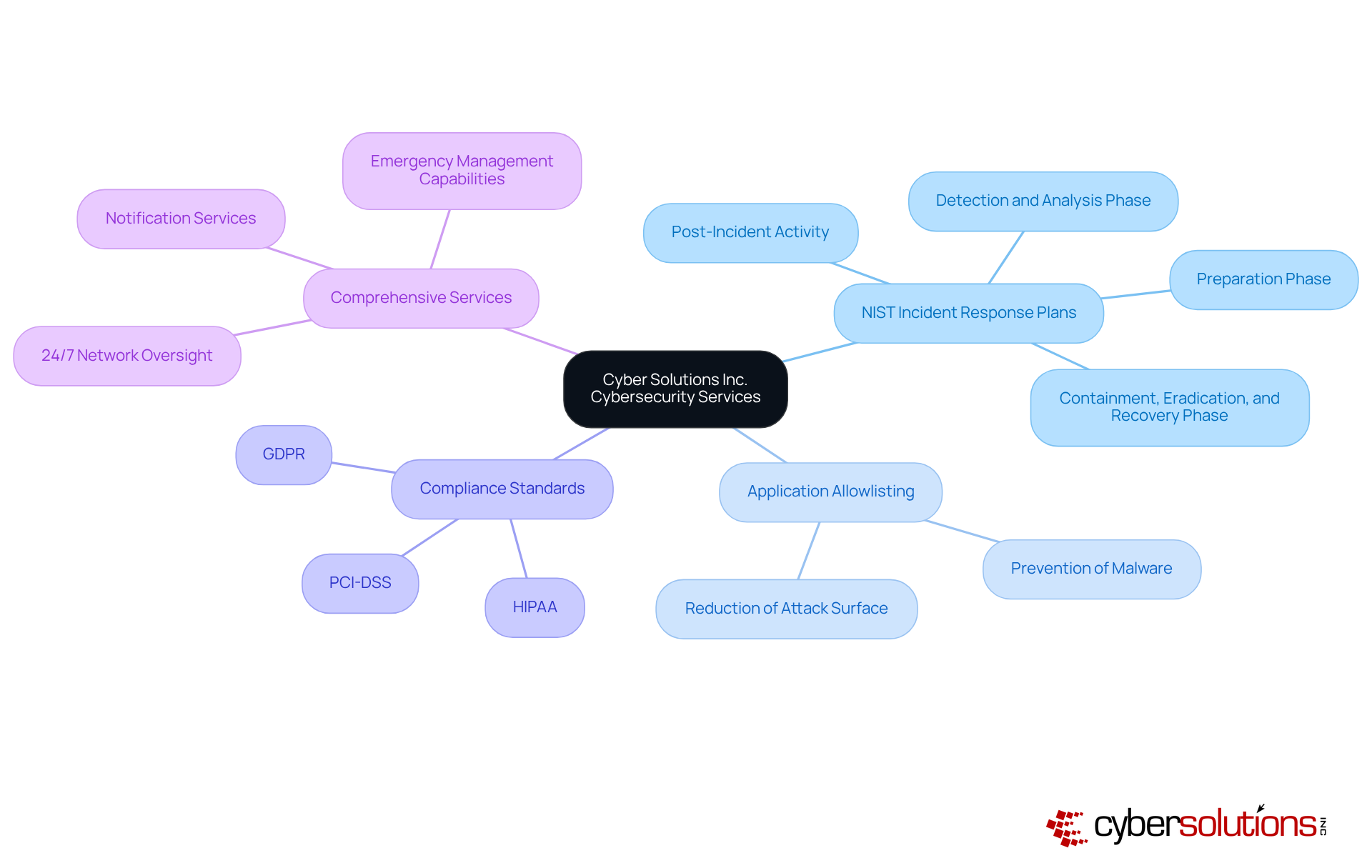
In today's digital landscape, the importance of robust cybersecurity cannot be overstated, especially for organizations navigating the complexities of diverse sectors. Cyber Solutions Inc. specializes in developing tailored NIST response strategies that meet the unique requirements of these companies. With their extensive expertise in managed IT and cybersecurity services, they empower organizations to effectively manage incidents using the NIST incident response plan while ensuring compliance with industry regulations.
A cornerstone of their approach is application allowlisting, a proactive measure that prevents malware and unauthorized software from executing. This strategy not only reduces the attack surface but also minimizes vulnerabilities, effectively thwarting potential cyber threats. Moreover, it ensures adherence to stringent standards such as:
These standards are critical for maintaining trust and integrity in the healthcare sector.
Cyber Solutions Inc. offers a comprehensive suite of services, including:
This allows companies to focus on their core operations without the burden of IT challenges. With skilled emergency management capabilities, they guarantee business continuity, enabling organizations to navigate the ever-evolving cybersecurity landscape with confidence. Are you ready to fortify your defenses and ensure compliance? Let Cyber Solutions guide you in safeguarding your organization against cyber threats.
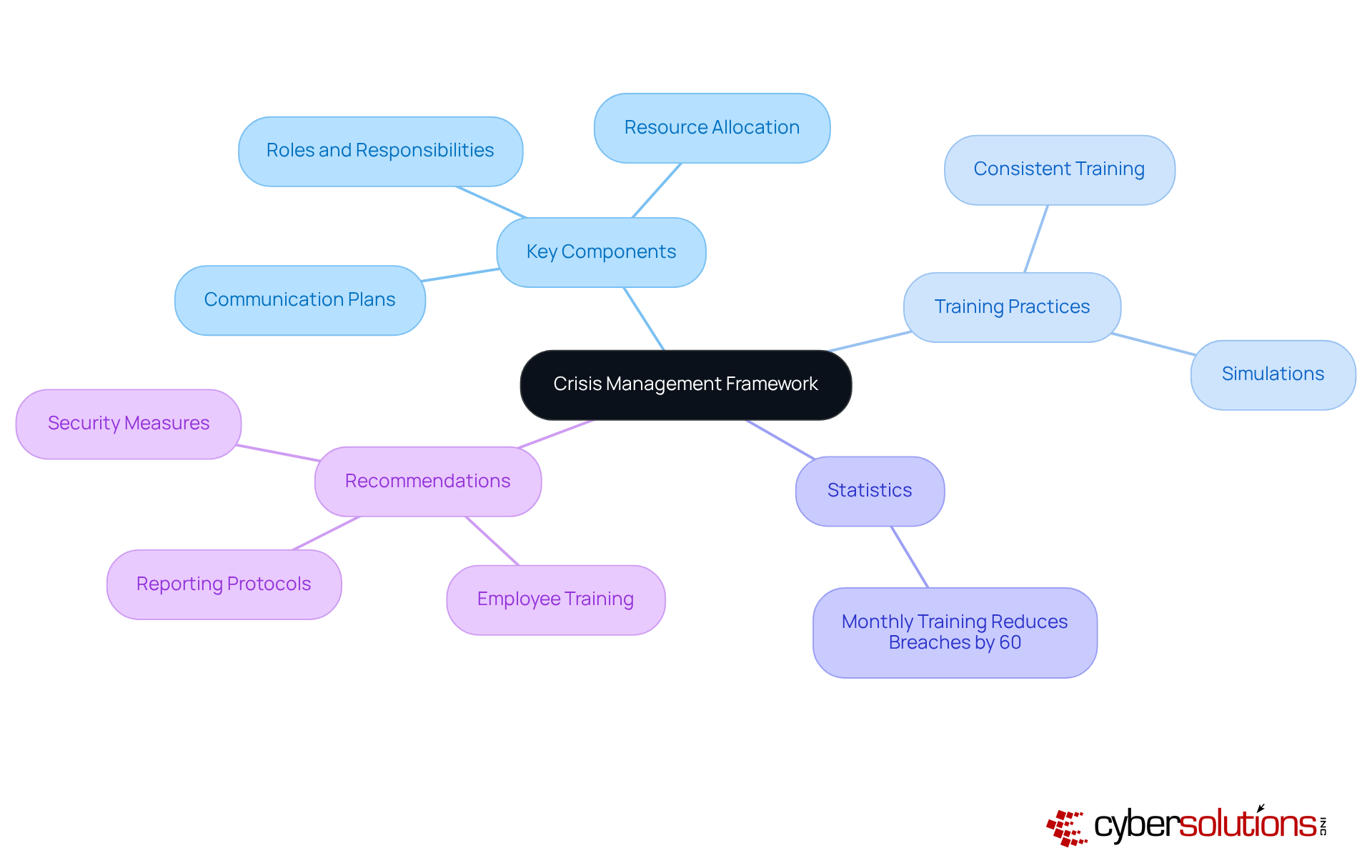
In today's healthcare landscape, the importance of a robust crisis management framework cannot be overstated. Establishing such a framework requires comprehensive policies, procedures, and training programs that equip teams to tackle potential situations with efficiency. Key components include:
Consistent training sessions and simulations are not just beneficial; they are essential. These practices bolster readiness and enhance the overall effectiveness of responses during real events. Regular practice and continuous improvement of these training programs are vital for transforming uncertainty into a coordinated reaction, ultimately minimizing the impact of security breaches. Did you know that companies conducting monthly security training can reduce the likelihood of breaches by 60%? This statistic underscores the power of regular training sessions.
Moreover, with the average breach lifecycle—from detection to containment—spanning 258 days, the necessity of a strong management framework is clear. As Rob Peterson, CEO of Infrascale, aptly states, "Preparedness is achieved through repetition." This highlights the critical role of ongoing training and refinement in response strategies.
Additionally, conducting thorough risk assessments and gap analyses is crucial for pinpointing compliance gaps and vulnerabilities within your systems, ensuring alignment with HIPAA standards. Practical recommendations from these evaluations may include:
It's also important to recognize the role of managed service providers (MSPs). A significant 49% of technology leaders report that MSPs often lead the initial triage phase, emphasizing the collaborative nature of effective issue management. By addressing these challenges head-on, healthcare organizations can fortify their defenses and ensure a more secure future.
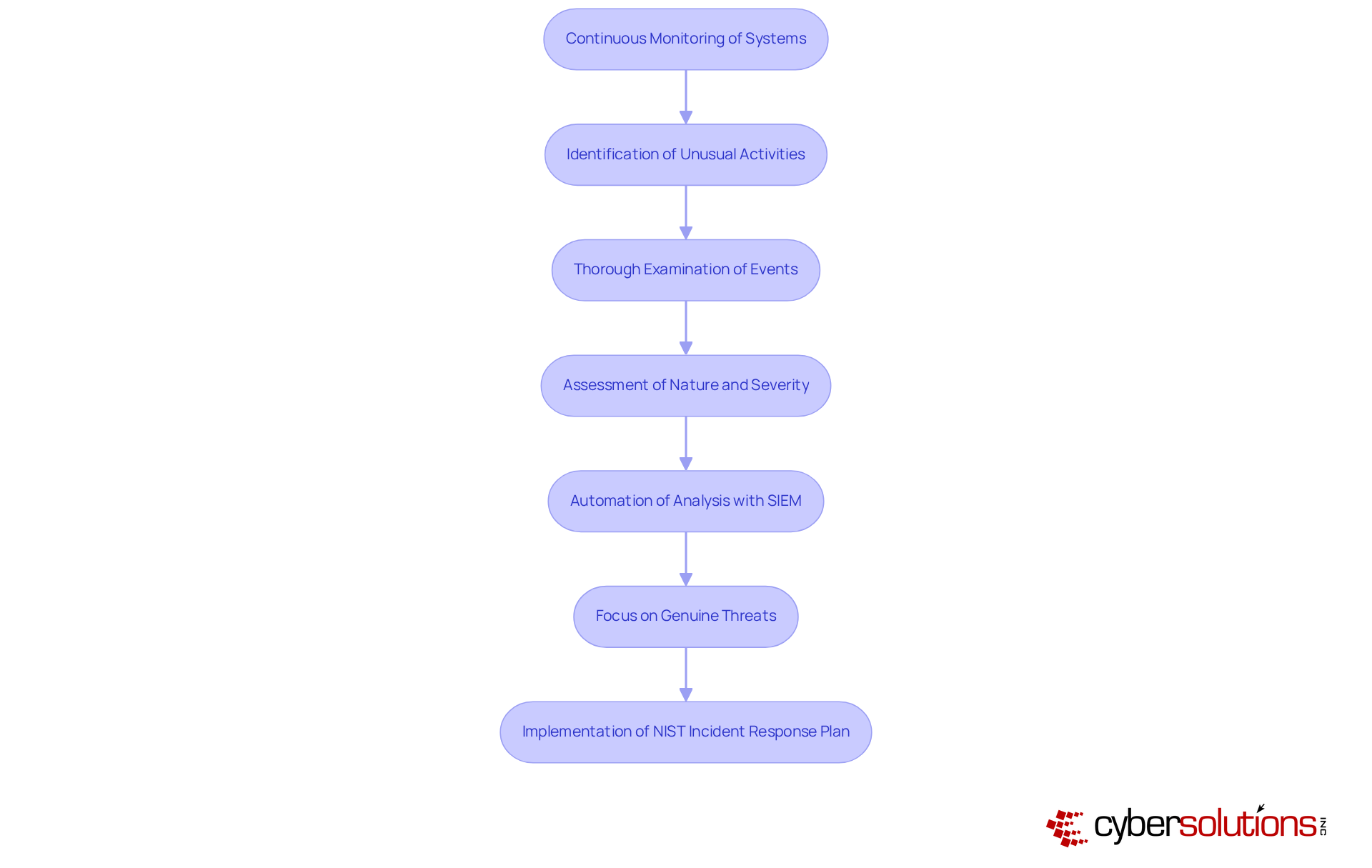
Detection and analysis are crucial components of an effective response strategy, focusing on the continuous monitoring of systems for unusual activities and the thorough examination of potential events to assess their nature and severity. Organizations are increasingly turning to advanced threat detection technologies, particularly Security Information and Event Management (SIEM) systems. These systems facilitate real-time monitoring and analysis of security events, simplifying the detection process and enhancing the accuracy of event analysis by correlating data from various sources.
In 2025, the average time to identify cybersecurity events remains a significant concern, with federal agencies reporting a mean resolution time of 20 days for incidents. This underscores the necessity for institutions to establish a NIST incident response plan that includes robust detection procedures and ensures they are regularly updated to adapt to evolving risks. For example, a major retail company successfully employed SIEM to identify unusual behavior and thwart a ransomware attack, demonstrating the effectiveness of these systems in real-world scenarios.
Moreover, expert insights reveal that SIEM systems improve event detection by automating the analysis of security alerts. This automation allows security teams to focus on genuine threats rather than being bogged down by false positives. As organizations face an increasing variety of cyber threats, investing in a NIST incident response plan is essential for enhancing crisis management capabilities and ensuring operational resilience.
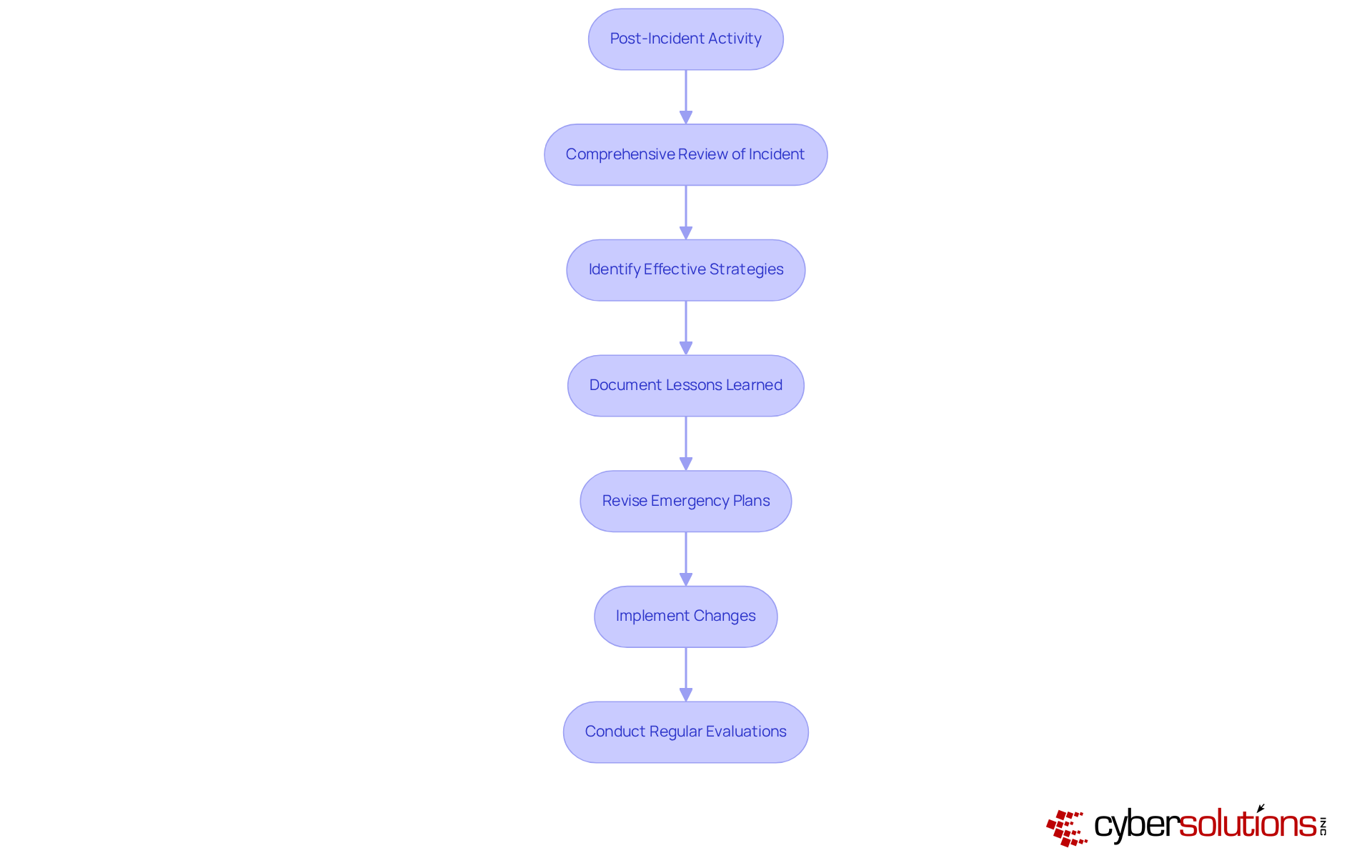
In today's healthcare landscape, cybersecurity is not just a necessity; it's a critical imperative. With the rise of sophisticated cyber threats, organizations must prioritize post-event actions as part of their NIST incident response plan to enhance their event management procedures. Comprehensive reviews are essential to assess which strategies proved effective and identify areas needing improvement. This stage fosters a culture of continuous enhancement, where insights gained from past incidents directly inform the NIST incident response plan and future action plans.
Recording these lessons is vital. Organizations should systematically revise their emergency plans to incorporate the NIST incident response plan and these findings. For instance, after a recent ransomware attack, Cyber Solutions swiftly assembled a specialized crisis management team within 24 hours. This enabled real-time evaluations and rapid remediation efforts, minimizing the threat's spread while reinforcing system defenses through around-the-clock containment efforts and staff training on recognizing suspicious emails.
Research indicates that companies can reduce future occurrence rates by as much as 50% by making adjustments based on previous breaches through a NIST incident response plan. Furthermore, entities that implement a NIST incident response plan and conduct regular post-event evaluations experience a 29% decrease in repeated incidents. This underscores the importance of extracting insights from each experience. By prioritizing thorough documentation and analysis—including compliance assessments and risk analysis—organizations not only bolster their resilience but also ensure they are better equipped to tackle future cybersecurity challenges, particularly in maintaining compliance with HIPAA standards.
In today's digital landscape, the significance of robust emergency management teams cannot be overstated. These teams play a pivotal role in monitoring events from detection to resolution, ensuring that organizations are prepared to tackle any crisis head-on. Key positions within these teams include:
Clearly defined roles and responsibilities are essential, enabling team members to act swiftly and efficiently during emergencies, thereby minimizing confusion and enhancing operational effectiveness.
The size of crisis management teams can vary, but organizations often find that a harmonious blend of internal and external members significantly boosts their capabilities. Internal teams bring invaluable knowledge of the organization's IT ecosystem, while external experts fill skill gaps and provide specialized insights. This hybrid approach fosters a more resilient response to incidents, particularly as cyber threats continue to evolve and become more sophisticated.
Moreover, effective event management hinges on collaboration among diverse skill sets, including network administrators and forensic analysts. Regular training and simulation exercises are crucial for honing team members' skills, ensuring they are well-prepared to handle various security scenarios. In fact, organizations that conduct emergency drills at least quarterly can respond to incidents 35% faster than those that do not.
A well-defined NIST incident response plan is essential for effectively addressing cyber events. The NIST incident response plan guides teams through a systematic process that encompasses:
Additionally, incorporating 24/7 network surveillance and alert services, such as those provided by Cyber Solutions, enhances response capabilities by ensuring that anomalies and potential vulnerabilities are identified in real-time. This proactive monitoring allows teams to react swiftly, minimizing downtime and mitigating the impact of threats like ransomware and phishing attacks.
Ultimately, a well-organized crisis management group not only lessens the impact of security incidents but also fosters a proactive culture that prioritizes continuous improvement and learning from past experiences. Ongoing assessment and oversight of cyber risks are essential for proactive event management, ensuring that teams remain vigilant against ever-evolving threats.
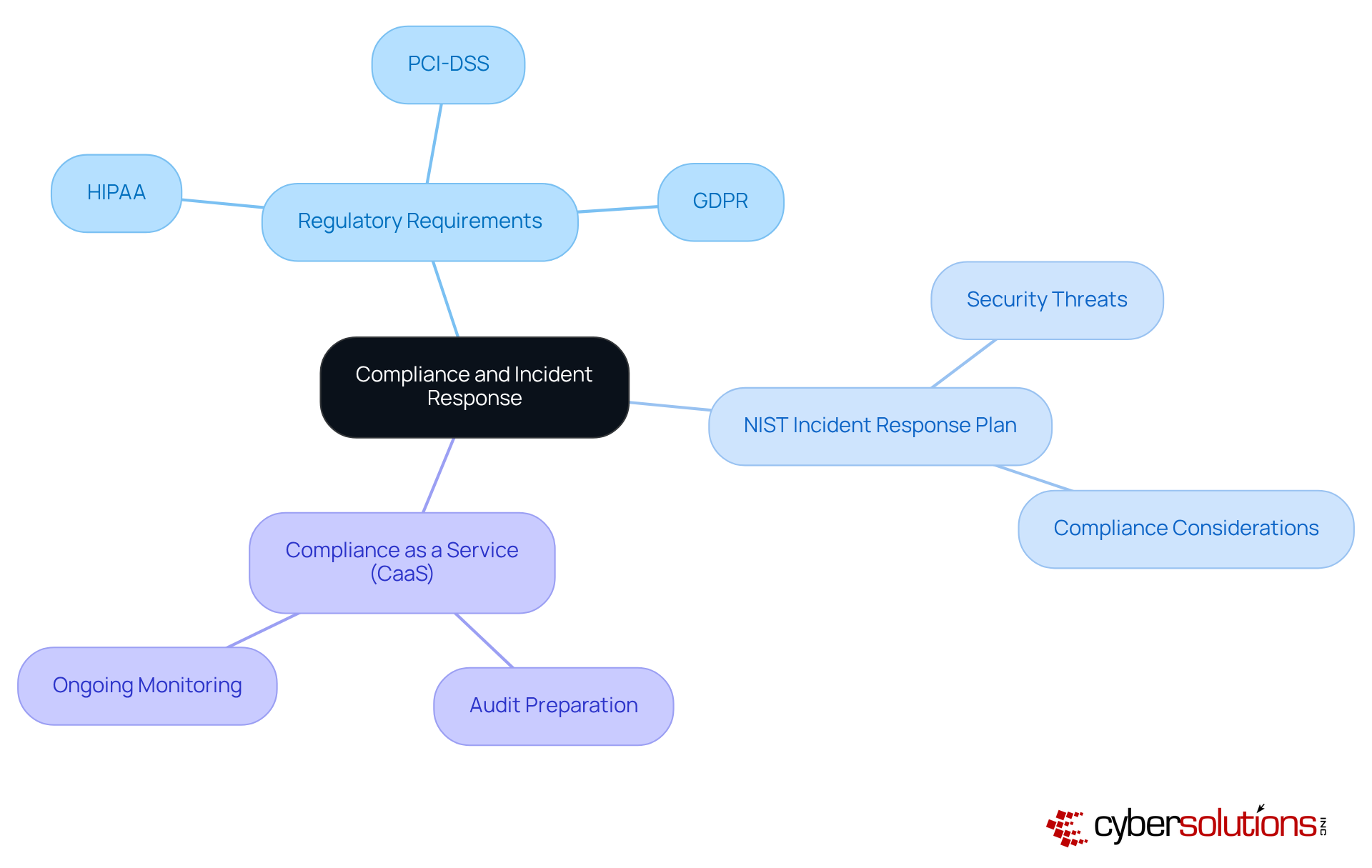
In today's digital landscape, aligning management strategies with regulatory requirements is crucial for safeguarding sensitive information. Understanding specific laws and regulations, such as HIPAA, PCI-DSS, and GDPR, is essential for any business aiming to navigate the complexities of compliance. Organizations must ensure their NIST incident response plan not only addresses security threats but also incorporates compliance considerations, including reporting requirements and documentation practices. This proactive approach mitigates legal risks and enhances overall security posture.
For small and medium-sized businesses, utilizing Compliance as a Service (CaaS) can be a game changer. CaaS provides access to enterprise-level compliance expertise without the hefty costs associated with maintaining in-house staff. These solutions offer extensive support for audit preparation and ongoing monitoring, ensuring that organizations remain compliant with stringent regulatory standards. By adopting this strategy, businesses not only protect themselves against potential penalties but also strengthen their overall security framework.
Are you ready to elevate your compliance efforts? Embracing CaaS could be the key to navigating the regulatory landscape effectively while enhancing your organization's security measures.
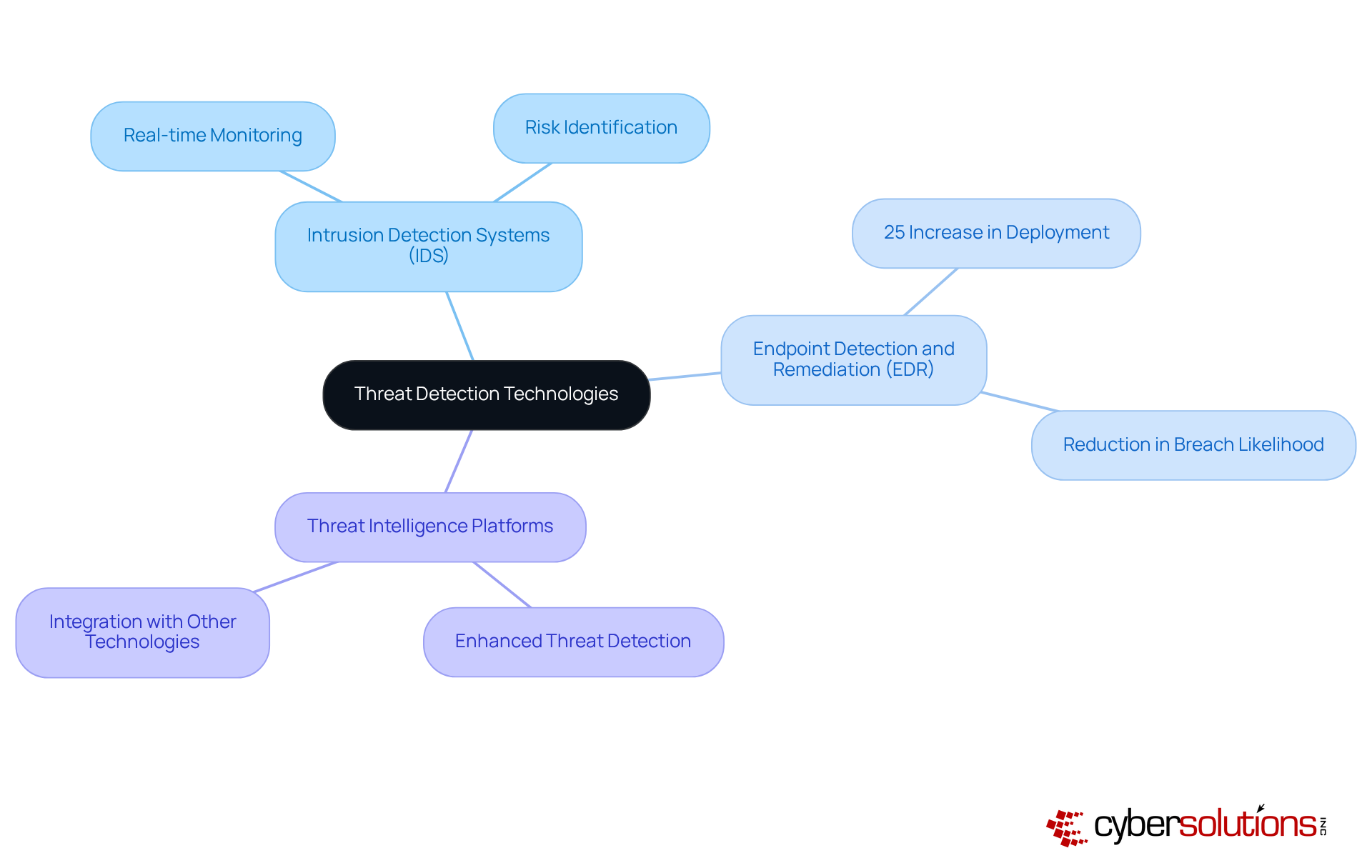
In today’s digital landscape, enhancing emergency management capabilities is crucial for organizations to safeguard against evolving cybersecurity threats. Investing in a diverse array of threat detection technologies—such as intrusion detection systems (IDS), endpoint detection and remediation (EDR) solutions, and threat intelligence platforms—is essential. Notably, EDR solutions have demonstrated a 25% increase in deployment, correlating with a significant reduction in breach likelihood. This statistic underscores their effectiveness in managing cybersecurity incidents. Moreover, with the typical eCrime breakout time recorded at just 48 minutes, the urgency for organizations to bolster their detection and response strategies cannot be overstated.
Intrusion detection systems are vital in this context, providing real-time monitoring and analysis of network traffic. This capability enables organizations to identify potential risks before they escalate into serious threats. For example, organizations that have integrated IDS and EDR solutions report improved management of incidents, facilitating quicker recognition and mitigation of risks. As cyber adversaries increasingly adopt sophisticated tactics—ranging from social engineering to malware-free attacks—the necessity for robust detection mechanisms becomes paramount. By leveraging these technologies, organizations can significantly reduce the risk of substantial damage during a cybersecurity event, thereby ensuring a more resilient operational framework.
In today's healthcare landscape, the importance of robust cybersecurity cannot be overstated. With the rise of sophisticated cyber threats, organizations must prioritize the ongoing enhancement of their NIST incident response plan. This involves frequently assessing and revising strategies to adapt to the ever-changing risk environment. Regular evaluations, informed by insights from past incidents and emerging challenges, are essential for maintaining an effective NIST incident response plan.
Consider a recent case study involving a healthcare provider that faced a ransomware attack. The swift mobilization of a crisis management team within 24 hours not only mitigated the immediate danger but also facilitated a quicker recovery. This highlights the critical need for immediate action and specialized expertise in crisis situations. By documenting these experiences and tailoring compliance reports to HIPAA standards, organizations can bolster their cybersecurity confidence and ensure they are audit-ready.
A multi-tiered strategy, including the NIST incident response plan, for managing crises is vital. This includes:
These are crucial for adapting to evolving threats and safeguarding patient data. As CFOs navigate these unique challenges, they must recognize that proactive measures are not just beneficial—they are essential for protecting their organizations and the sensitive information they handle. Are you prepared to take action and enhance your cybersecurity posture?
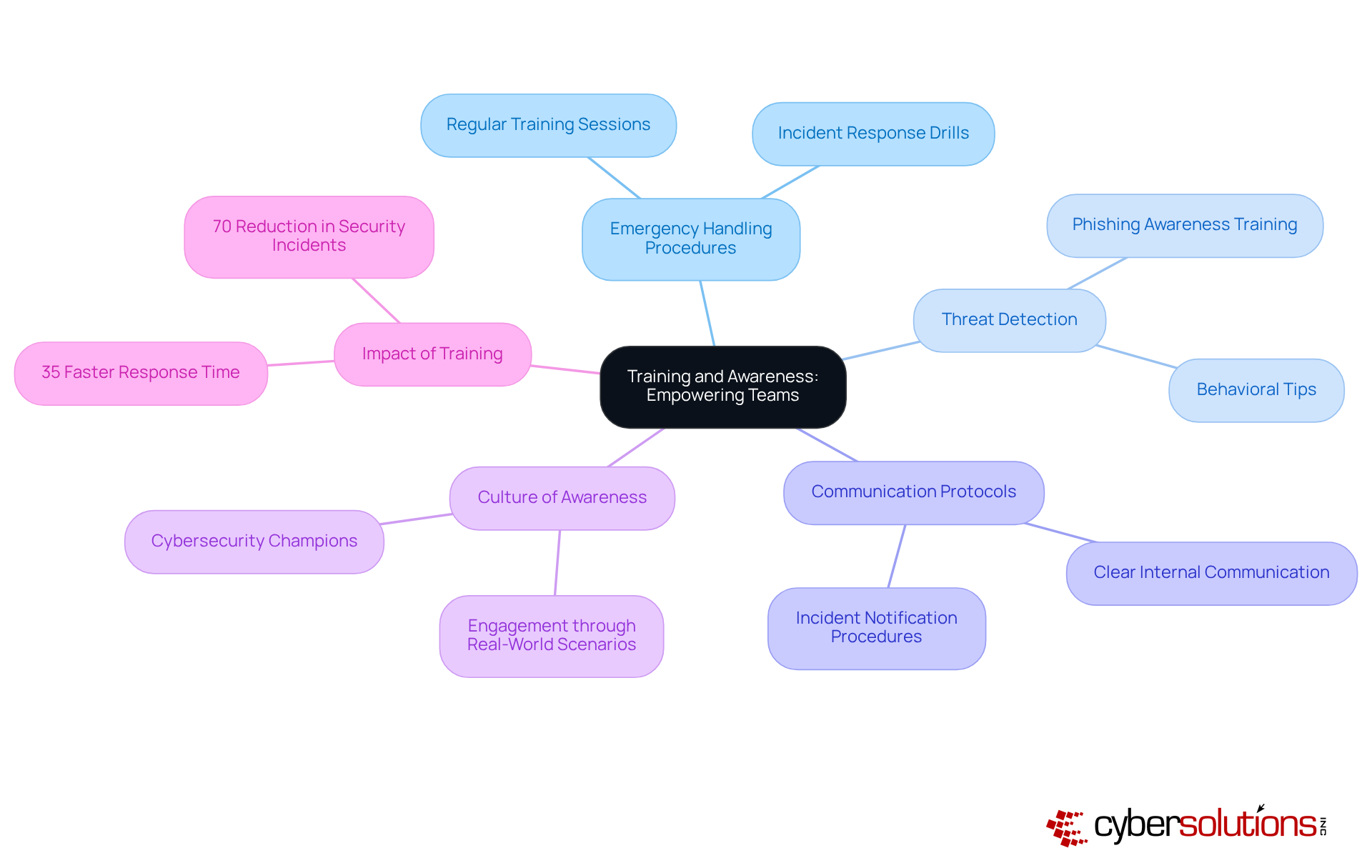
Training and awareness initiatives are not just beneficial; they are essential for empowering teams to respond effectively to cybersecurity events. In today’s landscape, organizations must conduct regular training sessions that cover:
This approach not only enhances employees' understanding of their roles during an incident but also cultivates a culture of awareness across the organization. Such a culture ensures that every staff member is engaged and informed, enabling a coordinated and effective response when challenges arise.
Consider this: organizations that conduct response exercises at least once every three months can react to events 35% faster. This statistic underscores the tangible benefits of ongoing training. Furthermore, entities that prioritize security awareness education experience a remarkable 70% reduction in security incidents. This highlights the critical importance of equipping employees with the knowledge and skills necessary to tackle potential threats.
By weaving security practices into daily operations, organizations can create an environment where each team member actively contributes to event management and strengthens overall cybersecurity resilience. Are you ready to take the necessary steps to enhance your organization’s cybersecurity posture?
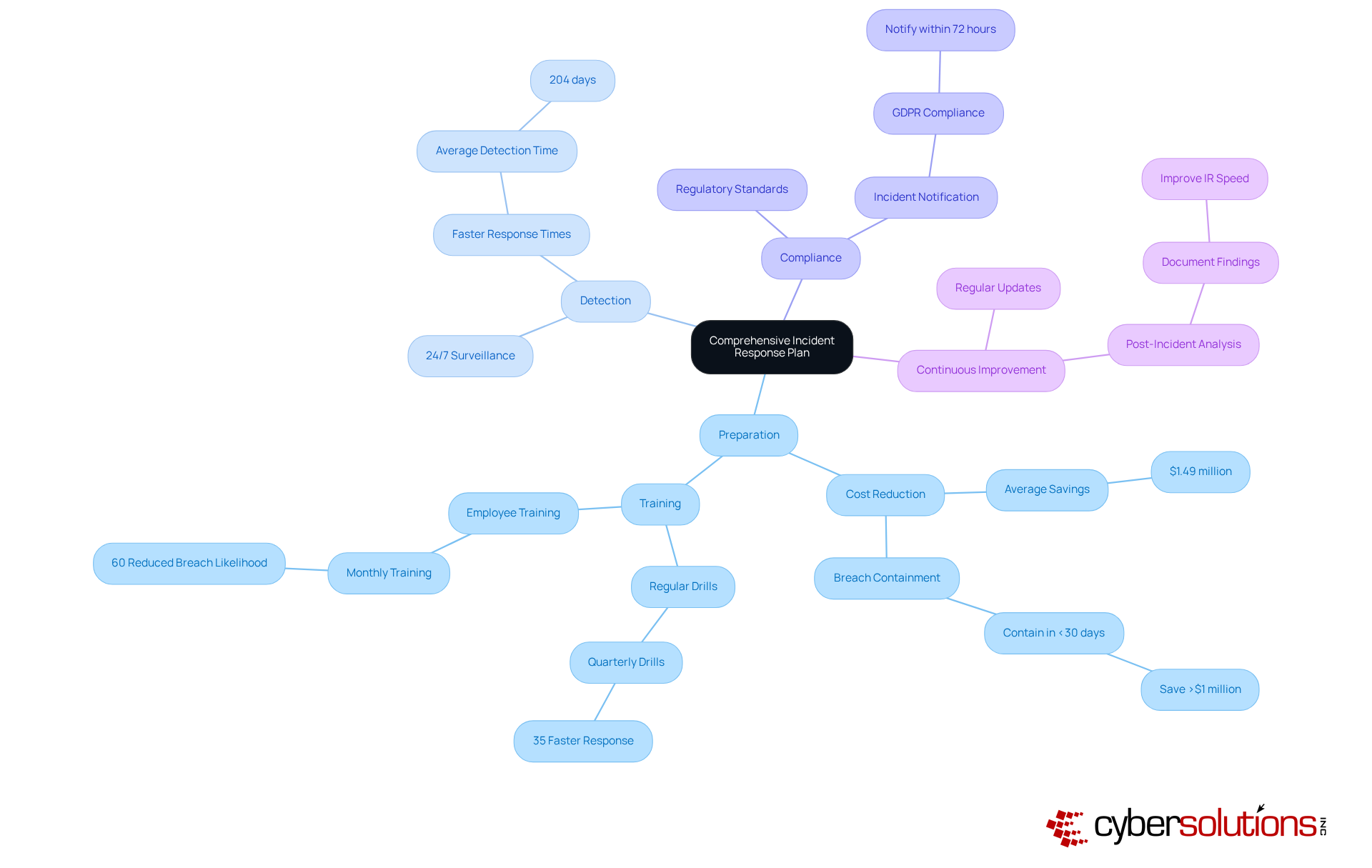
In today’s digital landscape, having a robust NIST incident response plan is not just beneficial but essential for companies to effectively manage cybersecurity events. By integrating preparation, detection, compliance, and continuous improvement, organizations can significantly bolster their resilience against ever-evolving threats. Consider this: firms that regularly assess their emergency action plans can reduce breach costs by an impressive average of $1.49 million. This statistic underscores the substantial financial benefits of adopting preventive strategies. Furthermore, organizations with a formal crisis management strategy experience an average breach lifecycle of 258 days, compared to just 204 days for those without a plan. This stark contrast highlights the critical need for structured readiness.
Investing in advanced technologies, such as Security Orchestration, Automation, and Response (SOAR) solutions, is equally vital. Companies leveraging these technologies can manage risks four times faster than those relying on manual processes. Consistent training and emergency exercises are crucial; entities conducting incident response drills at least once every three months respond 35% quicker to incidents. Additionally, establishing 24/7 surveillance for threats ensures that suspicious activities are detected and mitigated before they escalate into serious risks, protecting organizations from ransomware, phishing, and other malicious software attacks. Comprehensive firewall and network security solutions, with an emphasis on proactive monitoring, further strengthen defenses, providing a formidable barrier against unauthorized access while ensuring compliance with regulatory standards. As cyber threats continue to rise, organizations must prioritize the development and maintenance of a NIST incident response plan to ensure operational continuity and security well into 2025 and beyond.
In the realm of cybersecurity, a well-structured NIST incident response plan is not just beneficial; it’s essential for organizations striving to protect their operations from a multitude of digital threats. With a comprehensive approach that includes preparation, detection, compliance, and ongoing improvement, businesses can significantly bolster their resilience against the ever-evolving landscape of cyber risks. The financial implications are substantial; firms that routinely update their emergency strategies see marked reductions in breach management costs.
Key components of an effective incident response strategy have been highlighted, such as:
By leveraging these insights, organizations can enhance their immediate response capabilities and cultivate a culture of preparedness that lessens the impact of future incidents.
The urgency for organizations to develop and maintain a robust NIST incident response plan cannot be overstated. As cyber threats proliferate, adopting a proactive stance—characterized by regular assessments, advanced monitoring technologies, and comprehensive training—will be crucial for ensuring operational continuity and regulatory compliance. Taking these steps now empowers organizations to navigate the complex cybersecurity landscape with confidence, safeguarding their assets and reputation well into the future.
What is Cyber Solutions Inc. known for?
Cyber Solutions Inc. specializes in developing tailored NIST incident response strategies for organizations across diverse sectors, helping them manage cybersecurity incidents effectively and ensure compliance with industry regulations.
What proactive measure does Cyber Solutions Inc. emphasize in their cybersecurity approach?
They emphasize application allowlisting, which prevents malware and unauthorized software from executing, thereby reducing the attack surface and minimizing vulnerabilities.
Which industry standards does Cyber Solutions Inc. help organizations comply with?
They ensure compliance with critical standards such as HIPAA, PCI-DSS, and GDPR.
What services does Cyber Solutions Inc. offer to support businesses?
They offer a comprehensive suite of services, including 24/7 network oversight and notification services, allowing companies to focus on their core operations without IT burdens.
Why is establishing a robust incident response framework important?
A robust incident response framework is crucial for efficiently tackling potential crises, minimizing the impact of security breaches, and ensuring business continuity.
What are key components of a robust crisis management framework?
Key components include clearly defined roles and responsibilities, structured communication plans, and the allocation of necessary resources.
How can regular training impact an organization's security?
Companies that conduct monthly security training can reduce the likelihood of breaches by 60%, highlighting the importance of ongoing training and simulations.
What is the average breach lifecycle, and why does it matter?
The average breach lifecycle—from detection to containment—spans 258 days, emphasizing the necessity for a strong management framework to address security incidents effectively.
What role do managed service providers (MSPs) play in incident management?
MSPs often lead the initial triage phase of incident management, which underscores the collaborative nature of effective issue management.
How do organizations detect and analyze cybersecurity incidents?
Organizations focus on continuous monitoring of systems for unusual activities and utilize advanced threat detection technologies like Security Information and Event Management (SIEM) systems for real-time monitoring and analysis.
What is the significance of SIEM systems in incident detection?
SIEM systems enhance the accuracy of event analysis by correlating data from various sources and automating the analysis of security alerts, allowing security teams to focus on genuine threats.
Why is it essential for organizations to invest in a NIST incident response plan?
Investing in a NIST incident response plan is essential for enhancing crisis management capabilities, ensuring operational resilience, and adapting to evolving cyber threats.