
In today's digital landscape, cybersecurity is not just a technical issue; it's a critical business imperative. C-suite leaders must recognize that the stakes are higher than ever, as organizations face a barrage of sophisticated cyber threats. Implementing ten essential cybersecurity strategies is vital for enhancing your organization's security posture and safeguarding sensitive data.
First, consider the current landscape of cybersecurity threats. With data breaches and cyberattacks becoming increasingly common, the implications for healthcare organizations are profound. These threats not only jeopardize patient information but also expose organizations to regulatory penalties and reputational damage. Therefore, proactive measures are essential.
To effectively address these challenges, C-suite leaders should prioritize:
These strategies are crucial for ensuring compliance and protecting sensitive data. Have you assessed your organization's vulnerabilities lately? Regular evaluations can uncover weaknesses before they are exploited.
Moreover, fostering a culture of cybersecurity awareness among employees is paramount. Training programs that educate staff on recognizing phishing attempts and understanding security protocols can significantly reduce risk. Remember, your employees are your first line of defense.
In conclusion, the implementation of these ten cybersecurity strategies is not merely a recommendation; it is a necessity for any organization aiming to thrive in an increasingly complex digital environment. By taking decisive action now, C-suite leaders can fortify their organizations against potential threats and ensure a secure future.
In today’s world, where cyber threats are growing more sophisticated by the day, the onus of protecting sensitive data rests heavily on C-suite leaders. Particularly in the healthcare sector, organizations are grappling with unique challenges that demand immediate attention. The necessity for robust managed services cybersecurity strategies has never been more pressing. This article delves into ten essential strategies designed to not only bolster security posture but also empower executives to adeptly navigate the complexities of the current digital landscape. With the stakes at an all-time high, one must ask: are organizations truly ready to implement these strategies and shield themselves from the relentless evolution of cyber threats?
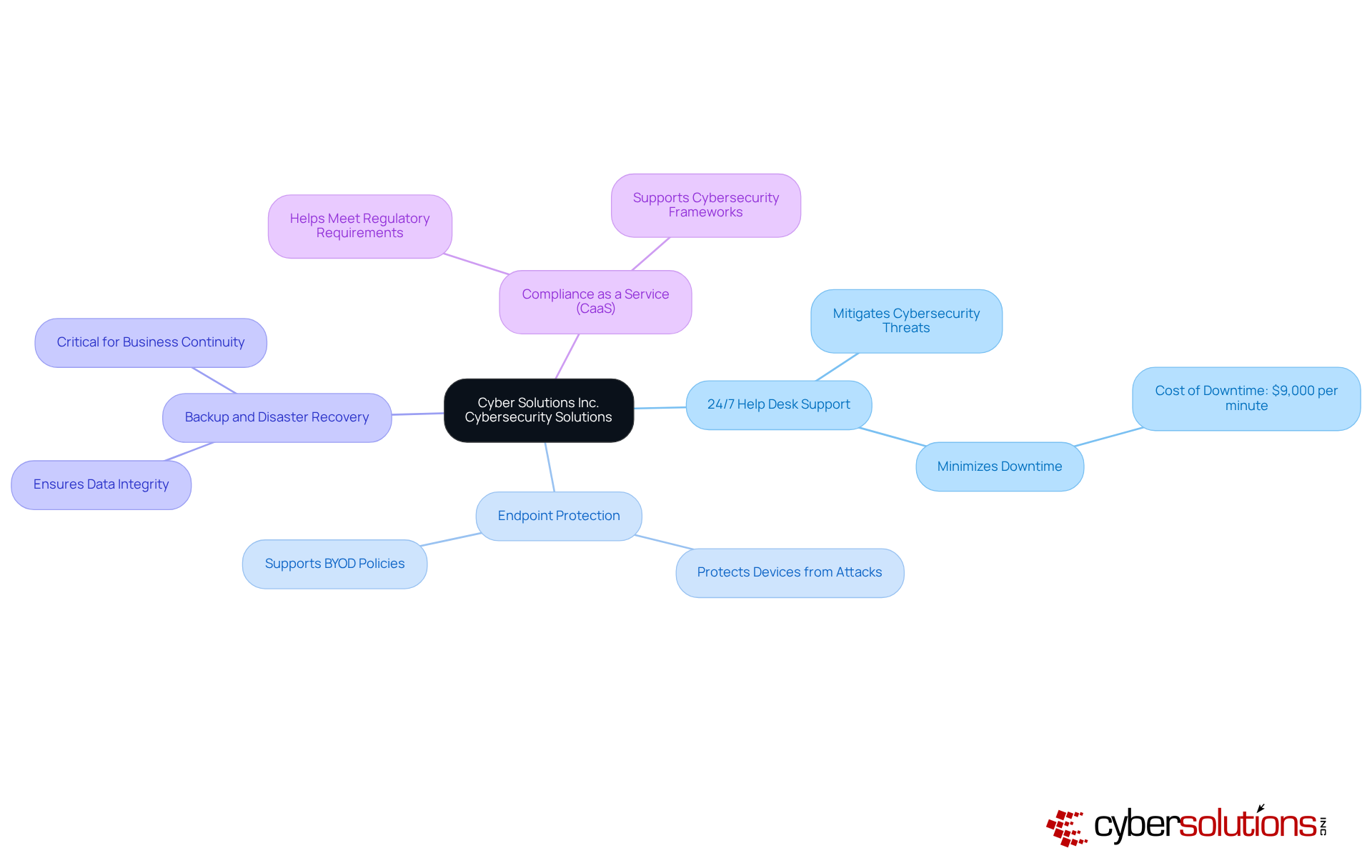
In today’s digital landscape, cybersecurity is not just an option; it’s a necessity, especially in healthcare. With the increasing complexity of cyber threats, healthcare organizations face unique challenges that demand immediate attention. Cyber Solutions Inc. stands ready to provide a comprehensive range of managed services cyber security and IT services tailored specifically for industries like healthcare, finance, manufacturing, and government.
Our key offerings include:
These managed services cyber security are crucial, as a staggering 82% of companies are expected to rely on managed IT services by 2025, highlighting a growing dependence on external expertise to enhance protection and operational efficiency. For instance, the implementation of 24/7 help desk support has proven effective in mitigating cybersecurity threats, allowing businesses to respond swiftly to incidents and minimize downtime, which can cost companies up to $9,000 per minute.
Consider a recent case study involving a healthcare provider: our rapid deployment of an incident response team led to a swift recovery from a ransomware attack, ultimately strengthening their security measures to protect sensitive patient data. By leveraging advanced technologies and expert knowledge, Cyber Solutions empowers organizations to focus on their core operations while ensuring their IT infrastructure remains secure and compliant with industry regulations.
Current trends indicate a significant shift towards managed services cyber security, with a projected market growth rate of 11.8% from 2025 to 2032. This growth is driven by the rising complexity of cyber dangers, necessitating proactive measures and continuous monitoring. Cyber Solutions offers 24/7 network monitoring and alert services to detect anomalies and potential vulnerabilities, ensuring that suspicious activities are addressed before they escalate into threats.
As organizations navigate evolving digital threats, customized security measures are vital. C-Suite leaders must prioritize investing in comprehensive cybersecurity strategies to safeguard their operations and maintain compliance. Are you ready to take the necessary steps to protect your organization? Let Cyber Solutions guide you in fortifying your cybersecurity posture.
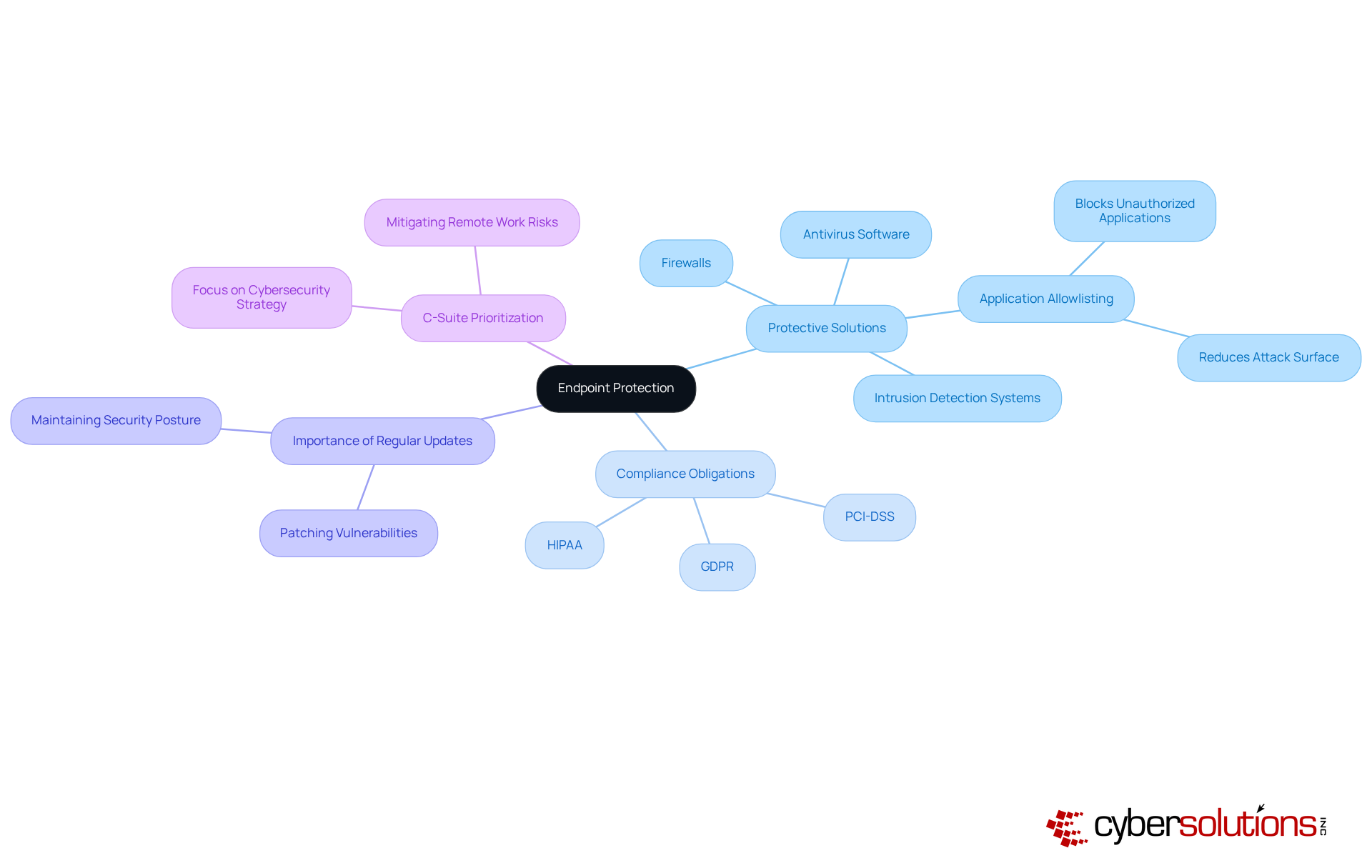
In today's digital landscape, managed services cyber security is not just an option; it's a necessity, especially in the healthcare sector. With the increasing number of devices accessing networks, implementing endpoint protection is crucial. This involves deploying protective solutions that monitor and manage these devices, including:
One standout feature is application allowlisting, a proactive measure that blocks all applications except those explicitly approved. This significantly reduces the attack surface, making it a vital component of any cybersecurity strategy.
Frequent updates and patches are essential to safeguard against vulnerabilities, but the proactive nature of application allowlisting sets it apart from conventional protective measures. It not only enhances security but also helps organizations meet compliance obligations such as:
C-suite leaders, particularly CFOs, must prioritize managed services cyber security, including endpoint protection and application allowlisting, as part of their overall cybersecurity approach. This is especially important in mitigating risks associated with remote work and mobile devices.
To bolster your organization's security posture, consider conducting regular reviews of your application allowlist. Ensuring it remains up-to-date and effective is key to staying ahead of potential threats. By taking these proactive steps, healthcare organizations can better protect sensitive data and maintain trust with patients and stakeholders alike.
In today's rapidly evolving digital landscape, the significance of advanced risk detection systems cannot be overstated. Organizations must recognize potential cyber risks in real-time, leveraging machine learning algorithms and behavioral analytics to identify anomalies effectively. As we approach 2025, the urgency for real-time danger detection grows, especially in sectors like healthcare where the stakes are high. Did you know that AI-driven systems can detect cyberattacks 85% faster than traditional tools? This remarkable speed not only enhances response times but also significantly reduces the risk of data breaches.
C-suite leaders, particularly CFOs, should prioritize investments in threat intelligence platforms that deliver actionable insights. These platforms enable swift responses to emerging threats, ensuring that organizations remain one step ahead of cybercriminals. For instance, large banks are already utilizing AI-powered behavior analytics to monitor login patterns and flag suspicious activities. Similarly, healthcare providers have successfully implemented AI-driven email filtering tools to combat phishing attacks. These real-world examples illustrate a growing trend: by adopting cutting-edge technologies, companies can bolster their cybersecurity posture and ensure operational resilience.
As cyber risks continue to evolve, the need for robust cybersecurity measures becomes increasingly critical. Organizations that invest in advanced detection systems not only protect their data but also safeguard their reputation and trust with clients. The question remains: are you ready to take action and fortify your defenses against the ever-present threat of cyberattacks? Embrace these technologies today and secure your organization's future in an increasingly complex digital environment.

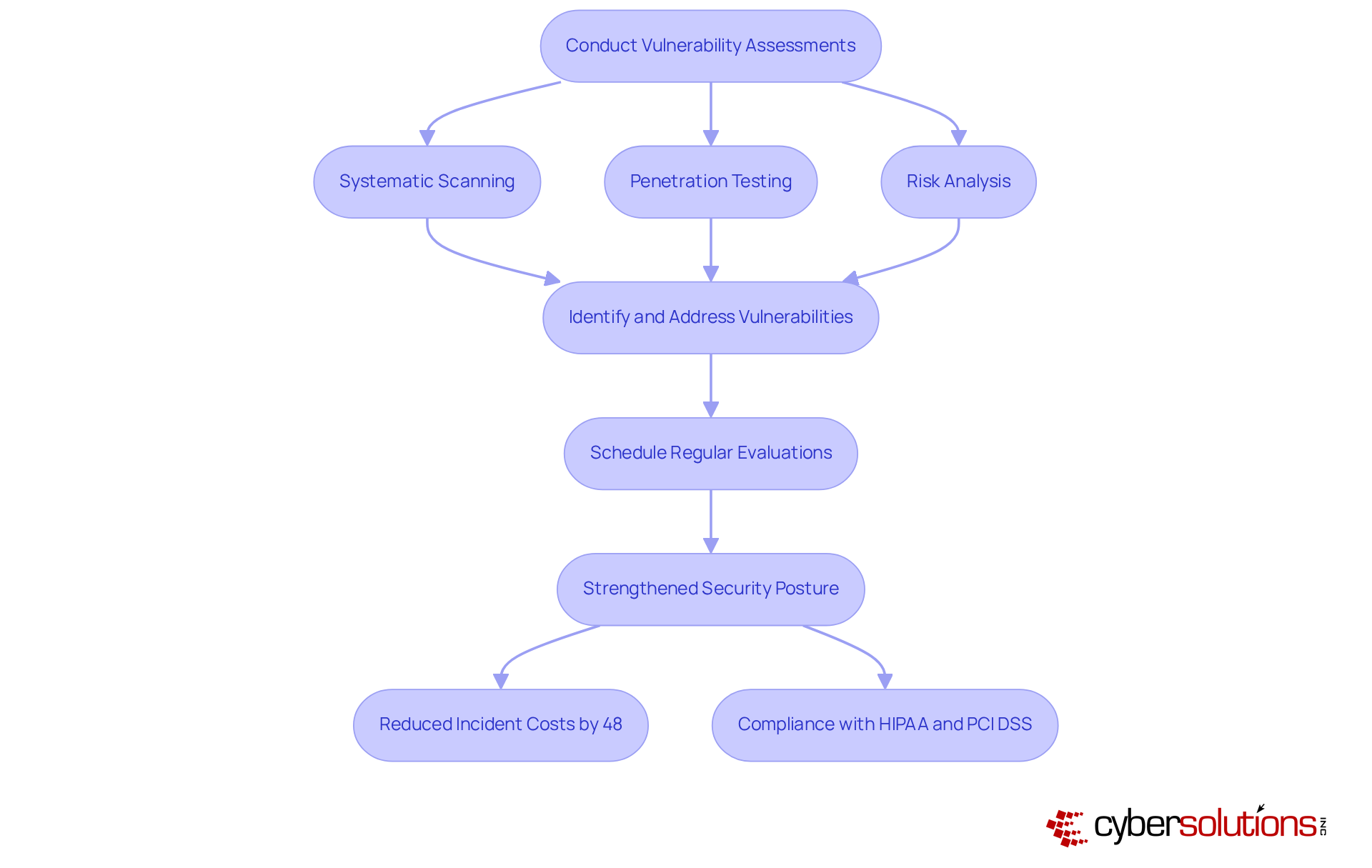
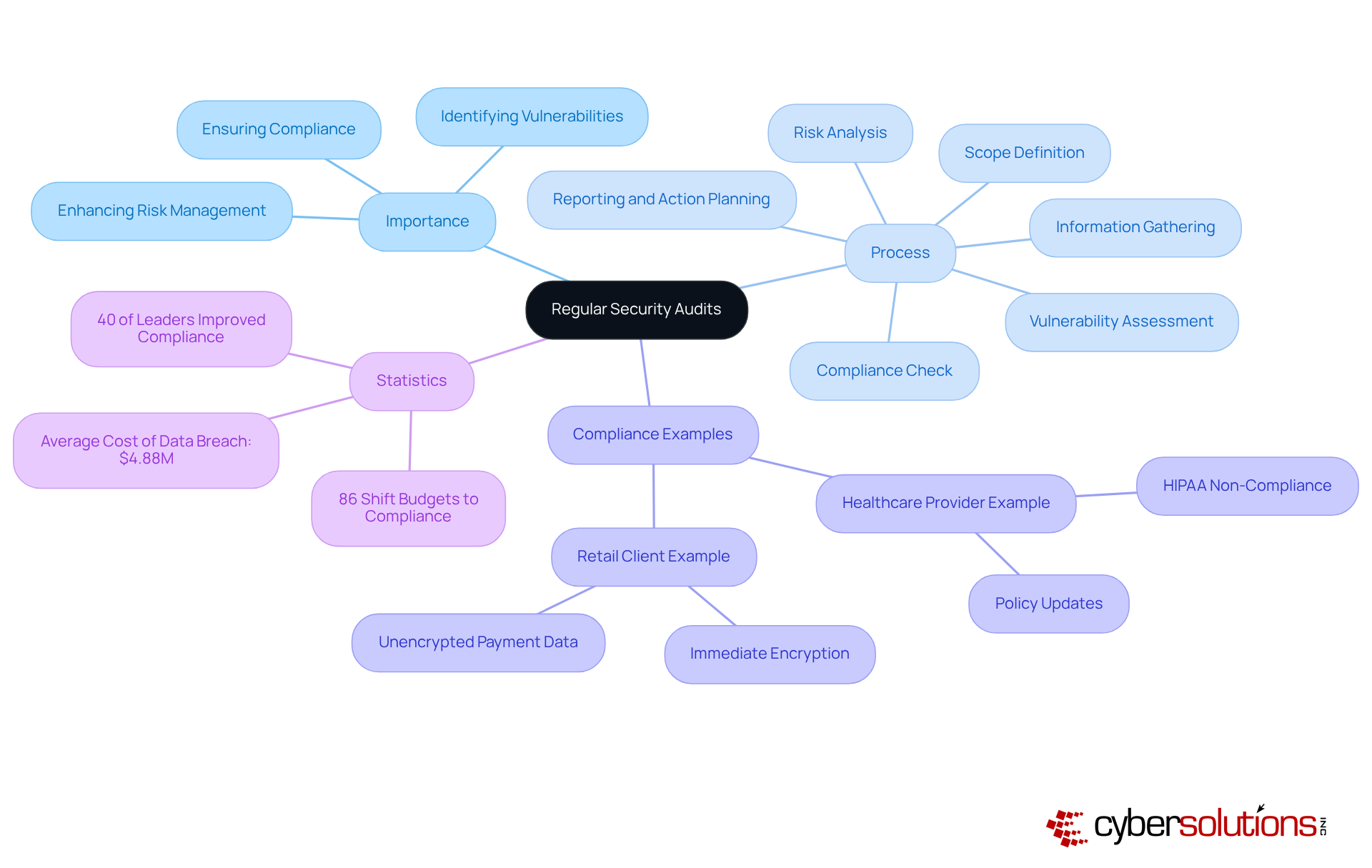
Routine vulnerability evaluations are essential for identifying and addressing weaknesses within a company's systems and networks. In today's landscape, where cyber threats are increasingly sophisticated, this proactive approach is not just beneficial—it's vital. Systematic scanning uncovers vulnerabilities, while penetration testing and risk analysis help pinpoint potential entry points for attackers. Organizations that conduct regular evaluations significantly enhance their protective stance, demonstrating compliance with industry standards like HIPAA and PCI DSS, and avoiding costly fines.
C-suite executives must prioritize establishing a regular timetable for these evaluations. Not only do they bolster safety, but they also build trust with stakeholders by showcasing a commitment to data protection. Expert insights reveal that integrating vulnerability assessments into the security strategy can reduce incident costs by an impressive 48%. This statistic underscores the necessity of a proactive security posture.
Moreover, organizations that consistently conduct these evaluations are better equipped to adapt to the ever-evolving threat landscape. This adaptability ensures that their defenses remain robust against emerging cyber threats. By fostering a culture of continuous improvement in security practices, companies can effectively safeguard their assets and maintain operational resilience.
In conclusion, the importance of routine vulnerability evaluations cannot be overstated. They are not merely a checkbox on a compliance list; they are a strategic imperative that enhances security, builds stakeholder confidence, and ultimately protects the organization from the financial and reputational damage of cyber incidents.
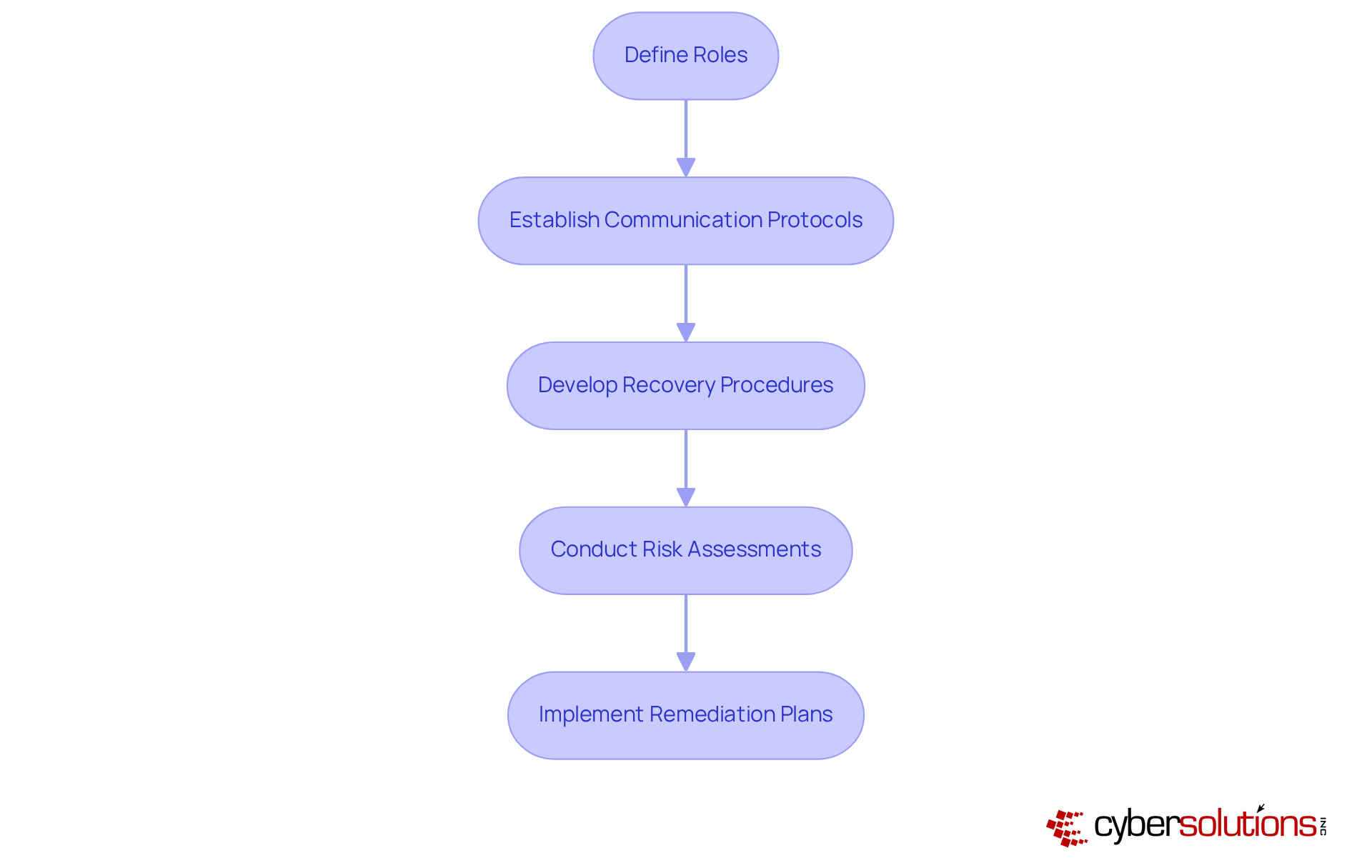
In today’s healthcare landscape, the importance of a robust cybersecurity strategy cannot be overstated. Establishing an incident response plan is essential; it involves creating a documented strategy that outlines the steps to take in the event of a cybersecurity breach. This plan should clearly define roles, communication protocols, and recovery procedures. C-suite executives must ensure their teams are well-educated and that the strategy is consistently evaluated to adapt to evolving risks.
Moreover, thorough documentation is crucial for compliance, particularly with standards like HIPAA. This includes risk assessments and tailored remediation plans. Cyber Solutions offers Compliance as a Service (CaaS), simplifying the navigation of regulatory requirements. This service ensures that businesses are audit-ready and can effectively manage incidents while maintaining compliance.
Are you prepared to face the unique challenges posed by cybersecurity threats? With the right strategies in place, healthcare organizations can not only protect sensitive information but also enhance their overall operational resilience. Cyber Solutions stands ready to assist in fortifying your defenses and ensuring compliance in an increasingly complex regulatory environment.
In today's rapidly evolving digital landscape, compliance is not just a regulatory requirement; it's a critical component of managed services cyber security strategy, especially in healthcare. Compliance as a Service (CaaS) empowers organizations to outsource their compliance needs to specialized providers like Cyber Solutions, effectively navigating the complexities of regulations such as HIPAA, PCI-DSS, and GDPR, and ensuring robust managed services cyber security.
Our CaaS solutions offer comprehensive services, including:
This approach not only simplifies compliance but also ensures that organizations remain vigilant against emerging threats. With our flat-rate pricing model, unexpected IT expenses become a thing of the past, allowing for predictable budgeting and financial planning for compliance services.
C-suite leaders, particularly CFOs, should seriously consider CaaS as a means to streamline compliance processes, reduce operational costs, and ensure adherence to industry standards. This strategic move enhances audit readiness and supports sustainable business growth. Moreover, our Incident Response services are a key component of our managed services cyber security, complementing CaaS by swiftly identifying and addressing risks, ensuring business continuity while maintaining compliance.
In a world where cybersecurity threats are increasingly sophisticated, can your organization afford to overlook compliance? By partnering with Cyber Solutions, you not only mitigate risks but also position your organization for success in a challenging regulatory environment.
Establishing a comprehensive backup and disaster recovery plan is essential for maintaining business continuity in the face of disruptions. In today's landscape, where cybersecurity threats loom large, this strategy must include:
to ensure that critical information remains secure and readily accessible. C-suite leaders must prioritize these measures; after all, the average downtime for businesses lacking effective disaster recovery solutions can exceed $5,600 per minute, with 40% of such businesses never reopening after a disaster. By implementing robust recovery protocols, organizations can minimize downtime, safeguard their operations, and enhance their resilience against potential crises.
In light of recent incidents, such as the ransomware attack on a healthcare provider, the importance of rapid incident response cannot be overstated. Having an incident response team on-site within 24 hours can significantly contain threats and minimize damage. A layered approach—including:
enables a faster and more complete recovery. For instance, the healthcare provider not only recovered ahead of schedule but also improved its security measures, demonstrating the effectiveness of these strategies. By showcasing a reliable and efficient response, companies can cultivate strong partnerships with service providers, enhancing their overall cybersecurity posture.
Real-world examples demonstrate that businesses with well-structured disaster recovery plans not only recover faster but also maintain customer trust and compliance with regulatory requirements, ultimately securing their competitive advantage in the market. To ensure the effectiveness of these plans, it is vital to regularly test and update them. C-suite leaders should consider consulting with experts to review and enhance their disaster recovery strategies, ensuring they are prepared for any potential disruptions.
Implementing co-managed IT support is crucial for organizations aiming to strengthen their internal teams with external expertise. In today’s landscape, where cybersecurity threats are increasingly sophisticated, this strategic alliance not only provides access to specialized skills but also ensures ongoing supervision through managed services cyber security and enhanced protective solutions. With 24/7 network oversight, organizations can swiftly identify anomalies and potential vulnerabilities, making it an essential strategy for C-suite leaders looking to tackle skill gaps and bolster their security posture without the burdensome process of extensive hiring.
Organizations that have embraced co-managed IT services report significant improvements in their managed services cyber security frameworks. This allows them to respond rapidly to risks while maintaining operational efficiency. By leveraging external knowledge, they can navigate the complexities of digital security more effectively with managed services cyber security, ensuring resilience in an ever-evolving online environment. Moreover, a layered strategy—including incident response teams and proactive network hardening techniques—further enhances recovery and protection against cyber threats.
In conclusion, co-managed IT support is not just a tactical decision; it’s a strategic imperative for organizations committed to safeguarding their assets and ensuring robust managed services cyber security. As the digital landscape continues to evolve, the need for such partnerships becomes increasingly clear. Are you ready to take the next step in fortifying your organization’s defenses?
In today's digital landscape, comprehensive cybersecurity training is not just beneficial—it's essential. Employees must be equipped with the skills to identify and respond to potential threats effectively. Programs that focus on key areas like:
are crucial. C-suite leaders, particularly CFOs, must prioritize ongoing training initiatives to foster a culture of security awareness. This proactive approach significantly reduces the likelihood of successful attacks.
Consider this: studies reveal that firms with robust training programs can lower employee vulnerability to phishing attacks by as much as 86%. This statistic underscores the importance of regular training, which enhances employees' ability to recognize sophisticated threats, including the increasingly effective AI-generated phishing attempts. By investing in ongoing education, companies not only safeguard their digital assets but also cultivate a proactive culture that empowers employees to actively protect company data.
The implications for healthcare organizations are profound. With the rise of cyber threats, the need for a well-informed workforce is more critical than ever. Cyber Solutions can address these challenges effectively, ensuring that employees are not just passive recipients of information but active participants in the security process. This shift not only protects sensitive data but also builds a resilient organizational culture.
Routine assessments are vital for evaluating a company's managed services cyber security practices, identifying weaknesses, and ensuring compliance with regulatory standards. This comprehensive process encompasses evaluations of policies, procedures, and technical controls, allowing organizations to uncover vulnerabilities before they can be exploited. For example, a healthcare provider's audit uncovered non-compliance with HIPAA, leading to immediate policy updates that significantly mitigated data breach risks.
C-suite leaders must establish a systematic schedule for these audits. Not only do they bolster security posture, but they also adapt to the ever-evolving threat landscape. Did you know that 40% of business leaders reported enhancements in their risk management strategies to achieve better compliance in the past year? Regular audits in managed services cyber security provide organizations with the visibility and control essential for safeguarding sensitive data and ensuring operational resilience.
Expert insights underscore the importance of these audits. As one cybersecurity leader aptly stated, "Regular audits provide entities the visibility and control they require to safeguard what is important." By prioritizing managed services cyber security audits, C-suite executives can ensure their organizations remain compliant and fortified against emerging cyber threats.
In today’s rapidly changing digital landscape, the need for strong managed services cybersecurity strategies is more critical than ever, especially for C-suite leaders. With organizations facing a surge in cyber threats, it’s essential to implement comprehensive solutions that not only protect assets but also ensure compliance with industry regulations. The strategies outlined here serve as a roadmap for executives aiming to bolster their cybersecurity posture and shield their organizations from potential breaches.
Key insights include:
By adopting endpoint protection and utilizing compliance as a service, organizations can proactively mitigate risks and maintain business continuity. Furthermore, integrating employee training programs empowers staff to recognize and respond to threats, fostering a culture of security awareness that is vital in today’s environment.
Ultimately, taking decisive action to strengthen cybersecurity measures transcends mere defense; it’s a strategic imperative for organizational resilience and trust. C-suite leaders are urged to embrace these best practices and cultivate a proactive approach to cybersecurity. By doing so, they can adeptly navigate the complexities of the digital landscape and safeguard their organizations against the ever-present threat of cyberattacks.
What services does Cyber Solutions Inc. provide for cybersecurity?
Cyber Solutions Inc. offers a comprehensive range of managed services including 24/7 help desk support, endpoint protection, backup and disaster recovery, and compliance as a service (CaaS).
Why is managed IT service expected to grow by 2025?
A staggering 82% of companies are expected to rely on managed IT services by 2025 due to the increasing complexity of cyber threats, which necessitates external expertise to enhance protection and operational efficiency.
How does 24/7 help desk support benefit organizations?
24/7 help desk support helps mitigate cybersecurity threats by allowing businesses to respond swiftly to incidents, minimizing downtime, which can cost companies up to $9,000 per minute.
What is the significance of endpoint protection in cybersecurity?
Endpoint protection is crucial as it involves deploying protective solutions that monitor and manage devices accessing networks, helping to safeguard against potential threats.
What is application allowlisting and why is it important?
Application allowlisting is a proactive security measure that blocks all applications except those explicitly approved, significantly reducing the attack surface and enhancing overall security.
How can organizations ensure compliance with regulations through cybersecurity?
Implementing endpoint protection and application allowlisting helps organizations meet compliance obligations such as HIPAA, PCI-DSS, and GDPR.
What role does threat detection play in cybersecurity?
Advanced threat detection systems help organizations recognize potential cyber risks in real-time, enabling them to respond promptly and effectively to emerging threats.
How can AI improve threat detection?
AI-driven systems can detect cyberattacks 85% faster than traditional tools, enhancing response times and significantly reducing the risk of data breaches.
What should C-suite leaders prioritize in their cybersecurity strategy?
C-suite leaders, especially CFOs, should prioritize investments in managed services cybersecurity, including endpoint protection, application allowlisting, and threat intelligence platforms for actionable insights.
What are the potential consequences of not investing in cybersecurity?
Organizations that fail to invest in robust cybersecurity measures risk data breaches, loss of reputation, and diminished trust with clients and stakeholders.