
In today's rapidly evolving digital landscape, mastering cybersecurity is paramount for healthcare CFOs. The protection of sensitive patient information and the mitigation of financial risks associated with cyber threats have never been more critical. With cyberattacks on the rise in the healthcare sector, it is essential for CFOs to implement robust security measures.
To effectively safeguard their organizations, CFOs must prioritize essential security practices such as:
Statistics reveal a troubling increase in cyberattacks, underscoring the urgent need for comprehensive security strategies. How can healthcare organizations navigate these unique challenges? The answer lies in adopting proactive Cyber Solutions that address these threats head-on.
By understanding the current landscape of cybersecurity threats, healthcare CFOs can better appreciate the implications for their organizations. Implementing effective security controls not only protects patient data but also ensures financial stability in an increasingly perilous environment. It is time for CFOs to take decisive action and invest in the security measures that will safeguard their organizations against the ever-present risk of cyber threats.
In an era where cyber threats loom larger than ever, healthcare organizations stand at a pivotal crossroads, navigating the delicate balance between safeguarding sensitive patient data and adhering to stringent regulatory requirements.
For CFOs, mastering digital security controls transcends mere technical necessity; it emerges as a strategic imperative that not only protects financial health but also enhances operational resilience.
With a staggering 92% of medical entities targeted by cyberattacks in the past year, the pressing question arises: how can healthcare leaders effectively implement and adapt these security measures to comply with regulations like HIPAA while fortifying their institutions against evolving threats?
The answer lies in a proactive approach to cybersecurity that integrates compliance with robust defense strategies.
Digital security controls are essential for safeguarding healthcare institutions against cyber threats and ensuring compliance with regulations such as HIPAA. These mechanisms include essential practices like:
All of which are part of effective digital security controls, complemented by application allowlisting, which stands as the gold standard in cybersecurity. Application allowlisting proactively prevents malware and unauthorized software from executing, significantly reducing the attack surface and minimizing vulnerabilities. For CFOs, grasping these digital security controls is vital not only for protecting patient information but also for mitigating financial risks associated with data breaches. In 2023, medical entities faced a troubling 92% rate of cyberattack targeting, up from 88% the previous year, underscoring the urgent need for robust protective strategies. By investing in these measures, including application allowlisting, healthcare organizations can avoid costly penalties—averaging $9.8 million per breach, a decrease from $10.9 million in 2023—and reputational damage, fostering a more secure operational environment.
Moreover, aligning financial strategies with digital security controls can significantly enhance return on investment (ROI). Organizations leveraging AI and automation tools have managed to detect and contain cyber incidents 98 days faster than average, resulting in savings of nearly $1 million. This proactive stance not only that disrupt operations but also curtails additional expenses related to recovery and compliance failures. As cybersecurity regulations intensify globally, with new legislation mandating stricter protection measures, the importance of digital security controls, including comprehensive HIPAA compliance solutions, in maintaining compliance and operational integrity cannot be overstated.
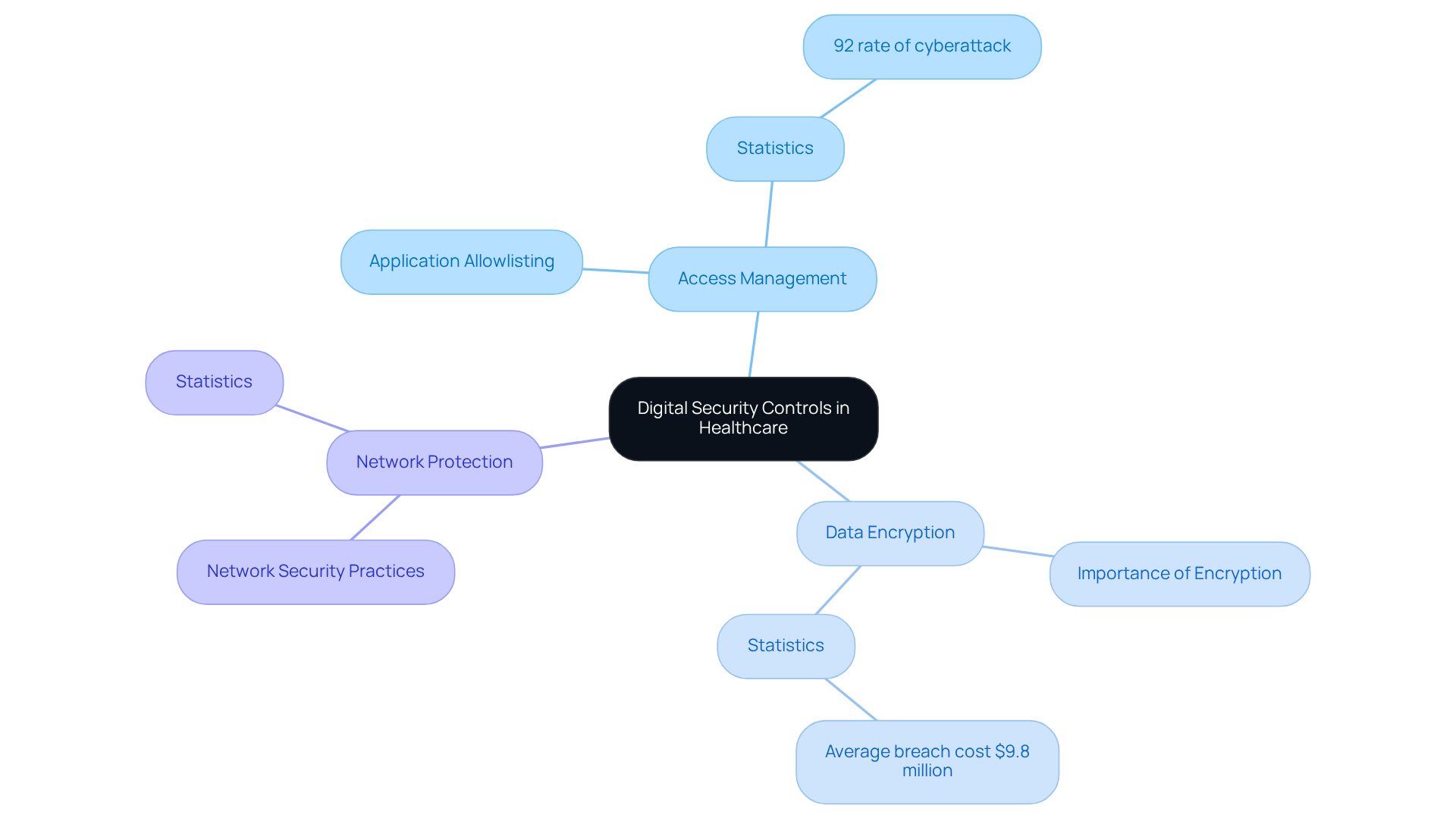
In today's healthcare landscape, the implementation of robust cybersecurity measures is not just a regulatory requirement but a critical necessity for safeguarding sensitive patient data. Healthcare organizations face a myriad of cybersecurity threats, and it is imperative that they adopt a comprehensive approach to security that includes digital security controls alongside various control types.
By understanding and implementing these vital security measures, CFOs can significantly enhance their organizations' defenses against cyber threats while ensuring compliance with industry standards. Continuous monitoring and proactive risk management are essential for maintaining HIPAA compliance. Partnering with Cyber Solutions provides organizations with expert guidance and support in these ongoing efforts, ensuring that sensitive patient information remains secure.
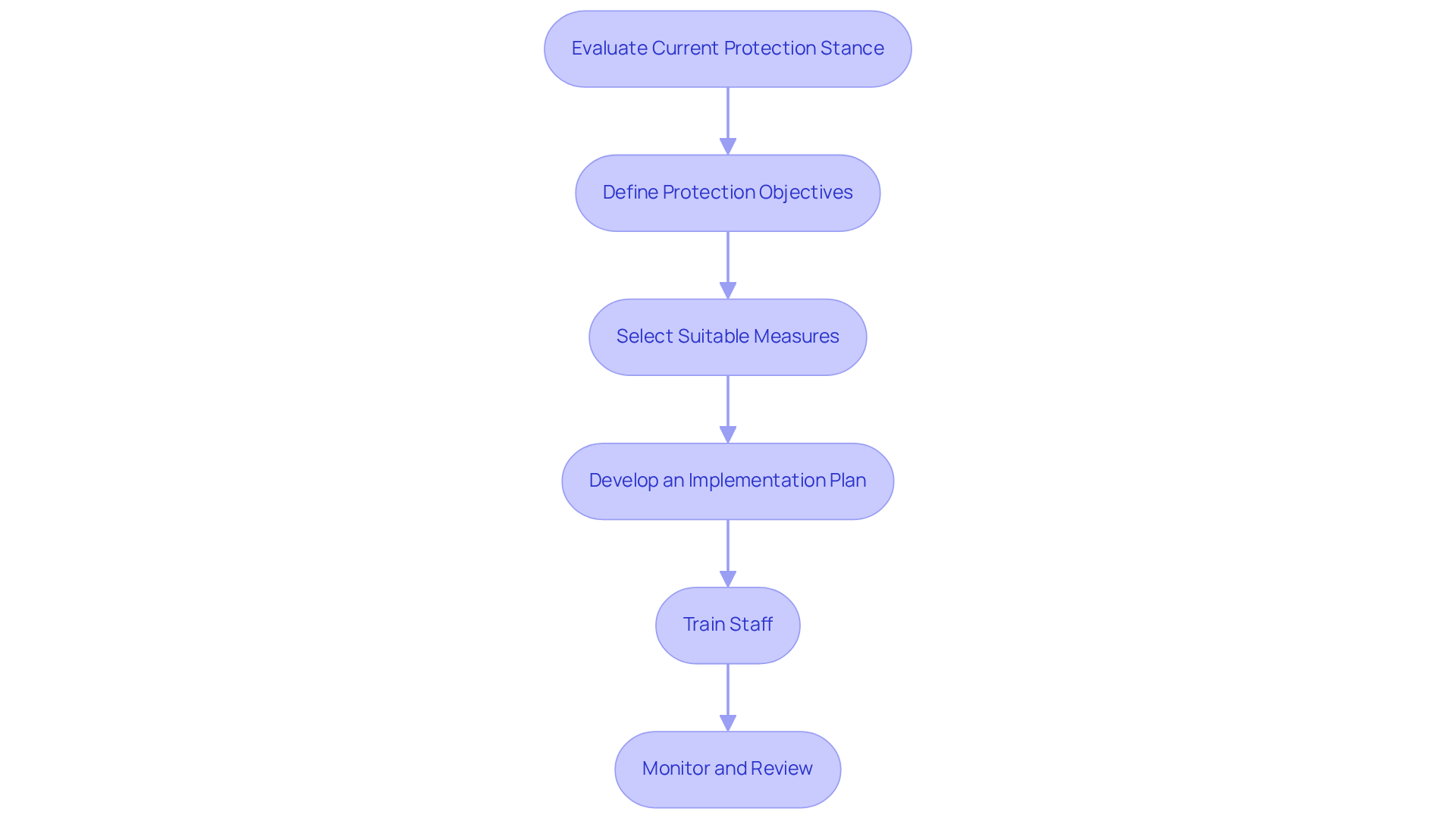
In today's healthcare landscape, where cybersecurity threats are increasingly sophisticated, implementing effective digital security controls is essential. A systematic and strategic approach is necessary to implement digital security controls that will safeguard sensitive information. Here’s a step-by-step guide tailored for healthcare organizations:
By following these steps, financial executives can ensure their institutions are equipped with effective digital security controls that not only protect sensitive information but also align with financial strategies and operational objectives.
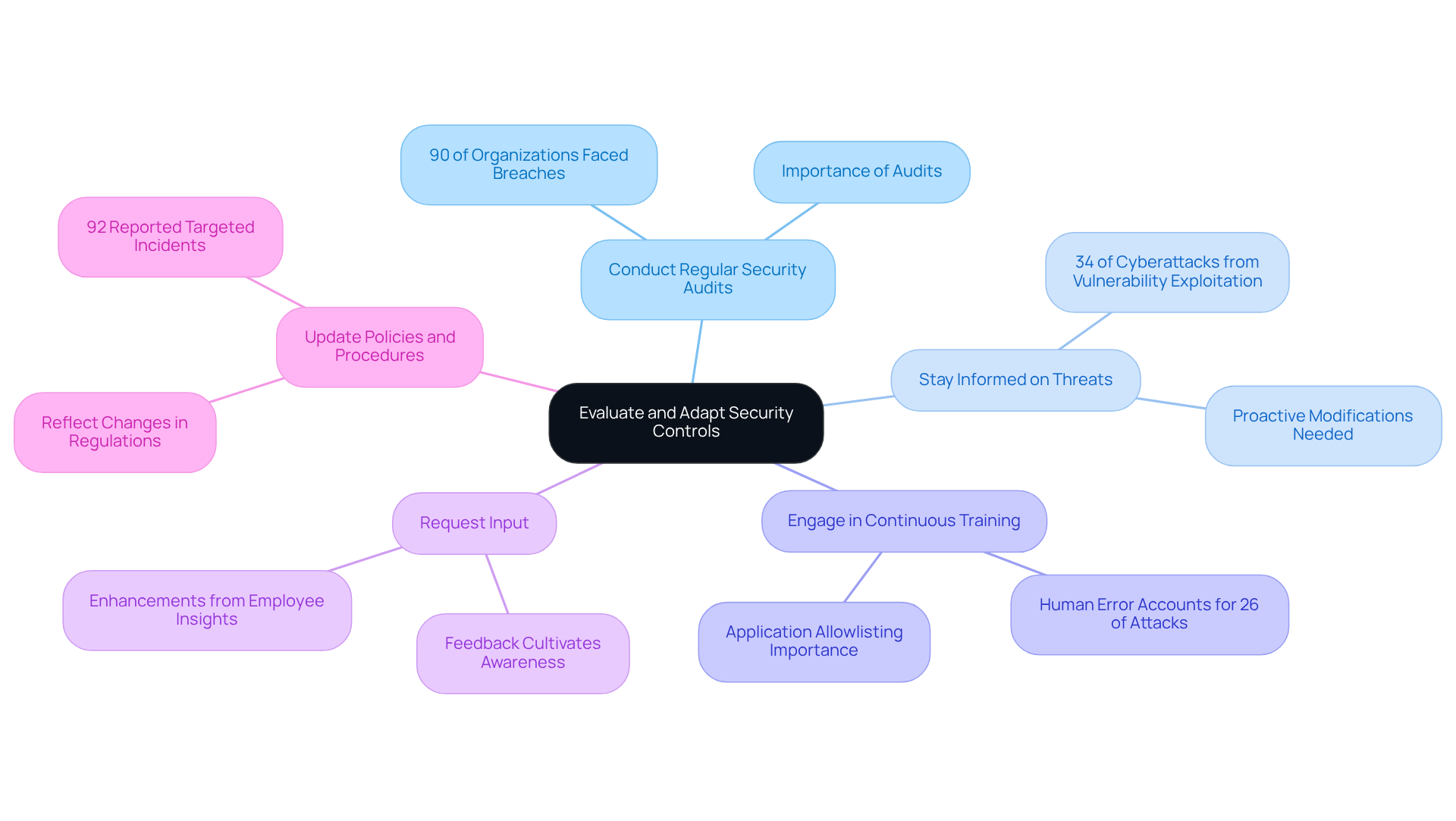
In today's digital landscape, the importance of digital security controls for a robust cybersecurity stance in healthcare cannot be overstated. Medical institutions must continually assess and modify their digital security controls to safeguard sensitive data and ensure patient care. Given the unique challenges faced by CFOs in this sector, implementing key practices for continuous improvement is essential.
Furthermore, the impact of ransomware assaults cannot be ignored; they have resulted in considerable operational interruptions, causing an average downtime of almost 19 days for U.S. medical facilities. By committing to continuous evaluation and adaptation, including the implementation of application allowlisting and rapid incident response strategies, healthcare CFOs can ensure their organizations remain resilient against cyber threats and compliant with industry regulations. This commitment ultimately safeguards patient care and sensitive data.
Digital security controls are not merely a regulatory requirement in healthcare; they are a fundamental necessity for the protection of sensitive patient information and the financial integrity of healthcare organizations. As cyber threats become increasingly sophisticated, CFOs must prioritize the implementation of comprehensive security measures that encompass:
These practices are crucial not only for safeguarding patient data but also for mitigating the financial risks associated with data breaches.
The alarming rise in cyberattacks targeting healthcare institutions underscores the significant financial implications of data breaches. By investing in robust digital security controls, organizations can protect themselves from costly penalties while enhancing their operational efficiency and return on investment. Continuous monitoring, regular audits, and employee training are essential components of a proactive cybersecurity strategy that can adapt to evolving threats and ensure compliance with regulations like HIPAA.
Ultimately, the commitment to effective digital security controls is vital for the sustainability and reputation of healthcare organizations. By embracing best practices and fostering a culture of security awareness, CFOs can lead their institutions toward a more secure future, ensuring that patient care remains uncompromised while navigating the complexities of the digital landscape. The stakes are high, and the time to act is now—prioritizing cybersecurity is not just a choice; it is an imperative for the healthcare sector.
What are digital security controls in healthcare?
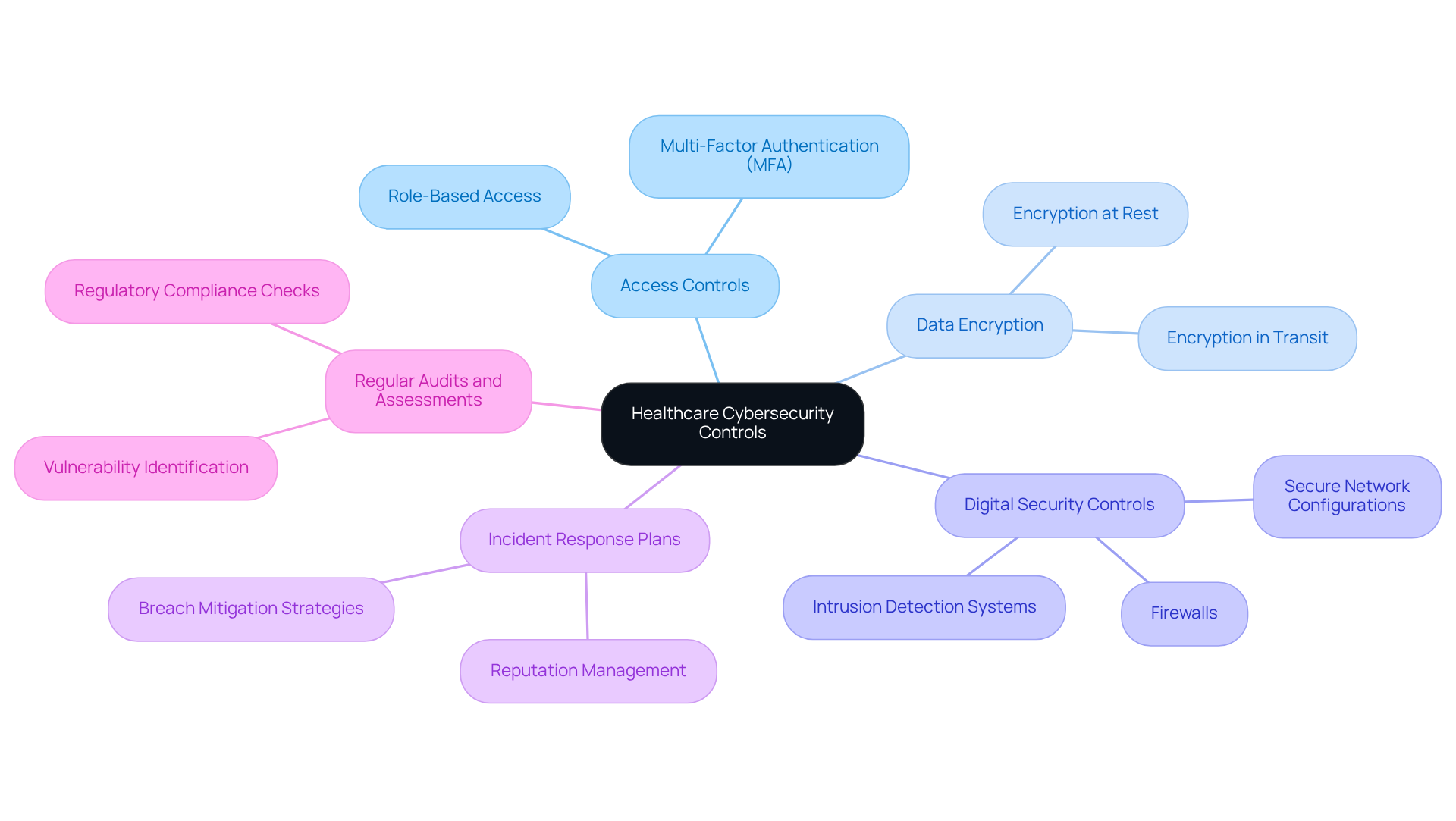
Digital security controls in healthcare are essential practices designed to protect healthcare institutions from cyber threats and ensure compliance with regulations such as HIPAA. Key components include access management, data encryption, and network protection.
What is application allowlisting and why is it important?
Application allowlisting is a cybersecurity practice that prevents malware and unauthorized software from executing. It is considered the gold standard in cybersecurity as it significantly reduces the attack surface and minimizes vulnerabilities.
Why is it important for CFOs to understand digital security controls?
For CFOs, understanding digital security controls is crucial for protecting patient information and mitigating financial risks associated with data breaches, which can lead to significant financial penalties and reputational damage.
What was the rate of cyberattacks targeting medical entities in 2023?
In 2023, medical entities faced a 92% rate of cyberattack targeting, an increase from 88% in the previous year.
What are the financial implications of data breaches in healthcare?
The average cost of a data breach in healthcare is $9.8 million, which has decreased from $10.9 million in 2022. However, the financial impact can still be substantial, highlighting the importance of robust security measures.
How can aligning financial strategies with digital security controls enhance ROI?
Aligning financial strategies with digital security controls can enhance ROI by enabling organizations to detect and contain cyber incidents more quickly, with reported savings of nearly $1 million due to faster response times.
How do AI and automation tools impact cybersecurity in healthcare?
Organizations that leverage AI and automation tools have been able to detect and contain cyber incidents 98 days faster than average, reducing the likelihood of operational disruptions and lowering additional expenses related to recovery and compliance failures.
Why is compliance with cybersecurity regulations becoming more critical?
Compliance with cybersecurity regulations is becoming increasingly critical due to the introduction of new legislation mandating stricter protection measures, making it essential for healthcare organizations to implement comprehensive digital security controls, including HIPAA compliance solutions.