
Cloud hosting support is revolutionizing business operations, delivering unmatched scalability, flexibility, and cost-efficiency through a network of virtual servers. For C-suite leaders, grasping the essentials of cloud hosting is vital. It empowers them to make informed decisions that align with their organizational goals and boost operational efficiency. Yet, as the digital landscape shifts, executives encounter the pressing challenge of choosing the right cloud service provider and implementing robust security measures.
How can leaders navigate this intricate terrain to maximize the benefits of cloud hosting while ensuring compliance and protection? The answer lies in understanding the current landscape of cloud services and the unique challenges that come with it. By addressing these issues head-on, executives can harness the full potential of cloud hosting, driving their organizations toward greater success.
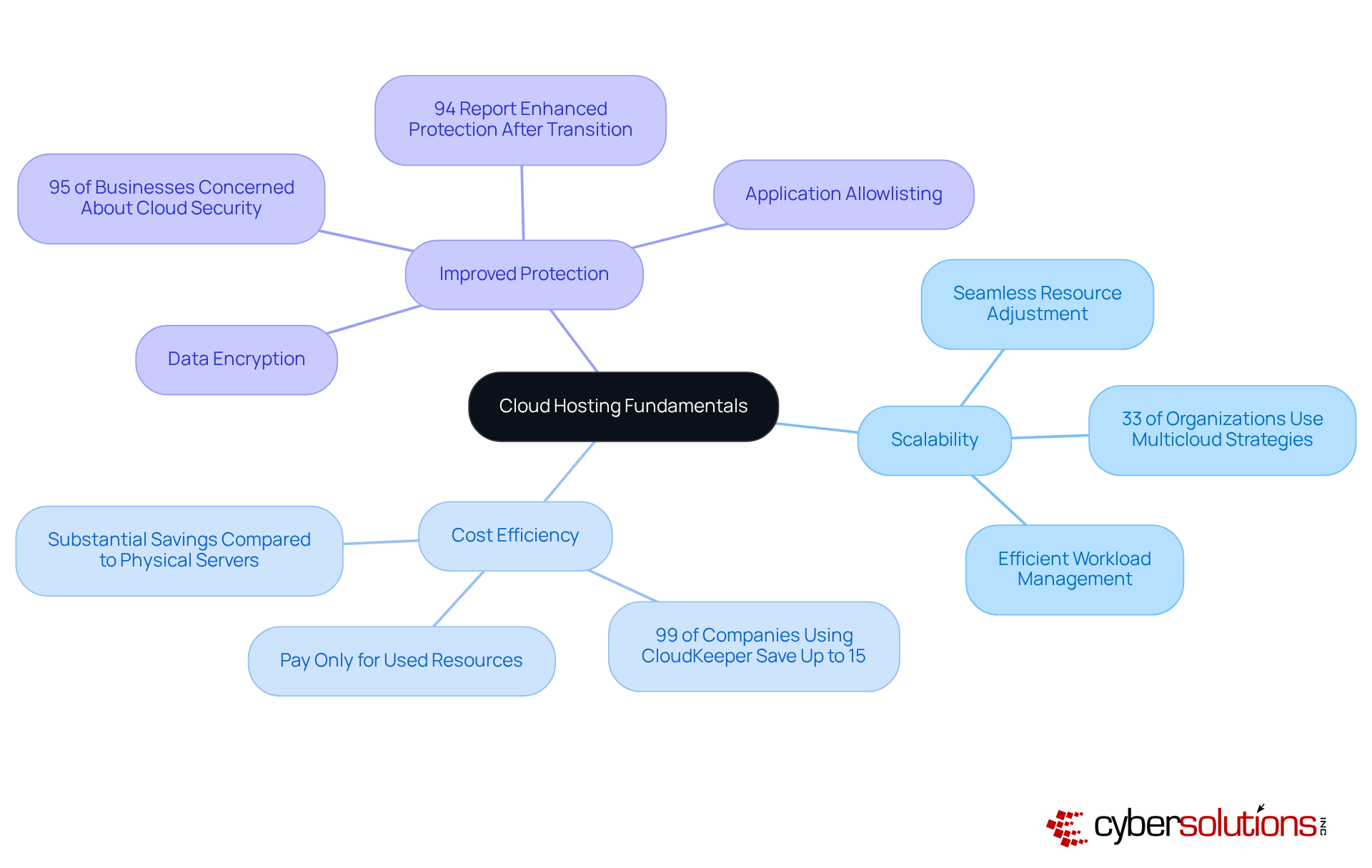
Cloud hosting support is revolutionizing the way businesses operate, leveraging a network of virtual servers to deliver applications and websites with unmatched scalability, flexibility, and cost-effectiveness. Unlike traditional hosting, which relies on a single physical server, cloud hosting support distributes resources across multiple servers, ensuring high availability and reliability. This shift is not just a trend; it’s a necessity in today’s digital landscape.
Scalability is one of the standout benefits of cloud hosting. Businesses can seamlessly adjust resources based on demand, enabling efficient workload management. In fact, 33% of organizations are now employing multicloud strategies to optimize their resource allocation. This adaptability, supported by effective cloud hosting support, is crucial for staying competitive in a fast-paced market.
Cost Efficiency is another compelling advantage. With cloud hosting support, organizations pay only for the resources they utilize, leading to substantial savings compared to the costs associated with maintaining physical servers. Significantly, 99% of companies utilizing CloudKeeper reported saving up to 15% on monthly expenses while achieving peak performance. This financial flexibility allows businesses to allocate funds to other critical areas.
Improved Protection is essential in an era where data breaches are rampant. Top online service providers implement robust protective measures, such as data encryption and frequent updates, to secure sensitive information. With 95% of businesses voicing concerns regarding online data protection, these measures are vital for upholding trust and compliance. Moreover, 94% of companies indicated enhanced protection following their transition to online services. A key element of this protection is application allowlisting, which proactively prevents unauthorized software from executing, thereby reducing vulnerabilities and assisting organizations in meeting compliance requirements such as HIPAA, PCI-DSS, and GDPR.
By understanding these fundamentals, C-suite leaders can make informed choices about online strategies that align with their organizational goals, ultimately improving operational efficiency and protection. As we approach a pivotal year for internet-based computing with significant AI integration, grasping these dynamics will be crucial for strategic planning.
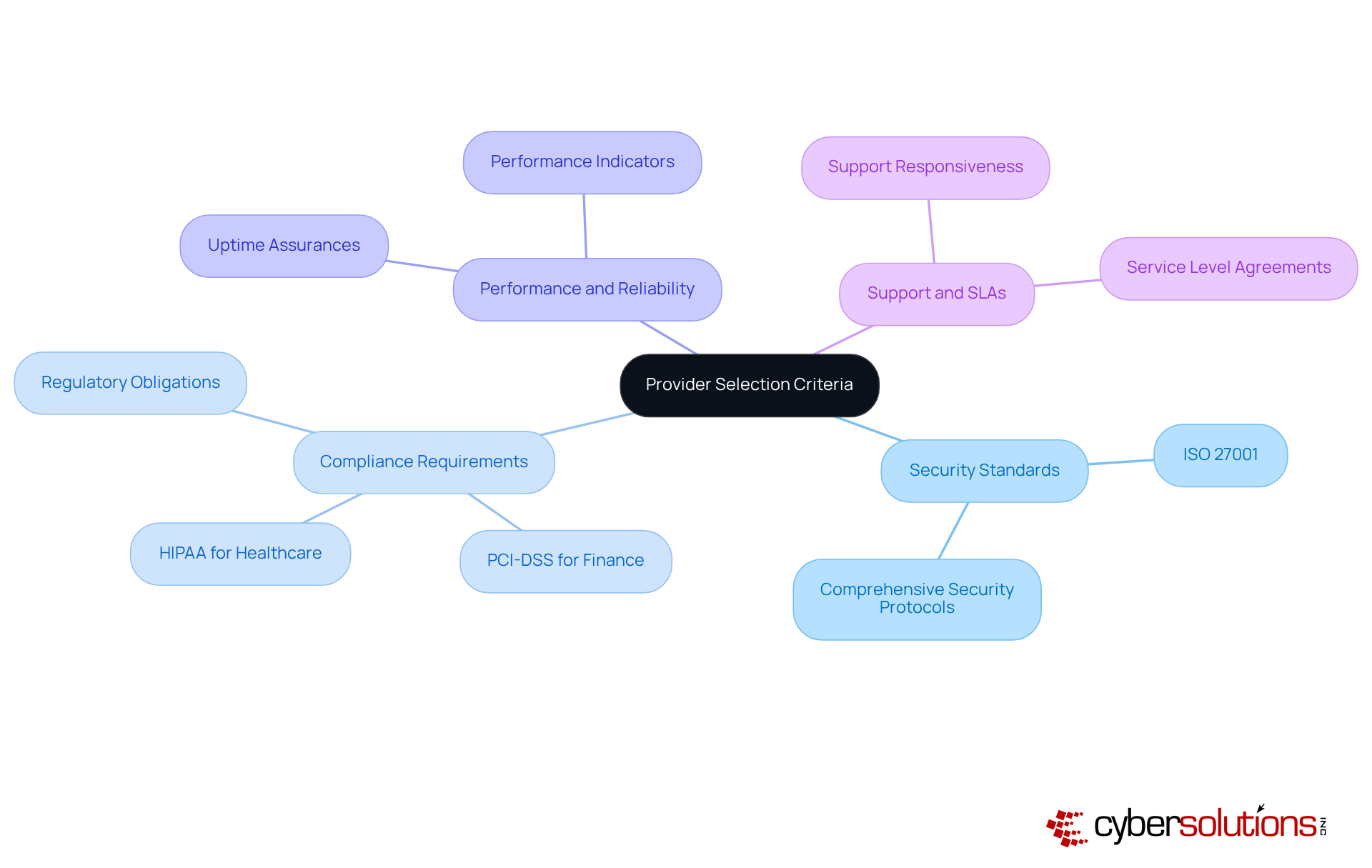
When it comes to selecting a cloud service provider, C-suite leaders must recognize the critical importance of making informed choices. The right provider can significantly enhance your organization's operational resilience and compliance readiness. Here are the essential criteria to prioritize:
By meticulously evaluating these criteria, executives can select a service provider that not only meets their technical requirements but also aligns with their strategic objectives. This careful consideration enhances overall operational resilience and compliance readiness.
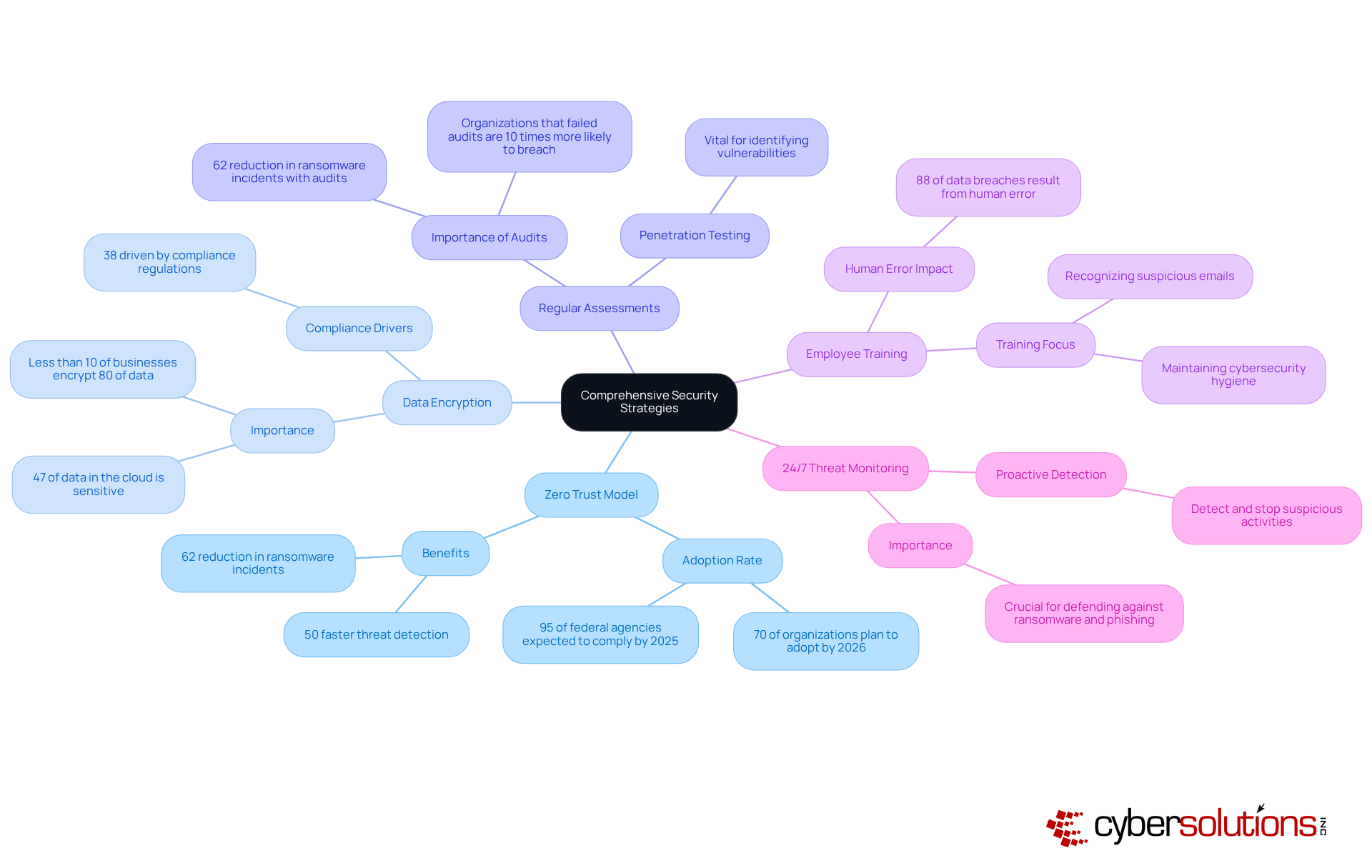
To enhance cloud security, C-suite leaders must adopt effective strategies that address the evolving landscape of cybersecurity threats:
Adopt a Zero Trust Model: This approach mandates that all users, regardless of their location, must be authenticated and authorized before accessing any resources. With over 70% of organizations planning to adopt Zero Trust by 2026, this model is becoming essential for safeguarding sensitive data against evolving threats.
Data Encryption: Encrypting sensitive data both in transit and at rest is crucial to protect it from unauthorized access. Despite the significance of encryption, fewer than 10% of businesses have secured 80% or more of their data online. Organizations that prioritize encryption can significantly mitigate risks associated with data breaches, which are increasingly prevalent in cloud environments.
Regular Assessments: Conducting periodic evaluations and penetration testing is vital for identifying vulnerabilities and addressing them proactively. Organizations that conduct regular audits can improve their protective stance and lessen the chances of breaches, as shown by the 62% reduction in ransomware incidents reported by those with advanced Zero Trust frameworks.
Employee Training: Ongoing training for employees on safety best practices is essential. With human error accounting for 88% of all data breaches, educating staff on safeguarding sensitive information can dramatically lower the risk of incidents. This includes training on recognizing suspicious emails and maintaining proper cybersecurity hygiene, which is crucial for minimizing operational disruption.
24/7 Threat Monitoring: Implement continuous monitoring to detect and stop suspicious activities before they escalate into threats, protecting your business from ransomware, phishing, and other malware attacks. This proactive approach is crucial for sustaining a strong defense posture.
By implementing these strategies, organizations can significantly lower their risk exposure and improve their overall security stance, positioning themselves to navigate the complexities of contemporary online environments effectively.
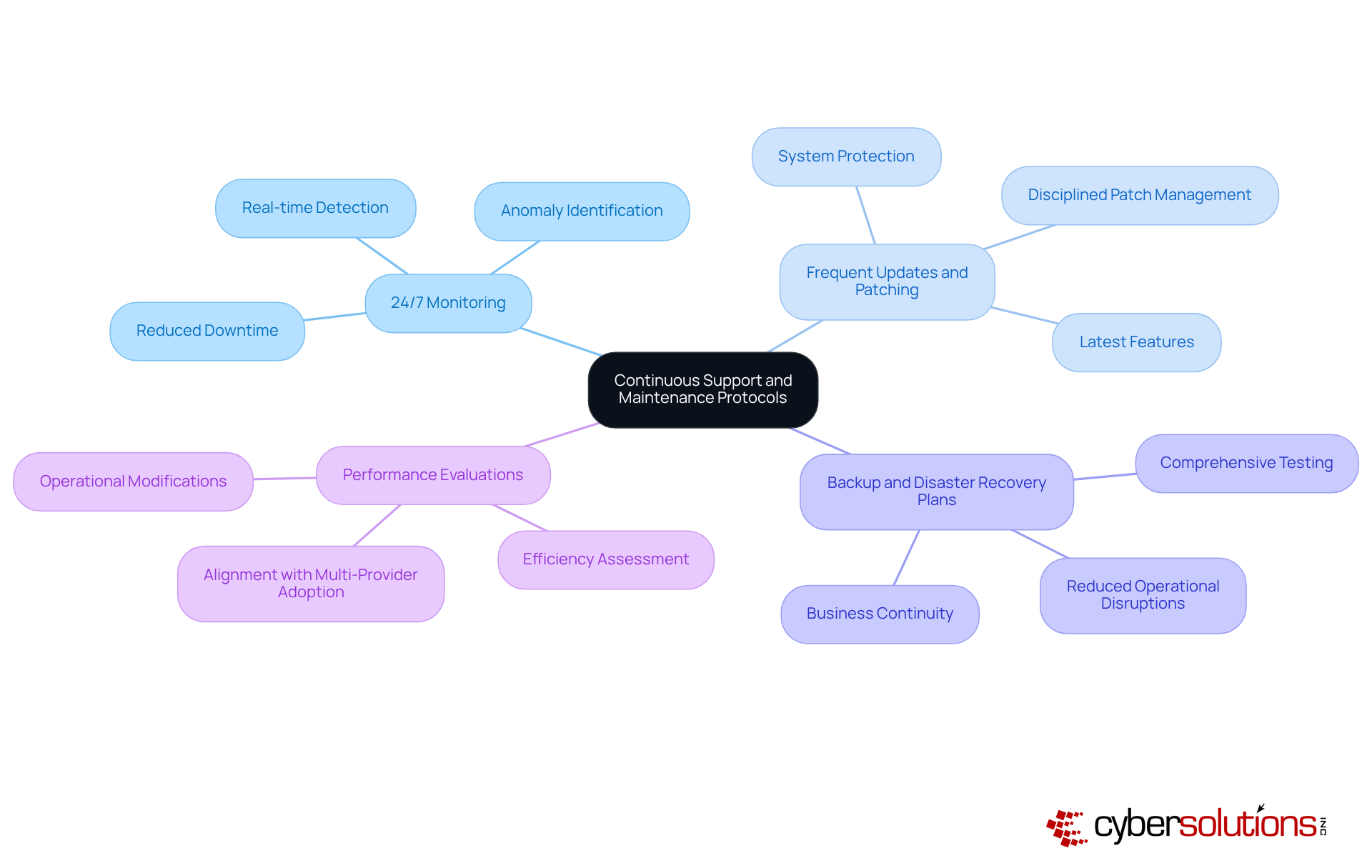
To ensure the ongoing success of cloud hosting solutions, C-suite leaders must establish robust support and maintenance protocols that encompass several key practices:
24/7 Monitoring: Continuous monitoring of cloud environments is crucial for real-time detection and response to potential issues. Cyber Solutions provides 24/7 network monitoring to identify anomalies and vulnerabilities, ensuring swift action to prevent downtime or breaches. This proactive approach significantly reduces the risk of undetected breaches, as organizations lacking 24/7 monitoring are far more susceptible to cyberattacks.
Frequent Updates and Patching: Regular updates and patch management are essential for maintaining system protection and ensuring that online environments are equipped with the latest features. Unpatched vulnerabilities account for a substantial percentage of online security breaches, highlighting the necessity for a disciplined approach to patch management.
Backup and Disaster Recovery Plans: Developing and rigorously testing comprehensive backup and disaster recovery plans is vital for ensuring business continuity in the event of a failure. Organizations that prioritize these plans can drastically reduce downtime and operational disruptions, which can average millions annually due to compromised online accounts.
Performance Evaluations: Conducting regular performance evaluations allows companies to assess the efficiency of their online solutions and implement necessary modifications. This practice not only enhances operational efficiency but also aligns with the growing trend of multi-provider adoption, where many entities utilize various service providers for increased flexibility.
By implementing these protocols, organizations can maintain optimal performance and security in their cloud environments, leveraging Cyber Solutions' comprehensive managed IT and cybersecurity services, which include cloud hosting support, endpoint protection, and threat detection.
Maximizing cloud hosting support is not just beneficial; it’s essential for C-suite leaders who want to enhance their organizations' operational efficiency and security. Understanding the fundamental benefits of cloud hosting - like scalability, cost efficiency, and improved protection - empowers executives to make informed decisions that align with their strategic goals. This proactive approach not only fosters a competitive edge but also equips businesses to navigate the complexities of the digital landscape effectively.
Key insights throughout this article underscore the importance of selecting the right cloud service provider. Criteria such as security standards, compliance requirements, and support agreements are crucial in this decision-making process. Moreover, implementing robust security strategies - such as adopting a Zero Trust model and conducting regular assessments - can significantly mitigate risks associated with cloud environments. Establishing continuous support and maintenance protocols ensures that organizations maintain optimal performance and security.
In light of these best practices, it’s clear that investing in cloud hosting support transcends a mere technical upgrade; it’s a strategic imperative. As organizations increasingly rely on cloud solutions, C-suite leaders must prioritize these practices to safeguard their operations and drive innovation. Embracing these strategies will empower businesses to thrive in an ever-evolving digital landscape, reinforcing their commitment to security, efficiency, and growth.
What is cloud hosting support?
Cloud hosting support involves leveraging a network of virtual servers to deliver applications and websites, offering unmatched scalability, flexibility, and cost-effectiveness compared to traditional hosting, which relies on a single physical server.
What are the benefits of cloud hosting?
The main benefits of cloud hosting include scalability, cost efficiency, and improved protection. It allows businesses to adjust resources based on demand, save on costs associated with physical servers, and implement robust security measures to protect sensitive information.
How does scalability work in cloud hosting?
Scalability in cloud hosting allows businesses to seamlessly adjust their resources based on demand, enabling efficient workload management and helping them stay competitive in a fast-paced market.
What is the significance of cost efficiency in cloud hosting?
Cost efficiency in cloud hosting means organizations only pay for the resources they utilize, leading to savings. For instance, 99% of companies using CloudKeeper reported saving up to 15% on monthly expenses while achieving peak performance.
How does cloud hosting improve data protection?
Cloud hosting improves data protection through robust measures like data encryption and frequent updates. These security practices are crucial as 95% of businesses express concerns about online data protection.
What are application allowlisting and its benefits?
Application allowlisting is a security measure that prevents unauthorized software from executing, thereby reducing vulnerabilities. It helps organizations meet compliance requirements such as HIPAA, PCI-DSS, and GDPR.
Why is understanding cloud hosting fundamentals important for C-suite leaders?
Understanding cloud hosting fundamentals enables C-suite leaders to make informed decisions about online strategies that align with their organizational goals, ultimately improving operational efficiency and protection.