
This article serves as a vital guide for CFOs in healthcare, focusing on the mastery of IT requests and underscoring the essential role of IT in boosting operational efficiency and ensuring regulatory compliance. It is critical to:
By emphasizing these elements, the article illustrates how structured IT requests can significantly enhance patient care and yield financial returns for healthcare organizations.
In the intricate realm of healthcare, the importance of IT requests is paramount; they play a crucial role in ensuring patient safety, protecting sensitive data, and enhancing operational efficiency. This article serves as a comprehensive guide for CFOs, empowering them to navigate the complexities of IT requests and equipping them with the essential tools to advocate for critical technology investments that align seamlessly with organizational objectives. As the demand for IT continues to escalate, the pressing question arises: how can CFOs adeptly prioritize and manage these requests to guarantee the success of their healthcare organizations?
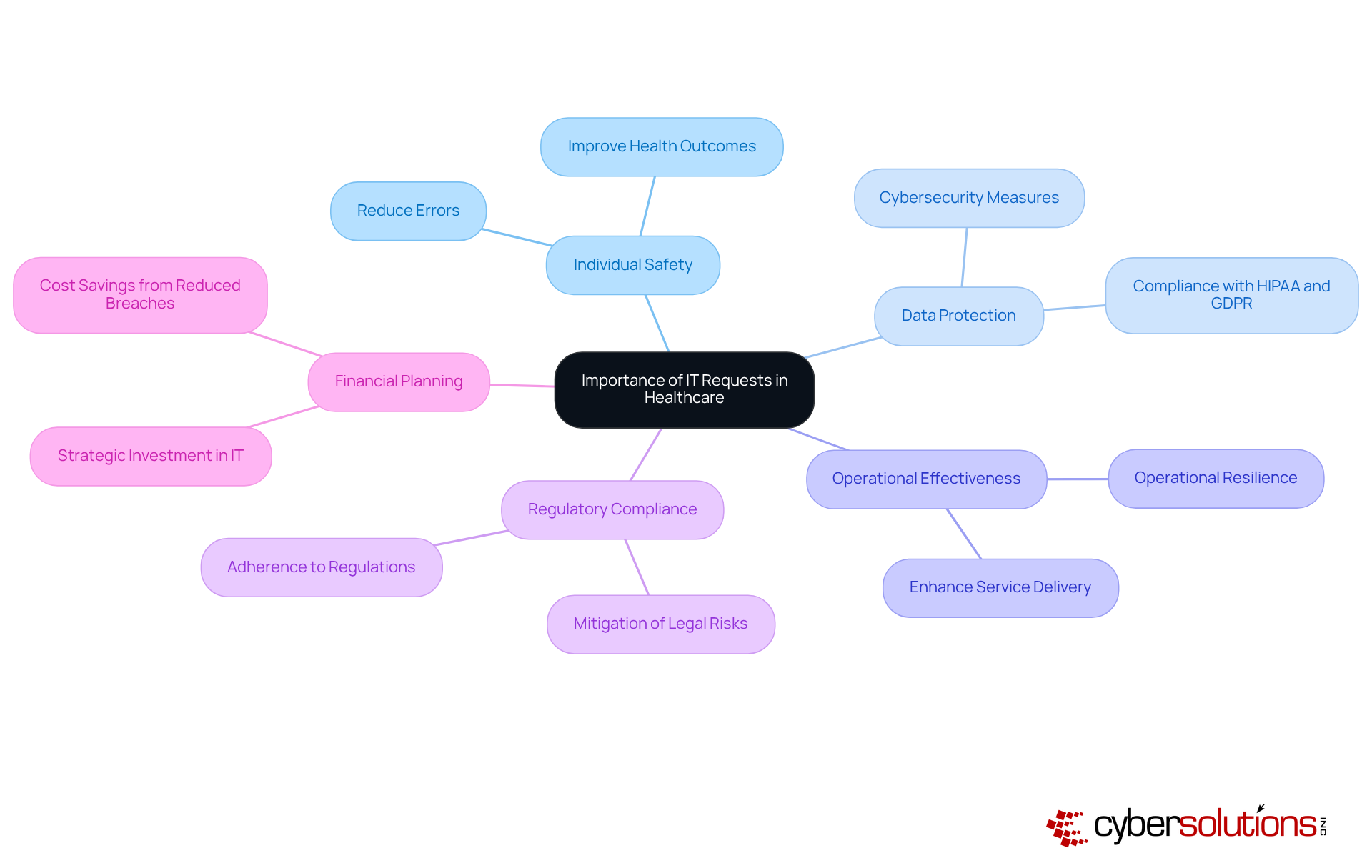
In the healthcare field, the demands for IT extend far beyond mere administrative duties; they are vital components that significantly impact individual safety, data protection, and operational effectiveness. Recognizing the importance of these demands empowers CFOs to prioritize IT initiatives that not only enhance service delivery but also with stringent regulations such as HIPAA and GDPR.
Effective IT management has been shown to reduce errors, improve health outcomes, and generate savings, making it imperative for CFOs to advocate for the necessary resources and support within their organizations. Furthermore, aligning IT requests with strategic financial planning is crucial, as it ensures that investments in technology yield measurable returns, ultimately benefiting both the organization and its clients.
For example, hospitals that have adopted robust cybersecurity measures have experienced a notable reduction in data breaches, which can incur an average cost of $408 per stolen health record—nearly three times the expense seen in other sectors. By fostering a culture of cybersecurity awareness and investing in advanced IT solutions, healthcare organizations can significantly bolster their operational resilience and safeguard trust.
To create an , it is crucial to begin by precisely defining the problem or need. Clearly articulate the nature of the issue, its urgency, and request any pertinent background information. For instance, when pursuing an enhancement to a management system for clients, explain how the current system affects care or operational efficiency. Furthermore, outline the anticipated outcomes of the proposal, such as enhanced data security or improved patient experiences.
Including a cost estimate and potential return on investment (ROI) will further strengthen your appeal, demonstrating to IT teams and stakeholders how the investment aligns with the entity's financial goals.
Leverage templates or examples from previous successful submissions to ensure your entry is clear and comprehensive. This structured approach not only facilitates better communication but also increases the likelihood of approval by showcasing a thorough understanding of the organization's needs and priorities.

Once an IT request has been submitted, it is crucial to follow up regularly to monitor its progress. Establish a follow-up schedule, whether weekly or bi-weekly, depending on the urgency of the inquiry. During these follow-ups, ask about the status of the appeal, any challenges encountered, and the anticipated timeline for resolution. Maintaining open lines of communication with IT staff not only fosters collaboration but also ensures that any issues are promptly addressed.
Furthermore, documenting all interactions and updates can provide valuable insights for future inquiries and assist in evaluating the effectiveness of the IT support process. Should delays arise, it is essential to or modifications to the request are necessary to facilitate a quicker resolution.

Recognizing the pivotal role of IT requests in healthcare is essential for CFOs aiming to enhance operational effectiveness and patient safety. By understanding and prioritizing these requests, CFOs can align technology investments with strategic financial goals, ensuring compliance with regulations and improving overall service delivery.
Throughout this guide, the importance of crafting clear and detailed IT requests has been emphasized. This includes the need for precise problem definitions, anticipated outcomes, and potential ROI. Furthermore, the significance of regular follow-ups and effective communication with IT teams cannot be overstated. These practices foster collaboration and facilitate timely resolutions.
Ultimately, managing IT requests in healthcare transcends mere procedural tasks; it is a strategic initiative that can significantly impact the quality of care provided. By adopting best practices in IT request management, healthcare organizations can safeguard patient trust, improve operational resilience, and drive meaningful advancements in service delivery. It is imperative for CFOs to take proactive steps in this area, ensuring that technology becomes a cornerstone of healthcare excellence.
Why are IT requests important in the healthcare field?
IT requests are crucial in healthcare because they significantly impact individual safety, data protection, and operational effectiveness, beyond just administrative duties.
How do effective IT management practices benefit healthcare organizations?
Effective IT management reduces errors, improves health outcomes, and generates savings, making it essential for CFOs to secure necessary resources and support.
What role do CFOs play in IT initiatives within healthcare organizations?
CFOs are responsible for prioritizing IT initiatives that enhance service delivery and ensure compliance with regulations such as HIPAA and GDPR.
Why is it important to align IT requests with strategic financial planning?
Aligning IT requests with strategic financial planning ensures that technology investments yield measurable returns, benefiting both the organization and its clients.
How do cybersecurity measures impact data breaches in hospitals?
Hospitals that adopt robust cybersecurity measures experience a notable reduction in data breaches, which can cost an average of $408 per stolen health record.
What is the cost difference of data breaches in healthcare compared to other sectors?
The cost of data breaches in healthcare is nearly three times higher than in other sectors, highlighting the importance of investing in cybersecurity.
How can healthcare organizations enhance their operational resilience?
By fostering a culture of cybersecurity awareness and investing in advanced IT solutions, healthcare organizations can significantly enhance their operational resilience and safeguard trust.