
In today's world, where cyber threats are more prevalent than ever, the importance of Security Information and Event Management (SIEM) systems cannot be overstated, especially for organizations in the healthcare sector. These robust tools not only enable real-time monitoring and threat detection but also help ensure compliance with stringent regulations, acting as a vital line of defense against ever-evolving cyber risks.
However, a pressing question arises: how can organizations truly maximize the effectiveness of their SIEM deployments to enhance their cybersecurity posture? This article explores best practices for leveraging SIEM events, providing insights that can transform security strategies and strengthen defenses against increasingly sophisticated threats. By understanding the unique challenges faced by healthcare organizations, we can better appreciate the critical role that SIEM systems play in safeguarding sensitive information and maintaining trust in healthcare services.
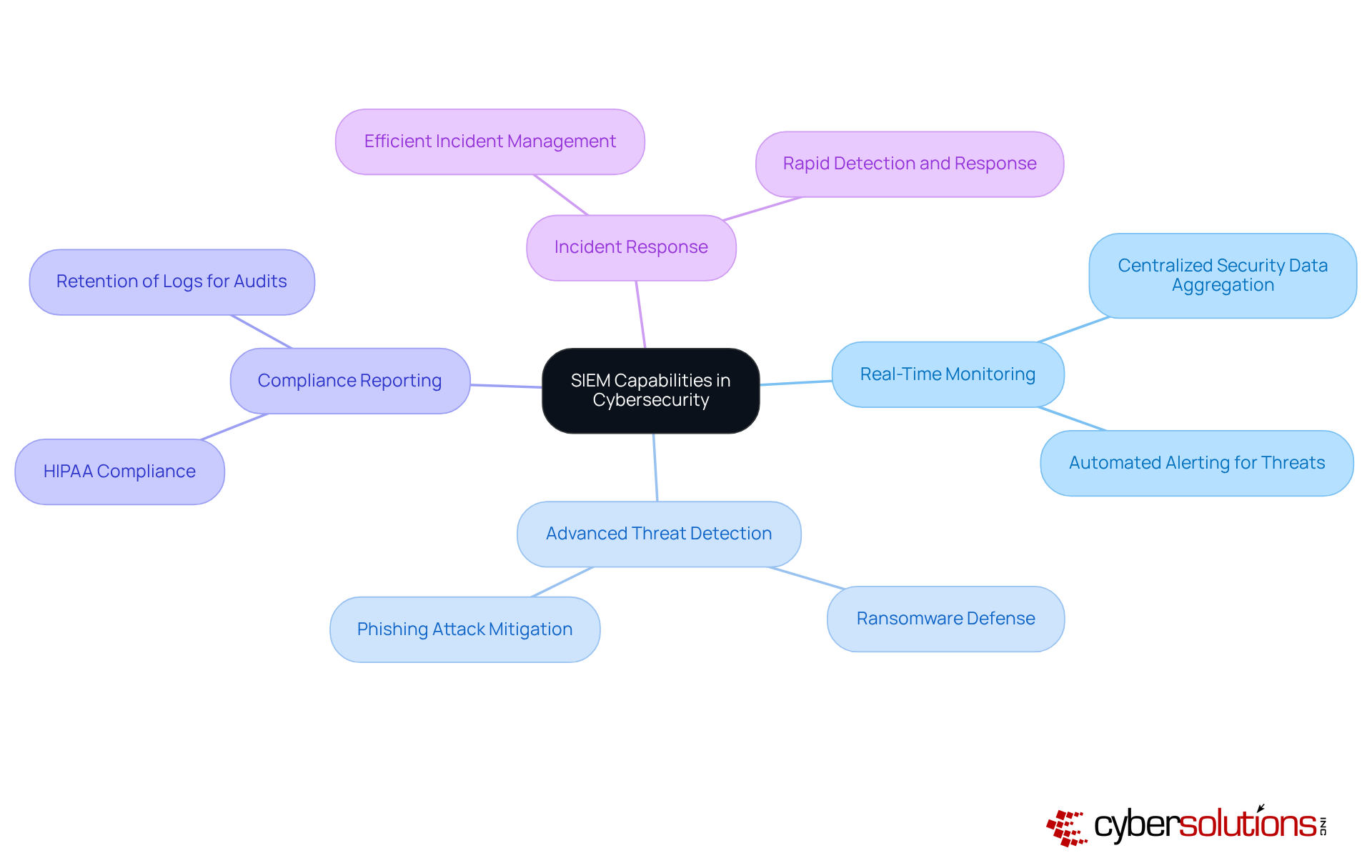
In today's digital age, cybersecurity is not just an option; it's a necessity, especially in healthcare. SIEM events play a crucial role in this landscape, acting as a centralized hub for aggregating and analyzing security data from various sources. These systems empower organizations with capabilities like real-time monitoring, advanced threat detection, compliance reporting, and efficient incident response.
Consider the implications for healthcare CFOs: with Cyber Solutions' 24/7 network monitoring and alerts, organizations can swiftly identify anomalies and potential vulnerabilities. This proactive approach is vital in defending against threats such as ransomware and phishing attacks. By leveraging these features, healthcare institutions can significantly bolster their security posture while ensuring they meet operational objectives. For instance, SIEM systems enable healthcare organizations to efficiently satisfy HIPAA compliance requirements, all while enhancing their overall security framework.
Moreover, compliance with stringent cybersecurity standards is essential for safeguarding Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). This is not just about regulatory adherence; it’s about maintaining eligibility for lucrative government contracts. As cyber risks evolve, the integration of SIEM events becomes increasingly critical for protecting sensitive data and ensuring regulatory compliance. Ultimately, this enhances organizational resilience in a complex digital environment, allowing healthcare entities to focus on what they do best - providing quality care.
Deploying security information and event management (SIEM events) solutions is not just beneficial; it’s essential for enhancing a company’s cybersecurity initiatives. In an era where cyber threats are increasingly sophisticated, organizations must prioritize their defenses. Here’s how these solutions can transform your cybersecurity posture:
Real-Time Threat Detection: SIEM events allow Security Information and Event Management systems to continuously monitor network activity, enabling rapid identification of potential threats before they escalate into serious incidents. This proactive approach is crucial; organizations that invest in early detection mechanisms can safeguard their revenue and uphold trust.
Centralized Compliance Management: By consolidating information from multiple sources, SIEM events solutions simplify adherence to regulations like GDPR and PCI-DSS, alleviating the workload on compliance teams. With only 34.4% of entities fully compliant with email-related regulations, effective deployment of these solutions is vital for meeting regulatory obligations.
Improved Incident Management: SIEM events enable faster responses to incidents by supplying security teams with actionable insights and automated notifications, allowing for prompt threat mitigation. For instance, organizations that have embraced comprehensive incident response strategies report significantly improved recovery times, with some achieving a 30% reduction in incident response time after implementing these solutions.
Cost Efficiency: By preventing breaches and minimizing downtime, SIEM events can result in substantial cost savings, making them a wise investment for organizations of all sizes. The average cost of a data breach in 2024 is projected to reach $4.35 million, highlighting the financial necessity for robust cybersecurity measures.
In summary, utilizing SIEM events not only enhances your security stance but also promotes operational efficiency, making them indispensable in today’s threat landscape.

To ensure a successful SIEM deployment, organizations must prioritize best practices that enhance their security posture:
Define Clear Use Cases: Identifying specific use cases that align with security objectives is crucial. This approach customizes the security information and event management setup to meet distinct requirements, ensuring that the deployment is both relevant and effective.
Prioritize Log Sources: Start by collecting logs from critical systems and applications. This prioritization guarantees that the most vital data is monitored and analyzed, allowing organizations to focus their resources where they matter most.
Tune Alerts to Reduce False Positives: Regularly adjusting alert thresholds and parameters is essential to minimize false positives. Overwhelming security teams with unnecessary alerts can lead to alert fatigue, undermining the effectiveness of the SIEM system.
Consistently Assess and Revise SIEM Settings: The risk environment is ever-changing, and so should be the SIEM settings. Regular reviews ensure that the system remains effective against emerging threats, adapting to new challenges as they arise.
Train Security Personnel: A well-trained security team is vital. Ensuring that personnel understand the capabilities of the SIEM system and can respond to alerts appropriately enhances the overall security framework.
By adhering to these best practices, organizations can significantly improve the efficiency of their management solutions for SIEM events, fortifying their defenses against evolving threats.

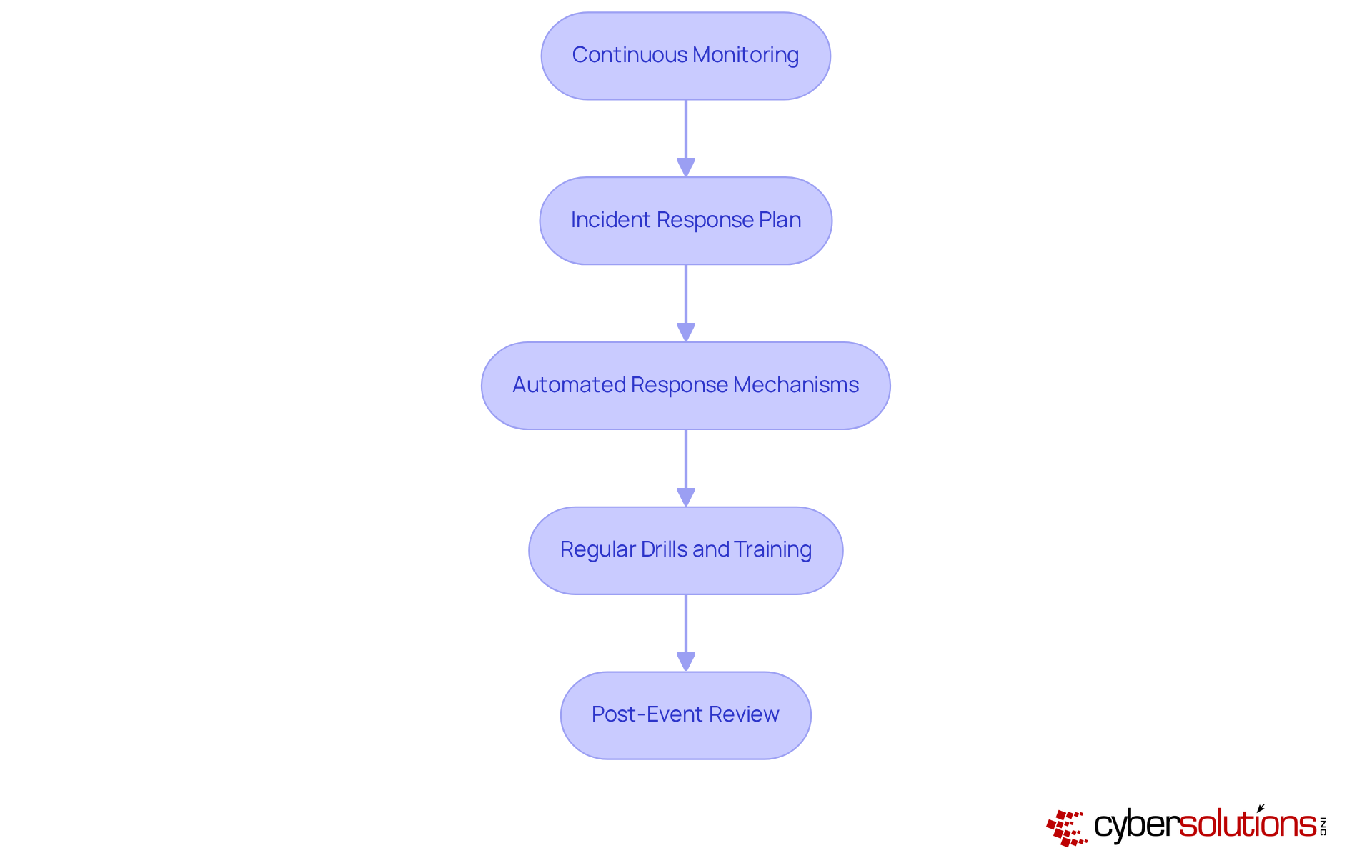
In today's digital landscape, continuous monitoring and effective incident response are not just important; they are essential for a robust cybersecurity strategy. Organizations must adopt the following protocols to safeguard their operations:
Continuous Monitoring: Utilize SIEM events to continuously analyze network traffic and system logs for suspicious activities. Cyber Solutions provides round-the-clock monitoring, identifying anomalies and potential vulnerabilities. This proactive approach enables early risk identification and prompt measures to prevent downtime or breaches. Tailored access controls ensure that only authorized users can access sensitive information.
Incident Response Plan: Develop a comprehensive incident response plan that clearly defines roles, responsibilities, and procedures for addressing security incidents. Regular testing and revisions of this plan are crucial to ensure its effectiveness and alignment with evolving risks. Insights from case studies can enhance the plan's relevance and applicability.
Automated Response Mechanisms: Integrate automated response capabilities that can act immediately upon detecting threats, such as isolating affected systems or blocking malicious IP addresses. This proactive strategy is vital for minimizing damage from SIEM events like ransomware and phishing attacks, supported by advanced threat intelligence.
Regular Drills and Training: Conduct frequent emergency response exercises to ensure all team members are well-prepared for their roles during real incidents. Organizations that engage in regular training can improve response times by up to 35%, significantly boosting overall cybersecurity confidence.
Post-Event Review: After any incident, perform a thorough examination to assess the events, evaluate response effectiveness, and identify areas for improvement in the response plan. This reflective practice is essential for the continuous enhancement of security protocols and can be informed by previous case studies to refine strategies.
By implementing these protocols, organizations can strengthen their resilience against cyber threats and ensure a swift, effective response to incidents, ultimately protecting their operations and reputation.
Maximizing the effectiveness of Security Information and Event Management (SIEM) systems is not just important; it’s essential for organizations striving to bolster their cybersecurity frameworks. In a world where cyber threats are increasingly sophisticated, understanding and leveraging SIEM capabilities allows organizations to proactively defend against emerging threats while ensuring compliance with regulatory standards. This proactive approach not only secures sensitive data but also fortifies the overall resilience of the organization.
To effectively deploy SIEM systems, organizations should focus on several key strategies:
The time to act is now. By adopting these strategies, organizations can significantly improve their cybersecurity posture and foster operational efficiency. Investing in robust SIEM solutions is a strategic move that not only safeguards valuable assets but also maintains trust in an ever-evolving digital environment. The question is: can your organization afford to wait?
What is the role of SIEM in cybersecurity?
SIEM acts as a centralized hub for aggregating and analyzing security data from various sources, enabling organizations to monitor security events in real-time, detect advanced threats, report on compliance, and respond efficiently to incidents.
Why is cybersecurity particularly important in healthcare?
Cybersecurity is crucial in healthcare to protect sensitive data, ensure compliance with regulations like HIPAA, and defend against threats such as ransomware and phishing attacks, which can compromise patient information and organizational integrity.
How can SIEM systems benefit healthcare organizations?
SIEM systems help healthcare organizations by providing 24/7 network monitoring and alerts, allowing for the swift identification of anomalies and vulnerabilities, thus enhancing their overall security posture and operational efficiency.
What compliance requirements do SIEM systems help healthcare organizations meet?
SIEM systems assist healthcare organizations in efficiently satisfying HIPAA compliance requirements and safeguarding Controlled Unclassified Information (CUI) and Federal Contract Information (FCI), which are essential for maintaining eligibility for government contracts.
How do SIEM capabilities enhance organizational resilience?
By integrating SIEM events, healthcare entities can better protect sensitive data, ensure regulatory compliance, and respond effectively to evolving cyber risks, allowing them to focus on providing quality care.