
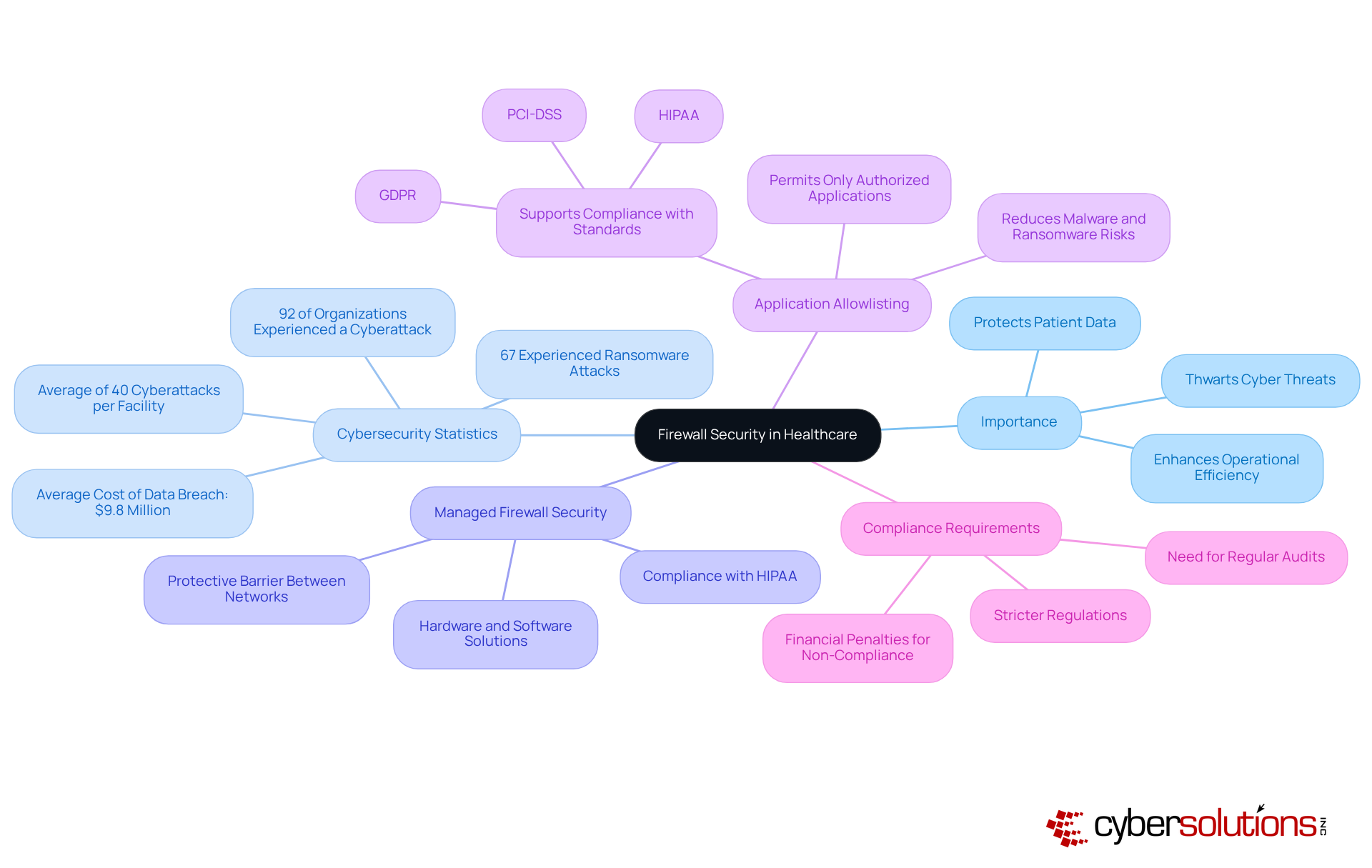
In the ever-evolving landscape of healthcare, the significance of managed firewall security cannot be overstated. As cyber threats continue to escalate, healthcare organizations face unique challenges in safeguarding sensitive patient data and ensuring compliance with stringent regulations. The increasing frequency of cyberattacks in this sector highlights the urgent need for robust security measures. Financial implications of data breaches are staggering, with potential losses that can cripple even the most resilient organizations. Therefore, it is imperative for CFOs to implement effective firewall security measures that bolster organizational resilience against these threats.
To navigate this complex environment, healthcare leaders must first understand the current cybersecurity threats they face. With cybercriminals targeting healthcare data more than ever, the stakes are high. The consequences of a breach extend beyond financial losses; they can damage reputations and erode patient trust. Cyber Solutions offers a comprehensive approach to addressing these challenges, providing tailored strategies that empower organizations to protect their most valuable asset: patient information.
CFOs play a crucial role in this endeavor. By following a step-by-step guide to implementing firewall security, they can enhance their organization's defenses against cyber threats. This proactive stance not only mitigates risks but also ensures compliance with regulatory requirements. The time to act is now—healthcare organizations must prioritize cybersecurity to safeguard their future.
In today's healthcare landscape, where organizations are increasingly targeted by cyber threats, the significance of robust managed firewall security stands paramount. With staggering statistics revealing that medical facilities encounter an average of 40 cyberattacks annually, CFOs must acknowledge the critical role these security measures play in safeguarding sensitive patient data and ensuring compliance with regulations. Yet, the challenge lies in navigating the complexities of various firewall types and effectively implementing a comprehensive security strategy.
How can CFOs lead their organizations in fortifying defenses while optimizing cybersecurity budgets? This pressing question demands attention as the stakes continue to rise.
In today's digital age, cybersecurity in healthcare is not just important—it's imperative. With delicate patient data being routinely stored and exchanged, the role of , which encompasses both hardware and software solutions, cannot be overstated. This managed firewall security acts as a protective barrier between trusted internal networks and untrusted external environments, effectively thwarting unauthorized access and cyber threats, while ensuring compliance with stringent regulations like HIPAA.
Recent statistics underscore the urgency for robust managed firewall security solutions: in 2024, medical facilities faced an alarming average of 40 cyberattacks each, with 92% reporting at least one incident. The financial ramifications are staggering, as the average cost of a medical data breach reached $9.8 million, highlighting the consequences of inadequate security measures. Furthermore, 67% of healthcare entities experienced ransomware attacks, further emphasizing the necessity for managed firewall security to ensure proactive defenses.
Beyond firewall management, application allowlisting emerges as a vital aspect of a comprehensive cybersecurity strategy. By permitting only authorized applications to operate, organizations can significantly reduce the risk of malware, ransomware, and unauthorized software execution. This proactive approach not only mitigates vulnerabilities but also aids medical entities in meeting compliance requirements for standards such as HIPAA, PCI-DSS, and GDPR.
Implementing effective managed firewall security and application allowlisting is essential for safeguarding sensitive patient data while enhancing operational efficiency. This makes it a crucial investment for CFOs aiming to optimize cybersecurity budgets. By prioritizing these protective measures, medical institutions can safeguard their resources, maintain patient trust, and minimize the risk of costly fines associated with data breaches. Real-world examples illustrate this point: entities that have successfully adopted advanced protection solutions and application allowlisting report notable reductions in breach incidents and improved compliance with regulatory standards, underscoring the critical importance of these measures in today's digital landscape.
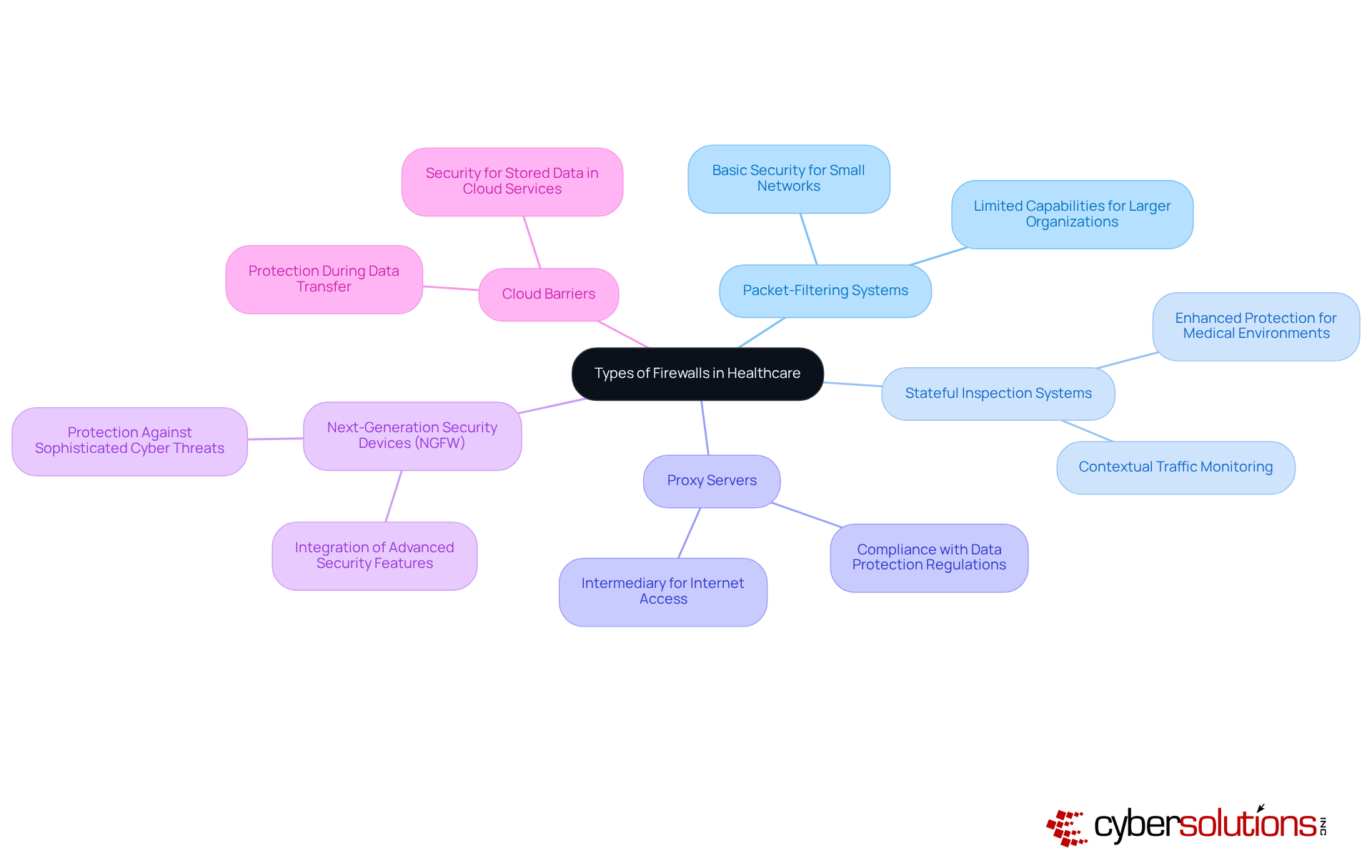
In the rapidly evolving landscape of cybersecurity, managed firewall security is indispensable for safeguarding medical organizations from cyber threats. Understanding the various is essential for effective managed firewall security in this sector. Here’s an overview of the primary firewall types and their applications in healthcare:
Looking ahead to 2025, the market share of these protective technologies in healthcare is expected to reflect a growing preference for NGFWs and cloud defenses, driven by the necessity for advanced protection strategies against evolving cyber threats. By comprehending these types of barriers and their specific applications, CFOs can make informed decisions that align with their organization's security requirements and budget constraints.
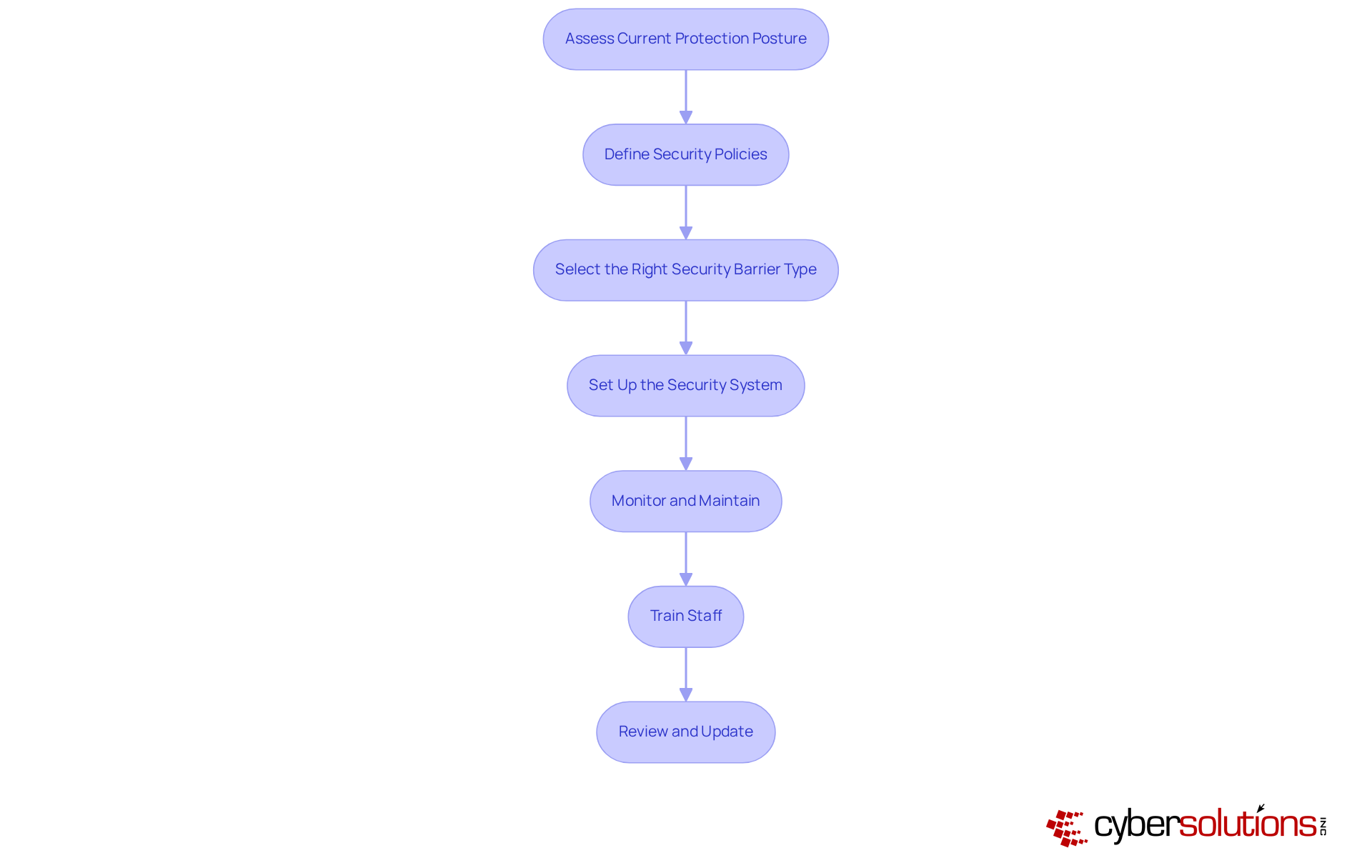
Implementing managed firewall security is essential in today’s healthcare landscape, where cybersecurity threats are increasingly sophisticated. CFOs must lead the charge in safeguarding sensitive data while ensuring compliance with industry regulations. Here are several key steps to effectively implement firewall security:
By diligently following these steps, CFOs can effectively lead their organizations in implementing managed firewall security that not only protects sensitive data but also ensures compliance with industry regulations.
In the realm of healthcare, the significance of managed firewall security cannot be overstated. As cyber threats grow increasingly sophisticated, CFOs must prioritize the implementation of robust firewall solutions to protect sensitive patient data and ensure compliance with industry regulations. This tutorial underscores the critical role that managed firewall security plays in safeguarding healthcare organizations against potential breaches and the financial repercussions that follow.
Key insights discussed include:
From assessing current security postures to training staff and regularly updating policies, each step is crucial for establishing a comprehensive cybersecurity strategy. Moreover, the importance of application allowlisting and the selection of appropriate firewall types are highlighted as pivotal components in enhancing overall security.
Ultimately, investing in managed firewall security is not merely a technical necessity but a strategic imperative for healthcare CFOs. By proactively addressing cybersecurity challenges and fostering a culture of compliance, organizations can protect their valuable resources, maintain patient trust, and mitigate the risks associated with data breaches. Taking action now ensures that healthcare institutions are well-equipped to navigate the evolving landscape of cybersecurity threats, safeguarding both their operations and the sensitive data they manage.
What is firewall security in healthcare?
Firewall security in healthcare refers to managed security solutions that include both hardware and software to protect sensitive patient data by creating a barrier between trusted internal networks and untrusted external environments, preventing unauthorized access and cyber threats.
Why is firewall security important in the healthcare sector?
Firewall security is crucial in healthcare to safeguard delicate patient data, ensure compliance with regulations like HIPAA, and protect against the increasing number of cyberattacks targeting medical facilities.
What statistics highlight the need for robust firewall security in healthcare?
In 2024, medical facilities experienced an average of 40 cyberattacks each, with 92% reporting at least one incident. The average cost of a medical data breach reached $9.8 million, and 67% of healthcare entities faced ransomware attacks.
What is application allowlisting, and why is it important?
Application allowlisting is a cybersecurity strategy that permits only authorized applications to run within an organization. It is important because it reduces the risk of malware, ransomware, and unauthorized software execution, helping organizations meet compliance requirements.
How do managed firewall security and application allowlisting contribute to compliance?
These measures help healthcare organizations meet compliance standards such as HIPAA, PCI-DSS, and GDPR by proactively protecting sensitive data and minimizing vulnerabilities.
What are the financial implications of inadequate cybersecurity measures in healthcare?
Inadequate cybersecurity can lead to significant financial ramifications, with the average cost of a medical data breach reaching $9.8 million, alongside potential fines for non-compliance with regulations.
How can healthcare institutions benefit from implementing firewall security and application allowlisting?
By implementing these protective measures, healthcare institutions can safeguard patient data, enhance operational efficiency, maintain patient trust, and reduce the risk of costly fines associated with data breaches.
Are there real-world examples of the effectiveness of these cybersecurity measures?
Yes, entities that have adopted advanced protection solutions and application allowlisting report notable reductions in breach incidents and improved compliance with regulatory standards, demonstrating the critical importance of these measures.