
In today's digital age, cybersecurity stands as a cornerstone of operational integrity in healthcare. For CFOs, the stakes are particularly high; protecting sensitive patient data is not just a regulatory requirement but a fundamental responsibility.
Defense in depth emerges as a vital strategy, emphasizing the necessity of implementing multiple layers of security to combat the ever-evolving landscape of cyber threats. This multifaceted approach substantially mitigates the risk of data breaches by integrating a variety of protective measures, including:
Such strategies not only ensure compliance with critical regulations like HIPAA but also bolster organizational resilience against emerging cyber risks.
The current landscape is fraught with challenges, as cyber threats grow increasingly sophisticated. Healthcare organizations face unique vulnerabilities, making it imperative for CFOs to adopt comprehensive security measures. By embracing a defense in depth strategy, healthcare leaders can enhance their security posture, safeguarding patient information while fostering trust and compliance.
Ultimately, the implementation of a robust cybersecurity framework is not merely an operational task but a strategic imperative. It is essential for healthcare CFOs to recognize the importance of layered security measures in their risk management strategies. Taking decisive action now will pave the way for a more secure future in healthcare, ensuring that patient data remains protected against the relentless tide of cyber threats.
In a time when cyber threats are more pronounced than ever, the healthcare sector stands at a pivotal juncture. The necessity for robust cybersecurity measures cannot be overstated, particularly as organizations face increasingly sophisticated attacks targeting sensitive patient data.
At the forefront of this challenge is the concept of defense in depth, a crucial strategy that employs multiple layers of security to safeguard information. This article explores the fundamental principles of this comprehensive approach, emphasizing how healthcare CFOs can utilize it to bolster security, ensure compliance, and mitigate risks.
However, as organizations grapple with the complexities of implementing such strategies, a pressing question arises: how can they effectively balance the imperative for strong protection against the backdrop of an ever-evolving cyber landscape?
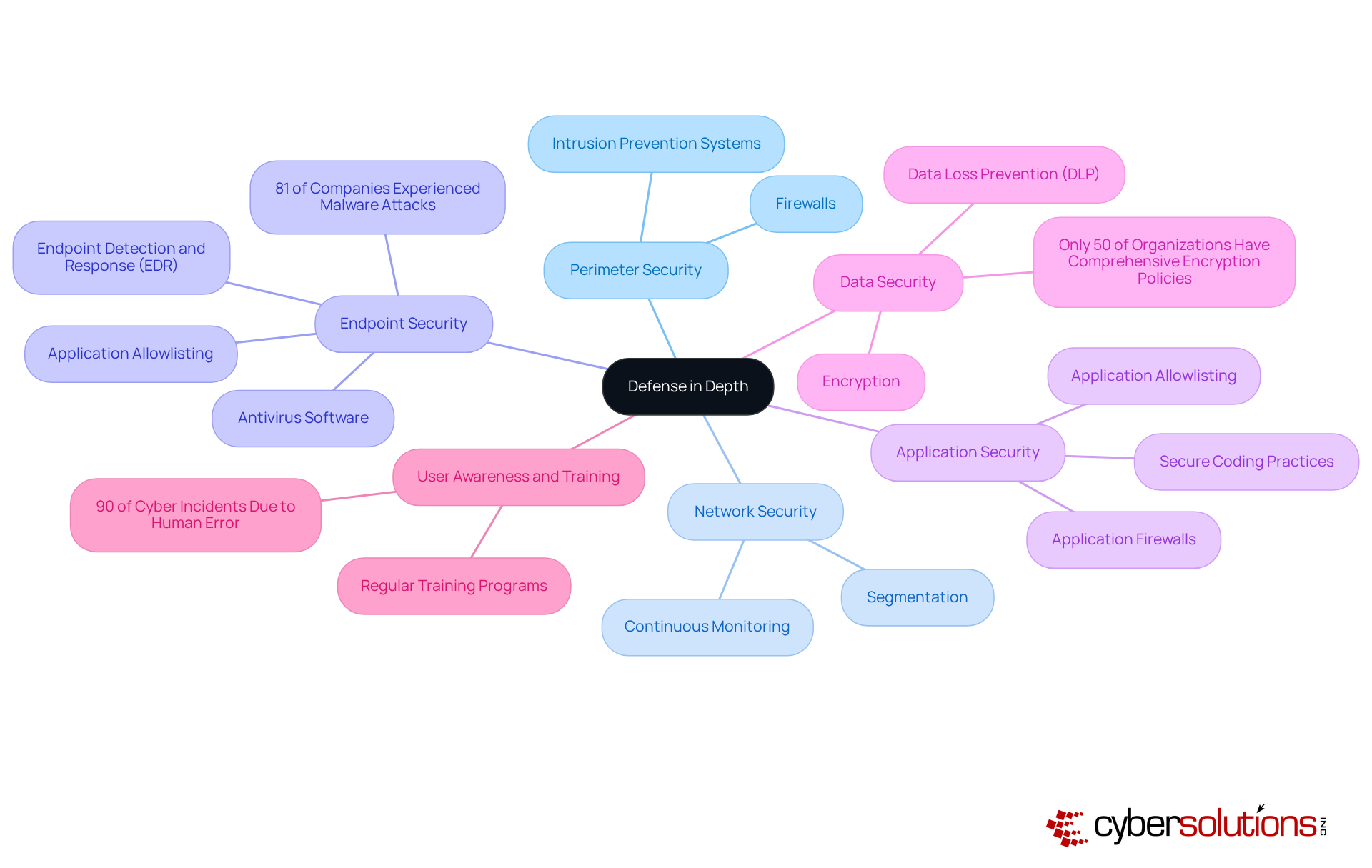
What is defense in depth? It is an essential cybersecurity strategy that employs multiple layers of protective measures to secure an organization's information and systems. In the healthcare sector, where safeguarding sensitive patient data is of utmost importance, this approach is particularly vital. The core principle of layered security ensures that if one tier fails, additional layers remain to provide protection, significantly reducing the likelihood of a successful cyberattack.
In healthcare, the integration of diverse protective measures—such as firewalls, intrusion detection systems, encryption, multi-factor authentication, and application allowlisting—creates a formidable defense against a variety of threats. Application allowlisting stands out as a critical component, proactively blocking unauthorized or malicious software from executing, thus minimizing the attack surface and vulnerabilities. Centralized management and continuous monitoring capabilities further enhance its effectiveness, allowing organizations to efficiently manage allowlists across all devices and swiftly detect unauthorized software attempts.
Real-world examples underscore the effectiveness of multi-layered security controls. In 2024, healthcare entities that adopted a multi-layered strategy reported a remarkable 93% decrease in data breaches compared to those relying on single-layer protections. Moreover, the implementation of Security Information and Event Management (SIEM) solutions has facilitated real-time threat intelligence, enabling organizations to swiftly identify and respond to suspicious activities.
The fundamental principles of defense in depth for healthcare encompass:
Ultimately, adopting a layered approach is crucial for healthcare organizations striving to maintain compliance with regulations like HIPAA while effectively protecting sensitive patient information from evolving cyber threats. As Stephen Kines, COO/Co-Founder of Goldilock, emphasizes, "To combat these intelligent threats, businesses must adopt a multilayered cybersecurity approach.

In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. What is defense in depth refers to the idea of layered protection, derived from military tactics, which emphasizes the necessity of employing multiple levels of security to safeguard essential assets. This strategy began gaining traction in the late 1990s and early 2000s as organizations encountered increasingly sophisticated cyber threats. Initially, protective measures were often isolated, primarily focusing on boundary safeguards. However, as cyberattacks grew in complexity and frequency, the necessity of understanding what is defense in depth became evident for a multi-layered approach.
Currently, layered protection integrates various technologies and practices, such as:
These exemplify what is defense in depth in illustrating a holistic view of cybersecurity. A pivotal component of this strategy is application allowlisting, which proactively prevents unauthorized or malicious applications from executing, thereby minimizing the attack surface and reducing vulnerabilities. This is particularly critical in sectors like healthcare, where compliance with regulations such as HIPAA, PCI-DSS, and GDPR is essential.
Features of application allowlisting, including:
Significantly enhance its effectiveness in protecting sensitive data. Moreover, the integration of advanced technologies like artificial intelligence (AI) and machine learning (ML) has become vital for improving threat detection and risk mitigation. Organizations are also adopting additional security layers, such as:
To strengthen their defenses.
Statistics reveal that 43% of cyberattacks target small businesses, underscoring the urgency of this approach for healthcare entities. Furthermore, the principle of least privilege plays a crucial role in safeguarding sensitive data, ensuring that users have only the minimum access necessary for their roles. As companies grapple with challenges like outdated anti-malware software and untrained staff, it is increasingly essential to know what is defense in depth, as a robust strategy, including application allowlisting, is necessary to combat evolving cyber threats.
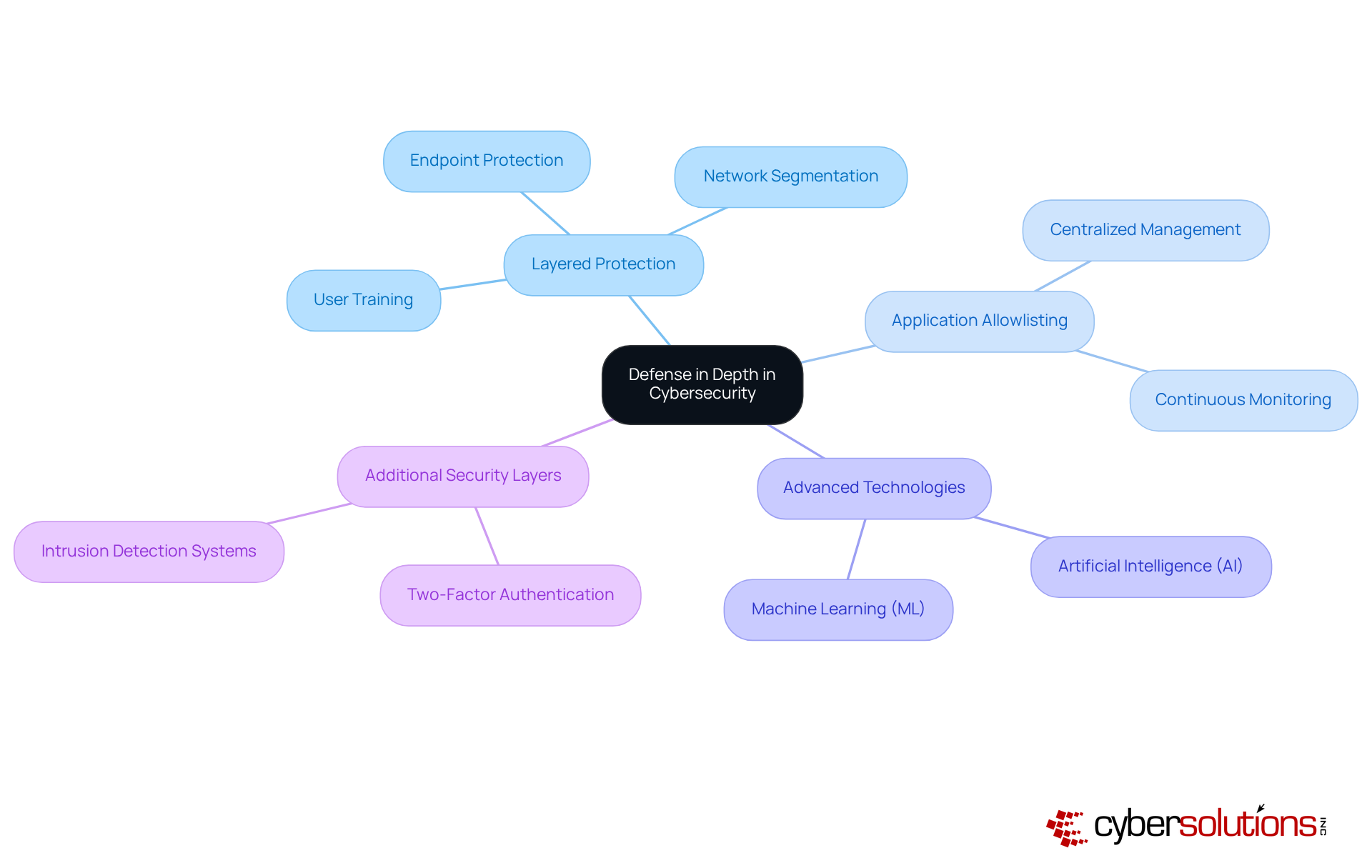
In today's healthcare landscape, a robust cybersecurity strategy is not just an option; it is a necessity. A defense in depth strategy encompasses several critical layers that work together to fortify an organization's cybersecurity posture:
What is defense in depth involves each layer serving a distinct purpose, collectively enhancing the entity's resilience against cyber threats. As the endpoint protection market is expected to expand from USD 13.37 billion in 2023 to USD 31.2 billion by 2032, investing in these layers is not merely a necessity but a strategic benefit for healthcare entities navigating the intricacies of contemporary cybersecurity. Moreover, the growth of remote work has heightened endpoint protection challenges, requiring increased vigilance from system administrators. Partnering with Cyber Solutions ensures that your systems remain secure, compliant, and audit-ready at all times.
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. Understanding what is defense in depth provides numerous advantages for entities, particularly in this sensitive field.
Enhanced Security: With multiple layers of protection, organizations significantly reduce the likelihood of a successful breach. To understand what is defense in depth, one can see how this strategy effectively minimizes weaknesses across various attack vectors, ensuring a more robust protective stance. Application allowlisting, a critical component of this approach, proactively prevents unauthorized software from executing, further reducing the attack surface and minimizing vulnerabilities. Centralized management and continuous monitoring enhance the effectiveness of application allowlisting, ensuring immediate identification and blocking of threats.
Regulatory Compliance: A strong security framework aids entities in meeting stringent regulations such as HIPAA and GDPR. Notably, 85% of organizations report increased complexity in compliance requirements. A comprehensive strategy that answers what is defense in depth simplifies adherence to these regulations, reducing the risk of costly violations. Furthermore, 78% of entities allocate a dedicated cybersecurity budget, reflecting the growing recognition of compliance's significance in cybersecurity investments.
Risk Mitigation: By addressing various threat vectors, entities can better manage and mitigate risks associated with cyberattacks. Statistics indicate that 70% of companies experienced considerable disruptions from data breaches, underscoring the necessity of a proactive security approach. Cyber Solutions' incident response team, available for 24-hour on-site support, plays a crucial role in containing threats and facilitating rapid recovery.
Enhanced Incident Response: Layered defenses empower entities to recognize and address incidents more effectively, thereby reducing potential damage. Healthcare organizations that have adopted strategies based on what is defense in depth report shorter incident response times, enabling quicker recovery and minimizing operational impact. This is particularly critical, given that 70% of organizations have faced significant disruptions due to data breaches. The layered approach, which includes endpoint isolation and malware removal, ensures a faster and more complete recovery.
Cost-Effectiveness: While implementing multiple layers may necessitate an upfront investment, the long-term savings from avoiding breaches and compliance fines can be substantial. For instance, the average cost of a data breach escalated to $4.88 million in 2024, highlighting the financial advantages of investing in a comprehensive security framework. Organizations that focus on what is defense in depth often experience lower costs associated with data breaches and improved overall financial health.

Implementing a defense in depth strategy is not merely advisable but essential for healthcare organizations striving to protect sensitive patient information from cyber threats. By integrating multiple layers of security, this approach significantly bolsters system resilience, ensuring that if one layer falters, others remain intact to provide ongoing protection. This multi-faceted method is particularly critical in the healthcare sector, where adherence to regulations like HIPAA is non-negotiable.
Key arguments underscore the necessity of layered security measures, including:
Together, these elements forge a robust defense against potential breaches. Organizations that embrace a defense in depth approach witness substantial reductions in data breaches and enhanced compliance with regulatory standards. Additionally, the advantages extend beyond security, offering cost-effectiveness and improved incident response capabilities.
The importance of grasping and implementing defense in depth cannot be overstated. As cyber threats continue to evolve, healthcare organizations must prioritize this strategy to safeguard sensitive data and maintain patient trust. Investing in a comprehensive cybersecurity framework is not just a necessity; it is a strategic imperative that secures the longevity and integrity of healthcare systems in an increasingly digital landscape.
What is defense in depth in cybersecurity?
Defense in depth is a cybersecurity strategy that employs multiple layers of protective measures to secure an organization's information and systems, significantly reducing the likelihood of a successful cyberattack.
Why is defense in depth particularly important in the healthcare sector?
In the healthcare sector, safeguarding sensitive patient data is crucial, making a multi-layered security approach essential to protect against various threats.
What are some protective measures included in a defense in depth strategy?
Protective measures include firewalls, intrusion detection systems, encryption, multi-factor authentication, and application allowlisting.
What role does application allowlisting play in defense in depth?
Application allowlisting proactively blocks unauthorized or malicious software from executing, minimizing the attack surface and vulnerabilities within an organization.
How does centralized management and continuous monitoring enhance defense in depth?
Centralized management allows organizations to efficiently manage allowlists across all devices, while continuous monitoring enables swift detection of unauthorized software attempts and other suspicious activities.
What evidence supports the effectiveness of a multi-layered security strategy in healthcare?
In 2024, healthcare entities that adopted a multi-layered strategy reported a 93% decrease in data breaches compared to those relying on single-layer protections.
What is the significance of Security Information and Event Management (SIEM) solutions in defense in depth?
SIEM solutions facilitate real-time threat intelligence, enabling organizations to quickly identify and respond to suspicious activities.
What are the fundamental principles of defense in depth for healthcare?
The fundamental principles include layered security, continuous monitoring, and incident response planning to identify, contain, and mitigate breaches.
How does adopting a layered approach help healthcare organizations?
A layered approach helps healthcare organizations maintain compliance with regulations like HIPAA while effectively protecting sensitive patient information from evolving cyber threats.