In today’s rapidly evolving digital landscape, mastering cybersecurity KPIs is not just important; it’s essential for aligning with business goals, especially in the healthcare sector. These metrics are crucial for measuring the effectiveness of cybersecurity strategies within organizations. Clearly defined KPIs, such as incident response times and threat detection frequencies, not only enhance security posture but also ensure that cybersecurity initiatives contribute to broader business objectives like customer trust and regulatory compliance.
Healthcare organizations face unique challenges in the realm of cybersecurity. With increasing threats and stringent regulations, CFOs must navigate a complex landscape where the stakes are incredibly high. How can they ensure that their cybersecurity measures are not only effective but also aligned with their overall business strategy? This is where the importance of KPIs comes into play.
By focusing on specific metrics, organizations can gain valuable insights into their cybersecurity performance. For instance, tracking incident response times can reveal how quickly a team can react to threats, while monitoring threat detection frequencies can indicate the effectiveness of existing security measures. These insights empower decision-makers to make informed adjustments that bolster their security framework.
Ultimately, the integration of well-defined cybersecurity KPIs into business strategy is not just a best practice; it’s a necessity. As healthcare organizations strive to protect sensitive data and maintain compliance, leveraging these metrics will not only enhance their security posture but also foster greater trust among customers and stakeholders. Are you ready to take your cybersecurity strategy to the next level?
In today's world, where cyber threats are becoming increasingly sophisticated, the urgency for effective cybersecurity strategies in healthcare is undeniable. Organizations must not only protect sensitive data but also ensure their cybersecurity initiatives align with broader business goals. This article explores the pivotal role of cybersecurity KPIs, demonstrating how they can turn security measures into strategic assets that foster trust, compliance, and operational resilience. As the digital landscape continues to evolve, how can organizations keep their cybersecurity metrics relevant and actionable in the face of emerging threats?
The healthcare sector faces unique challenges in this regard. With the rise of telehealth and electronic health records, sensitive patient information is more vulnerable than ever. CFOs and decision-makers must navigate a complex environment where regulatory compliance and financial performance intersect. By implementing robust cybersecurity strategies, organizations can not only mitigate risks but also enhance their overall operational efficiency.
Cybersecurity KPIs serve as essential tools in this endeavor. They provide measurable insights that help organizations assess their security posture and make informed decisions. For instance, tracking incident response times or the number of detected threats can reveal critical areas for improvement. Moreover, these metrics can help build a culture of security awareness within the organization, empowering employees to take an active role in safeguarding sensitive information.
However, the challenge remains: how do organizations ensure these metrics evolve alongside the threats they face? Regularly reviewing and updating cybersecurity KPIs is crucial. This proactive approach allows organizations to adapt to new vulnerabilities and maintain a strong defense against cyber attacks. By prioritizing cybersecurity as a strategic initiative, healthcare organizations can not only protect their assets but also enhance their reputation and trust among patients and stakeholders.
Cybersecurity is not just a technical necessity; it’s a strategic imperative for healthcare organizations. As cyber threats evolve, the need for robust cyber security KPIs has never been more critical. These cyber security KPIs serve as essential measurements that quantify how effectively an organization meets its cybersecurity goals. They encompass various measurable values, including:
Understanding and tracking these metrics is vital. They provide insights into the effectiveness of security measures and highlight areas needing improvement. For instance, a healthcare entity may monitor the duration required to address a data breach, a factor that significantly impacts patient trust and regulatory compliance. By setting clear cyber security KPIs, organizations not only enhance their security posture but also align their security initiatives with broader business objectives, ensuring that investments in protection yield tangible benefits.
In 2025, the focus on digital security metrics has intensified. Organizations are increasingly recognizing their role in evaluating defenses against emerging threats. Effective measurement of security effectiveness enhances overall organizational performance. Specific performance indicators, particularly those related to vulnerability management and incident response times, are crucial for assessing the impact of incident response efforts. For example, the immediate mobilization of a specialized incident response team within 24 hours of a ransomware attack, as demonstrated by Cyber Solutions, allowed for real-time assessments and minimized further spread of the threat.
This swift reaction, combined with ongoing efforts to manage the ransomware and educate personnel on digital security practices, illustrates how efficient incident response can significantly influence these performance indicators. Are you prepared to enhance your organization’s cybersecurity strategy? The time to act is now.
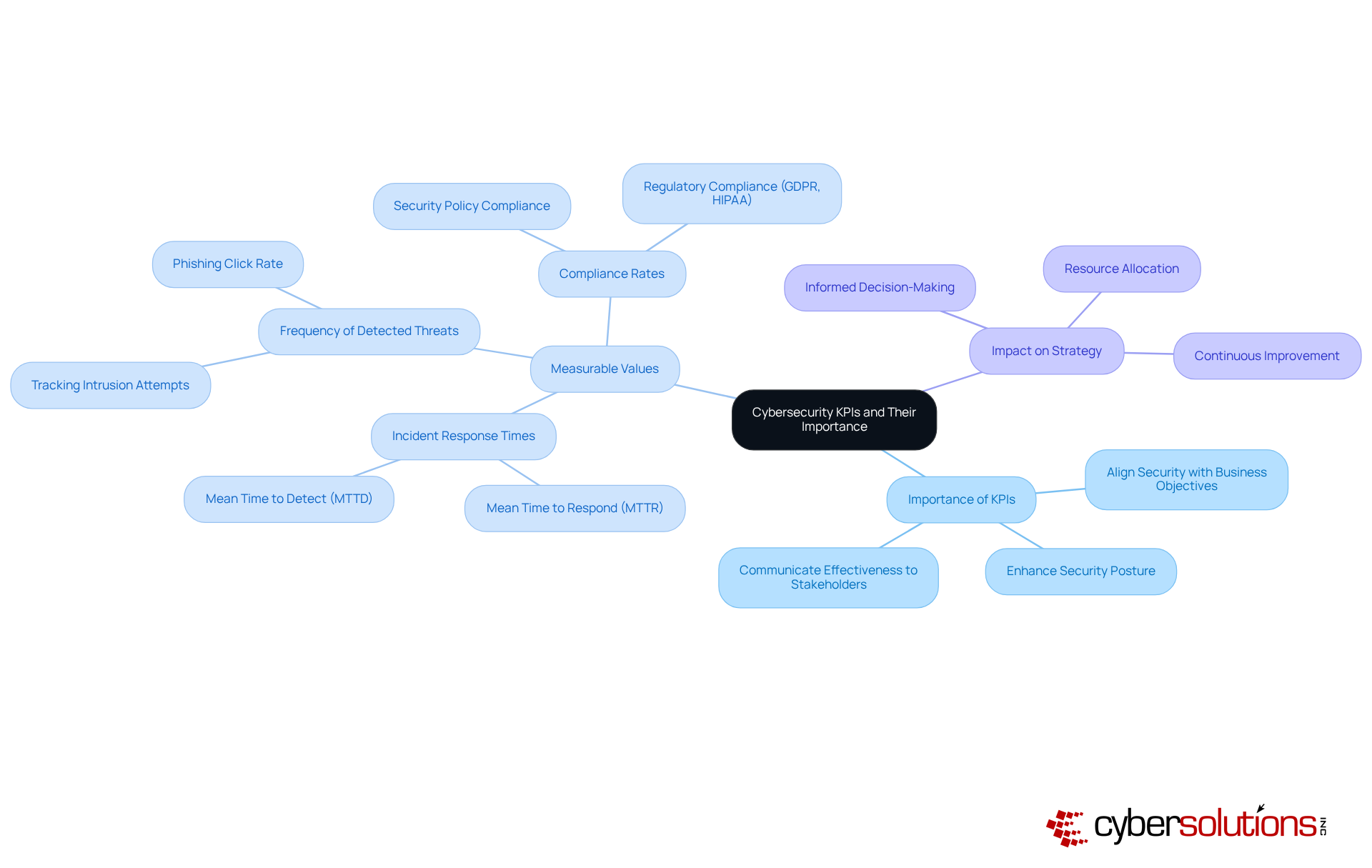
In today’s digital landscape, the importance of aligning business objectives with cyber security KPIs cannot be overstated. Organizations must first pinpoint their key goals—whether it’s enhancing customer trust, ensuring regulatory compliance, or minimizing operational disruptions. Once these goals are clearly defined, relevant cyber security KPIs can be established. For example, if the objective is to bolster customer trust, a critical KPI might be the percentage of successful phishing attempts thwarted.
Regular evaluations of these performance indicators against business goals are essential. This practice not only ensures the relevance and efficiency of security strategies but also validates security budgets. Moreover, it fosters a culture of safety awareness throughout the organization, enabling employees to understand how their actions contribute to broader business objectives. When entities effectively integrate security performance indicators with customer trust initiatives, they often witness increased stakeholder confidence and a strengthened brand reputation. This underscores the strategic importance of security in achieving business success.
Furthermore, the significance of rapid incident response is highlighted by the effectiveness of having an incident response team on-site within 24 hours. This capability can significantly contain threats and facilitate a layered recovery approach, including endpoint isolation and malware removal. Such proactive strategies not only enhance security settings but also emphasize the necessity for continuous employee cyber hygiene training. Ensuring that all staff are prepared to assist in the organization’s defense against cyber threats is crucial.
In conclusion, aligning security performance indicators with business objectives is not just a best practice; it’s a strategic imperative that can lead to enhanced trust, compliance, and operational resilience.
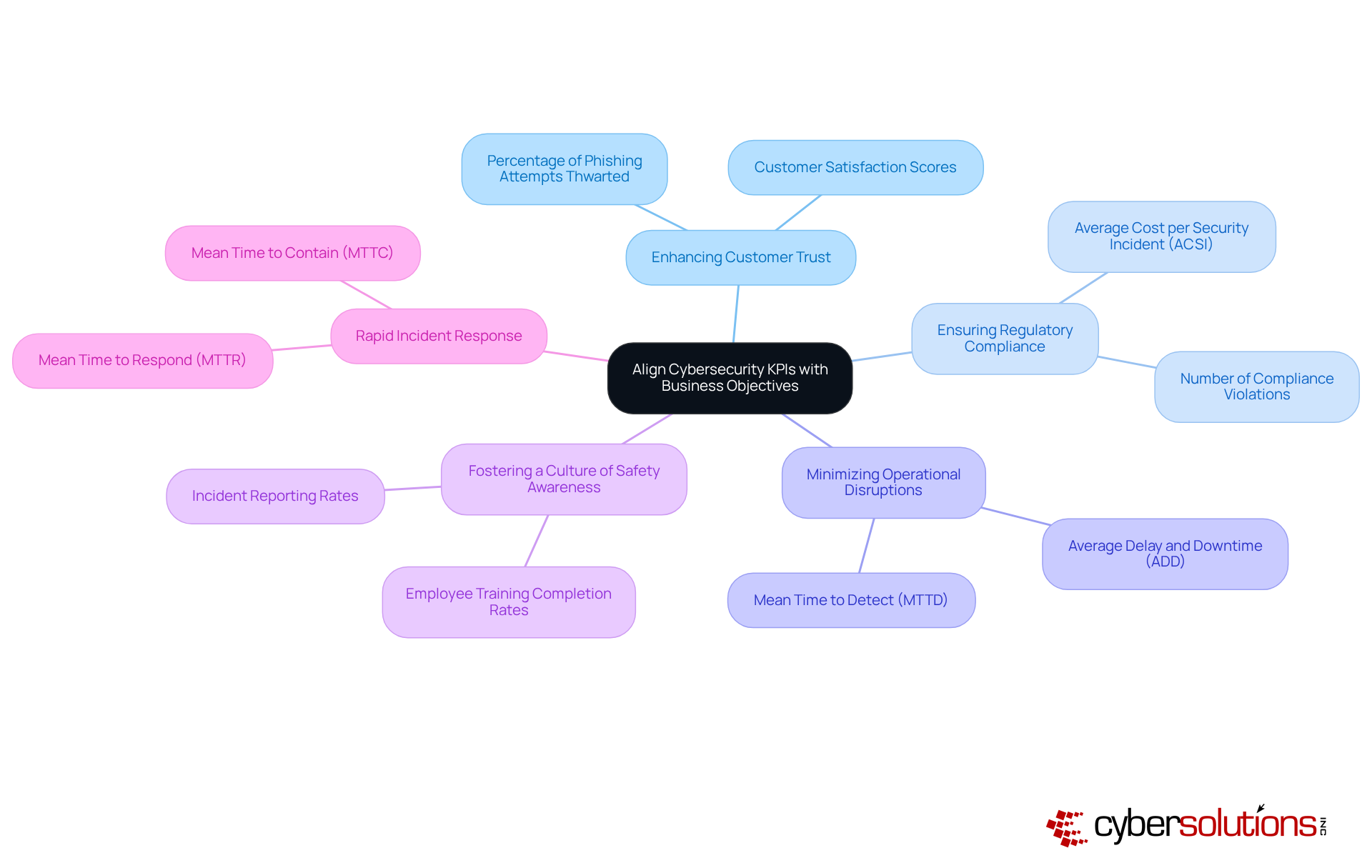
In today's digital landscape, the importance of effective cybersecurity cannot be overstated, especially in healthcare. Organizations face a myriad of threats that can compromise sensitive data and disrupt operations. To navigate these challenges, developing effective cybersecurity KPIs is essential. Entities must prioritize simplicity and actionability; overly complex measures can lead to confusion and hinder decision-making. For instance, rather than relying on intricate formulas to assess risk exposure, firms should track straightforward metrics, such as the number of vulnerabilities fixed within a designated timeframe.
Actionable KPIs must clearly indicate the necessary steps in response to the data. For example, if a KPI reveals an increase in attempted breaches, companies can promptly implement training sessions for employees to enhance their ability to recognize phishing attempts. This approach mirrors the proactive network fortification strategies employed by Cyber Solutions, which included extensive personnel training on security practices, as highlighted in the 'User Awareness Training Completion' case study.
By focusing on clear, actionable cybersecurity KPIs, organizations not only improve their responsiveness to cybersecurity threats but also cultivate a proactive security culture that empowers all employees to contribute to the organization's defense strategy. Moreover, with data indicating that 62% of alerts are overlooked due to excessive noise, the need for transparency in measurements becomes even more critical. Regular reassessment of key metrics is vital to avoid common pitfalls in KPI development, particularly in relation to cybersecurity KPIs, ensuring that organizations remain vigilant and prepared.
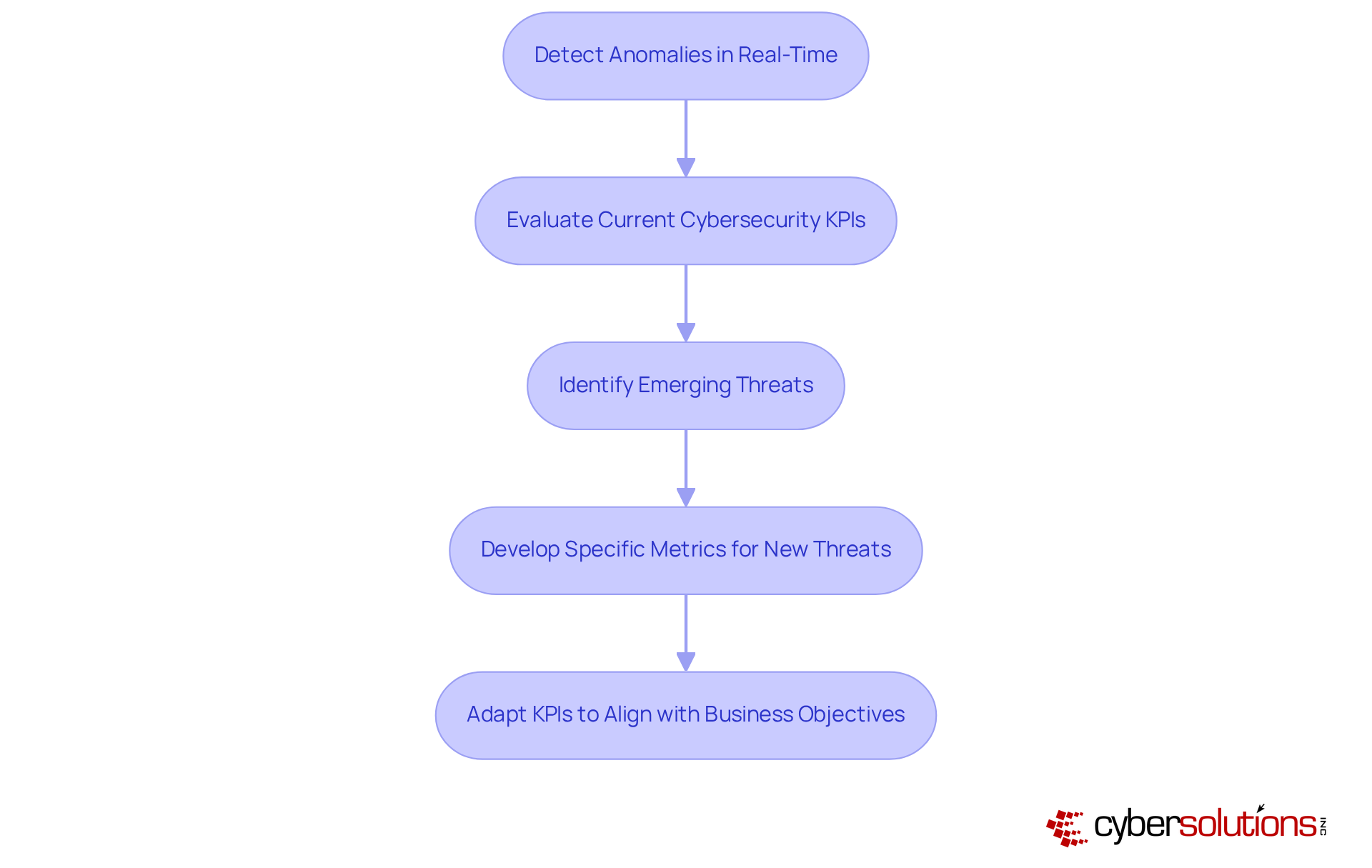
In today’s rapidly evolving cybersecurity landscape, the stakes have never been higher for organizations, especially in the healthcare sector. With Cyber Solutions' 24/7 monitoring services, companies can swiftly detect anomalies and potential vulnerabilities in real-time. This capability allows for immediate action, preventing costly downtime or breaches. Instant alerts and real-time insights significantly enhance responsiveness, ensuring that suspicious activities are addressed without delay.
Regular evaluations of cyber security KPIs are crucial. Organizations must assess the relevance of current metrics and identify emerging threats that may require new cyber security KPIs. For example, if a novel cyber threat emerges, it’s imperative to develop specific metrics to gauge effectiveness in countering that threat. Additionally, as business objectives evolve, so too should the KPIs, specifically the cyber security KPIs, that measure security performance.
This dynamic approach, bolstered by comprehensive network monitoring, cutting-edge threat intelligence, and tailored access controls, empowers organizations to remain agile in the face of cybersecurity challenges. By adapting to both security needs and business goals, companies can cultivate a more robust security posture. Are you ready to fortify your defenses and ensure your organization is prepared for whatever comes next?
In today’s digital age, establishing robust cybersecurity KPIs is not just important; it’s essential for organizations aiming to strengthen their security posture while aligning with broader business goals. These metrics provide a measurable framework for assessing cybersecurity effectiveness, ensuring that security initiatives contribute meaningfully to organizational success. By prioritizing clear and actionable KPIs, organizations can navigate the complex landscape of cyber threats and foster a culture of security awareness among employees.
The significance of aligning cybersecurity KPIs with business objectives cannot be overstated. Organizations must define specific goals, such as bolstering customer trust and ensuring regulatory compliance. Regular evaluations are crucial to maintain the relevance of these metrics. Simplicity in KPI development is key; straightforward and actionable measures empower organizations to respond proactively to emerging threats.
Ultimately, the journey toward effective cybersecurity is ongoing. Continuous monitoring and adaptation of KPIs are necessary as the cybersecurity landscape evolves. Organizations must remain agile, updating their metrics to reflect new threats and changing business objectives. By committing to this dynamic approach, they not only enhance their security measures but also reinforce their commitment to protecting sensitive data and maintaining stakeholder trust. Embracing these best practices will lead to a more resilient and secure future in the face of ever-evolving cyber challenges.
What are cybersecurity KPIs and why are they important?
Cybersecurity KPIs (Key Performance Indicators) are measurable values that quantify how effectively an organization meets its cybersecurity goals. They are important because they provide insights into the effectiveness of security measures, highlight areas needing improvement, and align security initiatives with broader business objectives.
What are some examples of cybersecurity KPIs?
Examples of cybersecurity KPIs include incident response times, the frequency of detected threats, and compliance rates with regulatory standards.
How do cybersecurity KPIs impact patient trust in healthcare organizations?
Monitoring metrics such as the duration required to address a data breach is crucial because it significantly impacts patient trust and regulatory compliance. Effective management of these KPIs can help maintain patient confidence in the organization.
How has the focus on cybersecurity metrics changed in recent years?
In 2025, the focus on digital security metrics has intensified, with organizations increasingly recognizing their role in evaluating defenses against emerging threats. Effective measurement of security effectiveness enhances overall organizational performance.
Why are incident response times a critical performance indicator?
Incident response times are critical because they assess the impact of incident response efforts. Quick mobilization of specialized teams can minimize the spread of threats and improve overall cybersecurity effectiveness.
What actions can organizations take to enhance their cybersecurity strategy?
Organizations can enhance their cybersecurity strategy by setting clear KPIs, monitoring incident response times, educating personnel on digital security practices, and ensuring swift reactions to incidents like ransomware attacks.