
In today's digital landscape, cybersecurity has emerged as a paramount concern for healthcare organizations. With the increasing frequency and sophistication of cyber threats, healthcare CFOs must adopt essential strategies to safeguard their institutions. Comprehensive measures such as:
are not merely optional; they are critical to protecting sensitive patient data and managing operational costs effectively. As cyberattacks continue to rise within the healthcare sector, the implications for organizations are profound. Failure to address these vulnerabilities can lead to devastating consequences, both financially and reputationally. Therefore, it is imperative for CFOs to take decisive action.
The current landscape of cybersecurity threats presents unique challenges for healthcare CFOs. As they navigate the complexities of financial management, they must also prioritize the protection of their organizations against cyber threats. This dual responsibility can be daunting, but it is essential for maintaining trust and ensuring the continuity of care. By implementing robust cybersecurity strategies, CFOs not only enhance their organizations' defenses but also contribute to a culture of security awareness among staff.
To address these challenges effectively, healthcare organizations must adopt a proactive approach to cybersecurity. This includes:
By embracing these strategies, CFOs can mitigate risks and foster resilience in the face of evolving cyber threats. Ultimately, the commitment to cybersecurity is not just about protecting data; it is about safeguarding the future of healthcare itself.
In a world where cyber threats loom larger than ever, healthcare CFOs find themselves at a critical juncture, grappling with the dual imperatives of safeguarding sensitive patient data and managing tight budgets. With a staggering 88% of medical institutions experiencing cyberattacks in the past year alone, the stakes have never been higher.
This article delves into essential cybersecurity strategies tailored specifically for small and medium-sized healthcare businesses, offering CFOs a roadmap to not only protect their organizations but also enhance operational efficiency.
How can these leaders effectively navigate the complex landscape of cybersecurity while ensuring compliance and maintaining patient trust? The urgency of addressing these challenges cannot be overstated.
Cyber Solutions Inc. delivers a comprehensive suite of cybersecurity services meticulously designed for small and medium-sized businesses (SMBs) operating within the medical sector. Among our key offerings are:
These services are vital for safeguarding sensitive patient data and ensuring compliance with rigorous regulations such as HIPAA, PCI-DSS, and GDPR. With 88% of medical institutions reporting at least one cyber assault in the past year and cyberattacks affecting over 100 million individuals in 2023, the urgency for has never been more pronounced.
Healthcare CFOs face the dual challenge of shielding their organizations from escalating cyber threats while managing operational costs. The average cost of a medical data breach reached $9.8 million in 2024, despite a 10.6% decrease from the previous year, underscoring the financial ramifications of inadequate cybersecurity. By adopting managed IT and cybersecurity services, including proactive incident response strategies, medical facilities can significantly bolster their security posture while realizing considerable cost savings. For example, Cyber Solutions' clients employing AI and automation tools have successfully detected and contained incidents 98 days faster than average, resulting in lower recovery expenses.
Moreover, as the risk landscape continues to shift, it is imperative for CFOs to remain informed about emerging trends. The proliferation of ransomware attacks, which have targeted 74% of hospitals in recent years, underscores the pressing need for proactive measures. Industry experts assert that investing in cybersecurity transcends mere choice; it is an ethical obligation to protect patient information and uphold trust. By leveraging tailored cybersecurity strategies, including effective CaaS and robust incident response, CFOs in the medical sector can adeptly navigate these challenges, ensuring their organizations remain resilient against rising cyber threats. Additionally, our flat-rate pricing model simplifies budgeting, enabling organizations to manage their cybersecurity expenses without unexpected costs.
In today's healthcare landscape, smb cybersecurity is not just an option; it is a necessity. Endpoint protection solutions are crucial for securing devices within your network, particularly in the medical field where sensitive data is perpetually at risk. These solutions not only detect but also respond to threats in real-time, significantly mitigating the risk of cyberattacks. For instance, implementing robust antivirus software and advanced intrusion detection systems can drastically lower vulnerability levels.
Consider this: half of medical institutions lack a formal cyber incident response strategy. This alarming statistic underscores the importance of emphasizing endpoint protection, especially for CFOs who are tasked with safeguarding their operations. Recent trends indicate that assailants are increasingly targeting medical devices, with 79% of medical entities reporting ransomware attacks in the past year.
By adopting comprehensive endpoint protection strategies, healthcare entities can enhance their security posture and ensure compliance with regulatory standards. This proactive approach not only but also maintains operational integrity. Furthermore, as the landscape of cyber risks evolves, it is crucial for small to medium-sized enterprises in the medical field to remain informed about the latest smb cybersecurity endpoint protection solutions. By doing so, they can effectively address these challenges and secure their vital assets.
Effective threat detection is paramount for healthcare entities, underscoring the necessity for advanced technologies to monitor network activity and identify potential threats. The implementation of Information and Event Management (SIEM) systems provides real-time insights into protective measures, enabling organizations to respond swiftly to incidents. This proactive strategy not only mitigates potential damage but also ensures adherence to stringent , including HIPAA.
Organizations utilizing SIEM systems have reported a significant reduction in incident response times, achieving resolutions of threat events up to 40% faster. Expert opinions affirm that SIEM systems enhance threat detection capabilities, allowing service providers to stay ahead of evolving cyber threats. Successful applications across various medical environments have demonstrated improved detection rates and a marked decrease in the impact of breaches, highlighting the critical role of these systems in safeguarding sensitive patient information.
As cyberattacks continue to escalate, with medical institutions facing an average of 2.91 phishing attempts per user in 2024, the integration of SIEM systems becomes increasingly vital for maintaining robust SMB cybersecurity protections. Moreover, entities should consider tailored remediation strategies and professional guidance, including virtual CISO services, to strengthen their compliance and security frameworks.

A successful incident response strategy is paramount for medical entities aiming to manage cyber incidents effectively. This plan must clearly delineate the necessary steps, including:
Given that medical data breaches average over $9.77 million per incident, a structured response can significantly mitigate financial losses and operational disruptions. Consider this: entities that conduct incident response testing at least twice annually can reduce breach expenses by an average of $1.49 million.
Furthermore, the typical recovery duration from cyber incidents in medical facilities is alarmingly prolonged, with entities taking an average of 258 days to identify and manage a breach. However, those equipped with a well-defined incident response plan can act swiftly, minimizing downtime and ensuring that patient care remains uninterrupted during crises.
Real-world examples demonstrate that medical entities employing can decrease response times by 30% and avert secondary breaches resulting from mismanaged efforts. By prioritizing incident response planning and leveraging expert advice, CFOs in the medical sector can safeguard their institutions against the escalating risk landscape while maintaining trust with patients.
Additionally, integrating user manuals for achieving and sustaining HIPAA compliance into the incident response strategy is crucial for ensuring that all regulatory obligations are met, thereby enhancing the entity's resilience against cyber risks.
Regular vulnerability evaluations are paramount for medical institutions, serving as a proactive measure to detect and address security flaws before they can be exploited. Alarmingly, statistics reveal that only a fraction of healthcare small and medium-sized businesses (SMBs) consistently perform these evaluations, leaving them vulnerable to SMB cybersecurity risks. Effective assessments must integrate automated scans with manual testing to guarantee comprehensive coverage of potential vulnerabilities. Notably, entities such as Ascension Health have faced significant breaches due to neglected vulnerabilities, underscoring the severe consequences of overlooking this essential practice.
Expert opinions reinforce the necessity of conducting vulnerability assessments as a cornerstone of a robust cybersecurity strategy. Cybersecurity architect Mohammed Khalil asserts that mastering these assessments is vital for establishing a resilient defense against evolving threats. By promptly addressing vulnerabilities, healthcare entities can dramatically reduce their risk of data breaches, which, in 2025, averaged $7.42 million per incident, while also ensuring compliance with stringent industry regulations like HIPAA.
To conduct effective vulnerability assessments, organizations should follow a structured approach that includes:
By implementing these strategies, medical entities can not only safeguard sensitive patient information but also enhance their overall security posture, ensuring compliance and resilience in an increasingly regulated environment.

In today's healthcare landscape, navigating the complexities of regulatory requirements is more critical than ever. Compliance as a Service (CaaS) equips healthcare entities with the essential tools and expertise needed to adeptly manage these challenges. By outsourcing compliance management, organizations can effectively meet vital standards such as HIPAA and PCI-DSS, alleviating the necessity for an in-house compliance team. This strategic approach not only reduces operational expenses but also significantly enhances safety and efficiency.
Consider this: healthcare providers can conduct comprehensive risk assessments in less than 30 days, ensuring they remain compliant with evolving regulations. With set to take effect in 2025—introducing improved patient access rights and stricter data protection measures—the utilization of CaaS becomes increasingly paramount. Organizations that have successfully navigated HIPAA compliance through outsourcing have reported enhanced security postures and diminished risks associated with data breaches.
Expert insights reveal a compelling perspective: viewing compliance as a proactive investment, rather than a mere expense, can lead to substantial long-term savings. This is particularly relevant when considering the high costs associated with potential breaches. By adopting CaaS, medical entities can focus on delivering quality care while confidently managing their compliance responsibilities.
In today's digital landscape, implementing robust backup and disaster recovery solutions is not just advisable but essential for medical institutions. Protecting data from loss due to cyberattacks or system failures is paramount. Regularly scheduled backups, paired with a comprehensive disaster recovery plan, facilitate the rapid restoration of critical data, significantly reducing downtime and mitigating financial repercussions.
Alarmingly, medical institutions without disaster recovery strategies experience an average downtime of over eight hours during incidents, leading to substantial operational disruptions and compliance risks. The Change Healthcare cyberattack, which compromised sensitive information from up to 190 million individuals, underscores the urgent need for effective disaster recovery strategies.
Therefore, healthcare CFOs must prioritize these solutions as . By doing so, they can ensure business continuity and safeguard patient trust in an increasingly volatile digital environment.
Firewalls are not just a component but a cornerstone of cybersecurity for medical networks, safeguarding against unauthorized access and cyber threats. By deploying both hardware and software firewalls, businesses can establish a multi-layered security framework that effectively blocks malicious traffic. This approach is particularly vital in the medical field, where sensitive patient data is at risk. Did you know that 92% of healthcare organizations reported being targeted by cyberattacks in the past year? This statistic underscores the necessity of robust defenses.
To maintain optimal protection against evolving threats, it is essential to and configurations. This proactive step not only improves safety but also guarantees adherence to regulations like HIPAA, which mandates the protection of Protected Health Information (PHI). Successful instances abound, with medical entities utilizing firewalls to prevent unauthorized access and mitigate risks linked to data breaches. In fact, entities utilizing managed firewall services have reported significant enhancements in their security posture, allowing them to concentrate on patient care rather than cybersecurity issues.
Moreover, firewalls play a crucial role in ensuring SMB cybersecurity for medical SMBs, which often face unique challenges due to limited resources. By implementing effective firewall strategies, these entities can significantly reduce their vulnerability to cyber threats, ensuring the confidentiality and integrity of patient data. As the medical industry continues to invest heavily in cybersecurity—projected to reach $5.61 billion by 2025—the significance of firewalls in establishing a secure environment cannot be overstated.
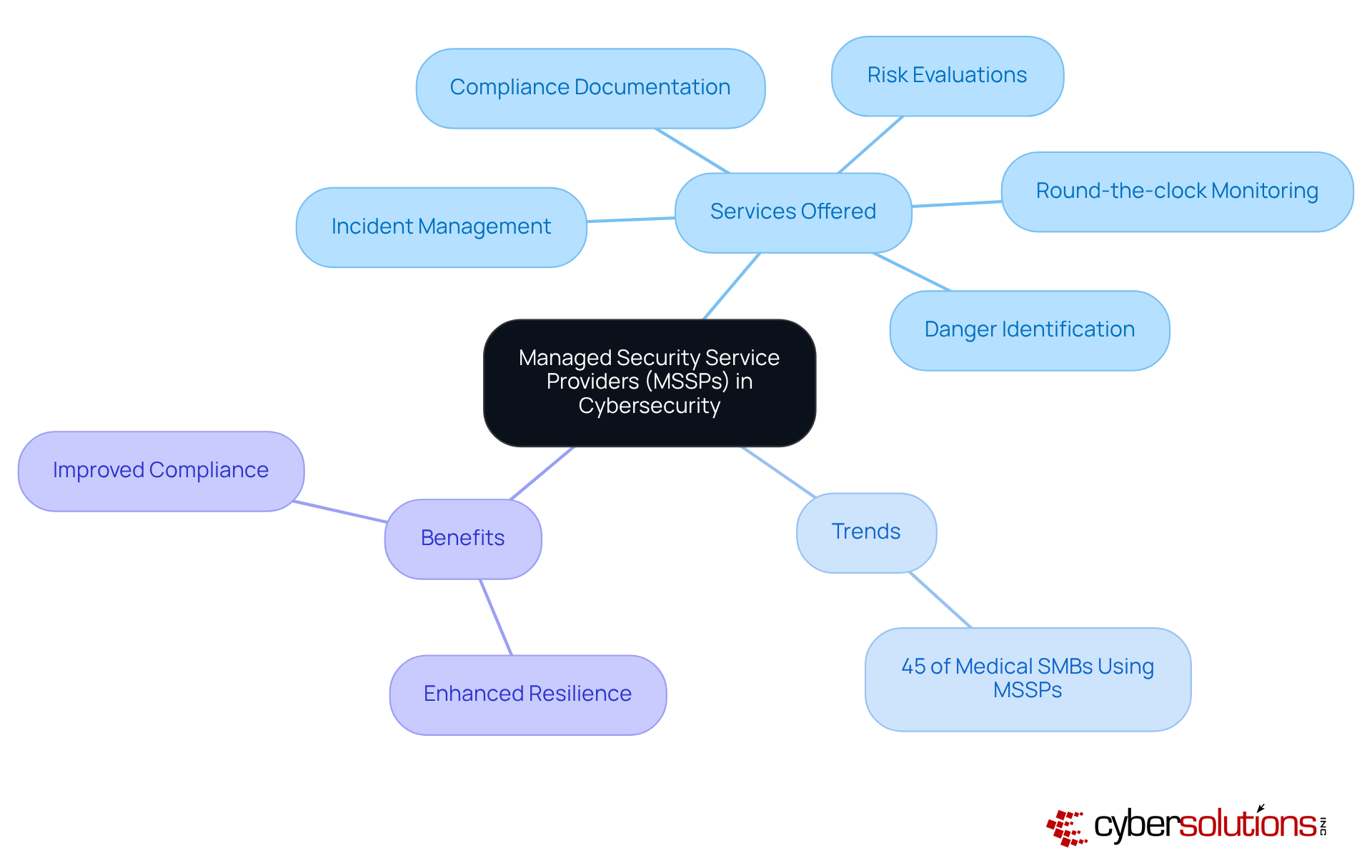
In today's digital landscape, the importance of cybersecurity in healthcare cannot be overstated. Partnering with a Managed Security Service Provider (MSSP) equips healthcare organizations with essential ongoing cybersecurity support and expertise. MSSPs offer a comprehensive range of services, including:
These are critical components for sustaining robust protective measures. This collaboration proves particularly advantageous for small and medium-sized businesses (SMBs) that often struggle with SMB cybersecurity due to limited resources for an in-house security team.
Recent trends indicate that approximately 45% of medical SMBs are now leveraging MSSPs to bolster their SMB cybersecurity posture, recognizing the necessity for specialized assistance in an increasingly complex risk environment. By utilizing MSSPs, medical organizations can ensure that their cybersecurity needs are addressed effectively and efficiently, allowing them to focus on their core operations. Expert opinions emphasize that continuous support from MSSPs not only enhances protection but also fosters a culture of resilience against evolving cyber threats.
A significant example of this is a recent case where Cyber Solutions assisted a medical provider in recovering from a ransomware attack. By implementing improved security measures, they successfully protected patient data and operations. This strategic choice is especially beneficial for healthcare CFOs who are tasked with and maintaining compliance in a challenging regulatory landscape.
In the realm of healthcare, the imperative for robust cybersecurity measures cannot be overstated, particularly for small and medium-sized businesses (SMBs). As healthcare CFOs grapple with the dual challenge of protecting sensitive patient data while managing operational costs, implementing comprehensive cybersecurity strategies emerges as a critical necessity. The escalating frequency and sophistication of cyberattacks highlight the ethical obligation of healthcare organizations to prioritize cybersecurity, ensuring patient trust and regulatory compliance.
This article has outlined essential strategies for enhancing cybersecurity within healthcare SMBs, including:
Each of these components plays a crucial role in building a resilient cybersecurity framework capable of withstanding the ever-evolving threat landscape. Moreover, the financial implications of data breaches further emphasize the need for strategic investment in cybersecurity solutions that not only mitigate risks but also promote operational efficiency.
Ultimately, the responsibility lies with healthcare CFOs to cultivate a culture of cybersecurity awareness and resilience within their organizations. By embracing these strategies and leveraging expert resources, healthcare entities can navigate the complexities of cybersecurity, ensuring the protection of patient information and compliance with regulatory standards. The time to act is now; safeguarding sensitive data is not merely a choice but a foundational element of healthcare excellence and patient trust in an increasingly digital world.
What services does Cyber Solutions Inc. offer for small and medium-sized businesses (SMBs) in the medical sector?
Cyber Solutions Inc. offers a comprehensive suite of cybersecurity services, including 24/7 help desk support, endpoint protection, backup and disaster recovery, compliance as a service (CaaS), and incident response solutions.
Why is cybersecurity important for medical institutions?
Cybersecurity is crucial for medical institutions to safeguard sensitive patient data and ensure compliance with regulations such as HIPAA, PCI-DSS, and GDPR. With a high percentage of medical institutions experiencing cyberattacks, robust cybersecurity protocols are essential.
What are the financial implications of inadequate cybersecurity in the medical field?
The average cost of a medical data breach reached $9.8 million in 2024, highlighting the significant financial ramifications of inadequate cybersecurity measures.
How can managed IT and cybersecurity services benefit medical facilities?
By adopting managed IT and cybersecurity services, medical facilities can enhance their security posture, reduce recovery expenses, and achieve faster incident detection and containment.
What is the significance of endpoint protection in healthcare cybersecurity?
Endpoint protection is vital for securing devices within a network, as it detects and responds to threats in real-time, significantly mitigating the risk of cyberattacks in the medical field.
What percentage of medical institutions lack a formal cyber incident response strategy?
Half of medical institutions lack a formal cyber incident response strategy, emphasizing the need for robust endpoint protection.
How do SIEM systems contribute to threat detection in healthcare organizations?
SIEM systems provide real-time insights into network activity, allowing organizations to identify potential threats and respond swiftly, thereby reducing incident response times by up to 40%.
What is the average number of phishing attempts faced by medical institutions in 2024?
Medical institutions face an average of 2.91 phishing attempts per user in 2024, highlighting the increasing need for effective cybersecurity measures.
How can CFOs in the medical sector navigate cybersecurity challenges?
CFOs can navigate cybersecurity challenges by leveraging tailored cybersecurity strategies, including effective CaaS and robust incident response, to protect patient information and maintain organizational resilience.
What pricing model does Cyber Solutions Inc. offer for its services?
Cyber Solutions Inc. offers a flat-rate pricing model, which simplifies budgeting and helps organizations manage their cybersecurity expenses without unexpected costs.