
In today's healthcare landscape, where cyber threats loom larger than ever, the significance of a robust HIPAA disaster recovery plan is paramount. This framework not only protects electronic protected health information (ePHI) but also ensures compliance with stringent regulations. As we delve into the seven critical steps for crafting an effective disaster recovery strategy, it’s essential to recognize that minimizing downtime and enhancing operational resilience are not just goals - they're necessities.
However, with a myriad of potential pitfalls and ever-evolving threats, how can healthcare organizations ensure their disaster recovery plans remain effective and relevant? The answer lies in a proactive approach that addresses the unique challenges faced by CFOs and other leaders in the field. By understanding the current cybersecurity landscape and its implications, organizations can better prepare themselves to navigate this complex environment.
A HIPAA disaster recovery strategy is not merely a document; it is a crucial plan that details how a healthcare organization will respond to emergencies that threaten the integrity of electronic protected health information (ePHI). In today’s landscape, where cybersecurity threats loom large, having a robust DRP is essential for safeguarding sensitive data.
Objectives: The goals of the DRP must be crystal clear. They should focus on minimizing downtime and ensuring the confidentiality, integrity, and availability of ePHI. This includes integrating strong cybersecurity measures like encryption and multi-factor authentication to protect against data breaches and unauthorized access.
Scope: It’s crucial to define the systems, processes, and data encompassed by the plan. Ensure that all critical components are included, particularly those related to HIPAA compliance and cybersecurity safeguards.
Compliance Requirements: Highlight the specific HIPAA regulations addressed by the plan. Every action taken during an emergency must comply with federal laws, including necessary technical safeguards like encryption and access controls.
Key Components: A comprehensive approach to crisis management includes elements such as data backup procedures, emergency operations protocols, and communication strategies. Additionally, proactive risk management strategies, continuous monitoring, and audit support are essential to maintain compliance and readiness for potential audits.
In conclusion, a well-structured HIPAA disaster recovery plan is indispensable for healthcare organizations. It not only protects ePHI but also fortifies the organization against the ever-evolving landscape of cybersecurity threats.
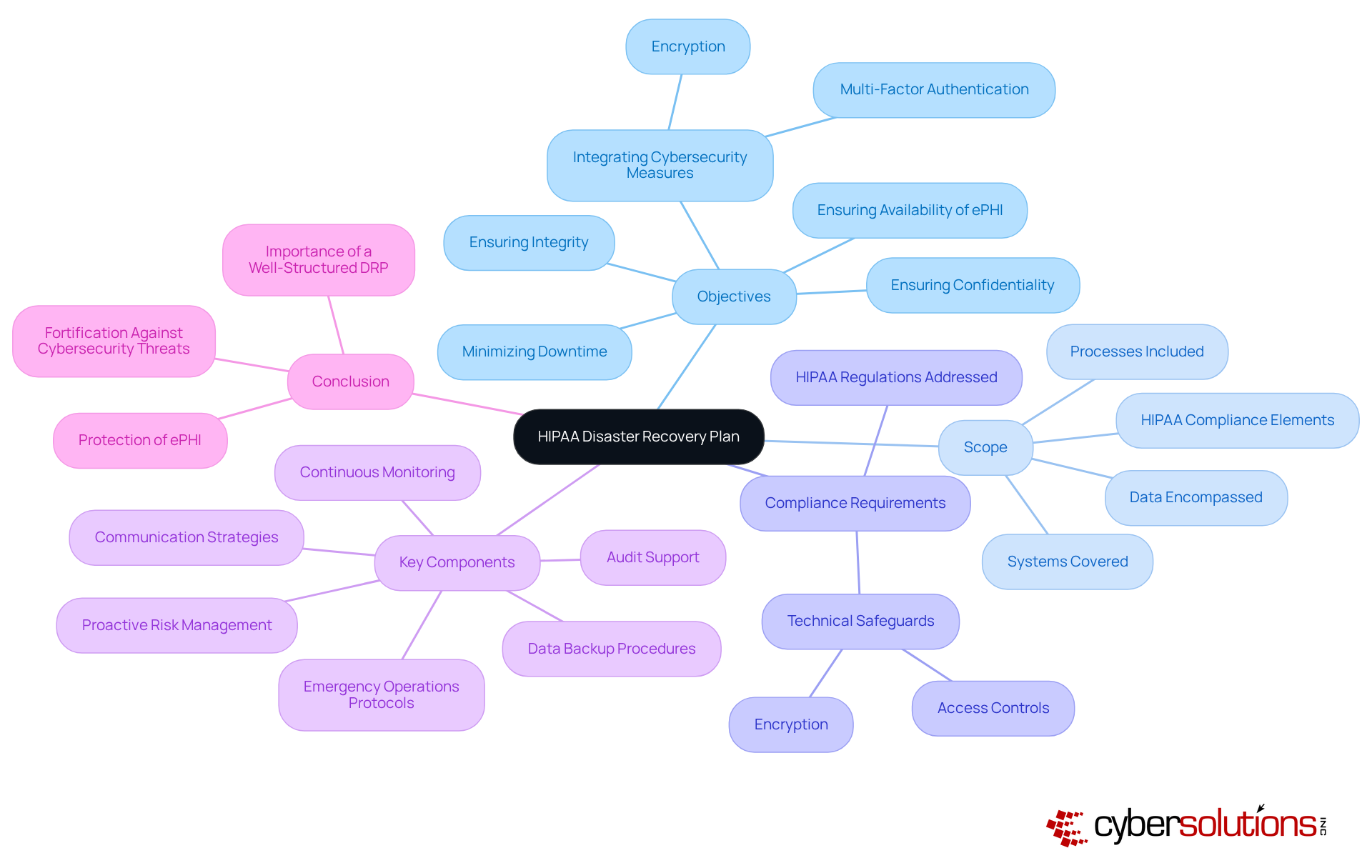
Establishing clear roles and responsibilities is vital for the successful implementation of HIPAA disaster recovery. In the face of increasing cybersecurity threats, healthcare organizations must prioritize effective team organization to ensure swift recovery during emergencies. Here are essential steps to ensure your team is prepared:
Studies show that merely 30% of groups have clearly outlined roles within their crisis management teams, emphasizing a notable area for enhancement. By creating defined roles, healthcare entities can improve their response abilities, ensuring a more efficient restoration process during emergencies.
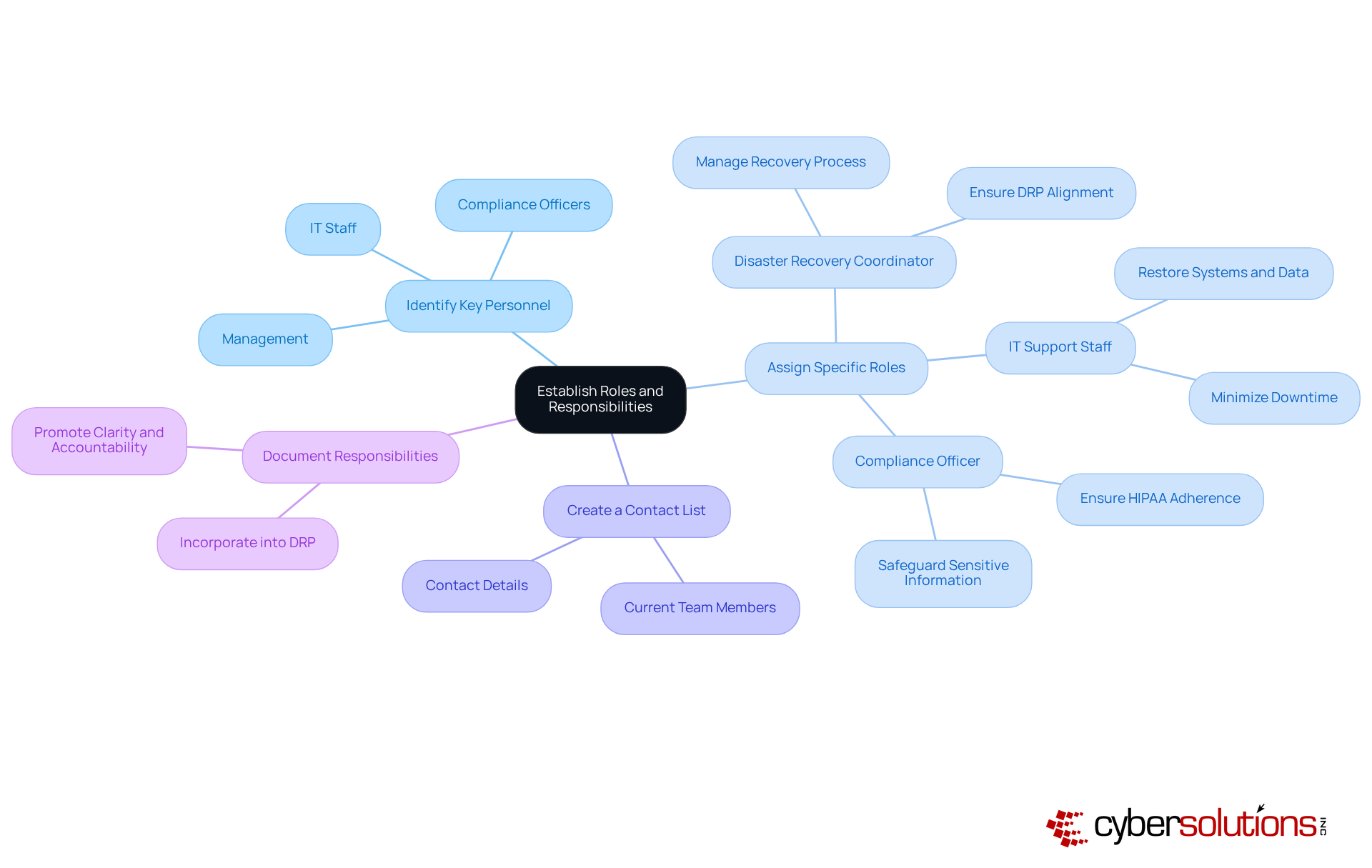
A comprehensive risk assessment is crucial for identifying potential threats to electronic Protected Health Information (ePHI) and understanding organizational vulnerabilities. In today’s healthcare landscape, cybersecurity is not just an option; it’s a necessity. With healthcare entities facing a staggering 58% of data breaches linked to vulnerabilities in third-party providers in 2023, the urgency for robust HIPAA disaster recovery planning has never been clearer.
Identify Potential Risks: Begin by considering various scenarios that could impact your organization, such as natural disasters, cyberattacks, and system failures. Each of these risks poses a significant threat to your operations and patient trust.
Evaluate Vulnerabilities: Next, assess your current systems and processes to identify weaknesses that could be exploited during a crisis. Regular updates to your risk assessment are essential, particularly after any significant changes in software or hardware.
Determine Likelihood and Impact: For every identified threat, evaluate both the likelihood of occurrence and the potential impact on your organization’s operations and compliance. This analysis is vital for effective risk management and ensuring compliance with HIPAA disaster recovery.
Prioritize Risks: Rank the identified risks based on their probability and potential impact. This prioritization allows you to focus your contingency efforts on the most critical areas. Organizations should revisit their risk assessments every 2-3 years, even if no major changes have occurred.
Document Findings: Finally, document the results of your risk assessment to guide the development of your HIPAA disaster recovery strategies. Utilizing Compliance as a Service (CaaS) can streamline this process, providing expert guidance and support for audit preparation. This not only helps maintain compliance with HIPAA and other regulations but also enhances your organization’s ability to respond effectively to audits, safeguarding against potential penalties and reputational damage.
In today’s healthcare landscape, developing a thorough inventory of critical assets is not just essential; it’s a cornerstone of effective disaster management planning and HIPAA disaster recovery compliance. Organizations must take proactive steps to ensure they are prepared for any eventuality. Here’s how:
By adhering to these steps, organizations can significantly enhance their emergency response capabilities and ensure compliance with HIPAA disaster recovery regulations, ultimately safeguarding sensitive patient information.
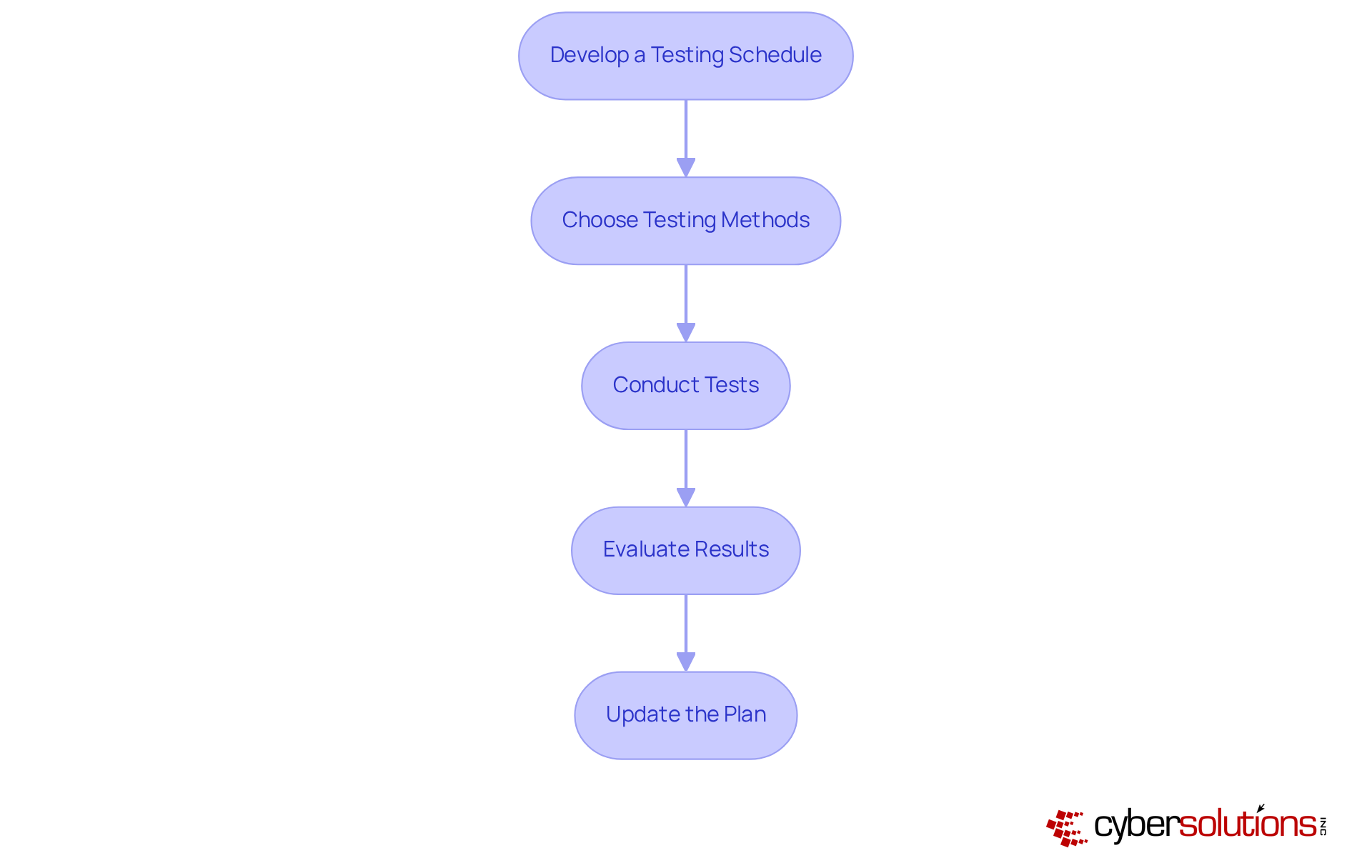
Establishing clear processes and procedures for HIPAA disaster recovery is vital for an effective response during a crisis. Why is this important? Because only 54% of entities have recorded emergency response plans, highlighting a significant gap in readiness. Implement the following steps to enhance your organization's resilience:
By following these best practices, healthcare entities can enhance their resilience and ensure compliance with HIPAA disaster recovery requirements, ultimately safeguarding patient data and maintaining trust.
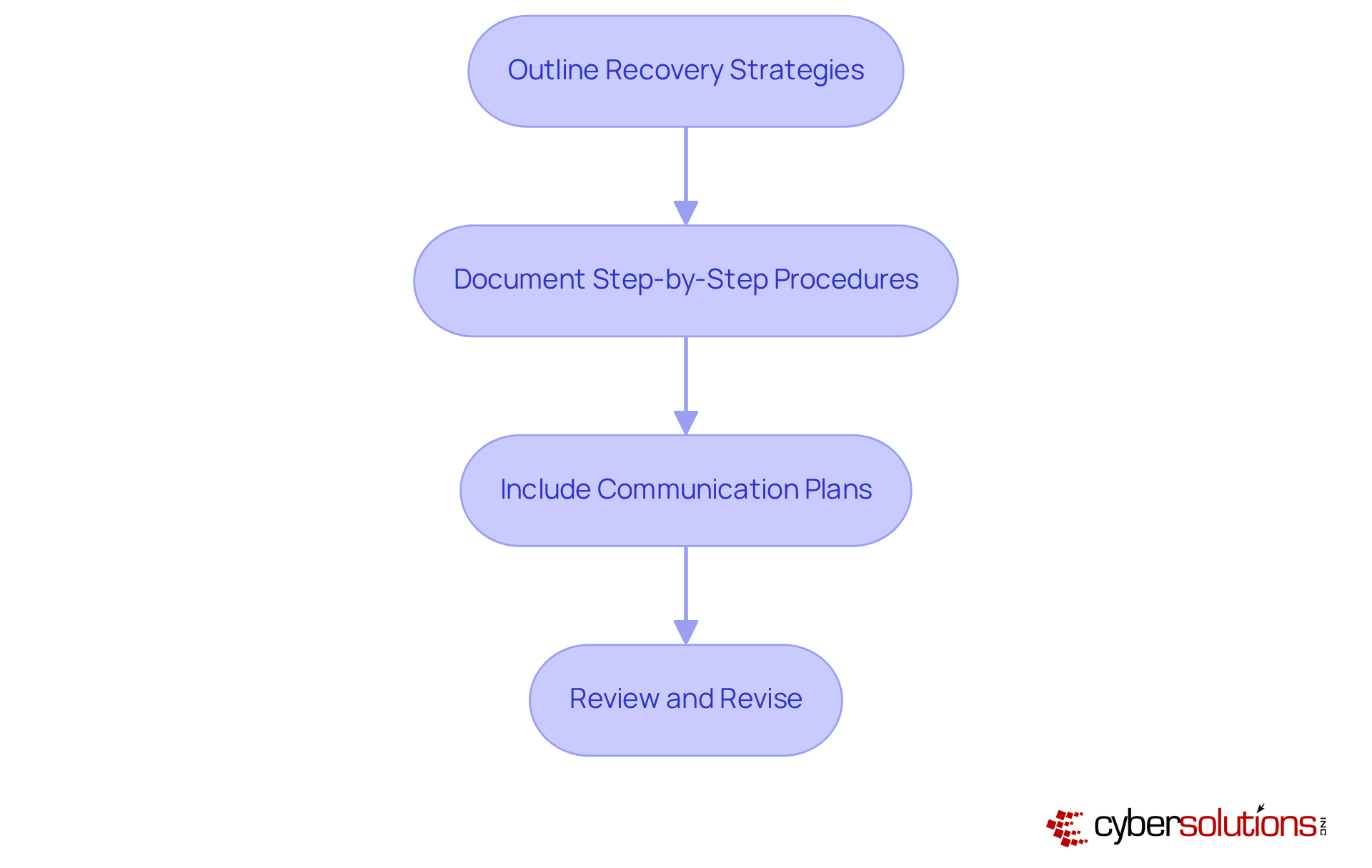
Regular evaluation of your emergency response strategy (ERS) is not just important; it’s essential for ensuring efficiency and durability in today’s cybersecurity landscape. With threats evolving rapidly, organizations must implement best practices to optimize their testing processes:
Develop a Testing Schedule: Establish a consistent testing schedule that includes both comprehensive full-scale tests and smaller, focused drills. Aim for annual full interruption tests across departments, with critical components evaluated quarterly or after significant system changes.
Choose Testing Methods: Select appropriate testing methods tailored to your organization's needs. Options include tabletop exercises, which replicate disaster situations to evaluate team reactions, and parallel testing, where the backup system operates alongside the main system to confirm restoration procedures without interrupting operations.
Conduct Tests: Execute the tests with full participation from all team members, ensuring they understand their roles and responsibilities. This collaborative approach enhances preparedness and identifies potential weaknesses in the disaster recovery plan (DRP). For instance, Cyber Solutions' experience with a healthcare provider demonstrated that having an incident response team physically present within a day helped contain a ransomware threat effectively.
Evaluate Results: After each test, thoroughly assess the outcomes to identify gaps or areas needing improvement. Frequent assessments assist organizations in comprehending their restoration capabilities and enhancing their strategies accordingly. The case study shows that a layered strategy-featuring endpoint isolation, malware elimination, and user education-facilitated a quicker and more thorough restoration.
Update the Plan: Revise the emergency response strategy based on insights gained from testing. Continuous updates ensure the DRP remains relevant and effective in addressing evolving threats and operational changes. The healthcare provider not only recovered ahead of schedule but also enhanced its security measures to safeguard patient data and operations against future threats.
Statistics reveal that only 54% of entities possess recorded contingency plans, and merely half of those that assess their CRPs do so annually or less often. Moreover, costs for restoration from ransomware surpassed $2.73 million per incident in 2024, underscoring the financial consequences of insufficient emergency planning. By prioritizing routine testing and adopting modern methods, organizations can significantly enhance their resilience against disruptions, ensuring compliance with regulations like HIPAA and implementing effective HIPAA disaster recovery to safeguard sensitive data. Incorporating the four C's of crisis management-communication, coordination, collaboration, and continuity-into your strategy is vital for successful restoration.
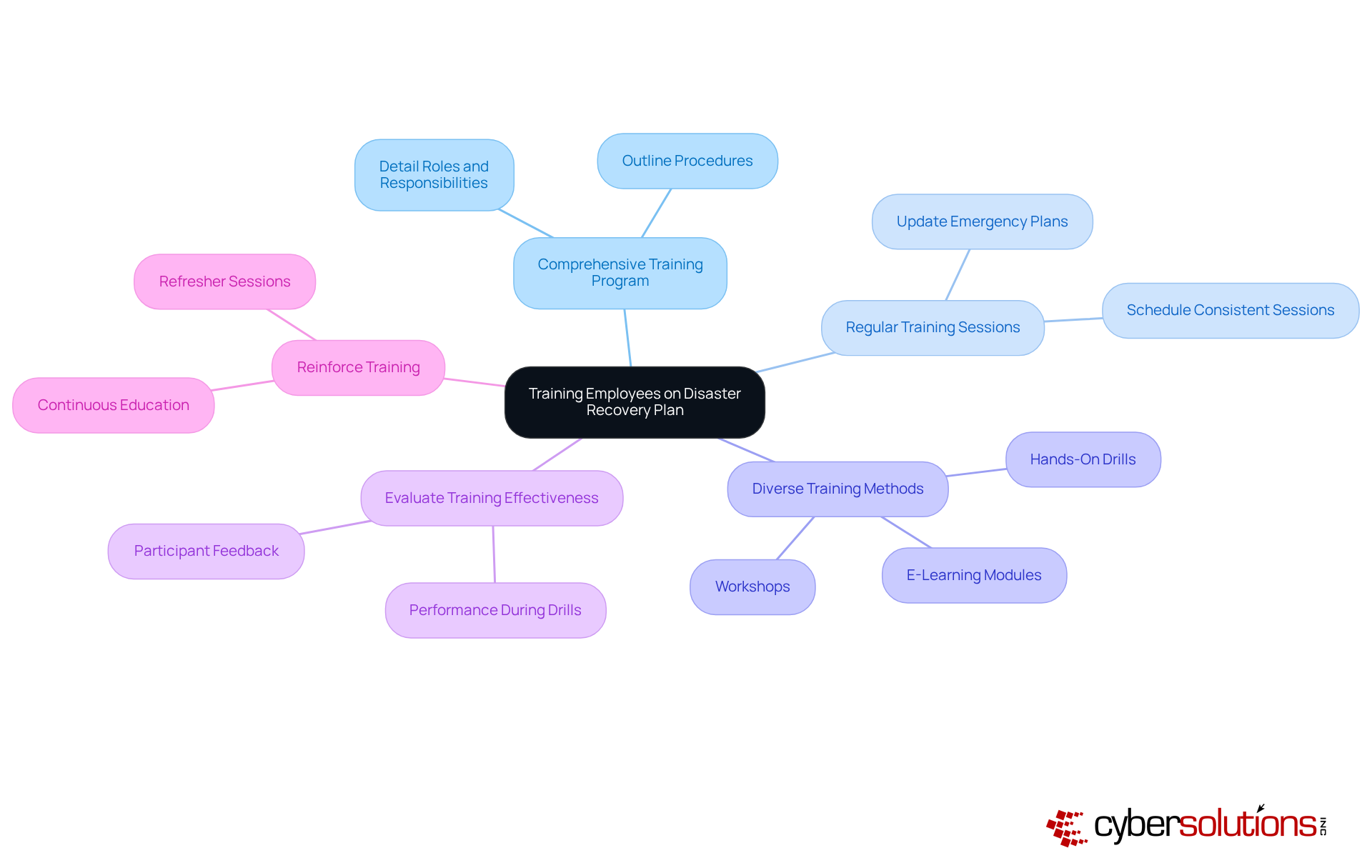
Training staff on the emergency response plan is crucial for ensuring a coordinated reaction during a crisis, especially in the context of HIPAA disaster recovery. Organizations must prioritize this training to safeguard their operations and personnel. To achieve this, consider implementing the following best practices:
A comprehensive HIPAA disaster recovery plan is not merely a regulatory requirement; it serves as a crucial framework for safeguarding electronic protected health information (ePHI) against unforeseen disasters. In today’s landscape of escalating cybersecurity threats, healthcare organizations must prioritize the establishment of a robust plan. This proactive approach not only ensures compliance with HIPAA regulations but also fortifies the protection of sensitive data during emergencies.
To effectively navigate these challenges, organizations should focus on several critical steps in their disaster recovery planning:
Ultimately, the significance of a well-structured HIPAA disaster recovery plan transcends mere compliance; it is fundamental for fostering trust with patients and stakeholders alike. As the cybersecurity landscape continues to evolve, healthcare organizations must take decisive action to implement these best practices. By doing so, they not only protect sensitive information but also enhance operational continuity, leading to improved patient care and organizational stability. Taking proactive measures today is essential for preparing for any crisis that may arise.
What is a HIPAA disaster recovery plan (DRP)?
A HIPAA disaster recovery plan is a crucial strategy that outlines how a healthcare organization will respond to emergencies threatening the integrity of electronic protected health information (ePHI), focusing on minimizing downtime and ensuring the confidentiality, integrity, and availability of ePHI.
What are the objectives of a HIPAA disaster recovery plan?
The objectives of a DRP include minimizing downtime and ensuring the confidentiality, integrity, and availability of ePHI, along with integrating strong cybersecurity measures like encryption and multi-factor authentication to protect against data breaches.
What should be included in the scope of a HIPAA disaster recovery plan?
The scope of the plan should define the systems, processes, and data it encompasses, ensuring all critical components related to HIPAA compliance and cybersecurity safeguards are included.
What compliance requirements must a HIPAA disaster recovery plan address?
The plan must highlight specific HIPAA regulations and ensure that all actions taken during an emergency comply with federal laws, including necessary technical safeguards like encryption and access controls.
What are the key components of a comprehensive HIPAA disaster recovery plan?
Key components include data backup procedures, emergency operations protocols, communication strategies, proactive risk management strategies, continuous monitoring, and audit support to maintain compliance and readiness for potential audits.
Why is establishing roles and responsibilities important in HIPAA disaster recovery?
Clear roles and responsibilities are vital for effective team organization, ensuring swift recovery during emergencies and improving response abilities within healthcare organizations.
Who are the key personnel typically involved in a HIPAA disaster recovery process?
Key personnel include the Disaster Recovery Coordinator, IT Support Staff, and Compliance Officer, each with specific responsibilities in managing the recovery process and ensuring adherence to HIPAA regulations.
What steps should be taken to prepare the disaster recovery team?
Steps include identifying key personnel, assigning specific roles, creating a current contact list of team members for prompt communication, and documenting responsibilities in the DRP to promote clarity and accountability.